A Trusted Transaction Method for Remote Sensing Image Data Based on a Homomorphic Encryption Watermark and Blockchain
Abstract
1. Introduction
2. Proposed Method
3. Algorithm and Implementation
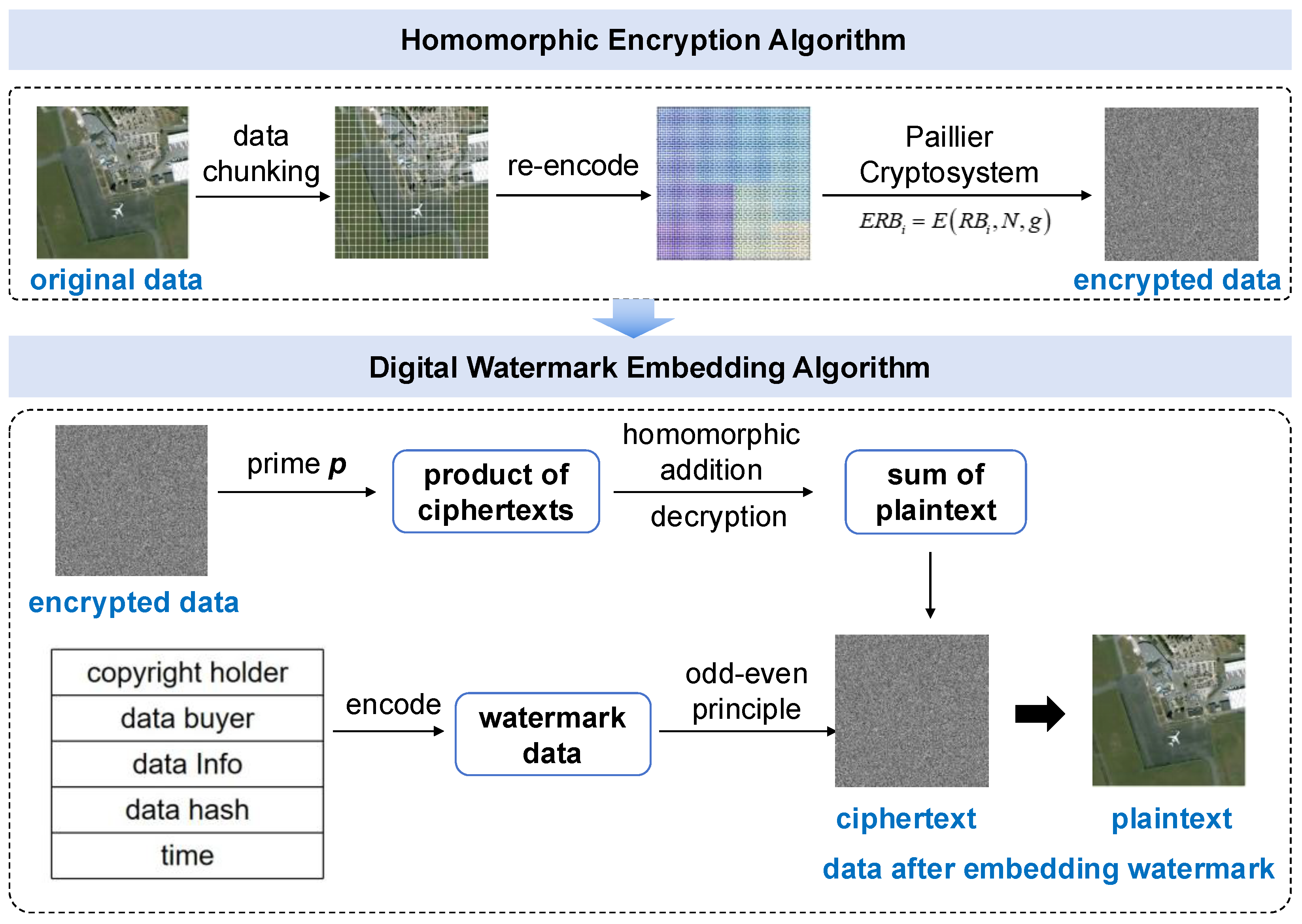
3.1. Digital Watermark Embedding Algorithm Based on Paillier Homomorphic Encryption
3.1.1. Homomorphic Encryption Algorithm
3.1.2. Digital Watermark Embedding Algorithm
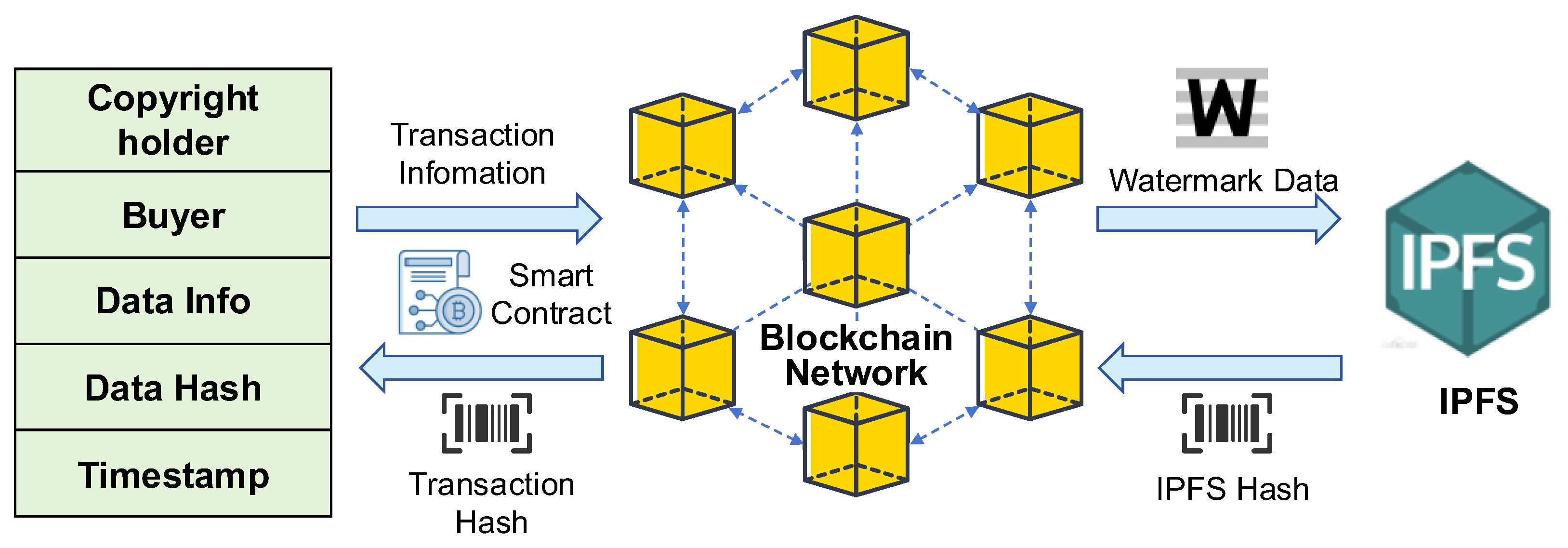
3.2. AntChain Combined with IPFS Depository Solution
| Contract 1 User Authentication Contract |
| Input: username, password, pubKey, userAddr Output: register status, login result, pubKey contract UserAuth { struct User { string username; bytes32 passwordHash; string pubKey; bool registered; } mapping(address => User) users; event Registered(address userAddr, string username); event LoginSuccess(address userAddr); event PublicKeySet(address userAddr, string pubKey); function register(string username, string password) public { users[msg.sender] = User(username, hash(password), getPublicKey(msg.sender), true); emit Registered(msg.sender, username); } function login(string password) public view returns (bool) { require(users[msg.sender].registered, “Not registered”); return (users[msg.sender].passwordHash == hash(password)); } function setPublicKey(string pubKey) public { require(users[msg.sender].registered, “Not registered”); users[msg.sender].pubKey = pubKey; emit PublicKeySet(msg.sender, pubKey); } function getPublicKey(address userAddr) public view returns (string) { require(users[userAddr].registered, “Not registered”); return users[userAddr].pubKey; } } |
| Contract 2 Transaction Deposit Contract |
| Input: receiver, dataHash, ipfsCid Output: transaction record, transaction count contract TransactionStorage { struct Transaction { address sender; address receiver; string dataHash; string ipfsCid; uint256 timestamp; } Transaction[] transactions; event TransactionStored(address sender, address receiver, string dataHash, string ipfsCid, uint256 timestamp); function storeTransaction(address receiver, string dataHash, string ipfsCid) public { add new Transaction(msg.sender, receiver, dataHash, ipfsCid, now); emit TransactionStored(msg.sender, receiver, dataHash, ipfsCid, now); } function getTransactionCount() public view returns (uint) { return transactions.length; } } |
| Contract 3 Transaction Verification Contract |
| Input: dataHash, ipfsCid, sender address Output: verification result, transaction details, transaction count contract TransactionVerifier { TransactionStorage storageContract; constructor(address storageAddress) public { storageContract = TransactionStorage(storageAddress); } function verifyTransactionByDataHash(string dataHash) public view returns (bool exists, address sender, address receiver, string ipfsCid, uint256 timestamp) { for each transaction in storageContract { if (hash(transaction.dataHash) == hash(dataHash)) { return (true, transaction.sender, transaction.receiver, transaction.ipfsCid, transaction.timestamp); } end if } end for return (false, null, null, null, 0); } function verifyTransactionByIPFSCid(string ipfsCid) public view returns (bool exists, address sender, address receiver, string dataHash, uint256 timestamp) { for each transaction in storageContract { if (hash(transaction.ipfsCid) == hash(ipfsCid)) { return (true, transaction.sender, transaction.receiver, transaction.dataHash, transaction.timestamp); } end if } end for return (false, null, null, null, 0); } function countTransactionsBySender(address sender) public view returns (uint count) { uint matchCount = 0; for each transaction in storageContract { if (transaction.sender == sender) { matchCount++; } end if } end for return matchCount; } } |
4. Trusted Transaction Model
4.1. Participants
4.2. Trading Model
4.2.1. Authentication Module
4.2.2. Transaction Module
4.2.3. Verification Module
- Watermark Extraction
- 2.
- Transaction Information Verification
5. Experiment and Analysis
5.1. Introduction of the Experiment
5.2. Experiment Design
5.2.1. Data Encryption and Watermark Embedding Experiment
5.2.2. Experiment on the Validity of Transaction Verification
5.2.3. Infringement Detection and Verification Experiment
5.2.4. Watermark Robustness Test
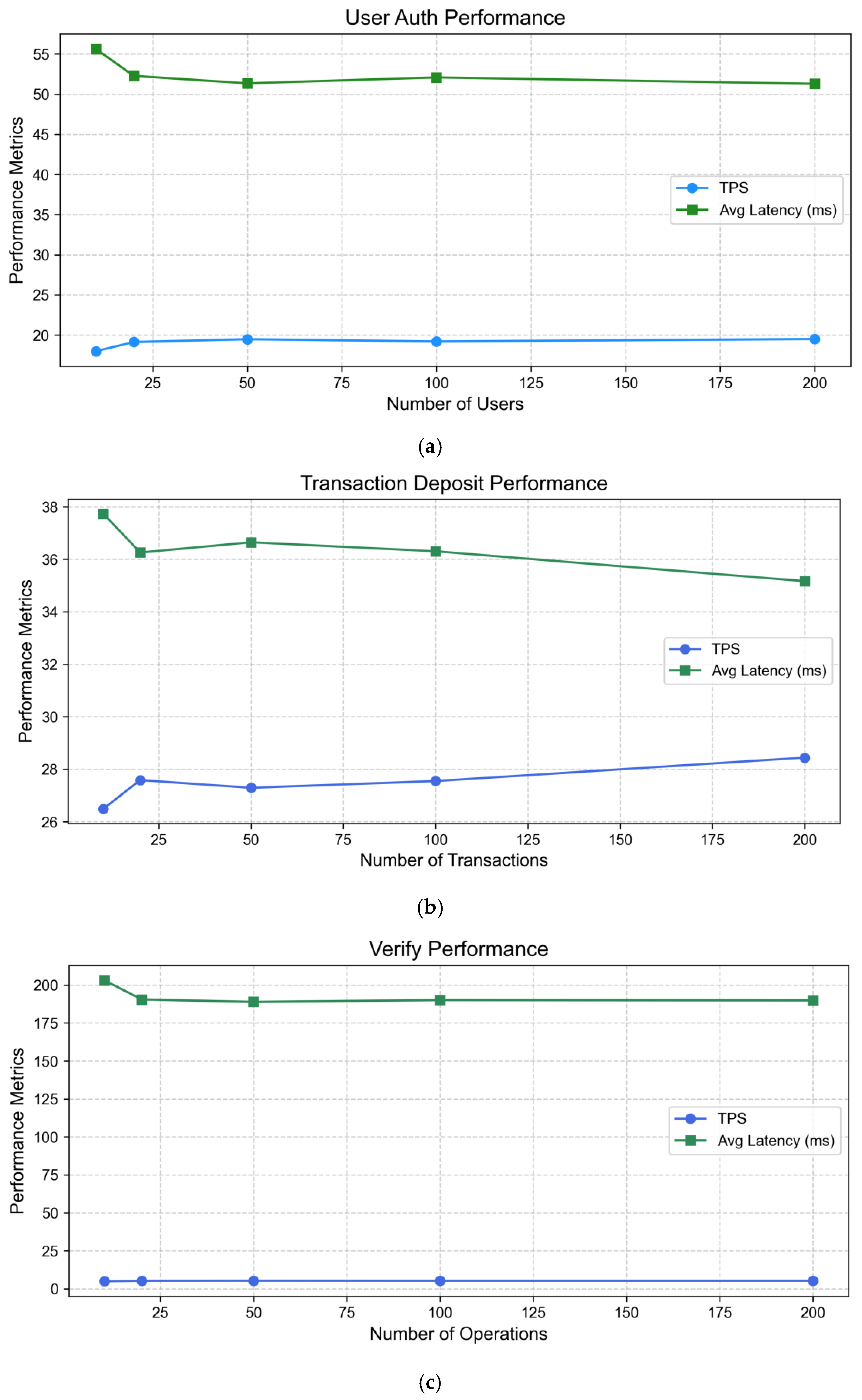
5.2.5. Smart Contract Execution Performance Test
6. Discussion
6.1. Transaction Security in the Proposed Model
6.1.1. Security for the Data Copyright Holder
6.1.2. Security for the Data Buyer
6.2. Fairness of the Proposed Model
6.3. Comparison with Existing Methods
6.3.1. Comparison with Traditional Databases
6.3.2. Comparison with Other Copyright Protection Models
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wang, X.; Zhang, L. A digital fingerprinting scheme for remote sensing images based on the homomorphic public key encryption algorithm. Remote Sens. Technol. Appl. 2022, 37, 532–538. [Google Scholar] [CrossRef]
- Li, H.; Li, F.; Shi, X.; Guo, Y.; Guo, S. Research on access control for secure cross-domain data circulation. J. Commun. 2025, 46, 238–254. [Google Scholar] [CrossRef]
- Kim, K.; Kim, T.; Lung, I. Blockchain-based information sharing between smart vehicles for safe driving. In Proceedings of the 2020 IEEE 91st Vehicular Technology Conference, Antwerp, Belgium, 25–28 May 2020. [Google Scholar] [CrossRef]
- Wang, L.; Liu, W.; Han, X. Blockchain-based government information resource sharing. In Proceedings of the 2017 IEEE 23rd International Conference on Parallel and Distributed Systems, Shenzhen, China, 15–17 December 2017. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 6 January 2025).
- Li, M.; Zeng, L.; Zhao, L.; Yang, R.; An, D.; Fan, H. Blockchain-watermarking for compressive sensed images. IEEE Access 2021, 9, 56457–56467. [Google Scholar] [CrossRef]
- Razzaq, A.; Mohsan, S.A.H.; Ghayyur, S.A.K.; Alsharif, M.H.; Alkahtani, H.K.; Karim, F.K.; Mostafa, S.M. Blockchain-enabled decentralized secure big data of remote sensing. Electronics 2022, 11, 3164. [Google Scholar] [CrossRef]
- Li, Z.; Ding, Y.; Yi, C.; Liang, H. A Blockchain Data Acceleration Exchange Method for Data Element Circulation. J. Comput. Res. Dev. 2024, 61, 2554–2569. [Google Scholar] [CrossRef]
- Li, J.; Grintsvayg, A.; Kauffman, J.; Fleming, C. LBRY: A blockchain-based decentralized digital content marketplace. In Proceedings of the 2020 IEEE International Conference on Decentralized Applications and Infrastructures, Oxford, UK, 3–6 August 2020. [Google Scholar] [CrossRef]
- Yu, F.; Peng, J.; Li, X.; Li, C.; Qiu, B. A copyright-preserving and fair image trading scheme based on blockchain. Tsinghua Sci. Technol. 2023, 28, 849–861. [Google Scholar] [CrossRef]
- Heo, G.; Yang, D.; Doh, I.; Chae, K. Efficient and secure blockchain system for digital content trading. IEEE Access 2021, 9, 77438–77450. [Google Scholar] [CrossRef]
- Xiao, Y.; Feng, Y.; Li, Y.; Fu, X. A privacy-preserved scheme for blockchain transaction based on homomorphic encryption. J. Cryptologic Res. 2022, 9, 1053–1066. [Google Scholar] [CrossRef]
- Khan, U.; An, Z.Y.; Imran, A. A blockchain Ethereum technology-enabled digital content: Development of trading and sharing economy data. IEEE Access 2020, 8, 217045–217056. [Google Scholar] [CrossRef]
- Zhang, Y.; Shi, Q. An intelligent transaction model for energy blockchain based on diversity of subjects. Alex. Eng. J. 2021, 60, 749–756. [Google Scholar] [CrossRef]
- Zhou, W.; Wei, M.; Xu, H.; Wu, Z. A small-sample remote sensing image feature classification model based on multimodal data. J. Electron. Inf. Technol. 2025, 47, 1747–1761. [Google Scholar] [CrossRef]
- Zou, Q.; Yu, W.; Bao, Z. A blockchain solution for remote sensing data management model. Appl. Sci. 2023, 13, 9609. [Google Scholar] [CrossRef]
- Zhu, C.; Ren, N.; Xu, D. Geo-information security technology: Progress and prospects. Acta Geod. Cartogr. Sin. 2022, 51, 1017–1028. [Google Scholar]
- Ren, N.; Guo, S.; Zhu, C.; Hu, Y. A zero-watermarking scheme based on spatial topological relations for vector dataset. Expert Syst. Appl. 2023, 226, 120217. [Google Scholar] [CrossRef]
- Wang, J.; Huang, W.; Zhang, J.; Luo, X.; Ma, B. Adversarial watermark: A robust and reliable watermark against removal. J. Inf. Secur. Appl. 2024, 22, 103750. [Google Scholar] [CrossRef]
- Zhang, J.; Du, J.; Xi, X.; Yang, Z. Chebyshev Chaotic Mapping and DWT-SVD-Based Dual Watermarking Scheme for Copyright and Integrity Authentication of Remote Sensing Images. Symmetry 2024, 16, 969. [Google Scholar] [CrossRef]
- Shao, S.; Wang, Y.; Yang, C.; Liu, Y.; Chen, X.; Qi, F. WFB: Watermarking-based copyright protection framework for federated learning model via blockchain. Sci. Rep. 2024, 14, 19453. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Xu, R.; Chen, Y. A decentralized digital watermarking framework for secure and auditable video data in smart vehicular networks. Future Internet 2024, 16, 390. [Google Scholar] [CrossRef]
- Yao, Q.; Xu, K.; Li, T.; Zhou, Y.; Wang, M. A secure image evidence management framework using multi-bits watermark and blockchain in IoT environments. Wirel. Netw. 2024, 30, 5157–5169. [Google Scholar] [CrossRef]
- Yuan, X.; Nie, H. Beyond protection: Unveiling neural network copyright trading. Knowl.-Based Syst. 2025, 320, 113617. [Google Scholar] [CrossRef]
- Natgunanathan, I.; Praitheeshan, P.; Gao, L.; Xiang, Y.; Pan, L. Blockchain-based audio watermarking technique for multimedia copyright protection in distribution networks. ACM Trans. Multimed. Comput. Commun. Appl. 2022, 18, 1–23. [Google Scholar] [CrossRef]
- Liu, T.; Lai, S.; Yuan, X.; Liu, Y.; Lam, C. A novel blockchain-watermarking mechanism utilizing interplanetary file system and fast walsh hadamard transform. iScience 2024, 27, 110821. [Google Scholar] [CrossRef]
- Hou, Z.; Yan, H.; Zhang, L.; Ren, N.; Ma, R.; Qu, R. Zero-watermark method based on multichannel pcnn and blockchain for remote sensing image transaction certificate and copyright protection. IEEE Trans. Geosci. Remote Sens. 2025, 63, 1–15. [Google Scholar] [CrossRef]
- Wang, B.; Shi, J.; Wang, W.; Peng, Z. Image copyright protection based on blockchain and zero-watermark. IEEE Trans. Netw. Sci. Eng. 2022, 9, 2188–2199. [Google Scholar] [CrossRef]
- Bhowmik, D.; Feng, T. The multimedia blockchain: A distributed and tamper-proof media transaction framework. In Proceedings of the 2017 22nd International Conference on Digital Signal Processing, London, UK, 23–25 August 2017. [Google Scholar] [CrossRef]
- Chen, L.; Bai, W.; Yao, Z. A secure and privacy-preserving watermark based medical image sharing method. Chin. J. Electron. 2020, 29, 819–825. [Google Scholar] [CrossRef]
- Zhu, C. Research progresses in digital watermarking and encryption control for geographical data. Acta Geod. Cartogr. Sin. 2017, 46, 1609–1619. [Google Scholar] [CrossRef]
- Guo, S.; Zhu, S.; Zhu, C.; Ren, N.; Tang, W.; Xu, D. A robust and lossless commutative encryption and watermarking algorithm for vector geographic data. J. Inf. Secur. Appl. 2023, 75, 103503. [Google Scholar] [CrossRef]
- Yan, Q.; Yan, H.; Zhang, L. Synergistic commutative algorithm for securing vector spatial data via GD-PBIBD fingerprint encoding and data encryption. Trans. GIS 2024, 28, 2652–2667. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, L.; Wang, H.; Wang, X. Commutative encryption and water-marking algorithm for high-resolution remote sensing images based homomorphic encryption. Laser Optoelectron. Prog. 2022, 59, 329–338. [Google Scholar] [CrossRef]
- Li, L.; Wang, S.; Zhang, S.; Luo, T.; Chang, C.-C. Homomorphic Encryption-Based Robust Reversible Watermarking for 3D Model. Symmetry 2020, 12, 347. [Google Scholar] [CrossRef]
- Zhao, M. Research on commutative watermarking and encryption algorithm for remote sensing image data. Nanjing Norm. Univ. 2020, 1–100. [Google Scholar] [CrossRef]
- Onwubiko, A.; Singh, R.; Awan, S.; Pervez, Z.; Ramzan, N. Enabling Trust and Security in Digital Twin Management: A Blockchain-Based Approach with Ethereum and IPFS. Sensors 2023, 23, 6641. [Google Scholar] [CrossRef] [PubMed]
- Wang, S.; Ouyang, L.; Yuan, Y.; Ni, X.; Han, X.; Wang, F. Blockchain-enabled smart contracts: Architecture, applications, and future trends. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 2266–2277. [Google Scholar] [CrossRef]
- Nan, R.; Zhang, L.; Xie, J.; Jin, Y.; Tan, T.; Liu, S.; Wang, H. Copyright Protection and Trusted Transactions for 3D Models Based on Smart Contracts and Zero-Watermarking. ISPRS Int. J. Geo-Inf. 2025, 14, 317. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R.; Marchang, N.; Srivastava, G.; Gadekallu, T.R.; Xiong, N.N. A secured distributed detection system based on IPFS and blockchain for industrial image and video data security. J. Parallel Distrib. Comput. 2021, 152, 128–143. [Google Scholar] [CrossRef]


| Symbol | Meaning | Symbol | Meaning |
|---|---|---|---|
| d | Original data | D | Data copyright holder |
| dD | Encrypted data | U | Data buyer |
| PubX | X’s public key | TA | Credible node |
| PriX | X’s private key | IPFS | Interplanetary file system |
| HX | X’s hash | W | Watermark |
| Data | Content |
|---|---|
| Original watermark (plaintext) | Copyright holder: Alice Buyer: Bob Data: RSOD remote sensing images Data HASH: 1001110111010010001110111001000010110010001… Time: 25 September 2025 19:36:05 |
| Original watermark (binary) | … 010000110110111101110000011110010111001001101001 011001110110100001110100001000000110100001101111… |
| Original data | Data after encryption |
 |  |
| Data after embedding the watermark (ciphertext) | Data after embedding the watermark (plaintext) |
 |  |
| Process | Result |
|---|---|
| 1. Upload the watermark to the IPFS for registration | QmREzWJKHLhFSnLCTxdaj3oAEU7taSndNxPGBSREksR4Lf |
| 2. Upload transaction information to Ant Open Consortium Chain | “logIndex”: “0x1”, “blockNumber”: “0x18”, “blockHash”: “0x2a6a1845e39d32150583447b217f 1cc71879bbf48e6cb7ccd00f139a7ce397a6”, “transactionHash”: “0xfbb52d570e8674d79e205563 2f913c415ae8570089bb06ac07f00cdd8939a0af”, “transactionIndex”: “0x0”, “address”: “0x93f8dddd876c7dBE3323723500e83E 202A7C96CC” |
| Data | Content | Hamming Distance |
|---|---|---|
| Extracted watermark information (binary) | …010000110110111101110000011110010111001001101001011001110110100001110100001000000110100001101111… | 0 |
| Recovered watermark information (plaintext) | Copyright holder: Alice Buyer: Bob Data: RSOD remote sensing images Data HASH: 1001110111010010001110111001000010110010001… Time: 25 September 2025 19:36:05 | 0 |
| Process | Result |
|---|---|
| 1. Verify the transaction on Ant Open Consortium Chain | bool: exists true, address: sender 0x5B38Da6a701c568545dCfcB03F cB875f56beddC4, address: receiver 0x5B38Da6a701c568545dCfcB03Fc B875f56beddC4, string: dataHash 100111011101001000111011100100 0010110010001…, String:_ipfsCid QmREzWJKHLhFSnLCTxdaj3oAE U7taSndNxPGBSREksR4Lf, uint256: timestamp 1759146466 |
| 2. Download the depository watermark from the IPFS | Copyright holder: Alice Buyer: Bob Data: RSOD remote sensing images Data HASH: 1001110111010010001110111001000010110010001… Time: 25 September 2025 19:36:05 |
| Attack Method | Attacked Image | NC | Result |
|---|---|---|---|
| Gaussian Noise (Variance = 0.05) |  | 0.876 | Success |
| Salt and Pepper Noise (Variance = 0.003) |  | 0.993 | Success |
| Crop 1 2048 × 1024 |  | 1 | Success |
| Crop 2 1024 × 1024 |  | 1 | Success |
| Rotate 1 10° |  | 0.831 | Success |
| Rotate 2 20° |  | 0.704 | Partial success |
| Contract | Gas Cost (Gas) | Ether Cost | USD Cost |
|---|---|---|---|
| User Authentication | 830,209 | 0.000830209 | 3.330 |
| Transaction Deposit | 508,109 | 0.000508109 | 2.038 |
| Transaction Verification | 953,418 | 0.000953418 | 3.825 |
| Contract | Function | Gas Cost (Gas) | Ether Cost | USD Cost |
|---|---|---|---|---|
| User Authentication | register | 72,913 | 0.000072913 | 0.292 |
| login | 73,215 | 0.000073215 | 0.294 | |
| set public key | 72,126 | 0.000072126 | 0.289 | |
| Transaction Deposit | store transaction | 143,294 | 0.000143294 | 0.575 |
| obtain transaction count | 7310 | 0.000007310 | 0.029 | |
| Transaction Verification | verify by watermark | 132,664 | 0.000132664 | 0.532 |
| verify by hash | 32,620 | 0.000032620 | 0.131 | |
| obtain transaction count | 7741 | 0.000007741 | 0.031 |
| Contract | Count | TPS | Avg Latency (s) |
|---|---|---|---|
| User Authentication | 10 | 17.976 | 0.056 |
| 20 | 19.129 | 0.052 | |
| 50 | 19.474 | 0.051 | |
| 100 | 19.199 | 0.052 | |
| 200 | 19.496 | 0.051 | |
| Transaction Deposit | 10 | 26.497 | 0.038 |
| 20 | 27.580 | 0.036 | |
| 50 | 27.287 | 0.037 | |
| 100 | 27.544 | 0.036 | |
| 200 | 28.437 | 0.035 | |
| Transaction Verification | 10 | 4.925 | 0.203 |
| 20 | 5.250 | 0.190 | |
| 50 | 5.294 | 0.189 | |
| 100 | 5.260 | 0.190 | |
| 200 | 5.266 | 0.190 |
| Indicator | Blockchain | Database |
|---|---|---|
| Traceability Accuracy Rate | 100.0% | 100.0% |
| Average Time to Source | 0.195 s | 0.023 s |
| Tamper Detection Capability | 100.0% | 0.0% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, M.; Zhang, L.; Ren, N.; Zhu, C. A Trusted Transaction Method for Remote Sensing Image Data Based on a Homomorphic Encryption Watermark and Blockchain. Symmetry 2025, 17, 1790. https://doi.org/10.3390/sym17111790
Wang M, Zhang L, Ren N, Zhu C. A Trusted Transaction Method for Remote Sensing Image Data Based on a Homomorphic Encryption Watermark and Blockchain. Symmetry. 2025; 17(11):1790. https://doi.org/10.3390/sym17111790
Chicago/Turabian StyleWang, Minxuan, Lei Zhang, Na Ren, and Changqing Zhu. 2025. "A Trusted Transaction Method for Remote Sensing Image Data Based on a Homomorphic Encryption Watermark and Blockchain" Symmetry 17, no. 11: 1790. https://doi.org/10.3390/sym17111790
APA StyleWang, M., Zhang, L., Ren, N., & Zhu, C. (2025). A Trusted Transaction Method for Remote Sensing Image Data Based on a Homomorphic Encryption Watermark and Blockchain. Symmetry, 17(11), 1790. https://doi.org/10.3390/sym17111790





