Models and Methods for Assessing Intruder’s Awareness of Attacked Objects
Abstract
1. Introduction
2. Research Methods
Review of Research on This Topic
- (1)
- The development of a structural and functional model of the system under test and its protection model;
- (2)
- The selection of testing tools:
- (a)
- application software, utilities;
- (b)
- hardware;
- (c)
- special radio-electronic equipment;
- (3)
- Collecting information about the test object:
- (a)
- open-source intelligence (OSINT);
- (b)
- the use of social engineering methods;
- (c)
- analysis of social networks and contacts;
- (d)
- analysis of e-mail and telephone contacts;
- (e)
- network scanning;
- (f)
- analysis of the software used;
- (g)
- analysis of the hardware architecture of network nodes, switching equipment, peripheral equipment and information input/output devices;
- (h)
- security perimeter analysis;
- (4)
- Vulnerability analysis of DI facilities at various levels;
- (5)
- The identification of entry points and DI target objects;
- (6)
- The identification of available CAs, tactics and techniques of implementation, patterns and vectors;
- (7)
- The formation of the CCA template and vector;
- (8)
- Practical implementation of penetration testing, adjustment ID, and the content of the next SCA after achieving the goals of the previous one;
- (9)
- Preparation of a report and recommendations for adjusting the protection system of the elements of the DIS.
3. Results and Discussion
3.1. The Development of Symmetric Models and Methods for Assessing the Awareness of the Intruder and Assessing the Intelligence Security of BIS Elements
3.2. Development of Experimental Models
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- CAPEC (Common Attack Pattern Enumeration and Classification)–A Standard for Describing Attack Classes and Their Hierarchical Relationships, a Catalog of Known Cyberattacks. Available online: https://capec.mitre.org (accessed on 18 April 2025).
- MITRE ATT&CK Matrix–Formal Description of Techniques and Tactics for Implementing Cyber-Attacks. Available online: https://attack.mitre.org/ (accessed on 25 July 2025).
- Almedires, M.A.; Elkhalil, A.; Amin, M. Adversarial attack detection in industrial control systems using LSTM-based intrusion detection and black-box defense strategies. J. Cyber Secur. Risk Audit. 2025, 2025, 4–22. [Google Scholar] [CrossRef]
- Wei, Y.; Wu, F. Self-adaptive intrusion detection model based on Bi-LSTM-CRF using historical access logs. In Proceedings on Advances in Natural Computing, Fuzzy Systems, and Knowledge Discovery: Proceedings of the ICNC-FSKD 2021 Conference 17; Springer International Publishing: Cham, Switzerland, 2022; pp. 185–197. [Google Scholar]
- Radanliev, P. Cyber diplomacy: Defining the opportunities for cybersecurity and risks from Artificial Intelligence, IoT, Blockchains, and Quantum Computing. J. Cyber Secur. Technol. 2024, 9, 28–78. [Google Scholar] [CrossRef]
- Radanliev, P. Artificial intelligence and quantum cryptography. J. Anal. Sci. Technol. 2024, 15, 4. [Google Scholar] [CrossRef]
- Alshuaibi, A.; Arshad, M.W.; Maayah, M. A hybrid genetic algorithm and hidden markov model-based hashing technique for robust data security. J. Cyber Secur. Risk Audit. 2025, 42–56. [Google Scholar] [CrossRef]
- Al-Shaer, R.; Ahmed, M.; Al-Shaer, E. Statistical Learning of APT TTP Chains from MITRE ATT&CK. In Proceedings of the RSA Conference 2017, San Francisco, CA, USA, 13–17 February 2017; pp. 1–2. Available online: https://www.researchgate.net/publication/351452885_Assessing_MITRE_ATTCK_Risk_Using_a_Cyber-Security_Culture_Framework (accessed on 25 July 2025).
- Skabtsov, N. Information Systems Security Audit; Peter: Saint Petersburg, Russia, 2018; p. 272. ISBN 978-5-4461-0662-2. Available online: https://books.yandex.ru/books/T54pW6oL/read-online (accessed on 20 July 2025).
- Kotenko, D.I.; Kotenko, I.V.; Saenko, I.B. Methods and tools for modeling attacks in large computer networks: The state of the problem. SPIIRAN 2012, 22, 5–30. [Google Scholar] [CrossRef]
- Baranov, V.V.; Shelupanov, A.A. Models and methods for assessing the destructive impact of violators on elements of distributed information systems. Rep. Tomsk. State Univ. Control. Syst. Radio Electronics 2024, 25, 88–100. Available online: https://journal.tusur.ru/storage/178924/5-Baranov-Shelupanov_п.pdf?1741931041 (accessed on 20 July 2025).
- Baranov, V.V.; Shelupanov, A.A. Cognitive model for assessing the security of information systems for various purposes. Symmetry 2022, 14, 2631. [Google Scholar] [CrossRef]
- Avezova, Y.; Badaev, A. In the Sights of APT Groups: Kill Chain of Eight Steps. Habr. 2023. Available online: https://habr.com/ru/companies/pt/articles/802697/ (accessed on 2 June 2025).
- Ang, S.; Huy, S.; Janarthanan, M. Utilizing IDS and IPS to improve cybersecurity monitoring process. J. Cyber Secur. Risk Audit. 2025, 77–88. [Google Scholar] [CrossRef]
- ISSAF-Information System Security Assesment Framework. 2006. 1264p. Available online: http://www.oissg.org/issaf02/issaf0.1-5.pdf (accessed on 8 June 2025).
- Orrey, K. Penetration Test Framework. Vulnerability Assessment. 2014. Available online: https://www.secureinfo.eu/data/files/docs/Framework_-_Penetration_Test.html (accessed on 8 June 2025).
- PTES–The Penetration Testing Execution Standard. 30 April 2012. Available online: http://www.pentest-standard.org/index.php/Main_Page (accessed on 9 June 2025).
- Special Publications 800-115, Technical Guide to Information Security Testing and Assessment; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2008. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-115.pdf (accessed on 12 June 2025).
- Aljumaiah, O.; Jiang, W.; Reddy Addula, S.; Amin Almaiah, M. Analyzing cybersecurity risks and threats in IT infrastructure based on NIST framework. J. Cyber Secur. Risk Audit. 2025, 2025, 12–26. [Google Scholar] [CrossRef]
- Beizer, B. Black box testing. In Technologies of Functional Testing of Software and Systems; Peter: Saint Petersburg, Russia, 2004; p. 320. ISBN 5-94723-698-2. Available online: https://djvu.online/file/UlGilEprxDkPy (accessed on 8 June 2025).
- Binder, R. Testing Object-Oriented Systems; Publisher Addison-Wesley Publishing Company Inc: Reading, MA, USA, 2000; ISBN 9780201809381. Available online: http://kagowyje.blog.free.fr/index.php?post/2016/10/22/Testing-Object-Oriented-Systems%3A-Models%2C-Patterns%2C-and-Tools-pdf (accessed on 18 June 2025).
- Ammann, P.; Offutt, J. An Introduction to Software Testing; University Press: Cambridge, UK, 2008; ISBN 978-0-521-88038-1. Available online: https://assets.cambridge.org/97805218/80381/frontmatter/9780521880381_frontmatter.pdf (accessed on 12 June 2025).
- Zadeh, L. (Ed.) The Concept of a Linguistic Variable and Its Application to Making Approximate Decisions; Translated from English; Mir: Moscow, Russia, 1976; p. 167. ISBN 978-5-85582-423-0. [Google Scholar]
- Sapkina, N.V. Properties of Operations on Fuzzy Numbers. Bulletin of the VSU. Series: System Analysis and Information Technology. 2013, Volume 1, pp. 23–28. Available online: https://www.elibrary.ru/download/elibrary_20156009_60491464.pdf (accessed on 12 June 2025).
- Asfha, A. Information security risk assessment in industry information system based on fuzzy set theory and artificial neural network. Inform. Autom. 2024, 23, 542–571. [Google Scholar] [CrossRef]


| Active Scanning | IP Block Scanning | Vulnerability Scanning | Wordlist Scanning | |||
|---|---|---|---|---|---|---|
| Collecting information about attacked nodes | Simple computer attacks | Software | Firmware update process | Client configurations | ||
| Collecting information about users | Credentials | E-mail addresses | Employee names | |||
| Collecting information about attacked network infrastructure | Domain properties | DNS systems | Trusted Networks | Network Topology | IP Addresses | Network defense tools |
| Gathering information about an organization | Determining the physical location | Counterparties | Study of work schedule and delivery mode | Employee role identification | ||
| Phishing for information | Spear phishing via third-party services | Spear phishing with attachment | Spear phishing with link | Verbal spear phishing | ||
| Search in closed sources | Threat information providers | Acquiring technical data | ||||
| Search in public sources | DNS/Passive DNS | Digital certificates | WHOIS | CDNs | Database scanning | |
| Search for open sites/domains | Social networks | Search engines | Code repositories | |||
| The Stage of a CCA | The Violator’s Awareness of the Elements of a DIS | Information Security Threat Model Levels that Define DI Objects | ||||||
|---|---|---|---|---|---|---|---|---|
| Assessment Methods | Rating Scale | Calculation of Indicators | Network | Hardware | System | Application | User Defined | |
| T(yj) | «White box» | Xi, T(xi) | T(zk) | T(zk) | T(zk) | T(zk) | T(zk) | |
| T(yn) | «Gray box» | Xn, T(xn) | T(zn) | T(zn) | T(zn) | T(zn) | T(zn) | |
| …… | …… | …… | …… | …… | …… | …… | ||
| T(y3) | X3, T(x3) | T(z3) | T(z3) | T(z3) | T(z3) | T(z3) | ||
| T(y2) | X2, T(x2) | T(z2) | T(z2) | T(z2) | T(z2) | T(z2) | ||
| T(y1) | «Black box» | X1, T(x1) | T(z1) | T(z1) | T(z1) | T(z1) | T(z1) | |
| Computational cluster | Available data on awareness level | |||||||
| The Scale of Awareness Levels Xi | [0;0.2] | [0.2;0.4] | [0.4;0.6] | [0.6;0.8] | [0.8;1] |
|---|---|---|---|---|---|
| Linguistic terms for assessing awareness T(xi) | VL | L | M | H | VH |
| Linguistic terms describing the stages of CCA T(yj) | Reconnaissance | Reconnaissance, login, legalization | Reconnaissance, login, legalization, privilege enhancement | Reconnaissance, login, legalization, privilege enhancement, dissemination | Reconnaissance, login, legalization, privilege enhancement, DI |
| Linguistic terms for describing CCA targets T(zk) | Externally accessible network objects of the attacked DIS element | The attacked node of the DIS element network | DI objects of the attacked DIS element, available according to the access control model | DI objects of the attacked DIS element, accessible nodes of the network of interacting elements of the DIS | Objects of DI of the attacked element and interacting elements of the DIS |
| Linguistic terms of the scale for assessing the awareness of the violator TXi(xi;a,b) | VL | L | M | H | VH |
| Linguistic terms of the scale for assessing the IS of elements DIS THi(hi;a,b) | VH | H | M | L | VL |
| Numerical values of the scale ranges | [0;0.2] | [0.2;0.4] | [0.4;0.6] | [0.6;0.8] | [0.8;1] |
| Inter- Network Interaction | Local Area Networks (LANs) | Data Center (DC) | Remote User (RU) | |
|---|---|---|---|---|
| LAN Segment1 DC; RU Segment1 DC; Segment1-Segment2 DC | Firewall 1.1 Router 1.1 Switch 1.1 Server 1.1 AW1.1 AW1.2 AW1.3 ……………. AW1.n | Firewall 2.1 Router 2.1 Switch 2.1 | Firewall 3.1 AW3.1 | |
| Virtualization Server 2.1 Server 2.1 AW2.1 ………… AW2.n | Container Virtualization Server 2.1 Container 2.1 …………… Container 2.n Database Server 2.1 | |||
| No | Segment1 | Segment2 | No | |
| Access control | ||||
| The Stage of the CCA | The Violator’s Awareness of the Elements of the DIS | Levels of Identification of DV Objects | ||||
|---|---|---|---|---|---|---|
| ID gathering | Very low: | Network | Hardware | System | Application | User defined |
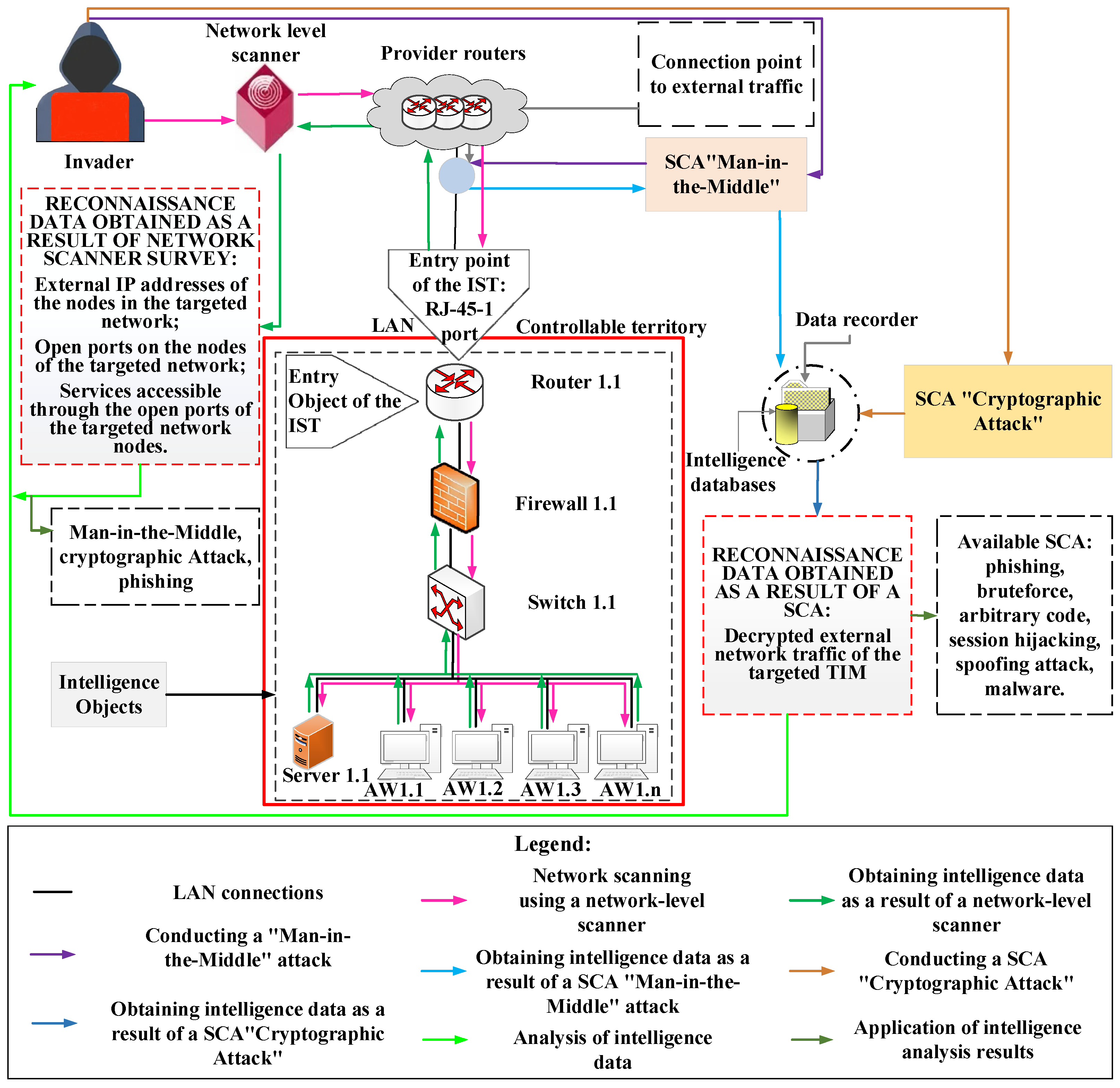
| External IP addresses; external open node ports; encrypted external traffic | No data available | No data available | No data available | No data available | ||
| Evaluation method: «black box» | ||||||
| Available data on awareness level | ||||||
| The Stage of the CCA | The Violator’s Awareness of the Elements of the DIS | Levels of Identification of DV Objects | ||||
|---|---|---|---|---|---|---|
| Penetration, legalization, ID gathering | «Low» | Network | Hardware | System | Application | User defined |
| Data on the attacked NN: | ||||||
| External IP addresses; external open node ports; encrypted external traffic | No data available | Protocol vulnerabilities on an external IP address | Vulnerabilities of protocols and services on the external IP address of the port | User credentials | ||
| Evaluation method: “grey box” | ||||||
| Available data on awareness level | ||||||
| The Stage of the CCA | The Violator’s Awareness of the Elements of the DIS | Levels of Identification of DV Objects | ||||
|---|---|---|---|---|---|---|
| Network | Hard Ware | System | Application | User Defined | ||
| Data on the Attacked NN in Accordance with the ACM: | ||||||
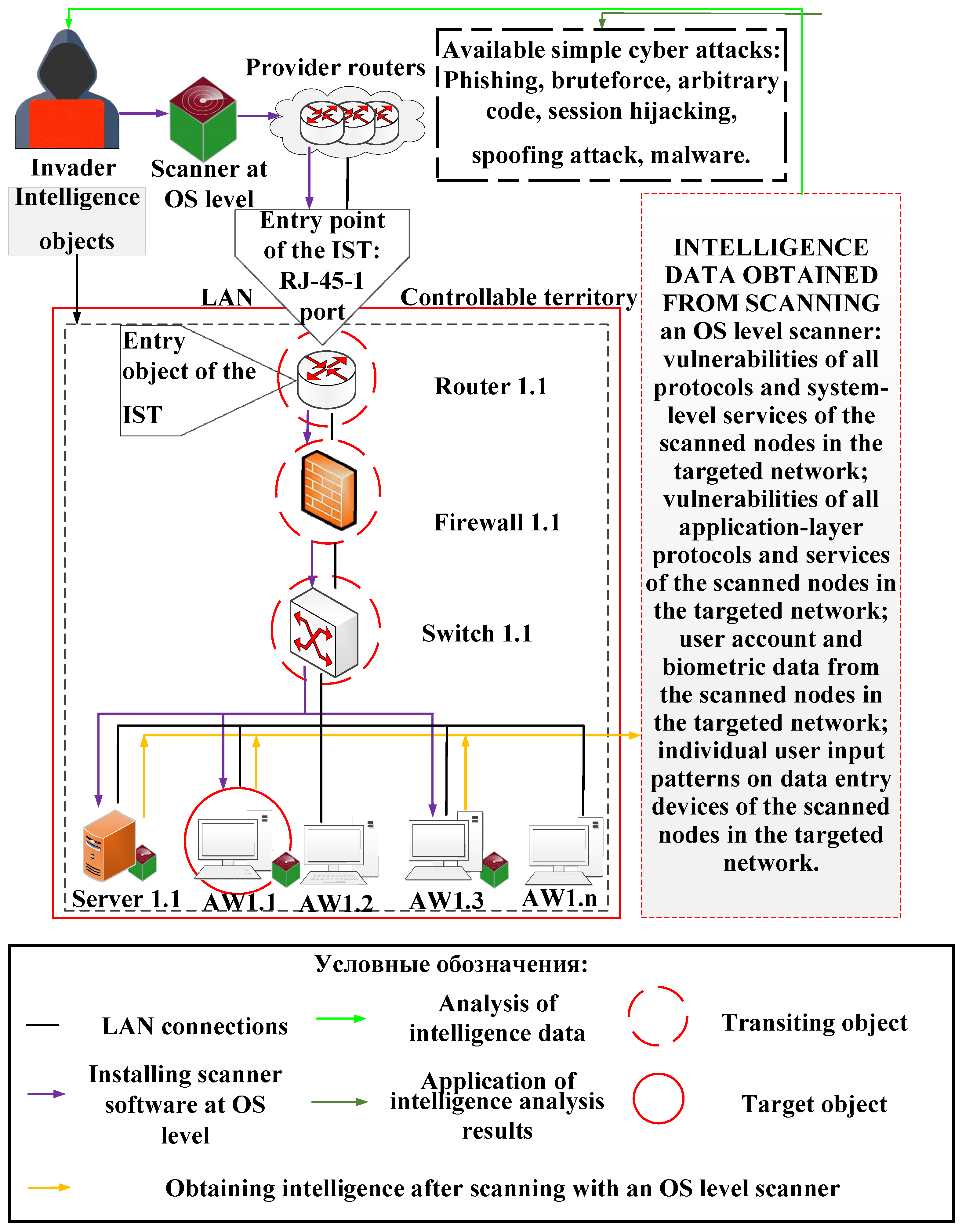
| Privilege escalation, penetration, legalization, ID gathering | Medium | View of a network node of a DIS element; IP addresses; open ports; encrypted external traffic. | Types and specification of hard ware architecture, embedded SW of NN and their vulnerabilities. | OS types and specification; vulnerabilities and types of all network protocols and control systems (CSs); ACM; file systems; drivers; process management subsystems. | Types and specification of ASW; all network protocols and application layer services; vulnerabilities in application-level protocols and services. | Types and specification of user-level devices and their vulnerabilities; credentials and biometric data of users of the NN; the individual handwriting of the users of the NN. |
| Evaluation method: “gray box” | ||||||
| Available data on awareness level | ||||||
| The Stage of the CCA | The Violator’s Awareness of the Elements of the DIS | Levels of Identification of DV Objects | ||||
|---|---|---|---|---|---|---|
| Proliferation, privilege escalation, penetration, legalization, ID gathering | High: | Network | Hardware | System | Applica- tion | User defined |
| Data on available NN: | ||||||
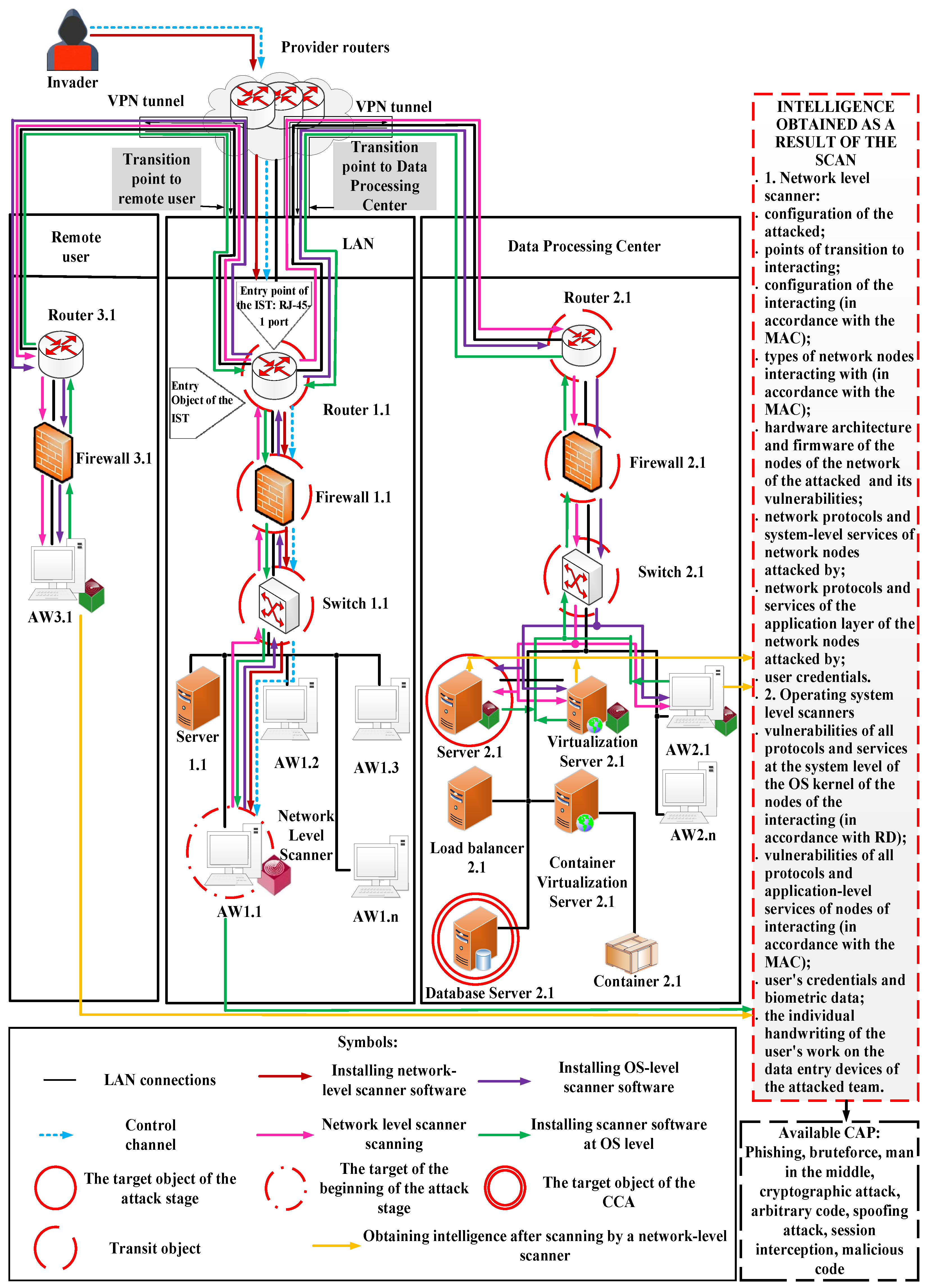
| Configuration of available NN; entry and transition points on accessible NN; types of available NN; all IP addresses; open ports; encrypted external traffic. | Types and specification of hardware architecture, embedded SW of NN and their vulnerabilities. | OS types and specification; vulnerabilities and types of all network protocols and control systems (CSs); ACM; file systems; drivers; process management subsystems. | Types and specification of ASW; all network protocols and application layer services; vulnerabilities in application-level protocols and services. | Types and specification of user-level devices and their vulnerabilities; credentials and biometric data of users of the NN; the individual handwriting of the users of the NN. | ||
| Evaluation method: “gray box” | Available data on awareness level | |||||
| The Stage of the CCA | The Violator’s Awareness of the Elements of the DIS | Levels of Identification of DV Objects | ||||
|---|---|---|---|---|---|---|
| Destructive impact, proliferation, privilege escalation, penetration, legalization, ID gathering | Very high: Evaluation method: “white box” | Network | Hardware | System | Application | User defined |
| Data on all network nodes: | ||||||
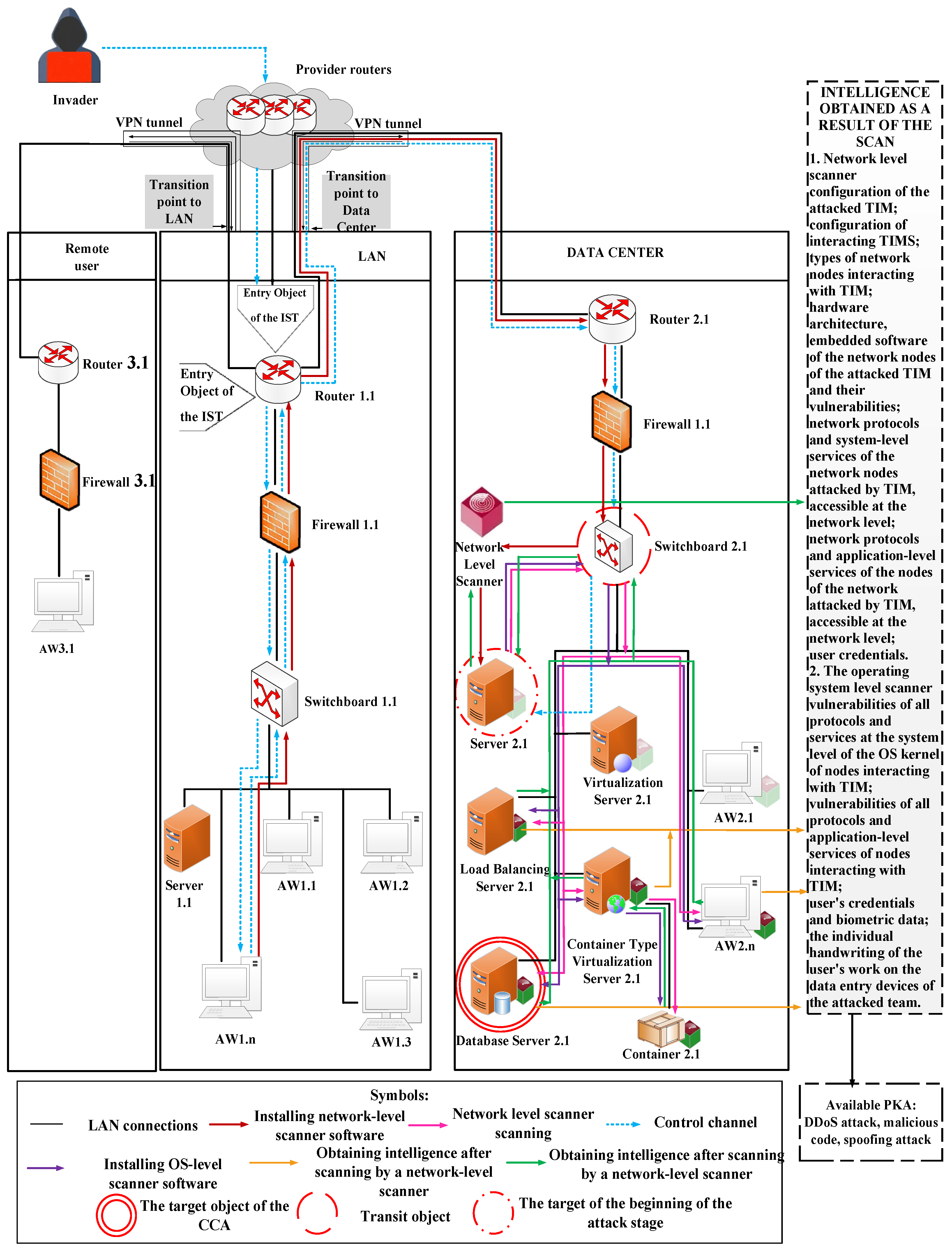
| Element configuration; entry and transition points to interacting elements; types of NN; all IP addresses and open ports of NN; decrypted network traffic. | Types and specification of the entire hardware architecture and embedded SW of NN and their vulnerabilities. | OS types and dpecification; vulnerabilities and types of all network protocols and services of NN; ACM; file systems; drivers; system-level process management subsystems. | Types and specification of ASW; vulnerabilities and types of all network protocols and application layer services. | Types and specification of user-level devices and their vulnerabilities; accounting and biometric data and individual handwriting of the users of the NN. | ||
| Available data on awareness level | ||||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Baranov, V.V.; Shelupanov, A.A. Models and Methods for Assessing Intruder’s Awareness of Attacked Objects. Symmetry 2025, 17, 1604. https://doi.org/10.3390/sym17101604
Baranov VV, Shelupanov AA. Models and Methods for Assessing Intruder’s Awareness of Attacked Objects. Symmetry. 2025; 17(10):1604. https://doi.org/10.3390/sym17101604
Chicago/Turabian StyleBaranov, Vladimir V., and Alexander A. Shelupanov. 2025. "Models and Methods for Assessing Intruder’s Awareness of Attacked Objects" Symmetry 17, no. 10: 1604. https://doi.org/10.3390/sym17101604
APA StyleBaranov, V. V., & Shelupanov, A. A. (2025). Models and Methods for Assessing Intruder’s Awareness of Attacked Objects. Symmetry, 17(10), 1604. https://doi.org/10.3390/sym17101604







