Privacy-Preserving Medical Data-Sharing System with Symmetric Encryption Based on Blockchain
Abstract
1. Introduction
- A medical data-sharing system is proposed based on blockchain for secure data sharing between hospitals. This system only stores simple data records on the blockchain, while the complete data are encrypted and stored in the application platform.
- A verification system is also proposed based on chameleon hash with revocable trapdoor, enabling patients to revoke the hospital’s right of managing data and allowing hospitals to revoke the application platform’s right of signing medical data.
- The proposed system can prevent the misuse of shared data based on chameleon signature. By designing this algorithm, we solve the problem of data misuse, which prevents data that have been shared from being leaked to other parties who do not have permission to access them.
2. Preliminaries
2.1. Blockchain
2.2. Chameleon Hash
- : On inputting a security parameter , the algorithm outputs a system parameter .
- : On inputting system parameter , the algorithm outputs a pair of private and public key .
- : On inputting a public key and a message m, the algorithm outputs chameleon randomness r and chameleon hash value h.
- : On inputting a private key , a chameleon hash value h, a chameleon randomness r, a message m and a new message , the algorithm outputs a new chameleon randomness .
- : On inputting a chameleon hash value h, a public key , a message m and a chameleon randomness r, the algorithm outputs 1 if is valid and otherwise outputs 0.
3. Chameleon Hash with Revocable Trapdoor
3.1. Chameleon Hash Based on Elliptic Curve Group
- : Let G be the generator point of the elliptic curve group E, and the smallest n that satisfies is a very large prime number, where O is the infinity point on the elliptic curve. The algorithm outputs the system parameter .
- : Choose an integer as the trapdoor and compute public key . Then , .
- : Randomly choose , where R is a random point on the elliptic curve group and . Compute and . Then the chameleon hash value .
- : Randomly choose . Compute and . Then .
- : Compute h = and . The algorithm outputs 1 if , and otherwise outputs 0.
3.2. Construction of CHRT
- : Run the algorithm and to obtain the public parameter and , and then return .
- : Run the algorithm to obtain the chameleon key pair , and then return .
- : Run the algorithm to obtain the chameleon key pair , and then return .
- : Run the algorithm to obtain hash/check string pair (, ). Then, run the algorithm to obtain hash/check string pair (, ). Finally, return .
- : Phrase r as and run the algorithm to obtain new check string . Then, return .
- : Phrase r as and run the algorithm to obtain a new hash value . Then, run the algorithm to obtain a new check string . Finally, return .
- : Choose a new chameleon public key using the algorithm . Then, run the algorithm to obtain and . Run the algorithm to obtain . Finally, return .
- : Phrase r as and run the algorithm to obtain hash value . Then run to obtain hash value . If , return 1; otherwise, return 0.
4. The Proposed System
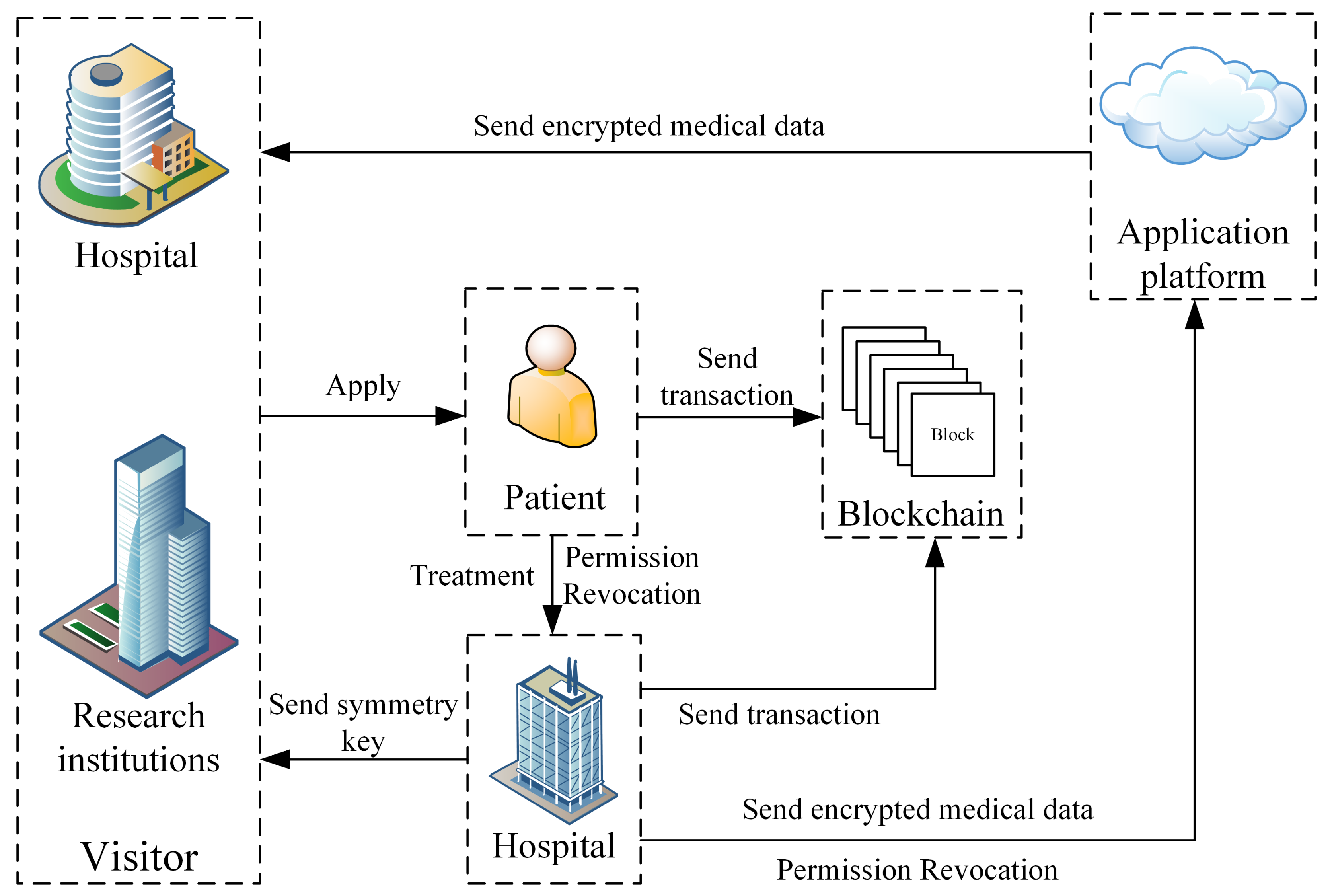
4.1. The System Model
- When a hospital receives a new patient, the hospital must register him to grant him control over his own medical data.
- During the visit of the patient, the hospital stores the generated medical data in the local database and submits the description and digest of the data to the blockchain.
- When the patient is discharged, the hospital sends the encrypted medical data, description and digest of the entire medical data to the application platform.
- The visitor applies for the patient to access his medical data. If the patient agrees to the visitor’s request, he needs to sends access parameters to the visitor.
- The visitor sends the access parameters to the hospital. If the access parameters is valid, the hospital sends the decryption key to the visitor.
- The platform signs the medical data and sends them along with the encrypted data to the visitor.
4.2. New Patient Registration
- Hospital uses its chameleon public key and patient’s chameleon public key to calculate
- The hospital selects a random number d and computes a new randomness using its chameleon private key :
- The hospital obtains the chameleon public key of the application platform. Then, it calculates using its private key and then sends to the application platform to give it proxy signing authority, where is the digital signature algorithm.
- The hospital sets and computeswhere represents the kind of transaction.
- The hospital submits the following transaction to the blockchain:
4.3. Data Storage
- sets and computes and , where is the signature key of and is the identifier of a series of medical data generated by this medical treatment.
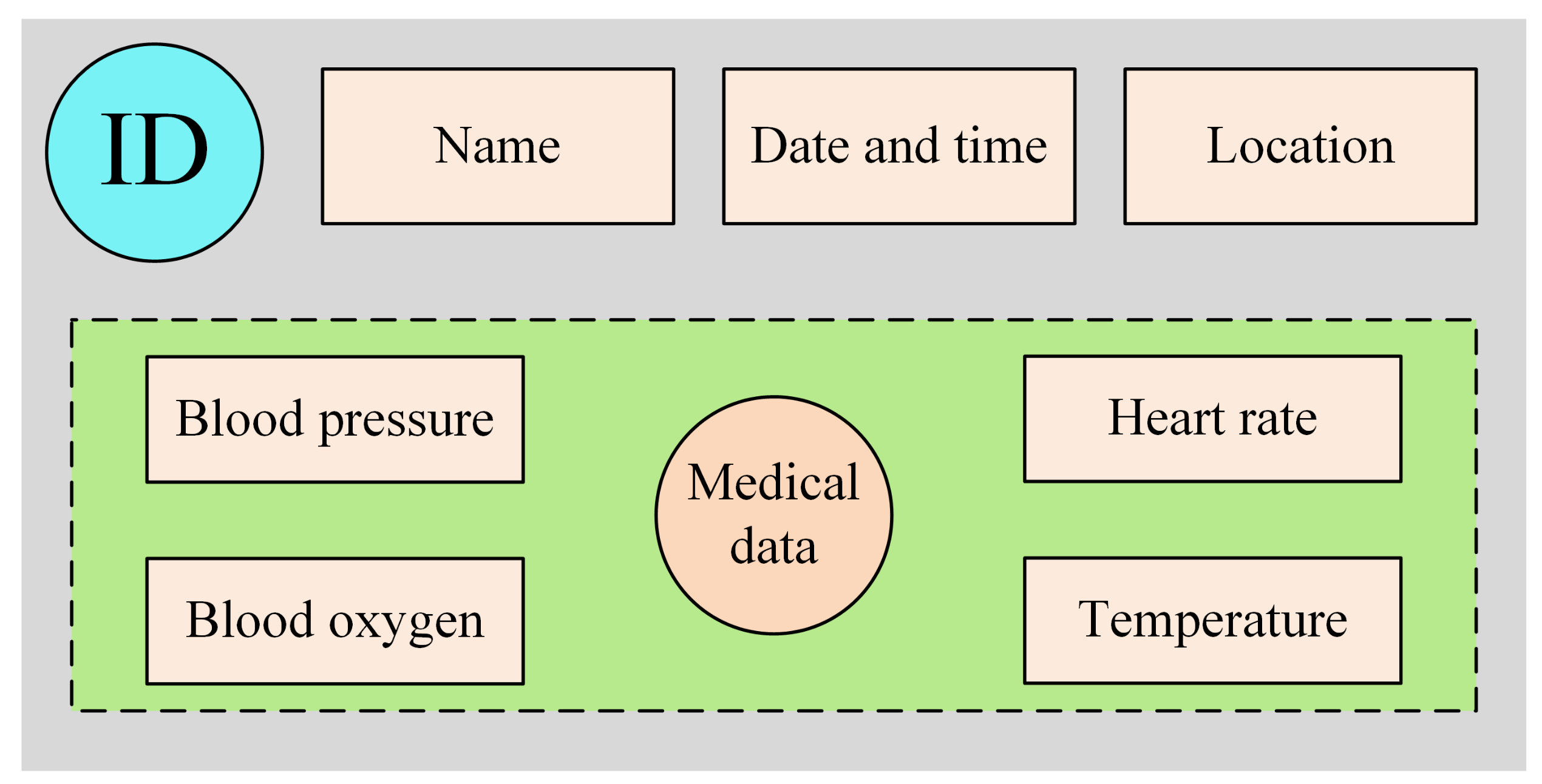
- computes , where A represents this kind of medical data, and contains brief information about the piece of medical data, such as the description and the time when the data were generated.
- submits to the blockchain, which will return the hash value of the transaction to .
- saves in the local database, where .
- obtains by in the hospital’s local database.
- sets and computes and .
- computes , where B represents this of medical data.
- submits the transaction to the blockchain and obtains the hash value of this transaction.
- saves in the local database, where .
- obtains by in the hospital’s local database.
- sets and computes , and , where .
- generates a symmetry key and saves and in the local database.
- computes , where C represents the kind of transaction.
- submits the transaction to the blockchain.
- computes and sends to the application platform. In our article, we choose the AES algorithm for encrypting and decrypting medical data.
4.4. Data Sharing
4.4.1. Permission Acquisition
4.4.2. Data Acquisition
4.5. Permission Revocation
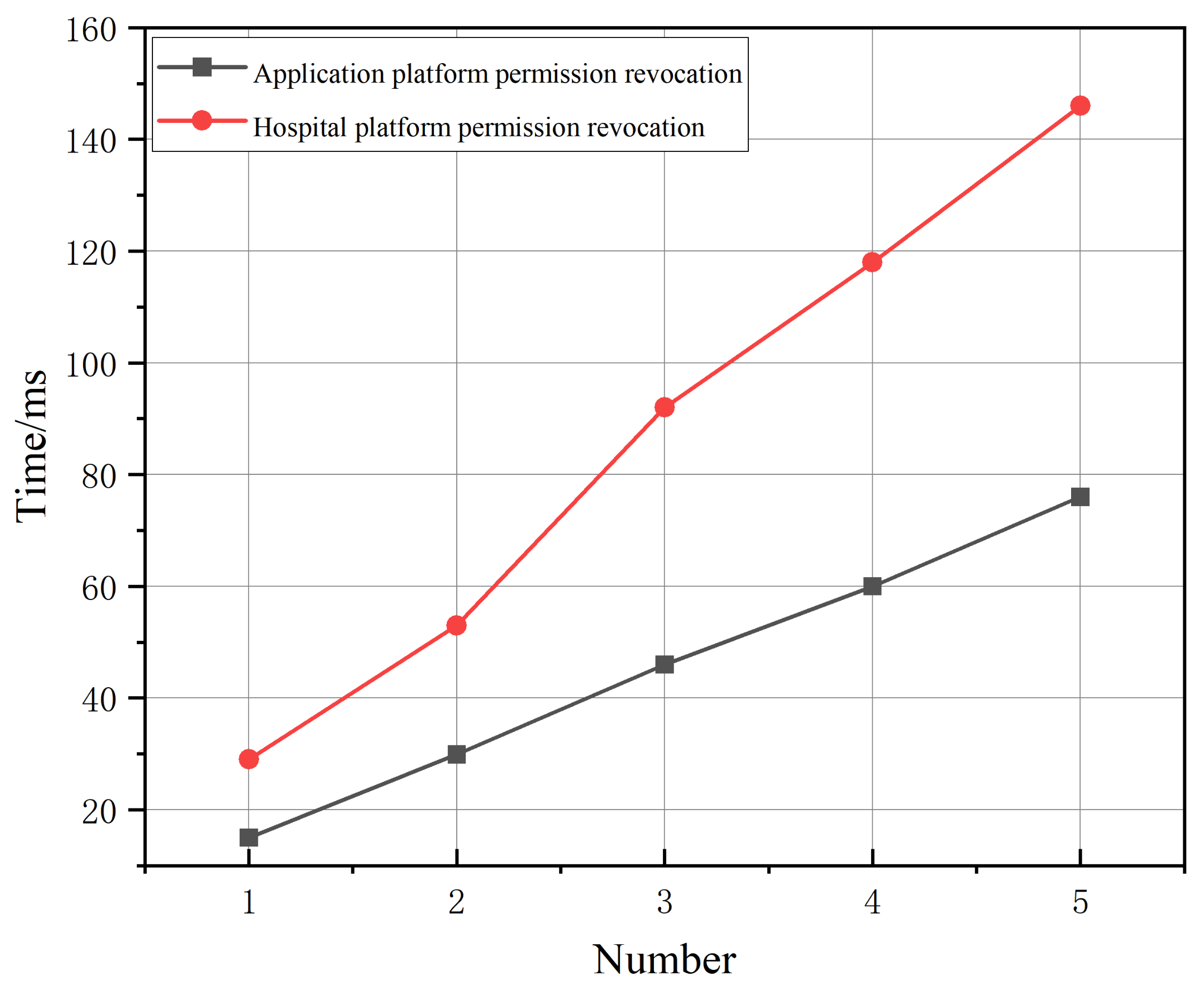
4.5.1. Application Permission Revocation
4.5.2. Hospital Permission Revocation
5. Analysis of the System
5.1. The Security of CHRT
5.2. Data Access Control
5.3. Data Security
6. Experiments
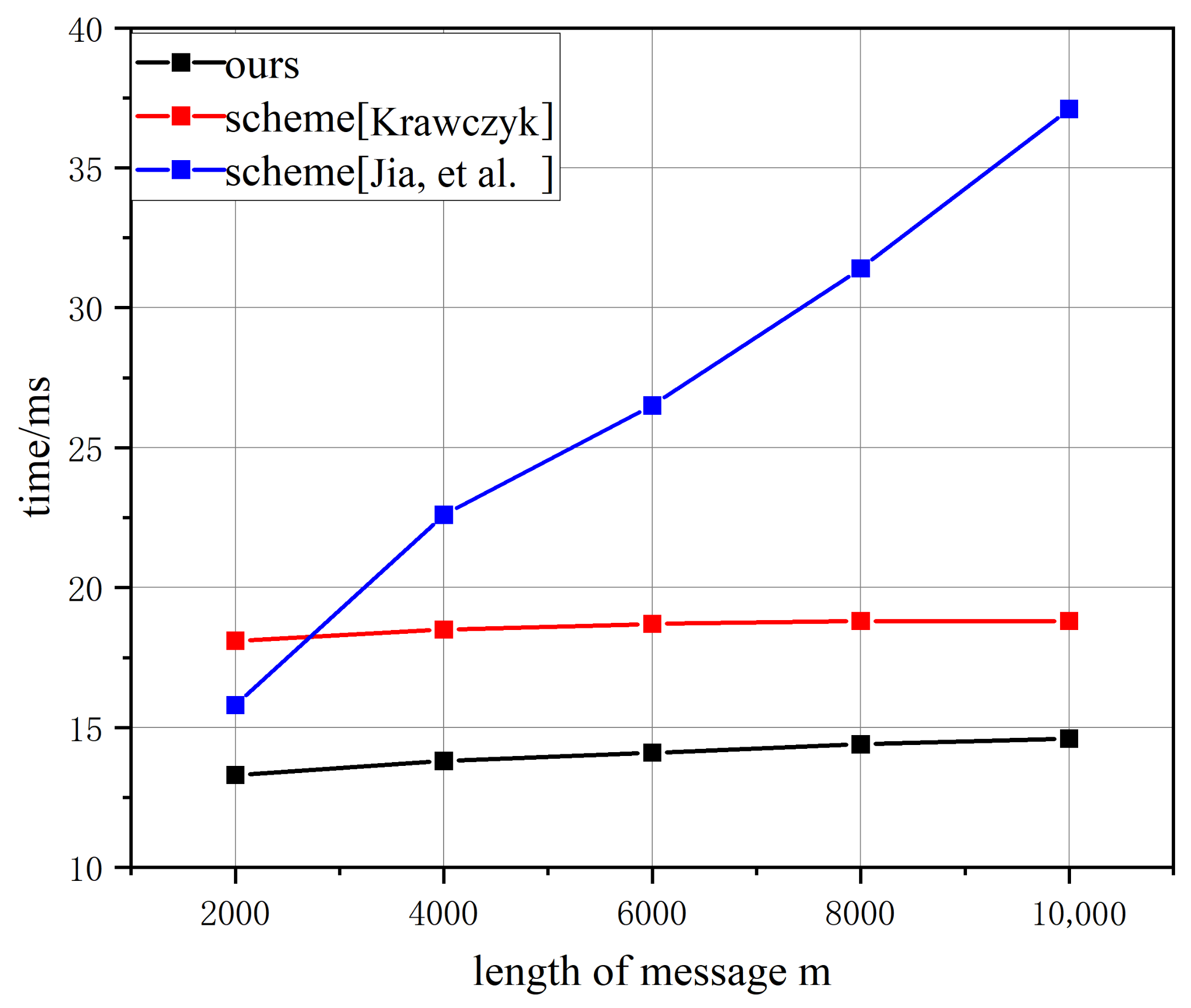
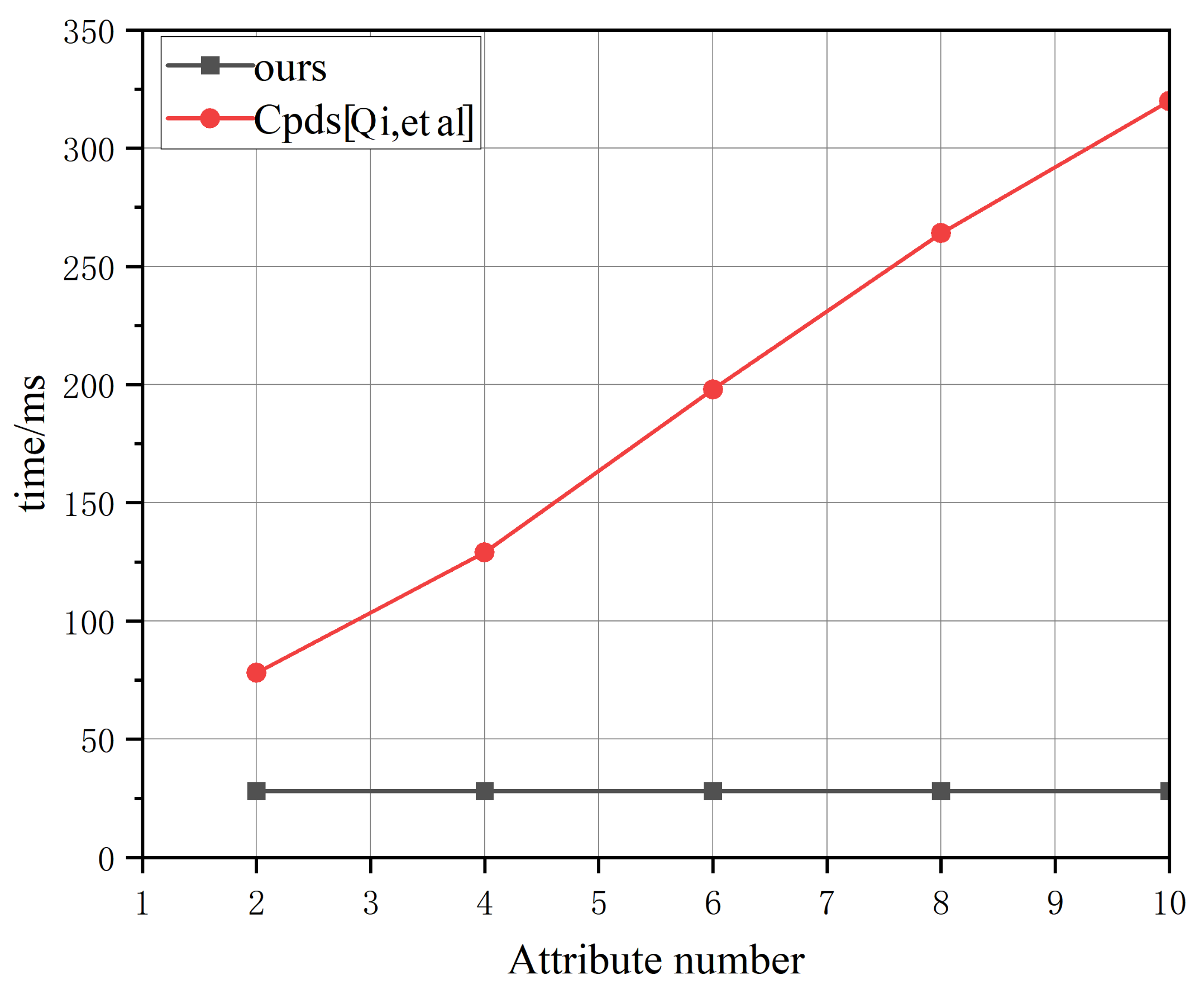
6.1. Computational Costs of Chameleon Hash
6.2. Computational Costs of Permission Operation
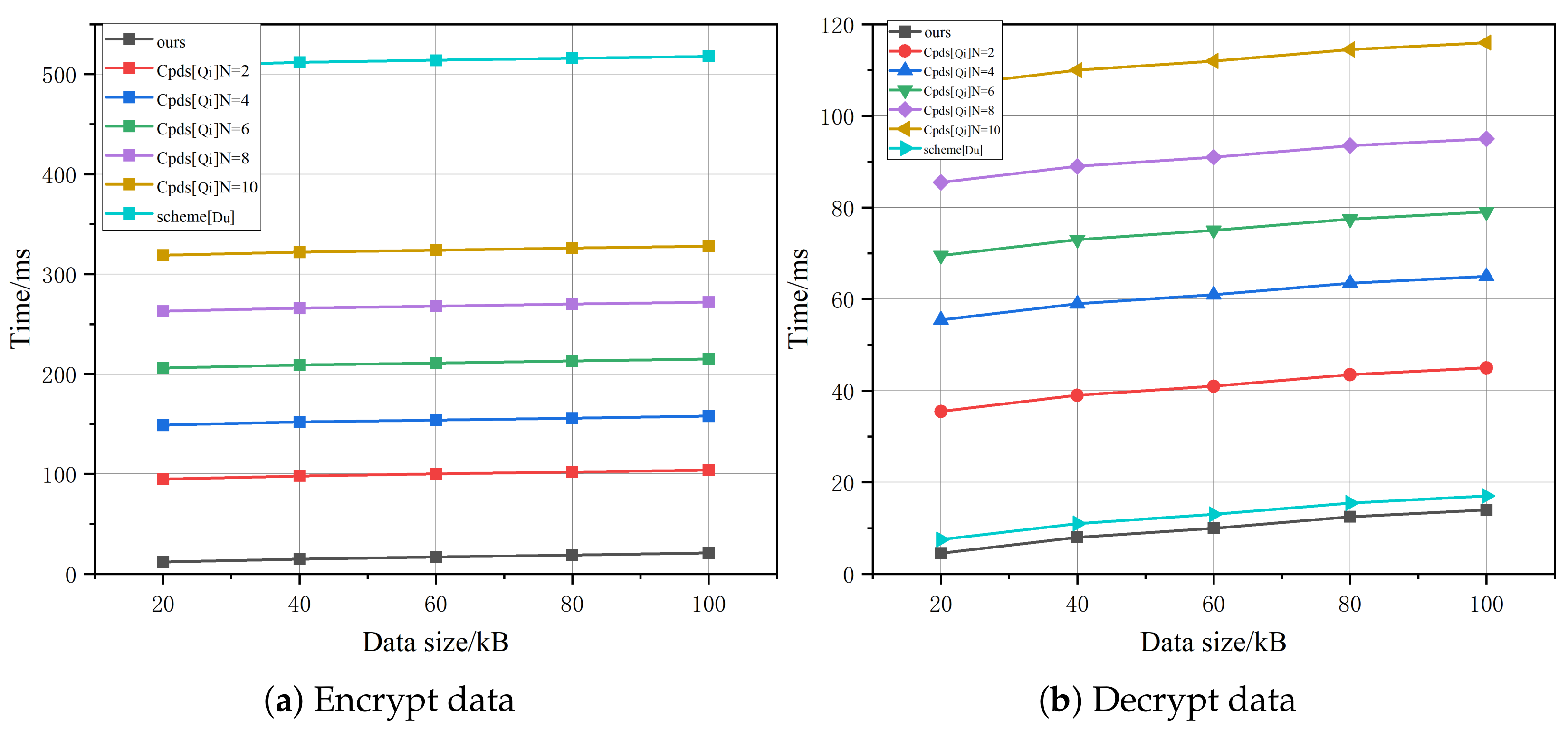
6.3. Computational Costs of Encryption and Decryption
6.4. Data Storage Overhead
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Engelhardt, M. Hitching Healthcare to the Chain: An Introduction to Blockchain Technology in the Healthcare Sector. Technol. Innov. Manag. Rev. 2017, 12, 22–34. [Google Scholar] [CrossRef]
- Pazaitis, A.; De Filippi, P.; Kostakis, V. Blockchain and Value Systems in the Sharing Economy: The Illustrative Case of Backfeed. Technol. Forecast. Soc. Chang. 2017, 12, 105–115. [Google Scholar] [CrossRef]
- Fiore, M.; Capodici, A.; Rucci, P.; Bianconi, A.; Longo, G.; Ricci, M.; Sanmarchi, F.; Golinelli, D. Blockchain for the Healthcare Supply Chain: A Systematic Literature Review. Appl. Sci. 2023, 13, 686. [Google Scholar] [CrossRef]
- Zhou, N.; Long, S.; Liu, H.; Liu, H. Structure—Attribute Social Network Graph Data Publishing Satisfying Differential Privacy. Symmetry 2022, 14, 2531. [Google Scholar] [CrossRef]
- Colomo-Palacios, R.; Sánchez-Gordón, M.; Arias-Aranda, D. A critical review on blockchain assessment initiatives: A technology evolution viewpoint. J. Softw. Evol. Process. 2020, 32, e2272. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: http://bitcoin.org/bitcoin.pdf (accessed on 14 April 2021).
- Yong, Y.; Wang, F. Blockchain: The State of the Art and Future Trends. Acta Autom. Sin. 2016, 42, 481–494. [Google Scholar]
- Yeh, K.-H.; Yang, G.-Y.; Butpheng, C.; Lee, L.-F.; Liu, Y.-H. A Secure Interoperability Management Scheme for Cross-Blockchain Transactions. Symmetry 2022, 14, 2473. [Google Scholar] [CrossRef]
- Wang, H.; Wang, Q.; He, D. Blockchain-Based Private Provable Data Possession. IEEE Trans. Dependable Secur. Comput. 2021, 18, 2379–2389. [Google Scholar] [CrossRef]
- Ma, Z.; Ma, J.; Miao, Y.; Li, Y.; Deng, R.H. ShieldFL: Mitigating model poisoning attacks in privacy-preserving federated learning. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1639–1654. [Google Scholar] [CrossRef]
- Ma, Z.; Ma, J.; Miao, Y.; Liu, X.; Choo, K.-K.R.; Deng, R. Pocket diagnosis: Secure federated learning against poisoning attack in the cloud. IEEE Trans. Serv. Comput. 2022, 15, 3429–3442. [Google Scholar] [CrossRef]
- Weng, J.; Weng, J.; Zhang, J.; Li, M.; Zhang, Y.; Luo, W. DeepChain: Auditable and privacy-preserving deep learning with blockchain-based incentive. IEEE Trans. Dependable Secur. Comput. 2021, 18, 2438–2455. [Google Scholar] [CrossRef]
- Swan, M. Blockchain: Blueprint for a New Economy; O’Reilly Media, Inc.: Newton, MA, USA, 2015. [Google Scholar]
- Khan, M.A.; Salah, K. IoT Security: Review, Blockchain Solutions, and Open Challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and Privacy for Healthcare Blockchains. IEEE Trans. Serv. Comput. 2022, 15, 3668–3686. [Google Scholar] [CrossRef]
- Saeed, H.; Malik, H.; Bashir, U.; Ahmad, A.; Riaz, S.; Ilyas, M.; Bukhari, W.A.; Khan, M.I.A. Blockchain technology in healthcare: A systematic review. PLoS ONE 2022, 17, e0266462. [Google Scholar] [CrossRef]
- Yin, H.L.; Fu, Y.; Li, C.L.; Weng, C.X.; Li, B.H.; Gu, J.; Lu, Y.S.; Huang, S.; Chen, Z.B. Experimental quantum secure network with digital signatures and encryption. Natl. Sci. Rev. 2022, 10, nwac228. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public-key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, 9–12 December 1984; pp. 175–179. [Google Scholar]
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F. Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400–403. [Google Scholar] [CrossRef]
- Xie, Y.M.; Lu, Y.S.; Weng, C.X.; Cao, X.Y.; Jia, Z.Y.; Bao, Y.; Wang, Y.; Fu, Y.; Yin, H.L.; Chen, Z.B. Breaking the Rate-Loss Bound of Quantum Key Distribution with Asynchronous Two-Photon Interference. PRX Quantum 3 2022, 3, 020315. [Google Scholar] [CrossRef]
- Gu, J.; Cao, X.Y.; Fu, Y.; He, Z.W.; Yin, Z.J.; Yin, H.L.; Chen, Z.B. Experimental measurement-device-independent type quantum key distribution with flawed and correlated sources. Sci. Bull. 2022, 67, 2167–2175. [Google Scholar] [CrossRef]
- Kassab, M.; DeFranco, J.; Malas, T. Exploring Research in Blockchain for Healthcare and a Roadmap for the Future. IEEE Trans. Emerg. Top. Comput. 2021, 9, 1835–1852. [Google Scholar] [CrossRef]
- Pan, H.; Zhang, Y.; Si, X.; Yao, Z.; Zhao, L. MDS2-C3PF: A Medical Data Sharing Scheme with Cloud-Chain Cooperation and Policy Fusion in IoT. Symmetry 2022, 14, 2479. [Google Scholar] [CrossRef]
- Rahulamathavan, Y.; Phan, R.; Rajarajan, M. Privacy-Preserving Blockchain Based IoT Ecosystem using Attribute-based Encryption. In Proceedings of the 2017 IEEE International Conference on Advanced Networks and Telecommunications Systems, Bhubaneswar, India, 17–20 December 2017; pp. 1–6. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Qi, S.; Lu, Y.; Zheng, Y.; Li, Y.; Chen, X. Cpds: Enabling Compressed and Private Data Sharing for Industrial Internet of Things over Blockchain. IEEE Trans. Ind. Inform. 2021, 17, 2376–2387. [Google Scholar] [CrossRef]
- Du, M.; Chen, Q.; Chen, J. An Optimized Consortium Blockchain for Medical Information Sharing. IEEE Trans. Eng. Manag. 2020, 68, 1677–1689. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N. SPDS: A Secure and Auditable Private Data Sharing Scheme for Smart Grid Based on Blockchain and Smart Contract. IEEE Trans. Ind. Inform. 2020, 17, 7688–7699. [Google Scholar] [CrossRef]
- Zhang, N.; Li, J.; Lou, W.; Hou, Y.T. PrivacyGuard: Enforcing Private Data Usage with Blockchain and Attested Execution. In International Workshop on Data Privacy Management; Springer: Berlin, Germany, 2018; pp. 345–353. [Google Scholar]
- Nguyen, D.; Pathirana, P.; Ding, M. BEdgeHealth: A Decentralized Architecture for Edge-Based IoMT Networks Using Blockchain. IEEE Internet Things J. 2021, 8, 11743–11757. [Google Scholar] [CrossRef]
- Wu, G.; Wang, S.; Ning, Z.; Zhu, B. Privacy-Preserved Electronic Medical Record Exchanging and Sharing: A Blockchain-Based Smart Healthcare System. IEEE J. Biomed. Health Inform. 2022, 26, 1917–1927. [Google Scholar] [CrossRef]
- Yu, C.; Zhan, Y.; Sohail, M. SDSM: Secure Data Sharing for Multilevel Partnerships in IoT Based Supply Chain. Symmetry 2022, 14, 2656. [Google Scholar] [CrossRef]
- Costan, V.; Devadas, S. Intel SGX Explained. Available online: https://eprint.iacr.org/2016/086.pdf (accessed on 17 September 2021).
- Ren, Y.; Zhang, X.; Gu, D.; Feng, G. Efficient outsourced extraction of histogram features over encrypted images in cloud. Sci. China Inf. Sci. 2021, 64, 139105. [Google Scholar] [CrossRef]
- Krawczyk, H.; Rabin, T. Chameleon Hashing and Signatures. In Proceedings of the 7th Annual Network and Distributed System Security Symposium, San Diego, CA, USA, 3–4 February 2000; pp. 143–154. [Google Scholar]
- Jia, Y.; Sun, S.; Zhang, Y. Redactable Blockchain Supporting Supervision and Self-Management. In Proceedings of the ASIA CCS, Virtual Event, Hong Kong, China, 7–11 June 2021; pp. 844–858. [Google Scholar]
- Chen, X.; Zhang, F.; Kim, K. Chameleon Hashing without Key Exposure. In Proceedings of the International Conference on Information Security, Palo Alto, CA, USA, 27–29 September 2004; pp. 87–98. [Google Scholar]
- Camenisch, J.; Derler, D.; Krenn, S. Chameleon Hashes with Ephemeral Trapdoors—And Applications to Invisible Sanitizable Signatures. Public Key Cryptogr. 2017, 20, 152–182. [Google Scholar]
- Ateniese, G.; de Medeiros, B. On the Key Exposure Problem in Chameleon Hashes. In Proceedings of the International Conference on Security in Communication Networks, Amalfi, Italy, 8–10 September 2004; pp. 165–179. [Google Scholar]
- Cordoş, A.A.; Bolboacă, S.D.; Prato, R.; Fortunato, F. iGeneration’s social media usage in retrieving information related to healthcare education: A web-based survey among Italian and Romanian undergraduate medical students. Ann. Ist. Super. Sanita 2019, 55, 34–40. [Google Scholar]
- Jäntschi, L. Binomial Distributed Data Confidence Interval Calculation: Formulas, Algorithms and Examples. Symmetry 2022, 14, 1104. [Google Scholar] [CrossRef]



| System | Access Control | Revocation of Power | Use Control | Data Privacy |
|---|---|---|---|---|
| Pbee [24] | ✔ | ✘ | ✘ | ✔ |
| Cpds [26] | ✔ | ✘ | ✘ | ✔ |
| Obms [27] | ✘ | ✘ | ✘ | ✔ |
| Spds [28] | ✔ | ✘ | ✔ | ✔ |
| PG [29] | ✔ | ✘ | ✔ | ✔ |
| BEdgeHealth [30] | ✔ | ✘ | ✘ | ✔ |
| Bshs [31] | ✔ | ✘ | ✘ | ✔ |
| SDSM [32] | ✔ | ✘ | ✘ | ✔ |
| Ours | ✔ | ✔ | ✔ | ✔ |
| Notation | Descriptions |
|---|---|
| Patient’s identification information | |
| Hospital’s chameleon key pair | |
| Patient’s chameleon key pair | |
| Hospital’s signature key pair | |
| Visitor’s chameleon key pair | |
| The validation public key and signature private key of the application platform | |
| The hash algorithm | |
| The digital signature algorithm and the verification algorithm of digital signature | |
| Symmetric encryption algorithm and symmetric decryption algorithm, which are used to encrypt and decrypt medical data | |
| The symmetric key for encryption and decryption |
| System | 100 B | 1 kB | 5 kB | 10 kB |
|---|---|---|---|---|
| Cpds [26] | 1.23 | 1.40 | 1.44 | 1.45 |
| ours | 1.56 | 15.63 | 78.12 | 156.25 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hu, M.; Ren, Y.; Chen, C. Privacy-Preserving Medical Data-Sharing System with Symmetric Encryption Based on Blockchain. Symmetry 2023, 15, 1010. https://doi.org/10.3390/sym15051010
Hu M, Ren Y, Chen C. Privacy-Preserving Medical Data-Sharing System with Symmetric Encryption Based on Blockchain. Symmetry. 2023; 15(5):1010. https://doi.org/10.3390/sym15051010
Chicago/Turabian StyleHu, Mingqi, Yanli Ren, and Cien Chen. 2023. "Privacy-Preserving Medical Data-Sharing System with Symmetric Encryption Based on Blockchain" Symmetry 15, no. 5: 1010. https://doi.org/10.3390/sym15051010
APA StyleHu, M., Ren, Y., & Chen, C. (2023). Privacy-Preserving Medical Data-Sharing System with Symmetric Encryption Based on Blockchain. Symmetry, 15(5), 1010. https://doi.org/10.3390/sym15051010