A Novel Disturbance Rejection Method Based on Robust Sliding Mode Control for the Secure Communication of Chaos-Based System
Abstract
:1. Introduction
2. Mathematical Modeling and Preliminary Mathematics
2.1. Mathematical Modeling of MSSs
2.2. Preliminary Mathematics
2.2.1. Fractional Calculus
2.2.2. Fixed-Time Sliding Mode Control
2.2.3. Proposed DO
3. Proposed Approach
3.1. Fixed-Time SMC for SCS
3.2. Proposed DO for SCS
3.3. Stability Analysis
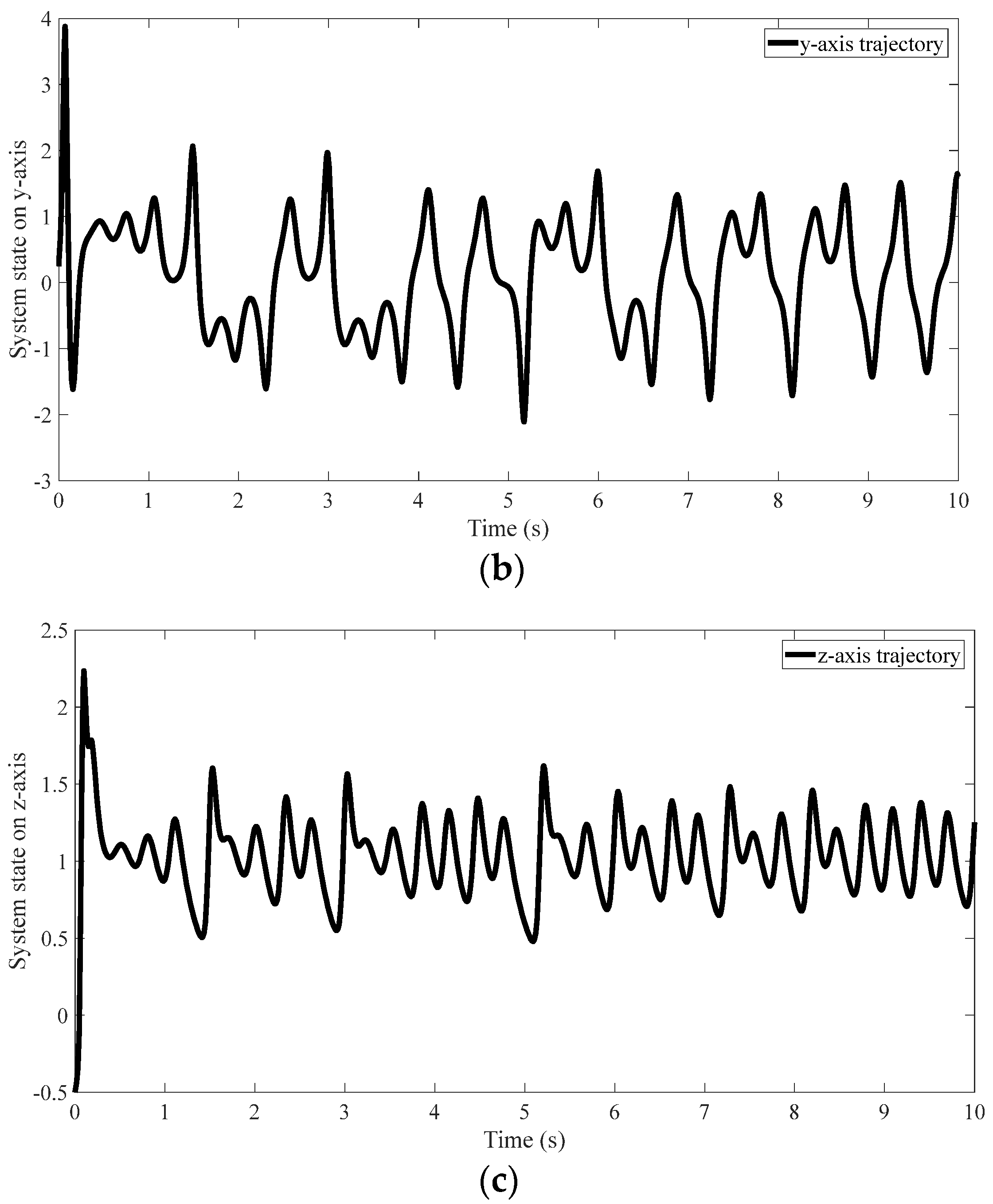
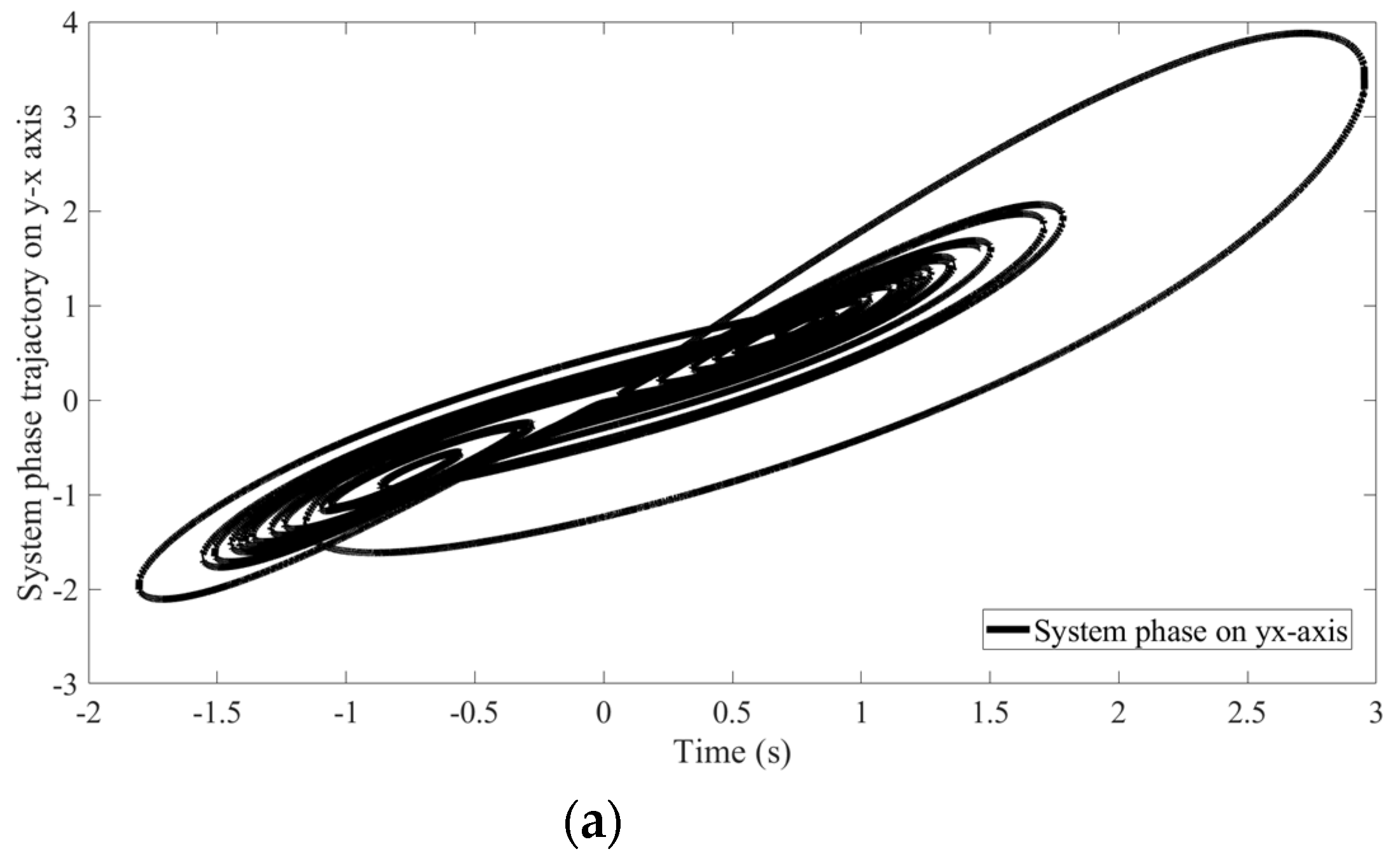
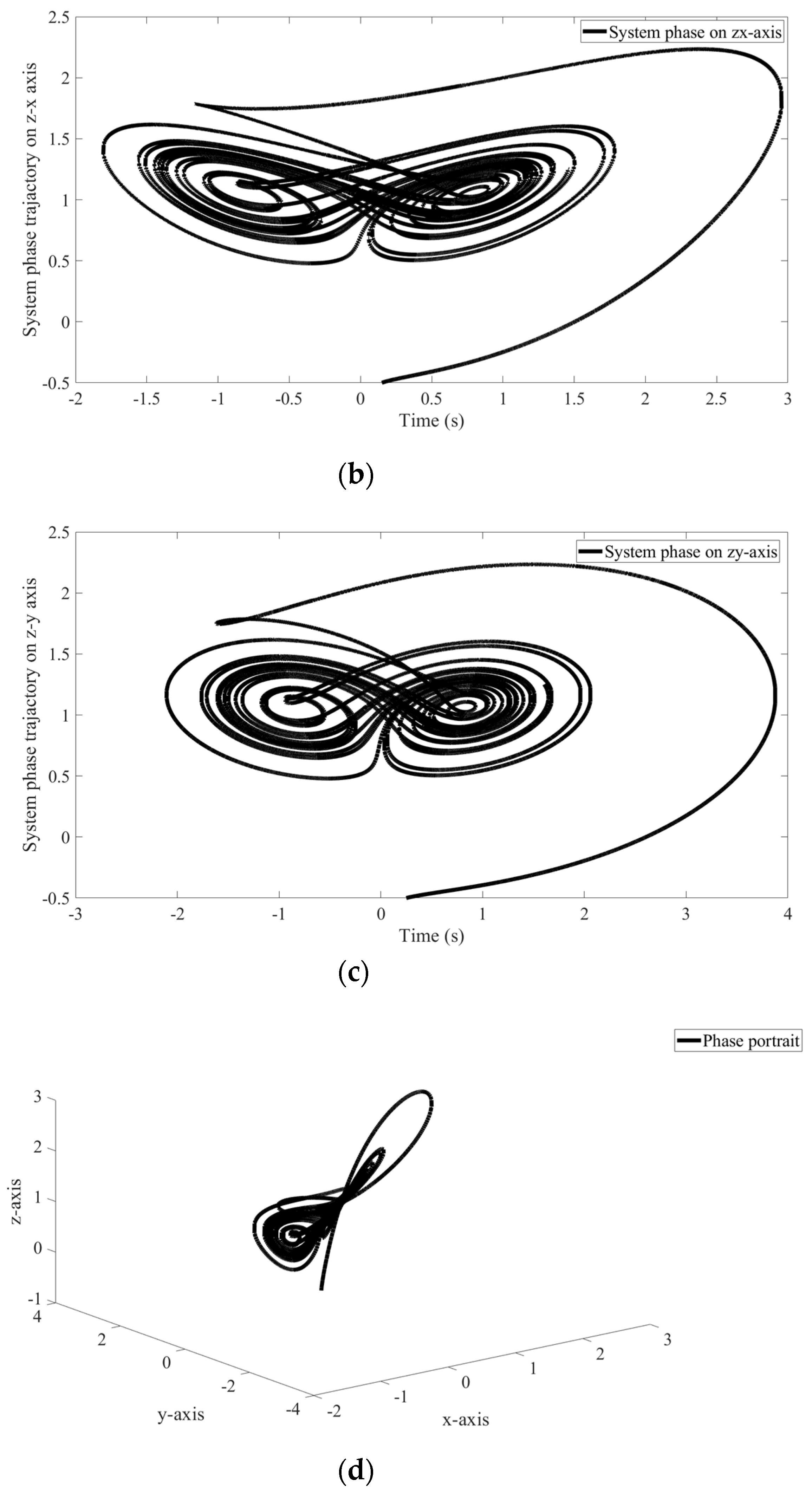
4. An Illustrative Example
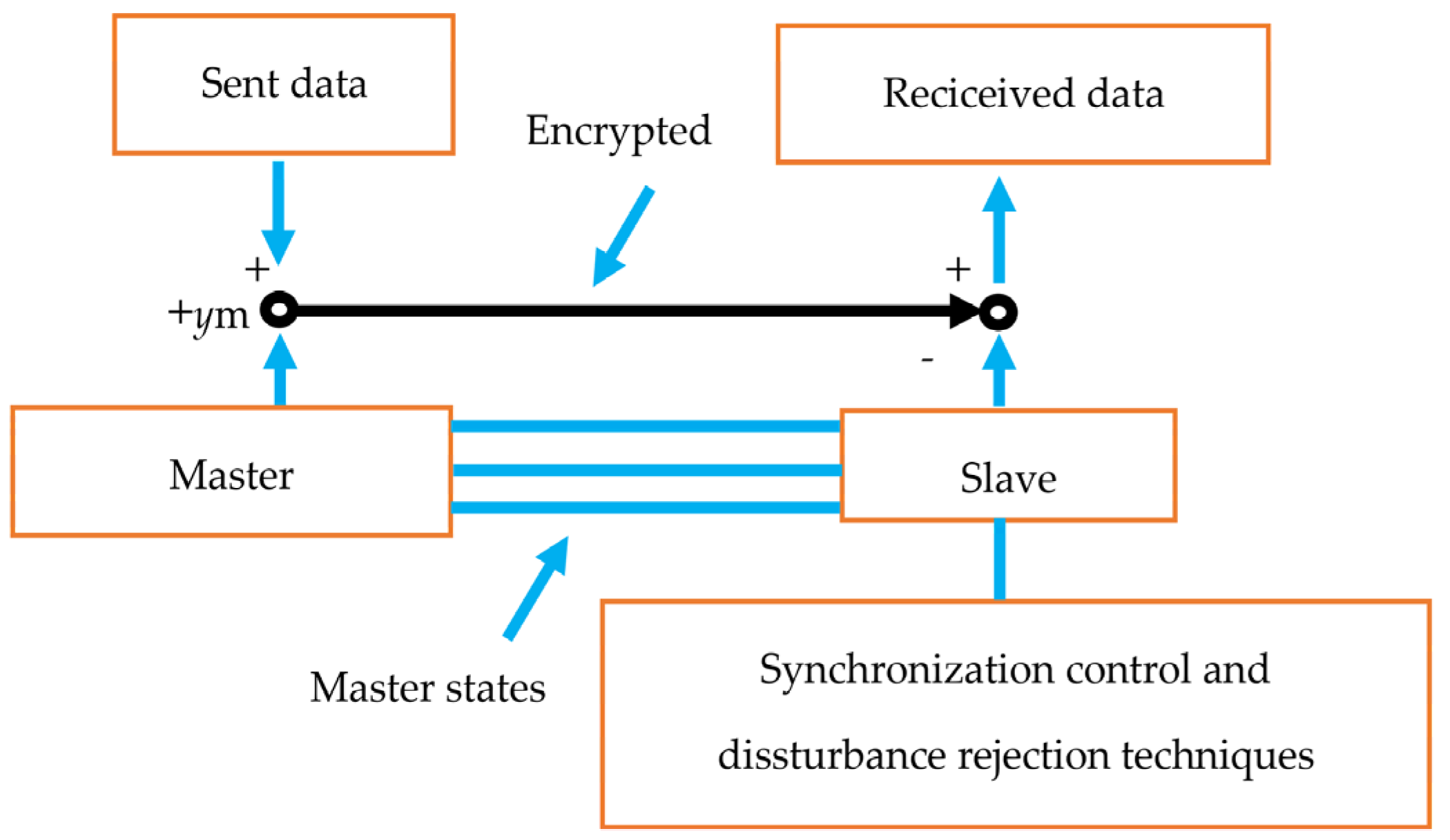
4.1. Scheme of SCS of the CBS and Parameters of Proposed Method
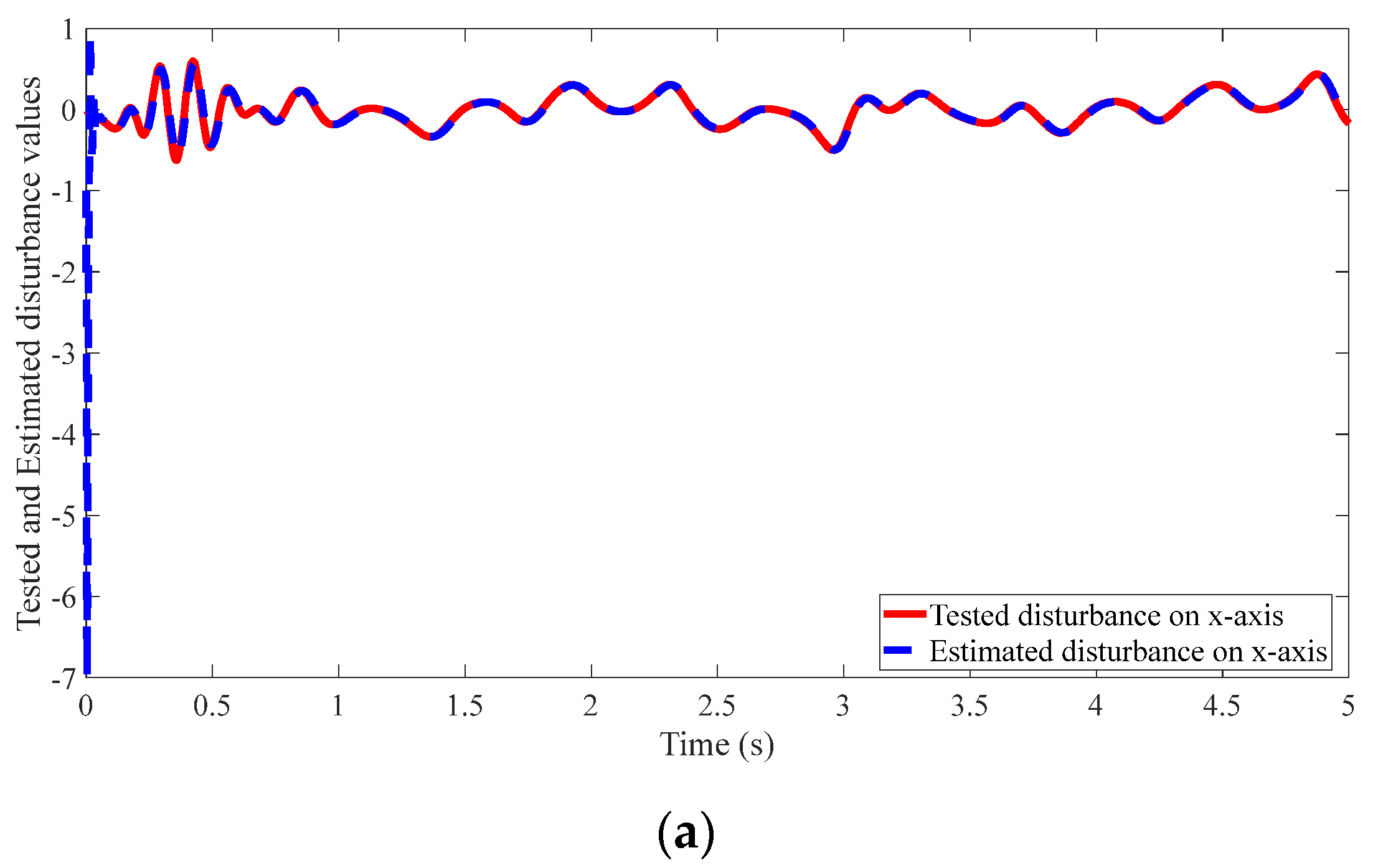
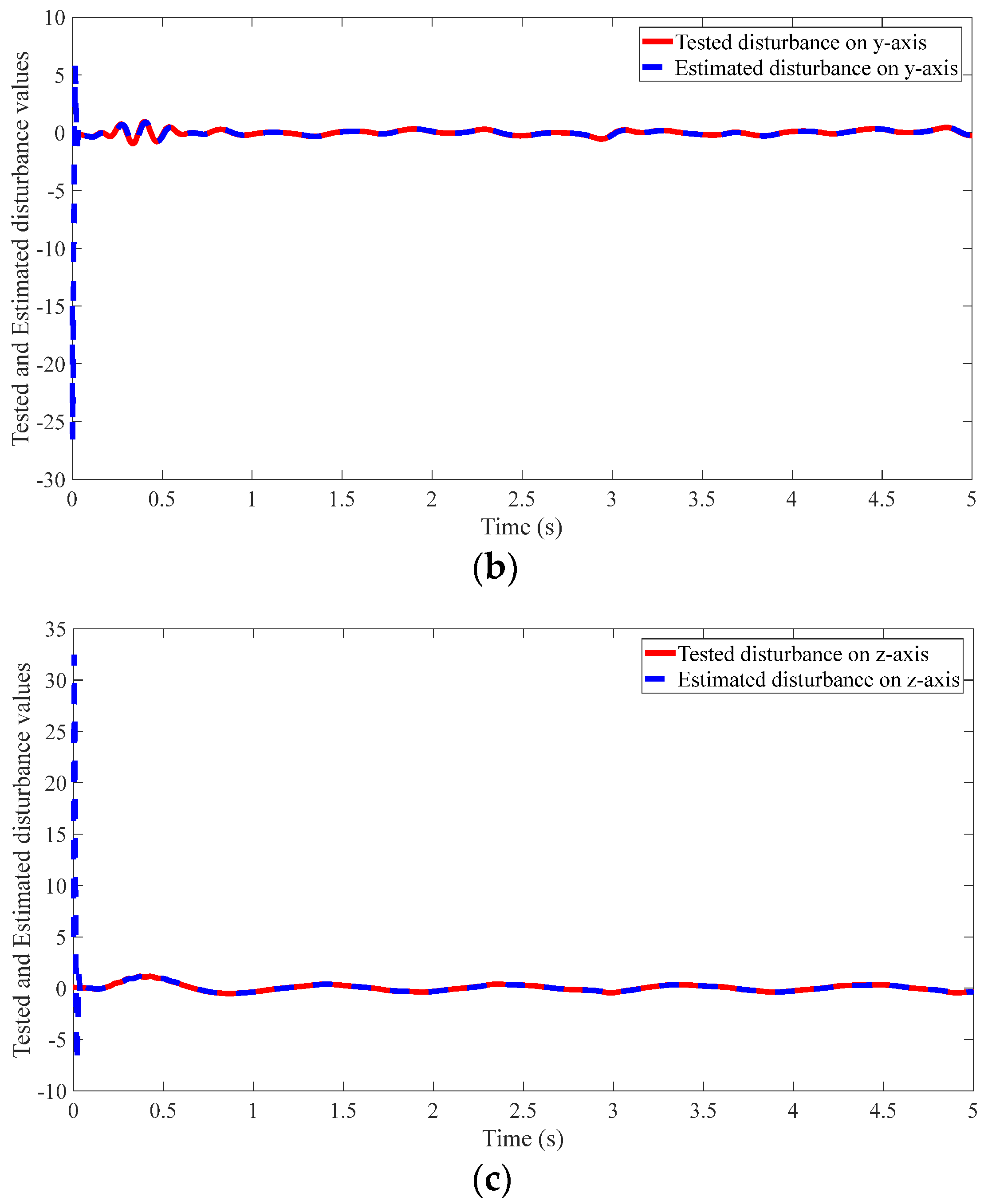
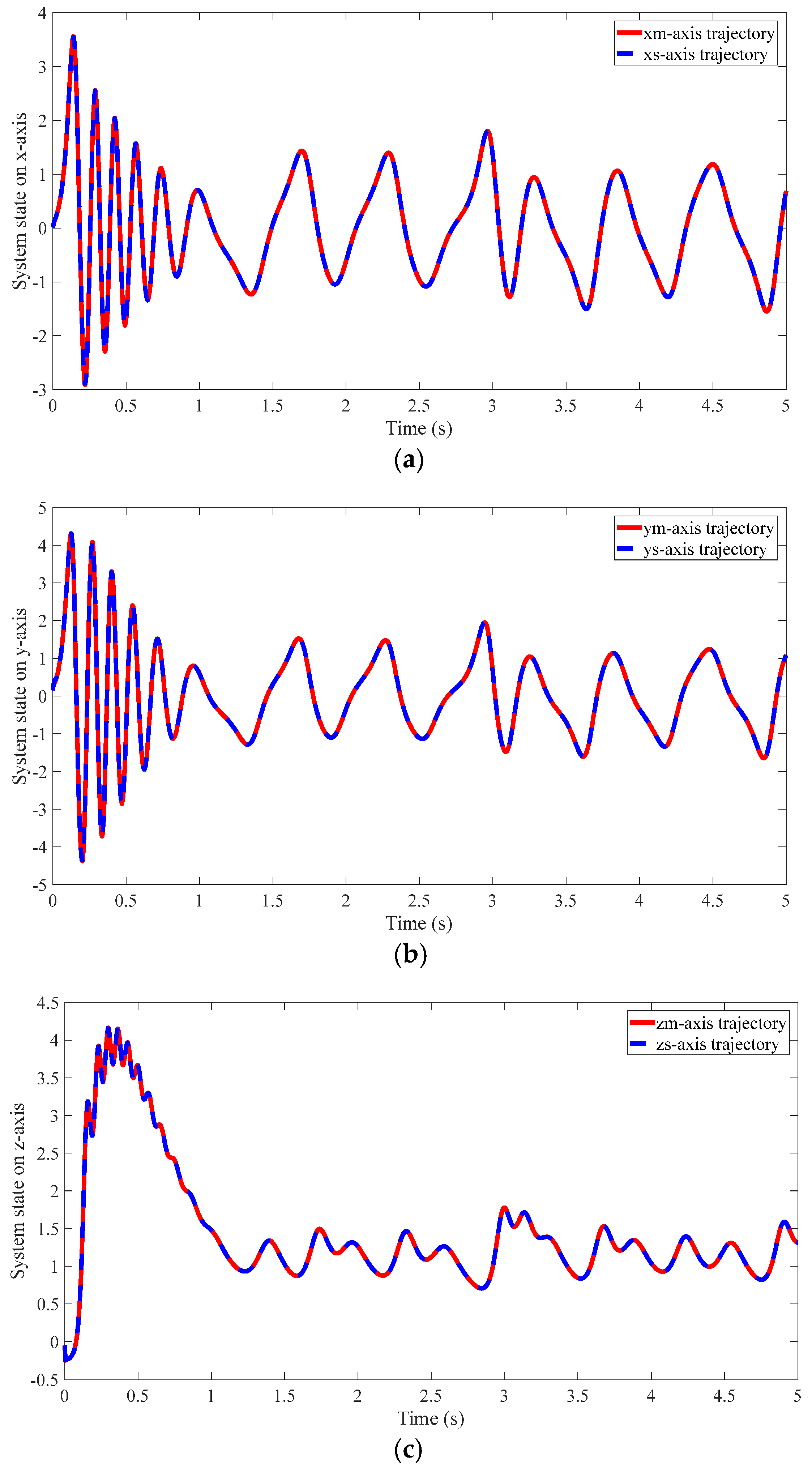
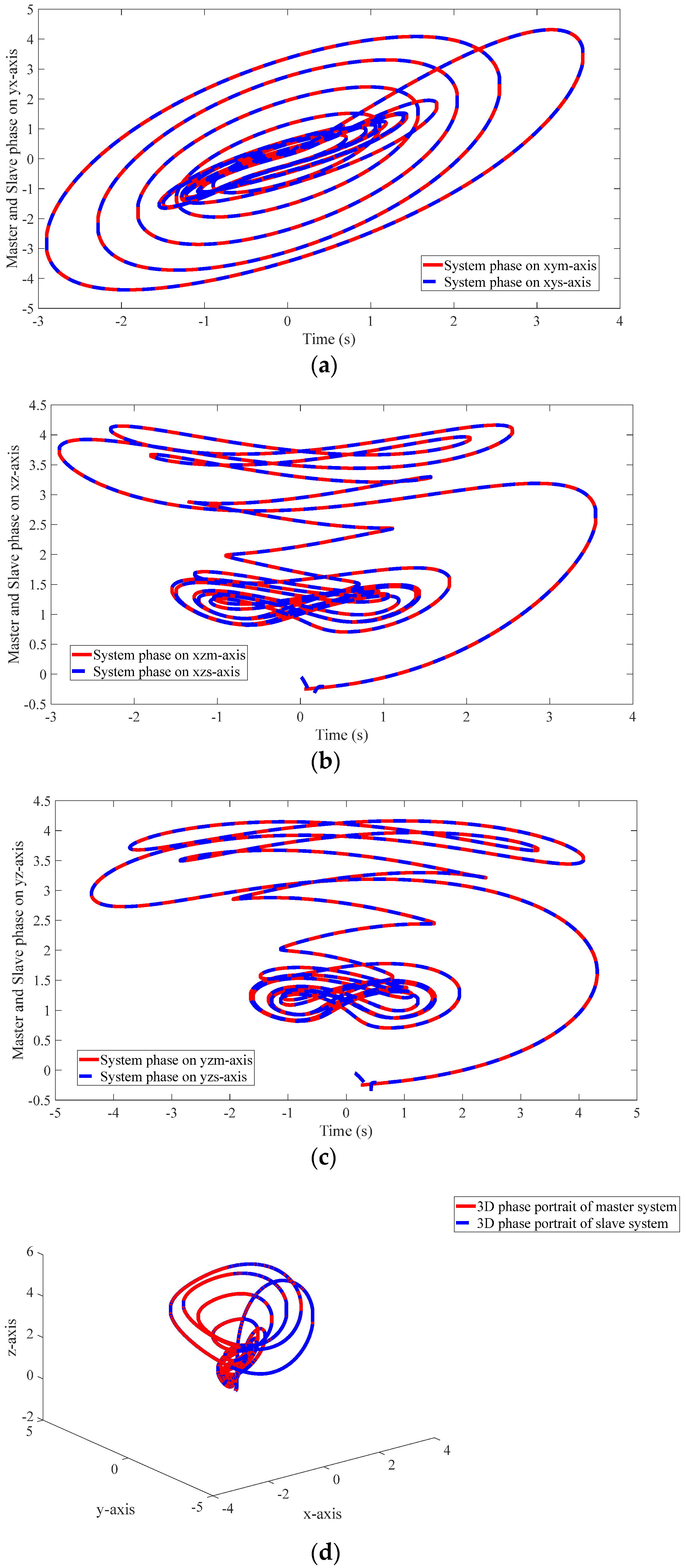
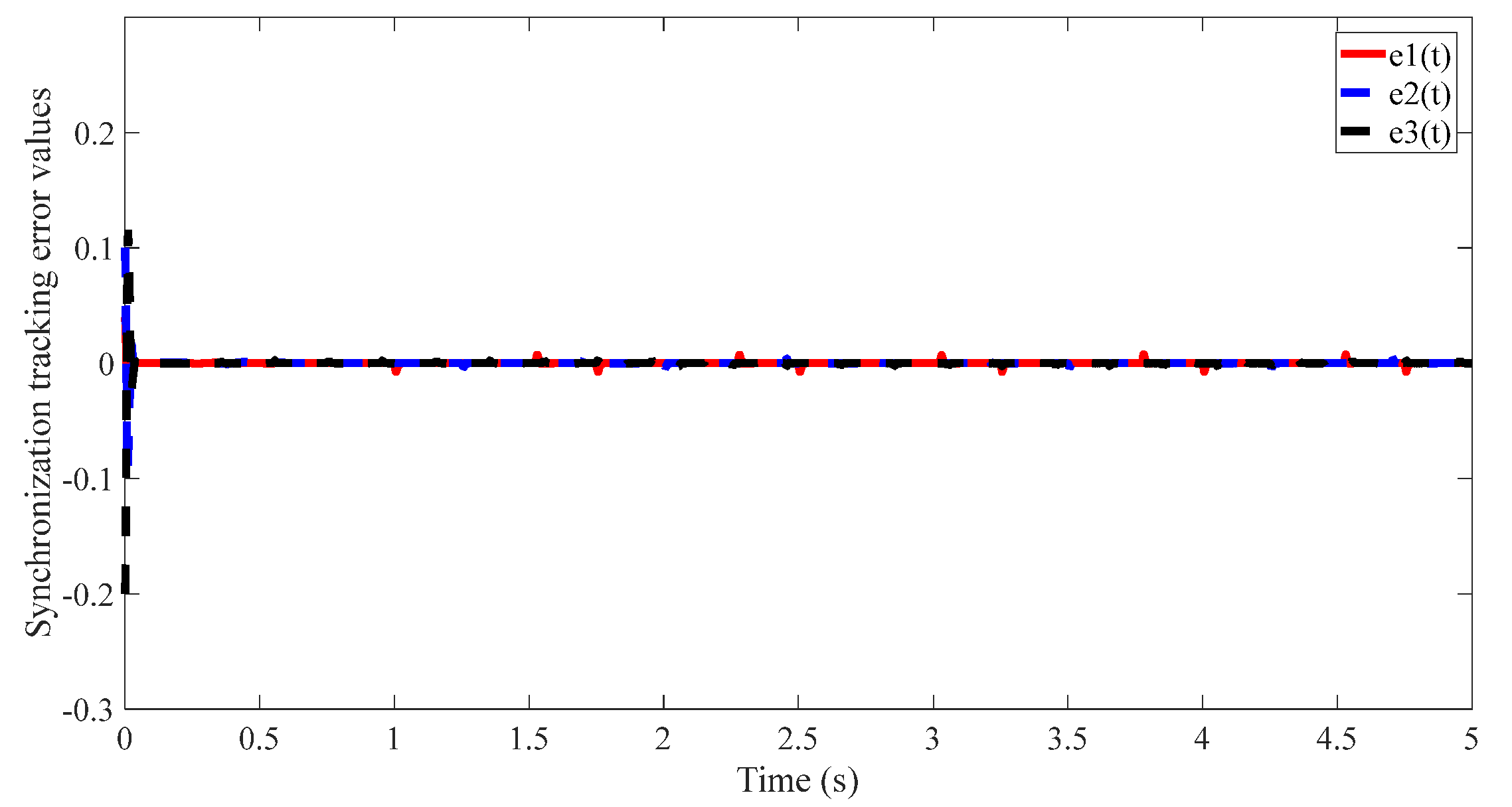
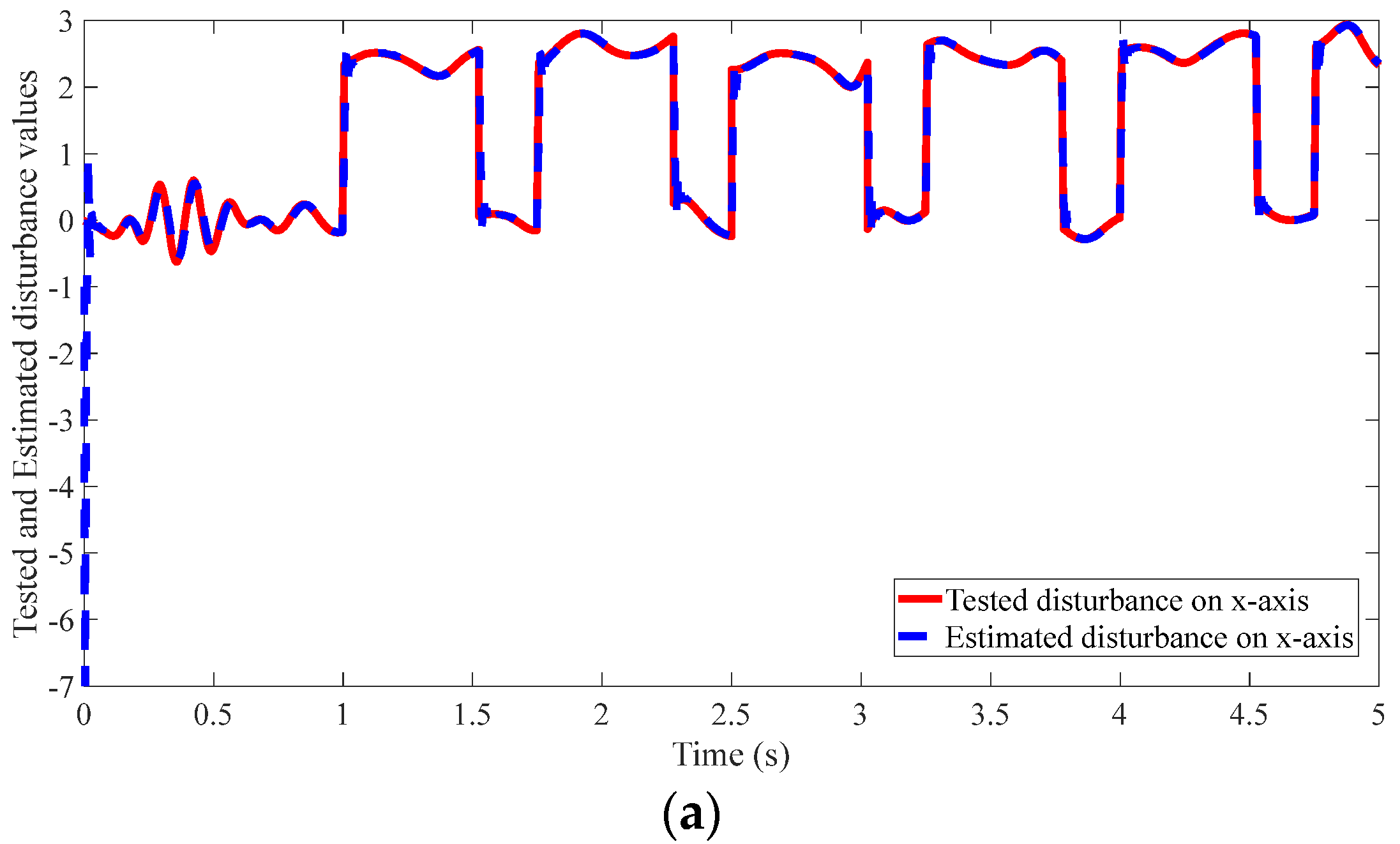
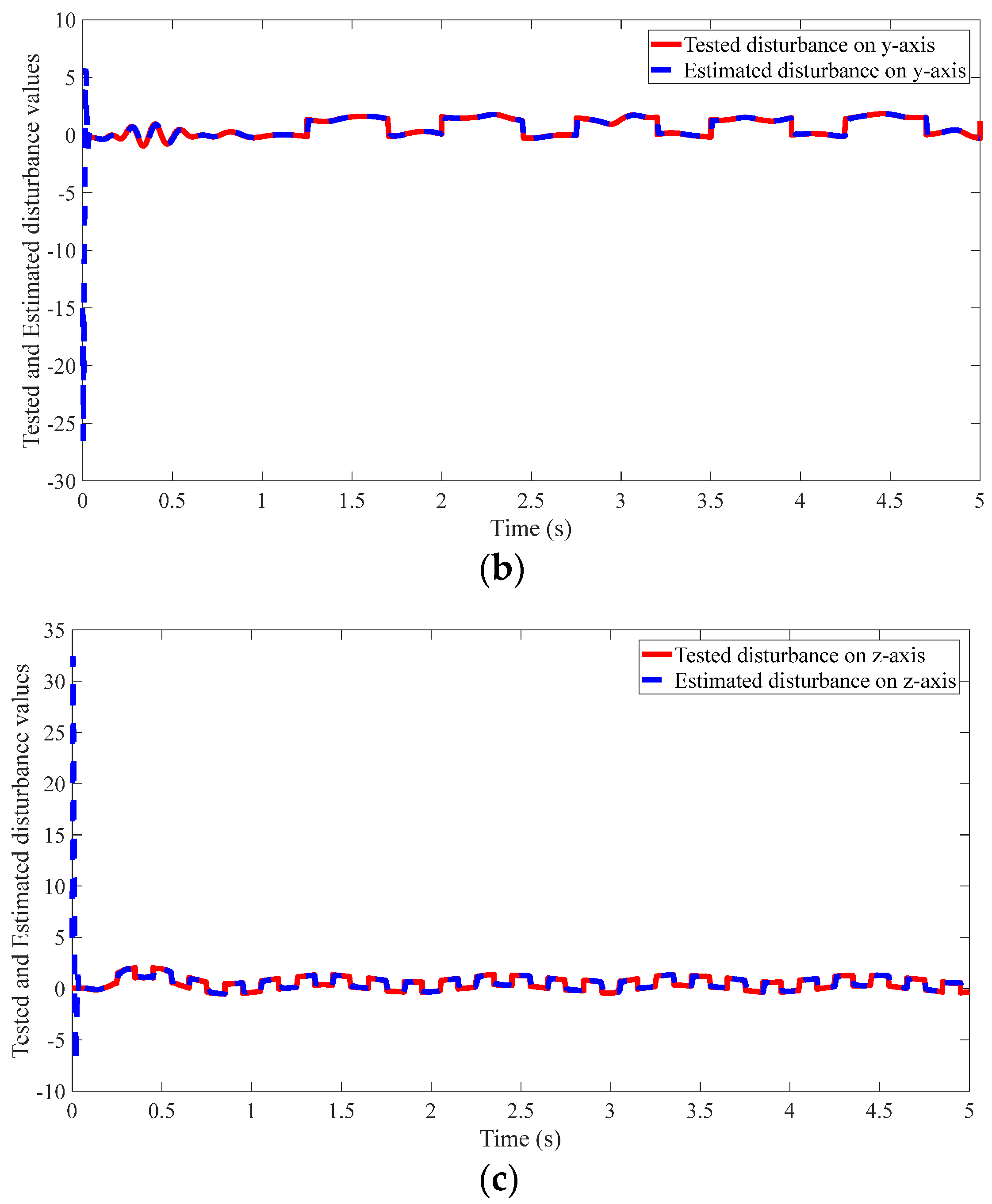
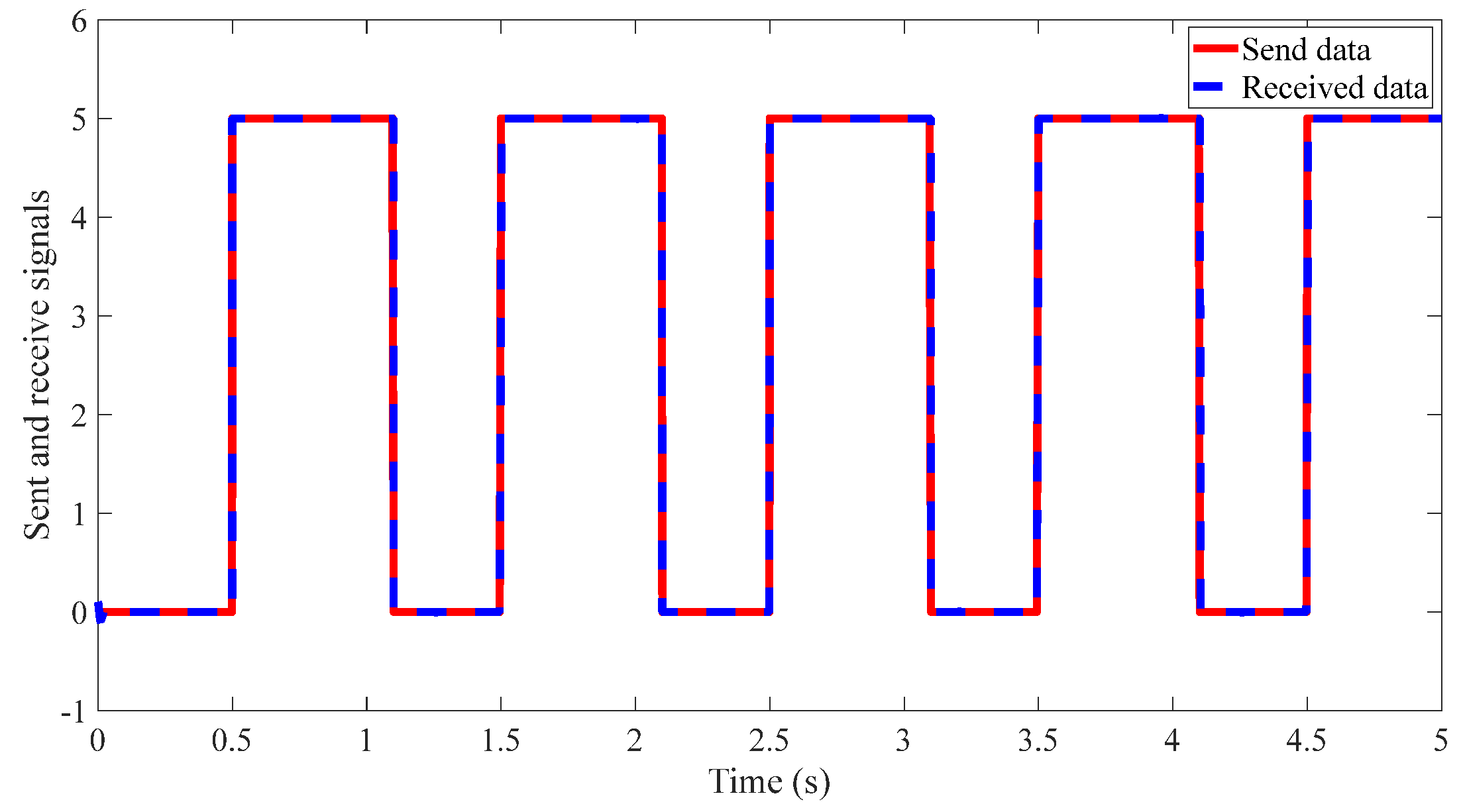
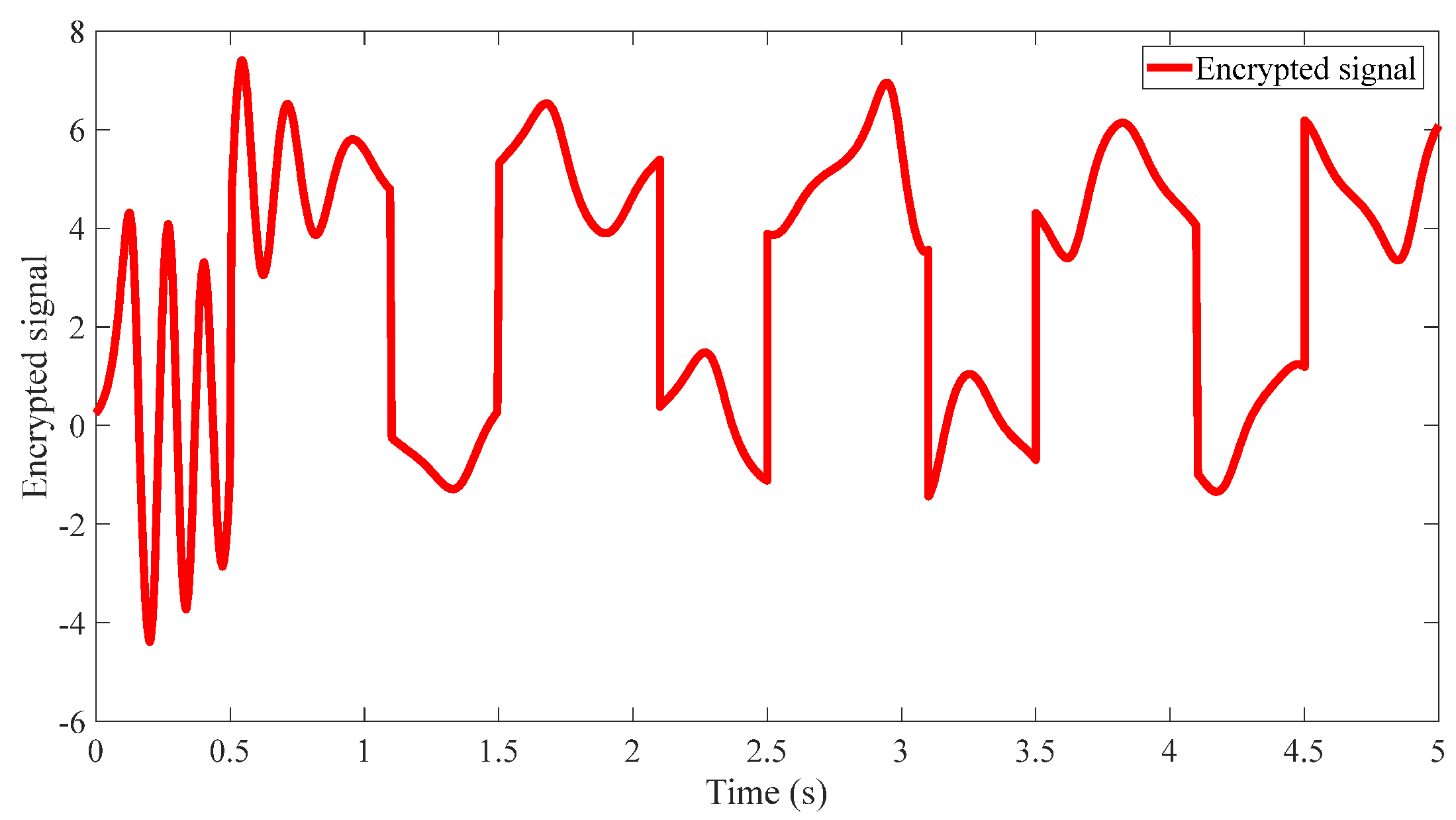
4.2. Results of the Proposed Method
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A

References
- Chen, W.H.; Ballance, D.J.; Gawthrop, P.J.; O’Reilly, J. A nonlinear disturbance observer for robotic manipulators. IEEE Trans. Ind. Electron. 2000, 47, 932–938. [Google Scholar] [CrossRef]
- Nguyen, A.T.; Basit, B.A.; Choi, H.H.; Jung, J.W. Disturbance attenuation for surface-mounted PMSM drives using nonlinear disturbance observer-based sliding mode control. IEEE Access 2020, 8, 86345–86356. [Google Scholar] [CrossRef]
- Wu, X.; Xu, K.; Lei, M.; He, X. Disturbance-compensation-based continuous sliding mode control for overhead cranes with disturbances. IEEE Trans. Autom. Sci. Eng. 2020, 17, 2182–2189. [Google Scholar] [CrossRef]
- Giap, V.N.; Huang, S.C.; Nguyen, Q.D.; Su, T.J. Disturbance observer-based linear matrix inequality for the synchronization of Takagi-Sugeno fuzzy chaotic systems. IEEE Access 2020, 8, 225805–225821. [Google Scholar] [CrossRef]
- Giap, V.N.; Nguyen, Q.D.; Huang, S.C. Synthetic adaptive fuzzy disturbance observer and sliding-mode control for chaos-based secure communication systems. IEEE Access 2021, 9, 23907–23928. [Google Scholar] [CrossRef]
- Giap, V.N.; Vu, H.S.; Nguyen, Q.D.; Huang, S.C. Disturbance and uncertainty rejection-based on fixed-time sliding-mode control for the secure communication of chaotic systems. IEEE Access 2021, 9, 133663–133685. [Google Scholar] [CrossRef]
- Giap, V.N.; Vu, H.S.; Huang, S.-C. Time-varying disturbance observer based on regulating boundary layer thickness sliding mode control for microelectromechanical systems gyroscope. Meas. Control 2022. [Google Scholar] [CrossRef]
- Hwang, S.; Kim, H.S. Extended disturbance observer-based integral sliding mode control for nonlinear system via T–S fuzzy model. IEEE Access 2020, 8, 116090–116105. [Google Scholar] [CrossRef]
- Giap, V.N.; Nguyen, Q.D.; Trung, N.K.; Huang, S.C.; Trinh, X.T. Disturbance Observer Based on Terminal Sliding-Mode Control for a Secure Communication of Fractional-Order Takagi-Sugeno Fuzzy Chaotic Systems. In Proceedings of the International Conference on Advanced Mechanical Engineering, Automation and Sustainable Development; Ha Long, Vietnam, 4–7 November 2021, Springer: Cham, Switzerland, 2022; pp. 936–941. [Google Scholar]
- Chen, Y.-J.; Chou, H.-G.; Wang, W.-J.; Tsai, S.-H.; Tanaka, K.; Wang, H.O.; Wang, K.-C. A polynomial-fuzzy-model-based synchronization methodology for the multi-scroll Chen chaotic secure communication system. Eng. Appl. Artif. Intell. 2020, 87, 103251. [Google Scholar] [CrossRef]
- Çiçek, S.; Kocamaz, U.E.; Uyaroglu, Y. Secure communication with a chaotic system owning logic element. AEU-Int. J. Electron. Commun. 2018, 88, 52–62. [Google Scholar] [CrossRef]
- Pappu, C.S.; Flores, B.C.; Debroux, P.S.; Boehm, J.E. An electronic implementation of Lorenz chaotic oscillator synchronization for bistatic radar applications. IEEE Trans. Aerosp. Electron. Syst. 2017, 53, 2001–2013. [Google Scholar] [CrossRef]
- Mahmoud, E.E.; Higazy, M.; Althagafi, O.A. A novel strategy for complete and phase robust synchronizations of chaotic nonlinear systems. Symmetry 2020, 12, 1765. [Google Scholar] [CrossRef]
- Vaseghi, B.; Hashemi, S.S.; Mobayen, S.; Fekih, A. Finite time chaos synchronization in time-delay channel and its application to satellite image encryption in OFDM communication systems. IEEE Access 2021, 9, 21332–21344. [Google Scholar] [CrossRef]
- Zhou, M.; Wang, C. A novel image encryption scheme based on conservative hyperchaotic system and closed-loop diffusion between blocks. Signal Process. 2020, 171, 107484. [Google Scholar] [CrossRef]
- Wang, X.; Gao, S. Image encryption algorithm for synchronously updating Boolean networks based on matrix semi-tensor product theory. Inf. Sci. 2020, 507, 16–36. [Google Scholar] [CrossRef]
- Vaidyanathan, S.; Akgul, A.; Kaçar, S.; Çavuşoglu, U. A new 4-D chaotic hyperjerk system, its synchronization, circuit design and applications in RNG, image encryption and chaos-based steganography. Eur. Phys. J. Plus 2018, 133, 46–64. [Google Scholar] [CrossRef]
- Zhang, Y.-Q.; Hao, J.-L.; Wang, X.-Y. An efficient image encryption scheme based on S-boxes and fractional-order differential logistic map. IEEE Access 2020, 8, 54175–54188. [Google Scholar] [CrossRef]
- Zhou, L.; Tan, F. A chaotic secure communication scheme based on synchronization of double-layered and multiple complex networks. Nonlinear Dyn. 2019, 96, 869–883. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Tan, Y. Hidden extreme multistability with hyperchaos and transient chaos in a Hopfield neural network affected by electromagnetic radiation. Nonlinear Dyn. 2020, 99, 2369–2386. [Google Scholar] [CrossRef]
- Fei, Z.; Guan, C.; Gao, H. Exponential synchronization of networked chaotic delayed neural network by a hybrid event trigger scheme. IEEE Trans. Neural Netw. Learn. Syst. 2018, 29, 2558–2567. [Google Scholar] [CrossRef]
- Liu, P.; Zeng, Z.; Wang, J. Global synchronization of coupled fractional-order recurrent neural networks. IEEE Trans. Neural Netw. Learn. Syst. 2019, 30, 2358–2368. [Google Scholar] [CrossRef]
- Wang, J.-L.; Qin, Z.; Wu, H.-N.; Huang, T. Passivity and synchronization of coupled uncertain reaction-diffusion neural networks with multiple time delays. IEEE Trans. Neural Netw. Learn. Syst. 2019, 30, 2434–2448. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.Y.; Karimi, H.R.; Yan, H.C. An adaptive event-triggered synchronization approach for chaotic Lur’e systems subject to aperiodic sampled data. IEEE Trans. Circuits Syst. II Exp. Briefs 2019, 66, 442–446. [Google Scholar] [CrossRef]
- Chang, D.; Li, Z.; Wang, M.; Zeng, Y. A novel digital programmable multi-scroll chaotic system and its application in FPGA-based audio secure communication. AEU-Int. J. Electron. Commun. 2018, 88, 20–29. [Google Scholar] [CrossRef]
- Giap, V.-N.; Huang, S.-C.; Nguyen, Q.D. Synchronization of 3D chaotic system based on sliding mode control: Electronic circuit implementation. In Proceedings of the 2020 IEEE Eurasia Conference on IOT, Communication and Engineering (ECICE), Yunlin, Taiwan, 23–25 October 2020; pp. 156–159. [Google Scholar] [CrossRef]
- Wu, Z.; Zhang, X.; Zhong, X. Generalized chaos synchronization circuit simulation and asymmetric image encryption. IEEE Access 2019, 7, 37989–38008. [Google Scholar] [CrossRef]
- Lai, Q.; Norouzi, B.; Liu, F. Dynamic analysis, circuit realization, control design and image encryption application of an extended Lü system with coexisting attractors. Chaos Solitons Fractals 2018, 114, 230–245. [Google Scholar] [CrossRef]
- Lendek, Z.; Guerra, T.M.; Babuska, R.; De Schutter, B. Stability Analysis and Nonlinear Observer Design Using Takagi-Sugeno Fuzzy Models; Springer: Berlin/Heidelberg, Germany, 2011; p. 262. [Google Scholar]
- Takagi, T.; Sugeno, M. Fuzzy identification of systems and its applications to modeling and control. IEEE Trans. Syst. Man Cybern. B Cybern. 1985, 1, 116–132. [Google Scholar] [CrossRef]
- Zhong, G.; Tang, W. Circuitry implementation and synchronization of Chen’s attractor. Inter. J. Bifurcation Chaos 2002, 12, 1423–1427. [Google Scholar] [CrossRef]
- Tepljakov, A.; Petlenkov, E.; Belikov, J. FOMCON: Fractional-order modeling and control toolbox for MATLAB. In Fractional-Order Modeling and Control of Dynamic Systems; Springer: Cham, Switzerland, 2011; pp. 684–689. [Google Scholar]
- Polyakov, A. Nonlinear feedback design for fixed-time stabilization of linear control systems. IEEE Trans. Autom. Control 2012, 57, 2106–2110. [Google Scholar] [CrossRef]
- Giap, V.N.; Nguyen, Q.D.; Trung, N.K.; Huang, S.C. Time-varying disturbance observer based on sliding-mode observer and double phases fixed-time sliding mode control for a TS fuzzy micro-electro-mechanical system gyroscope. J. Vib. Control 2022. [Google Scholar] [CrossRef]
- Truc, L.N.; Vu, L.A.; Thoan, T.V.; Thanh, B.T.; Nguyen, T.L. Adaptive Sliding Mode Control Anticipating Proportional Degradation of Actuator Torque in Uncertain Serial Industrial Robots. Symmetry 2022, 14, 957. [Google Scholar] [CrossRef]
- Giap, V.N.; Huang, S.C. Effectiveness of fuzzy sliding mode control boundary layer based on uncertainty and disturbance compensator on suspension active magnetic bearing system. Meas. Control 2020, 53, 934–942. [Google Scholar] [CrossRef]
- Petráš, I. Fractional-Order Nonlinear Systems: Modeling, Analysis and Simulation; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nguyen, Q.D.; Giap, V.N.; Tran, V.H.; Pham, D.-H.; Huang, S.-C. A Novel Disturbance Rejection Method Based on Robust Sliding Mode Control for the Secure Communication of Chaos-Based System. Symmetry 2022, 14, 1668. https://doi.org/10.3390/sym14081668
Nguyen QD, Giap VN, Tran VH, Pham D-H, Huang S-C. A Novel Disturbance Rejection Method Based on Robust Sliding Mode Control for the Secure Communication of Chaos-Based System. Symmetry. 2022; 14(8):1668. https://doi.org/10.3390/sym14081668
Chicago/Turabian StyleNguyen, Quang Dich, Van Nam Giap, Van Huy Tran, Duc-Hung Pham, and Shyh-Chour Huang. 2022. "A Novel Disturbance Rejection Method Based on Robust Sliding Mode Control for the Secure Communication of Chaos-Based System" Symmetry 14, no. 8: 1668. https://doi.org/10.3390/sym14081668
APA StyleNguyen, Q. D., Giap, V. N., Tran, V. H., Pham, D.-H., & Huang, S.-C. (2022). A Novel Disturbance Rejection Method Based on Robust Sliding Mode Control for the Secure Communication of Chaos-Based System. Symmetry, 14(8), 1668. https://doi.org/10.3390/sym14081668






