ShChain_3D-ResNet: Sharding Blockchain with 3D-Residual Network (3D-ResNet) Deep Learning Model for Classifying DDoS Attack in Software Defined Network
Abstract
:1. Introduction
- To suggest an Ouroboros Sharding technique for boosting the blockchain’s scalability. Shard numbers and sizes are determined based on application demands, allowing users to assign resources dynamically.
- To study the effectiveness, designers collaborate with just an IT order to implement an assessment in a genuine blockchain-based SDN environment. The outcomes of the experiments show how ShChain 3D-ResNet may fare better over comparable methodologies of categorization.
- The 3D-ResNet model enables the Efficient Attention Modules (EAM) such as EAM-S where S indicates spatial and EAM-T module where T indicates temporal is included. These EAMs learn attention weights for various channels in spatial aspect, as well as attention weights for multiple frames in temporal aspect whereby imposing symmetry constraints
2. Related Works
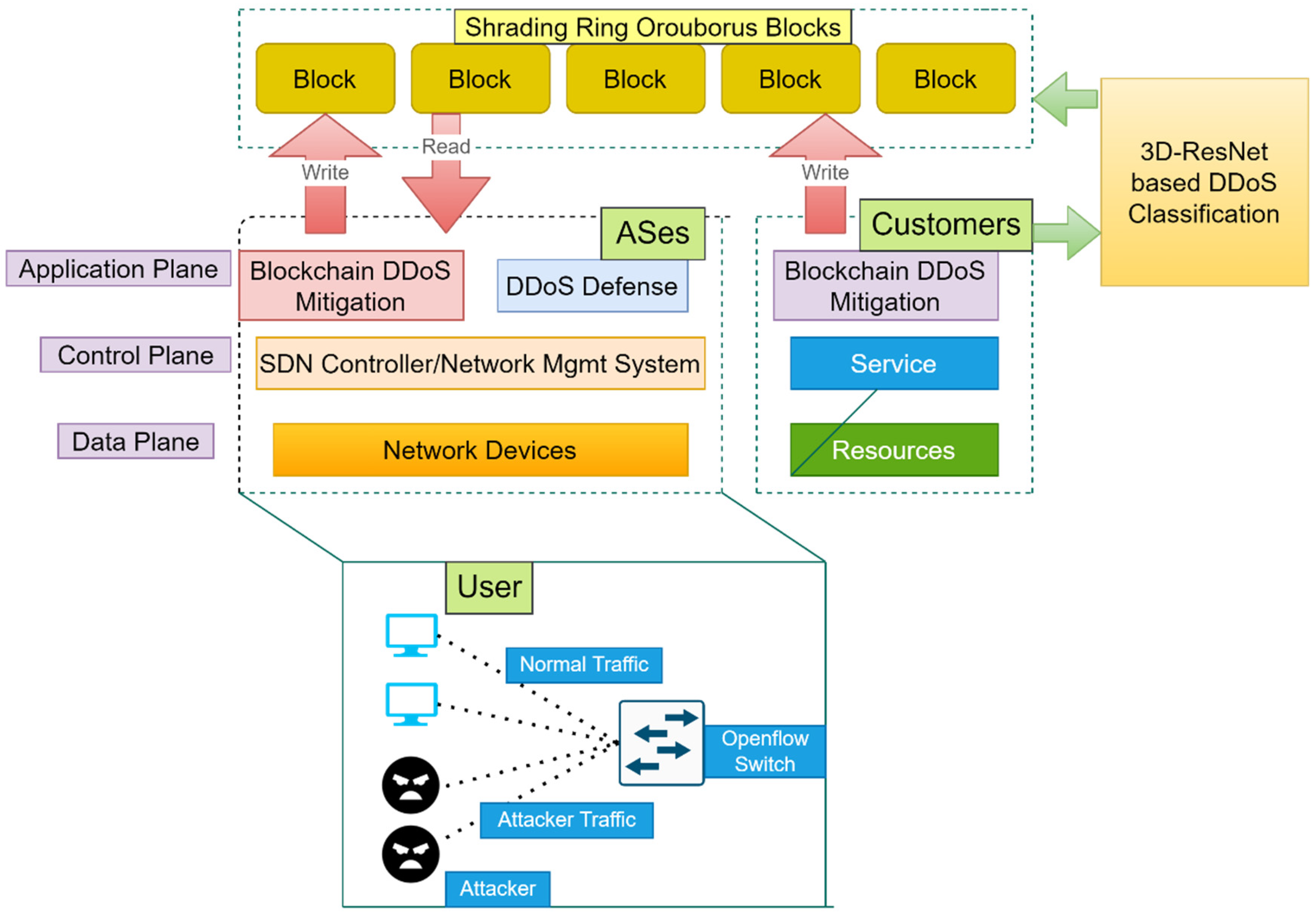
3. System Model
- Customers can use decentralized applications to submit white or blacklisted IPs to the Sharding ring ouroborusblockchain.
- ASes: can broadcast white or blacklisted IPs, get lists including the published Proxy servers, and use DDoS countermeasures.
- Blockchain/Smart Contract: the public Sharding ring ouroborusblockchain is powered by Structural rigidity smart contracts, including the logic for reporting IPs to the blockchain.
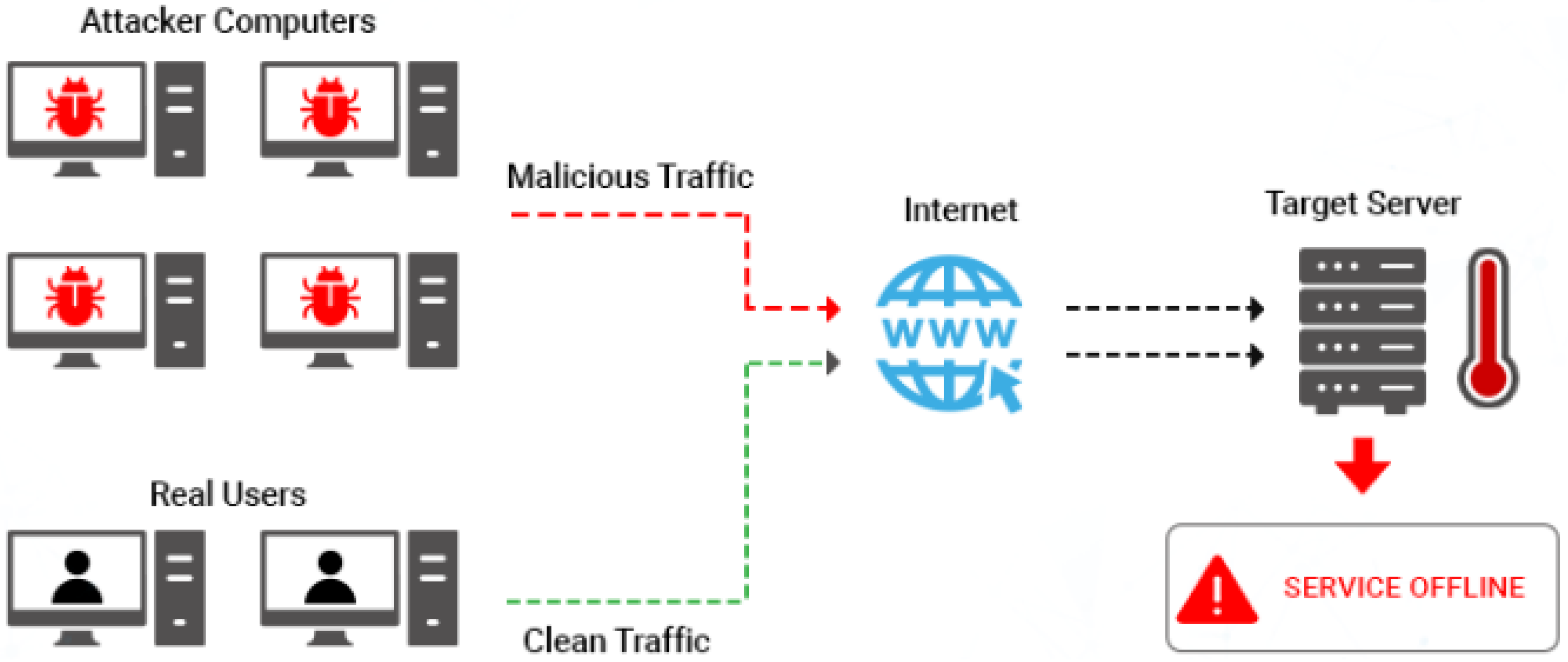
3.1. Threat Model:DDoS Attack
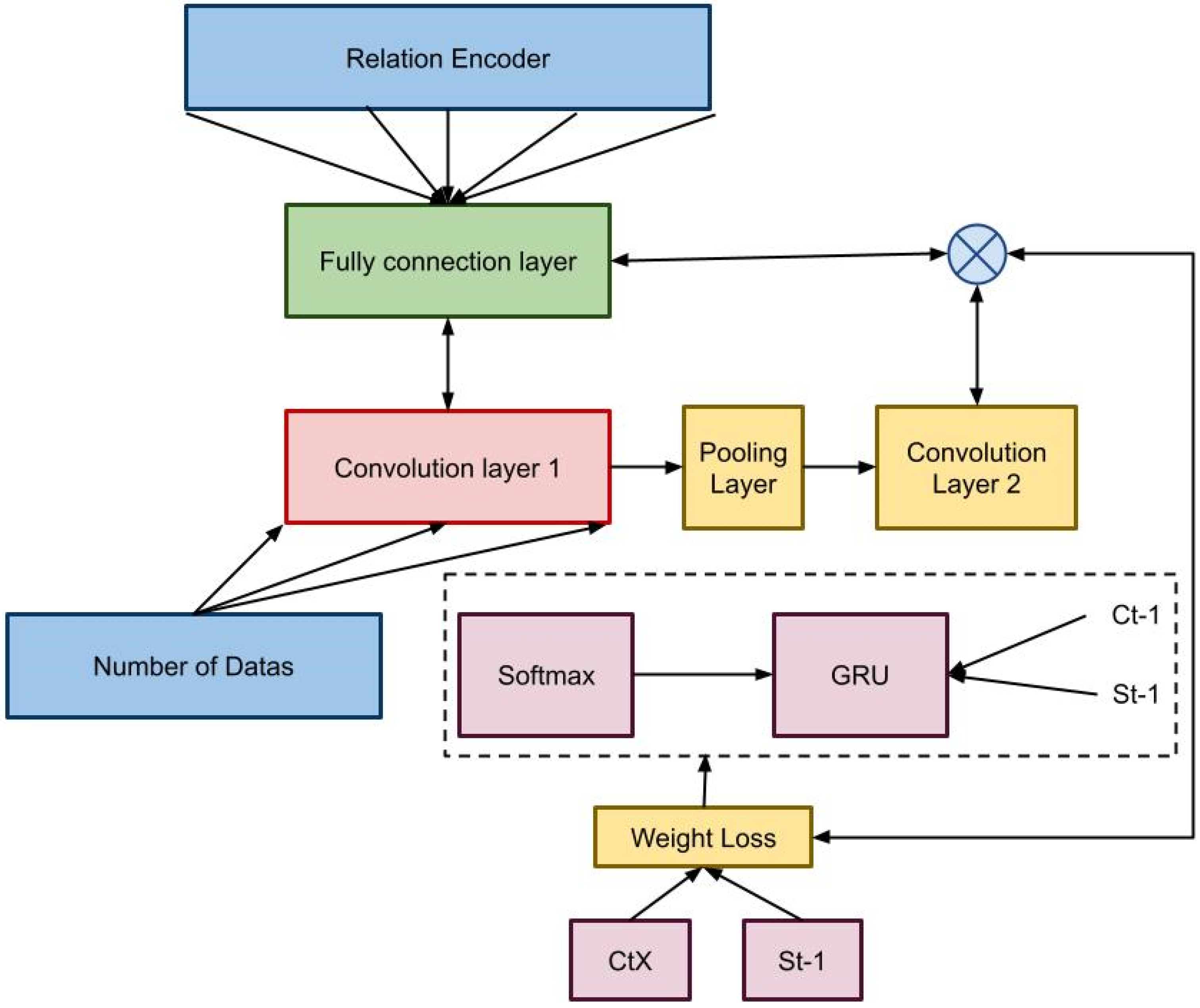
3.2. 3D ResNet Architecture for DDoS Attack Classification
3.3. Proposed Efficient Attention Module (EAM)
3.4. Dense Convolution Process
3.5. Reinforcement Layer
3.6. Detection of DDoS Attack Type
| Algorithm 1: DDoS Attack type Detection |
| 1: Input: Dataset (D), Attack types (A), weight matrix W, hidden layer element bias B, and visible layer element bias A |
| 2: Output: Categorized DoS attack |
| 3: for all k < D |
| 4: do |
| 5: initialize input-hidden weight matrix W |
| 6: Randomly initialize hidden biases B |
| 7: For k = 1 to N do |
| 8: for D = 1 to l do |
| 9: Update {Wi, Bi, Ni} |
| 10: End for |
| 11: End for |
| 12: Weight of class i |
| 13: wi = |
| 14: Update wi |
| 15: if wi = Bi then, DoS attack detected and categorize it |
| 16: if wi ≠ Bi then, no occurrence of attack |
3.7. Construction of Sharding Chain Structure for Privacy
- Query Mode (authenticity = TRUE): This is standard mode, which accepts input as well as returns output.
- Tracking Mode (authenticity = FALSE): When the block parameters of any block in network change, this mode is triggered. Any change in a parameter is propagated to hash of previous block. Block suspends general query business in this mode as well as attempts to identify compromised blocks.
4. Result and Discussion
4.1. Experimental Setup
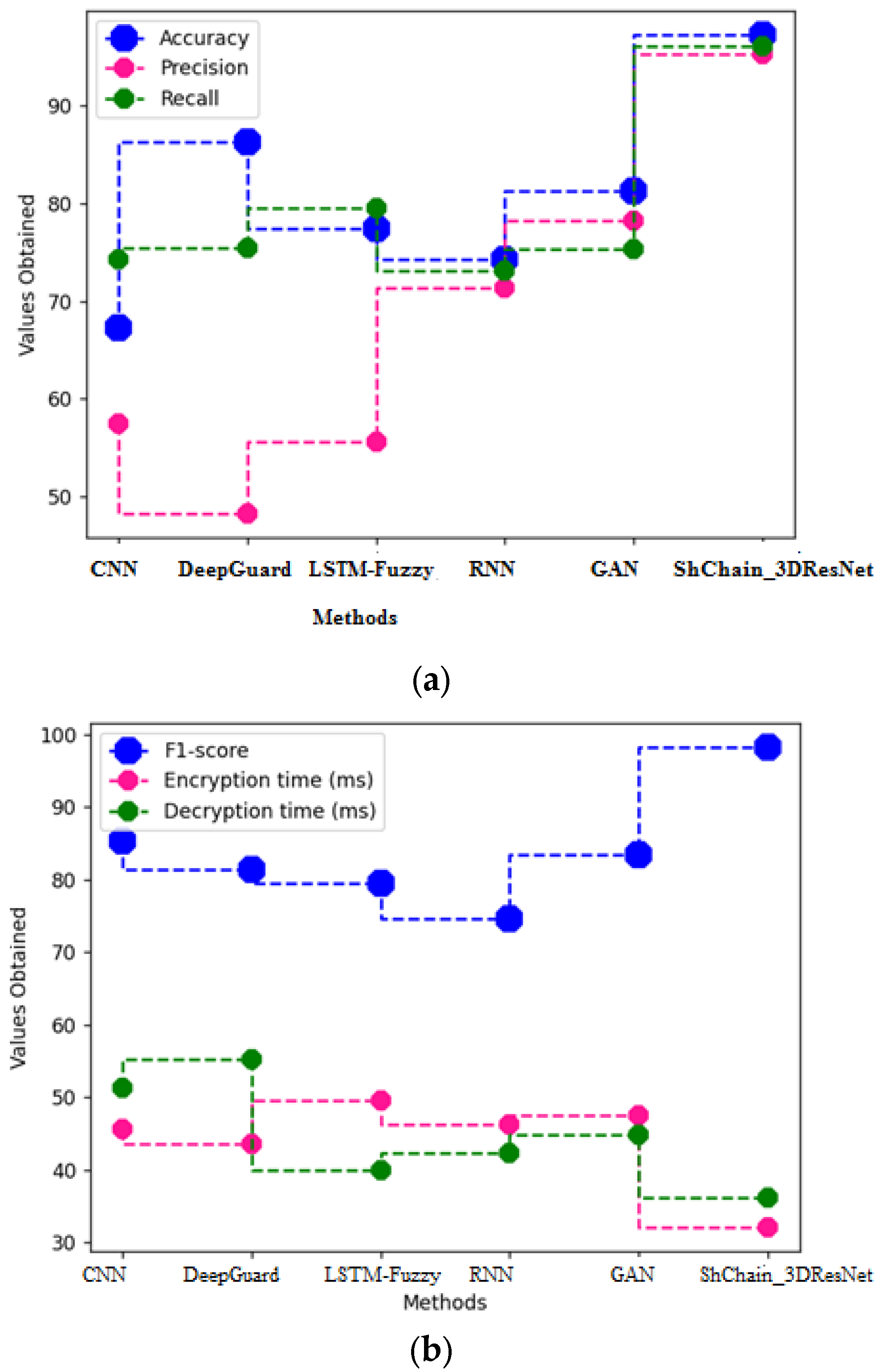
4.2. Comparative Analysis
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Al-Adaileh, M.A.; Anbar, M.; Chong, Y.W.; Al-Ani, A. Proposed statistical-based approach for detecting distribute denial of service against the controller of software defined network (SADDCS). In MATEC Web of Conferences; EDP Sciences: Les Ulis, France, 2018; Volume 218, p. 02012. [Google Scholar]
- Sanjeetha, R.; Srivastava, S.; Pokharna, R.; Shafiq, S.; Kanavalli, A. Mitigation of DDoS attack instigated by compromised switches on SDN controller by analyzing the flow rule request traffic. Int. J. Eng. Technol. 2018, 7, 46–49. [Google Scholar]
- Mladenov, B.; Iliev, G. Searching for optimal software defined network controller against dDoS attacks. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–4. [Google Scholar]
- Fenil, E.; Kumar, P.M. Towards a secure software defined network with adaptive mitigation of dDoS attacks by machine learning approaches. In Proceedings of the 2022 International Conference on Advances in Computing, Communication and Applied Informatics (ACCAI), Chennai, India, 28–29 January 2022; pp. 1–13. [Google Scholar]
- Zhao, Y.; Iannone, L.; Riguidel, M. On the performance of SDN controllers: A reality check. In Proceedings of the 2015 IEEE Conference on Network Function Virtualization and Software Defined Network (NFV-SDN), San Francisco, CA, USA, 18–21 November 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 79–85. [Google Scholar]
- Nanda, S.; Zafari, F.; DeCusatis, C.; Wedaa, E.; Yang, B. Predicting network attack patterns in SDN using machine learning approach. In Proceedings of the 2016 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Palo Alto, CA, USA, 7–10 November 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 167–172. [Google Scholar]
- Fenil, E.; Kumar, M.P. Survey on DDoSdefense mechanisms. Concurr. Comput. Pract. Exp. 2020, 32, e5114. [Google Scholar] [CrossRef]
- Gkountis, C.; Taha, M.; Lloret, J.; Kambourakis, G. Lightweight algorithm for protecting SDN controller against DDoS attacks. In Proceedings of the 2017 10th IFIP Wireless and Mobile Networking Conference (WMNC), Valencia, Spain, 25–27 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Dong, P.; Du, X.; Zhang, H.; Xu, T. A detection method for a novel DDoS attack against SDN controllers by vast new low-traffic flows. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–6. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.; Moschoyiannis, S.; Janicke, H. Deep learning for cyber security intrusion detection: Approaches, datasets, and comparative study. J. Inf. Secur. Appl. 2020, 50, 102419. [Google Scholar] [CrossRef]
- Bouras, C.; Kollia, A.; Papazois, A. SDN & NFV in 5G: Advancements and challenges. In Proceedings of the 2017 20th Conference on innovations in clouds, internet and networks (ICIN), Paris, France, 7–9 March 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 107–111. [Google Scholar]
- Tuor, A.; Kaplan, S.; Hutchinson, B.; Nichols, N.; Robinson, S. Deep learning for unsupervised insider threat detection in structured cybersecurity data streams. arXiv 2019, arXiv:1710.00811. [Google Scholar]
- Kobojek, P.; Saeed, K. Application of recurrent neural networks for user verification based on keystroke dynamics. J. Telecommun. Inf. Technol. 2020, 3, 80–90. [Google Scholar]
- Maimó, L.F.; Gómez, A.L.P.; Clemente, F.J.G.; Pérez, M.G. A self-adaptive deep learning-based system for anomaly detection in 5G networks. IEEE Access 2018, 6, 7700–7712. [Google Scholar] [CrossRef]
- Abdulhammed, R.; Faezipour, M.; Abuzneid, A.; AbuMallouh, A. Deep and machine learning approaches for anomaly-based intrusion detection of imbalanced network traffic. IEEE Sens. Lett. 2018, 3, 1–4. [Google Scholar] [CrossRef]
- Diro, A.A.; Chilamkurti, N. Leveraging LSTM Networks for Attack Detection in Fog-to-Things Communications. IEEE Commun. Mag. 2018, 56, 124–130. [Google Scholar] [CrossRef]
- He, Y.; Mendis, G.J.; Wei, J. Real-time detection of false data injection attacks in smart grid: A deep learning-based intelligent mechanism. IEEE Trans. Smart Grid 2017, 8, 2505–2516. [Google Scholar] [CrossRef]
- Rybnik, M.; Panasiuk, P.; Saeed, K.; Rogowski, M. Advances in the keystroke dynamics: The practical impact of database quality. In Computer Information Systems and Industrial Management; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7564, pp. 203–214. [Google Scholar]
- Cox, J.A.; James, C.D.; Aimone, J.B. A signal processing approach for cyber data classification with deep neural networks. Procedia Comput. Sci. 2015, 61, 349–354. [Google Scholar] [CrossRef] [Green Version]
- Lotfollahi, M.; Shirali, R.; Siavoshani, M.J.; Saberian, M. Deep Packet: A Novel Approach for Encrypted Traffic Classification Using Deep Learning. arXiv 2017, arXiv:1709.02656. [Google Scholar] [CrossRef] [Green Version]
- Sharma, P.K.; Singh, S.; Jeong, Y.-S.; Park, J.H. DistBlockNet: A distributed blockchains-based secure SDN architecture for IoT networks. IEEE Commun. Mag. 2017, 55, 78–85. [Google Scholar] [CrossRef]
- Steichen, M.; Hommes, S.; State, R. ChainGuard—A firewall for blockchain applications using SDN with OpenFlow. In Proceedings of the International Conference on Principles, Systems and Applications of IP Telecommunications (IPTComm), Chicago, IL, USA; 2017; pp. 1–8. [Google Scholar]
- Haider, S.; Akhunzada, A.; Mustafa, I.; Patel, T.B.; Fernandez, A.; Choo, K.K.R.; Iqbal, J. A deep CNN ensemble framework for efficient DDoS attack detection in software defined networks. IEEE Access 2020, 8, 53972–53983. [Google Scholar] [CrossRef]
- Phan, T.V.; Nguyen, T.G.; Dao, N.N.; Huong, T.T.; Thanh, N.H.; Bauschert, T. DeepGuard: Efficient anomaly detection in SDN with fine-grained traffic flow monitoring. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1349–1362. [Google Scholar] [CrossRef]
- Novaes, M.P.; Carvalho, L.F.; Lloret, J.; Proenca, M.L. Long short-term memory and fuzzy logic for anomaly detection and mitigation in software-defined network environment. IEEE Access 2020, 8, 83765–83781. [Google Scholar] [CrossRef]
- Polat, H.; Türkoğlu, M.; Polat, O.; Şengür, A. A novel approach for accurate detection of the DDoS attacks in SDN-based SCADA systems based on deep recurrent neural networks. Expert Syst. Appl. 2022, 197, 116748. [Google Scholar] [CrossRef]
- Novaes, M.P.; Carvalho, L.F.; Lloret, J.; Proença, M.L., Jr. Adversarial Deep Learning approach detection and defense against DDoS attacks in SDN environments. Future Gener. Comput. Syst. 2021, 125, 156–167. [Google Scholar] [CrossRef]
- Leipzig Intrusion Detection Dataset. Available online: https://www.exploids.de/lid-ds/ (accessed on 18 April 2020).
- WEKA Tool. Available online: https://www.cs.waikato.ac.nz/ml/weka/ (accessed on 1 February 2020).
- Nguyen, C.T.; Hoang, D.T.; Nguyen, D.N.; Dutkiewicz, E. MetaChain: A Novel Blockchain-based Framework for Metaverse Applications. arXiv 2021, arXiv:2201.00759. [Google Scholar]


| Author Year | Proposed Method | Merits | Demerits |
|---|---|---|---|
| Tuor et al., (2019) [12] | unsupervised DL network | It can detect attacks in early stages | Overload the controller |
| Kobojek et al., (2020) [13] | 1D CNN | Low false positive and false negative | Only handle on type of DDoS attack |
| Maimó et al., (2018) [14] | unsupervised stack auto encoder | Effectively protect the controller from attack | Delay when handling enormous number of incoming packets |
| Abdulhammed et al., (2018) [15] | autoencoder | Able to distinguish attack traffic from legitimate traffic | Only handles low traffic rate and threshold is fixed |
| Diro et al., (2018) [16] | LSTM | Low false positive | Less accuracy |
| He et al., (2017) [17] | CNN | Traces attack score reduces workload on controller in early stage | Works after controller received traffic flow which leads to flooding of packets |
| Kobojek et al., (2016) [18] | autoencoder-based classifier | Reduce overload between controller and switches | Unable to separate the legitimate user |
| Lotfollahi et al., (2017) [20] | RNNs mixed with MLP | Able to distinguish the attack from flash crowd | Overload the controller |
| Cox et al., (2015) [19] | RNN | Reduces controller overhead | Delay in DDoS attack detection |
| Sharma et al., (2017) [21] | DistBlockNet | Quick reaction in detecting DDoS attack | Unable to deal with complex traffic flow in the switch |
| Steichen et al., (2017) [22] | ChainGuard | Reduces resource consumption | Requires high computing resources and processing power of SDN controller |
| Haide et al., (2020) [23] | convolutional neural network (CNN) | High detection ratio on DDoS attack | Less accuracy |
| Phan et al., (2020) [24] | DeepGuard | Prompt, versatile, and accurate detection of DDoS attack | High resource consumption on controller |
| Novaes et al., (2020) [25] | LSTM-FUZZY | Limits false positive and false negative rate | Does not care about the temporal characteristic in order to accelerate detection process |
| Polat et al., (2022) [26] | Recurrent Neural Network (RNN) | Reduces congestion of incoming packets at controller | Need time to detect the attack |
| Novaes et al., (2021) [27] | Generative Adversarial Network (GAN) | Increased detection accuracy | Difficult to detect unknown or new types of DDoS attack |
| Notations | Expansion |
|---|---|
| Hashj | Hash of jth block |
| Pubi | public key of ith block |
| Privi | private key of ith block |
| AESi | AES key of ith block |
| wi | weigh |
| bi | bias |
| acti | activation function |
| Methods | Accuracy | Precision | Recall | F1-Score | Encryption Time (ms) | Decryption Time (ms) |
|---|---|---|---|---|---|---|
| CNN | 67.4 | 73.5 | 43.5 | 48.3 | 56.3 | 82.7 |
| DeepGuard | 58.2 | 77.5 | 56.4 | 35.2 | 77.8 | 85.1 |
| LSTM-Fuzzy | 83.4 | 63.2 | 71.3 | 46.2 | 73.2 | 89 |
| RNN | 76.2 | 58.3 | 65.2 | 78.1 | 56.2 | 73.5 |
| GAN | 84.1 | 82.4 | 69 | 46.2 | 77.2 | 77.1 |
| ShChain_3D-ResNet | 95.6 | 97.3 | 95.2 | 94.4 | 32.5 | 35.2 |
| Methods | Accuracy | Precision | Recall | F1-Score | Encryption Time (ms) | Decryption Time (ms) |
|---|---|---|---|---|---|---|
| CNN | 67.2 | 57.4 | 74.3 | 85.3 | 45.6 | 51.3 |
| DeepGuard | 86.3 | 48.2 | 75.4 | 81.4 | 43.6 | 55.2 |
| LSTM-Fuzzy | 77.4 | 55.6 | 79.5 | 79.5 | 49.6 | 40 |
| RNN | 74.3 | 71.4 | 73.1 | 74.6 | 46.3 | 42.3 |
| GAN | 81.3 | 78.3 | 75.3 | 83.4 | 47.5 | 44.9 |
| ShChain_3D-ResNet | 97.3 | 95.3 | 96.1 | 98.2 | 32.1 | 36.2 |
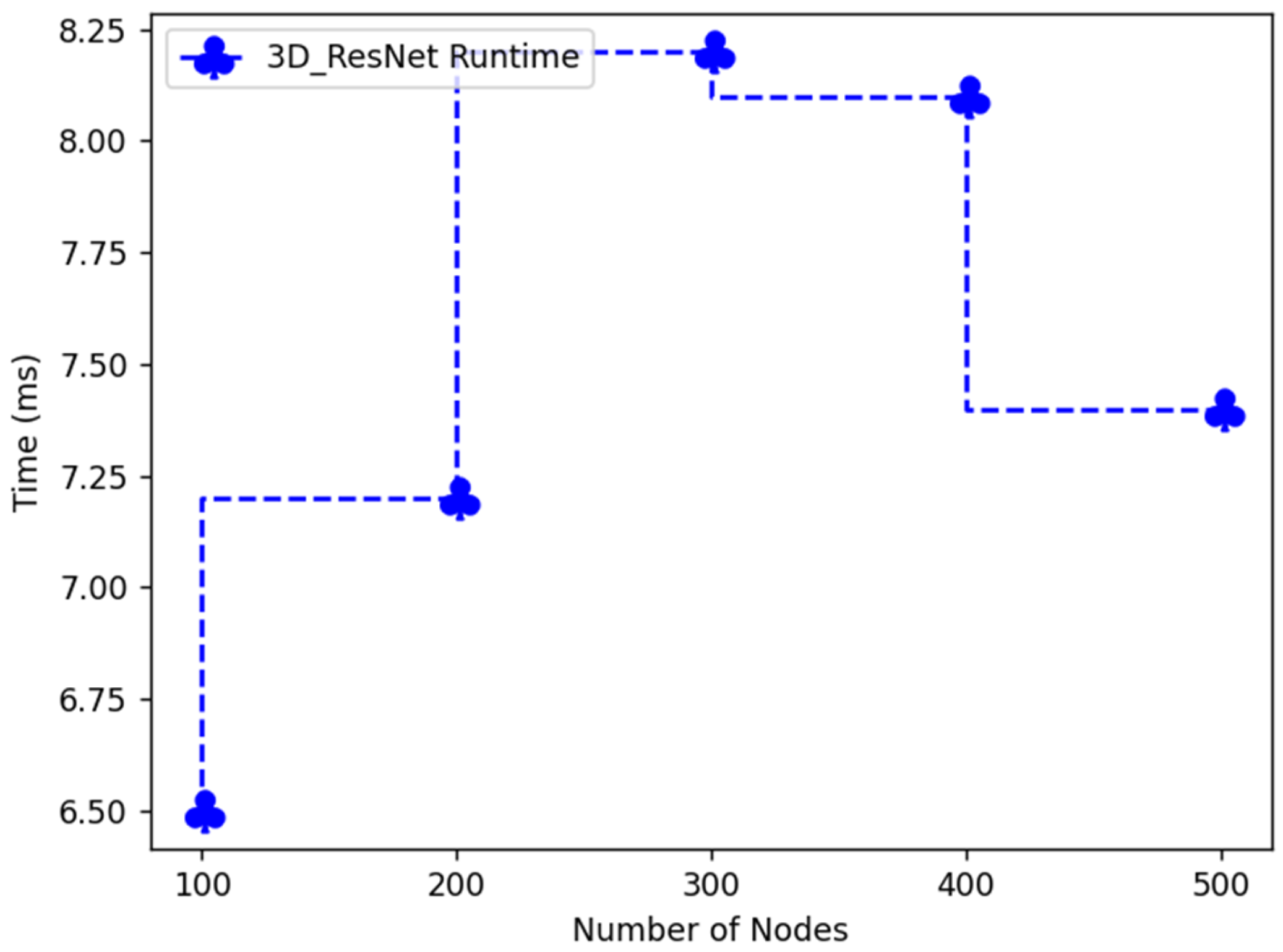
| Number of Nodes | 3D-ResNet Runtime |
|---|---|
| 100 | 6.5 |
| 200 | 7.2 |
| 300 | 8.2 |
| 400 | 8.1 |
| 500 | 7.4 |
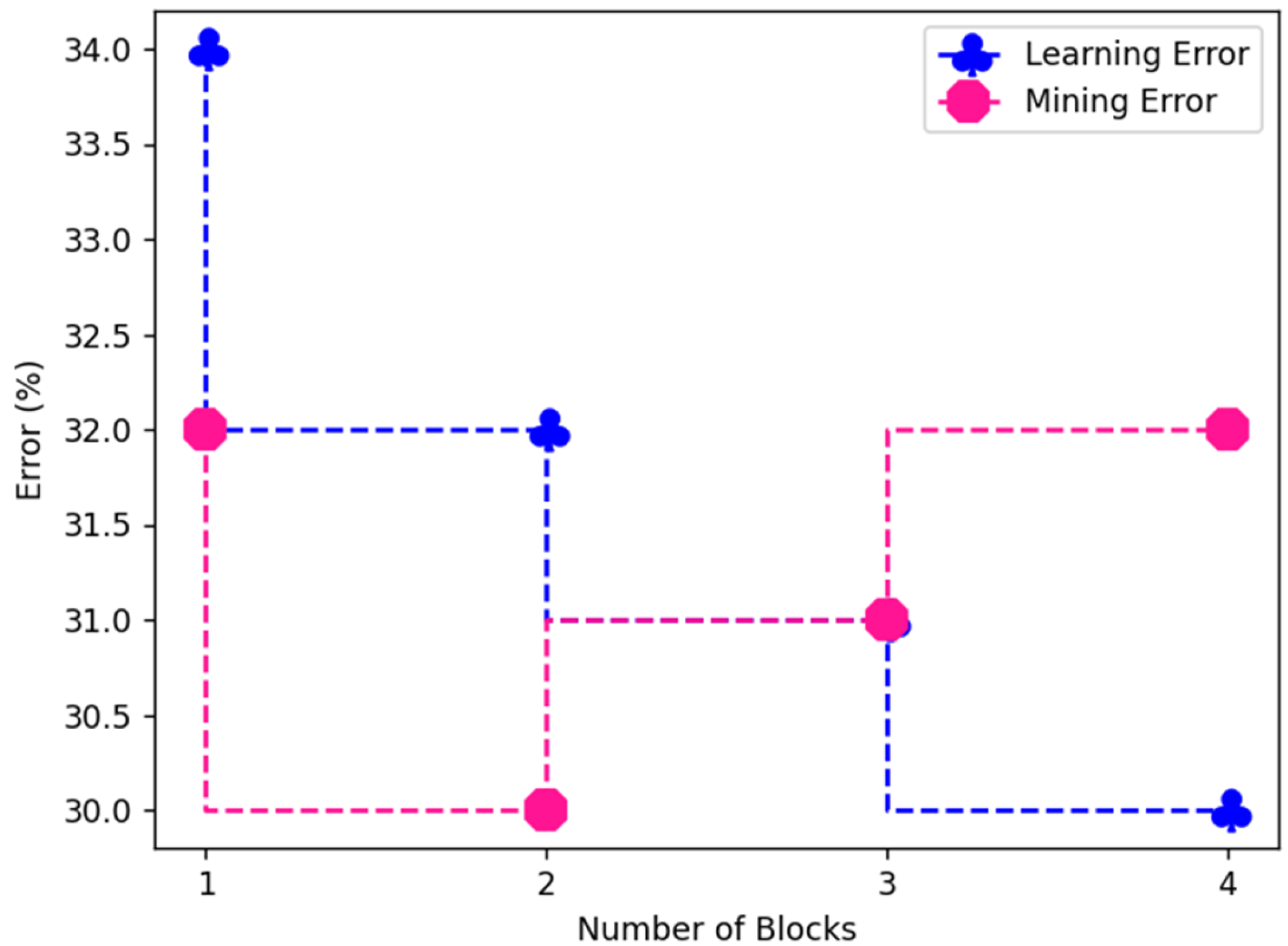
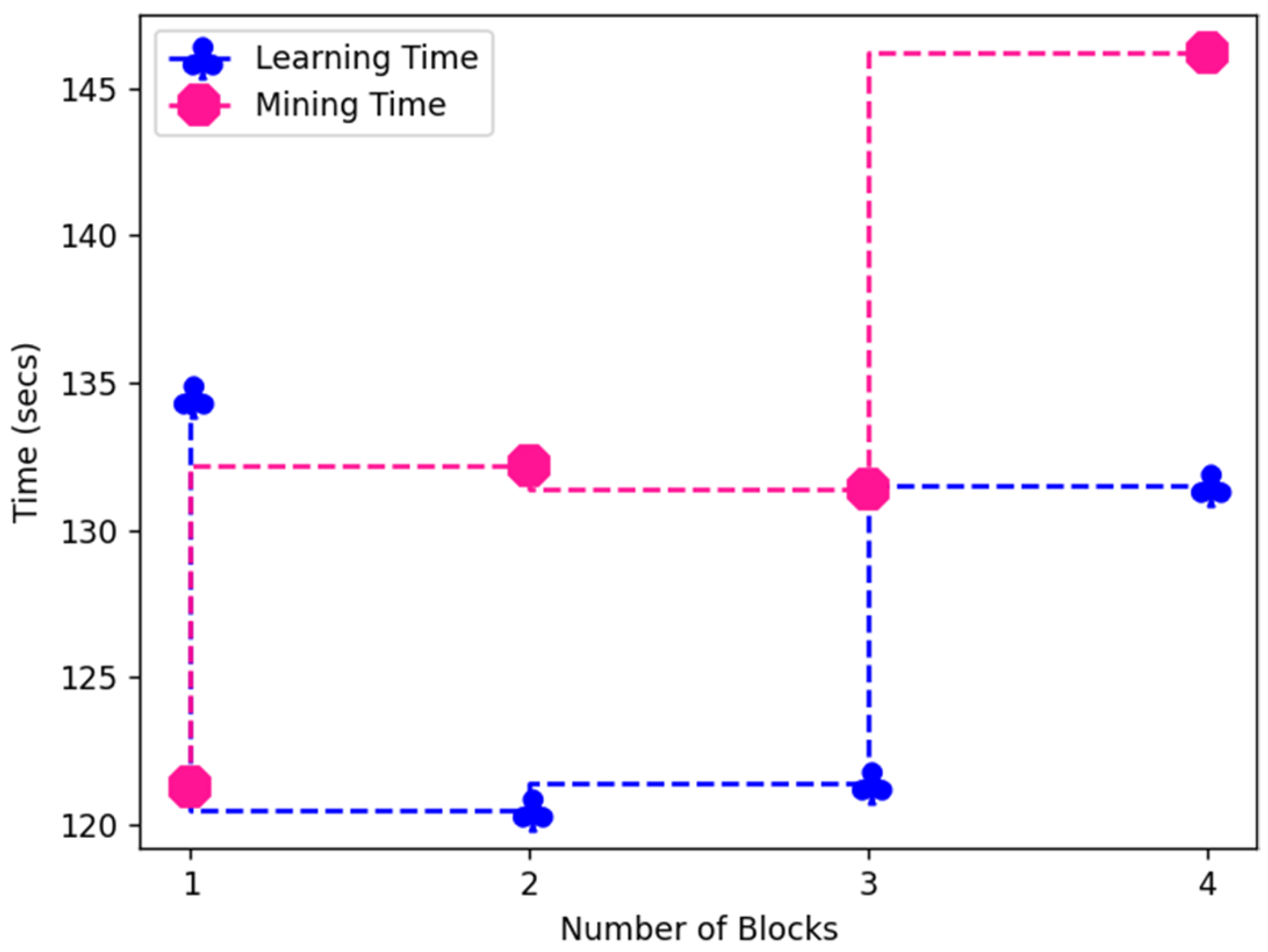
| Number of Blocks | Learning Iteration | Learning Time (s) | Learning Error | Mining Iteration | Mining Time | Mining Error |
|---|---|---|---|---|---|---|
| 1 | 245.2 | 134.5 | 34% | 34.5 | 121.31 | 32% |
| 2 | 192.1 | 120.5 | 32% | 32.1 | 132.2 | 30% |
| 3 | 170.3 | 121.4 | 31% | 38.3 | 131.4 | 31% |
| 4 | 165.3 | 131.5 | 30% | 36.2 | 146.2 | 32% |
| Number of Neurons | Mining Iteration | Mining Time | Mean ± Standard Deviation | Mining Threshold |
|---|---|---|---|---|
| 60-4-60 | 34.5 | 121.31 | 34.3 ± 32.4 | 145 |
| 124-4-60 | 32.1 | 132.2 | 34.2 ± 35.6 | 150 |
| 188-4-60 | 38.3 | 131.4 | 32.5 ± 36.7 | 165 |
| 252-4-60 | 36.2 | 146.2 | 32.5 ± 35.7 | 170 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fenil, E.; Mohan Kumar, P. ShChain_3D-ResNet: Sharding Blockchain with 3D-Residual Network (3D-ResNet) Deep Learning Model for Classifying DDoS Attack in Software Defined Network. Symmetry 2022, 14, 1254. https://doi.org/10.3390/sym14061254
Fenil E, Mohan Kumar P. ShChain_3D-ResNet: Sharding Blockchain with 3D-Residual Network (3D-ResNet) Deep Learning Model for Classifying DDoS Attack in Software Defined Network. Symmetry. 2022; 14(6):1254. https://doi.org/10.3390/sym14061254
Chicago/Turabian StyleFenil, E., and P. Mohan Kumar. 2022. "ShChain_3D-ResNet: Sharding Blockchain with 3D-Residual Network (3D-ResNet) Deep Learning Model for Classifying DDoS Attack in Software Defined Network" Symmetry 14, no. 6: 1254. https://doi.org/10.3390/sym14061254
APA StyleFenil, E., & Mohan Kumar, P. (2022). ShChain_3D-ResNet: Sharding Blockchain with 3D-Residual Network (3D-ResNet) Deep Learning Model for Classifying DDoS Attack in Software Defined Network. Symmetry, 14(6), 1254. https://doi.org/10.3390/sym14061254






