1. Introduction
Let be a real Hilbert space with inner product and its induced norm . In this paper, we present an iterative method to the equilibrium problem over the intersection of fixed-point set:
Problem 1 (BEP). Let , , be cutters with , and let be a bifunction satisfying for all . Then, our objective is to find a point such thatwhere denotes the set of fixed points of . The equilibrium problem, which was first introduced by Fan [
1], includes many problems as particular cases, for example, the fixed-point problem, the variational inequality, the optimization problem, the saddle point problem, the Nash equilibrium problem in non-cooperative games, and others; see, for instance, [
2,
3,
4,
5] and references therein.
The equilibrium problems over the fixed-point set have been considered in many articles; see, for instance, [
6,
7,
8,
9,
10] and references therein. The computational algorithms for solving these kinds of problems have been studied and developed by using the idea of the methods for equilibrium problems and the iterative schemes for fixed-point problems. In particular, Iiduka and Yamada [
6] considered the equilibrium problems over the fixed-point set of a firmly nonexpansive mapping and presented a subgradient-type method for solving the considered problems. They showed the convergence of their method and applied the method to the Nash equilibrium problems. After that, the equilibrium problems over the common fixed-point of nonexpansive mappings were considered by Duc and Muu in [
7]. They proposed the splitting algorithm, which was updated based on the idea of the classical gradient method and the Krasnosel’skii–Mann method and presented the strong convergence of the presented algorithm. Recently, Thuy and Hai [
8] considered the bilevel equilibrium problems and proposed the projected subgradient algorithm to solve the considered problem. They exhibited the strong convergence of the proposed method and applied it to the equilibrium problems over the fixed-point set of a nonexpansive mapping. We notice that the aforementioned literature is considered in the case of the equilibrium problems over the fixed-point set of nonexpansive mappings.
Let us focus on the constrained set of
BEP. Now, let
,
, be cutter operators. The common fixed-point problem is to find a point
The well-known methods of finding a point that belongs to the intersection of fixed-point sets are initially motivated by the cyclic projection method, which was introduced by Kaczmarz [
11]. After that, the convergence of cyclic projection-type methods are investigated in several directions and their convergence results are guaranteed under the operators’ assumptions, such as cutters or nonexpansive operators, see [
12,
13,
14,
15,
16] and references therein. In particular, Bauschke and Combettes [
17] proposed the cyclic cutter method and showed a weak convergence of the proposed method. In [
18], Cegielski and Censor presented the extrapolated cyclic cutter method, which is an acceleration of the cyclic cutter method by imposing an appropriate step-size function to the method. Indeed, let
,
, be cutters with
, we define the step-size function
as follows:
where the operator
T,
and
are defined as
It was shown that the extrapolated cyclic cutter method weakly converges provided that the cutter operators
satisfied the demi-closedness principle for all
. Note that, for some practical problem, the value of the extrapolation function may be huge, which lead to some numerical instabilities. To keep away from these instabilities, Cegielski and Nimana [
19] proposed the modified extrapolated subgradient projection method for solving the convex feasibility problem, which is a particular situation of common fixed-point problem, and established the convergence of the proposed method as well as demonstrated the performance of the method by the numerical results. After that, the authors in [
20] also utilized the idea of the extrapolated cyclic cutter method for dealing with the variational inequality problem with common fixed-point constraints. It can be noted that from [
19,
20], the iterative methods with extrapolated cyclic cutter terms achieve not only some numerical superiorities to utilizing the classical cyclic cutter scheme but also guarantee the boundedness of the generated sequence, see [
20] for further discussions.
In this paper, we propose an iterative algorithm called the Subgradient-type extrapolation cyclic method for solving the equilibrium problems over the intersection of fixed-point sets of cutter operators. The proposed algorithm can be considered as a combination of the subgradient iterative scheme for equilibrium problems in [
8] and the extrapolated cyclic cutter method for the intersection of fixed-point sets of cutter operators in [
18]. Using the cutter operators and assumptions, we investigate the convergence of the presented algorithm. Moreover, we also present a numerical result of our presented method to illustrate the efficiency of the method.
This paper is organized as follows. In
Section 2, we recall some definitions and tools which are needed for our convergence work. In
Section 3, we present the
subgradient-type extrapolation cyclic method for finding the solution of
BEP. We subsequently present the convergence result in this section. In
Section 4, the efficacy of the subgradient-type extrapolation cyclic method is illustrated by numerical experiments of the solving equilibrium problem governed by the positive definite symmetric matrices over the common fixed-point set. Finally, we give some concluding remarks in
Section 5.
2. Preliminaries
In section, we collect some basic definitions, properties, and useful tools for our work. The readers can consult the books [
16,
21] for more details.
We denote by the identity operator on a real Hilbert space . For a sequence , the strong and weak convergences of a sequence to a point are defined by the expression and , respectively.
In what follows, we recall some definitions and properties of the operator that will be referred to in our analysis.
Definition 1 ([
16]).
Let be an operator having a fixed point. The operator T is called- (i)
quasi-nonexpansive, iffor all and - (ii)
η-strongly quasi-nonexpansive, if there exists ,for all and , - (iii)
cutter, iffor all and
Lemma 1 [
16] (Remark 2.1.31 and Theorem 2.1.39)
. Let be an operator having a fixed point. Then the following statements are equivalent:- (i)
T is cutter.
- (i)
for all and for all .
- (ii)
T is 1-strongly quasi-nonexpansive.
Definition 2 [
16] (Definition 3.2.6)
. Let be an operator having a fixed point. The operator T is said to satisfy the demi-closedness (DC) principle if for every sequence , and , we have . Definition 3 [
16] (Definition 2.1.2)
. Let be an operator and be given. We define the relaxation of the operator T byand we call λ a relaxation parameter. Next, we recall the definition of a generalization of relaxation of an operator.
Definition 4 [
16] (Definition 2.4.1)
. Let be an operator, and . We define the operator byThis operator T is called a generalized relaxation of the operator T, the value λ is called a relaxation parameter and the function σ is called a step-size function. The operator is called an extrapolation of if the function for every .
We notice that, if
, for every
, then
. Note that
. Then, for every
, the following relations hold
and for any
, we have
Next, we provide an important lemma of the step-size function for proving the convergence result.
Lemma 2 [
16] (Section 4.10)
. Let be cutters with and denote the operator T, and as in (2). Let the function be given by (1). Then the following statements are true:- (i)
For every , it is true that - (ii)
The operator is a cutter.
Now, we recall a notion and some properties of a diagonal subdifferential which will be used in this work.
A function
is said to be subdifferentiable at
if there exists a vector
such that
The vector w is called a subgradient of the function h at . The collection of all such vectors constitute the subdifferential of h at and is denoted by
Let
be a bifunction which is convex in the second argument, that is, the function
is convex at
x, for all
Then, the set of all subgradient of
at
x is called the diagonal subdifferential and is denoted by
. The reader can find the notion of the diagonal subdifferential in [
22], for more detail.
We end this section by recalling some technical lemmas that are important tools in proving our convergence result.
Lemma 3 [
23] (Lemma 3.1)
. Let and be sequences of nonnegative real numbers such thatIf , then exists. Lemma 4 [
24] (Lemma 3.1)
. Let be a sequence of real numbers such that there exists a subsequence of with for all . If, for all , we definethen the following hold:- (i)
is non-decreasing.
- (ii)
.
- (iii)
and for every .
3. Algorithm and Its Convergence Result
In this section, we firstly propose the subgradient-type extrapolation cyclic method for solving BEP. Subsequently, we present useful lemmas and prove the main convergence theorem.
Remark 1. - (i)
When the number and , Algorithm 1 becomes Algorithm 2 considered in [8]. Moreover, it is worth noting that the class of operator considered in this work is different from [8]. In fact, we consider the cutter property of , whereas the nonexpansiveness of T is assumed in [8]. - (ii)
If the function , Algorithm 1 is reduced towhere for all . In the case when for all , this scheme is related to the extrapolated cyclic cutter proposed by [18]. Moreover, this scheme is also related to the work of Cegielski and Nimana [19] for solving a convex feasibility problem when the operator is omitted in their paper.
The following assumption relating to the convergence of Algorithm 1 is assumed throughout this work.
| Algorithm 1: Subgradient-type extrapolation cyclic method |
Initialization: Given the positive real sequences and . Choose and arbitrarily. Step 1. For given , compute the step size as
Step 2. Update the next iterate as
Put and go to Step 1. |
Assumption A1. Assume that
- (A1)
The bifunction f is ρ-strongly monotone on , that is, there exists a constant satisfying - (A2)
For each , the function is convex, subdifferentiable and lower semicontinuous on .
- (A3)
The function is bounded on a bounded subset of .
- (A4)
The sequences and satisfy , , , and .
Remark 2. - (i)
If the whole space is finite dimensional, the assumption that, for all , the function is subdifferentiable and weakly lower semicontinuous in (A2) can be omitted. This is because, in the finite dimensional setting, the convexity implies the continuity of a function.
- (ii)
The convexity of the function implies that the lower semicontinuity is equivalent to the weak lower semicontinuity of the function for all .
- (iii)
If the whole space is finite dimensional, by invoking the assumption (A2), we have the diagonal subdifferential is nonempty for all . Moreover, in this case, the assumption (A3) can be omitted, see [21] (Proposition 16.20). - (iv)
An example of the corresponding step-size sequences in (A4) is the positive real sequences and given bywhere and with and . In fact, since and , we have and then . Furthermore, since , we have . We note that . Moreover, we have that .
The following lemma states the important relation of the generated iterates.
Lemma 5. Let be the sequence generated by Algorithm 1. Then, for every and , it holds that Proof. Let
be fixed. Now, let us note that
By using the properties of
in (
3), Lemma 1 and Lemma 2, we note that
Finally, by utilizing the fact that
, we obtain
as desired. □
The following lemma guarantees the boundedness of the constructed sequence .
Lemma 6. The sequence generated by Algorithm 1 is bounded.
Proof. Let
and
be fixed. Let us notice that
which together with Lemma 5 yields
Now, we set
for all
. Thus, the relation (
4) can be rewritten as
To show that the sequence is bounded, we will consider the proof in two cases:
Case I: Suppose that there exists such that the sequence is nonincreasing for all . Then, we obtain that for all , which means that the sequence is bounded and, subsequently, is also a bounded sequence.
Case II: Suppose that there exists a subsequence
of
such that
for all
, and let
be given in Lemma 4. This yields, for every
, that
and
Invoking the relation (
6) in the inequaluty (
5) and the positivity of the sequences
,
and
, we obtain that
On the other hand, by using the definition of
and the fact that
, we get
This together with the inequality (
8) yields that
Now, it follows from the
-strong monotonicity of
f that
On the other hand, for a fixed
, we have
which together with the inequality (
9) implies that
and so
This means that the sequence
is bounded. Now, since
it follows that
is bounded above. Thus, by using (
7), we get that
is bounded and hence
is also bounded. This completes the proof. □
The following lemma provides some important boundedness properties of the sequences and .
Lemma 7. The sequences and are bounded.
Proof. Let
and
be fixed. Now, let note that
where the first inequality holds true by (
3) and the last one holds true by the fact that
is a cutter and consequently a quasi-nonexpansive operator.
As , we have from Assumption (A3) and the boundedness of that the sequence is bounded which implies the sequence is also bounded. Consequently, from the definition of the sequence , it can be seen that is also bounded. □
Now, we are in a position to present our main theorem.
Theorem 1. Let be the sequence generated by Algorithm 1. Suppose that Assumption A1 is satisfied and the operators , , satisfy the DC principle. Then the sequence converges strongly to the unique solution ofBEP.
Proof. Let
be the unique solution of
BEP. Firstly, we note from Lemma 5 with replacing
that
For simplicity, we denote
for all
. Then the inequality (
10) is nothing else than
To obtain the strong convergence of the generated sequence, we investigate the proof in two cases based on the behavior of the sequence .
Case I: Suppose that there is
such that
for every
. Thus, by using the definition of
, we note that
By utilizing Lemma 3 and the fact that
, we obtain that the sequence
is convergent and
Now, as
, we get that
As the sequence
is bounded, we have that, for all
,
On the other hand, we note from Lemma 5 and the fact that
, for all
, that
By summing up this relation and the condition that
, we obtain
Now, since the sequence
is bounded, there is a real number
such that
for all
. This together with the assumption
implies that
Next, we show that
Suppose to the contrary that there exist
and
such that
for all
. Then,
which leads to a contradiction. Thus, we obtain
From the
-strongly monotonicity of
f, it follows that
By taking the inferior limit, we have
Combining this and the inequality (
15), we have
Since the sequence
is bounded, there exist a weakly cluster point
and a subsequence
of
such that
. We note from (
12) that
Thus, by using the DC principle of
, we have that
Furthermore, since
and it holds that
which imply that
Moreover, we note that
By utilizing the DC principle of , we have
By processing the similar argument as above, we acquire that for all and hence .
In virtue of the weak lower semicontinuity of
, we obtain
Combining the inequality (
16) and (
17), we have
From the existence of
, we can conclude that
Case II: Suppose that there exists a subsequence
of
such that
for all
. By Lemma 4, there exists a sequence of indices
such that, for all
,
and
By using the inequalities (
11) and (
18), we have
By using the definition of
and the fact that
, we get
which implies that
Now, using the
-strongly monotonicity of
f that
and for a fixed
such that
we obtain
By using the boundedness of
and
, we obtain
On the other hand, by using the
-strongly monotonicity of
f and the inequality (
21), we have
By means of the fact that
in (
20), it follows that
Combining this and the above inequality, we obtain
By taking the superior limit, we have
As the sequence
is bounded, there exist a weakly cluster point
and a subsequence
of
such that
. By following the argument as used in
Case I together with the fact (
22) and the DC principle of each
, we obtain that, for any subsequence
of
,
.
By using the weak lower semicontinuity of
, we obtain
It follows from the inequality (
23) that
Note that from the definition of
and using the fact that
, we have
Combining this and using the triangle inequality, we have
By using the inequality (
24) and the fact that
, we obtain
Next, using the inequality (
19) and the fact that
, we have
Finally, by using the inequality (
25), and the fact
, we obtain
This completes the proof. □
Remark 3. The DC principle assumption, which is assumed in the Theorem 1 holds true when the operators , , are nonexpansive. Actually, the metric projection onto closed convex sets and the subgradient projections of a continuous convex function, which is Lipschitz continuous on every bounded subset also satisfy the DC principle, see [16] further details. Remark 4. It can be noted that the convergence result obtained in Theorem 1 holds true without any boundedness assumption of the generated sequence as in the previous works, for instance [20]. This underlines the convergence improvements accomplished in this work. 4. A Numerical Example
In this section, we present a numerical example for solving the equilibrium problem over a finite number of half-space constraints. Let
be
matrices,
, and
be given for all
, we consider the following equilibrium problem: find a point
such that
where the constrained set is
We consider the operator
in two cases. In the first case, we put
to be the subgradient projection defined by
where
with the distance function is given by
. In the second case, we put
, the metric projection onto
, for all
. Note that it is known that the operators
and
are cutters and satisfy the DC principle with
. We consider positive definite symmetric matrices
A and
B defined by
,
, where the
matrices
are randomly generated in
, and
is the identity
matrix. Note that the bifunction
is strongly monotone on
, and for fixed
, we have
is convex on
. Moreover, we note that the diagonal subdifferential
, and we also know that the function
is bounded on a bounded subset of
. These mean that the assumptions (A1)–(A3) are now satisfied. In this case, the problem (
27) is the particular case of Problem 1 so that the sequence generated by Algorithm 1 can be applied to solve the problem.
We consider behavior of the sequence
generated by Algorithm 1 for various positive real sequences
and
in the forms of Remark 3. We choose
, and generate a vector
in
by uniformly distributed random generating between
and a scalar
, for all
. We choose the starting point of Algorithm 1 to be a vector whose coordinates are one. We terminate Algorithm 1 by the stopping criterions
In the first experiment, we fix the parameters
and
. We perform 10 independent tests for any collections of parameters
, and
and
, and
when utilizing the operator
and
and the results are presented respectively in
Table 1 and
Table 2, where the average number of iterations and the average computational runtime for any collection of
and
are presented.
In
Table 1, we presented the number of iterations (
k) (Iter), the computational time (Time) in seconds when the stopping criteria of Algorithm 1 was met. Note that the larger
requires a larger number of iterations and computational runtime. Furthermore, the best choice of the involved parameters for both cases is
and
.
In a similar fashion with
Table 1, we also presented in
Table 2 the number of iterations (
k) (Iter), the computational time (Time) in seconds, when the stopping criterions of Algorithm 1 when using the operator
was met. The experimented results are in the same direction with
Table 1 where the best choice of the involved parameters for both cases is
and
.
In the next experiment, we consider the influence of parameters
a and
b by fixing the best parameters
and
. We performed 10 independent tests for any collections of parameters
,
,
,
,
,
to
and
,
,
,
,
,
,
, and
when utilizing the operator
and
and the results of the average number of iterations and the average computational runtime for any collection of
a and
b are presented in
Table 3 and
Table 4, respectively. We omit the combinations that do not satisfy the assumption in Theorem 1 and label it by -.
In
Table 3, we see that the numbers of iterations as well as computational running time decrease when the value
a increases. The the best result is obtained for the combination of
and
.
In the same direction as the results in
Table 3, it can be seen from
Table 4 that the numbers of iterations and the computational running time is decreases when the values
a grow up. The the best result is acquired for the combination of
and
.
From these all above experiment, we observe that the choice of corresponding parameters , , and yields the best performance of both considered cases.
In the next experiment, we consider the behavior of Algorithm 1 for various values
n and
m by fixing the corresponding parameters as the above best choice. We also terminate Algorithm 1 when the error tolerance
was met, and the results are presented in
Table 5.
It is observed from
Table 5 that for the values
, and 500, the using of the subgradient projection is more efficient than using the metric projection in the sense that the first one requires less computation than the second one in the average number of iterations for all values
m. In the case of
, we observe that there is no difference on these two cases. One notable behavior is that for each value
n, we observe that even if the value
m increases, the average numbers of iterations are almost the same, whereas the average computational runtime is increasing.
Finally, we present the comparison of the use of the subgradient projection and the metric projection for various optimality tolerances
. We set
and
and choose the corresponding parameters in the same manner as above, the average numbers of iterations with respect to the optimality tolerances are presented in
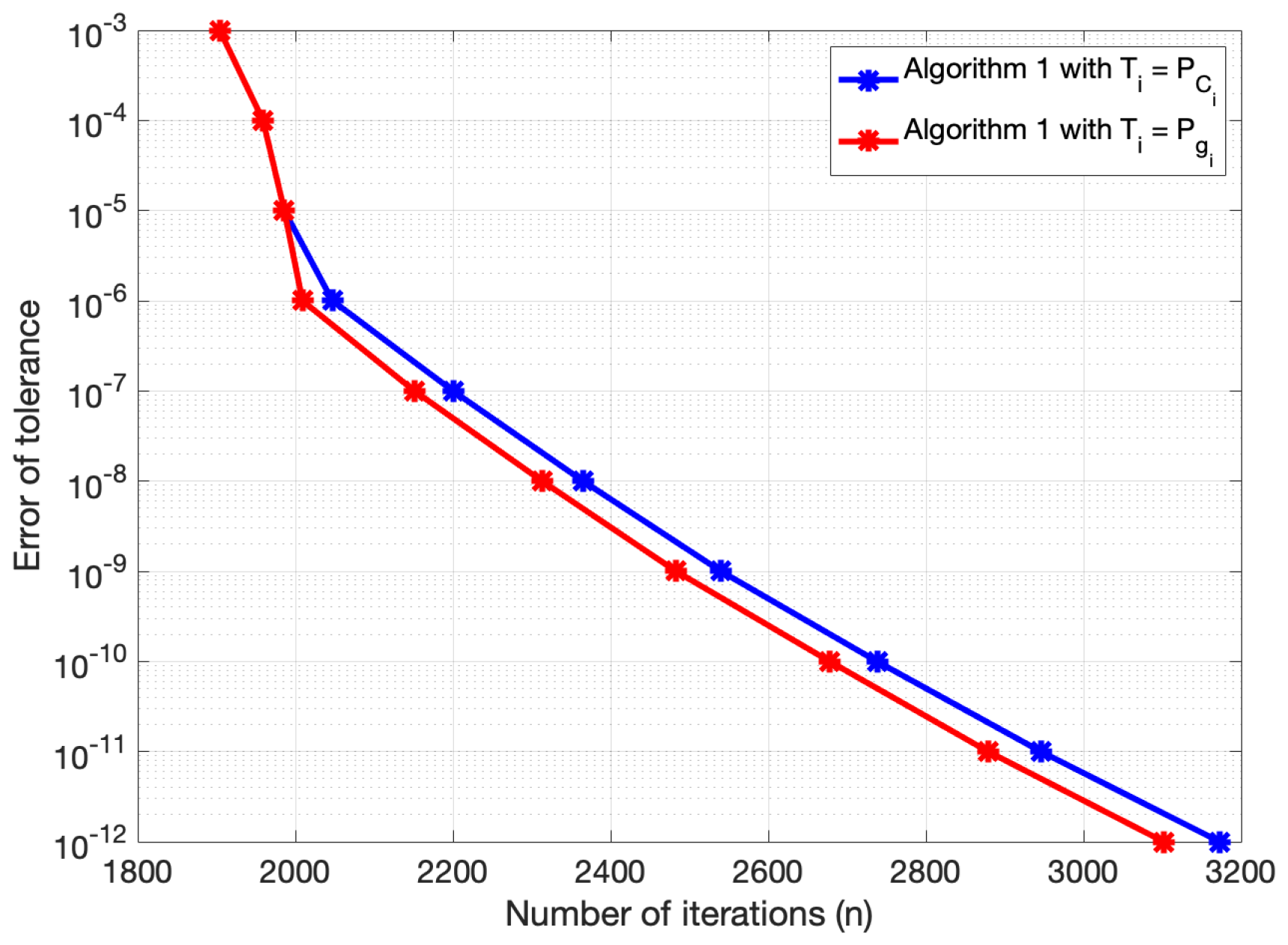
Figure 1.
The plots in
Figure 1 show that using the subgradient projection is more efficient than the metric projection for all the optimality tolerances. This emphasizes the superiority of using the subgradient projection when performing Algorithm 1.