Dynamic Load Balancing Techniques in the IoT: A Review
Abstract
1. Introduction
- It considers the recent LB techniques in IoT.
- It provides a classification of LB mechanisms.
- It presents the advantages and disadvantages of the LB algorithms in each class.
- It outlines future research directions to improve the LB algorithms.
2. IoT Architectures
2.1. The Three-Tier IoT Architecture
- −
- Perception Layer: This layer contains sensing hardware, scalar or multimedia sensors, and actuators. These devices sense, acquire, and preprocess data from the physical environment. They often send the environmental data to the centralized servers through gateways using various access network technologies. A variety of environmental sensors can be deployed in the monitoring area. Sensors create a network topology in the structure of self-organizing and multiple hops. This network system contains sensor nodes, sink nodes, and management nodes that perform monitoring tasks (initiated by the end-users). The captured data are transmitted through sink nodes by multi-hop. However, the network topology often changes because a few nodes are more prone to failure due to energy consumption and environmental impact. The needless links must be detached by energy control and backbone node selection to achieve an efficient network topology for data forwarding and, thus, ensure network connectivity and coverage.
- −
- Network Layer: This layer constructs an efficient network topology for data forwarding. It decides on the power-efficient optimum route to transmit the data to the IoT servers, devices, and applications via the Internet. Various networks, such as WiFi, Ethernet, 3G, Long-Term Evolution (LTE), and 5G, can be used. The Access Network sublayer interconnects various devices and applications through interfaces or gateways using numerous communication protocols. The networking models (included in this layer) can provide high data transmission capacity for nodes. For example, they can transmit the data to the cloud server through sink nodes, super nodes, and other relay units. High data transmission capacity is often required to forward the big data to cloud servers. In addition, self-organizing routing protocols can be used to enhance the robustness of networking models.
- −
- Application Layer: This layer contains various IoT applications, such as WiFi applications, wireless sensor network (WSN) applications, and vehicular network applications. WiFi networks support different protocols and have been widely adopted in homes, cities, and healthcare systems. Users can control the smart devices which connect to WiFi networks. A vehicular network application can monitor emergency traffic events and make traffic predictions on the basis of real-time traffic data. A WSN application can monitor environmental data such as humidity and temperature. The application layer consists of two sublayers: (1) the service sublayer, and (2) the application sublayer. The service sublayer provides data analytics, information management, data mining, and decision-making services. The application sublayer provides the required IoT services to the end users or machines. It delivers the services demanded by clients. Furthermore, this layer can offer decent QoS and quality of experience (QoE) to satisfy the client’s needs.
2.2. Middleware-Based IoT Architecture
2.3. The 5-Tier IoT Architecture
- −
- Things Abstraction Layer: This layer transfers data generated from the perception layer to the service management layer via some safe channels. Such data transfer can be achieved via technologies such as 3G/4G, GSM, WiFi, and RFID. Many advanced computing paradigms and functionalities, such as cloud computing (CC) and edge computing (EC), and data managing procedures can be implemented in the things abstraction layer [3]. For example, the CC paradigm can be implemented in this layer to enable large-scale IoT systems to handle massive amounts of data with increasing heterogeneity levels [29]. Cloud servers have powerful analytical computing capacity and data storage capabilities. They can also make decisions on the basis of analytical results. Smarter decision making is feasible using effective cloud computing. A cloud server can flawlessly implement communication for heterogeneous systems. Compared to middleware, CC has better heterogeneity capacity in IoT because of its powerful data analytical feature. Fog computing (or ‘clouds at the edge’) is a technology that allocates services near the devices to improve the QoS. It is a geographically distributed paradigm that complements CC to provide services. Fog computing (FC) can also be incorporated into the things abstraction layer. The fog system can extend storing and computing to the edge of the network. This can solve the difficulty of service computing in delay-sensitive IoT applications and enable location awareness as well as mobility support [30]. FC operates on ‘instant data’, i.e., real-time data generated by sensors or users.Generally, IoT intelligence can be offered at three levels: (1) in CC infrastructures, (2) in edge/fog nodes, and (3) in IoT software-defined networking (SDN) devices [31]. The need for intelligent control and decision at each level depends on the time sensitivity of the IoT application. For instance, a camera on an autonomous car must detect obstacles in real-time to prevent accidents. This quick decision making is impossible by transferring data instances from the vehicle to the cloud and returning the predictions back to the vehicle. Instead, all the operations should be performed locally in the vehicle. Such a real-time IoT scenario cannot be implemented within a cloud-based IoT environment.
- −
- The Service Management Layer: This layer is mainly accountable for order handling, grievance handling, and billing. Furthermore, this layer is responsible for providing interaction among services and service providers [32].
- −
- The Business Layer: This layer suggests the management of IoT services and system actions. Furthermore, this layer can assist in building charts, graphs, models, etc., using the incoming data from the Application Layer [3].
3. Computing and Networking Paradigms Adopted in IoT Environments
3.1. The Cloud Computing Paradigm
LB in a Cloud-Based Network Environment
3.2. The SDN Paradigm
LB in the Software-Defined IoT
3.3. The Edge Computing Paradigm
3.4. The Fog Computing Paradigm
Task Offloading in the Fog and EC Paradigms
3.5. Performance Evaluation Metrics for LB Schemes
4. Related Surveys
4.1. LB in CC
- Resource availability whenever required.
- Efficient resource utilization during less and heavy load.
- Controlled power consumption.
- Reduction in resource utilization cost [69].
4.2. LB in Software-Defined IoT
- A deterministic approach always produces the same output for specific input. Differential equations often describe its processes. Furthermore, the output of the model is completely specified by the values of the parameters and the primary situations. Deterministic approaches have used both distributed controllers and centralized controllers. Migration and rerouting are deterministic approaches that can reduce response time and overhead. They can also improve the system throughput and the degree of LB. However, these approaches may generate unacceptable energy consumption, unacceptable latency, unacceptable packet loss, and low availability. The determinist LB schemes do not evaluate many QoS parameters.
- Non-deterministic approaches: LB is an NP-complete problem and can be solved using a nondeterministic approach that can find a solution to the NP-complete problem in polynomial time. A nondeterministic LB approach may have different behaviors on different runs for the same input. It is often applied to acquire approximate solutions when an exact solution is difficult (or costly) to acquire using a deterministic algorithm. These approaches use various methods such as greedy, metaheuristic, approximation, genetic algorithm, multi-objective particle swarm, and particle swarm. These methods can improve utilization and the degree of LB. Moreover, latency can be reduced. However, these approaches have high computational time and can generate unacceptable energy consumption, throughput, packet loss, and overhead. Notably, non-determinist LB schemes need to consider all the LB metrics.
4.3. LB in the IoT Environment
- Mechanisms utilizing objective function and routing parameters to improve the load balance procedure.
- Studies (in the concerned area) based on heuristic schemes.
4.4. LB in Heterogeneous (IoT/Fog/Edge) Environment
5. Dynamic LB Techniques in IoT
5.1. Classification of Load-Balancing Techniques
5.2. Load-Balancing Policies for CC, EC, and FC
- Task Selection Policy: This policy identifies and selects the tasks that should be moved from one node to another. Such selection is based on the time needed to complete the task, the number of nonlocal system calls, and the amount of overhead required for migration.
- Location Policy: With this policy, tasks are transferred to underutilized (or free) computing nodes so they can process them. This policy selects the destination node via one of the three accessible methods (randomness, negotiation, and probing) and assesses the availability of necessary services for task transfer. The location policy selects the destination at random and transfers the task in the random approach. The destination is chosen by a node querying other system nodes in the probing strategy. The negotiation strategy involves nodes negotiating LB with one another.
- The Transfer Policy: This policy describes the conditions under which tasks must be transferred from one local node to another local or remote node. To determine the tasks that need to be transferred, two approaches, ‘all current tasks’ and ‘latest received task’, are used. In the ‘last received task’ approach, the task that arrives last is transferred once all incoming tasks have entered the transfer policy. Depending on the workload of each node, a transfer policy, based on a rule, determines whether a task has to migrate (task migration) or be processed locally (task rescheduling) in all existing task methods.
- Information Policy: This dynamic LB policy maintains all resource information in the system so that other policies can use it when making choices. It selects when to gather information. Agent, broadcasting, and centralized polling are three different techniques for gathering data from the nodes. In the broadcasting method, every node broadcasts its data, making it available to other nodes. Nodes now gather information using the agent approach. The demand-driven policy, periodic policy, and state change-driven policy are some examples of information policies.
5.3. The Function-as-a-Service(FaaS) Paradigm
- Cloud functions are short-lived; each function usually only requires tiny inputs and delivers outputs after a brief period of time, making them simple to automate (for example, they can be easily auto-scaled).
- A cloud function lacks operational logic since all operational concerns are transferred to the platform layer (operational and cloud-managed), enabling platform independence for the cloud function.
- A cloud function has no regard for the context in which it is employed.
5.4. Dynamic LB Techniques in the Cloud
5.4.1. General LB Schemes
5.4.2. Natural Phenomenon-based LB Schemes
- −
- Swarm Algorithms: In the case of ACO-based scheduling mechanisms, the workloads are depicted via ants. Pheromone intensity can denote the knowledge of commonly used resources and the load on each available resource. Moreover, the required critical resources in a cloud setup, i.e., VMs, can be depicted by food sources. In the case of ABC-based cloud scheduling schemes, the workloads can be demonstrated via each ABC. A beehive can be depicted as a cloud setup (environment), and VMs can be understandable as food sources. If we map the analogy of finding food for bees with cloud scheduling, this analogy can be analogous to workload scheduling on VMs in the cloud. However, assessing superior food sources can be explained as discovering and evaluating the underloaded VMs in the cloud to which all the newly arrived workloads can be scheduled. Then, PSO is adapted and mapped to handle scheduling issues in clouds. Especially in the case of PSO-based scheduling mechanisms, the number of workloads can be explained as the viewpoint of the potential solution. Εach position can be depicted as a collection of candidate VMs analogous to the scheduling procedure [151].
- −
- Evolutionary algorithms: The chromosomes play an essential role when dealing with GA-based mechanisms. A chromosome consists of a sequence of genes that depicts a possible solution. In such a mechanism, a basic factor, called fitness function, is utilized to verify whether the available chromosome is appropriate for the environment or not. Furthermore, concerning the fitness value, best-suited chromosomes are identified. Afterward, complex mutation and crossover computations are accomplished, generating more probable solutions (offspring), further creating a new population. However, the suitability of newly created possible solutions (offspring) is further verified via the fitness function in such a mechanism. This process continues until an ample number of probable solutions is found. In GA-based scheduling mechanisms, the workloads (scheduled on VMs) are depicted via the offspring computation process [151].
- −
- Swarm and Evolutionary Algorithms-based Load Scheduling and Balancing Schemes: Many authors explored and revealed interesting insights into smart swarm algorithms such as ACO. By utilizing the notion of ACO, Tawfeek et al. [152] showed that the considered adapts well and suggests improved performance compared to the GA notion suggested by Dasgupta et al. [153]. Nonetheless, ACO suffers from the issue of high network overhead, and it may fall into the local optimum as revealed by Farrag et al. [154]. Considering ACO as a nature-inspired scheme, Tawfeek et al. [152] considered makespan minimization as the objective function. Their suggested mechanism utilizes a random optimization exploration method to allocate and manage the arrival workloads on VMs. Nevertheless, this technique does not address the fault tolerance factor in the system.
5.4.3. Agent-Based LB Schemes
5.4.4. Task-Based LB Schemes
5.4.5. Cluster-Based LB Schemes
5.5. Dynamic LB in Fog Computing
5.5.1. Approximate Algorithms
- −
- Heuristic algorithms: These algorithms are born entirely from ‘experience’ with a particular optimization problem and aim to find the best solution to the problem in optimal time through ‘trial and error’. Solutions in heuristic approaches may not be the best or optimal, but they can be much better than a well-informed deduction. A heuristic approach uses the details of the problem. An exact approach takes substantial time to get the optimal solution. Thus, a heuristic approach is preferable to get a near-optimal solution in the optimal time. Existing heuristic methods include hill climbing [208], Min-conflicts [209], and the analytic hierarchy process (AHP) [210].
- −
- Metaheuristic Algorithms: A metaheuristic method is a higher-level heuristic method. It is a problem-independent method that can be practical for a wide range of problems. Any recent metaheuristic method has a diversification element and an intensification element. A balance is required between diversification and intensification to gain an influential and effective metaheuristic method. A metaheuristic method examines the entire solution space; a dissimilar set of solutions should be created. Moreover, the search must be heightened close to the neighborhood of the optimal or near-optimal solutions. Some metaheuristic algorithms include particle swarm optimization (PSO) [214,215,216], the fireworks algorithm [217], the bat algorithm [218], the whale optimization algorithm [219], and hybrid metaheuristics [220]. He et al. [214] proposed the fog and software-defined network (SDN). They introduced an SDN-based modified constrained optimization PSO approach for the adequate usage of the SDN and cloud/fog architecture on the Internet of vehicles. Wan et al. [215] proposed an energy-aware LB and scheduling solution based on the fog network. The authors provided an energy consumption model on the fog node that was related to the workload. Then, an optimization function was developed to balance the workload on the manufacturing cluster. The manufacturing cluster had to be prioritized as they used an upgraded PSO method to arrive at a good solution and complete tasks. Baburao et al. [216] proposed a resource allocation strategy based on PSO-based LB in a fog environment. Shi et al. [217] suggested a cloud-based mobile facial recognition architecture based on fog and the SDN architecture to solve the delay problem. In addition, they formulated LB in SDN and fog/cloud systems as an optimization problem. To solve the LB problem, they proposed the use of the fireworks algorithm (FWA) based on centralized SDN controls. Yang [218] proposed a three-layered architecture based on a fog/cloud network and big medical data. Their architecture contained the cloud, fog, and medical devices. In this architecture, their LB strategy used the bat algorithm to execute the initial setup of bat population data, which enhanced the quality of the solution in the initial sample. Malik et al. [219] proposed a fog-based framework that balances the load among fog nodes for handling the communication and processing requirements of intelligent real-time applications for patients. To provide better services to patients, they proposed an efficient cluster-based LB algorithm at the fog layer which consisted of fog nodes with various VMs. These VMs were grouped in line with their storage, functionality, computation capability, and specifications. These VMs together with the VM manager constituted a cluster. Such clustering assisted in the rapid allocation of tasks and reduced latency time. Concerning LB, Karthik and Kavithamani [220] proposed a whale optimization algorithm in a microgrid-connected wireless sensor network and fog settings. Moreover, Qun and Arefzadeh [221] introduced an LB method using a hybrid metaheuristic algorithm in fog-based vehicular ad hoc networks.
- −
5.5.2. Exact Algorithms
5.5.3. Fundamental Algorithms
5.5.4. Hybrid Algorithms
5.5.5. LB for Distributing Incoming Traffic across a Cluster of Brokers
- BROKER: An MQTT broker is a logical entity that couples publishers and subscribers. It is responsible for exchanging messages between the other participants. Widespread MQTT brokers are Mosquitto, Active-MQ, Hivemq, Bevywise, and VerneMQ. For example, HiveMQ [263] is a Java-based MQTT broker that supports MQTT 3.x and MQTT 5. Eclipse Mosquitto [264] is an open-source message broker that implements the MQTT protocol versions 5.0, 3.1.1, and 3.1. Mosquitto is lightweight and is suitable for use on all devices from low-power single-board computers to full servers.
- PUBLISHERs. These are the elements that send data to the broker so that it sends the data to one or more subscribers that require it.
- SUBSCRIBERs. These are the elements that receive data from the broker. The data they receive are the data sent by publishers.
5.5.6. LB Solutions for Multipath Communication in IoT
6. Lessons Learnt
- There is no perfect LB technique for improving overall LB metrics. For example, some techniques account for response time, resource utilization, and migration time, while others ignore these metrics and account for others. However, some metrics appear to be mutually exclusive, e.g., depending on VM migrations, LB can lead to longer response times. Service cost is another metric that is not taken into account. Therefore, it is highly advantageous to introduce a comprehensive LB technique for improving as many metrics as possible.
- In some situations, cloud providers need to send part of their workload to another cloud provider for LB processing. In short, using resources from multiple cloud providers is a key requirement for future LB. In this case, cloud providers face the problem of data lock-in. Our survey shows that very few articles addressed these issues. Therefore, another interesting area for future research might be to study the issue of data lock-in and cross-cloud services.
- Even though fog computing is a hot research topic, most researchers do not yet have access to a real testbed. It was discovered that the majority of the articles employed simulator-based tools for their evaluations. Implementing the stated algorithms in the real testbed is quite difficult since the outcomes of scenarios such as scheduling in the real environment can differ from those in the simulated environment.
- Some LB methods on FC need to be able to operate on massive scales (scalability). Some nodes, devices, and associated processes may not be guaranteed despite the small-scale validation of these approaches. Only a small number of works have addressed the scalability issue, despite its significance. Future research faces an open problem because the related publications were defined in small-scale contexts.
7. Open Research Issues
- Data prioritization: Many IoT multimedia applications use real-time delay-sensitive data that require data prioritization. Data prioritization can address several issues related to enhancing QoS, video streaming, scheduling, energy, memory, security, and reducing network latency, especially in information-centric networks [292].
- Traffic-aware load balancing: Through traffic identification and rerouting, an LB scheme can meet various QoS criteria by leveraging SDN’s ability to monitor and operate the network. The potential of SDN switches as an LB method in machine-to-machine (M2M) networks was examined in [293]. By utilizing the advantages of rapid traffic identification and dynamic traffic rerouting in SDN, they created a traffic-aware LB system to satisfy various QoS needs of M2M traffic. They focused on LB techniques for M2M networks. However, their plan can be used for IoT networks, where machines and people communicate via IP-based networks and send their data to the cloud. In this situation, SDN can help LB by implementing flow-based networking.
- Multi-objective optimization in LB decisions: There is no technique to define most QoS parameters for LB decisions in FC environments. For example, some algorithms consider only energy, cost, or response time and ignore parameters such as scalability, reliability, and security. Therefore, multi-objective optimization in LB decision making needs to be extended to consider some QoS parameters and tradeoffs between different parameters.
- Best solutions: Most fog-based LB techniques (scheduling and resource allocation) fall into the NP-hard and NP-complete problem complexity categories. Several metaheuristic and heuristic algorithms have been suggested to solve them. Future research should focus on other optimization methods such as the lion optimizer algorithm [294], firefly algorithm [295], simulated annealing [296], bacterial colony optimization [297], memetic [298,299], artificial immune system [300], and grey wolf optimizer [301].
- Context-aware computing: To balance the burden on fog nodes and IoT devices (which may be mobile), it is crucial to forecast where they will be in the future. Observing movement and activity patterns can help predict where nodes and devices will be in the future. LB systems can be enhanced with accessible contextual data and semantic assistance [302,303]. An exciting example of future trends is the development of LB methods for fog networks using context-aware computing.
- FC can enhance big data analytics: Decision-making and recommendation systems for various smart environments have been implemented using big data analytics. Fog computing can be utilized to satisfy the requirements for big data analysis in distributed network environments that include latency, mobility, scalability, and localization. Offloading computation and data storage to nearby fog nodes in the network can achieve these metrics [304,305]. Additionally, the QoS aspects of big data analytics can be enhanced by the application of LB methods. Thus, applying LB methods for fog contexts to big data analytics can be seen as an open issue for research.
- Interoperability: Fog nodes and sources are so diverse and dispersed. Thus, interoperability is a crucial success factor for LB in the IoT/fog context. Consumers often check for their favorites and other variables such as pricing and functionality because they do not want to employ just one service provider. They have the option to switch between IoT/fog-based solutions or to apply a combination of services and products to create smart LB-based IoT environments in a personalized manner due to interoperability [306]. Thus, a fascinating research direction is to consider interoperability as a crucial factor in combining the LB in IoT/fog-based services.
- Efficient load management in vehicular fog computing: To enable effective cooperation through vehicle-to-vehicle and vehicle-to-infrastructure communication, an IoT-enabled cluster of cars can offer a rich reservoir of computational resources. This is feasible in vehicular fog computing, in which cars act as fog nodes for the IoT and offer cloud-like services. Then, these services are further connected with the traditional cloud to help a group of users to cooperate and perform the tasks. The dynamic nature of the vehicular ad hoc network makes efficient load management in vehicular fog computing very challenging. Recently, Hameed et al. [307] provided a capacity-based LB approach with cluster support to carry out energy- and performance-aware vehicular fog distributed computing for effectively processing IoT tasks. Their research suggested a dynamic clustering method that forms clusters of vehicles as a function of their position, speed, and direction.
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| ABC | Artificial bee colony |
| ACO | Ant colony optimization |
| AMQP | Advanced message queuing protocol |
| AI | Artificial intelligence |
| CoAP | Constrained application protocol |
| CC | Cloud computing |
| cwnd | Congestion window |
| DL | Deep learning |
| DoDAG | Destination-oriented directed acyclic graph |
| DRL | Deep reinforcement learning |
| EC | Edge computing |
| EDCs | Edge data centers |
| FaaS | Function-as-a-service |
| FC | Fog computing |
| GA | Genetic algorithm |
| GSM | Global system for mobile communications |
| HVAC | Heating, ventilation, and air conditioning |
| IEEE | Institute of electrical and electronics engineers |
| IoT | Internet of things |
| IoMT | Internet of multimedia things |
| IP | Internet protocol |
| LAN | Local area network |
| LB | Load balancing |
| LPLN | Low power and lossy network |
| LTE | Long-term evolution |
| MAC | Medium access control |
| ML | Machine learning |
| MPTCP | MultiPath TCP |
| MQTT | Message queuing telemetry transport |
| M2M | Machine-to-machine |
| NB-API | Northbound application programming interface |
| PHY | Physical layer |
| PDR | Packet delivery ratio |
| PLR | Packet loss ratio |
| PM | Psychical machine |
| PSO | Particle swarm optimization |
| QoE | Quality of experience |
| QoS | Quality of service |
| REST | Representational state transfer protocol |
| RFID | Radio frequency identification device |
| RR | Round robin |
| rp-LPLNs | Routing protocol for low-power and lossy networks |
| RTT | Round trip time |
| SB-API | Southbound application programming interface |
| SDN | Software defined networking |
| SG | Smart grid |
| SLA | Service-level agreement |
| SOA | Service oriented architecture |
| TCP | Transmission control protocol |
| VM | Virtual machine |
| WAN | Wide area network |
| WSN | Wireless sensor network |
| 5G | 5th generation |
References
- Čolaković, A.; Hadžialić, M. Internet of Things (IoT): A review of enabling technologies, challenges, and open research issues. Comput. Netw. 2018, 144, 17–39. [Google Scholar] [CrossRef]
- Li, S.; Xu, L.D.; Zhao, S. The internet of things: A survey. Inf. Syst. Front. 2015, 17, 243–259. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Alvi, S.A.; Afzal, B.; Shah, G.A.; Atzori, L.; Mahmood, W. Internet of multimedia things: Vision and challenges. Ad Hoc Netw. 2015, 33, 87–111. [Google Scholar] [CrossRef]
- Nauman, A.; Qadri, Y.A.; Amjad, M.; Zikria, Y.B.; Afzal, M.K.; Kim, S.W. Multimedia Internet of Things: A comprehensive survey. IEEE Access 2020, 8, 8202–8250. [Google Scholar] [CrossRef]
- Asghari, P.; Rahmani, A.M.; Javadi, H.H.S. Internet of Things applications: A systematic review. Comput. Netw. 2019, 148, 241–261. [Google Scholar] [CrossRef]
- Hassan, R.; Qamar, F.; Hasan, M.K.; Aman, A.H.M.; Ahmed, A.S. Internet of Things and its applications: A comprehensive survey. Symmetry 2020, 12, 1674. [Google Scholar] [CrossRef]
- Qadri, Y.A.; Nauman, A.; Zikria, Y.B.; Vasilakos, A.V.; Kim, S.W. The future of healthcare internet of things: A survey of emerging technologies. IEEE Commun. Surv. Tutor. 2020, 22, 1121–1167. [Google Scholar] [CrossRef]
- Talavera, J.M.; Tobón, L.E.; Gómez, J.A.; Culman, M.A.; Aranda, J.M.; Parra, D.T.; Quiroz, L.A.; Hoyos, A.; Garreta, L.E. Review of IoT applications in agro-industrial and environmental fields. Comput. Electron. Agric. 2017, 142, 283–297. [Google Scholar] [CrossRef]
- Montori, F.; Bedogni, L.; Bononi, L. A collaborative internet of things architecture for smart cities and environmental monitoring. IEEE Internet Things J. 2017, 5, 592–605. [Google Scholar] [CrossRef]
- Souri, A.; Rahmani, A.M.; Jafari Navimipour, N. Formal verification approaches in the web service composition: A comprehensive analysis of the current challenges for future research. Int. J. Commun. Syst. 2018, 31, e3808. [Google Scholar] [CrossRef]
- Milani, A.S.; Navimipour, N.J. Load balancing mechanisms and techniques in the cloud environments: Systematic literature review and future trends. J. Netw. Comput. Appl. 2016, 71, 86–98. [Google Scholar] [CrossRef]
- Zhong, H.; Fang, Y.; Cui, J. LBBSRT: An efficient SDN load balancing scheme based on server response time. Future Gener. Comput. Syst. 2018, 80, 409–416. [Google Scholar] [CrossRef]
- Kanellopoulos, D. Congestion control for MANETs: An overview. ICT Express 2019, 5, 77–83. [Google Scholar] [CrossRef]
- Xu, M.; Tian, W.; Buyya, R. A survey on load balancing algorithms for virtual machines placement in cloud computing. Concurr. Comput. 2017, 29, e4123. [Google Scholar] [CrossRef]
- Nakai, A.; Madeira, E.; Buzato, L.E. On the use of resource reservation for web services load balancing. J. Netw. Syst. Manag. 2015, 23, 502–538. [Google Scholar] [CrossRef]
- Soundarabai, P.B.; Sahai, R.K.; Thriveni, J.; Venugopal, K.R. Comparative study on load balancing techniques in distributedsystems. Int. J. Inf. Technol. 2012, 6, 53–60. [Google Scholar]
- Al-Janabi, T.A.; Al-Raweshidy, H.S. Optimised clustering algorithm-based centralised architecture for load balancing in IoTnetwork. In Proceedings of the 2017 International Symposium on Wireless Communication Systems (ISWCS), Bologna, Italy, 28–31 August 2017; pp. 269–274. [Google Scholar] [CrossRef]
- Neghabi, A.A.; Navimipour, N.J.; Hosseinzadeh, M.; Rezaee, A. Load balancing mechanisms in the software defined networks: A systematic and comprehensive review of the literature. IEEE Access 2018, 6, 14159–14178. [Google Scholar] [CrossRef]
- Bormann, C.; Castellani, A.P.; Shelby, Z. CoAP: An application protocol for billions of tiny internet nodes. IEEE Internet Comput. 2012, 16, 62–67. [Google Scholar] [CrossRef]
- OASIS. OASIS Advanced Message Queuing Protocol (AMQP) Version 1.0—OASIS Standard; OASIS: Burlington, MA, USA, 2012. [Google Scholar]
- Kura—OSGi-Based Application Framework for M2M Service Gateways, Eclipse, Ottawa, ON, Canada. 25 September 2014. Available online: http://www.eclipse.org/proposals/technology.kura/ (accessed on 10 October 2022).
- Ponte—M2M Bridge Framework for REST Developers, Eclipse, Ottawa, ON, USA. 25 September 2014. Available online: http://eclipse.org/proposals/technology.ponte/ (accessed on 10 October 2022).
- Eclipse IoT. Available online: https://projects.eclipse.org/projects/iot (accessed on 10 December 2018).
- Eclipse SCADA. Available online: http://projects.eclipse.org/projects/technology.eclipsescada (accessed on 10 December 2018).
- Eclipse SmartHome. Available online: http://eclipse.org/proposals/technology.smarthome/ (accessed on 10 December 2018).
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on Internet of Things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Ngu, A.H.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, M.Z. IoT middleware: A survey on issues and enabling technologies. IEEE Internet Things J. 2017, 4, 1–20. [Google Scholar] [CrossRef]
- Qiu, T.; Chen, N.; Li, K.; Atiquzzaman, M.; Zhao, W. How can heterogeneous Internet of Things build our future: A survey. IEEE Commun. Surv. Tutor. 2018, 20, 2011–2027. [Google Scholar] [CrossRef]
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog computing and the internet of things: A review. Big Data Cogn. Comput. 2018, 2, 10. [Google Scholar] [CrossRef]
- Hu, P.; Ning, H.; Chen, L.; Daneshmand, M. An open Internet of Things system architecture based on software-defined device. IEEE Internet Things J. 2019, 6, 2583–2592. [Google Scholar] [CrossRef]
- Wu, M.; Lu, T.J.; Ling, F.Y.; Sun, J.; Du, H.Y. Research on the architecture of Internet of Things. In Proceedings of the 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), Chengdu, China, 20–22 August 2010; pp. V5-484–V5-487. [Google Scholar] [CrossRef]
- Ren, J.; Zhang, D.; He, S.; Zhang, Y.; Li, T. A survey on end-edge-cloud orchestrated network computing paradigms: Transparent computing, mobile edge computing, fog computing, and cloudlet. ACM Comput. Surv. 2019, 52, 1–36. [Google Scholar] [CrossRef]
- Shafiq, D.A.; Jhanjhi, N.Z.; Abdullah, A. Load balancing techniques in cloud computing environment: A review. J. King Saud Univ. Comput. Inf. Sci. 2021, 24, 3910–3933. [Google Scholar] [CrossRef]
- Odun-Ayo, I.; Ananya, M.; Agono, F.; Goddy-Worlu, R. Cloud computing architecture: A critical analysis. In Proceedings of the 18th International Conference on Computational Science and Applications (ICCSA), Melbourne, VIC, Australia, 2–5 July 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Adhikari, M.; Amgoth, T. Heuristic-based load-balancing algorithm for IaaS cloud. Future Gener. Comput. Syst. 2018, 81, 156–165. [Google Scholar] [CrossRef]
- Alboaneen, D.A.; Tianfield, H.; Zhang, Y. Glowworm swarm optimisation based task scheduling for cloud computing. In Proceedings of the 2nd International Conference on Internet of Things, Data and Cloud Computing, Cambridge, UK, 22–23 March 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Ortiz, S. Software-Defined Networking: On the verge of a breakthrough? Computer 2013, 46, 10–12. [Google Scholar] [CrossRef]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow: Enabling innovation in campus networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Singh, M.P.; Bhandari, A. New-flow based DDoS attacks in SDN: Taxonomy, rationales, and research challenges. Comput. Commun. 2020, 154, 509–527. [Google Scholar] [CrossRef]
- Ali, J.; Lee, G.M.; Roh, B.H.; Ryu, D.K.; Park, G. Software-Defined Networking approaches for link failure recovery: A survey. Sustainability 2020, 12, 4255. [Google Scholar] [CrossRef]
- Latif, Z.; Sharif, K.; Li, F.; Karim, M.M.; Biswas, S.; Wang, Y. A comprehensive survey of interface protocols for software defined networks. J. Netw. Comput. Appl. 2020, 156, 102563. [Google Scholar] [CrossRef]
- Semong, T.; Maupong, T.; Anokye, S.; Kehulakae, K.; Dimakatso, S.; Boipelo, G.; Sarefo, S. Intelligent load balancing techniques in software defined networks: A survey. Electronics 2020, 9, 1091. [Google Scholar] [CrossRef]
- Sharma, V.K.; Verma, L.P.; Kumar, M. A fuzzy-based adaptive energy efficient load distribution scheme in ad-hoc networks. Int. J. Intell. Syst. Appl. 2018, 10, 72. [Google Scholar] [CrossRef][Green Version]
- Sharma, V.K.; Kumar, M. Adaptive energy efficient load distribution using fuzzy approach. Adhoc Sens. Wirel. Netw. 2017, 39, 123–166. [Google Scholar]
- Sharma, V.K.; Verma, L.P.; Kumar, M.; Naha, R.K.; Mahanti, A. A-CAFDSP: An adaptive-congestion aware Fibonacci sequence based data scheduling policy. Comput. Commun. 2020, 158, 141–165. [Google Scholar] [CrossRef]
- Sharma, V.K.; Kumar, M. Adaptive load distribution approach based on congestion control scheme in ad-hoc networks. Int. J. Electron. 2019, 106, 48–68. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Garcia Lopez, P.; Montresor, A.; Epema, D.; Datta, A.; Higashino, T.; Iamnitchi, A.; Barcellos, M.P.; Felber, P.; Riviere, E. Edge-centric computing: Vision and challenges. ACM SIGCOMM Comput. Commun. Rev. 2015, 45, 37–42. [Google Scholar] [CrossRef]
- Beck, M.T.; Werner, M.; Feld, S.; Schimper, S. Mobile edge computing: A taxonomy. In Proceedings of the 6th International Conference on Advances in Future Internet, Lisbon, Portugal, 16–20 November 2014; pp. 48–55. [Google Scholar]
- Hu, P.; Dhelim, S.; Ning, H.; Qiu, T. Survey on fog computing: Architecture, key technologies, applications and open issues. J. Netw. Comput. Appl. 2017, 98, 27–42. [Google Scholar] [CrossRef]
- Kong, W.; Li, X.; Hou, L.; Li, Y. An efficient and credible multi-source trust fusion mechanism based on time decay for edge computing. Electronics 2020, 9, 502. [Google Scholar] [CrossRef]
- Mouradian, C.; Naboulsi, D.; Yangui, S.; Glitho, R.H.; Morrow, M.J.; Polakos, P.A. A comprehensive survey on fog computing: State-of-the-art and research challenges. IEEE Commun. Surv. Tutor. 2017, 20, 416–464. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Natarajan, P.; Zhu, J. Fog computing: A platform for internet of things and analytics. In Big Data and Internet of Things: A Roadmap for Smart Environments; Bessis, N., Dobre, C., Eds.; Springer: Cham, Switzerland, 2014; pp. 169–186. [Google Scholar]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the 1st Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar] [CrossRef]
- Chandak, A.; Ray, N.K. A review of load balancing in fog computing. In Proceedings of the 2019 International Conference on Information Technology (ICIT), Bhubaneswar, India, 19–21 December 2019; pp. 460–465. [Google Scholar] [CrossRef]
- Aslanpour, M.S.; Gill, S.S.; Toosi, A.N. Performance evaluation metrics for cloud, fog and edge computing: A review, taxonomy, benchmarks and standards for future research. Internet Things J. 2020, 12, 100273. [Google Scholar] [CrossRef]
- Sharma, V.K.; Kumar, M. Adaptive congestion control scheme in mobile ad-hoc networks. Peer-to-Peer Netw. Appl. 2017, 10, 633–657. [Google Scholar] [CrossRef]
- Sharma, V.K.; Verma, L.P.; Kumar, M. CL-ADSP: Cross-Layer Adaptive Data Scheduling Policy in mobile ad-hoc networks. Future Gener. Comput. Syst. 2019, 97, 530–563. [Google Scholar] [CrossRef]
- Kanellopoulos, D.; Sharma, V.K. Survey on power-aware optimization solutions for MANETs. Electronics 2020, 9, 1129. [Google Scholar] [CrossRef]
- Song, P.; Liu, Y.; Liu, T.; Qian, D. Flow Stealer: Lightweight load balancing by stealing flows in distributed SDN controllers. Sci. China Inf. Sci. 2017, 60, 032202. [Google Scholar] [CrossRef]
- Xu, H.; Li, X.Y.; Huang, L.; Du, Y.; Liu, Z. Partial flow statistics collection for load-balanced routing in software defined networks. Comput. Netw. 2017, 122, 43–55. [Google Scholar] [CrossRef]
- Guo, Z.; Su, M.; Xu, Y.; Duan, Z.; Wang, L.; Hui, S.; Chao, H.J. Improving the performance of load balancing in software-defined networks through load variance-based synchronization. Comput. Netw. 2014, 68, 95–109. [Google Scholar] [CrossRef]
- Han, T.; Ansari, N. A traffic load balancing framework for software-defined radio access networks powered by hybrid energy sources. IEEE/ACM Trans. Netw. 2015, 24, 1038–1051. [Google Scholar] [CrossRef]
- Ghomi, E.J.; Rahmani, A.M.; Qader, N.N. Load balancing algorithms in cloud computing: A survey. J. Netw. Comput. Appl. 2017, 88, 50–71. [Google Scholar] [CrossRef]
- Hamdan, M.; Hassan, E.; Abdelaziz, A.; Elhigazi, A.; Mohammed, B.; Khan, S.; Vasilakos, A.V.; Marsono, M.N. A comprehensive survey of load balancing techniques in Software-Defined Network. J. Netw. Comput. Appl. 2021, 174, 102856. [Google Scholar] [CrossRef]
- Lin, Y.D.; Wang, C.C.; Lu, Y.J.; Lai, Y.C.; Yang, H.C. Two-tier dynamic load balancing in SDN-enabled Wi-Fi networks. Wirel. Netw. 2018, 24, 2811–2823. [Google Scholar] [CrossRef]
- Boero, L.; Cello, M.; Garibotto, C.; Marchese, M.; Mongelli, M. BeaQoS: Load balancing and deadline management of queues in an OpenFlow SDN switch. Comput. Netw. 2016, 106, 161–170. [Google Scholar] [CrossRef]
- Katyal, M.; Mishra, A. A comparative study of load balancing algorithms in cloud computing environment. Int. J. Distrib. Cloud Comput. 2013, 1. [Google Scholar] [CrossRef]
- Ghahramani, M.H.; Zhou, M.; Hon, C.T. Toward cloud computing QoS architecture: Analysis of cloud systems and cloud services. IEEE/CAA J. Autom. Sin. 2017, 4, 6–18. [Google Scholar] [CrossRef]
- Al Nuaimi, K.; Mohamed, N.; Al Nuaimi, M.; Al-Jaroodi, J. A survey of load balancing in cloud computing: Challenges and algorithms. In Proceedings of the 2012 2nd Symposium on Network Cloud Computing and Applications, London, UK, 3–4 December 2012; pp. 137–142. [Google Scholar] [CrossRef]
- Randles, M.; Lamb, D.; Taleb-Bendiab, A. A comparative study into distributed load balancing algorithms for cloud computing. In Proceedings of the 2010 IEEE 24th International Conference on Advanced Information Networking and Applications Workshops, Perth, WA, Australia, 20–23 April 2010; pp. 551–556. [Google Scholar] [CrossRef]
- Sreenivas, V.; Prathap, M.; Kemal, M. Load balancing techniques: Major challenge in cloud computing-a systematic review. In Proceedings of the 2014 International Conference on Electronic Communication Systems (ICECS), Coimbatore, India, 13–14 February 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Raghava, N.S.; Singh, D. Comparative study on load balancing techniques in cloud computing. Open J. Mob. Comput. Cloud Comput. 2014, 1, 31–42. [Google Scholar]
- Mishra, M.; Das, A.; Kulkarni, P.; Sahoo, A. Dynamic resource management using virtual machine migrations. IEEE Commun. Mag. 2012, 50, 34–40. [Google Scholar] [CrossRef]
- Bari, M.F.; Boutaba, R.; Esteves, R.; Granville, L.Z.; Podlesny, M.; Rabbani, M.G.; Zhang, Q.; Zhani, M.F. Data center network virtualization: A survey. IEEE Commun. Surv. Tutor. 2012, 15, 909–928. [Google Scholar] [CrossRef]
- Thakur, A.; Goraya, M.S. A taxonomic survey on load balancing in cloud. J. Netw. Comput. Appl. 2017, 98, 43–57. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R. Issues and challenges of load balancing techniques in cloud computing: A survey. ACM Comput. Surv. 2019, 51, 1–35. [Google Scholar] [CrossRef]
- Ahmad, M.O.; Khan, R.Z. Load balancing tools and techniques in cloud computing: A systematic review. In Advances in Computer and Computational Sciences—Proceedings of the ICCCCS 2016; Bhatia, S.K., Mishra, K.K., Tiwari, S., Singh, V.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar] [CrossRef]
- Kaur, A.; Kaur, B.; Singh, D. Optimization techniques for resource provisioning and load balancing in cloud environment: A review. Int. J. Inf. Eng. Electron. Bus. 2017, 9, 28. [Google Scholar] [CrossRef]
- Belgaum, M.R.; Musa, S.; Alam, M.M.; Su’ud, M.M. A systematic review of load balancing techniques in software-defined networking. IEEE Access 2020, 8, 98612–98636. [Google Scholar] [CrossRef]
- Neghabi, A.A.; Navimipour, N.J.; Hosseinzadeh, M.; Rezaee, A. Nature-inspired meta-heuristic algorithms for solving the load balancing problem in the software-defined network. Int. J. Commun. Syst. 2019, 32, e3875. [Google Scholar] [CrossRef]
- Li, L.; Xu, Q. Load balancing researches in SDN: A survey. In Proceedings of the 2017 7th IEEE International Conference on Electronics Information and Emergency Communication (ICEIEC), Macau, China, 21–23 July 2017; pp. 403–408. [Google Scholar] [CrossRef]
- Zhang, J.; Yu, F.R.; Wang, S.; Huang, T.; Liu, Z.; Liu, Y. Load balancing in data center networks: A survey. IEEE Commun. Surv. Tutor. 2018, 20, 2324–2352. [Google Scholar] [CrossRef]
- Batista, E.; Figueiredo, G.; Prazeres, C. Load balancing between fog and cloud in fog of things based platforms through software-defined networking. J. King Saud Univ. Comput. Inf. Sci. 2021, 34, 7111–7125. [Google Scholar] [CrossRef]
- Hui, J.W.; Culler, D.E. Extending IP to low-power, wireless personal area networks. IEEE Internet Comput. 2008, 12, 37–45. [Google Scholar] [CrossRef]
- Pancaroglu, D.; Sen, S. Load balancing for RPL-based Internet of Things: A review. Ad Hoc Netw. 2021, 116, 102491. [Google Scholar] [CrossRef]
- Ghaleb, B.; Al-Dubai, A.Y.; Ekonomou, E.; Alsarhan, A.; Nasser, Y.; Mackenzie, L.M.; Boukerche, A. A survey of limitations and enhancements of the ipv6 routing protocol for low-power and lossy networks: A focus on core operations. IEEE Commun. Surv. Tutor. 2018, 21, 1607–1635. [Google Scholar] [CrossRef]
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.-P.; Alexander, R. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks (No. rfc6550). 2012. Available online: https://www.rfc-editor.org/rfc/rfc6550.html (accessed on 10 October 2022).
- Sebastian, A.; Sivagurunathan, S. A survey on load balancing schemes in RPL based Internet of Things. Int. J. Sci. Res. Netw. Secur. Commun. 2018, 6, 43–49. [Google Scholar]
- Kim, H.S.; Ko, J.; Culler, D.E.; Paek, J. Challenging the IPv6 routing protocol for low-power and lossy networks (RPL): A survey. IEEE Commun. Surv. Tutor. 2017, 19, 2502–2525. [Google Scholar] [CrossRef]
- Hou, J.; Jadhav, R.; Luo, Z. Optimization of Parent-Node Selection in RPL-Based Networks. Available online: https://datatracker.ietf.org/doc/html/draft-hou-roll-rpl-parent-selection-00 (accessed on 10 October 2022).
- Lamaazi, H.; Benamar, N. A comprehensive survey on enhancements and limitations of the RPL protocol: A focus on the objective function. Ad Hoc Netw. 2020, 96, 102001. [Google Scholar] [CrossRef]
- Oliveira, A.; Vazao, T. Low-power and lossy networks under mobility: A survey. Comput. Netw. 2016, 107, 339–352. [Google Scholar] [CrossRef]
- Iova, O.; Picco, P.; Istomin, T.; Kiraly, C. Rpl: The routing standard for the internet of things... or is it? IEEE Commun. Mag. 2016, 54, 16–22. [Google Scholar] [CrossRef]
- Zhao, M.; Kumar, A.; Joo Chong, P.H.; Lu, R. A comprehensive study of RPL and P2P-RPL routing protocols: Implementation, challenges and opportunities. Peer-to-Peer Netw. Appl. 2017, 10, 1232–1256. [Google Scholar] [CrossRef]
- Zikria, Y.B.; Afzal, M.K.; Ishmanov, F.; Kim, S.W.; Yu, H. A survey on routing protocols supported by the Contiki Internet of Things operating system. Future Gener. Comput. Syst. 2018, 82, 200–219. [Google Scholar] [CrossRef]
- Kim, H.S.; Kim, H.; Paek, J.; Bahk, S. Load balancing under heavy traffic in RPL routing protocol for low power and lossy networks. IEEE Trans. Mob. Comput. 2016, 16, 964–979. [Google Scholar] [CrossRef]
- Thubert, P. Objective Function Zero for the Routing Protocol for Low-Power and Lossy Networks (RPL); No. rfc6552; Internet Engineering Task Force: Fremont, CA, USA, 2012. [Google Scholar]
- Gnawali, O.; Levis, P. The Minimum Rank with Hysteresis Objective Function; No. rfc6719; Internet Engineering Task Force: Fremont, CA, USA, 2012. [Google Scholar]
- Kharrufa, H.; Al-Kashoash, H.A.; Kemp, A.H. RPL-based routing protocols in IoT applications: A review. IEEE Sens. J. 2019, 19, 5952–5967. [Google Scholar] [CrossRef]
- Kashani, M.H.; Mahdipour, E. Load balancing algorithms in fog computing: A systematic review. IEEE Trans. Serv. Comput. 2022. [CrossRef]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All one needs to know about fog computing and related edge computing paradigms: A complete survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Yi, S.; Li, C.; Li, Q. A survey of fog computing: Concepts, applications and issues. In Proceedings of the 2015 Workshop on Mobile Big Data, New York, NY, USA, 21 June 2015; pp. 37–42. [Google Scholar] [CrossRef]
- Xu, X.; Fu, S.; Cai, Q.; Tian, W.; Liu, W.; Dou, W.; Sun, X.; Liu, A.X. Dynamic resource allocation for load balancing in fog environment. Wirel. Commun. Mob. Comput. 2018, 2018, 6421607. [Google Scholar] [CrossRef]
- Al-Khafajiy, M.; Baker, T.; Al-Libawy, H.; Maamar, Z.; Aloqaily, M.; Jararweh, Y. Improving fog computing performance via fog-2-fog collaboration. Future Gener. Comput. Syst. 2019, 100, 266–280. [Google Scholar] [CrossRef]
- Memon, S.; Huang, J.; Saajid, H.; Khuda Bux, N.; Saleem, A.; Aljeroudi, Y. Novel multi-level dynamic traffic load-balancing protocol for data center. Symmetry 2019, 11, 145. [Google Scholar] [CrossRef]
- Carlucci, G.; De Cicco, L.; Holmer, S.; Mascolo, S. Congestion control for web real-time communication. IEEE/ACM Trans. Netw. 2017, 25, 2629–2642. [Google Scholar] [CrossRef]
- Vaquero, L.M.; Rodero-Merino, L. Finding your way in the fog: Towards a comprehensive definition of fog computing. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 27–32. [Google Scholar] [CrossRef]
- Chiang, M.; Ha, S.; Risso, F.; Zhang, T.; Chih-Lin, I. Clarifying fog computing and networking: 10 questions and answers. IEEE Commun. Mag. 2017, 55, 18–20. [Google Scholar] [CrossRef]
- Chiang, M.; Zhang, T. Fog and IoT: An overview of research opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Aazam, M.; Zeadally, S.; Harras, K.A. Offloading in fog computing for IoT: Review, enabling technologies, and research opportunities. Future Gener. Comput. Syst. 2018, 87, 278–289. [Google Scholar] [CrossRef]
- Fricker, C.; Guillemin, F.; Robert, P.; Thompson, G. Analysis of an offloading scheme for data centers in the framework of fog computing. ACM Trans. Model. Perform. Eval. Comput. Syst. 2016, 1, 1–18. [Google Scholar] [CrossRef]
- Mukherjee, M.; Shu, L.; Wang, D. Survey of fog computing: Fundamental, network applications, and research challenges. IEEE Commun. Surv. Tutor. 2018, 20, 1826–1857. [Google Scholar] [CrossRef]
- Ghobaei-Arani, M.; Souri, A.; Rahmanian, A.A. Resource management approaches in fog computing: A comprehensive review. J. Grid Comput. 2020, 18, 1–42. [Google Scholar] [CrossRef]
- Hong, C.H.; Varghese, B. Resource management in fog/edge computing: A survey on architectures, infrastructure, and algorithms. ACM Comput. Surv. 2019, 52, 1–37. [Google Scholar] [CrossRef]
- Lim, C. A survey on congestion control for RPL-based wireless sensor networks. Sensors 2019, 19, 2567. [Google Scholar] [CrossRef] [PubMed]
- Pourghebleh, B.; Hayyolalam, V. A comprehensive and systematic review of the load balancing mechanisms in the Internet of Things. Clust. Comput. 2020, 23, 641–661. [Google Scholar] [CrossRef]
- Gures, E.; Shayea, I.; Ergen, M.; Azmi, M.H.; El-Saleh, A.A. Machine learning based load balancing algorithms in future heterogeneous networks: A survey. IEEE Access 2022, 10, 37689–37717. [Google Scholar] [CrossRef]
- Kaur, M.; Aron, R. A systematic study of load balancing approaches in the fog computing environment. J. Supercomput. 2021, 77, 9202–9247. [Google Scholar] [CrossRef]
- Shahraki, A.; Taherkordi, A.; Haugen, Ø.; Eliassen, F. A survey and future directions on clustering: From WSNs to IoT and modern networking paradigms. IEEE Trans. Netw. Serv. Manag. 2020, 18, 2242–2274. [Google Scholar] [CrossRef]
- Singh, A.; Juneja, D.; Malhotra, M. Autonomous agent based load balancing algorithm in cloud computing. Procedia Comput. Sci. 2015, 45, 832–841. [Google Scholar] [CrossRef]
- Dinesh Babu, L.D.; Krishna, P.V. Honey bee behavior inspired load balancing of tasks in cloud computing environments. Appl. Soft Comput. 2013, 13, 2292–2303. [Google Scholar] [CrossRef]
- Ullah, A. Artificial bee colony algorithm used for load balancing in cloud computing. IAES Int. J. Artif. Intell. 2019, 8, 156. [Google Scholar] [CrossRef]
- Xue, H.; Kim, K.T.; Youn, H.Y. Dynamic load balancing of software-defined networking based on genetic-ant colony optimization. Sensors 2019, 19, 311. [Google Scholar] [CrossRef]
- Panigrahi, A.; Sahu, B.; Rout, S.K.; Rath, A.K. M-Throttled: Dynamic load balancing algorithm for cloud computing. In Intelligent and Cloud Computing—Smart Innovation, Systems and Technologies; Mishra, D., Buyya, R., Mohapatra, P., Patnaik, S., Eds.; Springer: Singapore, 2021; Volume 194. [Google Scholar] [CrossRef]
- Daraghmi, E.Y.; Yuan, S.M. A small world based overlay network for improving dynamic load balancing. J. Syst. Softw. 2015, 107, 187–203. [Google Scholar] [CrossRef]
- Van Eyk, E.; Iosup, A.; Seif, S.; Thömmes, M. The SPEC cloud group’s research vision on FaaS and serverless architectures. In Proceedings of the 2nd International Workshop on Serverless Computing, Las Vegas, NV, USA, 11–15 December 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Scheuner, J.; Leitner, P. Function-as-a-service performance evaluation: A multivocal literature review. J. Syst. Softw. 2020, 170, 110708. [Google Scholar] [CrossRef]
- Cicconetti, C.; Conti, M.; Passarella, A. FaaS execution models for edge applications. Pervasive Mob. Comput. 2022, 86, 101689. [Google Scholar] [CrossRef]
- Cassel, G.A.S.; Rodrigues, V.F.; da Rosa Righi, R.; Bez, M.R.; Nepomuceno, A.C.; da Costa, C.A. Serverless computing for Internet of Things: A systematic literature review. Future Gener. Comput. Syst. 2022, 128, 299–316. [Google Scholar] [CrossRef]
- Mattia, G.P.; Beraldi, R. P2PFaaS: A framework for FaaS peer-to-peer scheduling and load balancing in fog and edge computing. SSRN Electron. J. 2022. [CrossRef]
- Ren, H.; Lan, Y.; Yin, C. The load balancing algorithm in cloud computing environment. In Proceedings of the 2012 2nd International Conference on Computer Science and Network Technology, Changchun, China, 29–31 December 2012; pp. 925–928. [Google Scholar]
- Liu, Y.; Gong, B.; Xing, C.; Jian, Y. A virtual machine migration strategy based on time series workload prediction using cloud model. Math. Probl. Eng. 2014, 2014, 973069. [Google Scholar] [CrossRef]
- Chang, Y.C.; Chang, R.S.; Chuang, F.W. A predictive method for workload forecasting in the cloud environment. In Advanced Technologies, Embedded and Multimedia for Human-Centric Computing; Huang, Y.-M., Chao, H.-C., Deng, D.-J., Park, J.J., Eds.; Springer: Dordrecht, The Netherlands, 2014; pp. 577–585. [Google Scholar]
- Beloglazov, A.; Abawajy, J.; Buyya, R. Energy-aware resource allocation heuristics for efficient management of data centers for cloud computing. Future Gener. Comput. Syst. 2012, 28, 755–768. [Google Scholar] [CrossRef]
- Beloglazov, A.; Buyya, R. Optimal online deterministic algorithms and adaptive heuristics for energy and performance efficient dynamic consolidation of virtual machines in cloud data centers. Concurr. Comput. Pract. Exp. 2012, 24, 1397–1420. [Google Scholar] [CrossRef]
- Wang, X.; Chen, X.; Yuen, C.; Wu, W.; Zhang, M.; Zhan, C. Delay-cost tradeoff for virtual machine migration in cloud data centers. J. Netw. Comput. Appl. 2017, 78, 62–72. [Google Scholar] [CrossRef]
- Mann, Z.Á. Multicore-aware virtual machine placement in cloud data centers. IEEE Trans. Comput. 2016, 65, 3357–3369. [Google Scholar] [CrossRef]
- Zhang, X.; Li, K.; Zhang, Y. Minimum-cost virtual machine migration strategy in datacenter. Concurr. Comput. Pract. Exp. 2015, 27, 5177–5187. [Google Scholar] [CrossRef]
- Zhao, H.; Wang, J.; Liu, F.; Wang, Q.; Zhang, W.; Zheng, Q. Power-aware and performance-guaranteed virtual machine placement in the cloud. IEEE Trans. Parallel Distrib. Syst. 2018, 29, 1385–1400. [Google Scholar] [CrossRef]
- De Maio, V.; Prodan, R.; Benedict, S.; Kecskemeti, G. Modelling energy consumption of network transfers and virtual machine migration. Future Gener. Comput. Syst. 2016, 56, 388–406. [Google Scholar] [CrossRef]
- Liu, X.F.; Zhan, Z.H.; Deng, J.D.; Li, Y.; Gu, T.; Zhang, J. An energy efficient ant colony system for virtual machine placement in cloud computing. IEEE Trans. Evol. Comput. 2016, 22, 113–128. [Google Scholar] [CrossRef]
- Belabed, D.; Secci, S.; Pujolle, G.; Medhi, D. Striking a balance between traffic engineering and energy efficiency in virtual machine placement. IEEE Trans. Netw. Serv. Manag. 2015, 12, 202–216. [Google Scholar] [CrossRef]
- Wang, H.; Li, Y.; Zhang, Y.; Jin, D. Virtual machine migration planning in software-defined networks. IEEE Trans. Cloud Comput. 2017, 7, 1168–1182. [Google Scholar] [CrossRef]
- Wang, R.; Wickboldt, J.A.; Esteves, R.P.; Shi, L.; Jennings, B.; Granville, L.Z. Using empirical estimates of effective bandwidth in network-aware placement of virtual machines in datacenters. IEEE Trans. Netw. Serv. Manag. 2016, 13, 267–280. [Google Scholar] [CrossRef]
- Ilkhechi, A.R.; Korpeoglu, I.; Ulusoy, Ö. Network-aware virtual machine placement in cloud data centers with multiple traffic-intensive components. Comput. Netw. 2015, 91, 508–527. [Google Scholar] [CrossRef]
- Remesh Babu, K.R.; Samuel, P. Enhanced bee colony algorithm for efficient load balancing and scheduling in cloud. In Innovations in Bio-Inspired Computing and Applications; Snasel, V., Abraham, A., Kromer, P., Pant, M., Muda, A.K., Eds.; Springer: Cham, Switzerland, 2016; pp. 67–78. [Google Scholar]
- Hota, A.; Mohapatra, S.; Mohanty, S. Survey of different load balancing approach-based algorithms in cloud computing: A comprehensive review. In Computational Intelligence in Data Mining; Behera, H.S., Nayak, J., Naik, B., Abraham, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; pp. 99–110. [Google Scholar]
- Milan, S.T.; Rajabion, L.; Ranjbar, H.; Navimipour, N.J. Nature inspired meta-heuristic algorithms for solving the load-balancing problem in cloud environments. Comput. Oper. Res. 2019, 110, 159–187. [Google Scholar] [CrossRef]
- Houssein, E.H.; Gad, A.G.; Wazery, Y.M.; Suganthan, P.N. Task scheduling in cloud computing based on meta-heuristics: Review, taxonomy, open challenges, and future trends. Swarm Evol. Comput. 2021, 62, 100841. [Google Scholar] [CrossRef]
- Tawfeek, M.A.; El-Sisi, A.; Keshk, A.E.; Torkey, F.A. Cloud task scheduling based on ant colony optimization. In Proceedings of the 2013 8th International Conference on Computer Engineering & Systems (ICCES), Cairo, Egypt, 26–28 November 2013; pp. 64–69. [Google Scholar]
- Dasgupta, K.; Mandal, B.; Dutta, P.; Mandal, J.K.; Dam, S. A genetic algorithm (GA) based load balancing strategy for cloud computing. Procedia Technol. 2013, 10, 340–347. [Google Scholar] [CrossRef]
- Farrag, A.A.S.; Mahmoud, S.A.; El Sayed, M. Intelligent cloud algorithms for load balancing problems: A survey. In Proceedings of the 2015 IEEE 7th International Conference on Intelligent Computing and Information Systems (ICICIS), Cairo, Egypt, 12–14 December 2015; pp. 210–216. [Google Scholar]
- Fu, Y.; Zhu, Y.; Cao, Z.; Du, Z.; Yan, G.; Du, J. Multi-Controller Load Balancing Algorithm for Test Network Based on IACO. Symmetry 2021, 13, 1901. [Google Scholar] [CrossRef]
- Tsai, C.W.; Rodrigues, J.J. Metaheuristic scheduling for cloud: A survey. IEEE Syst. J. 2013, 8, 279–291. [Google Scholar] [CrossRef]
- Li, K.; Xu, G.; Zhao, G.; Dong, Y.; Wang, D. Cloud task scheduling based on load balancing ant colony optimization. In Proceedings of the 2011 6th Annual ChinaGrid Conference, Liaoning, China, 22–23 August 2011; pp. 3–9. [Google Scholar] [CrossRef]
- Moon, Y.; Yu, H.; Gil, J.M.; Lim, J. A slave ants based ant colony optimization algorithm for task scheduling in cloud computing environments. Hum. Centric Comput. Inf. Sci. 2017, 7, 28. [Google Scholar] [CrossRef]
- Muteeh, A.; Sardaraz, M.; Tahir, M. MrLBA: Multi-resource Load Balancing Algorithm for cloud computing using ant colony optimization. Clust. Comput. 2021, 24, 3135–3145. [Google Scholar] [CrossRef]
- Miao, Z.; Yong, P.; Mei, Y.; Quanjun, Y.; Xu, X. A discrete PSO-based static load balancing algorithm for distributed simulations in a cloud environment. Future Gener. Comput. Syst. 2021, 115, 497–516. [Google Scholar] [CrossRef]
- Mousavinasab, Z.; Entezari-Maleki, R.; Movaghar, A. A bee colony task scheduling algorithm in computational grids. In Digital Information Processing and Communications, Proceedings of the International Conference on Digital Information Processing and Communications (ICDIPC), Ostrava, Czech Republic, 7–9 July 2011; Snasel, V., Platos, J., El-Qawasmeh, E., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 200–210. [Google Scholar]
- Pan, J.S.; Wang, H.; Zhao, H.; Tang, L. Interaction artificial bee colony based load balance method in cloud computing. In Genetic and Evolutionary Computing; Sun, H., Yang, C.-Y., Lin, C.-W., Pan, J.-S., Snasel, V., Abraham, A., Eds.; Springer: Cham, Switzerland, 2015; pp. 49–57. [Google Scholar]
- Hashem, W.; Nashaat, H.; Rizk, R. Honey bee based load balancing in cloud computing. KSII Trans. Internet Inf. Syst. 2017, 11, 5694–5711. [Google Scholar]
- Kruekaew, B.; Kimpan, W. Virtual machine scheduling management on cloud computing using artificial bee colony. In Proceedings of the International MultiConference of Engineers and Computer Scientists, Hong Kong, China, 12–14 March 2014; Volume 1, pp. 12–14. [Google Scholar]
- Xu, G.; Ding, Y.; Zhao, J.; Hu, L.; Fu, X. A novel artificial bee colony approach of live virtual machine migration policy using Bayes theorem. Sci. World J. 2013, 2013, 369209. [Google Scholar] [CrossRef]
- Yakhchi, M.; Ghafari, S.M.; Yakhchi, S.; Fazeli, M.; Patooghi, A. Proposing a load balancing method based on Cuckoo Optimization Algorithm for energy management in cloud computing infrastructures. In Proceedings of the 2015 6th International Conference on Modeling, Simulation, and Applied Optimization (ICMSAO), Istanbul, Turkey, 27–29 May 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Kansal, N.J.; Chana, I. Energy-aware virtual machine migration for cloud computing-a firefly optimization approach. J. Grid Comput. 2016, 14, 327–345. [Google Scholar] [CrossRef]
- Elmagzoub, M.A.; Syed, D.; Shaikh, A.; Islam, N.; Alghamdi, A.; Rizwan, S. A survey of swarm intelligence based load balancing techniques in cloud computing environment. Electronics 2021, 10, 2718. [Google Scholar] [CrossRef]
- Bhargavi, K.; Babu, B.S.; Pitt, J. Performance modeling of load balancing techniques in Cloud: Some of the recent competitive swarm artificial intelligence-based. J. Intell. Syst. 2021, 30, 40–58. [Google Scholar] [CrossRef]
- Yuan, H.; Li, C.; Du, M. Optimal virtual machine resources scheduling based on improved particle swarm optimization in cloud computing. J. Softw. 2014, 9, 705–708. [Google Scholar] [CrossRef][Green Version]
- Aslanzadeh, S.; Chaczko, Z. Load balancing optimization in cloud computing: Applying Endocrine-particale swarm optimization. In Proceedings of the 2015 IEEE International Conference on Electro/Information Technology (EIT), DeKalb, IL, USA, 21–23 May 2015; pp. 165–169. [Google Scholar]
- Pan, K.; Chen, J. Load balancing in cloud computing environment based on an improved particle swarm optimization. In Proceedings of the 2015 6th IEEE International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 23–25 September 2015; pp. 595–598. [Google Scholar]
- Ebadifard, F.; Babamir, S.M. A PSO-based task scheduling algorithm improved using a load-balancing technique for the cloud computing environment. Concurr. Comput. Pract. Exp. 2018, 30, e4368. [Google Scholar] [CrossRef]
- Abbes, W.; Kechaou, Z.; Hussain, A.; Qahtani, A.M.; Almutiry, O.; Dhahri, H.; Alimi, A.M. An Enhanced Binary Particle Swarm Optimization (E-BPSO) algorithm for service placement in hybrid cloud platforms. Neural Comput. Appl. 2022, 1–19. [Google Scholar] [CrossRef]
- Wang, B.; Li, J. Load balancing task scheduling based on multi-population genetic algorithm in cloud computing. In Proceedings of the 2016 35th Chinese Control Conference (CCC), Chengdu, China, 27–29 July 2016; pp. 5261–5266. [Google Scholar]
- Cho, K.M.; Tsai, P.W.; Tsai, C.W.; Yang, C.S. A hybrid meta-heuristic algorithm for VM scheduling with load balancing in cloud computing. Neural Comput. Appl. 2015, 26, 1297–1309. [Google Scholar] [CrossRef]
- Shojafar, M.; Javanmardi, S.; Abolfazli, S.; Cordeschi, N. FUGE: A joint meta-heuristic approach to cloud job scheduling algorithm using fuzzy theory and a genetic method. Clust. Comput. 2015, 18, 829–844. [Google Scholar] [CrossRef]
- Wei, X.J.; Bei, W.; Jun, L. SAMPGA task scheduling algorithm in cloud computing. In Proceedings of the 2017 36th Chinese Control Conference (CCC), Dalian, China, 26–28 July 2017; pp. 5633–5637. [Google Scholar] [CrossRef]
- Jeyakrishnan, V.; Sengottuvelan, P. A hybrid strategy for resource allocation and load balancing in virtualized data centers using BSO algorithms. Wirel. Pers. Commun. 2017, 94, 2363–2375. [Google Scholar] [CrossRef]
- Ben Alla, H.; Ben Alla, S.; Ezzati, A. A priority based task scheduling in cloud computing using a hybrid MCDM model. In Ubiquitous Networking, Proceedings of the International Symposium on Ubiquitous Networking, Casablanca, Morocco, 9–12 May 2017; Sabir, E., Armada, A.G., Ghogho, M., Debbah, M., Eds.; Springer: Cham, Switzerland, 2017; pp. 235–246. [Google Scholar]
- Madni, S.H.H.; Abd Latiff, M.S.; Abdulhamid, S.I.M.; Ali, J. Hybrid gradient descent cuckoo search (HGDCS) algorithm for resource scheduling in IaaS cloud computing environment. Clust. Comput. 2019, 22, 301–334. [Google Scholar] [CrossRef]
- Chen, C.; Zhu, X.; Bao, W.; Chen, L.; Sim, K.M. An agent-based emergent task allocation algorithm in clouds. In Proceedings of the 2013 IEEE 10th International Conference on High-Performance Computing and Communications, Zhangjiajie, China, 13–15 November 2013; pp. 1490–1497. [Google Scholar] [CrossRef]
- Tasquier, L. Agent based load-balancer for multi-cloud environments. Int. J. Cloud Comput. Res. 2015, 1, 35–49. [Google Scholar]
- Gutierrez-Garcia, J.O.; Ramirez-Nafarrate, A. Agent-based load balancing in cloud data centers. Clust. Comput. 2015, 18, 1041–1062. [Google Scholar] [CrossRef]
- Keshvadi, S.; Faghih, B. A multi-agent based load balancing system in IaaS cloud environment. Int. Robot. Autom. J. 2016, 1, 3–8. [Google Scholar] [CrossRef][Green Version]
- Sangulagi, P.; Sutagundar, A. Agent based Load Balancing in Sensor Cloud. In Proceedings of the 2020 International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 26–28 February 2020; pp. 342–347. [Google Scholar] [CrossRef]
- Saini, S.; Jangra, A.; Singh, G. Real-time agent-based load-balancing algorithm for Internet of Drone (IoD) in cloud computing. In Internet of Things; Goyath, N., Sharma, S., Rena, A.K., Tripathi, S.L., Eds.; CRC Press: Boca Raton, FL, USA, 2022; pp. 81–94. [Google Scholar]
- Kim, B.; Byun, H.; Heo, Y.A.; Jeong, Y.S. Adaptive job load balancing scheme on mobile cloud computing with collaborative architecture. Symmetry 2017, 9, 65. [Google Scholar] [CrossRef]
- Ramezani, F.; Lu, J.; Hussain, F.K. Task-based system load balancing in cloud computing using particle swarm optimization. Int. J. Parallel Program. 2014, 42, 739–754. [Google Scholar] [CrossRef]
- Calheiros, R.N.; Ranjan, R.; Beloglazov, A.; De Rose, C.A.; Buyya, R. CloudSim: A toolkit for modeling and simulation of cloud computing environments and evaluation of resource provisioning algorithms. Softw. Pract. Exp. 2011, 41, 23–50. [Google Scholar] [CrossRef]
- Wu, Z.; Xing, S.; Cai, S.; Xiao, Z.; Ming, Z. A genetic-ant-colony hybrid algorithm for task scheduling in cloud system. In Smart Computing and Communication, Proceedings of the International Conference on Smart Computing and Communication, Shenzhen, China, 17–19 December 2016; Qiu, M., Ed.; Springer: Cham, Switzerland, 2017; pp. 183–193. [Google Scholar] [CrossRef]
- Shen, H.; Yu, L.; Chen, L.; Li, Z. Goodbye to fixed bandwidth reservation: Job scheduling with elastic bandwidth reservation in clouds. In Proceedings of the 2016 IEEE International Conference on Cloud Computing Technology and Science (CloudCom) Luxembourg, 12–15 December 2016; pp. 1–8. [Google Scholar] [CrossRef]
- Xin, Y.; Xie, Z.Q.; Yang, J. A load balance oriented cost efficient scheduling method for parallel tasks. J. Netw. Comput. Appl. 2017, 81, 37–46. [Google Scholar] [CrossRef]
- Aladwani, T. Impact of selecting virtual machine with least load on tasks scheduling algorithms in cloud computing. In Proceedings of the 2nd International Conference on Big Data, Cloud and Applications (BDCA’17), Tetouan, Morocco, 29–30 March 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Elmougy, S.; Sarhan, S.; Joundy, M. A novel hybrid of Shortest job first and round Robin with dynamic variable quantum time task scheduling technique. J. Cloud Comput. 2017, 6, 12. [Google Scholar] [CrossRef]
- Alguliyev, R.M.; Imamverdiyev, Y.N.; Abdullayeva, F.J. PSO-based Load Balancing Method in Cloud Computing. Autom. Control Comp. Sci. 2019, 53, 45–55. [Google Scholar] [CrossRef]
- Potluri, S.; Rao, K.S. Optimization model for QoS based task scheduling in cloud computing environment. Indones. J. Electr. Eng. Comput. Sci. 2020, 18, 1081–1088. [Google Scholar] [CrossRef]
- Mao, Y.; Ren, D.; Chen, X. Adaptive load balancing algorithm based on prediction model in cloud computing. In Proceedings of the 2nd International Conference on Innovative Computing and Cloud Computing (ICCC’13), Wuhan, China, 1–2 December 2013; pp. 165–170. [Google Scholar] [CrossRef]
- Zhao, J.; Yang, K.; Wei, X.; Ding, Y.; Hu, L.; Xu, G. A heuristic clustering-based task deployment approach for load balancing using Bayes theorem in cloud environment. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 305–316. [Google Scholar] [CrossRef]
- Pawlak, Z. Rough sets and decision algorithms. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2005, pp. 30–45. [Google Scholar] [CrossRef]
- Kang, B.; Hyunseung Choo, H. A cluster-based decentralized job dispatching for the large-scale cloud. EURASIP J. Wirel. Commun. Netw. 2016, 2016, 25. [Google Scholar] [CrossRef]
- Dhurandher, S.K.; Obaidat, M.S.; Woungang, I.; Agarwal, P.; Gupta, A.; Gupta, P. A cluster-based load balancing algorithm in cloud computing. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 2921–2925. [Google Scholar] [CrossRef]
- Zegrari, F.; Idrissi, A.; Rehioui, H. Resource allocation with efficient load balancing in cloud environment. In Proceedings of the International Conference on Big Data and Advanced Wireless Technologies (BDAW’16), Blagoevgrad, Bulgaria, 10–11 November 2011; pp. 1–7. [Google Scholar] [CrossRef]
- Han, Y.; Chronopoulos, A.T. Scalable loop self-scheduling schemes for large-scale clusters and cloud systems. Int. J. Parallel Program. 2017, 45, 595–611. [Google Scholar] [CrossRef]
- Nishitha, M.; Hussain, S.M.; Shobha, K.R. Cluster based load balancing in cloud environment. In ICT for Competitive Strategies; Mishra, D.K., Dey, N., Deora, B.S., Joshi, A., Eds.; CRC Press: Boca Raton, FL, USA, 2020; pp. 731–737. [Google Scholar]
- Agrawal, N. Dynamic load balancing assisted optimized access control mechanism for edge-fog-cloud network in Internet of Things environment. Concurr. Comput. Pract. Exp. 2021, 33, e6440. [Google Scholar] [CrossRef]
- Naranjo, P.G.V.; Pooranian, Z.; Shojafar, M.; Conti, M.; Buyya, R. FOCAN: A Fog-supported smart city network architecture for management of applications in the Internet of Everything environments. J. Parallel Distrib. Comput. 2018, 132, 24–283. [Google Scholar] [CrossRef]
- Zahid, M.; Javaid, N.; Ansar, K.; Hassan, K.; KaleemUllah Khan, M.; Waqas, M. Hill climbing load balancing algorithm on fog computing. In Advances on P2P, Parallel, Grid, Cloud and Internet Computing, Proceedings of the 13th International Conference on P2P, Parallel, Grid, Cloud and Internet Computing, Taichung, Taiwan, 27–29 October 2018; Xhafa, F., Leu, F.-Y., Ficco, M., Yang, C.-T., Eds.; Springer: Cham, Switzerland, 2019; pp. 238–251. [Google Scholar] [CrossRef]
- Kamal, M.B.; Javaid, N.; Naqvi, S.A.A.; Butt, H.; Saif, T.; Kamal, M.D. Heuristic min-conflicts optimizing technique for load balancing on fog computing. In Advances in Intelligent Networking and Collaborative Systems, Proceedings of the 10th International Conference on Intelligent Networking and Collaborative Systems, Bratislava, Slovakia, 5–7 September 2018; Xhafa, F., Barolli, L., Gregus, M., Eds.; Springer: Cham, Switzerland, 2019; pp. 207–219. [Google Scholar] [CrossRef]
- Banaie, F.; Yaghmaee, M.H.; Hosseini, S.A.; Tashtarian, F. Load-balancing algorithm for multiple gateways in Fog-based Internet of Things. IEEE Internet Things J. 2020, 7, 7043–7053. [Google Scholar] [CrossRef]
- Oueis, J.; Strinati, E.C.; Barbarossa, S. The fog balancing: Load distribution for small cell cloud computing. In Proceedings of the 2015 IEEE 81st Vehicular Technology Conference (VTC Spring), Glasgow, UK, 11–14 May 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Chien, W.; Lai, C.; Cho, H.; Chao, H. A SDN-SFC-based service-oriented load balancing for the IoT applications. J. Netw. Comput. Appl. 2018, 114, 88–97. [Google Scholar] [CrossRef]
- Zhang, Z.; Duan, A. An Adaptive Data Traffic Control Scheme with Load Balancing in a Wireless Network. Symmetry 2022, 14, 2164. [Google Scholar] [CrossRef]
- He, X.; Ren, Z.; Shi, C.; Fang, J. A novel load balancing strategy of software-defined cloud/fog networking in the Internet of Vehicles. China Commun. 2016, 13 (Suppl. S2), 140–149. [Google Scholar] [CrossRef]
- Wan, J.; Chen, B.; Wang, S.; Xia, M.; Li, D.; Liu, C. Fog computing for energy-aware load balancing and scheduling in smart factory. IEEE Trans. Ind. Inform. 2018, 14, 4548–4556. [Google Scholar] [CrossRef]
- Baburao, D.; Pavankumar, T.; Prabhu, C.S.R. Load balancing in the fog nodes using particle swarm optimization-based enhanced dynamic resource allocation method. Appl. Nanosci. 2021, 1–10. [Google Scholar] [CrossRef]
- Shi, C.; Ren, Z.; He, X. Research on load balancing for software defined cloud-fog network in real-time mobile face recognition. In Communications and Networking, Proceedings of the International Conference on Communications and Networking in China, Chongqing, China, 24–26 September 2016; Chen, Q., Meng, W., Zhao, L., Eds.; Springer: Cham, Switzerland, 2018; pp. 121–131. [Google Scholar]
- Yang, J. Low-latency cloud-fog network architecture and its load balancing strategy for medical big data. J. Ambient Intell. Humaniz. Comput. 2020, 11, 1–10. [Google Scholar] [CrossRef]
- Malik, S.; Gupta, K.; Gupta, D.; Singh, A.; Ibrahim, M.; Ortega-Mansilla, A.; Goyal, N.; Hamam, H. Intelligent load-balancing framework for fog-enabled communication in healthcare. Electronics 2022, 11, 566. [Google Scholar] [CrossRef]
- Karthik, S.S.; Kavithamani, A. Fog computing-based deep learning model for optimization of microgrid-connected WSN with load balancing. Wirel. Netw. 2021, 27, 2719–2727. [Google Scholar] [CrossRef]
- Qun, R.; Arefzadeh, S.M. A new energy-aware method for load balance managing in the fog-based vehicular ad hoc networks (VANET) using a hybrid optimization algorithm. IET Commun. 2021, 15, 1665–1676. [Google Scholar] [CrossRef]
- Li, C.; Zhuang, H.; Wang, Q.; Zhou, X. SSLB: Self-Similarity-based Load Balancing for large-scale fog computing. Arab. J. Sci. Eng. 2018, 43, 7487–7498. [Google Scholar] [CrossRef]
- Singh, S.P.; Sharma, A.; Kumar, R. Design and exploration of load balancers for fog computing using fuzzy logic. Simul. Model. Pract. Theory 2020, 101, 102017. [Google Scholar] [CrossRef]
- Abedin, S.F.; Bairagi, A.K.; Munir, M.S.; Tran, N.H.; Hong, C.S. Fog load balancing for massive machine type communications: A game and transport theoretic approach. IEEE Access 2018, 7, 4204–4218. [Google Scholar] [CrossRef]
- Beraldi, R.; Canali, C.; Lancellotti, R.; Proietti Mattia, G. Randomized load balancing under loosely correlated state information in fog computing. In Proceedings of the 23rd International ACM Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Alicante, Spain, 16–20 November 2020; pp. 123–127. [Google Scholar] [CrossRef]
- Ningning, S.; Chao, G.; Xingshuo, A.; Qiang, Z. Fog computing dynamic load balancing mechanism based on graph repartitioning. China Commun. 2016, 13, 156–164. [Google Scholar] [CrossRef]
- Puthal, D.; Obaidat, M.S.; Nanda, P.; Prasad, M.; Mohanty, S.P.; Zomaya, A.Y. Secure and sustainable load balancing of edge data centers in fog computing. IEEE Commun. Mag. 2018, 56, 60–65. [Google Scholar] [CrossRef]
- Cui, K.; Sun, W.; Lin, B.; Sun, W. Load balancing mechanisms of unmanned surface vehicle cluster based on marine vehicular fog computing. In Proceedings of the 2020 16th International Conference on Mobility, Sensing and Networking, Tokyo, Japan, 17–19 December 2020; pp. 797–802. [Google Scholar] [CrossRef]
- Fan, Q.; Ansari, N. Towards workload balancing in fog computing empowered IoT. IEEE Trans. Netw. Sci. Eng. 2018, 7, 253–262. [Google Scholar] [CrossRef]
- Barros, E.; Peixoto, M.; Leite, D.; Batista, B.; Kuehne, B. A fog model for dynamic load flow analysis in smart grids. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 1–6. [Google Scholar]
- Beraldi, R.; Alnuweiri, H. Sequential randomization load balancing for fog computing. In Proceedings of the 2018 26th International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 13–15 September 2018; pp. 1–6. [Google Scholar]
- Chen, D.; Kuehn, V. Adaptive radio unit selection and load balancing in the downlink of fog radio access network. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–6 December 2016; pp. 1–7. [Google Scholar]
- Maswood, M.M.S.; Rahman, M.R.; Alharbi, A.G.; Medhi, D. A novel strategy to achieve bandwidth cost reduction and load balancing in a cooperative three-layer fog-cloud computing environment. IEEE Access 2020, 8, 113737–113750. [Google Scholar] [CrossRef]
- Sthapit, S.; Thompson, J.; Robertson, N.M.; Hopgood, J.R. Computational load balancing on the edge in absence of cloud and fog. IEEE Trans. Mob. Comput. 2018, 18, 1499–1512. [Google Scholar] [CrossRef]
- Chen, Y.A.; Walters, J.P.; Crago, S.P. Load balancing for minimizing deadline misses and total runtime for connected car systems in fog computing. In Proceedings of the 2017 IEEE International Symposium on Parallel and Distributed Processing with Applications and 2017 IEEE International Conference on Ubiquitous Computing and Communications (ISPA/IUCC), Guangzhou, China, 12–15 December 2017; pp. 683–690. [Google Scholar]
- Dao, N.N.; Lee, J.; Vu, D.N.; Paek, J.; Kim, J.; Cho, S.; Chung, K.-S.; Keum, C. Adaptive resource balancing for serviceability maximization in fog radio access networks. IEEE Access 2017, 5, 14548–14559. [Google Scholar] [CrossRef]
- Mukherjee, M.; Liu, Y.; Lloret, J.; Guo, L.; Matam, R.; Aazam, M. Transmission and latency-aware load balancing for fog radio access networks. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Nazar, T.; Javaid, N.; Waheed, M.; Fatima, A.; Bano, H.; Ahmed, N. Modified shortest job first for load balancing in cloud-fog computing. In Advances on Broadband and Wireless Computing, Communication and Applications, Proceedings of the 13th International Conference on Broadband and Wireless Computing, Communication and Applications, Taichung, Taiwan, 27–29 October 2018; Barolli, L., Leu, F.-Y., Enokido, T., Chen, H.-C., Eds.; Springer: Cham, Switzerland, 2019; pp. 63–76. [Google Scholar]
- Ahmad, N.; Javaid, N.; Mehmood, M.; Hayat, M.; Ullah, A.; Khan, H.A. Fog-cloud based platform for utilization of resources using load balancing technique. In Advances in Network-Based Information Systems, Proceedings of the 21st International Conference on Network-Based Information Systems, Bratislava, Slovakia, 5–7 September 2018; Barolli, L., Kryvinska, N., Enokido, T., Takizawa, M., Eds.; Springer: Cham, Switzerland, 2019; pp. 554–567. [Google Scholar]
- Chekired, D.A.; Khoukhi, L.; Mouftah, H.T. Queuing model for EVs energy management: Load balancing algorithms based on decentralized fog architecture. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Neto, E.C.P.; Callou, G.; Aires, F. An algorithm to optimise the load distribution of fog environments. In Proceedings of the 2017 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Banff, AB, Canada, 5–8 October 2017; pp. 1292–1297. [Google Scholar]
- Batista, E.; Figueiredo, G.; Peixoto, M.; Serrano, M.; Prazeres, C. Load balancing in the fog of things platforms through software-defined networking. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1785–1791. [Google Scholar]
- Tariq, S.; Javaid, N.; Majeed, M.; Ahmed, F.; Nazir, S. Priority based load balancing in cloud and fog based systems. In Advances on Broadband and Wireless Computing, Communication and Applications, Proceedings of the 13th International Conference on Broadband and Wireless Computing, Communication and Applications, Taichung, Taiwan, 27–29 October 2018; Barolli, L., Leu, F.-Y., Enokida, T., Chen, H.-C., Eds.; Springer: Cham, Switzerland, 2019; pp. 725–736. [Google Scholar]
- Verma, S.; Yadav, A.K.; Motwani, D.; Raw, R.S.; Singh, H.K. An efficient data replication and load balancing technique for fog computing environment. In Proceedings of the 3rd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 16–18 March 2016; pp. 2888–2895. [Google Scholar]
- Alqahtani, F.; Amoon, M.; Nasr, A.A. Reliable scheduling and load balancing for requests in cloud-fog computing. Peer-to-Peer Netw. Appl. 2021, 14, 1905–1916. [Google Scholar] [CrossRef]
- Asghar, A.; Abbas, A.; Khattak, H.A.; Khan, S.U. Fog based architecture and load balancing methodology for health monitoring systems. IEEE Access 2021, 9, 96189–96200. [Google Scholar] [CrossRef]
- Mazumdar, N.; Nag, A.; Singh, J.P. Trust-based load-offloading protocol to reduce service delays in fog-computing-empowered IoT. Comput. Electr. Eng. 2021, 93, 107223. [Google Scholar] [CrossRef]
- Beraldi, R.; Canali, C.; Lancellotti, R.; Mattia, G.P. Distributed load balancing for heterogeneous fog computing infrastructures in smart cities. Pervasive Mob. Comput. 2020, 67, 101221. [Google Scholar] [CrossRef]
- Rehman, A.U.; Ahmad, Z.; Jehangiri, A.I.; Ala’Anzy, M.A.; Othman, M.; Umar, A.I.; Ahmad, J. Dynamic energy efficient resource allocation strategy for load balancing in fog environment. IEEE Access 2020, 8, 199829–199839. [Google Scholar] [CrossRef]
- Sharmin, Z.; Malik, A.W.; Rahman, A.U.; Noor, R.M. Toward sustainable micro-level fog-federated load sharing in internet of vehicles. IEEE Internet Things J. 2020, 7, 3614–3622. [Google Scholar] [CrossRef]
- Naqvi, S.A.A.; Javaid, N.; Butt, H.; Kamal, M.B.; Hamza, A.; Kashif, M. Metaheuristic optimization technique for load balancing in cloud-fog environment integrated with smart grid. In Advances in Network-Based Information Systems, Proceedings of the 21st International Conference on Network-Based Information Systems, Bratislava, Slovakia, 5–7 September 2018; Barolli, L., Kryvinska, N., Enokido, T., Takizawa, M., Eds.; Springer: Cham, Switzerland, 2019; pp. 700–711. [Google Scholar]
- Abbasi, S.H.; Javaid, N.; Ashraf, M.H.; Mehmood, M.; Naeem, M.; Rehman, M. Load stabilizing in fog computing environment using load balancing algorithm. In Advances on Broadband and Wireless Computing, Communication and Applications Proceedings of the 13th International Conference on Broadband and Wireless Computing, Communication and Applications, Taichung, Taiwan, 27–29 October 2018; Barolli, L., Leu, F.-Y., Enokido, T., Chen, H.-C., Eds.; Springer: Cham, Switzerland, 2019; pp. 737–750. [Google Scholar]
- Ali, M.J.; Javaid, N.; Rehman, M.; Sharif, M.U.; Khan, M.K.; Khan, H.A. State based load balancing algorithm for smart grid energy management in fog computing. In Advances in Intelligent Networking and Collaborative Systems, Proceedings of the 10th International Conference on Intelligent Networking and Collaborative Systems, Bratislava, Slovakia, 5–7 September 2018; Xhafa, F., Barolli, L., Gregus, M., Eds.; Springer: Cham, Switzerland, 2019; pp. 220–232. [Google Scholar]
- Zubair, M.; Javaid, N.; Ismail, M.; Zakria, M.; Asad Zaheer, M.; Saeed, F. Integration of cloud-fog based platform for load balancing using hybrid genetic algorithm using Bin packing technique. In Advances on P2P, Parallel, Grid, Cloud and Internet Computing, Proceedings of the 13th International Conference on P2P, Parallel, Grid, Cloud and Internet Computing, Taichung, Taiwan, 27–29 October 2018; Xhafa, F., Leu, F.-Y., Ficco, M., Yang, C.-T., Eds.; Springer: Cham, Switzerland, 2019; pp. 279–292. [Google Scholar] [CrossRef]
- Talaat, F.M.; Saraya, M.S.; Saleh, A.I.; Ali, H.A.; Ali, S.H. A Load Balancing and Optimization Strategy (LBOS) using reinforcement learning in fog computing environment. J. Ambient Intell. Humaniz. Comput. 2020, 11, 4951–4966. [Google Scholar] [CrossRef]
- Talaat, F.M.; Ali, S.H.; Saleh, A.I.; Ali, H.A. Effective load balancing strategy (ELBS) for real-time fog computing environment using fuzzy and probabilistic neural networks. J. Netw. Syst. Manag. 2019, 27, 883–929. [Google Scholar] [CrossRef]
- Yan, J.; Wu, J.; Wu, Y.; Chen, L.; Liu, S. Task offloading algorithms for novel load balancing in homogeneous fog network. In Proceedings of the 24th International Conference on Computer Supported Cooperative Work in Design, Dalian, China, 5–7 May 2021; pp. 79–84. [Google Scholar] [CrossRef]
- Bali, M.S.; Gupta, K.; Koundal, D.; Zaguia, A.; Mahajan, S.; Pandit, A.K. Smart architectural framework for symmetrical data offloading in IoT. Symmetry 2021, 13, 1889. [Google Scholar] [CrossRef]
- Singh, P.; Kaur, R.; Rashid, J.; Juneja, S.; Dhiman, G.; Kim, J.; Ouaissa, M. A fog-cluster based load-balancing technique. Sustainability 2022, 14, 7961. [Google Scholar] [CrossRef]
- Singh, S.P.; Kumar, R.; Sharma, A.; Abawajy, J.H.; Kaur, R. Energy efficient load balancing hybrid priority assigned laxity algorithm in fog computing. Clust. Comput. 2022, 25, 3325–3342. [Google Scholar] [CrossRef]
- Almutairi, J.; Aldossary, M. Modeling and analyzing offloading strategies of IoT applications over edge computing and joint clouds. Symmetry 2021, 13, 402. [Google Scholar] [CrossRef]
- OASIS. Message Queuing Telemetry Transport. Available online: http://mqtt.org (accessed on 10 November 2022).
- HiveMQ GmbH. HiveMQ Community. Version: 4. 18 June 2020. Available online: https://www.hivemq.com (accessed on 18 June 2020).
- Eclipse Mosquitto™. An Open Source MQTT Broker. Available online: https://mosquitto.org (accessed on 10 November 2022).
- Detti, A.; Funari, L.; Blefari-Melazzi, N. Sub-linear scalability of MQTT clusters in topic-based publish-subscribe applications. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1954–1968. [Google Scholar] [CrossRef]
- EMQX: The Most Scalable MQTT Broker for IIoT. Available online: https://www.emqx.io (accessed on 10 November 2022).
- HAProxy. Available online: https://www.haproxy.com/solutions/load-balancing/ (accessed on 10 November 2022).
- Kawaguchi, R.; Bandai, M. A distributed MQTT Broker system for location-based IoT applications. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–13 January 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Anwer, H.; Azam, F.; Anwar, M.W.; Rashid, M. A model-driven approach for load-balanced MQTT protocol in internet of things (IoT). In Complex, Intelligent, and Software Intensive Systems, Proceedings of the 13th International Conference on Complex, Intelligent, and Software Intensive Systems, Sydney, Australia, 3–5 July 2019; Barolli, L., Hussain, F.K., Ikeda, M., Eds.; Springer: Cham, Switzerland, 2020; pp. 368–378. [Google Scholar]
- HiveMQ. Available online: https://www.hivemq.com/docs/hivemq/4.9/user-guide/load-balancer.html#ssl-offloading (accessed on 10 October 2022).
- Longo, E.; Redondi, A.E.C.; Cesana, M.; Manzoni, P. BORDER: A benchmarking framework for distributed MQTT brokers. IEEE Internet Things J. 2022, 9, 17728–17740. [Google Scholar] [CrossRef]
- Adil, M. Congestion free opportunistic multipath routing load balancing scheme for Internet of Things (IoT). Comput. Netw. 2021, 184, 107707. [Google Scholar] [CrossRef]
- Adil, M.; Song, H.; Ali, J.; Jan, M.A.; Attique, M.; Abbas, S.; Farouk, A. EnhancedAODV: A robust three phase priority-based traffic load balancing scheme for internet of things. IEEE Internet Things J. 2021, 9, 14426–14437. [Google Scholar] [CrossRef]
- Verma, L.P.; Sharma, V.K.; Kumar, M.; Kanellopoulos, D. A novel Delay-based Adaptive Congestion Control TCP variant. Comput. Electr. Eng. 2022, 101, 108076. [Google Scholar] [CrossRef]
- Li, Y.; Gao, Z.; Huang, L.; Du, X.; Guizani, M. Resource management for future mobile networks: Architecture and technologies. Comput. Netw. 2017, 129, 392–398. [Google Scholar] [CrossRef]
- Verma, L.P.; Sharma, V.K.; Kumar, M.; Mahanti, A. An adaptive multi-path data transfer approach for MP-TCP. Wirel. Netw. 2022, 28, 2185–2212. [Google Scholar] [CrossRef]
- Verma, L.P.; Sharma, V.K.; Kumar, M.; Kanellopoulos, D.; Mahanti, A. DB-CMT: A New Concurrent Multi-path Stream Control Transport Protocol. J. Netw. Syst. Manag. 2022, 30, 67. [Google Scholar] [CrossRef]
- Tomar, P.; Kumar, G.; Verma, L.P.; Sharma, V.K.; Kanellopoulos, D.; Rawat, S.S.; Alotaibi, Y. CMT-SCTP and MPTCP Multipath Transport Protocols: A Comprehensive Review. Electronics 2022, 11, 2384. [Google Scholar] [CrossRef]
- Verma, L.P.; Sharma, V.K.; Kumar, M. New delay-based fast retransmission policy for CMT-SCTP. Int. J. Intell. Syst. Appl. 2018, 10, 59–66. [Google Scholar] [CrossRef]
- Hurtig, P.; Grinnemo, K.J.; Brunstrom, A.; Ferlin, S.; Alay, Ö.; Kuhn, N. Low-latency scheduling in MPTCP. IEEE/ACM Trans. Netw. 2018, 27, 302–315. [Google Scholar] [CrossRef]
- Aljubayri, M.; Peng, T.; Shikh-Bahaei, M. Reduce delay of multipath TCP in IoT networks. Wirel. Netw. 2021, 27, 4189–4198. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Pan, L.; Kumar, N.; Doss, R.; Vu, H.L. Multipath TCP meets transfer learning: A novel edge-based learning for industrial IoT. IEEE Internet Things J. 2021, 8, 10299–10307. [Google Scholar] [CrossRef]
- Morawski, M.; Ignaciuk, P. A green multipath TCP framework for industrial internet of things applications. Comput. Netw. 2021, 187, 107831. [Google Scholar] [CrossRef]
- Dong, Z.; Cao, Y.; Xiong, N.; Dong, P. EE-MPTCP: An Energy-Efficient Multipath TCP Scheduler for IoT-based power grid monitoring systems. Electronics 2022, 11, 3104. [Google Scholar] [CrossRef]
- Silva, C.F.; Ferlin, S.; Alay, O.; Brunstrom, A.; Kimura, B.Y. IoT traffic offloading with MultiPath TCP. IEEE Commun. Mag. 2021, 59, 51–57. [Google Scholar] [CrossRef]
- Dong, P.; Shen, R.; Wang, Q.; Zhang, D.; Li, Y.; Zuo, Y.; Yang, W.; Zhang, L. Multipath TCP meets Reinforcement Learning: A novel energy-efficient scheduling approach in heterogeneous wireless networks. IEEE Wirel. Commun. 2022, 1–9. [Google Scholar] [CrossRef]
- Xu, Z.; Tang, J.; Yin, C.; Wang, Y.; Xue, G. Experience-driven congestion control: When multi-path TCP meets deep reinforcement learning. IEEE J. Sel. Areas Commun. 2019, 37, 1325–1336. [Google Scholar] [CrossRef]
- Li, W.; Zhang, H.; Gao, S.; Xue, C.; Wang, X.; Lu, S. SmartCC: A reinforcement learning approach for multipath TCP congestion control in heterogeneous networks. IEEE J. Sel. Areas Commun. 2019, 37, 2621–2633. [Google Scholar] [CrossRef]
- Naeem, F.; Srivastava, G.; Tariq, M. A software defined network based fuzzy normalized neural adaptive multipath congestion control for the internet of things. IEEE Trans. Netw. Sci. Eng. 2020, 7, 2155–2164. [Google Scholar] [CrossRef]
- Chen, Y.R.; Rezapour, A.; Tzeng, W.G.; Tsai, S.C. Rl-routing: An SDN routing algorithm based on deep reinforcement learning. IEEE Trans. Netw. Sci. Eng. 2020, 7, 3185–3199. [Google Scholar] [CrossRef]
- Tang, F.; Mao, B.; Kawamoto, Y.; Kato, N. Survey on machine learning for intelligent end-to-end communication toward 6G: From network access, routing to traffic control and streaming adaption. IEEE Commun. Surv. Tutor. 2021, 23, 1578–1598. [Google Scholar] [CrossRef]
- Zahedinia, M.S.; Khayyambashi, M.R.; Bohlooli, A. Fog-based caching mechanism for IoT data in information centric network using prioritization. Comput. Netw. 2022, 213, 109082. [Google Scholar] [CrossRef]
- Chen, Y.J.; Wang, L.C.; Chen, M.C.; Huang, P.M.; Chung, P.J. SDN-enabled traffic-aware load balancing for M2M networks. IEEE Internet Things J. 2018, 5, 1797–1806. [Google Scholar] [CrossRef]
- Yazdani, M.; Jolai, F. Lion Optimization Algorithm (LOA): A nature-inspired metaheuristic algorithm. J. Comput. Des. Eng. 2016, 3, 24–36. [Google Scholar] [CrossRef]
- Yang, X.S.; Slowik, A. Firefly algorithm. In Swarm Intelligence Algorithms; Yang, X.-S., Slowik, A., Eds.; CRC Press: Boca Raton, FL, USA, 2020; pp. 163–174. [Google Scholar]
- Hanine, M.; Benlahmar, E.H. A load-balancing approach using an improved simulated annealing algorithm. J. Inf. Process. Syst. 2020, 16, 132–144. [Google Scholar] [CrossRef]
- Niu, B.; Wang, H. Bacterial colony optimization. Discret. Dyn. Nat. Soc. 2012, 2012, 698057. [Google Scholar] [CrossRef]
- Keshanchi, B.; Navimipour, N.J. Priority-based task scheduling in the cloud systems using a memetic algorithm. J. Circuits Syst. Comput. 2016, 25, 1650119. [Google Scholar] [CrossRef]
- Dowlatshahi, M.B.; Rafsanjani, M.K.; Gupta, B.B. An energy aware grouping memetic algorithm to schedule the sensing activity in WSNs-based IoT for smart cities. Appl. Soft Comput. 2021, 108, 107473. [Google Scholar] [CrossRef]
- Dasgupta, D. Advances in artificial immune systems. IEEE Comput. Intell. Mag. 2006, 1, 40–49. [Google Scholar] [CrossRef]
- Faris, H.; Aljarah, I.; Al-Betar, M.A.; Mirjalili, S. Grey wolf optimizer: A review of recent variants and applications. Neural Comput. Appl. 2018, 30, 413–435. [Google Scholar] [CrossRef]
- Minh, Q.T.; Kamioka, E.; Yamada, S. CFC-ITS: Context-aware fog computing for intelligent transportation systems. IT Prof. 2018, 20, 35–45. [Google Scholar] [CrossRef]
- Islam, M.S.U.; Kumar, A.; Hu, Y.C. Context-aware scheduling in fog computing: A survey, taxonomy, challenges and future directions. J. Netw. Comput. Appl. 2021, 180, 103008. [Google Scholar] [CrossRef]
- Zhang, W.; Zhang, Z.; Chao, H.C. Cooperative fog computing for dealing with big data in the internet of vehicles: Architecture and hierarchical resource management. IEEE Commun. Mag. 2017, 55, 60–67. [Google Scholar] [CrossRef]
- Badidi, E.; Mahrez, Z.; Sabir, E. Fog computing for smart cities’ big data management and analytics: A review. Future Internet 2020, 12, 190. [Google Scholar] [CrossRef]
- Negash, B.; Westerlund, T.; Tenhunen, H. Towards an interoperable Internet of Things through a web of virtual things at the Fog layer. Future Gener. Comput. Syst. 2019, 91, 96–107. [Google Scholar] [CrossRef]
- Hameed, A.R.; ul Islam, S.; Ahmad, I.; Munir, K. Energy-and performance-aware load-balancing in vehicular fog computing. Sustain. Comput. Inform. Syst. 2021, 30, 100454. [Google Scholar] [CrossRef]
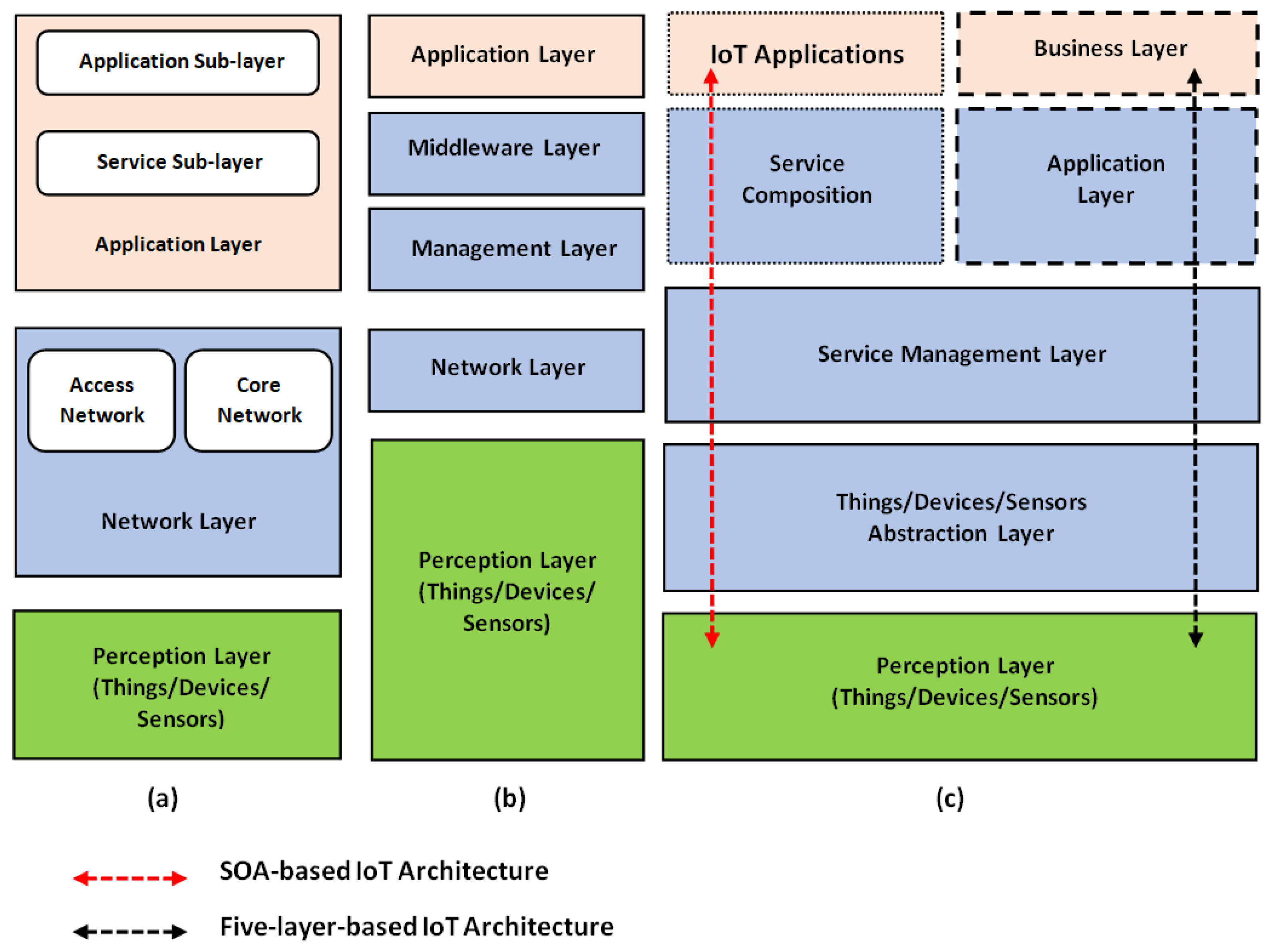
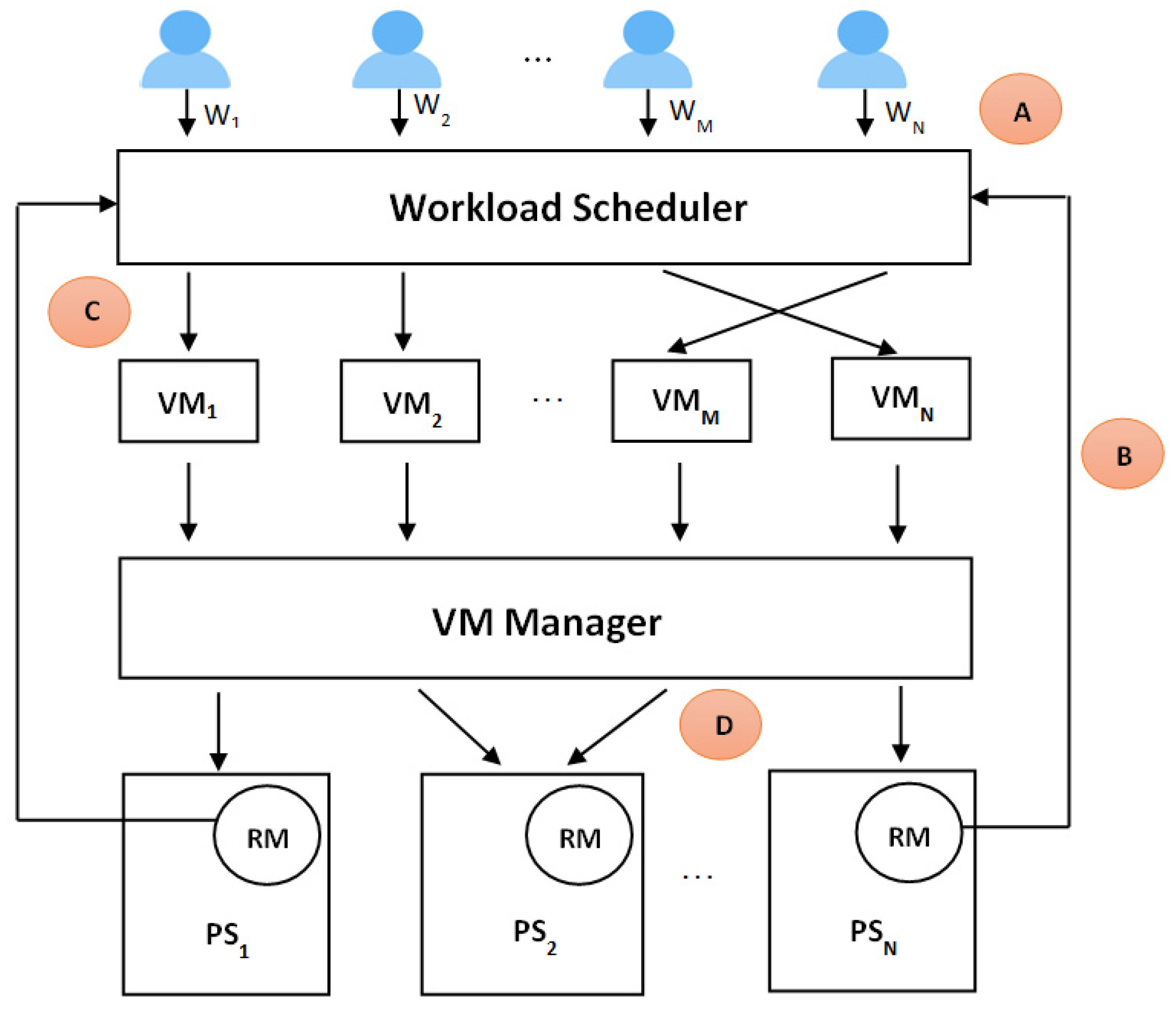
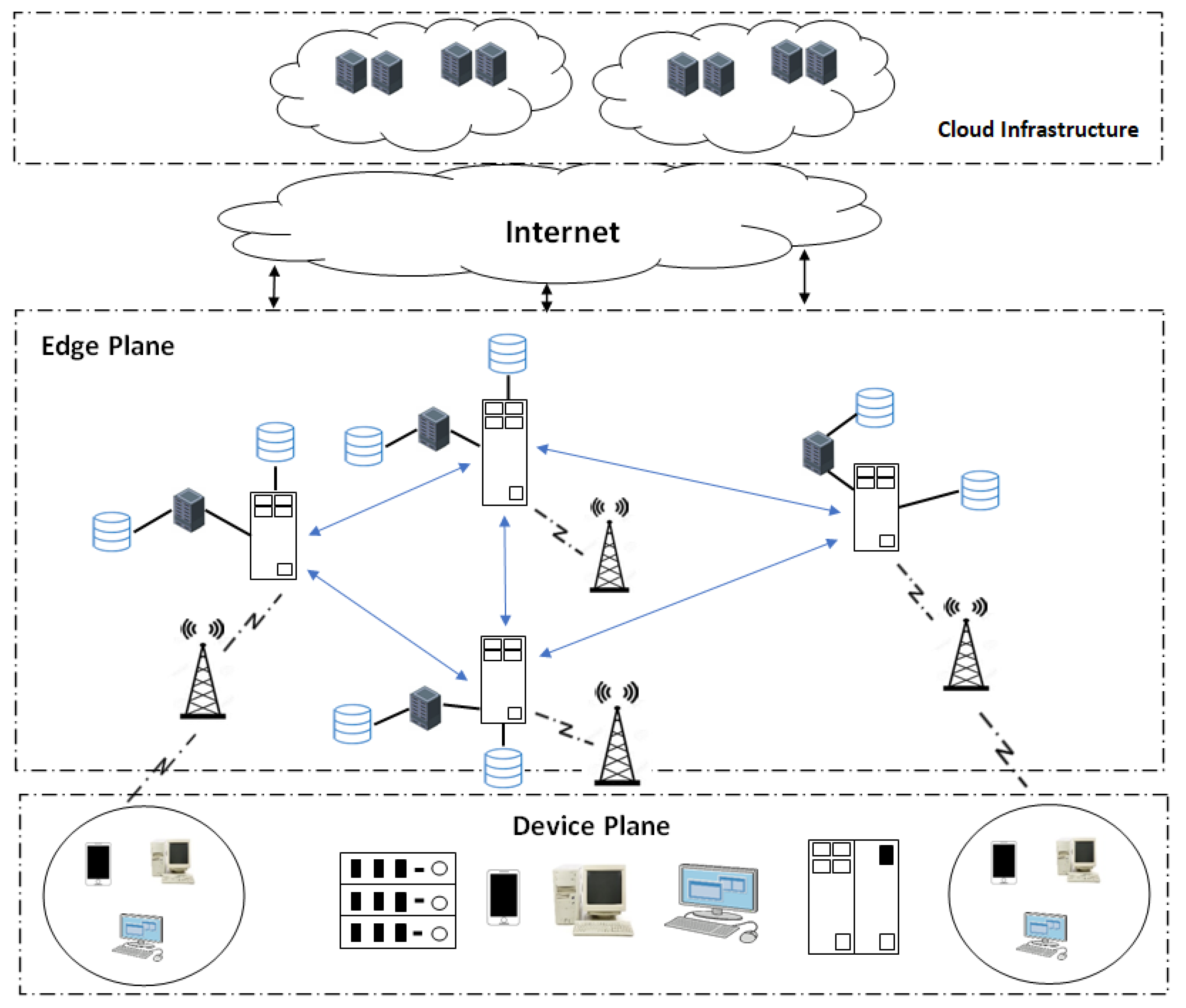
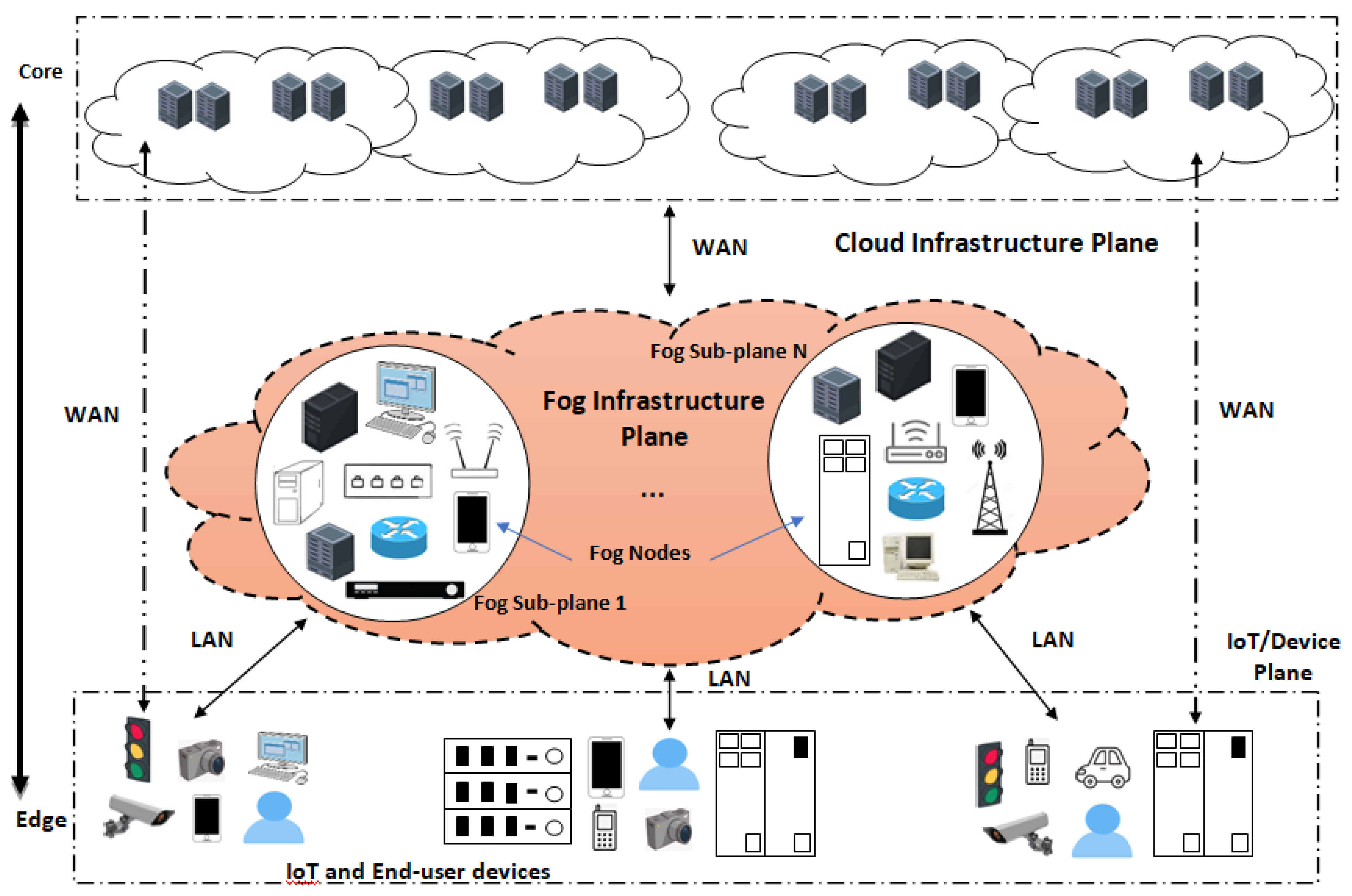
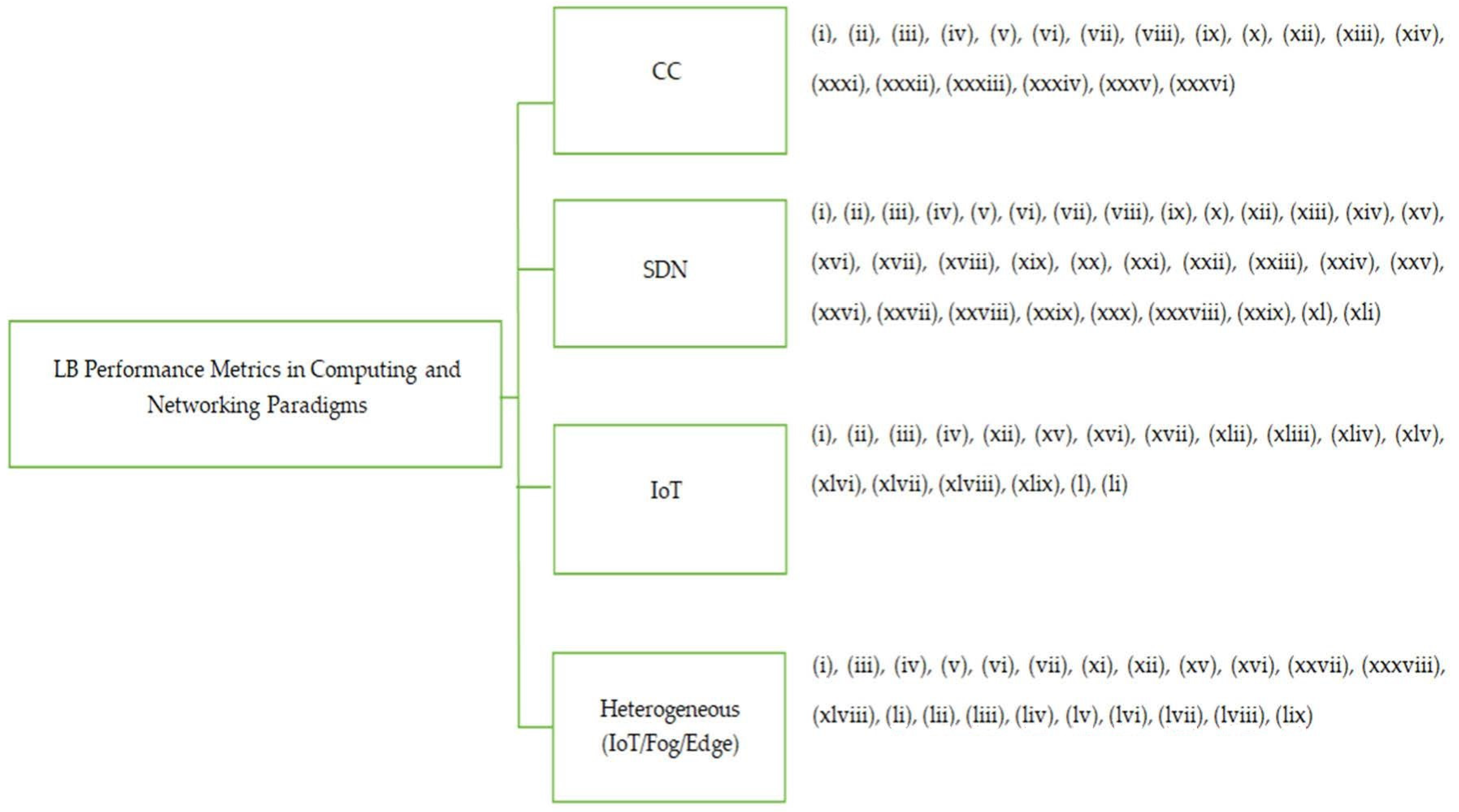
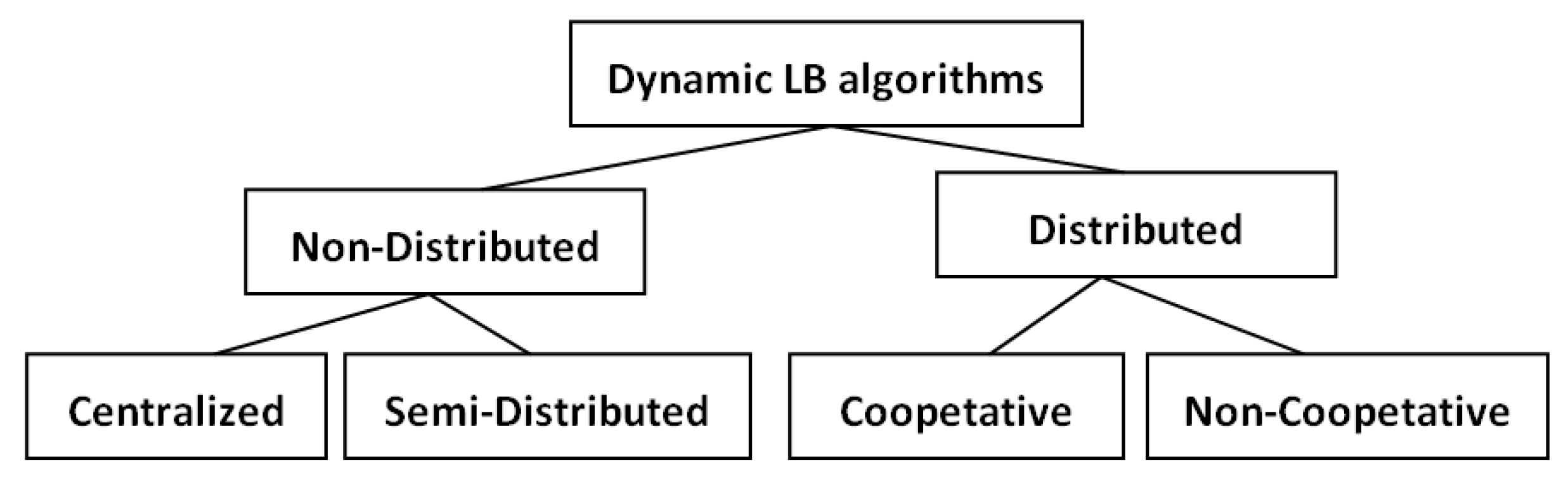
| Metric | Description |
|---|---|
| Throughput | It states the number of workloads served when LB obtains efficiency in a unit of time. |
| Response time | It is the aggregate period it takes for a user to get responses from the IoT application. It comprises the transmission, propagation, processing at middle-boxes (waiting), and service time. It mainly depends on the available bandwidth, the number of users contending for resources simultaneously, and processing time. A larger number of workloads (per unit time) must be served to obtain a faster response time. |
| Scalability | The LB algorithm must be adaptable (scalable) when the number of receiving requests is increasing. The algorithm should be scalable enough to handle the increasing load and workload requests during its lifetime. |
| Fault tolerance | Any element can fail when the IoT system does its tasks flawlessly if a VM fails (i.e., low or no available resources) while performing a task. In that case, there must be some way so that the task has to be offloaded from the overburdened VM to a lesser-loaded VM, which ultimately executes the job completely. The failure element(s) perspective can assess the degree of fault tolerance. |
| Migration time | It is an aggregate period required to transfer a workload from an overloaded VM to an underloaded VM. This offloading procedure should happen without influencing the system’s or application’s availability. An efficient LB policy has low migration times. |
| Resource utilization | It is the degree of resource (i.e., CPU and memory) usage in the computing system. Due to the incoming workload requests, the demands for resources have increased. Thus, the policy must utilize the available resources efficiently to accommodate almost all incoming requests. In a decent LB policy, resource utilization is as maximum as possible. |
| Overhead | It describes the extra operational cost after deploying an LB scheme. This overhead can be due to the huge transmission of control packets (i.e., communication overhead [19,58,59,60], massive migrations, or high offloading amongst VMs). Any extra resource usage in handling and completing requests is treated as an overhead. There are other types of overhead that influence the overall performance of an LB scheme, such as flow stealing [61], flow statistics collection [62], and synchronization overhead [63]. |
| Makespan | It is an aggregate period taken to complete an assigned workload and designate required resources to the consumers in the system. A shorter time leads to the consideration of a better LB policy. |
| Power consumption/management | It is the power consumed by each node while maintaining the system’s connectivity, task assignment, task migration/offloading, and complete execution [64]. It does not matter whether the task is fully accomplished or not; the energy is consumed somewhere. Power consumption should be as minimum as possible. |
| Carbon emission | It is the carbon produced by all the system’s resources. The LB schemes are highly applicable to reduce this metric by migrating the tasks from the underloaded VMs to other VMs and shutting down their whole system [65]. |
| Transmission hop count | It specifies the network system’s degree of congestion level and packet loss probability. In a higher hop count path, the intermediate devices are more likely to be congested, or the links are more likely to be the bottleneck. Thus, we have a higher packet loss probability and transmission delay. In a lower hop count path, the opposite happens. On the basis of this metric, along with overhead, end-to-end delay, PLR, and resources availability, an LB policy designer can design an optimized function for effectively balancing the system. |
| Flow completion time (FCT) | This metric describes the flow transmission efficacy in a system’s long-lived traffic flows. It is an aggregate period taken by a flow to transfer a file completely. |
| Types of traffic | In data center systems, the traffic can be characterized as short-lived (i.e., web browsing or web queries) or long-lived (VMs migration and data transfer) flows. The short-lived flows have a shorter lifetime (duration), which must be transmitted before FCT. The long-lived flows (generated by applications) have a higher lifetime and usually require better throughput [66]. These two types of traffic flow run in a single network whose basic requirements are opposite. The short-lived flows require faster FCT, and the longer-lived flows require higher throughput. Hence, an LB mechanism must adapt its procedure when differentiating traffic types. |
| Workload balance | Concerning SDN controllers, workload balancing is very much required. Here, the term ‘workload’ itself suggests the number of tasks to be completed by an SDN controller. |
| Peak load ratio | This metric can be assessed by estimating the traffic load of each link at a given time [62]. Any LB policy should consider this metric while performing workload and traffic scheduling in the system. |
| Re-association time | This metric [67] states the time taken to associate a client’s device to the underloaded access point to ensure appropriate LB amongst access points. |
| Matched deadline flows | This metric defines the total proportion of flows sustaining its time delay deadline constraints. For instance, some flows running may need to arrive at the destination within a time constraint. Otherwise, the received information could be more beneficial [68]. |
| Cumulative frequency | This metric suggests the precise traffic load information in the queue, which assists in maintaining an efficient LB in the system [68]. |
| Percentage of all VMs to be positioned in host | This metric applies to VM LB mechanisms in data centers. It indicates the percentage distribution of VMs of multiple data centers as restraints. This metric’s assessment has been done by utilizing the maximum and minimum percentage values of all VMs positioned in each cloud. That is how the allocation of these VMs is balanced amongst clouds [15]. |
| Number of migrations | It is the number of tasks switching between multiple VMs. If a VM is overloaded, the tasks performed by it can be switched to other VMs with a lesser workload. If this switching is significant, the system’s performance (i.e., migration and scheduling time overhead) will degrade significantly [15]. |
| Year/Ref. | Techniques Presented | LB Metrics Discussed 1 | Suggested Future Directions | Tool(s)/Testbed(s) Discussed | Weakness | Coverage |
|---|---|---|---|---|---|---|
| Surveys on CC-based LB | ||||||
| 2019 [78] | Static and dynamic LB techniques. | (i), (iii), (iv), (v), (vi), (vii), (viii), and (xiii) | Power saving, resource utilization cost, and carbon emissions. | Cloud Simulators (simulation tool) | An analysis of some extra performance (i.e., communication overhead) and operational attributes is missing. | 2010–2018 |
| 2018 [79] | Fair load distribution for better resource utilization methodologies. | (i), (ii), (iii), (iv), (v), (vi), and (x) | CloudAnalyst, GroudSim, GreenCloud | 2008–2016 | ||
| 2017 [15] | Centralized and distributed load schedulers for VMs placements. | (iii), (ix), (xiii), (xxxi), (xxxii), (xxxiii), (xxxiv), (xxxv), and (xxxvi) | Realistic implementation of metaheuristic approaches. | Realistic Platforms: ElasticHosts, OpenNebula, Amazon EC2 (web service) Simulation toolkits: FlexCloud, CloudSched, CloudSim. | These attempts do not discuss much regarding workload scheduling and LB schemes for IoT. | 2008–2016 |
| 2017 [77] | Statistics-based and nature-inspired LB techniques. | (i), (iii), (v), (vi), (ix), and (xii) | Refinement in algorithms to ascertain migration cost, active thresholding, and communication overhead to accomplish LB efficiently. Efficient workload prediction schemes. Current schemes do not address and focus on the effective usage of available limited network resources. Algorithms should be tested over real-time testbeds and a cloud scenario. | × | The issue of high communication overhead needs to be discussed in detail, which is missing from this survey. | 2007–2017 |
| 2017 [65] | Task scheduling and LB (schedulers in Hadoop, MapReduce optimization, agent-based, natural phenomenon-based, and general schemes). | (i), (iii), (iv), (v), (vii), (viii), (ix), (xii), (xiii), and (xiv) | A tradeoff between various LB metrics. Proposing an LB scheme that could improve as many parameters/metrics as possible. Resource utilization for processing from multiple clouds (providers). Power consumption and carbon emissions. | × | This attempt lacks cluster-based and workload-based LB mechanisms, for accomplishing workload on limited available resources. | 2008–2017 |
| 2016 [12] | Hybrid and dynamic cloud-based LB. | (i), (iii), (v), (vi), (viii), and (ix) | Decentralized LB, task relocation, and failure management features. | × | It superficially discusses workload scheduling and LB schemes for IoT. | 2010–2015 |
| 2014 [73] | Sender-initiated, receiver-initiated, symmetric, static, and dynamic LB techniques. | (i), (ii), (iii), (iv), (v), (vi), and (vii) | Power and stored data management, server association, programmed service provisioning, VMs migration, and carbon emission rate. | × | This survey does not identify or consider the shortcomings of the assessed LB techniques. | 2010–2012 |
| 2014 [69] | Task dependencies and spatial node distribution (distributed, centralized, and hierarchical schemes) in LB schemes. | × | × | CloudSim [68] | An analysis of QoS performance metrics and operational attributes is missing. | 2007–2012 |
| 2014 [74] | Issues (i.e., spatial nodes’ geographical distribution and their traffic pattern analysis, dynamic/static behavior, and complexity of algorithms) affecting LB mechanisms. | (i), (ii), (iii), (iv), (v), (vi), and (viii) | × | × | An analysis of some more performance (i.e., communication overhead) and operational attributes is missing. | 2000–2011 |
| 2012 [71] | Static and dynamic LB mechanisms | × | × | × | An analysis of QoS performance metrics and operational attributes is missing. | 2008–2012 |
| Surveys on SDN-based LB | ||||||
| 2021 [66] | Control plane and data plane-based LB methodologies. | (ii), (iii), (v), (vi), (xv), (xvi), (xvii), (xviii), (xix), and (xx) | Managing heavier controller load in data plane schemes. Active LB practices in case of more than a single and hierarchical controller. Network virtualization inside controllers, controller assignment methods, flow regulation arrangement delay, and network management. | × | The specific comments regarding tools, testbeds, and simulation platforms are missing. | 2008–2020 |
| 2020 [81] | Conventional and artificial intelligence-based schemes. | (ii), (iii), (v), (vi), (viii), (xii), (xiii) (xv), (xvi), (xxii), (xxv), (xxviii), (xxix), and (xxx) | Traffic-aware LB mechanisms, reduction in communication latency when the center controller becomes congested, power-efficient LB schemes, and network function virtualization assistance to cloud users. | × | 2015–2019 | |
| 2020 [43] | LB in controller, server, and wireless links. Communication path selection and AI-based LB. | (iii), (xvi), (xxxvii), (xxxviii), (xxxix), (xl),and (xli) | Energy preservation issue while designing LB scheme for SDN. Smart LB schemes (in SDN) require node and link failure consideration. Adaptations of such schemes in 5G environment. | Mininet, OMNET++, IPerf, MATLAB, Python, .Net, Maxinet (tools and emulators) | This survey lacks in discussing fast adaptive rerouting and multipath solutions, which are also important areas of concern, especially when the network’s links fail rapidly. Moreover, in [48], the authors do not discuss much regarding tools, testbeds, and simulation platforms. | 2007–2020 |
| 2019 [82] | Nature-stimulated metaheuristic techniques. | (ii), (iii), (v), (vi) (xiii), (xv), (xvi), and (xxii) | Traffic shaping, its pattern, and packet priorities can be utilized in the future. Power consumption and carbon emission should be addressed in future nature-inspired metaheuristic load-balancing proposals. | × | 2013–2017 | |
| 2018 [19] | Deterministic and nondeterministic LB techniques in SDN. | (ii), (iii), (vi), (viii), (xii), (xiii), (xvi), (xv), (xxi), (xxii), (xxiii), (xix), (xxiv), (xxv), (xxvi), and (xxvii) | Planning a more poised LB-based QoS metric, power saving, resource utilization cost, and carbon emissions. | × | The issue of communication overhead needs to be discussed in the context of SDN in detail, which is missing from this survey. | 2013–2017 |
| 2017 [83] | Centralized and distributed SDN-based LB schemes. | × | × | × | This survey does not consider the shortcomings of the assessed LB techniques. It does not present specific comments regarding tools, testbeds, and simulation platforms. No performance and operational metrics-based comparison is made in this survey. | 2009–2017 |
| Surveys on LB in LPLNs-based IoT | ||||||
| 2021 [87] | LB mechanisms for rp-LPLNs-based IoT. | (iii), (xii), (xv), (xvi), (xvii), (xlii), (xliii), and (xliv) | Concerning LB, the following are the challenges and open issues allied with rp-LPLNs: power consumption, stability, reliability, mobility, objective function, and congestion. | × | This survey lacks in discussing fast adaptive rerouting and multipath solutions, which are also important areas of concern, especially when the network’s links fail rapidly. | 2009–2020 |
| 2019 [101] | Significant attributes of rp-LPLN and various pros and cons of rp-LPLN in numerous IoT applications are discussed. rp-LPLN improvement for power efficiency, mobility management, QoS, and congestion control. | × | There is not a variant of rp-LPLN which succeeds optimality in all IoT applications. Thus, in the future, rp-LPLN’s functionality must be improved so that it will work and provide optimum performance for most IoT applications. The original rp-LPLN standard ignored mobility management and congestion control completely. Thus, researchers must consider them while designing improved algorithms for rp-LPLN. | × | This survey systematically discusses the rp-LPLN-based routing protocol’s performance-enhanced mechanisms. However, a detailed discussion on LB mechanisms is missing. | 2010–2017 |
| 2019 [117] | LB and congestion control schemes in the wireless sensor networks context. Schemes were classified on the basis of several criteria, e.g., routing metrics, cross-layer design, and path variety. | × | To design a more efficient scheme considering how to reduce resource overutilization. Real-time/testbed implementations and deployment. Contemplation of numerous rp-LPLN. More solid experimental conclusions are required when integrating TCP with rp-LPLN. Cross-layering-based schemes must be proposed. | × | Since this attempt addresses congestion as an essential factor concerning deprived rp-LPLN’s performance, there is a need to specifically evaluate the communication overhead in terms of normalized routing and MAC load, which is missing from the survey. | 2009–2019 |
| 2020 [118] | Centralized and distributed load scheduling. | (i), (ii), (iv), (xii), (xv),(xvi), (xlix), (l), and (li) | Considering traffic shaping/patterns and data/control packet priorities, QoS parameter investigation for LB, and power saving, resource utilization cost, and carbon emissions is required. | × | The specific comments regarding tools, testbeds, and simulation platforms are missing. The issue of communication overhead needs to be discussed in the context of IoT in detail, which is missing from this survey. This survey does not discuss rp-LPLN’s performance issues. | 2009–2019 |
| 2018 [88] | Routing optimization, routing maintenance procedures, and downward routing. | (xii), (xvii), (xliii), (xliv), (xlv), and (xlvi) | Downward traffic forms, LB, single vs. multi-instance optimization, metric composition, real-time assessment via testbeds, and RPL deployment. | × | Although this attempt provides deep insight into the shortcomings of rp-LPLN, the focus is still not on LB schemes. Instead, the authors concentrated on routing procedures’ (path selection and maintenance) optimization, which indirectly affects LB. | 2011–2017 |
| 2018 [90] | LB problems in rp-LPLN such as hotspot, bottleneck, thundering-herd, instability, increased load on nodes, and low PDR. | (xlvii), and (xlviii) | Designing a more composed LB metric is still an open issue in RPL-based IoT-based networks. | × | It does not consider the shortcomings of the LB techniques. Specific analysis regarding tools, testbeds, and simulation platforms is missing. No performance metrics-based comparison is made. | 2012–2018 |
| Surveys on LB in heterogeneous (IoT/Fog/Edge) environment | ||||||
| 2022 [119] | LB in advanced heterogeneous networks (HetNets) and machine learning (ML)-based LB methodologies. | (iii), (xxxviii), (lii), (liii), and (liv) | Incorporation of next-level ML procedures for planning LB schemes. Deep and transfer learning-based LB schemes. NFV/SDN, unmanned aerial vehicle (UAV) base station’s (BS) dynamic deployment to improve LB performance in HetNets. | × | The specific comments regarding tools, testbeds, and simulation platforms are missing. This survey does not consider optimization and computational complexity for ML approaches. | 2013–2021 |
| 2022 [102] | LB in fog computing environment. hybrid, precise, fundamental, and approximate LB methodologies. | (i), (iii), (v), (vi), (xii),(xxvii), (li), (lv), (lvi) and (lvii) | Systematic study of the problems such as power saving, multi-objective optimization, context-aware computing, green Fog, NFV/SDN, social networks analytics, and interoperability. | Mininet, CloudSim, MATLAB, iFogSim, CustomSimulator, Java platform, Work-robots, NS-2/3, Jmeter, CloudAnalyst, CPLEX/AMPL, and Scyther | Although the authors give a percentage of tools utilized so far in the literature, their relative analysis is missing in the survey. The issue of communication overhead needs to be discussed in the context of fog in detail, which is missing from this survey. | 2013–2021 |
| 2021 [120] | LB and resource management in the fog computing environment. | (v), (vi), (vii) (xii), (xvi), (lv), and (lvi) | Load scheduling in fog. Testing of fog-based load balancers in a real-time environment. Power-aware resource utilization-based load balancers’ design. | × | 2013–2020 | |
| 2020 [121] | The performance demands of ad hoc IoT networks. The authors contemplated the impetus for clustering as follows: LB, reducing power depletion, and refining connectivity. | (i), (iii), (iv), (xii), (xi), (xv), (xvi), (xlviii),(li),(lviii), and (lix) | Big challenges ahead when assimilating clustering with edge and fog such as resource provision improvement, and computational offloading. Challenges allied when combining clustering with 5G. Heterogeneity, interference, dynamicity, and scalability. Hierarchical management. | × | Since clustering was the main point of consideration in the context of WSNs, this attempt does not talk much about rp-LPLNs-based proposals, which is essential while dealing with LB in an IoT system. However, those internal details are missing from this survey. | 2000–2019 |
| 2020 [113] | Resource management in the fog context: application placement, resource scheduling, task offloading, LB, and resource allocation. | (i), (iii), (vi), (xii), (xvi), and (lvi) | Resource management in the FC paradigm (open issues): power consumption, interoperability, scheduling and offloading, mobility, and scalability. | × | Although this survey gives a percentage of tools utilized so far in the literature, its relative analysis is missing. The issue of communication overhead is not discussed in the context of fog. | 2014–2019 |
| This survey | It covers several LB issues from different perspectives: (1) dynamic LB and resources management in the cloud, edge/fog computing environments, (2) LB solutions for multipath communication in IoT, and (3) LB for distributing incoming traffic across a cluster of brokers. This survey has an advantage over the previous surveys. | It discuses many LB parameters | Traffic-aware LB, data prioritization, multi-objective optimization in LB decisions, optimal LB solutions, LB based on context-aware computing, interoperability, and efficient load management in vehicular fog computing | × | This comprehensive survey does not identify and review all the existing LB schemes for clusters of MQTT brokers. | 2016–2022 |
| Classification Descriptor |
|---|
| Dynamic LB techniques for CC |
| General LB |
| Natural phenomenon-based LB |
| Agent-based LB |
| Task-based LB |
| Cluster-based LB |
| Dynamic LB in the Fog |
| Approximation algorithms |
| Exact algorithms |
| Fundamental algorithms |
| Hybrid algorithms |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kanellopoulos, D.; Sharma, V.K. Dynamic Load Balancing Techniques in the IoT: A Review. Symmetry 2022, 14, 2554. https://doi.org/10.3390/sym14122554
Kanellopoulos D, Sharma VK. Dynamic Load Balancing Techniques in the IoT: A Review. Symmetry. 2022; 14(12):2554. https://doi.org/10.3390/sym14122554
Chicago/Turabian StyleKanellopoulos, Dimitris, and Varun Kumar Sharma. 2022. "Dynamic Load Balancing Techniques in the IoT: A Review" Symmetry 14, no. 12: 2554. https://doi.org/10.3390/sym14122554
APA StyleKanellopoulos, D., & Sharma, V. K. (2022). Dynamic Load Balancing Techniques in the IoT: A Review. Symmetry, 14(12), 2554. https://doi.org/10.3390/sym14122554








