MDS2-C3PF: A Medical Data Sharing Scheme with Cloud-Chain Cooperation and Policy Fusion in IoT
Abstract
1. Introduction
- A multi-stage system model is proposed. The access control right of medical data between doctors and patients becomes symmetric through their co-authorization. A symmetric cloud-chain cooperation storage and retrieval method is designed to detect malicious feedback from the cloud and to improve the medical data retrieval efficiency.
- An attribute-based access policy fusion method is proposed to develop an access control policy created by both doctors and patients. When the medical data access control policies made by doctors and patients conflict, the balance score matrix is calculated to solve this by using the mutual influence weight and intention score of doctors and patients.
- Considering both medical records retrieval efficiency and detecting malicious feedback from cloud servers, a cloud-chain cooperation retrieval method is proposed. It can improve medical records retrieval efficiency by designing the off-chain search structure and performing an initial search on the cloud server with a secondary search on the blockchain.
2. Related Work
3. Preliminaries
3.1. Bilinear Maps
- Bilinear: and with ;
- Non-degeneracy: ;
- Computability: with computable.
3.2. Access Structure
- If there exists an attribute set S satisfying the access control tree T, then ;
- If x is a leaf node, if and only if the attribute set S contains the attribute of the current leaf node, then ;
- If x is a non-leaf node, for a child node of node x, compute ; if and only if at least children return , it can be denoted as .
4. System and Security Model
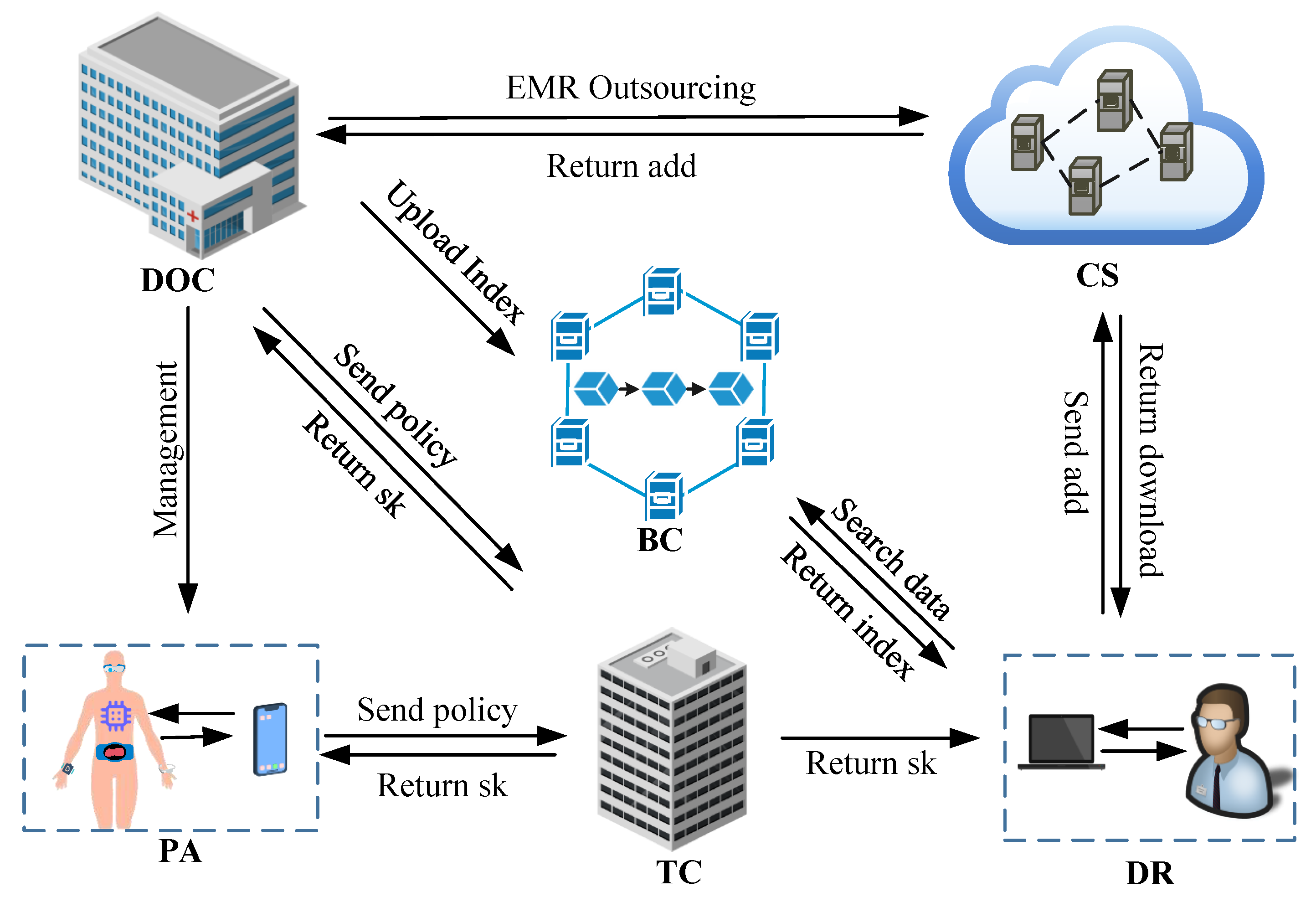
4.1. System Model
- Trust Center (TC). The TC generates key pairs for all legitimate users and executes the policy fusion algorithm.
- Blockchain (BC). The BC is a consortium blockchain that consists of multiple medical institutions to store index information.
- Doctor (DOC). The DOC is the medical data owner responsible for encrypting medical data and uploading the encrypted data to the cloud.
- Cloud Server (CS). The CS is responsible for storing the ciphertext of medical data and sending the file storage address to the DOC.
- Patient (PA). The PA is the owner of the medical data, responsible for developing access policies for the medical data.
- Data Requester (DR). The DR generates a search trapdoor to obtain the corresponding type of data from the cloud and decrypts the medical data.
4.2. Scheme Definition
- : Inputs security parameter and outputs public parameter and master key .
- : The TC inputs attribute set S, master key , and public parameter . Then, the TC outputs the attribute key for all legitimate users.
- : The TC inputs the access control policy tree A of the PA and the tree B of the DOC. The TC fuses A and B and expresses the result as T.
- : The DOC inputs the encryption key k and the medical data and outputs the ciphertext of the medical data.
- : The DOC inputs the keyword W, access control policy tree T, system public key , master key , and public parameter . Then, the DOC outputs index I and partial index ciphertext .
- : The DR runs the algorithm to generate trapdoors based on the keyword that needs to be queried and then uploads the trapdoors to the BC.
- : The CS inputs medical type , trapdoor , and secret key . Then, the CS outputs the dataset .
- : The BC executes the algorithm and performs the blockchain keyword search operation based on the trapdoor and the initial filtered dataset and outputs the transactions .
- : The DR obtains the hash value , verifies whether the ciphertext is modified, and outputs if the hash value is consistent; otherwise, .
- : If the medical data verification is passed, the DR will decrypt the key k of the medical data according to its own attribute private key and I.
4.3. Security Model
4.3.1. The Definition of INDC-SCKA
4.3.2. The Definition of KS-SCSKA
5. Scheme Construction
5.1. Access Control Policy Fusion Algorithm
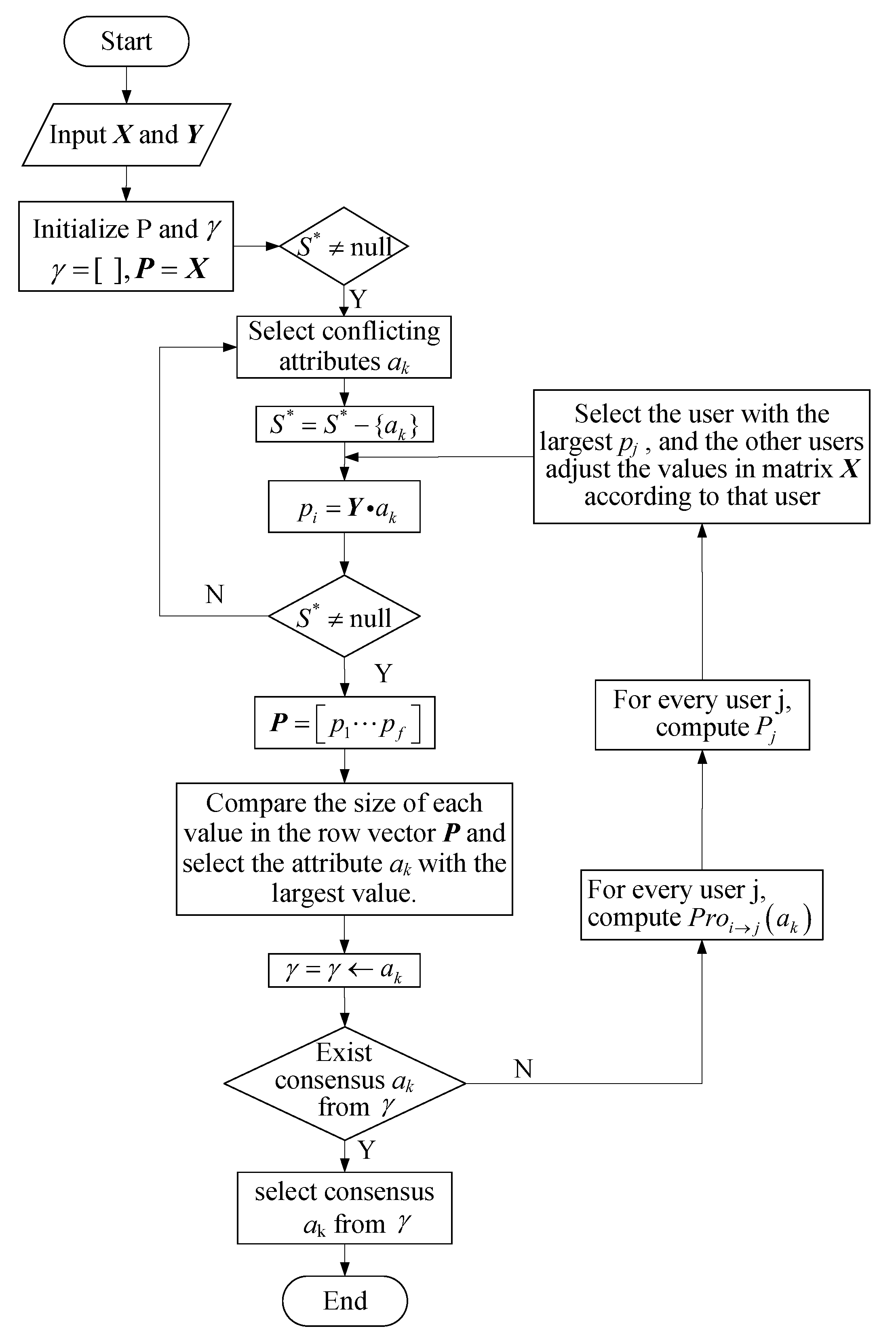
5.1.1. Policy Conflict Resolution Algorithm
- Initialize the matrix:Let it contain n users (resource owners) and f conflicting attributes, then initialize user i’s intention score for conflicting attribute as , where . The value range of the intention score is 0 to 5. Intention score matrix X is denoted asSuppose the initialized user i is influenced by user j’s influence score , taking values in the range of 0–1. Impact score matrix Y is denoted as
- Generate the balance score matrix:Let the sentiment gain of user for an attribute bewhere is the initial willingness value set by the user and is the final willingness value influenced by other users.Let , which givesThat is, when , the user has the highest gain. From Equation (5), the final user’s intention is the sum of his/her own and the player’s influence score. If there is no player influence, then . The final willingness value of each player is calculated by computing the user’s initial settings.Therefore, the column vector P of the balance score matrix is denoted asLet , and thus, P is denoted as
- Judge rule:This rule determines whether the policy is successfully merged. Firstly, it compares the size of each value of in the row vector, selects the attribute corresponding to the largest value, and stores it in the attribute selection set . Next, the rule judges whether the attribute in the set is the same attribute and outputs the result.
- Modify the intention matrix:Calculate the probability that user j is referenced by other users.where denotes the probability that i imitates j’s strategy under attribute and denotes the fraction of i influenced by j. and denote the equilibrium fraction of users i and j choosing attribute . For each user j, the average probability:where the user j with the highest probability is selected and all other users modify the intention score referring to the policy of j. The balance matrix P is recalculated to determine whether the users’ choices are consistent.
5.1.2. Policy Conflict Resolution Algorithm Process
| Algorithm 1 Policy conflict resolution algorithm. |
Input: Output: 1. while do 2. 3. compute 4. end while 5. while true do 6. let 7. 8. if do 9. break 10. end if 11. if do 12. for do 13. 14. for do 15. if do 16. update according to 17. end if 18. end for 19. end for 20. Compute 21. end if 22. end while 23. return |
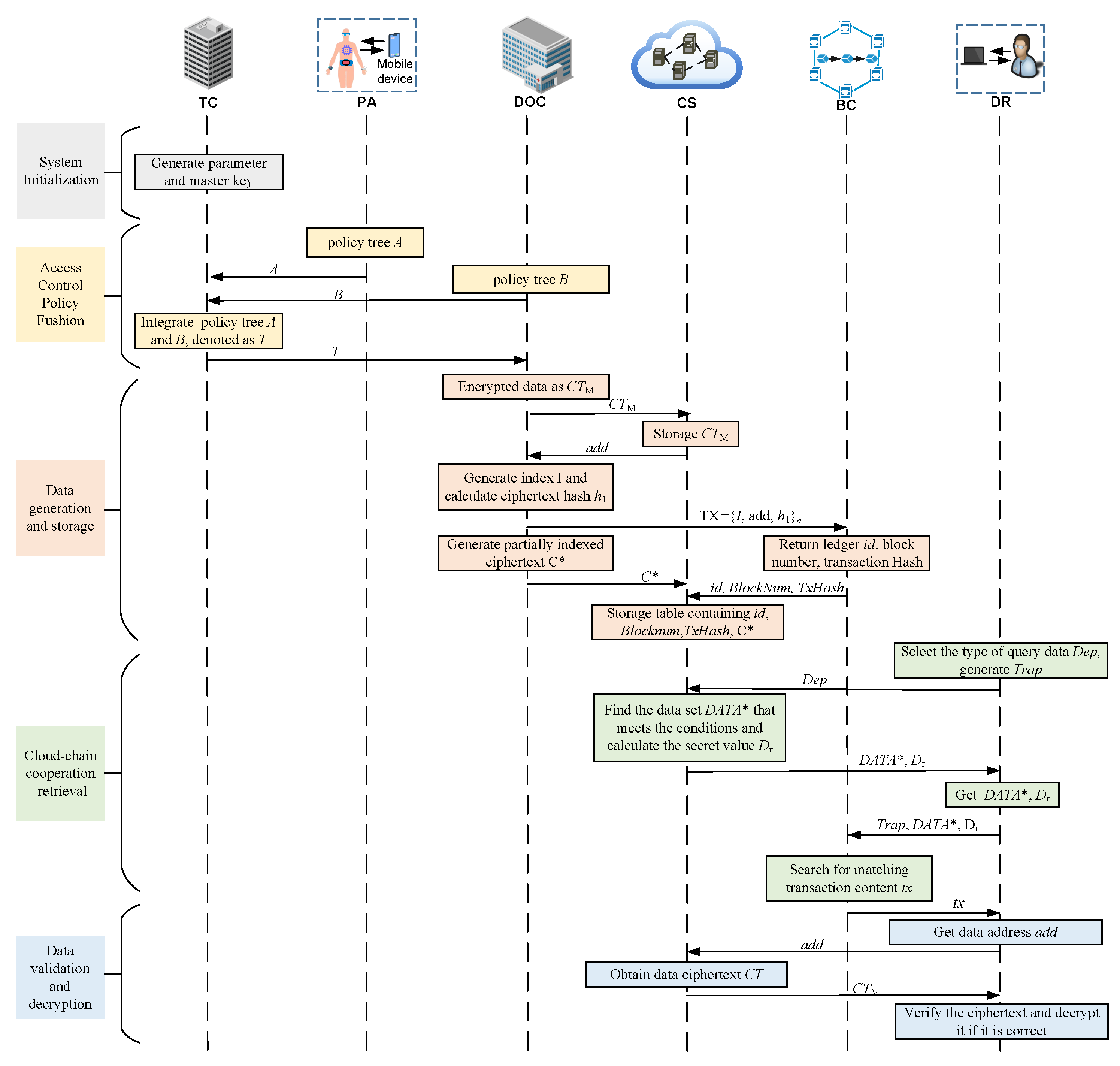
5.2. Details of Five Stages
- System parameter setting:Given security parameter and mapping parameter , the TC executes to generate parameter , system public key , and master key . Then, it selects two hash functions . Besides, the TC chooses and computes , , . Finally, the TC generates public parameter , system public key , and master key .
- Key generation:The TC executes and generates key for the user who owns attribute set S. Firstly, the TC selects random and chooses for every attribute . Then, it computes , and calculates , . Finally, it generates the user’s attribute key .
- Encryption of medical data:The DOC inputs the medical data M and randomly selects a symmetric key k from the key space, then outputs . The DOC stores to the CS and obtains the storage address . Moreover, the DOC performs a hash operation for ciphertext to obtain the result , which ensures that the medical data on the cloud are neither tampered with nor forged.
- Index generation:The DOC selects random and generates an access control policy tree T with as the secret value. Then, the DOC encrypts the keyword set W. The specific algorithm is shown below:(1) The DOC computes , , , and .(2) For each keyword , the DOC computes .(3) For each leaf node , the DOC computes , .(4) Finally, , .
- Data storage:The DOC puts n in a transaction sheet . If the number of correct node verification results is more than 2/3, the transaction is uploaded to the blockchain. The system obtains the transaction information from the blockchain, constructs the cloud-chain cooperation mapping table according to Dep, and stores it on the cloud, as shown in Table 5.
- Trapdoor generation:(1) The DR selects random and chooses the keyword set .(2) The DR calculates ,, , , and , where .(3) The DR generates the trapdoor .
- Cloud search:The CS runs . According to the medical data type , the CS finds the corresponding medical dataset from the cloud-chain cooperation mapping table and then performs access control policy matching to select the dataset that satisfies the conditions.(1) If x is a leaf node, let , then the CS calculates .(2) If x is a non-leaf node, let be a child node of x. The CS computes if holds, where . If not, .(3) Let , .(4) Finally, the CS outputs the dataset .
- Blockchain search:The BC executes . According to the trapdoor uploaded by the DR, the nodes on the blockchain carry out keyword matching by Equation (10).
- Medical data validation:After successful retrieval, the DR obtains the medical data ciphertext from the CS. The DR executes to verify the hash value. The DR calculates . If , it outputs ; otherwise, it returns .
- Ciphertext decryption:If , the DR calculatesThe correctness of Equation (12) is verified as follows:
6. Security Analysis
6.1. The Security Analysis of Our Scheme under the INDC-SCKA
6.2. The Security Analysis of Our Scheme under the KS-SCSKA
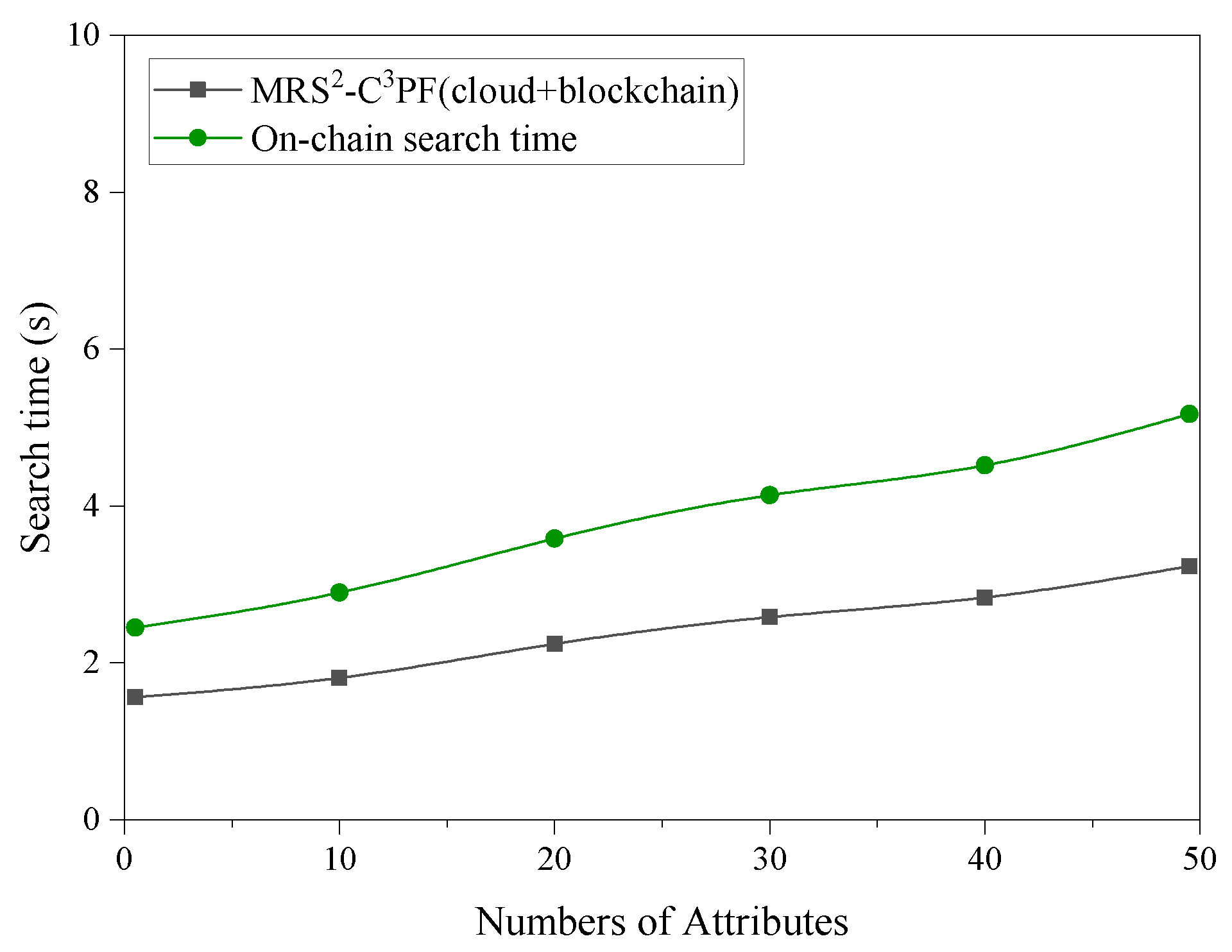
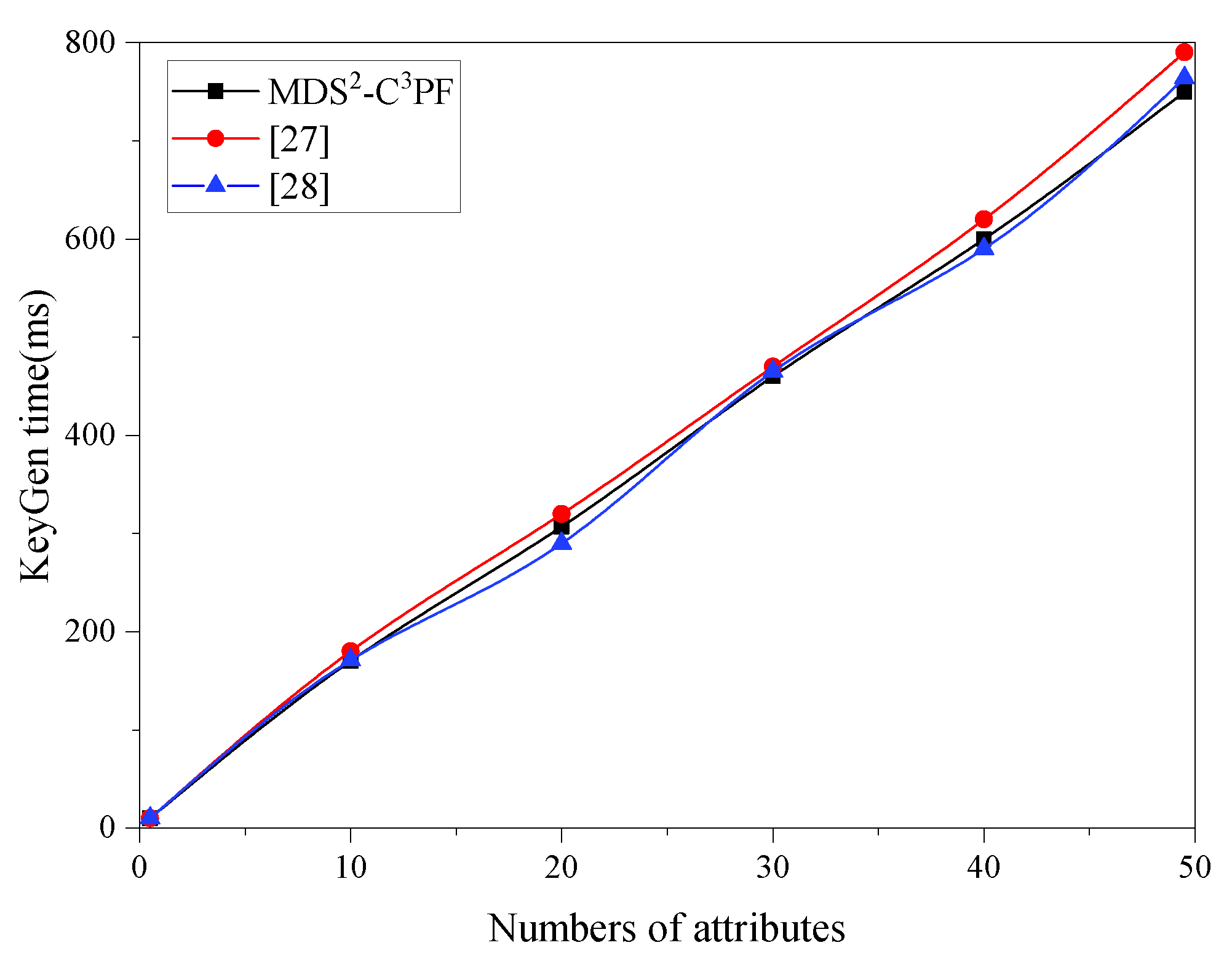
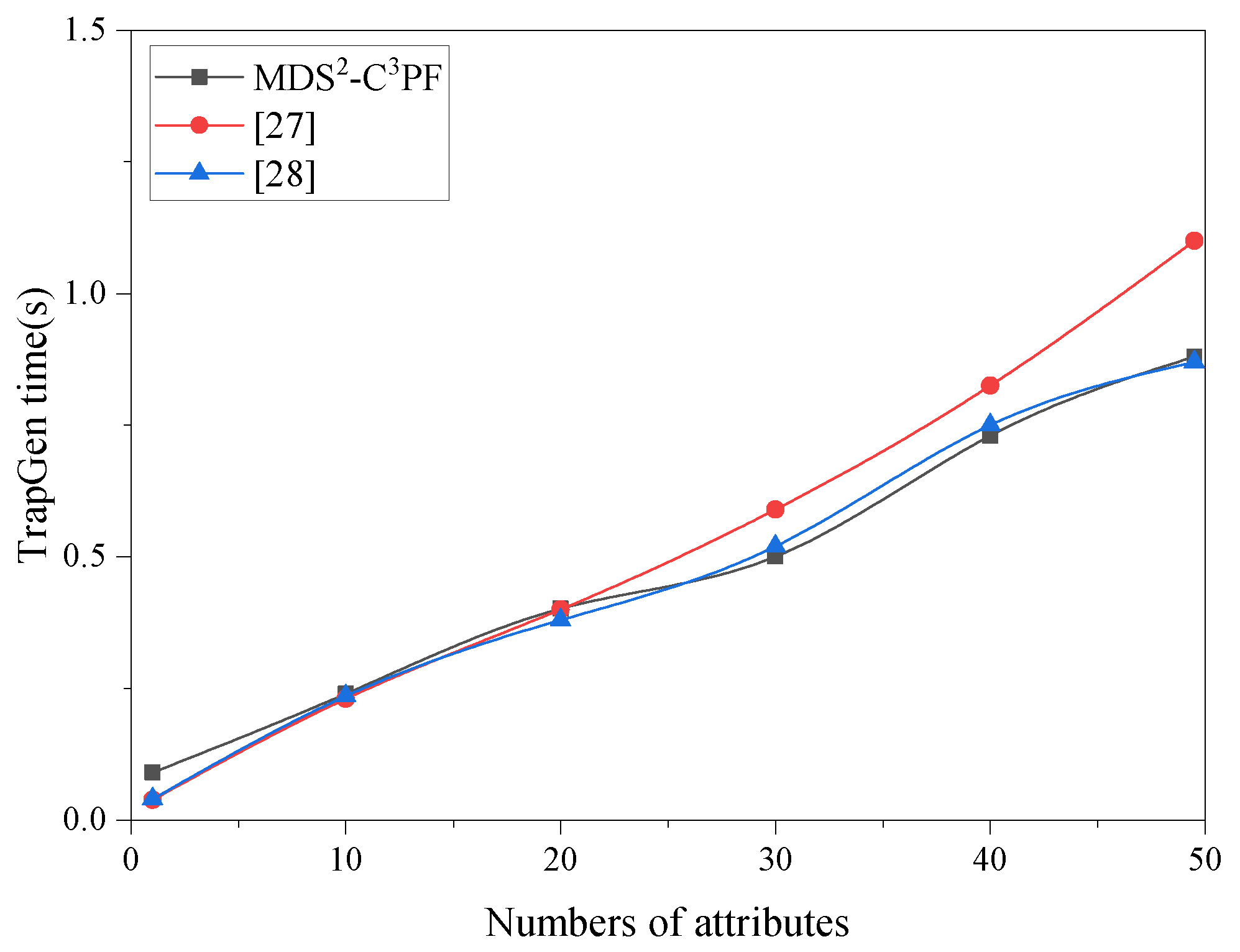
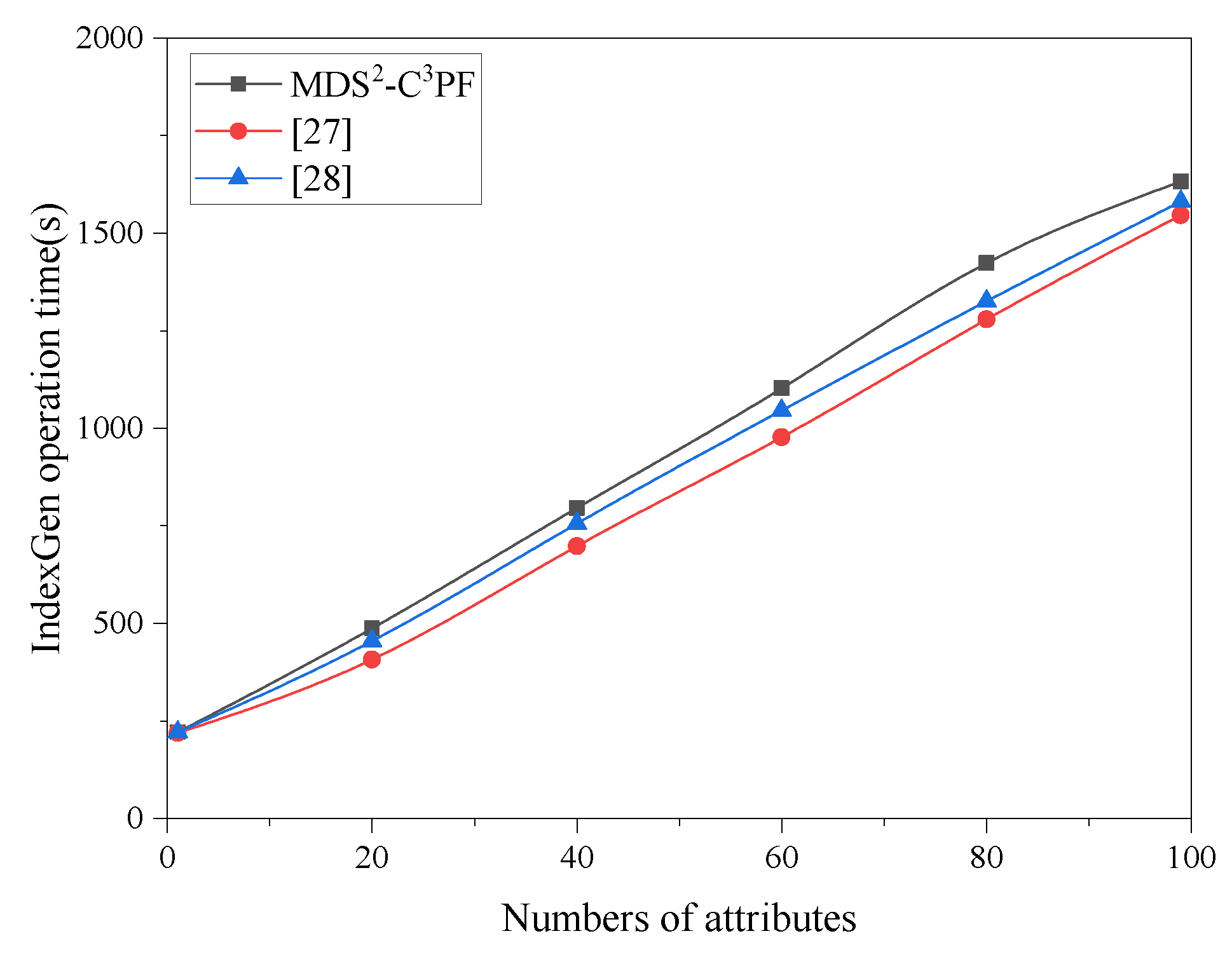
7. Experiments and Performance Analysis
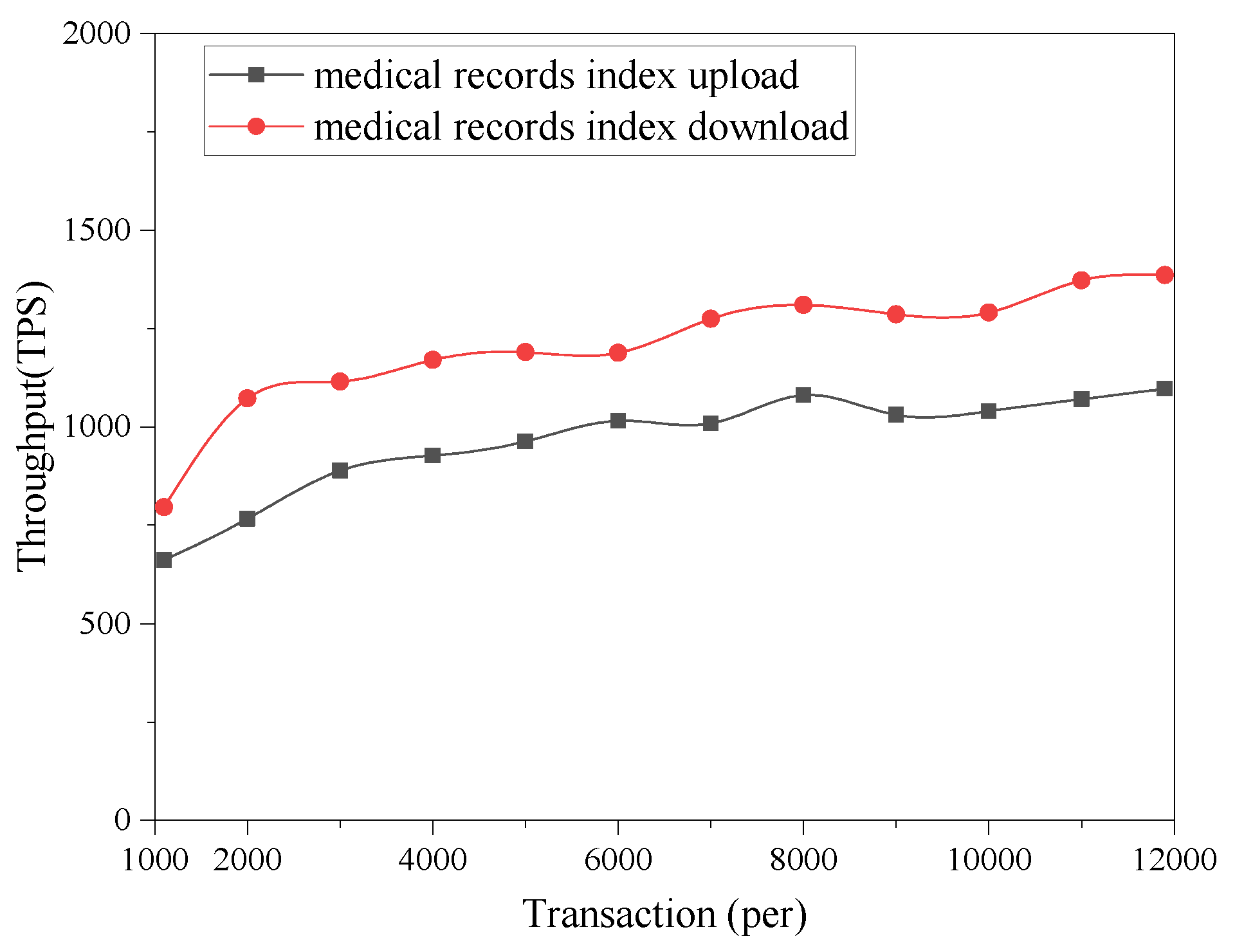
7.1. Blockchain Performance Analysis
7.2. Experimental Analysis
7.2.1. Function Comparison
7.2.2. Complexity Analysis
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A.V. Security and Privacy for Cloud-Based IoT: Challenges, Countermeasures, and Future Directions. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy Identity-Based Encryption; Springer: Berlin, Germany, 2005; pp. 457–473. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ’07), Oakland, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Yin, C.; Wang, H.; Zhou, L.; Fang, L. Ciphertext-policy attribute-based encryption with multi-keyword search over medical cloud data. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 9 February 2021. [Google Scholar]
- Hsieh, G.; Chen, R.J. Design for a secure interoperable cloud-based Personal Health Record service. In Proceedings of the 4th IEEE International Conference on Cloud Computing Technology and Science Proceedings, Taipei, Taiwan, 3–6 December 2012; pp. 472–479. [Google Scholar]
- Sangeetha, D.; Chakkaravarthy, S.S.; Satapathy, S.C.; Vaidehi, V.; Cruz, M.V. Multi keyword searchable attribute based encryption for efficient retrieval of health Records in Cloud. Multimed. Tools Appl. 2022, 81, 22065–22085. [Google Scholar] [CrossRef]
- Boneh, D.; Crescenzo, G.D.; Ostrovsky, R.; Persiano, G. Public Key Encryption with Keyword Search; Springer: Berlin, Germany, 2004; pp. 506–522. [Google Scholar]
- Ding, Y.; Xu, H.; Wang, Y.; Yuan, F.; Liang, H. Secure Multi-Keyword Search and Access Control over Electronic Health Records in Wireless Body Area Networks. Secur. Commun. Netw. 2021. [Google Scholar] [CrossRef]
- Ramu, G.; Reddy, B.E.; Jayanthi, A.; Prasad, L.V. Fine-grained access control of EHRs in cloud using CP-ABE with user revocation. Health Technol. 2019, 9, 487–496. [Google Scholar] [CrossRef]
- Zheng, Z.B.; Xie, S.A.; Dai, H.N.; Wang, H. Blockchain challenges and opportunities: A survey. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Xu, C.; Fulong, C.; Dong, X.; Sun, H.; Huang, C. Design of a Secure Medical Data Sharing Scheme Based on Blockchain. J. Med. Syst. 2020, 44, 52. [Google Scholar]
- Gai, K.; Guo, J.; Zhu, L.; Yu, S. Blockchain Meets Cloud Computing: A Survey. IEEE Commun. Surv. Tutorials 2020, 22, 2009–2030. [Google Scholar] [CrossRef]
- Chen, L.; Lee, W.K.; Chang, C.C.; Choo, K.K.R.; Zhang, N. Blockchain based searchable encryption for electronic health record sharing. Future Gener. Comput. Syst. 2019, 95, 420–429. [Google Scholar] [CrossRef]
- Gupta, B.B.; Li, K.C.; Leung, V.C.; Psannis, K.E.; Yamaguchi, S. Blockchain-Assisted Secure Fine-Grained Searchable Encryption for a Cloud-Based Healthcare Cyber-Physical System. IEEE/CAA J. Autom. Sin. 2021, 8, 1877–1890. [Google Scholar]
- Han, D.; Pan, N.; Li, K. A Traceable and Revocable Ciphertext-Policy Attribute-based Encryption Scheme Based on Privacy Protection. IEEE Trans. Dependable Secur. Comput. 2022, 19, 316–327. [Google Scholar] [CrossRef]
- Li, Q.; Xia, B.; Huang, H.; Zhang, Y.; Zhang, T. TRAC: Traceable and revocable access control scheme for mHealth in 5G-enabled IIoT. IEEE Trans. Ind. Inform. 2021, 18, 3437–3448. [Google Scholar] [CrossRef]
- Hu, G.; Zhang, L.; Mu, Y.; Gao, X. An Expressive “Test-Decrypt-Verify” Attribute-Based Encryption Scheme with Hidden Policy for Smart Medical Cloud. IEEE Syst. J. 2020, 15, 365–376. [Google Scholar] [CrossRef]
- Sowjanya, K.; Dasgupta, M.; Ray, S. A lightweight key management scheme for key-escrow-free ECC-based CP-ABE for IoT healthcare systems. J. Syst. Archit. 2021, 117, 102108. [Google Scholar] [CrossRef]
- Hwang, Y.W.; Lee, I.Y. A Study on CP-ABE-Based Medical Data Sharing System with Key Abuse Prevention and Verifiable Outsourcing in the IoMT Environment. Sensors 2020, 20, 4934. [Google Scholar] [CrossRef]
- Liu, J.; Wu, M.; Sun, R.; Du, X.; Guizani, M. BMDS: A Blockchain-based Medical Data Sharing Scheme with Attribute-Based Searchable Encryption. In Proceedings of the ICC 2021-IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Wang, S.; Wang, H.; Li, J.; Wang, H.; Chaudhry, J.; Alazab, M.; Song, H. A fast CP-ABE system for cyber-physical security and privacy in mobile healthcare network. IEEE Trans. Ind. Appl. 2022, 56, 4467–4477. [Google Scholar] [CrossRef]
- Li, H.; Yang, Y.; Dai, Y.; Yu, S.; Xiang, Y. Achieving Secure and Efficient Dynamic Searchable Symmetric Encryption over Medical Cloud Data. IEEE Trans. Cloud Comput. 2020, 8, 484–494. [Google Scholar] [CrossRef]
- Mingwu, Z.; Yu, C.; Jiajun, H. SE-PPFM: A Searchable Encryption Scheme Supporting Privacy-Preserving Fuzzy Multikeyword in Cloud Systems. IEEE Syst. J. 2021, 15, 2980–2988. [Google Scholar]
- Payal, C.; Manik, L.D. Privacy Preserving Searchable Encryption with Fine-Grained Access Control. IEEE Trans. Cloud Comput. 2021, 9, 753–762. [Google Scholar]
- Shahzaib, T.; Sushmita, R.; Yogachandran, R.; Rajarajan, M.; Glackin, C. A New Secure and Lightweight Searchable Encryption Scheme over Encrypted Cloud Data. IEEE Trans. Emerg. Top. Comput. 2019, 7, 530–544. [Google Scholar]
- Sun, W.; Yu, S.; Lou, W.; Hou, Y.T.; Li, H. Protecting your right: Verifiable attribute-based keyword search with fine-grained owner-enforced search authorization in the cloud. IEEE Trans. Parallel Distrib. Syst. 2014, 27, 1187–1198. [Google Scholar] [CrossRef]
- Zheng, Q.; Xu, S.; Ateniese, G. VABKS: Verifiable attribute-based keyword search over outsourced encrypted data. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April 2014; pp. 522–530. [Google Scholar]
- Liu, S.; Yu, J.; Xiao, Y.; Wan, Z.; Wang, S.; Yan, B. BC-SABE: Blockchain-Aided Searchable Attribute-Based Encryption for Cloud-IoT. IEEE Internet Things J. 2020, 7, 7851–7867. [Google Scholar] [CrossRef]
- Liu, J.; Li, X.; Ye, L.; Zhang, H.; Du, X.; Guizani, M. BPDS: A blockchain based privacy-preserving data sharing for electronic medical records. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Cao, S.; Zhang, G.; Liu, P.; Zhang, X.; Neri, F. Cloud-assisted secure eHealth systems for tamper-proofing EHR via blockchain. Inf. Sci. 2019, 485, 427–440. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, T.; Wu, Q.; Mu, Y.; Rezaeibagha, F. Secure Decentralized Attribute-Based Sharing of Personal Health Records with Blockchain. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Munagala, N.V.L.M.; Rani, A.; Reddy, D.V. Blockchain-Based Internet-of-Things for Secure Transmission of Medical Data in Rural Areas. Comput. J. 2022. [Google Scholar] [CrossRef]
- Chen, W.; Zhu, S.; Li, J.; Wu, J.; Chen, C.L.; Deng, Y.Y. Authorized Shared Electronic Medical Record System with Proxy Re-Encryption and Blockchain Technology. Sensors 2021, 21, 7765. [Google Scholar] [CrossRef] [PubMed]
- Saini, A.; Zhu, Q.; Singh, N.; Xiang, Y.; Gao, L.; Zhang, Y. A Smart-Contract-Based Access Control Framework for Cloud Smart Healthcare System. IEEE Internet Things J. 2021, 8, 5914–5925. [Google Scholar] [CrossRef]
- Chen, C.L.; Deng, Y.Y.; Weng, W.; Sun, H.; Zhou, M. A blockchain-based secure inter-hospital EMR sharing system. Appl. Sci. 2020, 10, 4958. [Google Scholar] [CrossRef]
- Yang, L.; Jiguo, L. Efficient searchable public key encryption against keyword guessing attacks for cloud-based EMR systems. Clust. Comput. 2018, 22, 285–299. [Google Scholar]
- Chen, N.; Li, J.; Zhang, Y.; Guo, Y. Efficient CP-ABE scheme with shared decryption in cloud storage. IEEE Trans. Comput. 2020, 71, 175–184. [Google Scholar] [CrossRef]
- Xiao, Q.; Tan, K.L. Peer-aware collaborative access control in social networks. In Proceedings of the 8th International Conference on Collaborative Computing: Networking, Applications and Worksharing (CollaborateCom), Pittsburgh, PA, USA, 14–17 October 2012; pp. 30–39. [Google Scholar]

| Symbols | Description |
|---|---|
| Public parameter | |
| System public key | |
| Master key | |
| M | Medical data |
| Medical data ciphertext | |
| Private key | |
| H | Medical data ciphertext hash |
| k | Encryption key for medical data |
| P | Balance score matrix |
| Y | Impact score matrix |
| X | Intention score matrix |
| W | Keyword set |
| T | Access control policy tree |
| Storage Address |
| PA | ||
| DOC |
| PA | DOC | |
|---|---|---|
| PA | 1 | |
| DOC | 1 |
| PA | ||
| DOC |
| Department | Ledger ID | Block Number | Transaction Hash | Partial Ciphertext Index |
|---|---|---|---|---|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pan, H.; Zhang, Y.; Si, X.; Yao, Z.; Zhao, L. MDS2-C3PF: A Medical Data Sharing Scheme with Cloud-Chain Cooperation and Policy Fusion in IoT. Symmetry 2022, 14, 2479. https://doi.org/10.3390/sym14122479
Pan H, Zhang Y, Si X, Yao Z, Zhao L. MDS2-C3PF: A Medical Data Sharing Scheme with Cloud-Chain Cooperation and Policy Fusion in IoT. Symmetry. 2022; 14(12):2479. https://doi.org/10.3390/sym14122479
Chicago/Turabian StylePan, Heng, Yaoyao Zhang, Xueming Si, Zhongyuan Yao, and Liang Zhao. 2022. "MDS2-C3PF: A Medical Data Sharing Scheme with Cloud-Chain Cooperation and Policy Fusion in IoT" Symmetry 14, no. 12: 2479. https://doi.org/10.3390/sym14122479
APA StylePan, H., Zhang, Y., Si, X., Yao, Z., & Zhao, L. (2022). MDS2-C3PF: A Medical Data Sharing Scheme with Cloud-Chain Cooperation and Policy Fusion in IoT. Symmetry, 14(12), 2479. https://doi.org/10.3390/sym14122479









