A Digital Media Subscription Management System Combined with Blockchain and Proxy Re-Encryption Mechanisms
Abstract
1. Introduction
1.1. Background
1.2. Research Goals and Threat Model
- (1)
- Decentralization for information sharing: In the blockchain network architecture, decentralized bookkeeping and storage are adopted. All nodes have the same rights and obligations. Therefore, any error or shutdown of any node will not affect the operation of the entire blockchain network.
- (2)
- Openness and privacy: The sharing of digital media and the protection of the interests of creators, at first glance, are opposite things. By using the ECDSA-based blockchain mechanism combined with the encryption mechanism of the public key system, in addition to the encrypted private information of the transaction subject, the signature data information stored in the blockchain is also open and transparent. All members of the same alliance can verify the correctness of the message and reduce the asymmetry of data, which is the openness of the blockchain system. In addition, the plaintext of the message is also encrypted by the public key, and only the members of the alliance with the corresponding private key can decrypt the message settings to achieve privacy protection.
- (3)
- Proxy re-encryption for access control: Behind the alliance chain combined with blockchain technology, different creators can store their works on the digital media cloud. Blockchain technology can protect data security in the blockchain through a public key system. The system not only allows authorized parties to access encrypted data through their private keys, but also ensures that the database and the core data will not be leaked. To protect the interests of creators, a proxy re-encryption mechanism can also be applied. Only parties can view individual contracts, and the key lies in the hands of media creators. Licensees can access digital media through keys issued by the media creator only if authorized by the media creator. When the licensee arbitrarily shares the digital media with others, the media creator can revoke the access right of the licensee at any time. Through the proxy re-encryption mechanism, the access rights of alliance members can be effectively controlled to achieve access control.
- (4)
- Verifiable: The sender’s message will be signed by the sender, and the receiver can verify the authenticity of the signature. The message sender will sign with his/her private key, and the message receiver will verify with the message sender’s public key.
- (5)
- Traceable: Blockchain technology ensures that all parties have equal rights to choose and know, anything exchanged between two roles is auditable. All transaction information is accessible to all participants in the alliance. Due to the distributed storage and verification feature, the blockchain system will synchronize all changed records. In the event of disputes in the future, there is data to prove that the rights and interests of any two roles are protected.
- (6)
- Mutual authentication: The legality of the sender’s and receiver’s identity must be able to be verified. The BAN logic proof is applied to determine whether mutual authentication is achieved between the two parties. Mutual authentication is achieved once the sender and receiver mutually verify the legality of each other’s identities.
- (7)
- Integrity and unforgery: The timestamp and signature mechanism is applied to ensure the transmitted message is not tampered with; it can also ensure the integrity of the message in the communication process.
- (8)
- Non-repudiation: The data is stored forever once it is verified and added to the blockchain, and the inherent time stamping feature of the blockchain system records the time of creation. Modifying the content of messages that have been uploaded to the Blockchain Center requires the control of more than 51% of the consortium members, which will be difficult to achieve.
- (9)
- Resist Sybil attacks: The transmitted messages can be intercepted by an attacker, and the attacker will send illegitimate messages to legal users. To protect transmitted messages, the ECDSA system can be applied. Therefore, an attacker cannot properly intercept important information when conducting a Sybil attack.
2. Preliminary
2.1. Smart Contract
2.2. ECDSA
2.3. Hyperledger Fabric
3. The Proposed Scheme
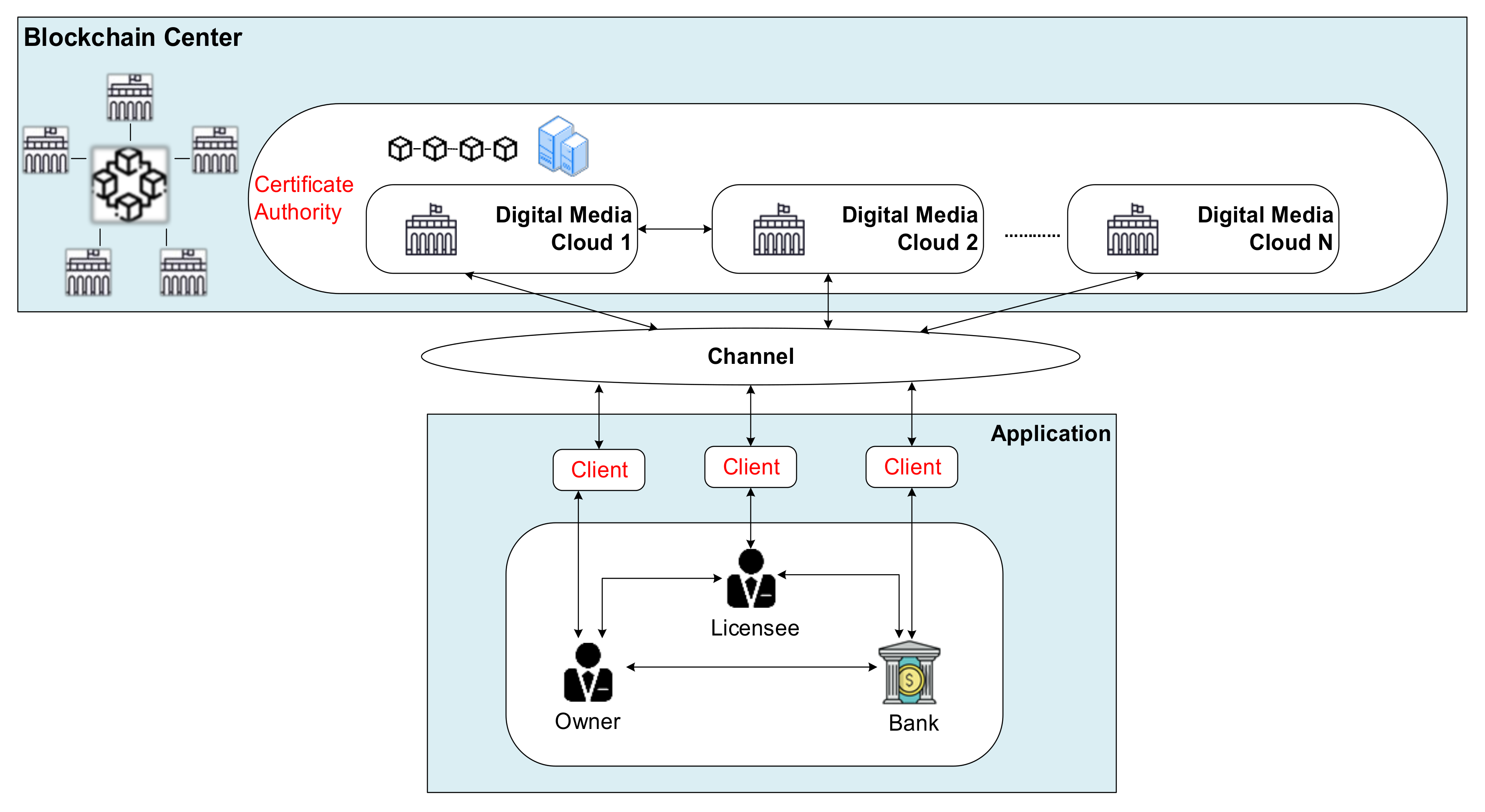
3.1. System Architecture
- Step 1:
- Certificate Authority (CA), Digital Media Cloud (DMC), Owner (OR), Licensee (LE), and Bank (BK) must register with the Blockchain Center to obtain public and private keys for message encryption/decryption, and ECDSA signature key.
- Step 2:
- Media-related institutions form the Digital Media Cloud, and the media-related data of each institution will be stored in the Digital Media Cloud, and access rights will be controlled through the access control mechanism. All relevant information is also uploaded to the Blockchain Center through Certificate Authority.
- Step 3:
- If the Licensee wishes to purchase digital media content from the Owner, the Owner will inform the Licensee of the fees and payment methods for the digital media. Licensee goes to the Bank for payment. After the payment is completed, Licensee will get a payment receipt. The licensee provides proof of payment to the Owner, who in turn provides the Licensee with the right to use the digital media. All relevant information is also uploaded to the Blockchain Center through the Certificate Authority.
- Step 4:
- The Owner uploads the digital content purchased by the Licensee to the Digital Media Cloud for proxy re-encryption. Licensee can obtain the re-encrypted media data through the Digital Media Cloud and obtain the relevant content for research after decryption. All relevant information is also uploaded to the Blockchain Center through the Certificate Authority.
3.2. Notation
| q | A q-bit prime number |
| GF(q) | Finite group q |
| E | The elliptic curve defined on finite group q |
| G | A generating point based on the elliptic curve E |
| IDx | A name representing identity x |
| kx-y | A random value on the elliptic curve of x to y |
| (rx-y, sx-y) | Elliptic curve signature value of x to y |
| Mx-y | A message from x to y |
| IDBC | An index value of blockchain message |
| BCx-y | Blockchain message of x to y |
| TSx-y | Timestamp message of x to y |
| ΔT | Checks if the difference between two timestamps is less than a specified timestamp |
| Encrypt a message M using the asymmetric public key of x | |
| Decrypt a message M using the asymmetric private key of x | |
| Encx-y | Encrypted message using the asymmetric key of x to y |
| Certx | The certificate of role x conforms to the X.509 standard |
| c1, c2 | The proxy re-encryption message content |
| a, b | The private key pair for proxy re-encryption |
| keyx_y | The proxy re-encryption session key of roles x and y |
| h(.) | Hash function |
| Verify whether A is equal to B |
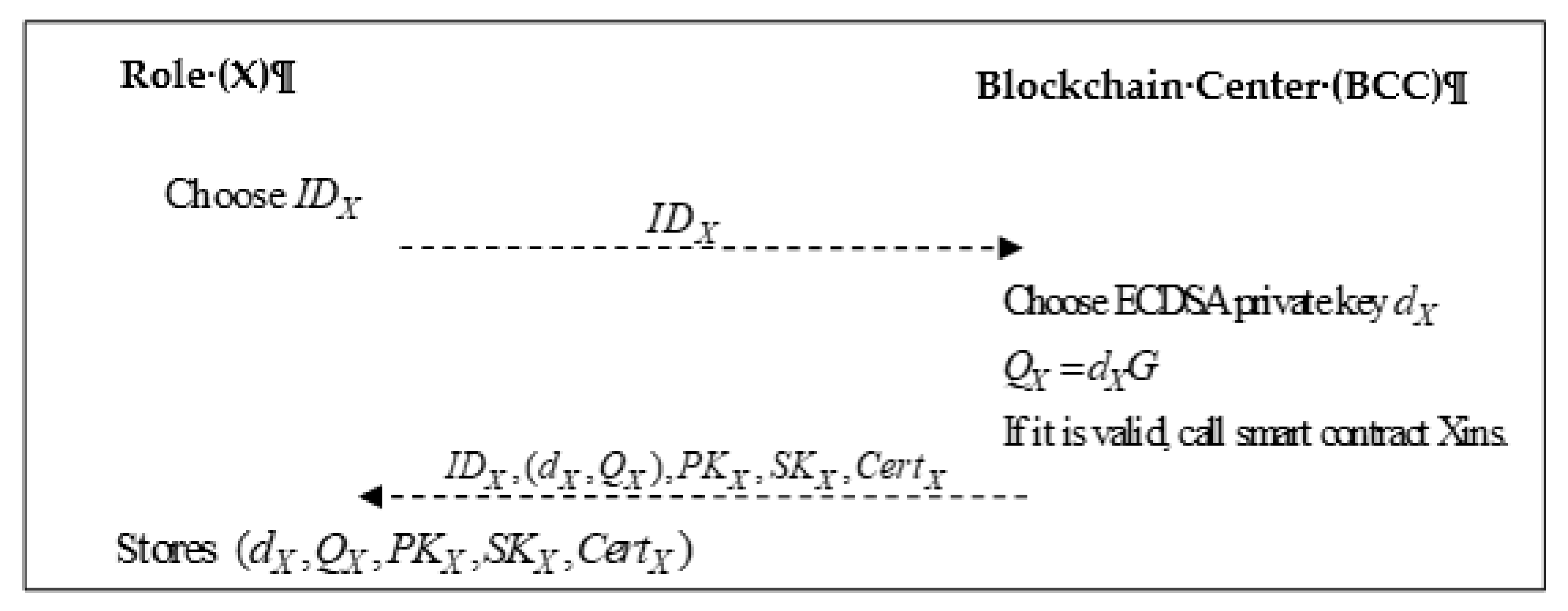
3.3. Registration Phase
- Step 1:
- Role X generates an identity IDx, and sends it to the Blockchain Center.
- Step 2:
- The Blockchain Center generates an ECDSA private key dx based on the role X, calculating
| Algorithm 1. Smart contract Xins of the proposed scheme. |
| function inserted X smart contract Xins ( string X_id, string X_detail) { count++; X[count].id = id; X[count].detail = detail; } string X_keypairs; |
- Step 3:
- The role X stores .
3.4. Smart Contract Initialization
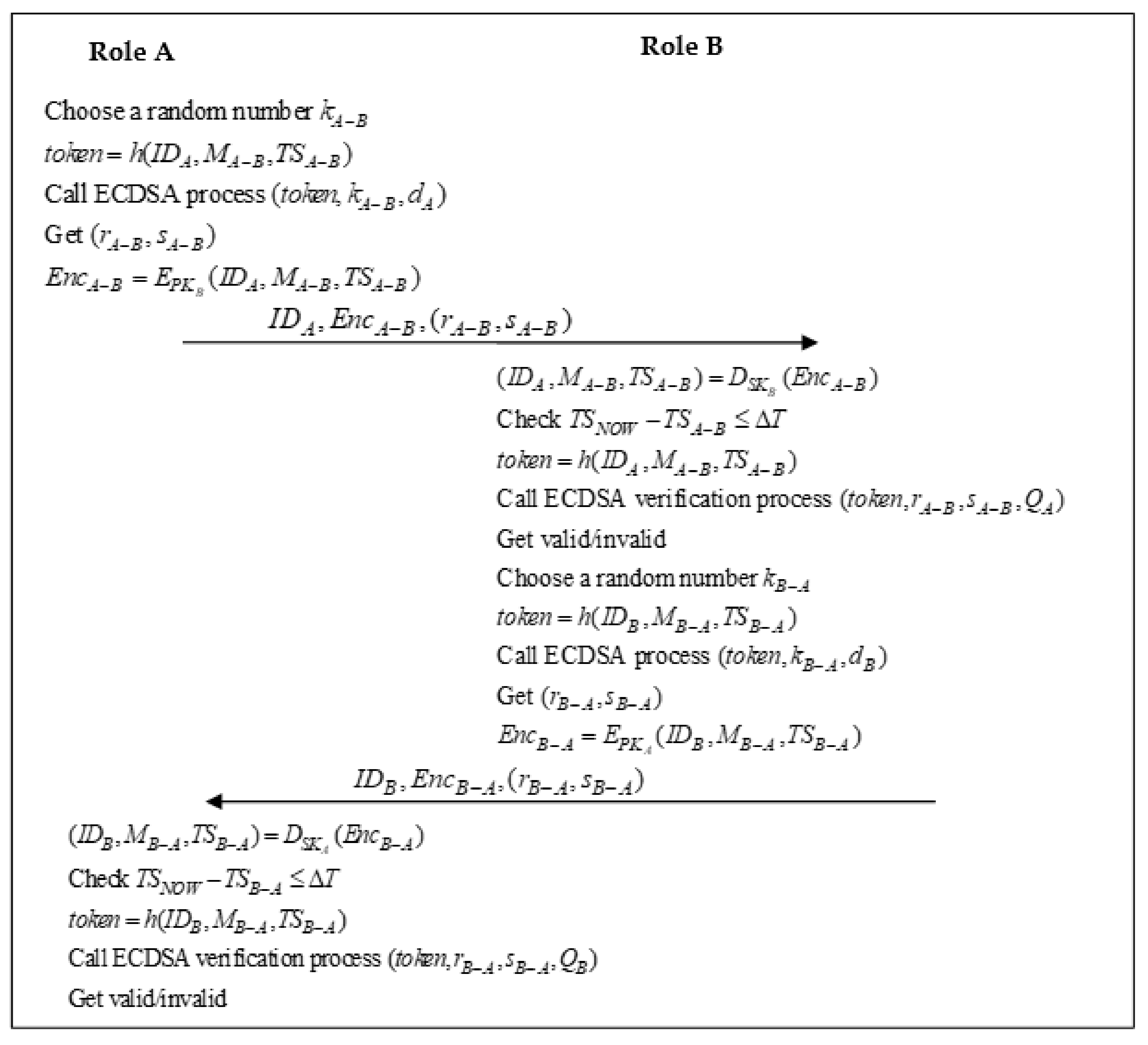
3.5. ECDSA Authentication Process
| Algorithm 2. ECDSA process between role A and role B. |
| string token, kA − B, dA; function ECDSA process (token, kA − B, dA) zA − B = token; (XA − B, yA − B) = kA − BG rA − B = XA − B mod n SA − B = kA − B−1 (zA − B + rA − B dA) mod n return (rA − B, sA − B); |
| Algorithm 3. ECDSA verification process between role A and role B |
| string token, rA − B, sA − B, QA; function ECDSA verification process (rA − B, sA − B, QA) zA − B’ = token; (uA − B1 = zA − B’ sA − B−1 mod n uA − B2 = rA − B sA − B−1 mod n; (xA − B’, yA − B’) = uA − B1G + uA − B2 QA; check if xA − B’ = rA − B mod n; return valid/invalid; |
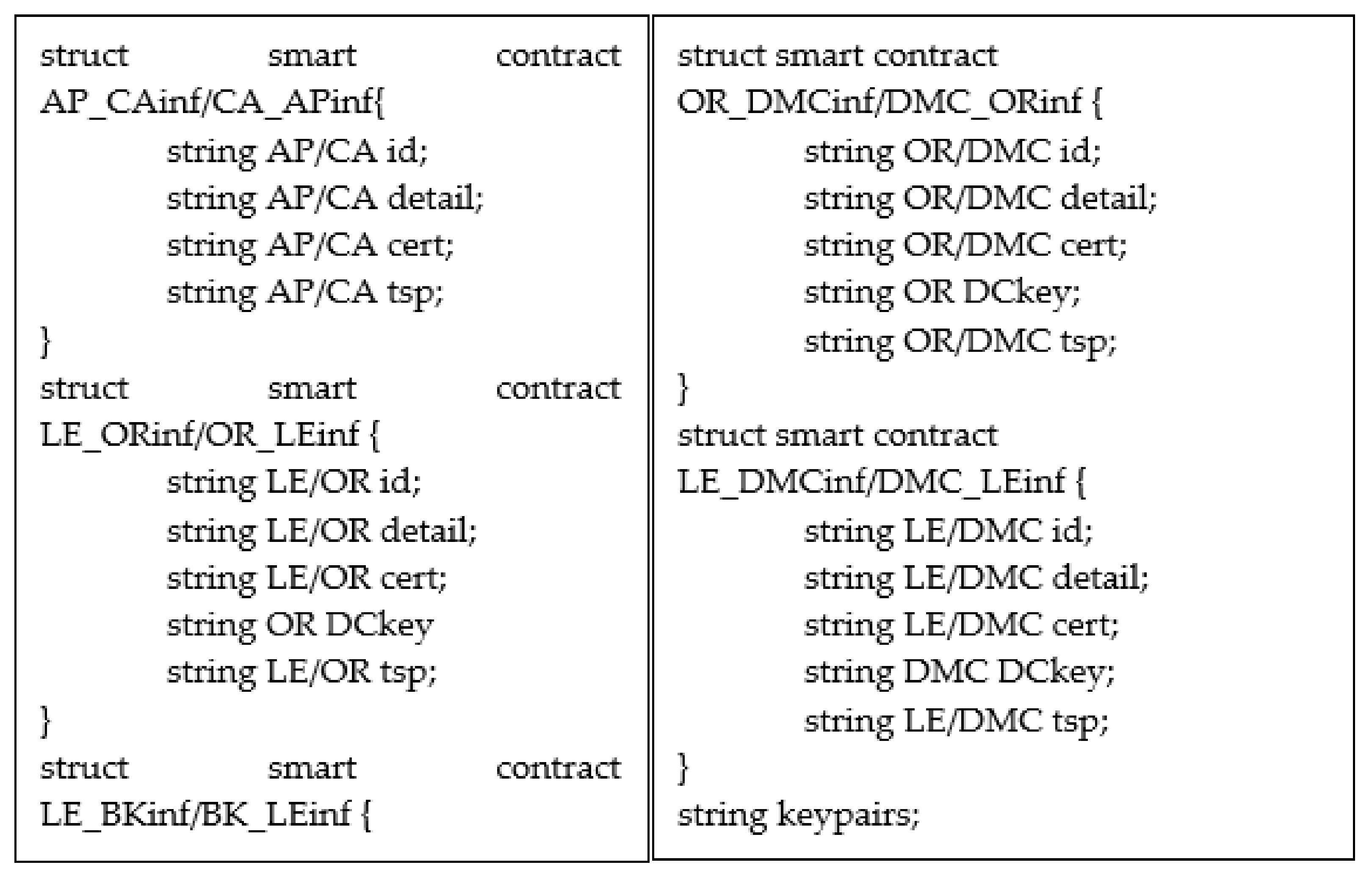
3.6. CA Communication Process
| Algorithm 4. Smart contract AP_CAins and AP_CAchk of the proposed scheme. |
| function insert smart contract AP_CAins (string AP_id, string AP_detail, string AP_cert, string AP_tsp) { count++; AP[count].id = id; AP[count].detail = detail; AP[count].cert = cert; AP[count].tsp = tsp; } sign string AP_key (AP_id, AP_detail, AP_cert, AP_tsp); verify string AP_key (AP_id, AP_detail, AP_cert, AP_tsp); function check smart contract AP_CAchk (string AP_id, string AP_detail, string AP_cert, string AP_tsp) { return AP_id.exist; return AP_detail.exist; return AP_cert.exist; return AP_tsp.exist; } |
| Algorithm 5. Smart contract CA_APins and CA_APchk of the proposed scheme. |
| function insert smart contract CA_APins (string CA_id, string CA _detail, string CA _cert, string CA _tsp) { count++; CA[count].id = id; CA[count].detail = detail; CA[count].cert = cert; CA[count].tsp = tsp; } sign string CA_key (CA_id, CA _detail, CA _cert, CA _tsp); verify string CA _key (CA _id, CA _detail, CA _cert, CA _tsp); function check smart contract CA_APchk (string CA _id, string CA _detail, string CA _cert, string CA _tsp){ return CA_id.exist; return CA_detail.exist; return CA_cert.exist; return CA_tsp.exist; } |
3.7. Subscription Negotiation Phase
| Algorithm 6. Smart contract LE_ORins and LE_ORchk of the proposed scheme |
| function insert smart contract LE_ORins (string LE_id, string LE_detail, string LE_cert, string LE_tsp) { count++; LE[count].id = id; LE[count].detail = detail; LE[count].cert = cert; LE[count].tsp = tsp; } sign string LE_key (LE_id, LE_detail, LE_cert, LE_tsp); verify string LE_key (LE_id, LE_detail, LE_cert, LE_tsp); function check smart contract LE_ORchk (string LE_id, string LE_detail, string LE_cert, string LE_tsp) { return LE_id.exist; return LE_detail.exist; return LE_cert.exist; return LE_tsp.exist; } |
| Algorithm 7. Smart contract OR_LEins and OR_LEchk of the proposed scheme |
| function insert smart contract OR_LEins (string OR_id, string OR_detail, string OR_cert, string OR_tsp) { count++; OR[count].id = id; OR[count].detail = detail; OR[count].cert = cert; OR[count].tsp = tsp; } sign string OR_key (OR_id, OR_detail, OR_cert, OR_tsp); verify string OR_key (OR_id, OR_detail, OR_cert, OR_tsp); function check smart contract OR_LEchk (string OR_id, string OR_detail, string OR_cert, string OR_tsp) { return OR_id.exist; return OR_detail.exist; return OR_cert.exist; return OR_tsp.exist; } |
3.8. Bank Payment Phase
| Algorithm 8. Smart contracts LE_BKins and LE_BKchk of the proposed scheme |
| function insert smart contract LE_BKins (string LE_id, string LE_detail, string LE_cert, string LE_tsp) { count++; LE[count].id = id; LE[count].detail = detail; LE[count].cert = cert; LE[count].tsp = tsp; } sign string LE_key (LE_id, LE_detail, LE_cert, LE_tsp); verify string LE_key (LE_id, LE_detail, LE_cert, LE_tsp); function check smart contract LE_BKchk (string LE_id, string LE_detail, string LE_cert, string LE_tsp) { return LE_id.exist; return LE_detail.exist; return LE_cert.exist; return LE_tsp.exist; } |
| Algorithm 9. Smart contract BK_LEins and BK_LEchk of the proposed scheme. |
| function insert smart contract BK_LEins (string BK_id, string BK_detail, string BK_cert, string BK_tsp) { count++; BK[count].id = id; BK[count].detail = detail; BK[count].cert = cert; BK[count].tsp = tsp; } sign string BK_key (BK_id, BK_detail, BK_cert, BK_tsp); verify string BK_key (BK_id, BK_detail, BK_cert, BK_tsp); function check smart contract BK_LEchk (string BK_id, string BK_detail, string BK_cert, string BK_tsp) { return BK_id.exist; return BK_detail.exist; return BK_cert.exist; return BK_tsp.exist; } |
3.9. Subscription Confirmation Phase
| Algorithm 10. Smart contract CA_APins and CA_APchk of the proposed scheme. |
| function insert smart contract LE_ORins (string LE_id, string LE_detail, string LE_cert, string LE_tsp) { count++; LE[count].id = id; LE[count].detail = detail; LE[count].cert = cert; LE[count].tsp = tsp; } sign string LE_key (LE_id, LE_detail, LE_cert, LE_tsp); verify string LE_key (LE_id, LE_detail, LE_cert, LE_tsp); function check smart contract LE_ORchk (string LE_id, string LE_detail, string LE_cert, string LE_tsp) { return LE_id.exist; return LE_detail.exist; return LE_cert.exist; return LE_tsp.exist; } |
| Algorithm 11. Smart contract OR_LEins and OR_LEchk of the proposed scheme. |
| function insert smart contract OR_LEins (string OR_id, string OR_detail, string OR_cert, string OR_DCkey, string OR_tsp) { count++; OR[count].id = id; OR[count].detail = detail; OR[count].cert = cert; OR[count]. DCkey = DCkey; OR[count].tsp = tsp; } sign string OR_key (OR_id, OR_detail, OR_cert, OR_DCkey, OR_tsp); verify string OR_key (OR_id, OR_detail, OR_cert, OR_DCkey, OR_tsp); function check smart contract OR_LEchk (string OR_id, string OR_detail, string OR_cert, string OR_DCkey, string OR_tsp) { return OR_id.exist; return OR_detail.exist; return OR_cert.exist; return OR_DCkey; return OR_tsp.exist; } |
3.10. Proxy Re-Encryption and Proxy-Key Update Phase
| Algorithm 12. Proxy-key generation process between role A and role B. |
| string keyX − Y, a, gk function proxy-key process (keyX − Y, a, gk) c1 = keyX − Y gak mod p; c2 = gk mod p; return (c1, c2); |
| Algorithm 13. Smart contract OR_DMCins and OR_DMCchk of the proposed scheme. |
| function insert smart contract OR_DMCins (string OR_id, string OR_detail, string OR_cert, string OR_DCkey, string OR_tsp) { count++; OR[count].id = id; OR[count].detail = detail; OR[count].cert = cert; OR[count].DCkey = DCkey; OR[count].tsp = tsp; } sign string OR_key (OR_id, OR_detail, OR_cert, OR_DCkey, OR_tsp); verify string OR_key (OR_id, OR_detail, OR_cert, OR_DCkey, OR_tsp); function check smart contract OR_DMCchk (string OR_id, string OR_detail, string OR_cert, string OR_DCkey, string OR_tsp) { return OR_id.exist; return OR_detail.exist; return OR_cert.exist; return OR_DCkey.exist; return OR_tsp.exist; } |
| Algorithm 14. Smart contract DMC_ORins and DMC_ORchk of the proposed scheme. |
| function insert smart contract DMC_ORins (string DMC_id, string DMC_detail, string DMC_cert, string DMC_tsp) { count++; DMC[count].id = id; DMC[count].detail = detail; DMC[count].cert = cert; DMC[count].tsp = tsp; } sign string DMC_key (DMC_id, DMC_detail, DMC_cert, DMC_tsp); verify string DMC_key (DMC_id, DMC_detail, DMC_cert, DMC_tsp); function check smart contract DMC_ORchk (string DMC_id, string DMC_detail, string DMC_cert, string DMC_tsp) { return DMC_id.exist; return DMC_detail.exist; return DMC_cert.exist; return DMC_tsp.exist; } |
3.11. Digital Media Browsing Phase
| Algorithm 15. Smart contract LE_DMCins and LE_DMCchk of the proposed scheme. |
| function insert smart contract LE_DMCins (string LE_id, string LE_detail, string LE_cert, string LE_tsp) { count++; LE[count].id = id; LE[count].detail = detail; LE[count].cert = cert; LE[count].tsp = tsp; } sign string LE_key (LE_id, LE_detail, LE_cert, LE_tsp); verify string LE_key (LE_id, LE_detail, LE_cert, LE_tsp); function check smart contract LE_DMCchk (string LE_id, string LE_detail, string LE_cert, string LE_tsp) { return LE_id.exist; return LE_detail.exist; return LE_cert.exist; return LE_tsp.exist; } |
| Algorithm 16. Smart contract DMC_LEins and DMC_LEchk of the proposed scheme. |
| function insert smart contract DMC_LEins (string DMC_id, string DMC_detail, string DMC_cert, string DMC_DCkey, string DMC_tsp) { count++; DMC[count].id = id; DMC[count].detail = detail; DMC[count].cert = cert; DMC[count].DCkey = DCkey; DMC[count].tsp = tsp; } sign string DMC_key (DMC_id, DMC_detail, DMC_cert, DMC_ DCkey, DMC_tsp); verify string DMC_key (DMC_id, DMC_detail, DMC_cert, DMC_ DCkey, DMC_tsp); function check smart contract DMC_LEchk (string DMC_id, string DMC_detail, string DMC_cert, string DMC_DCkey, string DMC_tsp) { return DMC_id.exist; return DMC_detail.exist; return DMC_cert.exist; return DMC_DCkey.exist; return DMC_tsp.exist; } |
3.12. Arbitration Mechanism Phase
4. Security Analysis
4.1. Decentralization and Information Sharing
4.2. Openness and Privacy
4.3. Proxy Re-Encryption for Access Control
4.4. Verifiable
4.5. Traceable
4.6. Mutual Authentication
- Role B authenticates role A.
4.7. Integrity and Unforgery
4.8. Non-Repudiation
4.9. Resist Sybil Attack
- Scenario:
- The attacker intercepts the message from the sender to the receiver and tampers with the message before sending it to the receiver.
- Analysis:
- The attacker will fail because our proposed method uses a public key to encrypt data as follows.
5. Discussions
5.1. Computation Cost
5.2. Communication Performance
5.3. Characteristic Comparison
5.4. Limitations
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ballhaus, W.; Chow, W. Perspectives from the Global Entertainment & Media Outlook 2020–2024. 2020. Available online: https://www.pwc.com/gx/en/entertainment-media/outlook-2020/perspectives.pdf (accessed on 30 August 2022).
- Perez, S.S.; Vizoso, A.; Lopez, G.X. Accepting the Digital Challenge: Business Models and Audience Participation in Online Native Media. J. Media 2020, 1, 78–91. [Google Scholar]
- Eriksson, C.I.; Akesson, M.; Lund, J. Designing Ubiquitous Media Services—Exploring the Two-Sided Market of Newspapers. J. Theor. Appl. Electron. Commer. Res. 2016, 11, 1–19. [Google Scholar] [CrossRef]
- Evans, W.D.; Abroms, L.C.; Broniatowski, D.; Napolitano, M.A.; Arnold, J.; Ichimiya, M.; Agha, S. Digital Media for Behavior Change: Review of an Emerging Field of Study. Int. J. Environ. Res. Public Health 2022, 19, 9129. [Google Scholar] [CrossRef]
- Saboor, A.; Hassan, M.F.; Akbar, R.; Shah SN, M.; Hassan, F.; Magsi, S.A.; Siddiqui, M.A. Containerized Microservices Orchestration and Provisioning in Cloud Computing: A Conceptual Framework and Future Perspectives. Appl. Sci. 2022, 12, 5793. [Google Scholar] [CrossRef]
- Yu, Y.; Dong, Y.; Guo, X. Pricing for sales and per-use rental services with vertical differentiation. Eur. J. Oper. Res. 2018, 270, 586–598. [Google Scholar] [CrossRef]
- Yuan, Y.; Wang, F.-Y. Blockchain: The State of the Art and Future Trends. Acta Autom. Sin. 2016, 42, 481–494. [Google Scholar]
- Kim, H.; Laskowski, M. A perspective on blockchain smart contracts: Reducing uncertainty and complexity in value exchange. Soc. Sci. Electron. Publ. 2018, 1–6. [Google Scholar] [CrossRef]
- Cong, W.; He, Z. Blockchain Disruption and Smart Contracts. Rev. Financ. Stud. 2019, 32, 1754–1797. [Google Scholar] [CrossRef]
- Huang, Z.; Su, B. Research on hierarchical blockchain architecture based on Ethereum. Comput. Appl. Softw. 2020, 37, 16–19. [Google Scholar]
- Hong, W.; Wang, Q. Construction and analysis of intelligent contract framework for maritime industry based on blockchain. Logist. Technol. 2020, 43, 97–101. [Google Scholar]
- Fu, X.; Wang, H.; Shi, P. A survey of Blockchain consensus algorithms: Mechanism, design, and applications. Sci. China Inf. Sci. 2020, 64, 1–15. [Google Scholar] [CrossRef]
- Pan, J.; Han, D.; Guo, F.; Zheng, W.; Yu, J.; Chen, W. A visual exploration method for bitcoin trading network topology. Softw. J. 2019, 30, 3017–3025. [Google Scholar]
- Pan, W.; Huang, X. Identity management and authentication model based on smart contract. Comput. Eng. Des. 2020, 41, 915–919. [Google Scholar]
- Li, F.; Li, J.; Zhen, S.; Zhang, L.-L.; Lu, Y. Market oriented trading model and algorithm of multi microgrid based on smart contract. J. Netw. Inf. Secur. 2020, 6, 56–66. [Google Scholar]
- Chen, C.-L.; Deng, Y.-Y.; Weng, W.; Zhou, M.; Sun, H. A blockchain-based intelligent anti-switch package in tracing logistics system. J. Supercomput. 2021, 77, 7791–7832. [Google Scholar] [CrossRef]
- Chen, C.-L. A secure and traceable E-DRM system based on mobile device. Expert Syst. Appl. 2008, 35, 878–886. [Google Scholar] [CrossRef]
- Chen, C.-L. An all-in-one mobile DRM system design. Int. J. Innov. Comput. Inf. Control. 2010, 6, 897–911. [Google Scholar]
- Chen, C.-L.; Tsaur, W.J.; Chen, Y.Y.; Chang, Y.C. A secure mobile DRM system based on cloud architecture. Comput. Sci. Inf. Syst. 2014, 11, 925–941. [Google Scholar] [CrossRef]
- Zhao, B.; Fang, L.; Zhang, H.; Ge, C.; Meng, W.; Liu, L.; Su, C. Y-DWMS: A digital watermark management system based on smart contracts. Sensors 2019, 19, 3091. [Google Scholar] [CrossRef]
- Ma, Z.; Jiang, M.; Gao, H.; Wang, Z. Blockchain for digital rights management. Future Gener. Comput. Syst. 2018, 89, 746–764. [Google Scholar] [CrossRef]
- Vishwa, A.; Hussain, F.K. A blockchain based approach for multimedia privacy protection and provenance. In Proceedings of the 2018 IEEE Symposium Series on Computational Intelligence (SSCI), Bengaluru, India, 18–21 November 2018; pp. 1941–1945. [Google Scholar]
- Ma, Z.; Huang, W.; Bi, W.; Gao, H.; Wang, Z. A master-slave blockchain paradigm and application in digital rights management. China Commun. 2018, 15, 174–188. [Google Scholar] [CrossRef]
- Mishra, D.; Rana, S. A provably secure content distribution framework for portable DRM systems. J. Inf. Secur. Appl. 2021, 61, 102928. [Google Scholar] [CrossRef]
- Hassan HE, R.; Tahoun, M.; ELTaweel, G.S. A robust computational DRM framework for protecting multimedia contents using AES and ECC. Alex. Eng. J. 2020, 59, 1275–1286. [Google Scholar] [CrossRef]
- Rana, S.; Obaidat, M.S.; Mishra, D.; Mukhopadhyay, S.; Sadoun, B. Computational Efficient Authenticated Digital Content Distribution Frameworks for DRM Systems: Review and Outlook. IEEE Syst. J. 2021, 15, 1586–1593. [Google Scholar] [CrossRef]
- Shrestha, B.; Halgamuge, M.N.; Treiblmaier, H. Using Blockchain for Online Multimedia Management: Characteristics of Existing Platforms. In Blockchain and Distributed Ledger Technology Use Cases; Springer: Cham, Switzerland, 2020; pp. 289–303. [Google Scholar]
- Zhaofeng, M.; Weihua, H.; Hongmin, G. A new blockchain-based trusted DRM scheme for built-in content protection. EURASIP J. Image Video Process. 2018, 91, 1–12. [Google Scholar] [CrossRef]
- Lu, Z.; Shi, Y.; Tao, R.; Zhang, Z. Blockchain for digital rights management of design works. In Proceedings of the 2019 IEEE 10th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 18–20 October 2019; pp. 596–603. [Google Scholar]
- Ma, Z. Digital rights management: Model, technology and application. China Commun. 2017, 14, 156–167. [Google Scholar]
- Du Toit, J. Protecting private data using digital rights management. J. Inf. Warf. 2018, 17, 64–77. [Google Scholar]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A survey of IoT security based on a layered architecture of sensing and data analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef]
- Han, W.; Zhu, Z. An ID-based mutual authentication with key agreement protocol for multiserver environment on elliptic curve cryptosystem. Int. J. Commun. Syst. 2014, 27, 1173–1185. [Google Scholar] [CrossRef]
- Boneh, D.; Lynn, B.; Shacham, H. Short signatures from the Weil pairing. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security; Springer: Heidelberg/Berlin, Germany, 2001; pp. 514–532. [Google Scholar]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1998; pp. 127–144. [Google Scholar]
- Szabo, N. Smart contracts: Building blocks for digital markets. EXTROPY J. Transhumanist Thought 1996, 18, 16. [Google Scholar]
- Szabo, N. The Idea of Smart Contracts. 1997. Available online: http://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/smart_contracts_idea.html (accessed on 30 August 2022).
- Vanstone, S. Responses to NIST’s proposal. Commun. ACM 1992, 35, 50–52. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. The Elliptic Curve Digital Signature Algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Hyperledger Fabric Docs. Available online: https://hyperledger-fabric.readthedocs.io/en/release-2.2 (accessed on 30 August 2022).
- Foschini, L.; Gavagna, A.; Martuscelli, G.; Montanari, R. Hyperledger Fabric Blockchain: Chaincode Performance Analysis. In Proceedings of the ICC 2020–2020 IEEE International Conference on Communications (ICC); 7–11 June 2020; pp. 1–6. [CrossRef]
- Uddin, M. Blockchain Medledger: Hyperledger fabric enabled drug traceability system for counterfeit drugs in pharmaceutical industry. Int. J. Pharm. 2021, 597, 120235. [Google Scholar] [CrossRef] [PubMed]
- Marcus, M.J. 5G and IMT for 2020 and beyond. IEEE Wirel. Commun. 2015, 22, 2–3. [Google Scholar] [CrossRef]







| Item | Signature | Sender | Receiver | Signature Verification |
|---|---|---|---|---|
| Phase | ||||
| CA communication process | AP | CA | ||
| CA | AP | |||
| Subscription negotiation/confirmation phase | LE | OR | ||
| OR | LE | |||
| Bank payment phase | LE | BK | ||
| BK | LE | |||
| Proxy re-encryption and proxy-key update phase | OR | DMC | ||
| DMC | OR | |||
| Digital media browsing phase | LE | DMC | ||
| DMC | LE |
| Party | LE | OR | BK | DMC |
|---|---|---|---|---|
| Phase | ||||
| Subscription negotiation phase | 2Tasy + 2Tcmp +2Th + 7Tmul | 2Tasy + 2Tcmp +3Th + 7Tmul | N/A | N/A |
| Bank payment phase | 2Tasy + 2Tcmp +2Th + 7Tmul | N/A | 2Tasy + 2Tcmp +2Th + 7Tmul | N/A |
| Subscription confirmation phase | 2Tasy + 2Tcmp +2Th + 7Tmul | 2Tasy + 2Tcmp +3Th + 7Tmul | N/A | N/A |
| Proxy re-encryption and proxy-key update phase | N/A | 2Tasy + 2Tcmp +2Th + 9Tmul | N/A | 2Tasy + 2Tcmp +2Th + 7Tmul |
| Digital media browsing phase | 2Tasy + 2Tcmp +2Th + 9Tmul | N/A | N/A | 2Tasy + 2Tcmp +2Th + 8Tmul |
| Party | Message Length | Round | 4G (100 Mbps) | 5G (20 Gbps) |
|---|---|---|---|---|
| Phase | ||||
| CA communication process | 2Tsig + 2Tasy + 5Tohter = 2 * 512 + 2 * 1024+ 2 * 80 = 3232 bits | 2 | 3232/102,400 =0.032 ms | 3232/20,480,000 =0.16 us |
| Subscription negotiation/confirmation phase | 2Tsig + 2Tasy + 5Tohter= 2 * 512 + 2 * 1024 + 2 * 80 = 3232 bits | 2 | 3232/102,400= 0.032 ms | 3232/20,480,000= 0.16 us |
| Bank payment phase | 2Tsig + 2Tasy + 5Tohter= 2 * 512 + 2 * 1024+ 2 * 80 = 3232 bits | 2 | 3232/102400= 0.032 ms | 3232/20,480,000= 0.16 us |
| Proxy re-encryption and proxy-key update phase | 2Tsig + 2Tasy + 5Tohter= 2 * 512 + 2 * 1024+ 2 * 80 = 3232 bits | 2 | 3232/102,400= 0.032 ms | 3232/20,480,000= 0.16 us |
| Digital media browsing phase | 2Tsig + 2Tasy + 5Tohter= 2 * 512 + 2 * 1024+ 2 * 80 = 3232 bits | 2 | 3232/102,400= 0.032 ms | 3232/20,480,000= 0.16 us |
| Authors | Year | Objective | 1 | 2 | 3 | 4 | 5 | 6 |
|---|---|---|---|---|---|---|---|---|
| Ma et al. [21] | 2018 | Blockchain for digital rights management | Y | NA | Y | Y | NA | Y |
| Ma et al. [23] | 2018 | A master-slave blockchain paradigm and application in digital rights management | Y | NA | Y | Y | NA | NA |
| Mishra et al. [24] | 2021 | Proposed a provably secure content distribution framework for portable DRM systems | NA | NA | Y | Y | NA | Y |
| Hassan et al. [25] | 2020 | Proposed a robust computational DRM framework for protecting multimedia content by using AES and ECC | NA | NA | Y | NA | NA | NA |
| Rana et al. [26] | 2021 | Proposed a computational efficient authenticated digital content distribution framework for DRM systems | NA | NA | Y | NA | NA | Y |
| Shrestha et al. [27] | 2020 | Using blockchain for online multimedia management: characteristics of existing platforms | Y | NA | NA | Y | NA | Y |
| Zhaofeng et al. [30] | 2018 | A new blockchain-based trusted DRM scheme for built-in content protection | Y | NA | Y | Y | NA | Y |
| Our scheme | 2022 | Proposed a digital media subscription mechanism based on the Hyperledger blockchain architecture combined with proxy re-encryption | Y | Y | Y | Y | Y | Y |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, D.-C.; Liu, L.-C.; Deng, Y.-Y.; Chen, C.-L. A Digital Media Subscription Management System Combined with Blockchain and Proxy Re-Encryption Mechanisms. Symmetry 2022, 14, 2167. https://doi.org/10.3390/sym14102167
Huang D-C, Liu L-C, Deng Y-Y, Chen C-L. A Digital Media Subscription Management System Combined with Blockchain and Proxy Re-Encryption Mechanisms. Symmetry. 2022; 14(10):2167. https://doi.org/10.3390/sym14102167
Chicago/Turabian StyleHuang, Der-Chen, Ling-Chun Liu, Yong-Yuan Deng, and Chin-Ling Chen. 2022. "A Digital Media Subscription Management System Combined with Blockchain and Proxy Re-Encryption Mechanisms" Symmetry 14, no. 10: 2167. https://doi.org/10.3390/sym14102167
APA StyleHuang, D.-C., Liu, L.-C., Deng, Y.-Y., & Chen, C.-L. (2022). A Digital Media Subscription Management System Combined with Blockchain and Proxy Re-Encryption Mechanisms. Symmetry, 14(10), 2167. https://doi.org/10.3390/sym14102167







