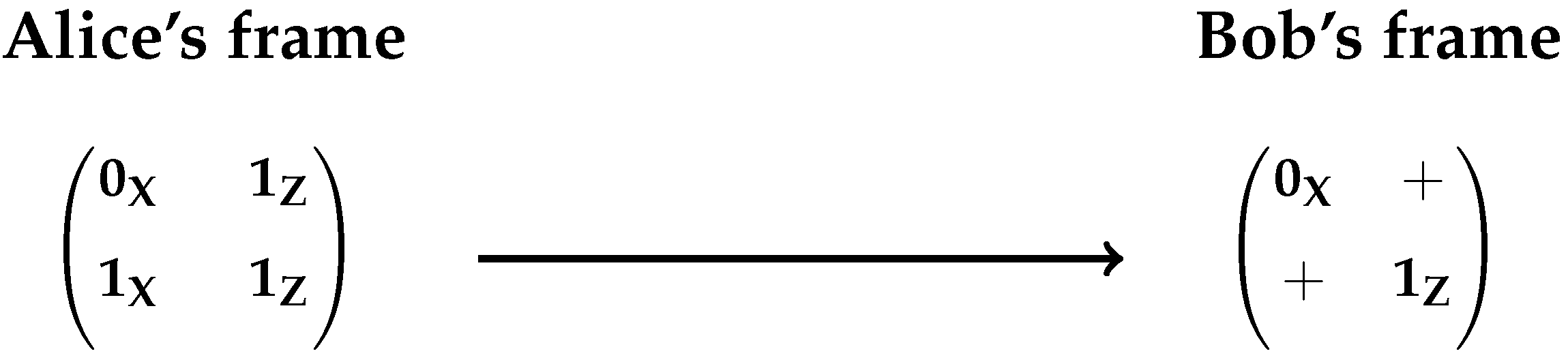1. Introduction
The arrival of the quantum era and quantum computers in the short term is imminent. One of the most profound consequences of the quantum era is that the security of digital data as we know it today must be radically changed due to the power of computers to break the security of asymmetric key cryptographic methods and at the same time must increase the sizes of the symmetrical keys.
Countermeasures to address the threat of quantum computers have been led by NIST, which launched a selection process for new cryptographic algorithms for the quantum era in 2017 [
1]. However, it is to be expected that it will take years to implement and technologically adapt the new methods to be used in global data networks [
2].
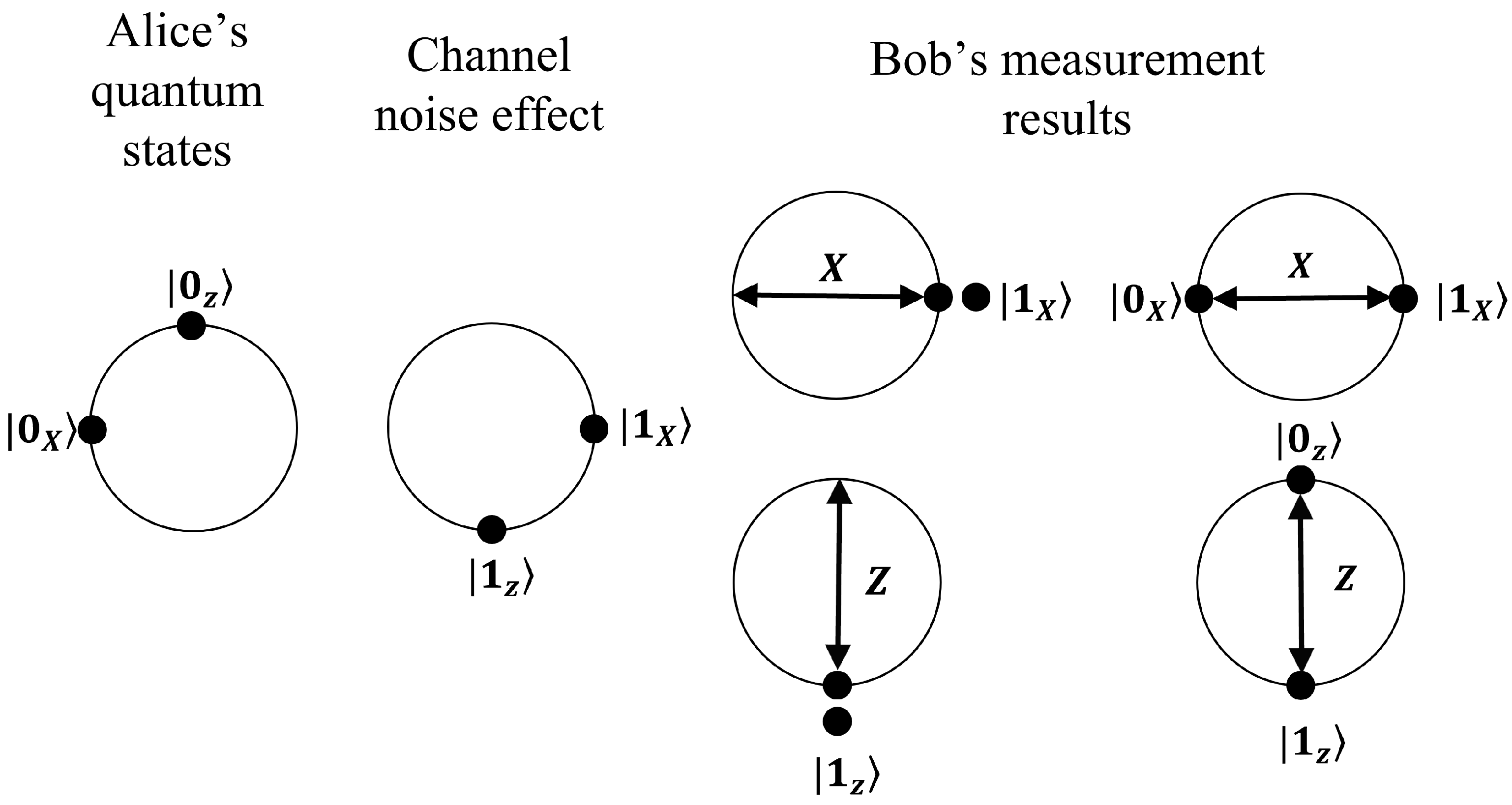
Fortunately, the quantum cryptographic key distribution (QKD) is a cryptographic scheme that appeared almost four decades ago that has been widely evaluated and discussed by the scientific community. In addition, QKD can be implemented through satellite links or already installed fiber optic networks. Quantum Key Distribution (QKD) allows the establishment of a secret key between two remote entities taking advantage of the principles of quantum physics and therefore theoretically secure. Unfortunately, the transmission of quantum states through a noisy quantum channel causes errors to appear in the received information, severely limiting the deployment of QKD technology as it reduces the secret bit rate and the distance achievable by the QKD system. For this reason, error correction algorithms have been developed to detect and correct errors during the post-processing phase, which includes sifting, error reconciliation, and privacy amplification. The reconciliation algorithm must be carried out preserving the secrecy of the cryptographic key [
3].
Reconciliation methods developed natively for QKD are BBBSS [
4] based on binary search, Cascade [
5,
6] that uses binary search and backtracking, but they are based on the parity computation of the received information blocks and do not take advantage of the properties of communication with quantum states; instead, it is highly interactive, requiring multiple rounds of correction of bits.
In view of the above, it has been necessary to resort to other reconciliation techniques developed in the field of data communications. Reconciliation methods based on error correcting codes are Winnow [
7,
8,
9] which uses parity check and Hamming error correction code. It corrects one error per block, so the choice of block length is very sensitive because additional errors may be introduced if a block contains two or more errors [
10]. Also, Forward Error Correction (FEC) is used to achieve reconciliation as the discrete number of Low-Density Parity-Check (LDPC) codes. However, LDPC has the disadvantage that requires redundant information that must be transmitted along the information data [
11,
12,
13,
14,
15]. Recently, polar encoding has emerged as an encoding method in finding error correction codes that are close to the Shannon limit [
16,
17,
18]. Beyond the mentioned drawbacks, none of these schemes is capable of handling a quantum channel error rate beyond 25% [
19].
We published in [
20,
21] a new reconciliation algorithm that takes advantage of the characteristics of quantum communication, which, simply put, is equivalent to having two classical communication channels, one in the quantum
basis and the other in the
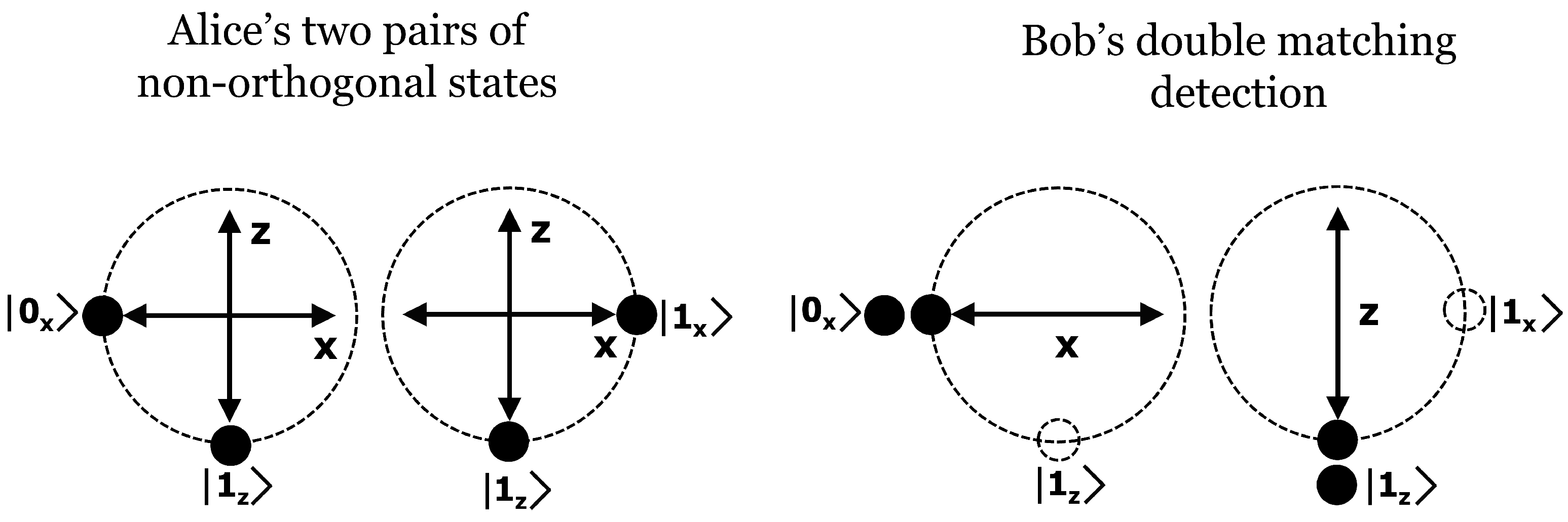
basis. By means of a reverse reconciliation process, Bob sends parity information from these two channels so that Alice is able to recognize Bob’s chosen bases on which the secret information is encoded as depicted in
Figure 1.
A two order frame, as it can be seen in
Figure 1, is a 2 × 2 matrix, structured by two rows and two columns. One row represents a pair of non-orthogonal states where the first column of the frame contains the base
encoded quantum bit
or
and the second column the base
quantum bit, that is
or
where
. Once Bob measures a pair of non-orthogonal states and provided he gets a DMDE (Double Matching Detection Event), he obtains the encoded bit in the first or second column of the first row of the frame, as shown in
Figure 1 and
Figure 2. Bob’s frame is complete once he gets the second DMDE.
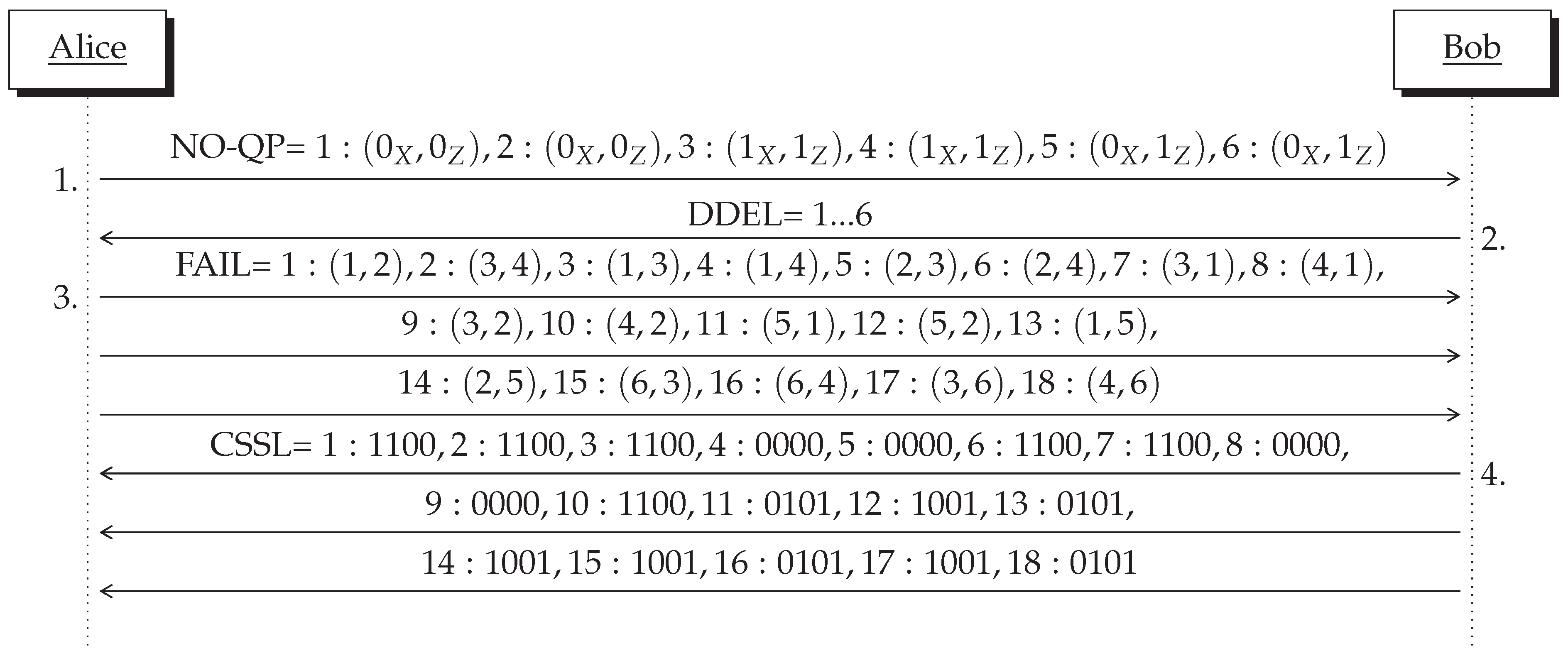
In fact, the two rows of a frame are not received sequentially, instead Bob must inform Alice about the DMDE that he obtained, then Alice responds to Bob how to arrange the rows to construct the frames as illustrated in the message exchange in
Figure 3. For this reason, each DMDE is labelled by an index that has the form (CSS,
,
) where
is the number of the first NO-QP and
is the number of the second NO-QP. The index is assigned during transmission, so is known by Alice and Bob, CSS will be explained shortly.
This article is focused on the discussion and explanation of the reconciliation method, rather than on a detailed discussion of the attacks over the system. So,
Section 2 contains a detailed discussion of the reconciliation method. In
Section 3 we derive the relation for the secret throughput of the frame-based method. Finally,
Section 4 contains a brief discussion about the main quantum attacks. But before going to the details of the reconciliation method, let us succinctly state the research problem and the general idea of the new method.
1.1. Research Problem Statement
The reconciliation method must be able to detect the errors produced into the pairs of non-orthogonal quantum states
,
,
,
,
,
,
and
where the overbracket symbol ﹇ represents the error that is produced in a transmitted NO-QP. We argue that if we can detect all these types of errors, we will achieve error correction that is invariant with respect to the error rate of the quantum channel. The following types of frames (which have been enumerated according to [
20]) will be used:
- 1.
Auxiliary frames, of two types, null and unitary frames as well as their conjugate denoted with a math apostrophe. We call the null frame while is the unitary frame:
- 2.
Regular-frames (twelve types) and their conjugate:
The frame and the frame are not used in this context. Bob obtains the conjugate frames by inverting the measured bits so they are not obtained from the channel measurements.
1.2. General Idea of the Method
It is our goal to demonstrate that using the Composed Sifting String (CSS) is possible that Alice reconciliate 100% of the errors produced in received Bob’s DMDE.
- —
Just to bring it in context, the Sifting String (SS) as stated in [
20] is constructed using the sifting bits and the measured bits into Bob’s frames. The sifting bits are obtained applying the XOR function to the bits within the columns (from the left to the right column) of Bob’s frames, where a vacuum bit is taken as a zero bit. The measured bits are taken directly from the bits inside Bob’s frame. This is so because the secret bit is derived from the final configuration of Bob’s frames, that we call Measurement Results (MR) as represented in
Table 1. The sifting bits are written first into SS while the measured bits are placed next:
Unfortunately, using SS as designed in [
20] is impossible to detect the errors
,
,
and
.
- —
Now, in this new reconciliation method we introduce the Composed Sifting String (CSS) which is constructed taken the sifting bits of Bob’s frame but also the sifting bits of Bob’s conjugate frame, that is:
We will demonstrate that using CSS and without compromising the security of the scheme, is possible to detect the errors , , , , , , and .
2. Perfect Reconciliation Using Order-Two Binary Frames
We begin this section by establishing the general steps of the reconciliation method which we will justify throughout the section. To simplify notation, throughout this document we will represent a quantum state using a bold letter instead of the usual ket notation, so we denote as .
- 1.
Alice creates NO-QPL (the Non-Orthogonal Quantum Pair List) and sends, one by one, each NO-QP (the Non-Orthogonal Quantum Pair) across QC (the Quantum Channel). NO-QP can be or where .
- 2.
Bob chooses randomly the measurement basis: X or Z, that he will use to measure both states inside NO-QP. After Bob registers DDE (the Double Detection Events) he sends DDEL (the Double Detection Event List) to Alice.
- 3.
Alice receive DDEL from QC, she creates FAIL (the Frame Arrangement Information List) and sends it to Bob.
- 4.
Bob receives FAIL and he computes CSSL (the Composed Sifting String List). Then he returns CSSL to Alice.
- 5.
Alice detect errors and identifies MR in regular frames. Alice sends FDL (the Frame to Delete List) to Bob.
- 6.
Bob eliminates the frames indicated in FDL, then he creates SeS using MRT as written in
Table 1.
We call step 3 of the protocol privacy pre-amplification, in this step Alice performs all the combinations of the DMDE to form the frames that she is going to use in order to successfully carry out the error correction process. Then, the number of possible frames is given by the combination formula
where
n is the number of DMDE. The general diagram showing the protocol message exchange is shown in
Figure 3.
2.1. Regular and Conjugate 2 × 2 Frames
Conjugate frames are derived from regular frames thus they are not obtained from the physical quantum channel. They are used just to derive a useful complementary set of sifting bits. Below we will show each one of the regular frames, each one with its respective conjugated frame and we will add its corresponding CSS each MR.
The sifting algorithm can also be applied to the remaining regular frames
,
,
,
,
,
which we do not show here to facilitate the exposition of the method. The security property or frame-based model states that each CSS must map to at least two MR because the secret bit is derived from MR. The results are presented in
Table 2. As can be seen there, the cases CSS 1010 and 0101 should be removed because they map a single MR: 00 and 01, respectively.
Now, we proceed to demonstrate which errors can be detected inside a frame. Due to their structure, is convenient to see the frames grouped as: {, }, {, }, {, }, {, }, {, }. In the following equations, the top line contains the frame under MR while the second line shows the conjugated frame. The bottom line hold the computed CSS in each case. The error detection illustrated depends on an error-free NO-QP, so we will solve this point as the error correction pre-processing.
- 1.
The error
is detected with an error-free NO-QP
, as the second row in
because the CSS that is produced by the error is none of the possible error-free CSS.
- 2.
The error
is detected with an error-free NO-QP
, as the first row in
because the CSS that is produced by the error is none of the possible error-free CSS.
- 3.
The error
is detected with an error-free NO-QP
, as the second row in
because the CSS that is produced by the error is none of the possible error-free CSS.
- 4.
The error
is detected with an error-free NO-QP
, as the first row in
because the CSS that is produced by the error is none of the possible error-free CSS.
- 5.
The error
is detected with an error-free NO-QP
, as the second row in
because the CSS that is produced by the error is none of the possible error-free CSS.
- 6.
The error
is detected with an error-free NO-QP
, as the second row in
because the CSS that is produced by the error is none of the possible error-free CSS.
- 7.
The error
and also the error
are detected with an error-free NO-QP
, as the first row in
because the CSS that is produced by the error is none of the possible error-free CSS.
- 8.
The error
and also the error
are detected with an error-free NO-QP
, as the second row in
because the CSS that is produced by the error is none of the possible error-free CSS.
2.2. Error Correction Pre-Processing
In the error-detection cases exhibited above we have assumed that the non-orthogonal quantum pairs (NO-QP) and are error-free, which implies being able to detect any error in these NO-QP. In this section, we explain how to detect such errors using null-frames and unitary-frames . To achieve this we must note that in the absence of error, produce CSS that only contain zeros while produces 0000 and 1100 under MRT.
2.2.1. Null-Frame Errors
The error can arrive in several ways and we need a method to detect them, so the following cases can occur:
- —
Single error:
, , ,
- —
Non-orthogonal error, two errors in different basis:
,
- —
Parallel error, two errors in the same basis:
,
As we will see right away, single and parallel errors will be detected as if they were non-orthogonal error using the algorithm for Detection of Parallel-Pair Errors (DPPE) that we explain next:
- —
Alice separates CSSL from null frames into the error-detected-null-frames and the error-free-null-frames just checking that CSS ≠ 0000. The last list contain, however, frames with hidden (parallel) errors. For example, consider Alice’s null frame
. If Bob’s frame contains two errors, say
then the errors kept hidden since
. Alice takes the row-indices
and
and she looks for them into the error-detected list (see
Table 3).
- —
Two cases in the error-detected list reveals the errors in and . The frame with where the first row is , reveals an error in the frame but the result it is ambiguous because the frame also produces CSS = 1010. Thus, the result is inconclusive because the CSS does not indicate if the error is in the first or the second row. However, Alice keeps searching into the list of errors and she finds which comes from the frame where the first row contains and the second row also contains an error. Interestingly, this CSS reveals the presence of a non-orthogonal error. Similarly, Alice finds another label that exhibits and the parallel error is detected using a non-orthogonal error which applies for single errors too.
The following aspects must be remarked here:
- 1.
Given an error rate in the quantum channel, it is to be expected that about half of the errors will occur in the first quantum state of and the other half in the second state . Therefore, the method described to detect single and parallel errors in null-frames is completely feasible.
- 2.
The algorithm detailed above allows finding all the errors in the null frames, but it does not tell us which of the two non-orthogonal states is the error. To find the position of the error, Alice must use an error free NO-QP say
from the list of error-free-null-frames. Then she finds
which reveals the error is in the first state while
unveils the error in the second state (see
Table 3).
How should it be clear, in all cases, Alice must be able to identify the position of the error to perform reconciliation successfully. Importantly here is that detecting the position of the error also allows Alice to find MR when using this error-row inside a frame. For this purpose and assuming Alice has detected all the errors, consider the following frame cases:
- 1.
First and second rows without errors. Alice applies the usual frame-based sifting algorithm identifying MR in each case.
- 2.
First and second rows with errors. Since error-detection reveals the position of the error, Alice identifies MR straightforward.
- 3.
Error-free (first/second) row and error-detected (second/first) row. In the next lines we discuss this case.
Suppose Alice has detected all the errors and she must guess MR when she sends and Bob gets thus he returns to Alice CSS = 1100. But Alice knows the following facts:
- —
CSS comes from .
- —
The first row is error-free but the first state of the second row is error-detected, that is .
Then Alice tests
under MRT (see
Table 1) given
and CSS = 1100, thus she concludes that the unique MR that matches CSS is under MR = 11.
2.2.2. Unitary-Frame Errors
Frames
behave similarly as frames
, so we present the summary results in
Table 4. As far as we go, we are able to detect
,
,
,
errors.
2.3. Reconciliation Algorithm
To close this section let us summarize the steps of the reconciliation algorithm.
Table 5 shows the error detection results using regular frames.
- 1.
Identify and , errors in the set of . Identify single and parallel errors using DPPE algorithm.
- 2.
Identify and , errors in the set of . Identify single and parallel errors using DPPE algorithm.
- 3.
Identify MR using , and , in , .
- 4.
Identify , and , errors in , , , using , , . Identify MR in , , , .
- 5.
Identify , and , errors in , , , using , , , , , , . Identify MR in , , , .
- 6.
Identify MR in , using , , , , , .
As has been demonstrated so far, errors can be detected regardless of the number of errors. Thus, the gain of the secret bits does not depend on the error rate of the quantum channel.
3. The Throughput of Frame Reconciliation
Not all the frames are converted into secret bits. In [
21] we derived the throughput as
that reaches a maximum gain of
when
. Taking into account
Table 2, we arrive to the throughput Equation (
1) of frame reconciliation
T where
n is the number or Double Matching Detection Events.
Computing the photonic gain of double detection events at Bob’s side as
(neglecting the losses generated by the quantum channel and the losses of the optical detection system), we derived Equation (
2) where
N is the total number of quantum pulses sent by Alice to Bob. As a result, the number of secret bits grows doubly quadratically as a function of the number of quantum pulses
N.
One of the biggest challenges posed by the Photon Number Splitting (PNS) attack is that the number of photons per pulse () should not be increased because an attacker can split the pulse and store a copy of it. However, in frame-based reconciliation, the secret bits do not result only from the quantum pulses that arrive to Bob’s detector, but from the double detection events that occur at Bob’s station. So the security of our approach does no depend on the photon mean of the quantum pulse neither the channel error-rate e.
6. Conclusions
We introduced a method to achieve complete reconciliation in Quantum Key Distribution which identifies the transmitted errors in a reverse reconciliation that corrects 100% of the errors that is invariant with respect to the error rate of the quantum channel.
The QKD protocol, which is based on sending pairs of non-orthogonal quantum states and reconciliation through frames of two-order, is executed in a single process that includes quantum communication and classical post-processing. Furthermore, it does not require the sending of redundant bits, nor is it necessary to estimate the error rate of the quantum channel.
At least theoretically, the number of secret bits grows doubly quadratically as a function of the number of quantum pulses sent by Alice because the mean photon value can be properly increased in the quantum regime, so that longer distance can be achieved in QKD system.