A Consortium Blockchain Wallet Scheme Based on Dual-Threshold Key Sharing
Abstract
:1. Introduction
2. Related Information
2.1. Consortium Blockchain
- Request: Client sends a request to the master node 0;
- Pre-Prepare: Node 0 broadcasts to node 1, node 2, and node 3 after receiving Client’s request;
- Prepare: Each node records and broadcasts it again after receiving it. Node 3 cannot broadcast due to downtime;
- Commit: In the Prepare phase, if a node receives the same request exceeding (F is the number of Byzantine nodes that can be tolerated), it will enter the Commit phase and broadcast the Commit request;
- Reply: In the Commit phase, if one of the nodes receives more than a certain number of the same request, it will give feedback to Client.
2.2. Shamir’s Threshold Secret-Sharing Scheme
2.2.1. Share Generation
2.2.2. Secret Reconstruction
2.3. Harn–Hsu TCSS Scheme
2.3.1. Share Generation
2.3.2. Secret Reconstruction
3. Proposed Scheme
3.1. Algorithms
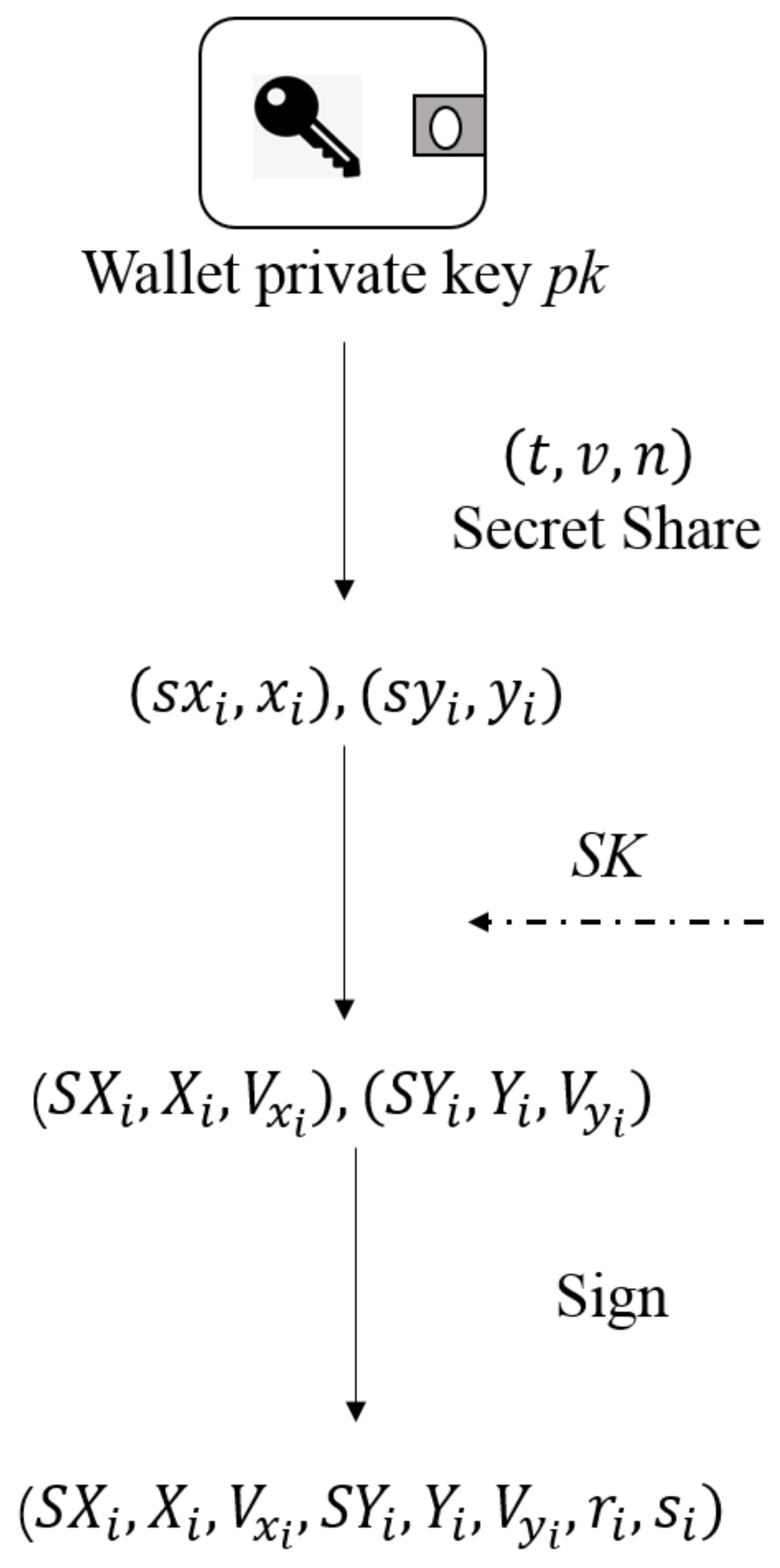
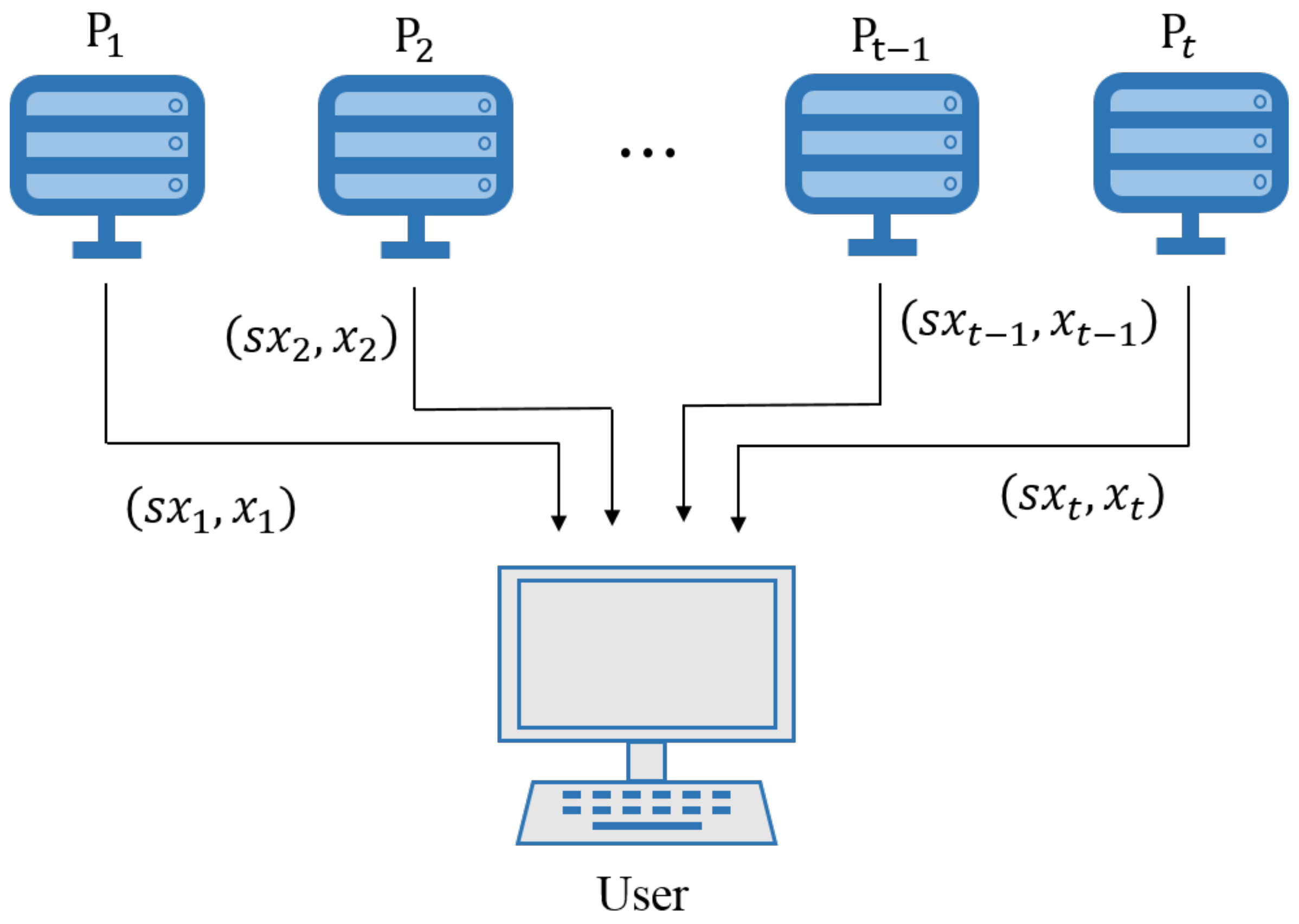
3.1.1. Secret-Sharing Phase
- .
- .
- .
- .
- User computes the verification message ,.
- Let be the plaintext, then use the improved the El Gamal signature to sign . Select a large prime number p and set g to be the generator of the group . Additionally, user selects a random number , gcd = 1, l is the private key, and computes the modulo inverse of l as . Then user computes , sets as the public key.
- The user signs the plaintext, selects a random number , then computes .
- U computes , the signature of is .
3.1.2. Peers Verification Phase
- (i)
- computes ;
- (ii)
- if is true, the signature is valid, and the secret share is correct.
3.1.3. Secret Reconstruction Phase
- .
- .
- .
- if is equal to , the P is an honest peer, and the share P provided is correct and valid, otherwise it can be judged as malicious peer. Malicious peers will be punished.
- .
- .
- .
3.1.4. Peers Addition and Deletion
- Join and Exit of User Nodes:Whether user nodes join or quit the consortium chain network does not affect the secret share and recovery of the user’s wallet private key in the scheme. A new user joins the consortium chain network should perform the secret-sharing scheme, and the user’s private key would be stored by the peers, and can be reconstructed normally. When the user logs off the account, the share is also deleted.
- Join of Peers:When a new peer joins the consortium chain network will not affect the secret-sharing that has been performed, but the value of involved in the subsequent secret-sharing will change accordingly, and the user needs to perform a new threshold secret-sharing after completing a secret reconstruction phase. All the original shadow shares stored in each peer should be destroyed, and peers keep the brand-new shadow shares of the new threshold secret sharing.
- Exit of Peers:When an original peer exits the consortium blockchain network, there is a possibility that the number of remaining peers is less than the threshold t. At this time, the user can use the second threshold scheme to reconstruct the wallet secret key. And after the user finishing the secret recovery, the old shares should be updated. Thus, all the original shadow shares stored in each peer should be destroyed, and peers keep the brand-new shadow shares of the new threshold secret-sharing.
4. Security Analysis and Scheme Comparison
4.1. Security Analysis
4.2. Schemes’ Comparison
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| SPV | Simplified Payment Verification |
| HD | Hierarchical Deterministic |
| PoW | Proof of Work |
| DPoS | Delegated Proof of Stake |
| PBFT | Practical Byzantine Fault Tolerant Algorithm |
References
- Nofer, M.; Gomber, P.; Hinz, O.; Schiereck, D. Blockchain. Bus. Inf. Syst. Eng. 2017, 59, 183–187. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Business Review. 2008. Available online: https://www.google.com.hk/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwibtt7khJzyAhXOQfUHHfkzBTgQFnoECAYQAw&url=https%3A%2F%2Fbitcoin.org%2Fbitcoin.pdf&usg=AOvVaw05-4mYD7EyyKjwcHh8i0Vw (accessed on 3 August 2021).
- Zhu, L.; Gao, F.; Shen, M.; Li, Y.; Zheng, B.; Mao, H.; Wu, Z. Survey on Privacy Preserving Techniques for Blockchain Technology. J. Comput. Res. Dev. 2017, 54, 2170–2186. [Google Scholar]
- Peterson, B. Thieves stole potentially millions of dollars in bitcoin in a hacking attack on a cryptocurrency company. Bus. Insid. 2017, 6, 12–13. [Google Scholar]
- Dai, W.; Deng, J.; Wang, Q. SBLWT: A secure blockchain lightweight wallet based on trustzone. IEEE Access 2018, 6, 40638–40648. [Google Scholar] [CrossRef]
- Gutoski, G.; Stebila, D. Hierarchical deterministic bitcoin wallets that tolerate key leakage. In Proceedings of the International Conference on Financial Cryptography and Data Security, San Juan, Puerto Rico, 26–30 January; Springer: Berlin/Heidelberg, Germany, 2015; pp. 497–504. [Google Scholar]
- Rezaeighaleh, H.; Zou, C.C. New secure approach to backup cryptocurrency wallets. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Wei, Q.; Li, S.; Li, W.; Li, H.; Wang, M. Decentralized Hierarchical Authorized Payment with Online Wallet for Blockchain. In Proceedings of the International Conference on Wireless Algorithms, Systems, and Applications, Honolulu, HI, USA, 24–26 June 2019; Springer: Cham, Switzerland, 2019; pp. 358–369. [Google Scholar]
- He, X.; Lin, J.; Li, K.; Chen, X. A novel cryptocurrency wallet management scheme based on decentralized multi-constrained derangement. IEEE Access 2019, 7, 185250–185263. [Google Scholar] [CrossRef]
- Thota, A.R.; Upadhyay, P.; Kulkarni, S.; Selvam, P.; Viswanathan, B. Software Wallet Based Secure Participation in Hyperledger Fabric Networks. In Proceedings of the 2020 International Conference on COMmunication Systems & NETworkS (COMSNETS), Bangalore, India, 7–11 January 2020; pp. 1–6. [Google Scholar]
- Boneh, D.; Gennaro, R.; Goldfeder, S. Using level-1 homomorphic encryption to improve threshold dsa signatures for bitcoin wallet security. In Proceedings of the International Conference on Cryptology and Information Security in Latin America, Havana, Cuba, 20–22 September 2017; Springer: Cham, Switzerland, 2017; pp. 352–377. [Google Scholar]
- Dikshit, P.; Singh, K. Efficient weighted threshold ECDSA for securing bitcoin wallet. In Proceedings of the 2017 ISEA Asia Security and Privacy (ISEASP), Surat, India, 29 January–1 February 2017; pp. 1–9. [Google Scholar]
- Jian, Z.; Ran, Q.; Liyan, S. Securing blockchain wallets efficiently based on threshold ECDSA scheme without trusted center. In Proceedings of the 2021 Asia-Pacific Conference on Communications Technology and Computer Science (ACCTCS), Shenyang, China, 22–24 January 2021; pp. 47–51. [Google Scholar]
- Aitzhan, N.Z.; Svetinovic, D. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Trans. Dependable Secur. Comput. 2016, 15, 840–852. [Google Scholar] [CrossRef]
- Maxwell, G.; Poelstra, A.; Seurin, Y.; Wuille, P. Simple schnorr multi-signatures with applications to bitcoin. Des. Codes Cryptogr. 2019, 87, 2139–2164. [Google Scholar] [CrossRef]
- Han, J.; Song, M.; Eom, H.; Son, Y. An efficient multi-signature wallet in blockchain using bloom filter. In Proceedings of the 36th Annual ACM Symposium on Applied Computing, Gwangju, Korea, 22–26 March 2021; pp. 273–281. [Google Scholar]
- Pal, O.; Alam, B.; Thakur, V.; Singh, S. Key management for blockchain technology. ICT Express 2019, 7, 76–80. [Google Scholar] [CrossRef]
- Jiang, Y.; Ding, S. A high performance consensus algorithm for consortium blockchain. In Proceedings of the 2018 IEEE 4th International Conference on Computer and Communications (ICCC), Chengdu, China, 7–10 December 2018; pp. 2379–2386. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the security and performance of proof of work blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 3–16. [Google Scholar]
- Saad, S.M.S.; Radzi, R.Z.R.M. Comparative Review of the Blockchain Consensus Algorithm Between Proof of Stake (POS) and Delegated Proof of Stake (DPOS). Int. J. Innov. Comput. 2020, 10. [Google Scholar] [CrossRef]
- Sukhwani, H.; Martínez, J.M. Performance modeling of PBFT consensus process for permissioned blockchain network (hyperledger fabric). In Proceedings of the 2017 IEEE 36th Symposium on Reliable Distributed Systems (SRDS), Hong Kong, China, 26–29 September 2017; pp. 253–255. [Google Scholar]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Harn, L.; Hsu, C.F. Dynamic threshold secret reconstruction and its application to the threshold cryptography. Inf. Process. Lett. 2015, 115, 851–857. [Google Scholar] [CrossRef]
- Jamshidpour, S.; Ahmadian, Z. Security analysis of a dynamic threshold secret sharing scheme using linear subspace method. Inf. Process. Lett. 2020, 163, 105994. [Google Scholar] [CrossRef]
- Zhang, N.; Zang, Y.L.; Tian, J. The integration of biometrics and cryptography—A new solution for secure identity authentication. J. Cryptologic Res. 2015, 2, 159–176. [Google Scholar]



| Notation | Description |
|---|---|
| t | The value of the first threshold |
| v | The value of the second threshold |
| n | The number of peers |
| SHA-256 hash function | |
| Encoding a and b as strings for a concatenation operation | |
| Encoding a and b as a binary bit string for an XOR operation | |
| The wallet private key | |
| The biometric key of user | |
| The sub-secret of secret-sharing | |
| The sub-secret of secret-sharing | |
| The random number corresponding to | |
| The random number corresponding to | |
| The shadow share of | |
| The shadow share of | |
| The shadow number of | |
| The shadow number of | |
| The verification message of ss | |
| The verification message of ss |
| Scheme | Collusion Resistance | Single Peer Failure | Recoverability | Anonymity | Single Peer Control |
|---|---|---|---|---|---|
| Threshold signature scheme | ✓ | ✓ | ✓ | × | × |
| Multi-signature scheme | ✓ | ✓ | × | × | × |
| Hierarchical deterministic wallet | ✓ | × | ✓ | ✓ | ✓ |
| Proposed scheme | ✓ | ✓ | ✓ | ✓ | ✓ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, G.; You, L. A Consortium Blockchain Wallet Scheme Based on Dual-Threshold Key Sharing. Symmetry 2021, 13, 1444. https://doi.org/10.3390/sym13081444
Li G, You L. A Consortium Blockchain Wallet Scheme Based on Dual-Threshold Key Sharing. Symmetry. 2021; 13(8):1444. https://doi.org/10.3390/sym13081444
Chicago/Turabian StyleLi, Guojia, and Lin You. 2021. "A Consortium Blockchain Wallet Scheme Based on Dual-Threshold Key Sharing" Symmetry 13, no. 8: 1444. https://doi.org/10.3390/sym13081444
APA StyleLi, G., & You, L. (2021). A Consortium Blockchain Wallet Scheme Based on Dual-Threshold Key Sharing. Symmetry, 13(8), 1444. https://doi.org/10.3390/sym13081444






