Detecting Anonymous Target and Predicting Target Trajectories in Wireless Sensor Networks
Abstract
1. Introduction
2. Related Work
3. WSN Model for Anonymous Target Tracking
3.1. Rudimentary WSN Representation
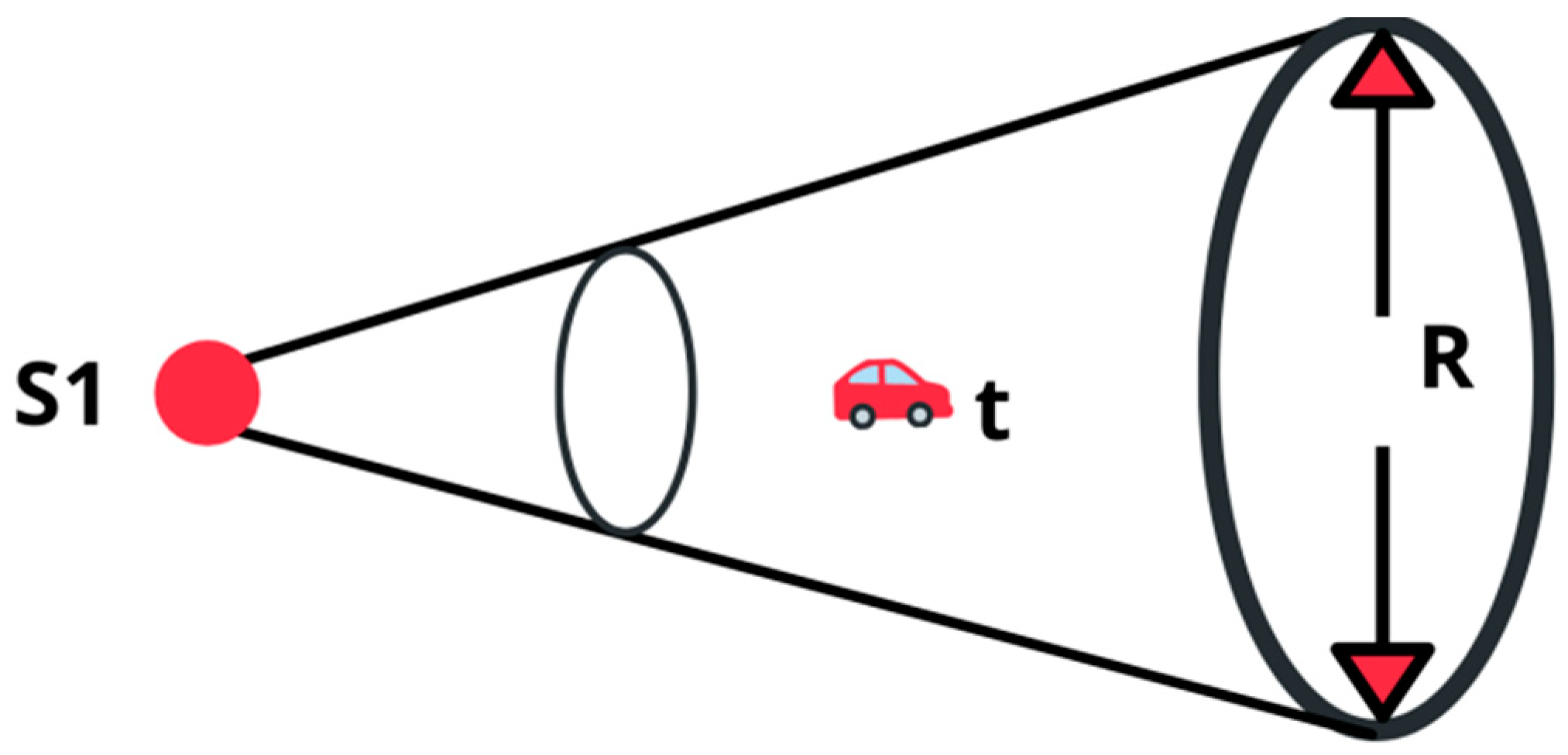
3.2. Sensor Representation for Detecting Targets
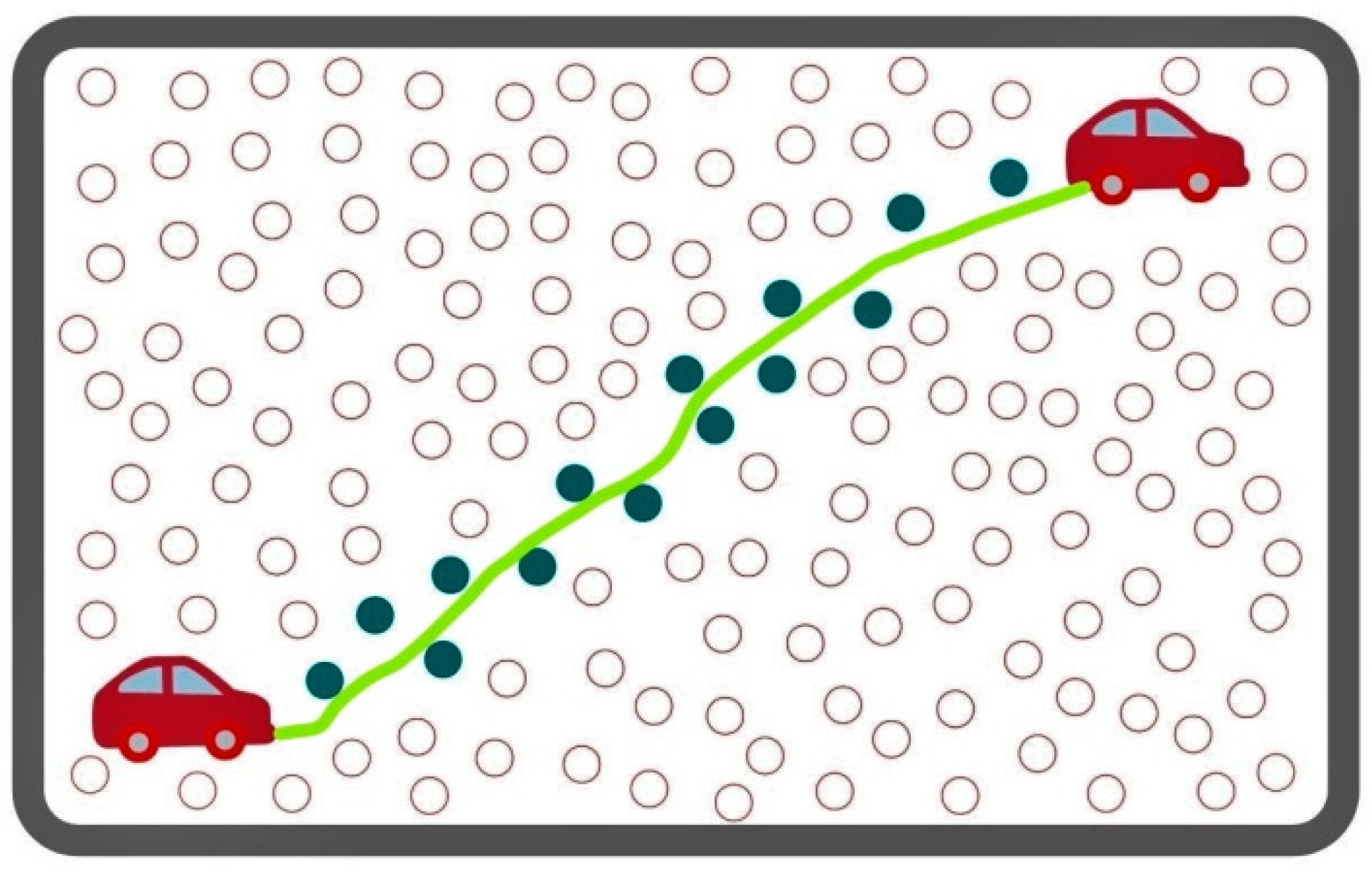
3.3. Strategies in Target Tracking
3.3.1. Naive Activation
3.3.2. Random Activation
3.3.3. Selective Activation
3.3.4. Periodic Activation
3.4. Representation of Energy in WSN
3.5. Representation of Target in Motion
- wx is not correlated to wy.
- Covariance and mean of multiplicative noise is given.
- Covariance and mean of additive noise is also given.
- Another crucial assumption is that if noises are absent, then it is fairly straightforward to determine position of the target.
4. Materials and Methods
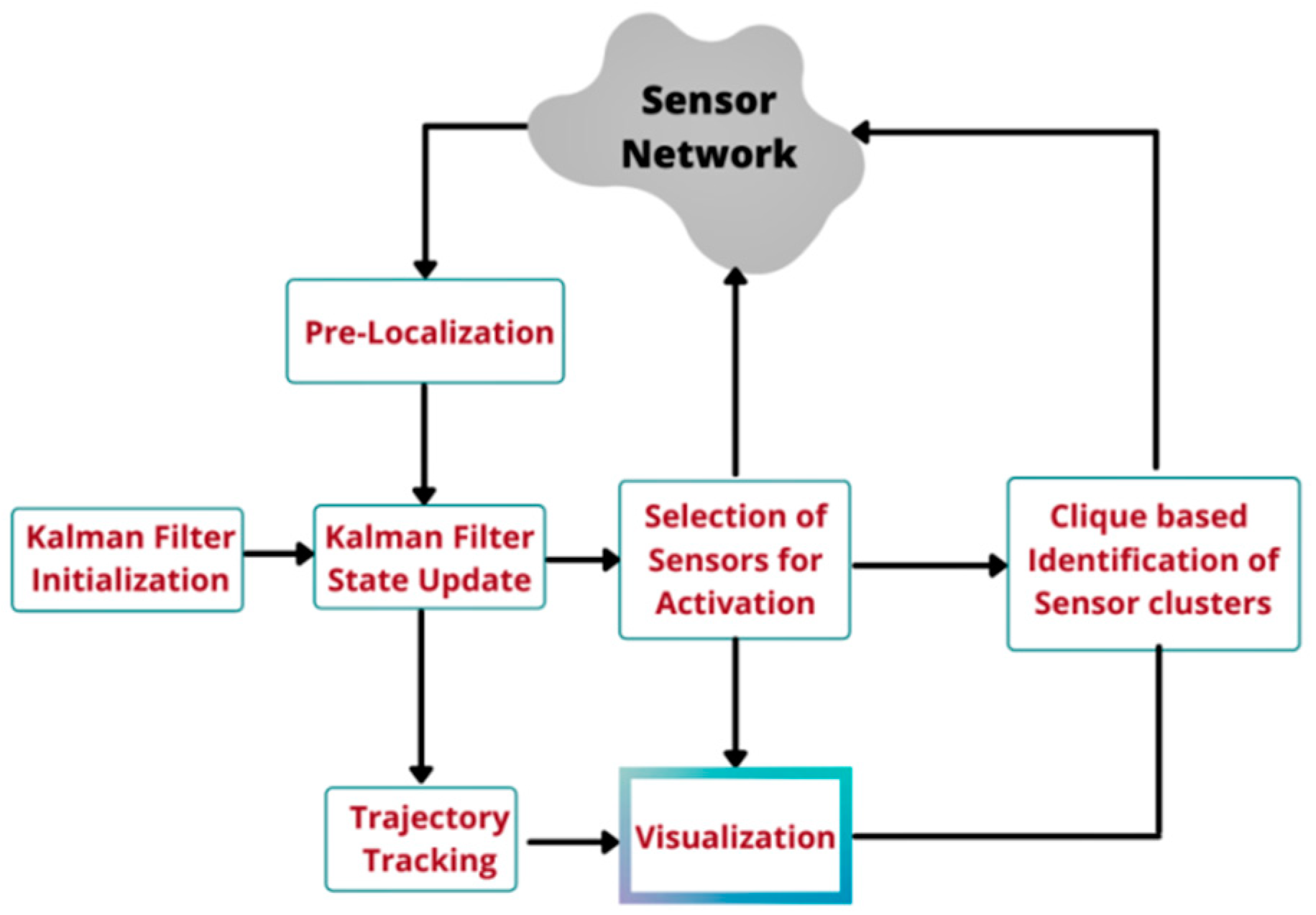
4.1. Proposed TDTT Model
4.2. Pre-Localization
4.3. Position Estimation Using KF
4.4. Choosing Sampling Period
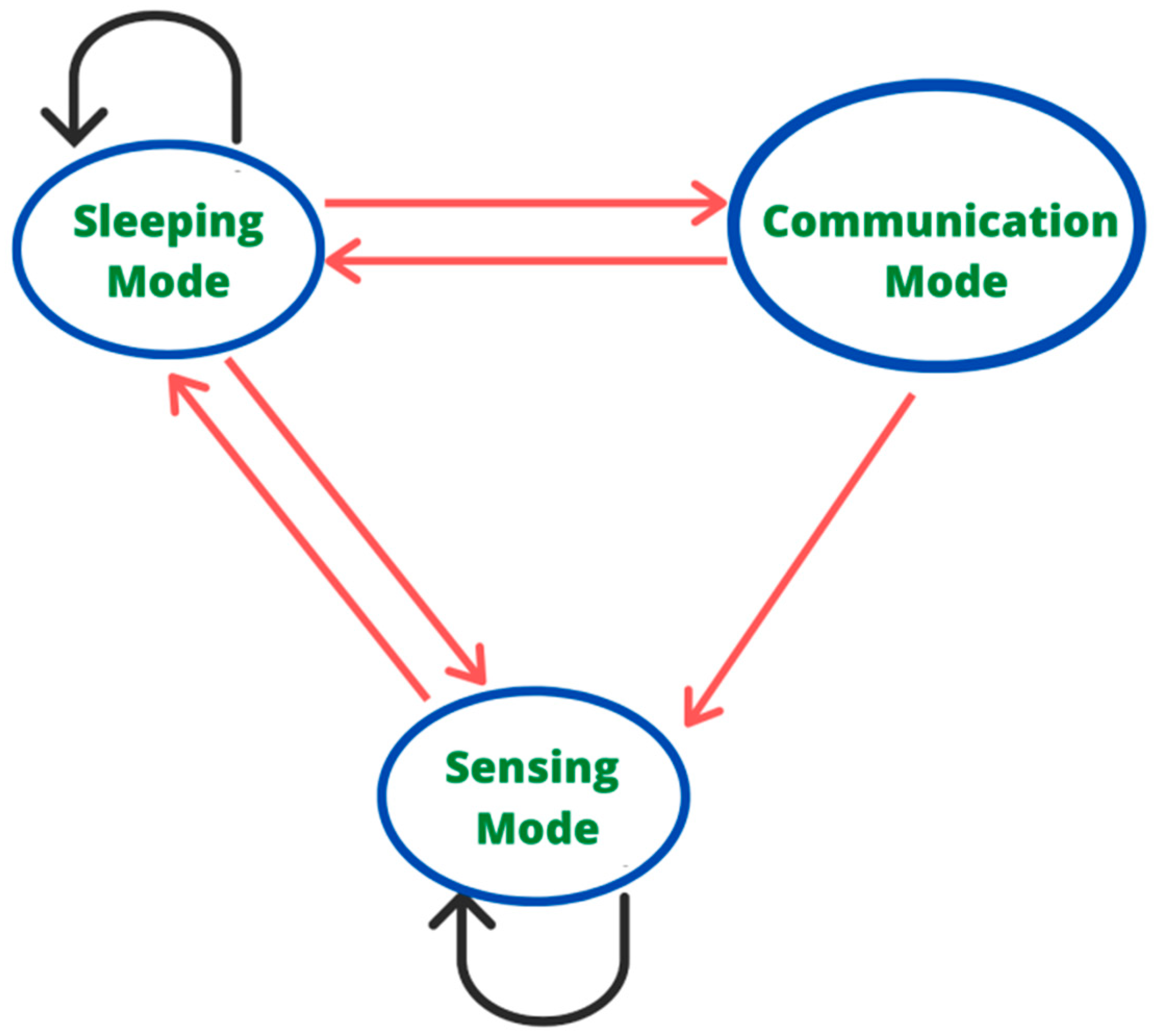
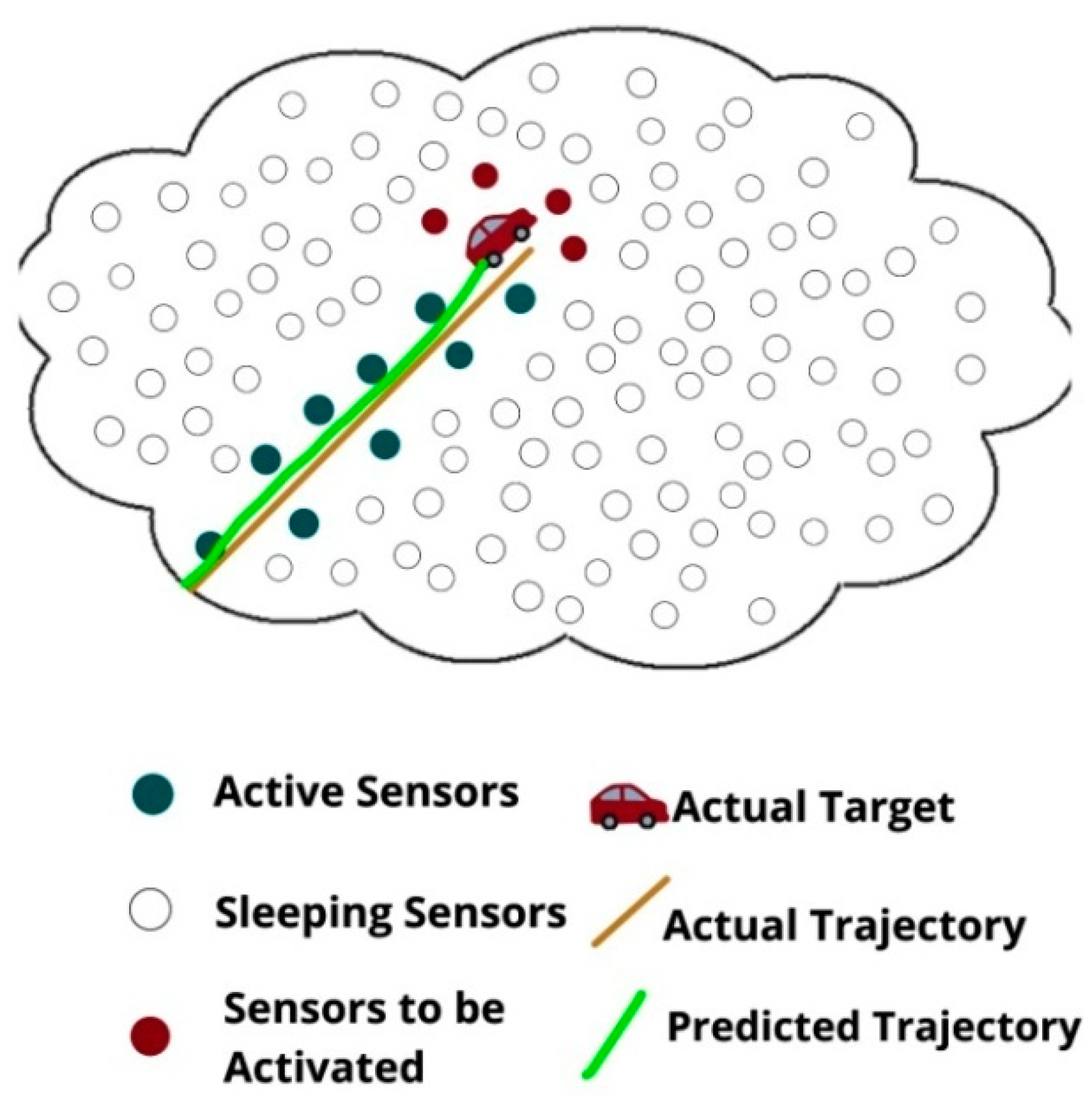
4.5. Choosing Sensors to Be in Sensing Mode
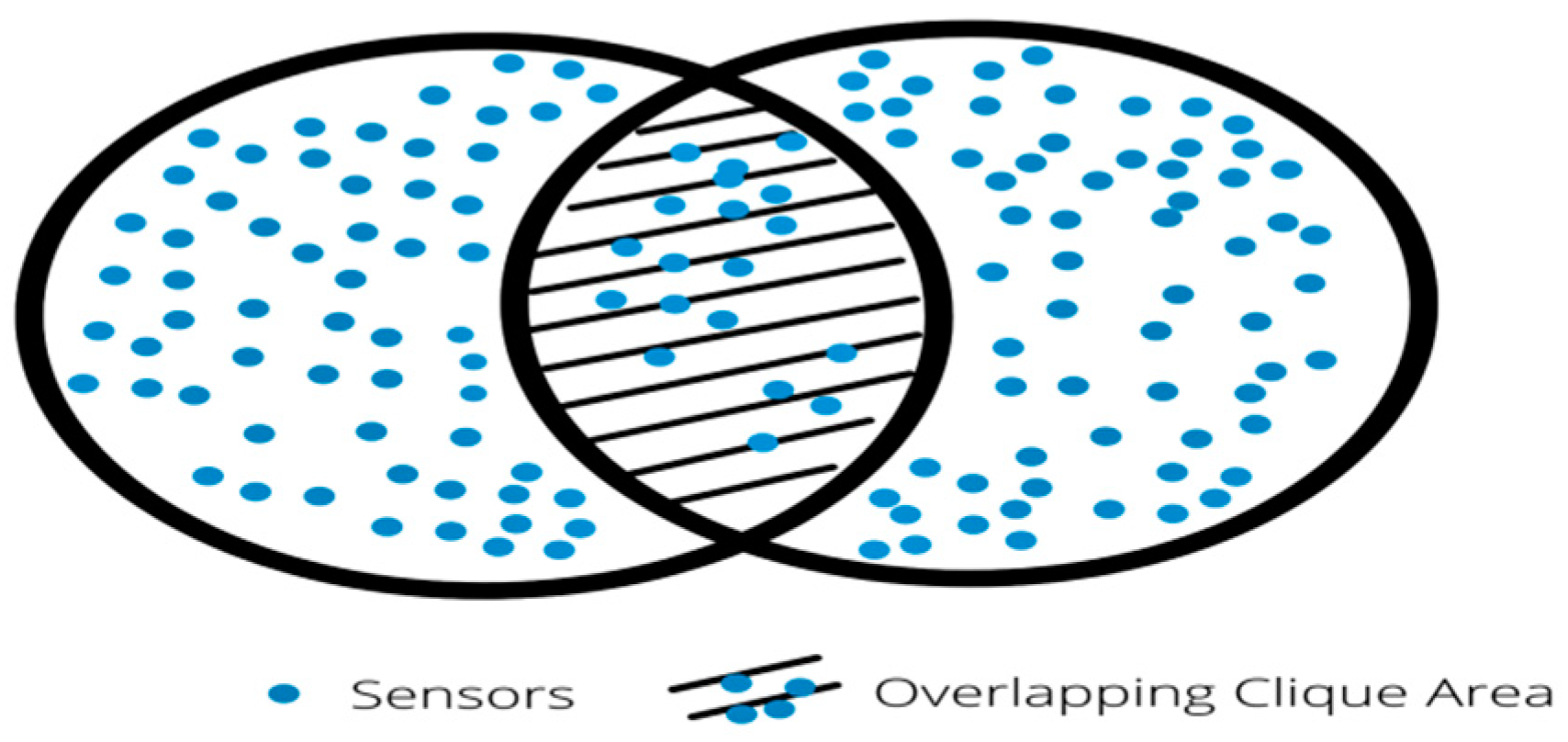
4.6. Identification of Successive Cliques
- t1 is detected by s3.
- s3 exchanges this information with the neighbors.
- s3 receives the information from all other neighbors and conducts the comparison between its own information and the neighbors’ information.
- All the neighboring sensor nodes are in sensing mode and t1 is tracked within the sensing region and the immediate neighbor closest to t1 maintains the required information.
- The clique in which t1 moves is constructed.
| Algorithm 1 TDTT Model |
| 1. Activate sensor at regular interval. |
| 2. Apply prelocalization on the set of activated sensors. |
| 3. Apply Kalman filter. |
| 4. If no target detected then go to step 1. |
| 5. Select neighboring set of sensors. |
| 6. Recalculate sampling period. |
| 7. Exchange information about target with its neighbor. |
| 8. Track target’s clique using monitor and backup operation. |
| 9. Compute direction of target’s motion. |
5. Results
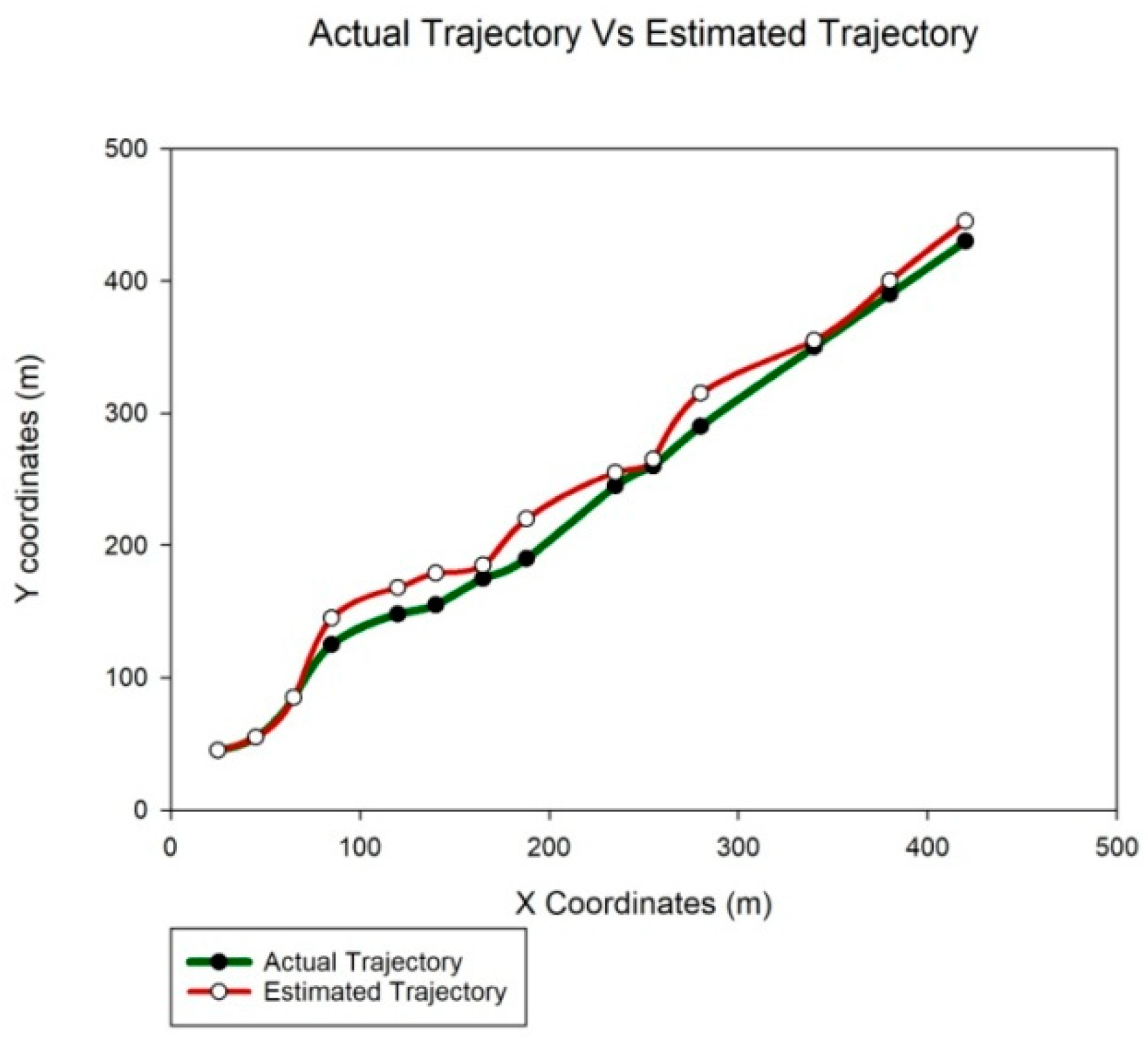
5.1. Scenario 1
5.2. Scenario 2
5.3. Scenario 3
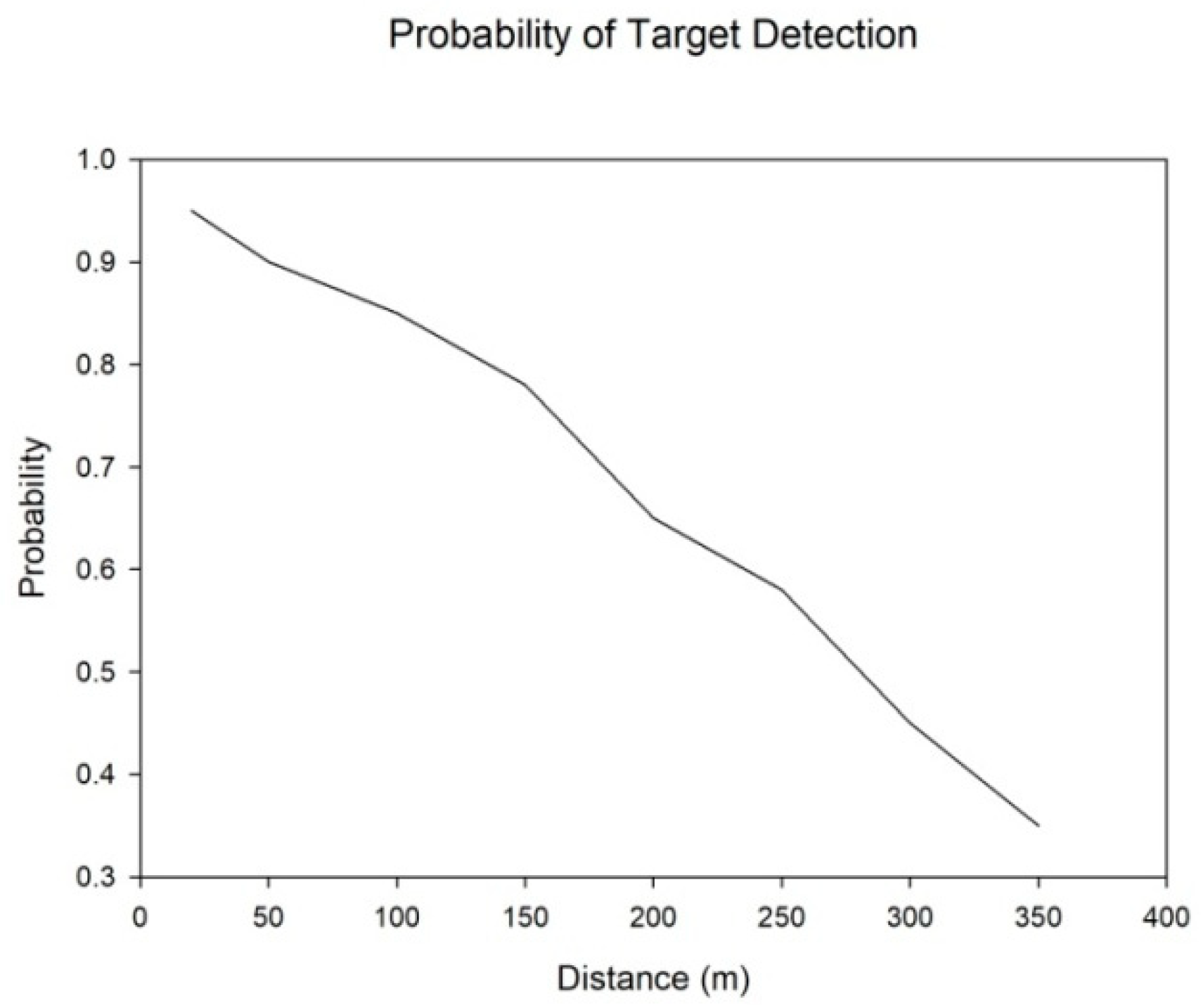
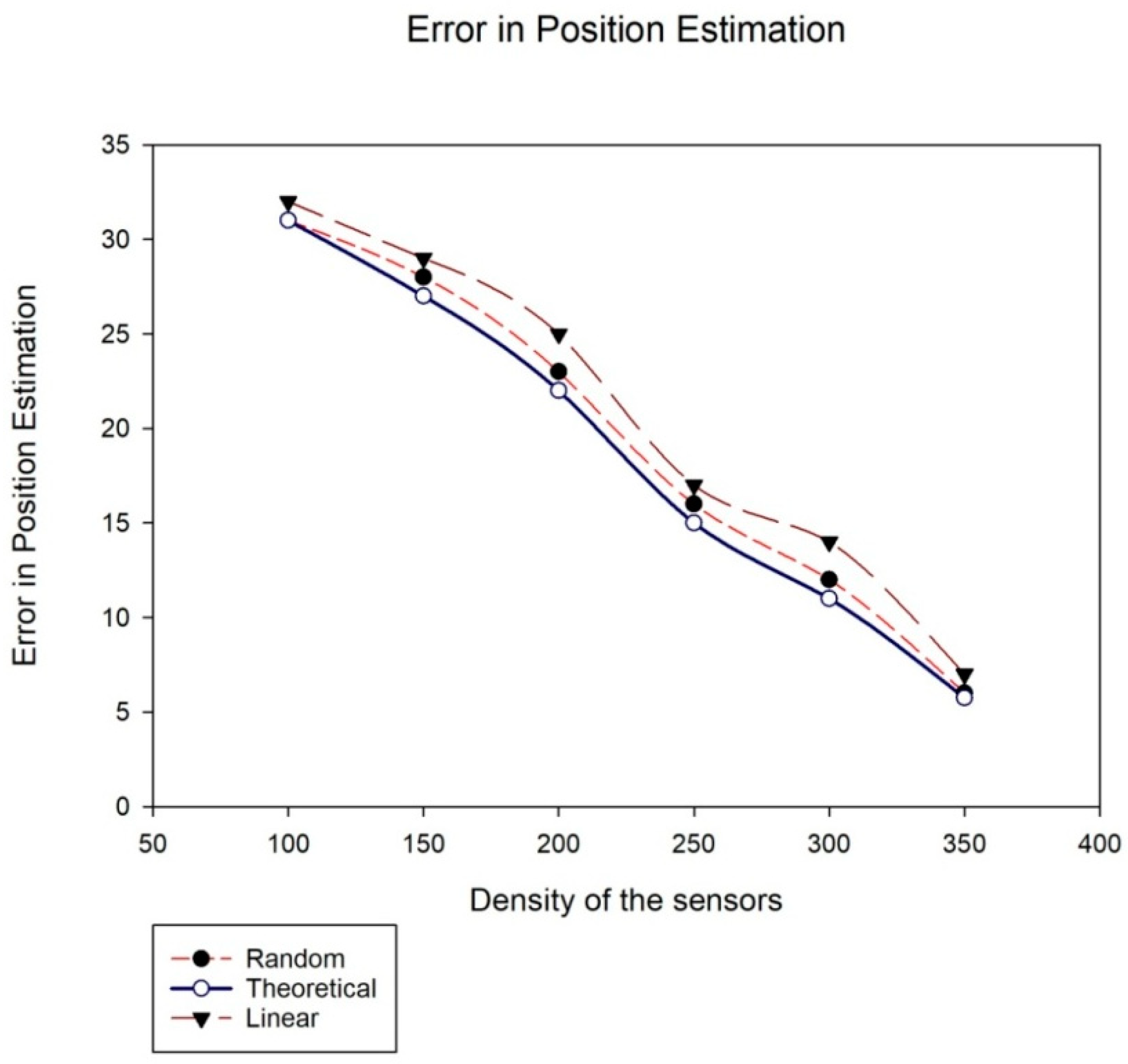
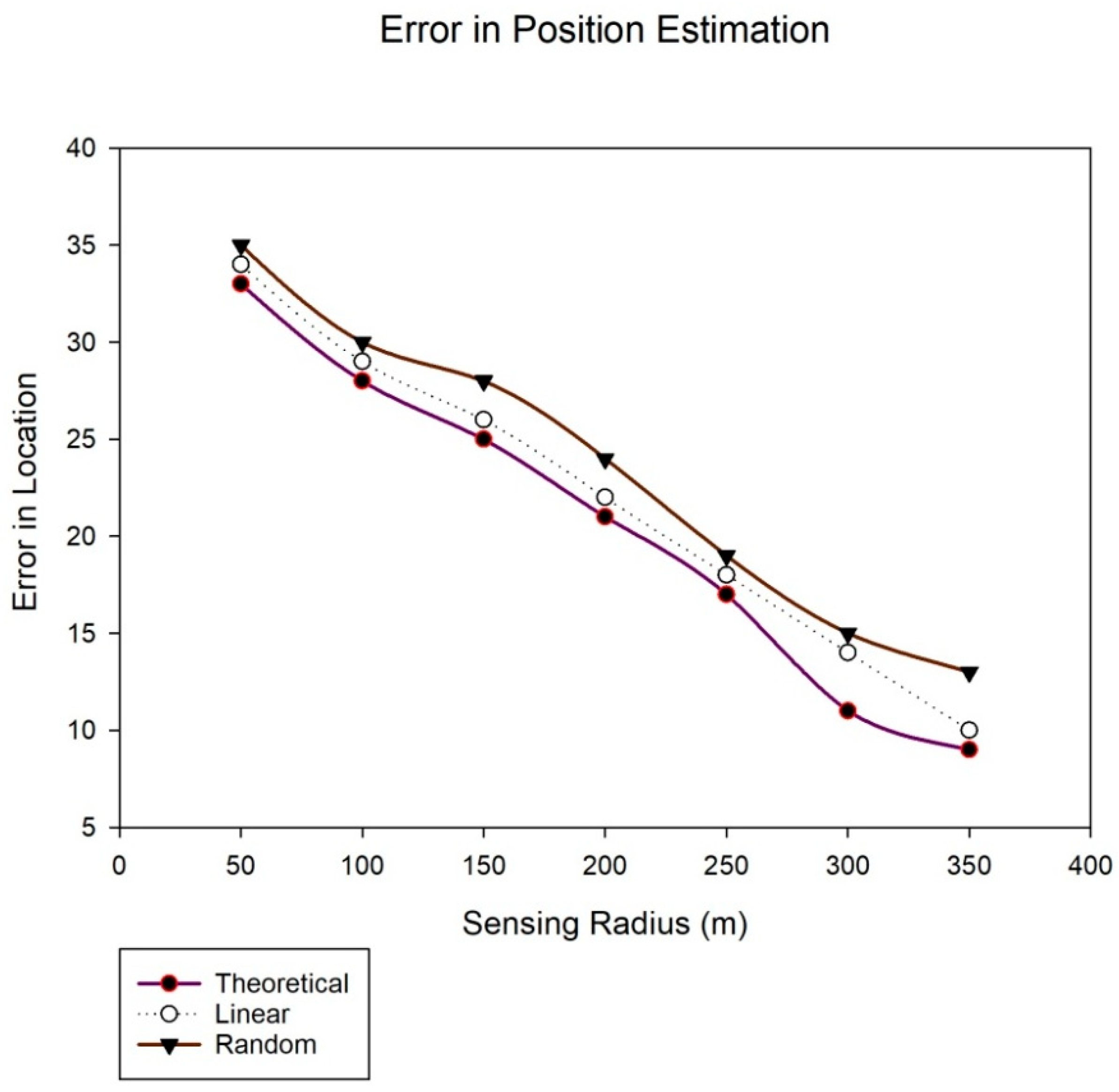
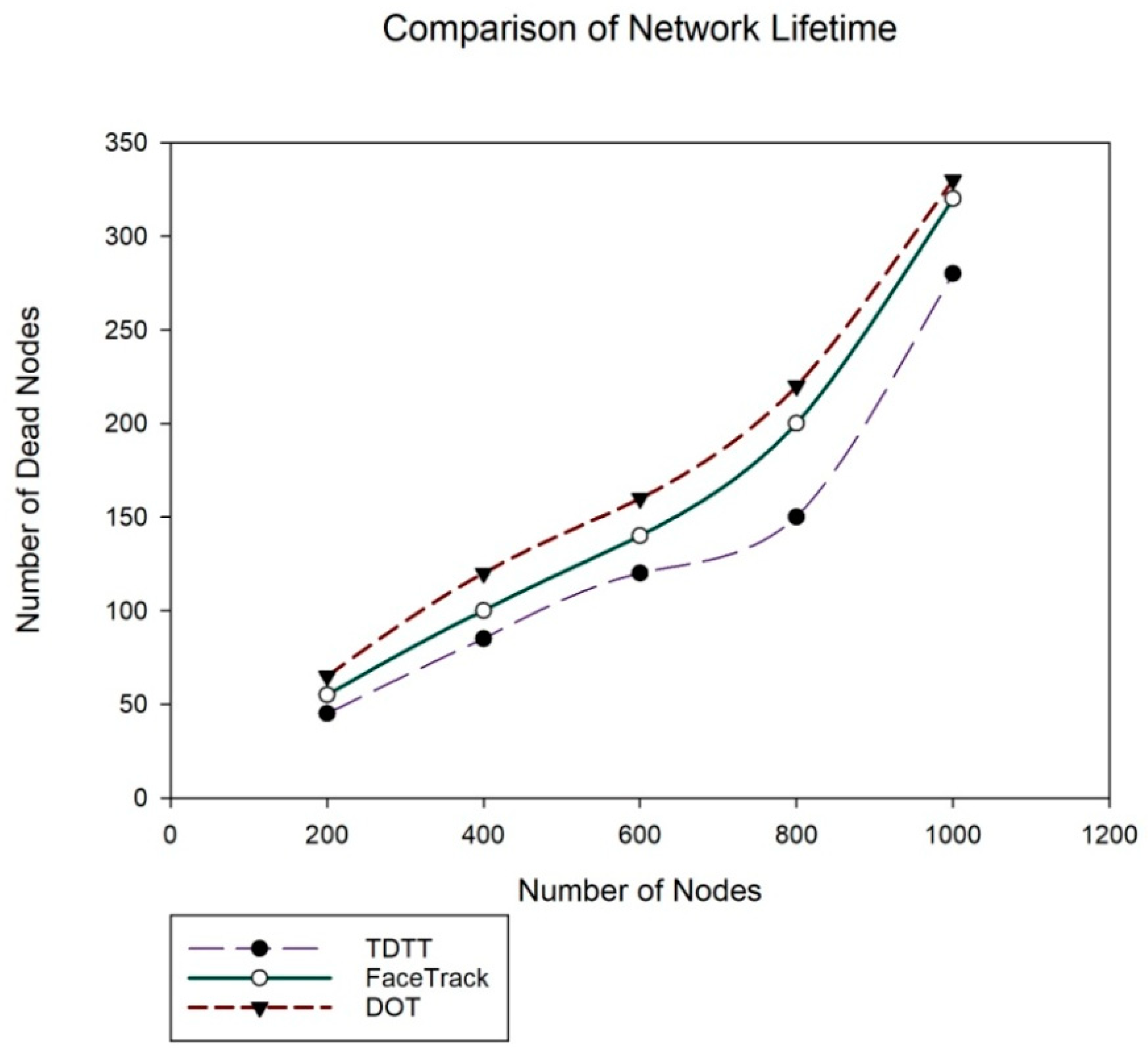
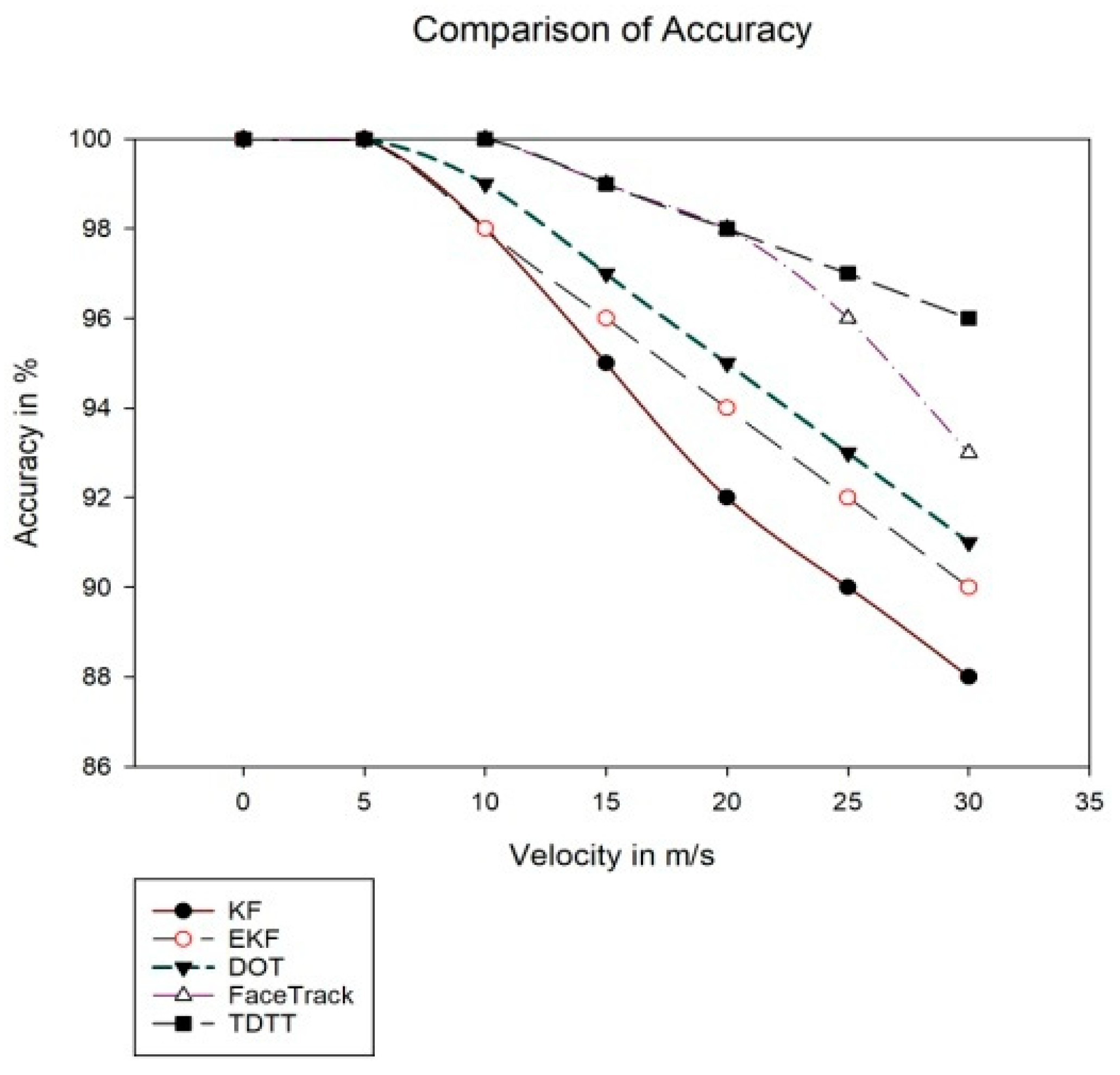
5.4. Comparison of TDTT with Other Existing Approaches in Terms of Accuracy
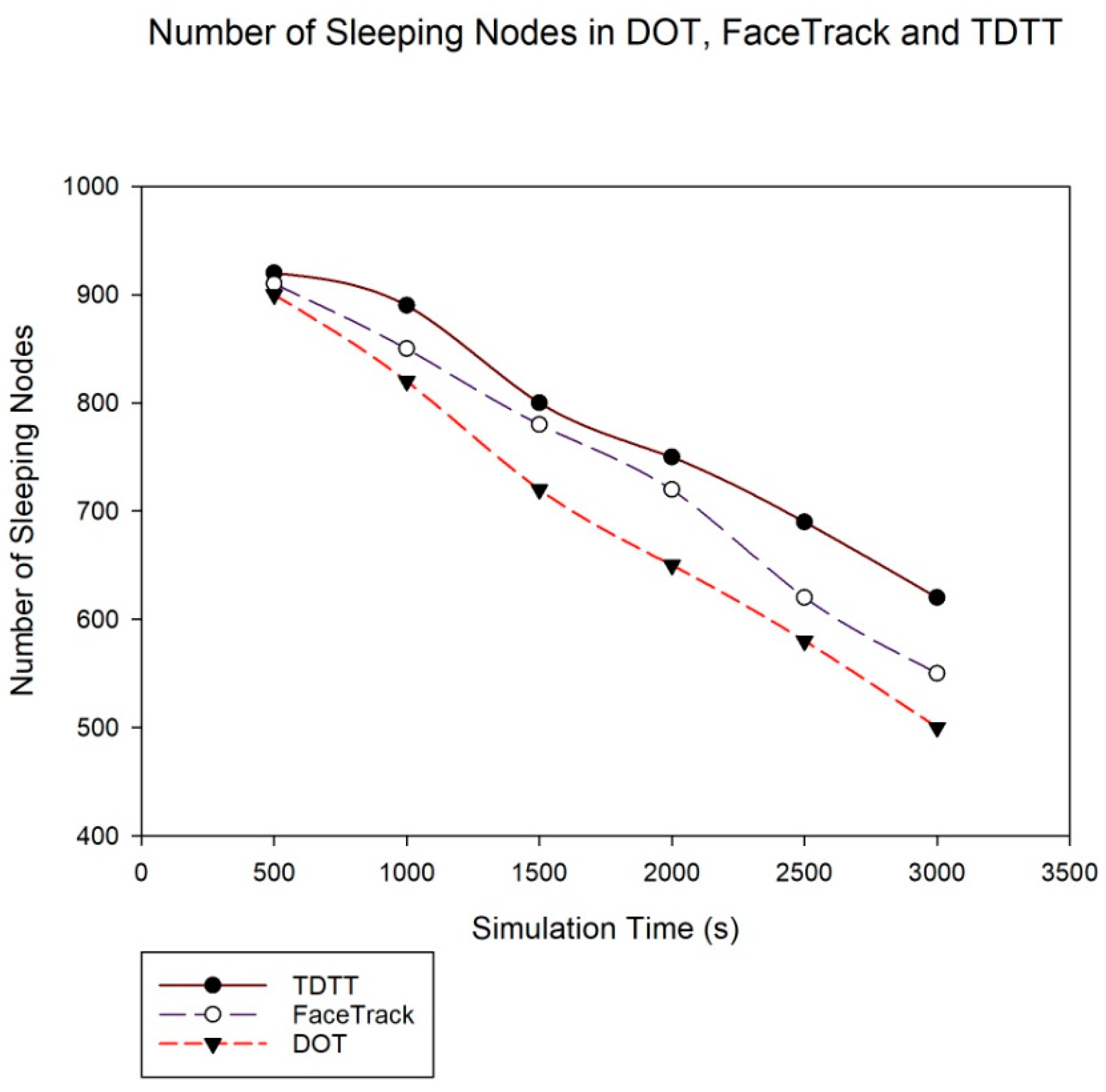
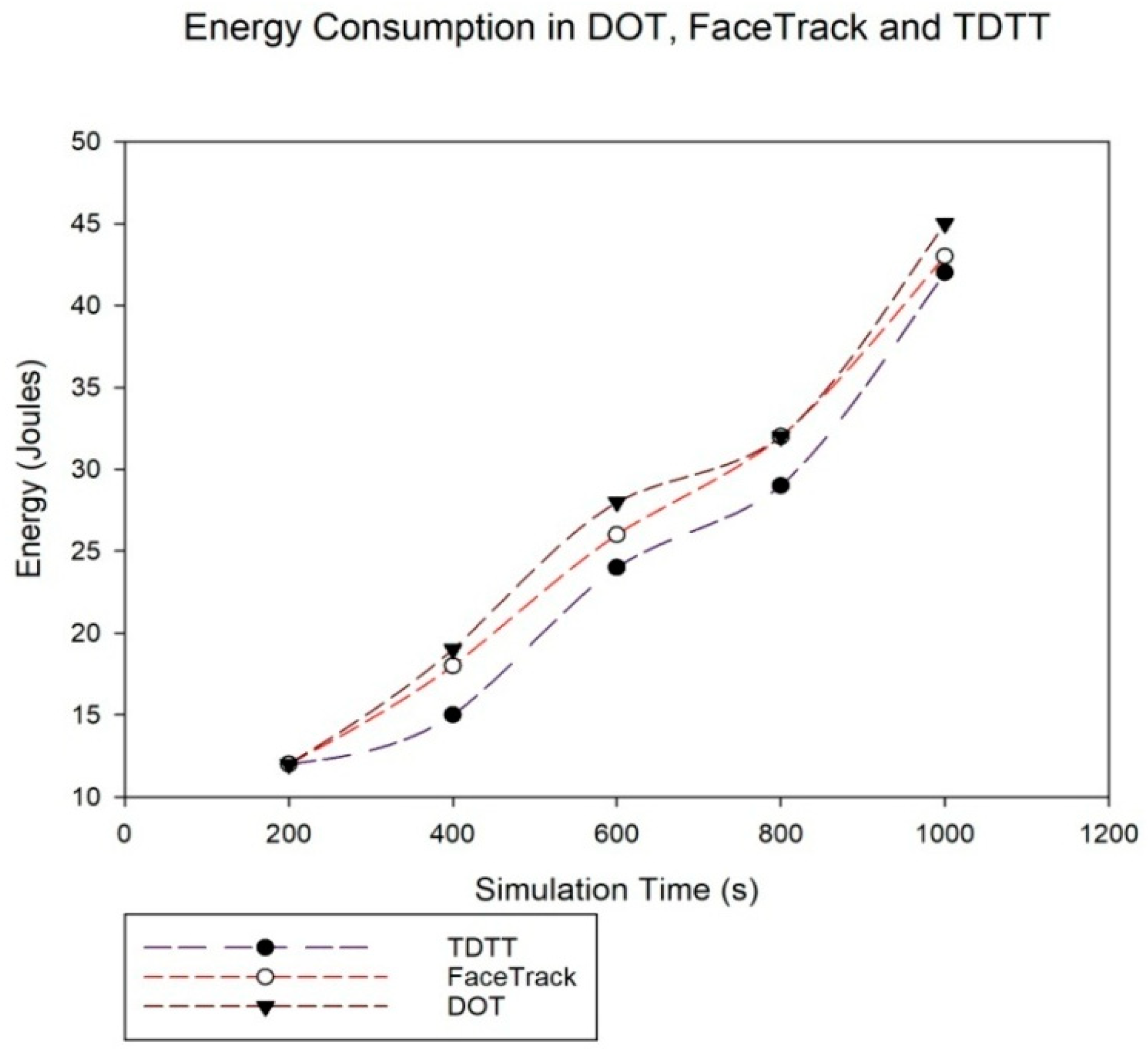
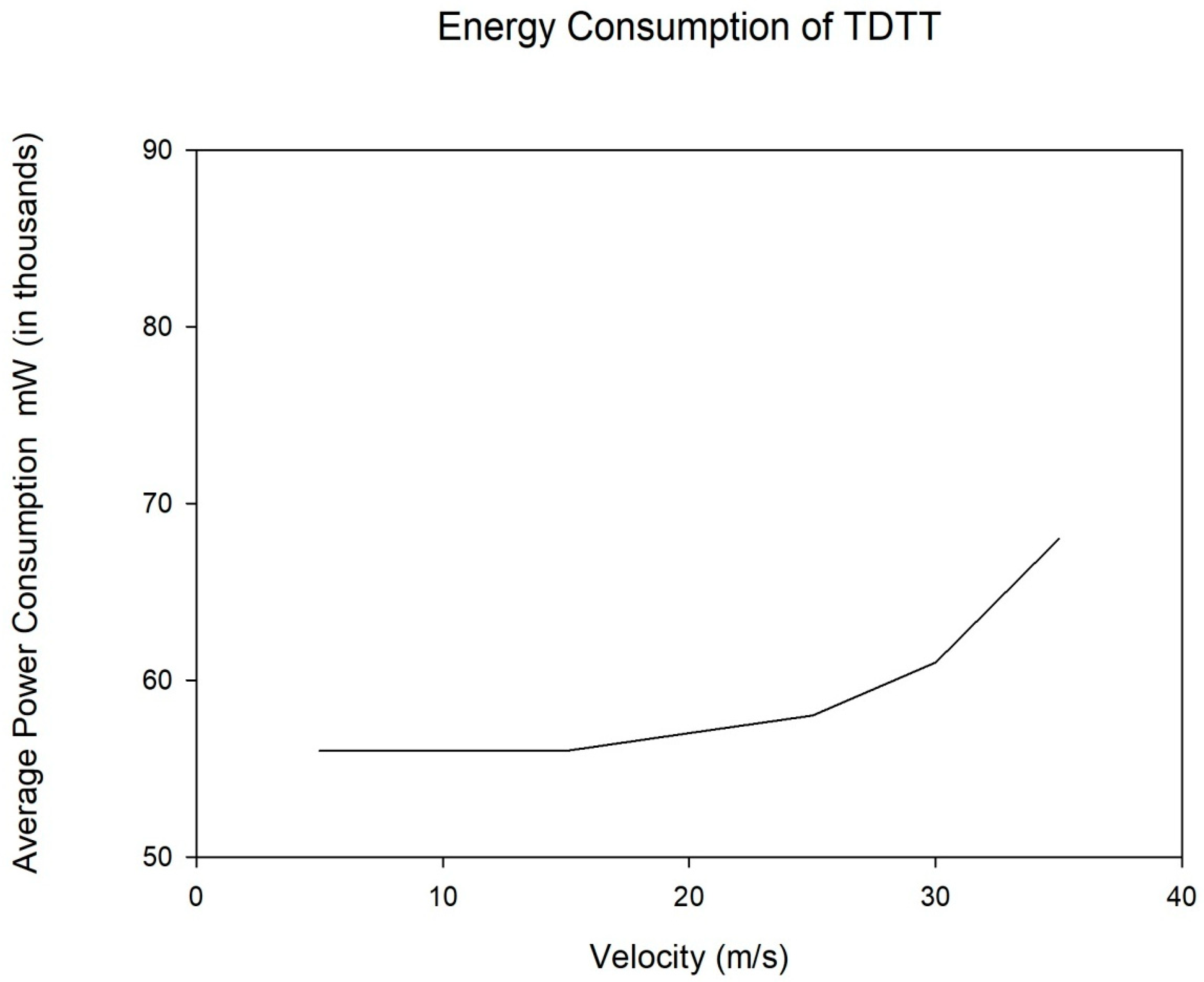
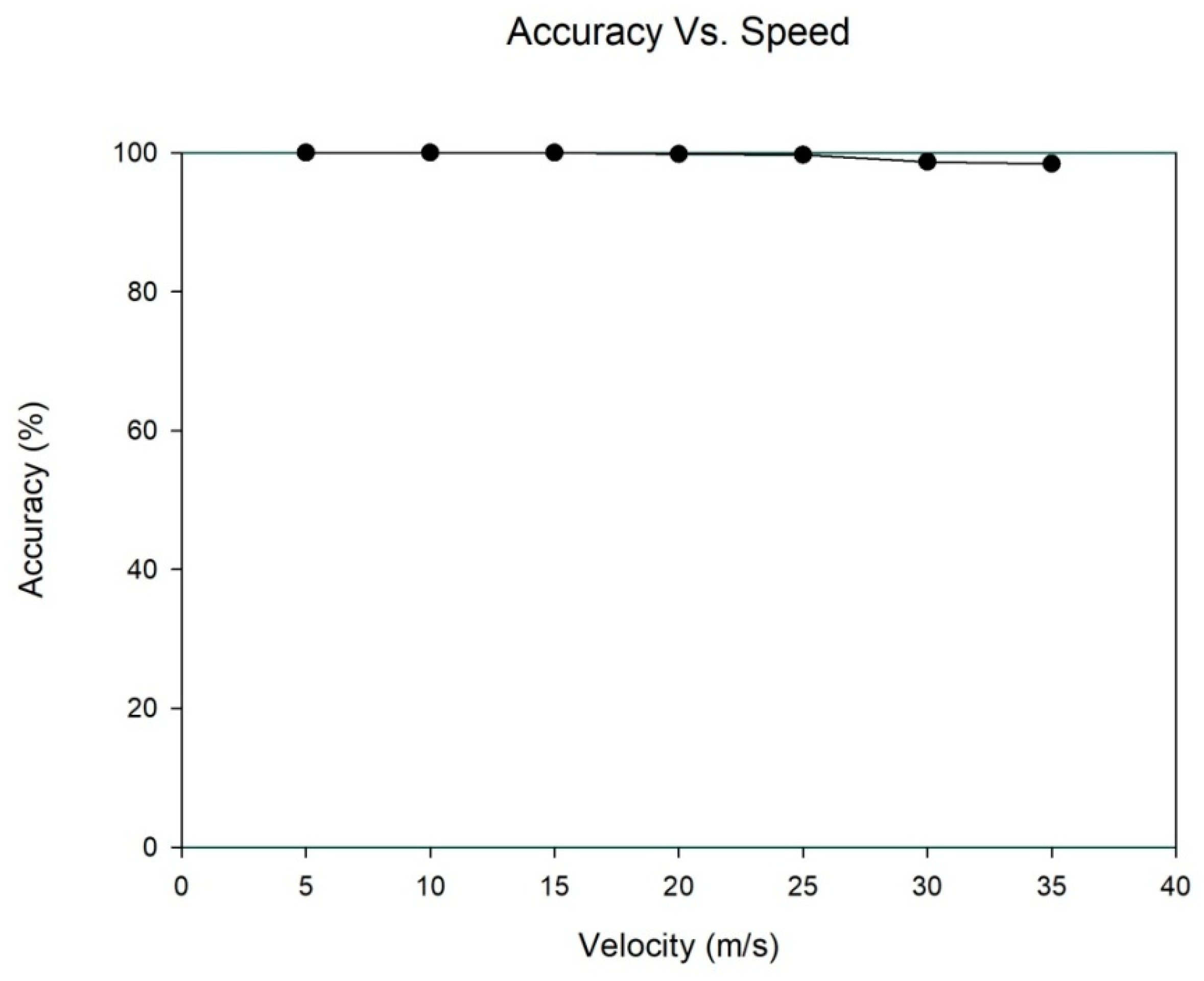
5.5. Assessment of Energy Consumption and Accuracy
6. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Conflicts of Interest
References
- Barile, G.; Leoni, A.; Pantoli, L.; Stornelli, V. Real-time autonomous system for structural and environmental monitoring of dynamic events. Electronics 2018, 7, 420. [Google Scholar] [CrossRef]
- Zhao, F.; Shin, J.; Reich, J. Information-driven dynamic sensor collaboration. IEEE Signal Process. Mag. 2002, 19, 61–72. [Google Scholar] [CrossRef]
- Lau, E.E.L.; Chung, W.Y. Enhanced RSSI-Based Real-Time User Location Tracking System for Indoor and Outdoor Environments. In Proceedings of the 2007 International Conference on Convergence Information Technology (ICCIT 2007), Gyeongju-si, Korea, 21–23 November 2007. [Google Scholar]
- Kumar, S.; Hegde, R.M. A Review of Localization and Tracking Algorithms in Wireless Sensor Networks 2017. Available online: http://arxiv.org/abs/1701.02080 (accessed on 9 January 2017).
- Viani, F.; Rocca, P.; Oliveri, G.; Trinchero, D.; Massa, A. Localization, tracking, and imaging of targets in wireless sensor networks: An invited review. Radio Sci. 2011, 46, RS5002. [Google Scholar] [CrossRef]
- Catovic, A.; Sahinoglu, Z. The Cramer-Rao bounds of hybrid TOA/RSS and TDOA/RSS location estimation schemes. IEEE Commun. Lett. 2004, 8, 626–628. [Google Scholar] [CrossRef]
- Vasuhi, S.; Vaidehi, V. Target tracking using interactive multiple model for wireless sensor network. Inf. Fusion 2016, 27, 41–53. [Google Scholar] [CrossRef]
- Cheng, L.; Wang, Y.; Sun, X.; Hu, N.; Zhang, J. A mobile localization strategy for wireless sensor network in NLOS conditions. China Commun. 2016, 13, 69–78. [Google Scholar] [CrossRef]
- Mahfouz, S.; Mourad-Chehade, F.; Honeine, P.; Farah, J.; Snoussi, H. Target tracking using machine learning and kalman filter in wireless sensor networks. IEEE Sens. J. 2014, 14, 3715–3725. [Google Scholar] [CrossRef]
- Souza, E.L.; Nakamura, E.F.; Pazzi, R.W. Target tracking for sensor networks: A survey. ACM Comput. Surv. 2016, 49. [Google Scholar] [CrossRef]
- Pahlavan, K.; Li, X. Indoor geolocation science and technology. IEEE Commun. Mag. 2002, 40, 112–118. [Google Scholar] [CrossRef]
- Ashraf, I.; Hur, S.; Park, Y. Indoor Positioning on Disparate Commercial Smartphones Using Wi-Fi Access Points Coverage Area. Sensors 2019, 19, 4351. [Google Scholar] [CrossRef]
- Ali, M.U.; Hur, S.; Park, S.; Park, Y. Harvesting Indoor Positioning Accuracy by Exploring Multiple Features From Received Signal Strength Vector. IEEE Access 2019, 7, 52110–52121. [Google Scholar] [CrossRef]
- Patwari, N.; Wilson, J. RF sensor networks for device-free localization: Measurements, models, and algorithms. Proc. IEEE 2010, 99, 1–13. [Google Scholar] [CrossRef]
- Wilson, J.; Patwari, N. See through walls: Motion tracking using variance-based radio tomography networks. IEEE Trans. Mobile Comput. 2011, 10, 612–621. [Google Scholar] [CrossRef]
- Touvat, F.; Poujaud, J.; Noury, N. Indoor localization with wearable RF devices in 868 MHz and 2.4 GHz bands. In Proceedings of the IEEE 16th International Conference on e-Health Networking, Applications and Services (Healthcom), Natal, Brazil, 15–18 October 2014; pp. 136–139. [Google Scholar]
- Bosisio, A.V. Performances of an RSSI-based positioning and tracking algorithm. In Proceedings of the Indoor Positioning and Indoor Navigation (IPIN), 2011 International Conference, Guimarães, Portugal, 21–23 September 2011; pp. 1–8. [Google Scholar] [CrossRef]
- Leela Rani, P.; Sathish Kumar, G.A. A survey on algorithms used for tracking targets in WSNs. In Proceedings of the 2017 International Conference on Energy, Communication, Data Analytics and Soft Computing (ICECDS), Chennai, India, 1–2 August 2017; pp. 1464–1468. [Google Scholar] [CrossRef]
- Sadowski, S.; Spachos, P. RSSI-Based Indoor Localization with the Internet of Things. IEEE Access 2018, 6, 30149–30161. [Google Scholar] [CrossRef]
- Ceylan, O.; Taraktas, K.F.; Yagci, H.B. Enhancing RSSI Technologies in Wireless Sensor Networks by Using Different Frequencies. In Proceedings of the 2010 International Conference on Broadband, Wireless Computing, Communication and Applications, Fukuoka, Japan, 4–6 November 2010; pp. 369–372. [Google Scholar] [CrossRef]
- Ahmadi, H.; Viani, F.; Polo, A.; Bouallegue, R. Improved target tracking using regression tree in wireless sensor networks. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–6. [Google Scholar]
- Jondhale, S.R.; Deshpande, R.S.; Walke, S.M.; Jondhale, A.S. Issues and challenges in RSSI based target localization and tracking in wireless sensor networks. In Proceedings of the 2016 International Conference on Automatic Control and Dynamic Optimization Techniques (ICACDOT), Pune, India, 9–10 September 2016; pp. 594–598. [Google Scholar] [CrossRef]
- Din, S.; Paul, A.; Ahmad, A.; Kimet, J.H. Energy efficient topology management scheme based on clustering technique for software defined wireless sensor network. Peer-to-Peer Netw. Appl. 2019, 12, 348–356. [Google Scholar] [CrossRef]
- Sthapit, P.; Gang, H.; Pyun, J. Bluetooth Based Indoor Positioning Using Machine Learning Algorithms. In Proceedings of the 2018 IEEE International Conference on Consumer Electronics-Asia (ICCE-Asia), JeJu, Korea, 24–26 June 2018; pp. 206–212. [Google Scholar] [CrossRef]
- Banihashemian, S.S.; Adibnia, F.; Sarram, M.A. A New Range-Free and Storage-Efficient Localization Algorithm Using Neural Networks in Wireless Sensor Networks. Wireless Pers. Commun. 2018, 98, 1547–1568. [Google Scholar] [CrossRef]
- Kalman, R.E.; Bucy, R.S. A new approach to linear filtering and prediction problems. Trans. ASME J. Basic Eng. ASME 1960, 82D, 34–45. [Google Scholar] [CrossRef]
- Giannitrapani, A.; Ceccatrlli, N.; Scortecci, F.; Garulli, A. Comparison of EKF and UKF for Spacecraft Localization via Angle Measurements. IEEE Trans. Aerosp. Electron. Syst. 2011, 47, 75–84. [Google Scholar] [CrossRef]
- Fayazi Barjini, E.; Gharavian, D.; Shahgholian, M. Target tracking in wireless sensor networks using NGEKF algorithm. J. Ambient Intell. Human Comput. 2020, 11, 3417–3429. [Google Scholar] [CrossRef]
- Jondhale, S.R.; Deshpande, R.S. Kalman Filtering Framework-Based Real Time Target Tracking in Wireless Sensor Networks Using Generalized Regression Neural Networks. IEEE Sens. J. 2019, 19, 224–233. [Google Scholar] [CrossRef]
- Chuang, P.-J.; Jiang, Y. Effective neural network-based node localisation scheme for wireless sensor networks. IET Wirel. Sens. Syst. 2014, 4, 97–103. [Google Scholar] [CrossRef]
- Torres-Sospedra, J.; Montoliu, R.; Martínez-Usó, A.; Avariento, J.P.; Arnau, T.J.; Benedito-Bordonau, M.; Huerta, J. Ujiindoorloc: A new multi-building and multi floor database for WLAN finger print based indoor localization problem. In Proceedings of the 2014 International Conference on Indoor Positioning and Indoor Navigation (IPIN), Busan, Korea, 27–30 October 2014; pp. 261–270. [Google Scholar]
- Ali, K.; Rasid, M.F.A.; Sali, A. Face-Based Mobile Target Tracking Technique in Wireless Sensor Network. Wirel. Pers. Commun. 2020, 111, 1853–1870. [Google Scholar] [CrossRef]
- Tsai, H.-W.; Chu, C.-P.; Chen, T.-S. Mobile object tracking in wireless sensor networks. Comput. Commun. 2007, 30, 1811–1825. [Google Scholar] [CrossRef]
- Wang, G.; Bhuiyan, M.; Cao, J.; Wu, J. Detecting movements of a target using face tracking in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1–11. [Google Scholar] [CrossRef]
- Javed, N.; Wolf, T. Multiple object tracking in sensor networks using distributed clique finding. In Proceedings of the 2013 International Conference on Computing, Networking and Communications (ICNC), San Diego, CA, USA, 28–31 January 2013; pp. 1139–1145. [Google Scholar] [CrossRef]

Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Leela Rani, P.; Sathish Kumar, G.A. Detecting Anonymous Target and Predicting Target Trajectories in Wireless Sensor Networks. Symmetry 2021, 13, 719. https://doi.org/10.3390/sym13040719
Leela Rani P, Sathish Kumar GA. Detecting Anonymous Target and Predicting Target Trajectories in Wireless Sensor Networks. Symmetry. 2021; 13(4):719. https://doi.org/10.3390/sym13040719
Chicago/Turabian StyleLeela Rani, P., and G. A. Sathish Kumar. 2021. "Detecting Anonymous Target and Predicting Target Trajectories in Wireless Sensor Networks" Symmetry 13, no. 4: 719. https://doi.org/10.3390/sym13040719
APA StyleLeela Rani, P., & Sathish Kumar, G. A. (2021). Detecting Anonymous Target and Predicting Target Trajectories in Wireless Sensor Networks. Symmetry, 13(4), 719. https://doi.org/10.3390/sym13040719




