A Traceable Firearm Management System Based on Blockchain and IoT Technology
Abstract
:1. Introduction
2. Preliminary and Security Requirements
2.1. Elliptic Curve Digital Signature Algorithm (ECDSA)
2.2. Burrows–Abadi–Needham logic (BAN logic) Logic
2.3. Security Requirements
3. The Proposed Scheme
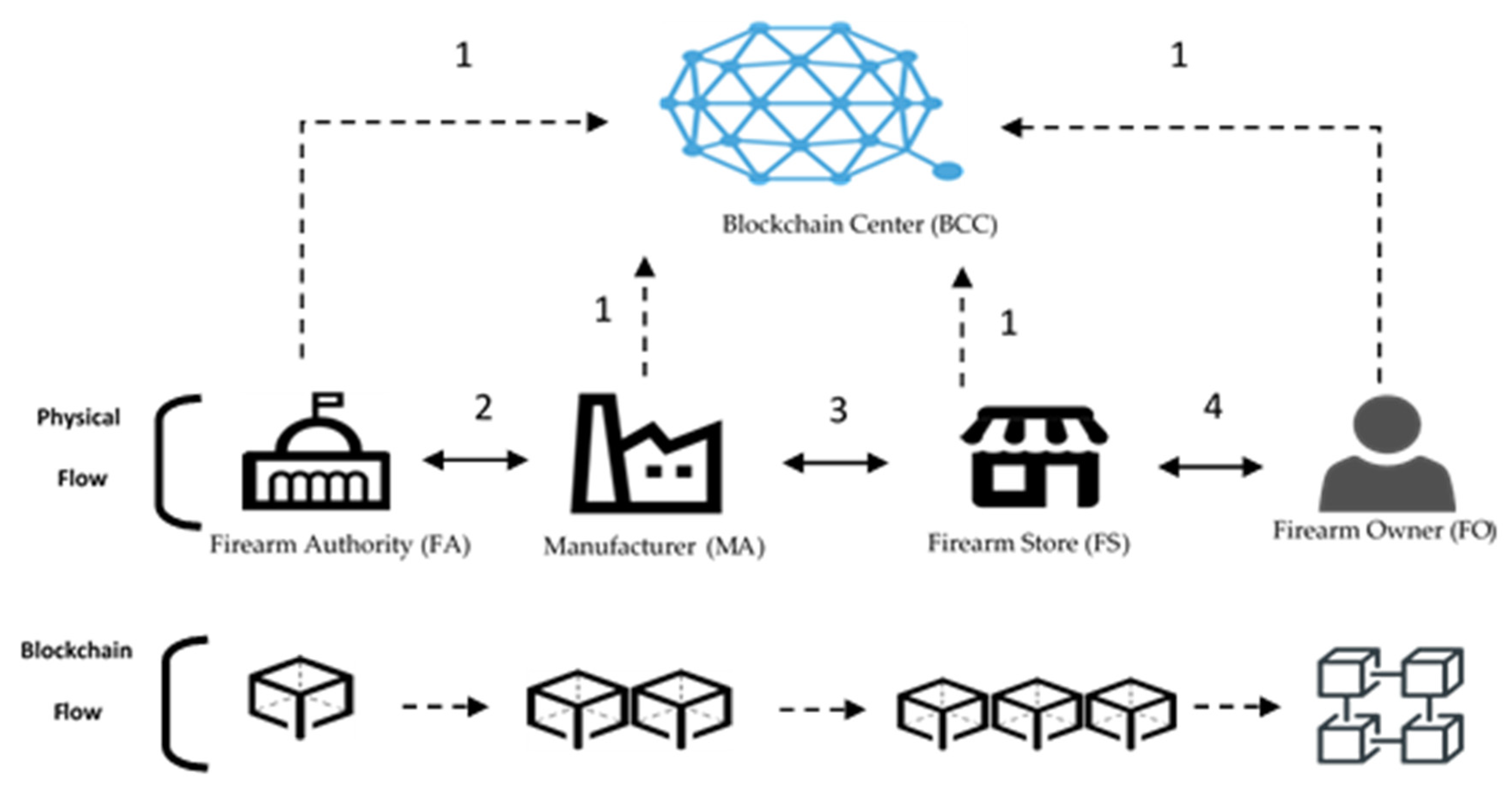
3.1. System Architecture
- Blockchain center (BCC): An Ethereum platform to produce a public key and private key for participating parties.
- Firearm authority (FA): This is the firearm management department that belongs to the government organization. This is a trusted institution. The firearm management must authenticate and certify a user when any party wants to purchase the firearm.
- Manufacturer (MA): They produce the firearm and sell the firearm to the retailer. Moreover, they can also produce the genesis blockchain after obtaining the license.
- Firearm store (FS): They sell the firearm to the customer. In addition, they can join a transaction to the blockchain after obtaining the license.
- Firearm owner (FO): They can proceed with the transaction to buy a firearm, and they are allowed to add this transaction to the blockchain.
- Step 1.
- All parties want to register with the BCC. All parties get public/private keys from the BCC.
- Step 2.
- When the MA produces the firearm, the MA must embed an RFID tag in the firearm. Then, the MA hands out to the FA to upload the firearm data to the genesis blockchain. After uploading, the firearm is sent back to the MA.
- Step 3.
- The MA uses the blockchain to initiate a transaction to the FS and deliver the firearm to the FS. After the FS receives the firearm, the firearm transaction is recorded to the blockchain center.
- Step 4.
- If the FO wants to buy the firearm, the FS initiates a transaction in the blockchain and delivers the firearm to the FO.
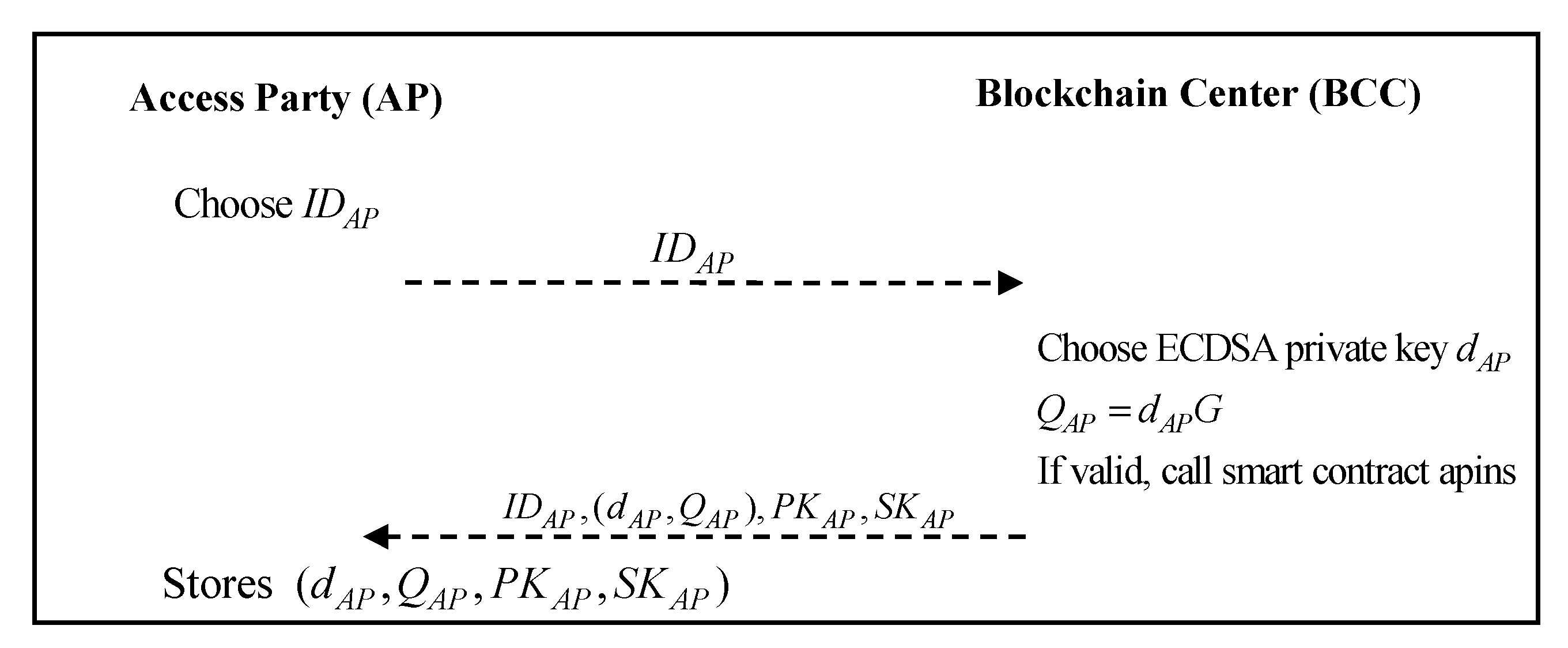
3.2. Registration Phase
| Algorithm 1. Smart contract apins of the proposed scheme. | |
| function insert ap smart contract apins ( string ap_id, string ap_detail) { count ++; ap[count].id = id; | ap[count].id = id; } string ap_keypairs; |
3.3. Smart Contract Initialization
| Algorithm 2. Smart contract mafainf/famainf/mafsinf/fsmainf of the proposed scheme. | |
| struct smart contract mafainf/famainf/mafsinf/ fsmainf { string mafa/fama/mafs/fsma id; string mafa/fama/mafs/fsma detail; string mafa/fama/mafs/fsma cert; string mafa/fama/mafs/fsma tsp; } | struct smart contract mafainf/famainf/mafsinf/ string fofs/fsfo id; string fofs/fsfo detail; string fofs/fsfo ssn; string fofs/fsfo tsp; } string keypairs; string count; |
3.4. Authorized Production Phase
- Step 1:
- The MA generates a random value , calculates , , , , , and sends to the FA.
- Step 2:
- The FA first calculates , uses to confirm whether the timestamp is valid, and then verifies the correctness of the ECDSA signature, by calculating ,, , , . If the verification is passed, the FA gets the relevant production request information and trigger the smart contracts mafains and mafachk. The content is the Algorithm 3 as follows:
| Algorithm 3. Smart contract mafains of the proposed scheme. | |
| function insert smart contract mafains( string mafa_id, string mafa_detail, string mafa_cert, string mafa_tsp) { count ++; mafa[count].id = id; mafa[count].detail = detail; mafa[count].cert = cert; mafa[count].tsp = tsp; } sign string ma_key (mafa_id, mafa_detail, mafa_cert, mafa_tsp); | verify string ma_key (mafa_id, mafa_detail, mafa_cert, mafa_tsp); function check smart contract mafachk( string mafa_id, string mafa_detail, string mafa_cert, string mafa_tsp) { return mafa_id.exist; return mafa_detail.exist; return mafa_cert.exist; return mafa_tsp.exist; } |
- Step 3.
- The MA first calculates , uses to confirm whether the timestamp is valid, and then verifies the correctness of the ECDSA signature, calculates , , , , . If the verification is passed, the production request information is confirmed by MA, and the smart contracts famains and famachk are sent. The content is the Algorithm 4 as follows:
| Algorithm 4. Smart contract famains of the proposed scheme. | |
| function insert smart contract famains( string fama_id, string fama_detail, string fama_cert, string fama_tsp) { count ++; fama[count].id = id; fama[count].detail = detail; fama[count].cert = cert; fama[count].tsp = tsp; } sign string fa_key (fama_id, fama_detail, fama_cert, fama_tsp); | verify string fa_key (fama_id, fama_detail, fama_cert, fama_tsp); function check smart contract famachk( string fama_id, string fama_detail, string fama_cert, string fama_tsp) { return fama_id.exist; return fama_detail.exist; return fama_cert.exist; return fama_tsp.exist; } |
3.5. Firearm Selling Phase
- Step 1:
- The MA generates a random value , calculates , , , , , and sends to the FS.
- Step 2:
- The FS first calculates , uses to confirm whether the timestamp is valid, verifies the correctness of the ECDSA signature, and then calculates , , , , . If the verification is passed, the FS gets the relevant firearm production information and trigger the smart contracts mafsins and mafschk. The content is the Algorithm 5 as follows:
| Algorithm 5. Smart contract mafsins of the proposed scheme. | |
| function insert smart contract mafsins( string mafs_id, string mafs_detail, string mafs_cert, string mafs_tsp) { count ++; mafs[count].id = id; mafs[count].detail = detail; mafs[count].cert = cert; mafs[count].tsp = tsp; } sign string ma_key (mafs_id, mafs_detail, mafs_cert, mafs_tsp); | verify string ma_key (mafs_id, mafs_detail, mafs_cert, mafs_tsp); function check smart contract mafschk( mafs_id, string mafs_detail, string mafs_cert, string mafs_tsp) { return mafs_id.exist; return mafs_detail.exist; return mafs_cert.exist; return mafs_tsp.exist; } |
- Step 3: The MA first calculates , uses to confirm whether the timestamp is valid, verifies the correctness of the ECDSA signature, and calculates , , , , . If the verification is passed, the firearm selling information is confirmed by MA, and the smart contracts fsmains and fsmachk are sent. The content is the Algorithm 6 as follows:
| Algorithm 6. Smart contract fsmains of the proposed scheme. | |
| function insert smart contract fsmains( string fsma_id, string fsma_detail, string fsma_cert, string fsma_tsp) { count ++; fsma[count].id = id; fsma[count].detail = detail; fsma[count].cert = cert; fsma[count].tsp = tsp; } sign string fs_key (fsma_id, fsma_detail, fsma_cert, fsma_tsp); | verify string fs_key (fsma_id, fsma_detail, fsma_cert, fsma_tsp); function check smart contract fsmachk( string fsma_id, string fsma_detail, string fsma_cert, string fsma_tsp) { return fsma_id.exist; return fsma_detail.exist; return fsma_cert.exist; return fsma_tsp.exist; } |
3.6. Owner Holding Phase
- Step 1:
- The FO generates a random value , calculates , , , , , and sends to the FS.
- Step 2:
- The FS first calculates , uses to confirm whether the timestamp is valid, verifies the correctness of the ECDSA signature, and calculates , , , , . If the verification is passed, the FS gets the relevant firearm request information and triggers the smart contracts fofsins and fofschk. The content is the Algorithm 7 as follows:
| Algorithm 7. Smart contract fofsins of the proposed scheme. | |
| function insert smart contract fofsins( string fofs_id, string fofs_detail, string fofs_ssn, string fofs_tsp) { count ++; fofs[count].id = id; fofs[count].detail = detail; fofs[count].ssn = ssn; fofs[count].tsp = tsp; } sign string fo_key (fofs_id, fofs_detail, fofs_ssn, fofs_tsp); | verify string fo_key (fofs_id, fofs_detail, fofs_ssn, fofs_tsp); function check smart contract fofschk( string fofs_id, string fofs_detail, string fofs_ssn, string fofs_tsp) { return fofs_id.exist; return fofs_detail.exist; return fofs_ssn.exist; return fofs_tsp.exist; } |
- Step 3:
- The FO first calculates , uses to confirm whether the timestamp is valid, verifies the correctness of the ECDSA signature, and calculates , , , , . If the verification is passed, the firearm-related information is confirmed by FO, and the smart contracts fsfoins and fsfochk are sent. The content is the Algorithm 8 as follows:
| Algorithm 8. Smart contract fsfoins of the proposed scheme. | |
| function insert smart contract fsfoins( string fsfo_id, string fsfo_detail, string fsfo_ssn, string fsfo_tsp) { count ++; fsfo[count].id = id; fsfo[count].detail = detail; fsfo[count].ssn = ssn; fsfo[count].tsp = tsp; } sign string fs_key (fsfo_id, fsfo_detail, fsfo_ssn, fsfo_tsp); | verify string fs_key (fsfo_id, fsfo_detail, fsfo_ssn, fsfo_tsp); function check smart contract fsfochk( string fsfo_id, string fsfo_detail, string fsfo_ssn, string fsfo_tsp) { return fsfo_id.exist; return fsfo_detail.exist; return fsfo_ssn.exist; return fsfo_tsp.exist; } |
4. Security Analysis and Discussion
4.1. Mutual Authentication
- G1: .
- G2: .
- G3: .
- G4: .
- G5: .
- G6: .
- G7: .
- G8: .
- M1: ,
- M2: .
- A1: ,
- A2: ,
- A3: ,
- A4: ,
- A5: ,
- A6: ,
- A7: ,
- A8: .
- The firearm authority FA authenticates the manufacturer MA.
- b.
- The manufacturer MA authenticates the firearm authority FA.
- G9: .
- G10: .
- G11: .
- G12: .
- G13: .
- G14: .
- G15: .
- G16: .
- M3: ,
- M4: .
- A9: ,
- A10: ,
- A11: ,
- A12: ,
- A13: ,
- A14: ,
- A15: ,
- A16: .
- c.
- The firearm store FS authenticates the manufacturer MA.
- d.
- The manufacturer MA authenticates the firearm store FS.
- G17: .
- G18: .
- G19: .
- G20: .
- G21: .
- G22: .
- G23: .
- G24: .
- M5: ,
- M6: .
- A17: ,
- A18: ,
- A19: ,
- A20: ,
- A21: ,
- A22: ,
- A23: ,
- A24: .
- e.
- The firearm store FS authenticates the firearm owner FO.
- f.
- The firearm owner FO authenticates the firearm store FS.
4.2. Verifiability
4.3. Resistance to Forgery
4.4. Traceability
4.5. Integrity
4.6. Decentralization/Distribution
4.7. Nonrepudiation
4.8. Computation Cost
4.9. Communication Cost
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations are Used in This Paper and Listed as Follows
| q | A k-bit prime number |
| GF(q) | Finite group q |
| E | The elliptic curve defined on finite group q |
| G | A generating point based on the elliptic curve E |
| IDx | A name representing identity x |
| kx | A random value on the elliptic curve |
| (rx, sx) | Elliptic curve signature value of x |
| (xx, yx) | An ECDSA signature message of x |
| Mx-y | A message from x to y |
| IDBC | An index value of blockchain message |
| BCx | Blockchain message of x |
| TSx | Timestamp message of x |
| Cx | Encrypted message using the asymmetric key of x |
| SSNx | The social security number of x |
| Infox | The manufacturing information of the firearm |
| Certx | A digital certificate of x conforming to the X.509 standard |
| h(.) | Hash function |
| Verification of whether A is equal to B |
References
- Alcorn, T. Trends in research publications about gun violence in the United States, 1960 to 2014. JAMA Intern. Med. 2017, 177, 124–126. [Google Scholar] [CrossRef] [PubMed]
- Gun Control Offers No Cure-All in America. Available online: http://nbcpolitics.nbcnews.com/_news/2012/12/18/15977143-gun-control-offers-no-cure-all-in-america (accessed on 30 December 2020).
- How, U.S. Gun Deaths Compare to Other Countries. Available online: https://www.cbsnews.com/news/how-u-s-gun-deaths-compare-to-other-countries/ (accessed on 30 December 2020).
- Gun Violence Archive. Available online: https://www.gunviolencearchive.org/past-tolls (accessed on 30 December 2020).
- Gun Deaths in U.S. Reach Highest Level in Nearly 40 Years, CDC Data Reveal. Available online: https://edition.cnn.com/2018/12/13/health/gun-deaths-highest-40-years-cdc/index.html (accessed on 30 December 2020).
- Gun Trace Report—City of Chicago. Available online: https://www.chicago.gov/content/dam/city/depts/mayor/Press%20Room/Press%20Releases/2017/October/GTR2017.pdf (accessed on 30 December 2020).
- Angeles, R. RFID technologies: Supply-chain applications and implementation issues. Inf. Syst. Manag. 2005, 22, 51–65. [Google Scholar] [CrossRef]
- Sarac, A.; Absi, N.; Dauzère-Pérès, S. A literature review on the impact of RFID technologies on supply chain management. Int. J. Prod. Econ. 2010, 128, 77–95. [Google Scholar] [CrossRef]
- Weapon Tracking System. Available online: http://www.bartronics.com/weapon-tracking.html (accessed on 18 March 2020).
- RFID for Weapons Tracking. Available online: https://www.vizinexrfid.com/industry-applications/weapons-tracking/ (accessed on 18 March 2020).
- Dutta, P.; Choi, T.M.; Somani, S.; Butala, R. Blockchain technology in supply chain operations: Applications, challenges and research opportunities. Transp. Res. Part E Logist. Transp. Rev. 2020, 142, 102067. [Google Scholar] [CrossRef] [PubMed]
- Miller, V.S. Use of Elliptic Curves in Cryptography. In Proceedings of the Conference on the Theory and Application of Cryptographic Techniques, Linköping, Sweden, 20–22 May 1986; Springer: Berlin/Heidelberg, Germany, 1985; pp. 417–426. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proc. R. Soc. Lond. Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar]
- Chen, C.L.; Li, Y.T.; Deng, Y.Y.; Weng, W.; Zhou, M.; Sun, H. A blockchain based intelligent anti-switch package in tracing logistics system. J. Supercomput. 2021, 1–42. [Google Scholar] [CrossRef]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Pap. 2014, 3, 1–36. [Google Scholar]
- Chen, C.L.; Chen, Y.X.; Lee, C.F.; Deng, Y.Y.; Chen, C.H. An efficient and secure key agreement protocol for sharing emergency events in VANET systems. IEEE Access 2019, 7, 148472–148484. [Google Scholar] [CrossRef]
- Chen, C.L.; Li, Y.T.; Deng, Y.Y.; Li, C.T. Robot identification and authentication in a robot cloud service system. IEEE Access 2018, 6, 56488–56503. [Google Scholar] [CrossRef]
- Chen, C.L.; Deng, Y.Y.; Li, C.T.; Zhu, S.; Chiu, Y.J.; Chen, P.Z. An IoT-based traceable drug anti-counterfeiting management system. IEEE Access 2020, 8, 224532–224548. [Google Scholar] [CrossRef]
- Szabo, N. Smart contracts: Building blocks for digital markets. EXTROPY J. Transhumanist Thought 1996, 18, 16. [Google Scholar]
- Szabo, N. The Idea of Smart Contracts. 1997. Available online: http://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/smart_contracts_idea.html (accessed on 26 November 2020).
- Han, W.; Zhu, Z. An ID-based mutual authentication with key agreement protocol for multiserver environment on elliptic curve cryptosystem. Int. J. Commun. Syst. 2014, 27, 1173–1185. [Google Scholar] [CrossRef]
- Boneh, D.; Lynn, B.; Shacham, H. Short Signatures from the Weil Pairing. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, 2001, Innsbruck, Austria, 6–10 May 2001; Ans. Springer: Berlin/Heidelberg, Germany, 2001; pp. 514–532. [Google Scholar]
- Chen, C.-L.; Yang, T.-T.; Chiang, M.-L.; Shih, T.-F. A privacy authentication scheme based on cloud for medical environment. J. Med. Syst. 2014, 38, 143. [Google Scholar] [CrossRef] [PubMed]
- Chen, C.-L.; Yang, T.-T.; Shih, T.-F. A secure medical data exchange protocol based on cloud environment. J. Med. Syst. 2014, 38, 112. [Google Scholar] [CrossRef] [PubMed]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible Protocols and Atomic Proxy Cryptography. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Espoo, Finland, 31 May–4 June 1998; Springer: Berlin/Heidelberg, Germany, 1998; pp. 127–144. [Google Scholar]
- Marcus, M.J. 5G and IMT for 2020 and beyond. IEEE Wirel. Commun. 2015, 22, 2–3. [Google Scholar] [CrossRef]



| Item | Signature | Sender | Receiver | Signature Verification | |
|---|---|---|---|---|---|
| Phase | |||||
| Authorized production phase | MA | FA | |||
| FA | MA | ||||
| Firearm selling phase | MA | FS | |||
| FS | MA | ||||
| Owner holding phase | FO | FS | |||
| FS | FO | ||||
| Role | BCC | MA | FA | FS | FO | |
|---|---|---|---|---|---|---|
| Phase | ||||||
| Access party registration phase | N/A | N/A | N/A | N/A | ||
| Authorized production phase | N/A | N/A | N/A | |||
| Firearm selling phase | N/A | N/A | N/A | |||
| Owner holding phase | N/A | N/A | N/A | |||
| Item | Message Length | Rounds | 3.5G (14 Mbps) | 4G (100 Mbps) | 5G (20 Gbps) | |
|---|---|---|---|---|---|---|
| Phase | ||||||
| Access party registration phase | 2528 bits | 2 | 0.181 ms | 0.025 ms | 0.126 us | |
| Authorized production phase | 2528 bits | 2 | 0.181 ms | 0.025 ms | 0.126 us | |
| Firearm selling phase | 2528 bits | 2 | 0.181 ms | 0.025 ms | 0.126 us | |
| Owner holding phase | 2528 bits | 2 | 0.181 ms | 0.025 ms | 0.126 us | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, C.-L.; Chiang, M.-L.; Deng, Y.-Y.; Weng, W.; Wang, K.; Liu, C.-C. A Traceable Firearm Management System Based on Blockchain and IoT Technology. Symmetry 2021, 13, 439. https://doi.org/10.3390/sym13030439
Chen C-L, Chiang M-L, Deng Y-Y, Weng W, Wang K, Liu C-C. A Traceable Firearm Management System Based on Blockchain and IoT Technology. Symmetry. 2021; 13(3):439. https://doi.org/10.3390/sym13030439
Chicago/Turabian StyleChen, Chin-Ling, Mao-Lun Chiang, Yong-Yuan Deng, Wei Weng, Kunhao Wang, and Ching-Cheng Liu. 2021. "A Traceable Firearm Management System Based on Blockchain and IoT Technology" Symmetry 13, no. 3: 439. https://doi.org/10.3390/sym13030439
APA StyleChen, C.-L., Chiang, M.-L., Deng, Y.-Y., Weng, W., Wang, K., & Liu, C.-C. (2021). A Traceable Firearm Management System Based on Blockchain and IoT Technology. Symmetry, 13(3), 439. https://doi.org/10.3390/sym13030439







