Abstract
Narrowband Internet of Things is one of the most promising technologies to support low cost, massive connection, deep coverage, and low power consumption. In this paper, a computationally efficient narrowband secondary synchronization signal detection method is proposed in the narrowband Internet of Things system. By decoupling the detection of complementary sequence and Zadoff–Chu sequence that make up the synchronization signal sequence, the search space of narrowband secondary synchronization signal hypotheses is reduced. Such a design strategy along with the use of the symmetric property of synchronization signals allows reduced-complexity synchronization signal detection in the narrowband Internet of Things system. Both theoretical and simulation results are provided to verify the usefulness of the proposed detector. It is shown via simulation results that the complexity of the proposed detection method is significantly reduced while producing some performance degradation, compared to the conventional detection method.
1. Introduction
With the rapid growth of the Internet of Things (IoT) industry, Low-Power Wide-Area (LPWA) technologies become more and more popular [1]. Recently, cellular LPWA solutions, such as enhanced Long Term Evolution for Machine-Type Communication (LTE-MTC), Extended Coverage-Global System for Mobile communications for the IoT (EC GSM-IoT), and Narrowband IoT (NB-IoT), have been envisaged as a promising technology for existing and future cellular networks [2,3,4,5]. Due to the various advantages, such as low cost, massive connectivity, and high reliability, NB-IoT can be used in a variety of vertical industries [6,7]. NB-IoT is a new rapid-growing wireless technology, which is designed primarily targeting ultra-low-end IoT applications including home automation, smart health, smart factory, and smart environment that demand low cost, high reliability, and ultra-low power [8,9]. Therefore, low complexity of implementation, deployment, and maintenance is one of the most demanding aspects of NB-IoT User Equipments (UEs) so that they can be installed on a huge scale and even in a disposable manner [10].
During initial power-on, a UE has to perform a series of processes of attaining timing and frequency synchronization and acquiring Physical Cell ID (PCID) information [11,12,13,14]. The process of selecting the best serving enhanced base station (eNodeB) by a UE is called an initial cell search. In doing so, the UE monitors two special signals transmitted from the eNodeB: Narrowband Primary Synchronization Signal (NPSS) and Narrowband Secondary Synchronization Signal (NSSS). During initial cell search procedure, the UE has no information on the system timing and the local frequency of the UE is not yet synchronized to the network [12,13]. Furthermore, most NB-IoT devices are designed with low-cost crystal oscillators leading to Carrier Frequency Offset (CFO) of as much as 20 parts per million (ppm) [14]. Thus, there may be a relatively large offset in both time and frequency, and such an uncertainty can substantially deteriorate initial synchronization performance.
1.1. Related Works
For NB-IoT, the frequency and timing offsets are estimated and compensated by using the NPSS, while the PCID detection is performed by NSSS. To establish a connection with the eNodeB, a coarse synchronization is performed before extracting the Cyclic Prefix (CP) in the time domain. The CP is then removed and a Fast Fourier Transform (FFT) unit transforms the signal to the frequency domain, wherein a post-FFT synchronization is applied. In the pre-FFT stage, the auto-correlation and cross-correlation methods are widely used for initial synchronization [13,14,15,16]. Once initial time and frequency synchronization has been accomplished using the NPSS in the time domain, frequency-domain samples are generated from the FFT unit and then the UE attempts to acquire the PCID by detecting the NSSS in the frequency domain. If NSSS detection fails, a full frequency scan has to be restarted and it increases power consumption, eventually reducing a battery life of an NB-IoT terminal [13]. Therefore, NSSS detection is a challenging problem which has been intensively developed in the NB-IoT system [14,15,16,17]. The exhaustive Maximum Likelihood (ML) search-based method attains an optimal detection performance with high computational burden because it compares all the potential combinations of Zadoff–Chu (ZC) and complementary sequences with the received NSSS sequence [14]. To solve this issue, a number of NSSS detection methods were studied for the NB-IoT system [15,16]. These methods exploit the property that the complementary sequences consisting of the NSSS are binary-modulated signals. By using the property of binary complementary sequences and repeated nature of ZC sequences, these detection methods significantly reduce the number of complex multiplication operations, when compared to the ML approach [14]. This is due to the fact that it only reverses the polarity of the received NPSS samples. However, the simplified methods developed in [15,16] no longer takes advantage of NSSS properties despite reducing their computational complexity. When considering other arithmetic operations, the complexity of these detection methods is still high due to a large number of hypotheses. In practice, NB-IoT needs to compare 4032 possible NSSS candidates since the NSSS is generated by both PCIDs and radio frame numbers. Accordingly, NSSS detection represents an important task of initial cell search procedure in the NB-IoT communication system. Furthermore, NB-IoT UEs are intended to extend up to 10 years battery life in certain scenarios and thus reducing a computational complexity is of paramount importance [8].
1.2. Contributions
In this paper, a complexity-effective NSSS detection method is presented for the cellular NB-IoT communication system. The main contributions of this paper include the following:
- By decoupling the detection of a ZC sequence and a binary complementary sequence, a multi-dimensional detection problem is reduced to several low-dimensional problems.
- With such a strategy, the PCID is obtained by sequentially identifying both ZC sequence and complementary sequence, which contributes to reducing the computational processing load.
- To confirm the feasibility of the proposed NSSS detector, the probability of detection failure is analytically derived in a flat fading channel. It is shown via simulation results that the analytical analysis is very accurate.
- Using simulations, we demonstrate that the computational load of the proposed NSSS detector can be incredibly reduced at the expense of some performance degradation, compared to the conventional NSSS detector.
The structure of this paper is as follows. Section 2 introduces the signal model and synchronization signal in the NB-IoT system. In Section 3, the reduced-complexity NSSS detector is proposed and the detection performance is numerically evaluated. In Section 4, we present the simulation results to prove the usefulness of the presented NSSS detection scheme. In Section 5, we draw some conclusions of this paper.
2. System Model
In this section, we briefly address the synchronization signal, cell search procedure, and signal model in the NB-IoT system. Throughout this paper, we use , , , , , , and for complex conjugation, absolute value, square, real part, argument, expectation, and floor operation of the enclosed quantity, respectively. Denote to be the remainder of . The notation means that a random variable x follows a complex Gaussian Probability Density Function (PDF) with mean and variance .
2.1. Signal Model
Consider an OFDM system employing N-point FFT. After taking an N-point Inverse FFT (IFFT) on the complex data symbols, a CP with length of is placed in the beginning of the time-domain symbol. Consequently, one OFDM symbol with time duration of is created, where is the sampling time instant and . Accordingly, the time-domain samples during the l-th period are given by
where denotes the time-domain sample index, k is the frequency-domain subcarrier index, and is the transmitted k-th subcarrier symbol with symbol energy .
The transmitted signal is passed through a frequency-selective multipath fading channel and is distorted by Additive White Gaussian Noise (AWGN). At the receiver, the CFO is caused by the mismatch between the local oscillators in transmitter and receiver. In this scenario, the q-th time-domain sample during the l-th symbol period is represented as
where is the Integer CFO (IFO) normalized by subcarrier spacing , is the Fractional CFO (FFO) normalized by , is the integer-valued Symbol Timing Offset (STO), is the complex channel gain, ⊗ is the linear convolution operator, and is the zero-mean AWGN with variance . At the receiver, the CFO denoted by can be decomposed to an integer part and a fractional part, leading to . Throughout this paper, the notation stands for the estimated value of parameter x. During initial timing and frequency detection procedure, the STO estimate and the CFO estimate are estimated and recovered from the received signal [15,16]. After performing initial time and frequency synchronization, there remain Residual CFO (RFO) and Residual STO (RTO) denoted by and , respectively. After removing the CP and taking the FFT operation, the FFT output at the k-th subcarrier during the l-th OFDM block is expressed as [18,19]:
where , , is the channel transfer function with variance , is the Inter-Carrier Interference (ICI) contribution with variance , and is the AWGN contribution with .
2.2. Synchronization Signal
Figure 1 depicts the radio frame structure in the NB-IoT system. The NB-IoT radio frame in downlink composes 10 subframes with duration 10 ms, leading to 20 slots in a radio frame. As shown in Figure 1, there are two downlink synchronization signals, called the NPSS and the NSSS, which facilitate the UE to perform time-frequency estimation and synchronize to the NB-IoT network. To this end, the NPSS is sent periodically in subframe 5 in every 10 ms frame, while the NSSS is present in subframe number 9 in every even-numbered radio frame. During initial cell search procedure, the NPSS is used by the UEs to correct the CFO and detect STO with respect to the subframe boundary. The NPSS sequence is fixed and thus carries no information about the cell. On the other hand, the NSSS helps to detect the PCID and frame timing within an ambiguity of 80 ms. In NB-IoT systems, there are 504 unique PCIDs indicated by the NSSS, which can be transmitted with four distinct phase shifts in every even-numbered frame to indicate 80 ms frame boundaries. Thus, the UE has to search for a total of 4032 hypotheses to detect the NSSS. The Narrowband Physical Broadcast Channel (NPBCH) can be used to convey the master information block, which indicates configuration information for the UE to operate in the NB-IoT cell.
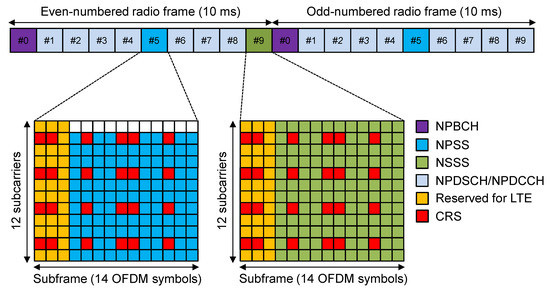
Figure 1.
Radio frame structure in NB-IoT systems.
Both NPSS and NSSS are based on ZC sequences in the frequency domain [20]. The NPSS is designed to cope with very large CFO and is constructed from length-11 ZC sequences according to
where is the 11-symbols cover sequence to resolve the timing ambiguity due to the NPSS repetitions given by . In every fifth subframe, is allocated to the last 11 consecutive OFDM symbols each comprising 12 subcarriers. In the frequency domain, the NSSS sequence is formulated by multiplying a ZC sequence and a binary complementary sequence, leading to
where is the length of NSSS sequence, , , , , , is the PCID, is the Radio Frame Number (RFN), and is one of the four length-M complementary sequences defined in [4]. The NSSS is assigned to all 12 subcarriers of the Positioning Reference Signal (PRS) leading to 132 Resource Elements (REs) in an NSSS subframe, as shown in Figure 1. For convenience of notation, is equally divided into 11 symbols and is sequentially allocated to 11 consecutive OFDM symbols, which are denoted by for and . Therefore, the transmission bandwidth of the NPSS and NSSS is only one Resource Block (RB) consisting of 12 subcarriers.
2.3. Cell Search Procedure
In the NB-IoT network, the cell search procedure can be decomposed to pre-FFT stage and post-FFT stage. At the pre-FFT stage, an averaged auto-correlation metric is used to explore the NPSS structure repeated over 11 OFDM symbols [15]. In this stage, a coarse timing is jointly detected together with FFO. For this purpose, the -times average auto-correlation metric is simply formulated by
where is the number of radio frames used for average estimate in the pre-FFT stage, is the number of observation samples within one radio frame of 10 ms, and is the modulation sequence compensated received signal. Based on this, the -times average estimate of and is thus obtained by
where .
After coarse time and frequency offset compensation, a joint detection of the IFO and fine timing is carried out using NPSS matched filter. Using a coarse timing estimate , the average cross-correlation between initially detected NPSS and local NPSS can be written by
where is the hypothetical value of the true IFO, G is the maximum value of , is the hypothetical value to refine the timing, is maximum value of , and is the -samples sequence representing the concatenated time-domain NPSS symbols. Consequently, the estimate of is obtained by finding the maximum of , leading to
Once these tasks have been completed, the FFT unit is used to convert the received time-domain samples into the frequency domain. In the post-FFT step, the UE attempts to acquire the PCID and frame timing by detecting the NSSS, which is carried out either coherently or non-coherently [16]. Since NPSS and NSSS may be not transmitted on the same antenna port, we focus non-coherent NSSS detection method in this paper.
3. Proposed NSSS Detection Scheme for NB-IoT
In this section, a complexity-effective NSSS detection scheme is proposed for the NB-IoT communication system. Numerical analysis is presented to assess the feasibility of the presented NSSS detector. Figure 2 shows the block diagram of initial synchronization and cell search procedure. This paper focuses on the post-FFT processing including the PICD and RFN detections.
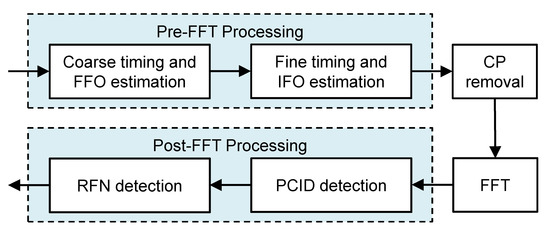
Figure 2.
Block diagram for the initial synchronization and cell search procedure.
3.1. Sequential PCID and RFN Detection (SPRD) Method
For and , let denote , and to be sequences derived from , , and , respectively. Then, the NSSS sequence can be expressed as the product of the three sequences for , , and . Note that a PCID v is uniquely associated with a pair . Referring to [4], one can see that consists of one of four complementary sequences and is common to four ’s, yielding total 2016 combinations. Using the relation that and , a PCID v is uniquely obtained by combining a pair such that .
To reduce the search space of the NSSS hypothesis, we design an objective function that does not rely on knowledge of binary complementary sequences. To end this, we use the property regardless of l and n, which leads to a local NSSS template
where takes a value of 1 or −1 due to squaring operation. It is worthy mentioning that due to unit energy of and . For notational simplicity, consider for , where stands for the number of OFDM symbols in one radio frame. Let us also denote , where and .
Bearing this definition in mind, the objective function independent of binary complementary sequences within window i is formulated as
where is the the hypothetical value for due to squaring operation, is the hypothetical value for w, is the hypothetical value for deciding the radio frame to which the NSSS belongs, and is the set of NSSS subcarriers whose cardinality is 13. Upon substituting Equations (3) and (10) into Equation (11), takes the form
where and . For notational convenience, it is assumed that the timing estimation has been successfully performed at a previous step. However, the impact of imperfect timing estimation on the detection performance will be assesses through simulations. When hypothetical values exactly match corresponding actual values, i.e., , Equation (12) can be rewritten as
If we assume that the channel is frequency-flat and stationary over NSSS subframe, we arrange Equation (13) as
which is further derived as
where . It is worthy mentioning that for small values of and follows a complex Gaussian distribution. Under hypothesis that , it follows from Equation (12) that for , while is a random complex symbol in Narrowband Physical Downlink Shared Channel (NPDSCH) or Narrowband Physical Downlink Control Channel (NPDCCH) for , as illustrated in Figure 1. Based on such observations, the estimate of can be jointly obtained as
and is the number of radio frames used for average estimate in the post-FFT stage and Equation (16) requires only 504 hypotheses.
Once the estimates have been obtained, have to be identified to fully detect the PCID and RFN, which can be accomplished by searching the maximum of the objective function within window i defined as
where is the hypothetical value for n and is the hypothetical value for . Substituting Equation (3) into Equation (17) yields
where and . If we assume that the received signal exactly coincides with the local NSSS sequence, i.e., , Equation (18) can be simplified to
Similarly, we can exploit Equation (19) to arrive at
Based upon such observations, the estimated PCID is uniquely obtained by combining the detected pair and thus we obtain , while and thus combining with determines an RFN.
3.2. Detection Performance
We assume that the STO is perfectly estimated by using the NPSS in the pre-FFT stage. The probability of detection failure of the proposed SPRD method using is derived in a flat fading channel. Let us denote as the probability that is incorrectly detected in Equation (16). Under hypothesis that in Equation (15), conditioned on , with and . Note that and are variances of and , respectively. Under hypothesis that , with . Under hypothesis , in Equation (16) obeys Rician distribution given by
where represents the modified Bessel function of zeroth order. When , the PDF of is Rayleigh distributed with distribution . Using these distributions, the probability that is erroneously detected conditioned on is written by
where denotes the cumulative density function of . Based on binomial expansion, Equation (22) becomes
which has a closed-form expression as
In Equation (24), we get
and
where is the received Signal-to-Noise Ratio (SNR) and denotes the received signal-to-ICI ratio. Without attempting to solve a closed-form expression, we resort to numerical integration , where is the PDF of .
It is seen from Equation (18) that when , while under the hypothesis that , which is because of good cross-correlation properties of the complementary sequence . If w is perfectly estimated, therefore, the conditional probability is similarly calculated by
Therefore, the probability that the PCID and RFN are incorrectly recognized can be calculated as .
4. Simulation Results and Discussions
In this section, simulations were performed to verify the feasibility of the NSSS detector in the NB-IoT network. The performance of the PCID and RFN detection methods was evaluated in terms of the probability of detection failure observed in the estimation of each parameter of interest u and v. As a global performance measure, we also assessed the overall probability of detection failure defined as .
4.1. Simulation Settings
We used FFT of length and CP of length . The sampling time instant was s, the subcarrier spacing was equal to 15 kHz, , and samples. We adopted the Pedestrian A (PedA) and Vehicular A (VehA) channel models, which was characterized by a maximum channel delay spread of 0.41 s and 2.15 s [21]. Considering that the stability of common oscillators for IoT applications was assumed to be ppm, a maximum initial CFO value was kHz at 900 MHz carrier frequency, which amounted to putting . The NB-IoT terminal was considered to be almost static with a Doppler frequency equal to 1 Hz. Unless stated otherwise, initial CFO was set to .
As benchmark, we considered two existing schemes developed in [15,16]. One was a Joint PCID and RFN Detection (JPRD) scheme [15], whose objective function takes the form
Using Equation (28), the JPRD method is formulated by
which requires 4032 hypotheses. The other was a reduced-complexity PCID and RFN Detection (RPRD) method presented in [16], which can be viewed as a low-complexity version of the JPRD method and is based on the same observation as Equation (28). For both approaches, the estimated PCID was , while an RFN was obtained by combining and . Comparing Equations (17) and (28), it was observed that was statistically equivalent to . Thus, the probability of detection failure of the JPRD and RPRD methods could be expressed in an identical form to Equation (27) replacing 7 with 4031.
4.2. Complexity Evaluation
In this section, the computational burden of the proposed SPRD approach was compared to that of the RPRD approach with respect to floating point operations (flops). In order to conduct a fair comparison, one complex multiplication, one complex addition, one complex squaring, and one complex magnitude were equivalent to six, two, five, and three flops, respectively [22]. It was assumed that the local template was a priori available at the receiver. For all presented methods, the elements generated by and were assumed to be implemented without any multiplication.
4.2.1. Pre-FFT Processing
We considered a sliding window to implement an average operation. Then, in Equation (11) required complex multiplications, complex additions, and complex magnitudes for all possible trials. The estimate required one additional flop. Thus, coarse STO and FFO estimates required flops. To complete the IFO and fine STO detection, required complex multiplications, complex additions, and one complex magnitude for each trial. Thus, Equation (13) was computed with flops.
4.2.2. Post-FFT Processing
In the proposed SPRD method, computing required M complex squaring operations. For each hypothesis, both quantities and required the same number of arithmetic operations, except for the squaring operation. Thus, both quantities required complex multiplications, complex additions, real additions, and one complex magnitude using the symmetric property of . Therefore, flops were required to obtain Equation (16) for 504 hypotheses, while Equation (20) required flops for 8 hypotheses. As a result, the SPRD method required flops. In the case of the RPRD method, was calculated with complex multiplications, complex additions, real additions, and one complex magnitude for each hypothesis. Considering 4032 hypotheses in Equation (29), the overall number of flops was equal to .
Table 1 compares the number of flops required to implement the conventional and proposed detection methods. For , the overall computational burden of the SPRD method was remarkably decreased by regardless of , compared to the RPRD method. This is because that the number of flops used in both the RPRD and SPRD methods were almost linearly proportional to .

Table 1.
Complexity comparison of the conventional and proposed detection methods.
4.3. Performance Evaluation
Figure 3 presents of the proposed NSSS detection method in AWGN and flat fading channels. To verify the accuracy of the performance analysis, we considered the scenario where the STO was completely estimated at the pre-FFT synchronization step. As benchmark, the probability of detection failure of the JPRD method Equation (29) is also provided. The first behavior we observe from Figure 3 is that the simulation result (marker) exactly coincided with the theoretical analysis (line) in both AWGN and flat-fading channels. Although not shown in this figure, analytical curve of the RPRD method was the same to that of the JPRD method. As predicted, the presence of channel fading and RFO substantially deteriorates the accuracy of the JPRD and SPRD methods. In particular, the RFO caused an irreducible ICI as the SNR increased, leading to error floor phenomenon as observed in Figure 3b. Compared to the JPRD approach, it can be seen that the SPRD approach suffered from some performance loss, showing the performance versus complexity tradeoffs. This phenomenon is attributed to the reason that squaring operation in Equation (11) increased noise variance of the proposed SPRD method.
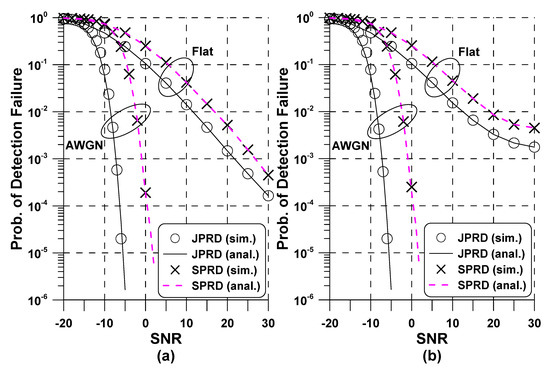
Figure 3.
Performance of the proposed Narrowband Secondary Synchronization Signal (NSSS) detector in Additive White Gaussian Noise (AWGN) and flat fading channels: (a) ; (b) .
Figure 4 depicts the probability of detection failure of the RFN detector and the probability of detection failure of the PCID detector in the PedA channel. We considered the scenario where both STO and CFO were detected in the time domain adopting the method in Equations (7) and (9), wherein initial STO and CFO estimation was based on -times average autocorrelation metric of the NPSS. After initial STO and CFO compensation, the received signal was transformed to the frequency domain, leading to residual errors and at the post-FFT stage. When compared to the RPRD method, the performance of the SPRD method came to approach that of ideal initial synchronization as increased, equivalently, initial STO and CFO estimation became more accurate. Another interesting remark is that was greater than due to the larger number of hypotheses associated with detecting the PCID. Based on such observation, it was expected that the overall probability was primarily determined by .
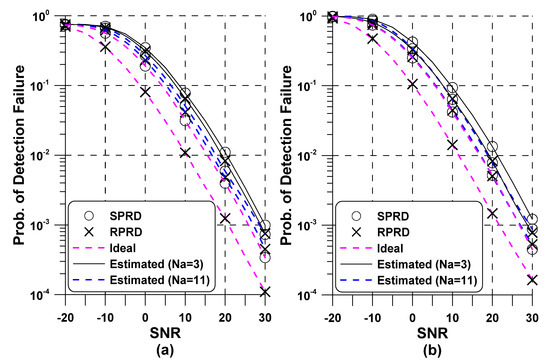
Figure 4.
Performance of the conventional and proposed NSSS detectors versus in Pedestrian A (PedA): (a) Radio Frame Number (RFN); (b) Physical Cell ID (PCID).
Figure 5 presents of the existing and proposed NSSS detection methods in the PedA channel. The simulation setting remained the same as in Figure 4. Immediately, we observed a similar trend to that in Figure 4, clearly indicating that accurate estimates of STO and CFO could improve the performance of the NSSS detectors. As predicted, the detection curves of the JPRD and RPRD methods almost overlapped due to using basically the same objective function. When compared to the result of ideal initial time-frequency estimation, a performance gap between the conventional and proposed schemes decreased, leading to the SNR loss within 2 dB. Based on this observation, the accuracy of initial synchronization has more impact on the performance of the conventional NSSS detectors. Therefore, it was concluded that the SPRD method effectively detected the NSSS with significantly reduced complexity in a more realistic situation where there still remained the RTO and RFO at the post-FFT stage.
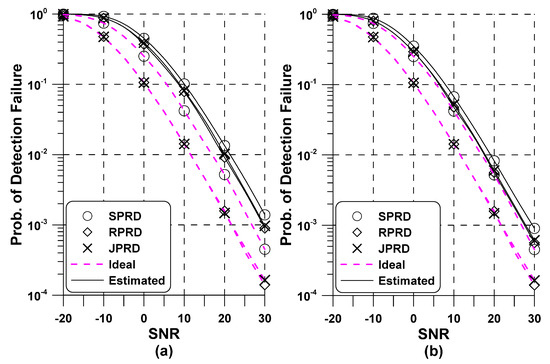
Figure 5.
Performance of the conventional and proposed NSSS detectors in the PedA channel: (a) ; (b) .
In Figure 6 and Figure 7, we compared the performance of different detection methods as a function of the processing time equivalently when dB and dB, respectively. As a baseline, the ideal performance when was plotted. In the estimated case, the initial synchronization was based on 11-times average autocorrelation metric of Equations (7) and (9). The number of radio frames needed to attain 10% error probability was defined as , which is equivalent to the processing time of ms. It was seen that an increased number of radio frames could average out the noise and enhance the detection capability of both the detection methods. When the SNR was equal to −5 dB, Figure 6b clearly indicates that both RPRD and SPRD methods required and 43, respectively, to achieve 10% error probability in the PedA channel. Considering the number of flops in Table 1, it can be seen that the complexity of the SPRD method using reduced by 73.2% at the cost of processing time delay, compared to that of the RPRD method using . On the other hand, the number of radio frames significantly decreased in the VehA channel so that and 20 were required for the RPRD and SPRD methods, respectively. Based on this observation, the same complexity reduction was expected in the case of the VehA channel. Basically, power consumption is proportional to the number of flops used to implement the detection algorithms [23]. Thus, it was intuitively expected that a reduced number of flops of the proposed method could improve the power consumption efficiency if other system parameters that determined the power consumption were the same. Consequently, both the RPRD and SPRD approaches achieved better performance in the VehA channel due to the increased multipath diversity. When the NB-IoT UE operated in the extended coverage with dB, as shown in Figure 7, it required a large number of radio frames to attain a target error probability, eventually increasing the processing time for both methods. In the case of the PedA channel, the RPRD method achieved its target error probability with 120 radio frames of 10 ms each at the cost of computational complexity, while the SPRD method used 170 radio frames, which suffered from increased processing time. By adopting the proposed approach to the NB-IoT communication system, the computational burden of the initial synchronization receiver could be thus reduced, thus improving a battery life of NB-IoT UEs.
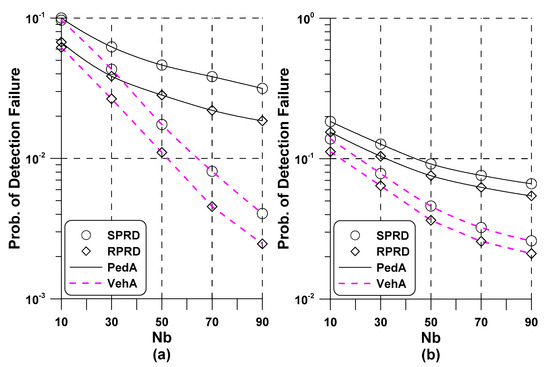
Figure 6.
Performance of the conventional and proposed NSSS detectors when Signal-to-Noise Ratio dB: (a) ideal; (b) estimated.
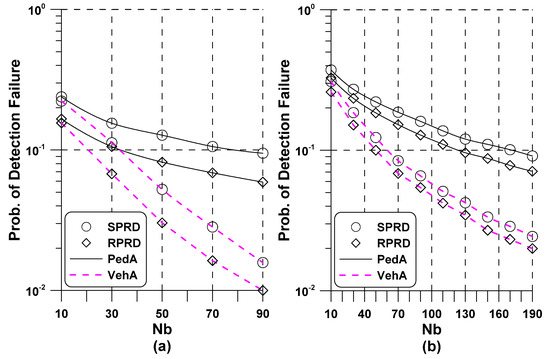
Figure 7.
Performance of the conventional and proposed NSSS detectors when dB: (a) ideal; (b) estimated.
5. Conclusions
In this paper, a low-complexity NSSS detection method is suggested in the cellular NB-IoT communication system. Using the property of binary complementary sequence, the NSSS detection problem can be decoupled into sequential detection task of complementary sequence and ZC sequence, yielding a highly complexity-effective NSSS detection method. To prove the usefulness of the proposed detector, the probability of detection failure is analytically computed in the flat fading channel. It has been shown from simulation results that the proposed NSSS detector can save nearly one-fifth of the computational burden at the expense of some performance loss, compared to the conventional NSSS detector. Furthermore, the proposed NSSS detection method effectively performs in a realistic scenario where there remain the RTO and RFO. By using the proposed approach to the cellular NB-IoT communication system, it allows NB-IoT devices to synchronize robustly with less power during the initial cell search procedure and provides the useful information in designing a simple efficient NB-IoT synchronization receiver.
Funding
This research was supported by Basic Science Research Program through the National Research Foundation of Korea(NRF) funded by the Ministry of Education (NRF-2018R1D1A1B07048819) and this research was supported by Unmanned Vehicles Advanced Core Technology Research and Development Program through the National Research Foundation of Korea (NRF), Unmanned Vehicle Advanced Research Center (UVARC) funded by the Ministry of Science and ICT, the Republic of Korea (NRF-2017M1B3A2A01049997).
Conflicts of Interest
The author declares no conflict of interest.
References
- Ikpehai, A.; Adebisi, B.; Rabie, K.M.; Anoh, K.; Ande, R.E.; Hammoudeh, M.; Gacanin, H.; Mbanaso, U.M. Low-power wide area network technologies for Internet-of-Things: A comparative review. IEEE Internet Things J. 2019, 6, 2225–2240. [Google Scholar] [CrossRef]
- 3GPP. Study on Provision of Low-Cost Machine-Type Communications (MTC) User Equipments (UEs) Based on LTE; TR 36.888; 3GPP: Sophia Antipolis, France, 2013. [Google Scholar]
- Akpakwu, G.A.; Silva, B.J.; Hancke, G.P.; Abu-Mahfouz, A.M. A survey on 5G networks for the Internet of Things: Communication tchnologies and challenges. IEEE Access 2018, 6, 3619–3647. [Google Scholar] [CrossRef]
- 3GPP. Physical Channels and Modulation (Release 14); 3GPP TS 36.211; 3GPP: Sophia Antipolis, France, 2017. [Google Scholar]
- Popli, S.; Jha, R.K.; Jain, S. A survey on energy efficient narrowband Internet of Things (NBIoT): Architecture, application and challenges. IEEE Access 2019, 7, 16739–16776. [Google Scholar] [CrossRef]
- Xu, J.; Yao, J.; Wang, L.; Ming, Z.; Wu, K.; Chen, L. Narrowband internet of things: Evolutions, technologies, and open issues. IEEE Internet Things J. 2018, 5, 1449–1462. [Google Scholar] [CrossRef]
- Mwakwata, C.B.; Malik, H.; Alam, M.; Moullec, Y.; Parand, S.; Mumtaz, S. Narrowband internet of things (NB-IoT): From physical (PHY) and media access control (MAC) layers perspectives. Sensors 2019, 19, 2613. [Google Scholar] [CrossRef] [PubMed]
- 3GPP. Cellular System Support for Ultra-Low Complexity and Low Throughput Internet of Things (CIoT); TR 45.820, V13.1.0; 3GPP: Sophia Antipolis, France, 2015. [Google Scholar]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial Internet of Things: Challenges, opportunities, and directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Malik, H.; Pervaiz, H.; Alam, M.; Moullec, Y.; Kuusik, A.; Imran, M. Radio resource management scheme in NB-IoT systems. IEEE Access 2018, 6, 15051–15064. [Google Scholar] [CrossRef]
- Kroll, H.; Korb, M.; Weber, B.; Willi, S.; Huang, Q. Maximum-llikelihood detection for energy-efficient timing acquisition in NB-IoT. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), San Francisco, CA, USA, 19–22 March 2017; pp. 1–5. [Google Scholar]
- Qiu, T.; Zhang, Y.; Qiao, D.; Zhang, X.; Wymore, M.; Sangaiah, A.K. A robust time synchronization scheme for industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3570–3580. [Google Scholar] [CrossRef]
- Yang, W.; Hua, M.; Zhang, J.; Xia, T.; Zou, J.; Jiang, C.; Wang, M. Enhanced system acquisition for NB-IoT. IEEE Access. 2017, 5, 13179–13191. [Google Scholar] [CrossRef]
- Intel Corporation. Synchronization and Cell Search in NB-IoT: Performance Evaluations; 3GPP TSG RAN WG1; R1-161898; Intel Corporation: Santa Clara, CA, USA, 2016. [Google Scholar]
- Ali, A.; Hamouda, W. On the cell search and initial synchronization for NB-IoT LTE systems. IEEE Commun. Lett. 2017, 21, 1843–1846. [Google Scholar] [CrossRef]
- Li, Y.; Chen, S.; Ye, W.; Lin, F. A joint low-power cell search and frequency tracking scheme in NB-IoT systems for green Internet of Things. Sensors 2018, 18, 3274. [Google Scholar] [CrossRef] [PubMed]
- Magani, S.; Kuchi, K. Cell-search and tracking of residual time and frequency offsets in low power NB-IoT devices. CSI Trans. ICT 2019, 7, 27–34. [Google Scholar] [CrossRef]
- Hwang, J.-K.; Li, C.-F.; Ma, C. Efficient detection and synchronization for superimposed NB-IoT NPRACH preambles. IEEE Internet Things J. 2019, 6, 1173–1182. [Google Scholar] [CrossRef]
- Murin, Y.; Dabora, R. Low complexity estimation of carrier and sampling frequency offsets in burst-mode OFDM systems. Wirel. Commun. Mob. Comput. 2016, 16, 1018–1034. [Google Scholar] [CrossRef]
- Popovic, B.M. Generalized chirp-like polyphase sequences with optimum correlation properties. IEEE Trans. Inf. Theory 1992, 30, 769–777. [Google Scholar] [CrossRef]
- International Telecommunication Union. Guidelines for Evaluation of Radio Transmission Technologies for IMT-2000; ITU-R M. 1225-97; International Telecommunication Union: Geneva, Switzerland, 1997.
- Golub, G.H.; Loan, C.F.V. Matrix Computations; The Johns Hopkins University Press: Baltimore, MD, USA, 2013. [Google Scholar]
- Xiao, Z.; Zhao, J.; Liu, T.; Geng, L.; Zhang, F.; Tong, J. On the energy efficiency of massive MIMO systems with low-resolution ADCs and lattice reduction aided detectors. Symmetry 2020, 12, 406. [Google Scholar] [CrossRef]
© 2020 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).