This section analyzes the requirements for designing a methodology that assesses the effects of threats and attacks on the cyber environment linked with EW systems. To achieve this, we consider related research conducted on damage assessment of cyberspace, concurrently with analyzing features for measuring the performance of EW and target systems.
2.1. Damage Assessment in Cyberspace
This paper focuses on cyberattacks, defined by the National Institute of Standards and Technology (NIST) as attacks that target cyberspace to disrupt, deactivate, destroy, or maliciously control the computing environment and infrastructure, damage the integrity of data, or steal controlled information [
9]. Battle damage assessment (BDA) is a significant factor that affects the time and space in which military activities take place. Several studies that evaluate the impacts of cyberattacks have been published in the literature.
Denning [
10] introduced a framework for assessing cyber warfare. The framework is used as its foundation risk assessment that assesses the risks to cyber systems, operations, and organizations, from cyberattacks in terms of threats, vulnerabilities, impacts, and possibilities. The framework assesses risks based on NIST’s guide for conducting risk assessments [
11] and provides an assessment of cyber battle damage and cyber strength to assess cyber warfare.
Kotenko and Chechulin [
12] suggested a framework modeling cyberattacks and evaluating impacts, considering a common approach based on providing risk analysis procedures. It is a framework that graphically traces all possible sequences of actions to determine an attacker’s purpose and evaluate the impact on the action through graphical analysis.
Musman and Temin [
13] implemented the Cyber Mission Impact Assessment (CMIA) method to simulate the application of potential security and resilience methods to a system within a mission context and perform assessments of the system. They implemented a functional subset of the business process modeling notation (BPMN) to present the mission and its cyber dependencies. After defining measures of effectiveness (MOE) and measures of performance (MOP) for the cyber mission, the method identifies how the performance of mission activities contributes to achieving them. The CMIA model considers only the effects of successful cyberattacks: degradation, interruption, modification, fabrication, unauthorized use, and interception (DIMFUI). The model is executed both with and without cyberattack effects to compute MOE, MOP, and KPP; changes in these performance parameters reflect mission impacts.
Kim et al. [
14] proposed a framework that assesses cyber battle damage by measuring MOP and MOE before and after cyberattacks. They designed a framework to communicate and integrate with other systems, such as physical warfare and EW.
To the best of our knowledge, the primary method of evaluating the impact or damage to cyberspace is to use MOP and MOE. The effectiveness of objects constituting cyberspace is quantified, and then the damage is evaluated by comparing the cyberspace before and after cyberattacks. The result of the assessment helps C2 when it plans and executes the mission successfully. Generally, cyberspace evaluation methods are divided into the evaluation of damage and the relative ability to respond to cyberattacks. This paper focuses on how to assess the damage caused by a cyberattack.
2.2. Electronic Warfare
Nowadays, EW has become an increasingly important factor in military operations; it is highly dependent on electronic equipment, and has been used in military operations in complex information environments integrated with the electromagnetic spectrum.
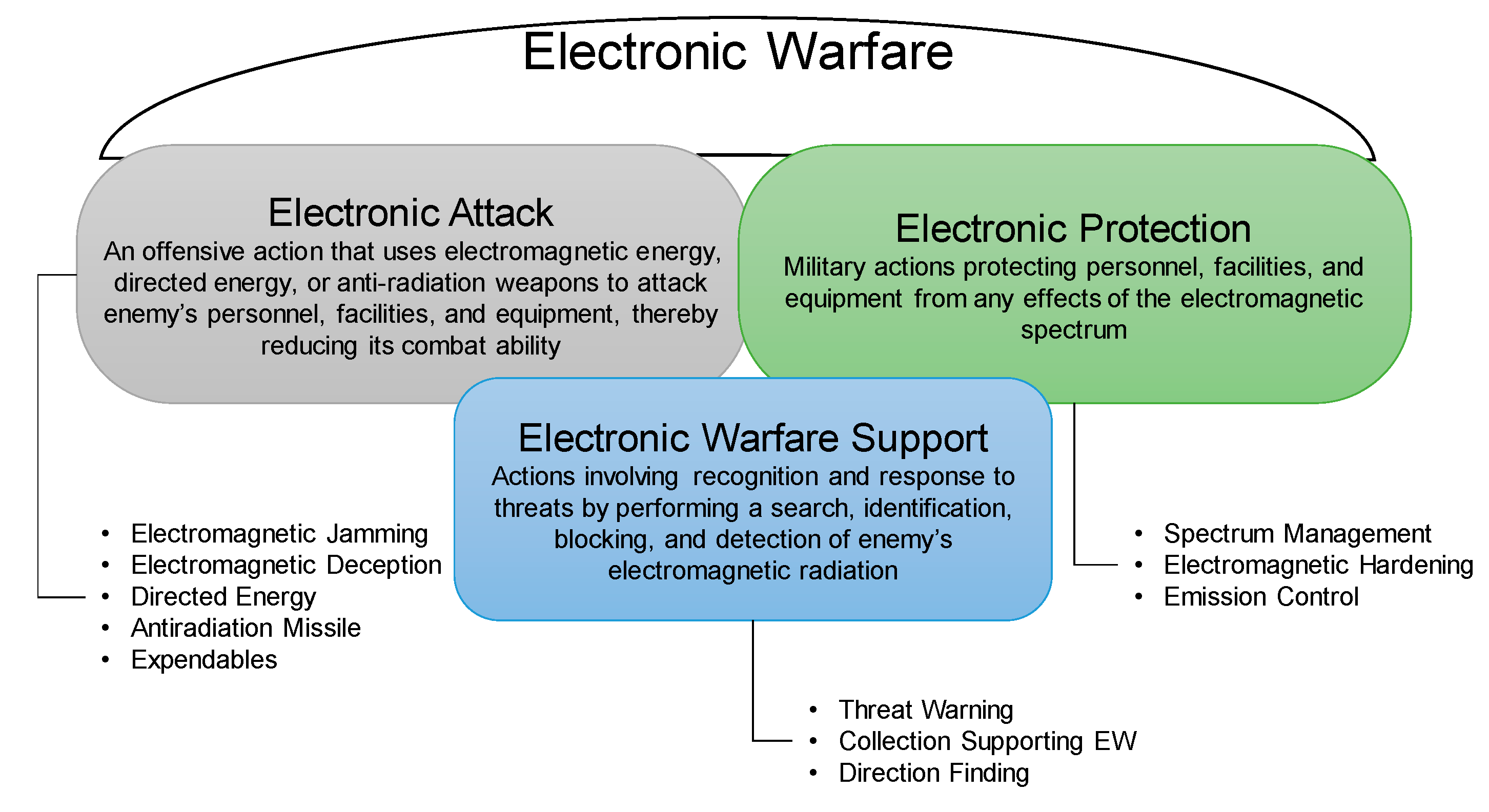
EA refers to an offensive action that uses electromagnetic energy, directed energy, anti-radiation weapons, etc., to destroy, damage, or degrade the enemy’s personnel, facilities, and equipment, thereby reducing its combat ability. As shown in
Table 1, EA is classified according to the type of attack.
ES refers to military activities involving immediate recognition and response to threats by performing a search, blocking, identification, and location detection of enemy electromagnetic radiation. It is also called electronic support measure (ESM), and its primary function is the production/collection of tactical information.
Table 2 lists the steps to achieve the ultimate goal of ES, that is, the analysis and judgment of enemy intentions and abilities. It is classified into signal intelligence, electronic intelligence, and communications intelligence, according to the target of information collection. Typical types of ES systems include a radar warning receiver, missile warning receiver, laser warning receiver, and surveillance radar.
EP refers to the act of protecting a friendly electronic facility from enemy EAs. It is divided into anti-ES, which suppresses the enemy’s ES ability against allies, and anti-EA, which responds to the enemy’s EA attacks. The types of EP activities include emission control (EMCON), shielding, and communication security (COMSEC). EMCON attempts to suppress unnecessary electromagnetic radiation as much as possible when the enemy tries to collect intelligence on allies by conducting ES activities against allies.
EW systems can be classified into standalone, federated, and integrated systems according to the type of operation [
6,
7]. Standalone systems are mainly used in scenarios that require a rapid response. An example is a decoy system for promptly responding to an unexpected anti-ship missile attack during a regular voyage or at the berth when the ship is not ready for combat. The federated system can be configured by adding a data-sharing function through a network/bus to an independently operating system. A standalone radar warning receiver (RWR) system that performs simple self-defense and threat alert can be extended to detect and identify remote threats by additionally configuring data link equipment for electronic information transmission.
Unlike conventional tactical systems with “federated” EW systems, modern fighter planes and Aegis ships use an integrated system that shares resources across all EW components and electronic systems. F-35, for example, is highly integrated. Radio-frequency and electro-optical receivers are built around the edge of the airframe allowing continuous detection of unfriendly emitters from all directions. All sensors are fused through a central computer and displayed on the visor of the pilot’s helmet. The system also merges information from off-board sensors to provide a comprehensive view of the local electronic environment [
15].
EW systems in complex electromagnetic environments play a crucial part in modern warfare. Therefore, evaluation of the effectiveness of EW in such environments has become a crucial factor responsible for establishing and maintaining a favorable position in the combat environment. To achieve this critical mission, NATO tests and evaluates the equipment used in modern EW systems with a wide range of testing techniques to ensure the readiness of the EW system for users to complete their mission in the combat environment [
7].
NATO introduces a disciplined approach to the test and evaluation (T&E) for EW systems, including the technical considerations for planning execution and operations. Although the specification concentrates on radio/radar frequency and infrared systems operating in EW frequency ranges, all system types are covered for EW T&E capabilities.
The T&E objectives are derived from the operational requirements of the users and the requirements of the specification to ensure survivability and operational effectiveness in the military action. It defines the T&E process of EW systems, as depicted in
Figure 2. The process continuously improves the estimated performance, allowing the tester to provide decision-makers with quantifiable technical risks [
7].
The capabilities of an EW system are assessed using a wide range of test resources, such as measurement facilities, system integration laboratories, hardware-in-the-loop facilities, installed system test facilities, open air ranges, and modeling and simulation [
7]. When the tester designs the T&E, it must be ensured that two questions are answered as follows:
The test must determine if the manufacturer has met each of the specification requirements.
The EW system must be evaluated to determine if the military utility is feasible to perform a dedicated operational T&E, i.e., field test.
The T&E objectives must verify both the specification compliance and military utility. Once they are established, the test team must determine to evaluate the performance or effectiveness. These are known as the MOP and the MOE. NATO defines the MOP as generally suitable for development T&E and relevant to technical performance requirements, and the MOE applies to operational T&E.
A large T&E charged with acquiring several potentially integrated sub-systems might have a hierarchy of test objectives. For example, it has an overall test objective: “evaluate the performance of the F-XX aircraft.” The objective could consist of lower-level objectives: “evaluate the tactical avionics suite” or “evaluate the fire control radar system.” An objective to evaluate EW systems of the aircraft could have sub-objectives: “evaluate the performance of the RWR system” or “evaluate the expendable countermeasures system.” A small T&E might have a single stand-alone objective, such as “evaluate the infrared countermeasure.”
In the abovementioned context, the MOP must be measurable attributes related to operational functions. Most performances of the EWs are measured based on whether the value of the attribute, such as response time, meets the expectations.
2.3. Cyberspace and Electronic Warfare
Today’s armed forces also operate in cyberspace, a network-based environment, and leverage the more congested electromagnetic spectrum (EMS). According to the U.S. Army, wireless cyberspace capabilities use the EMS as a transport medium to form links in the Department of Defense Information Network (DODIN) [
16]. Moreover, it is emphasized that cyber warfare and EW operations must be performed in a converged form because they are mostly used for similar purposes; such military activities are called cyberspace electromagnetic activities (CEMA), as shown in
Figure 3 [
8].
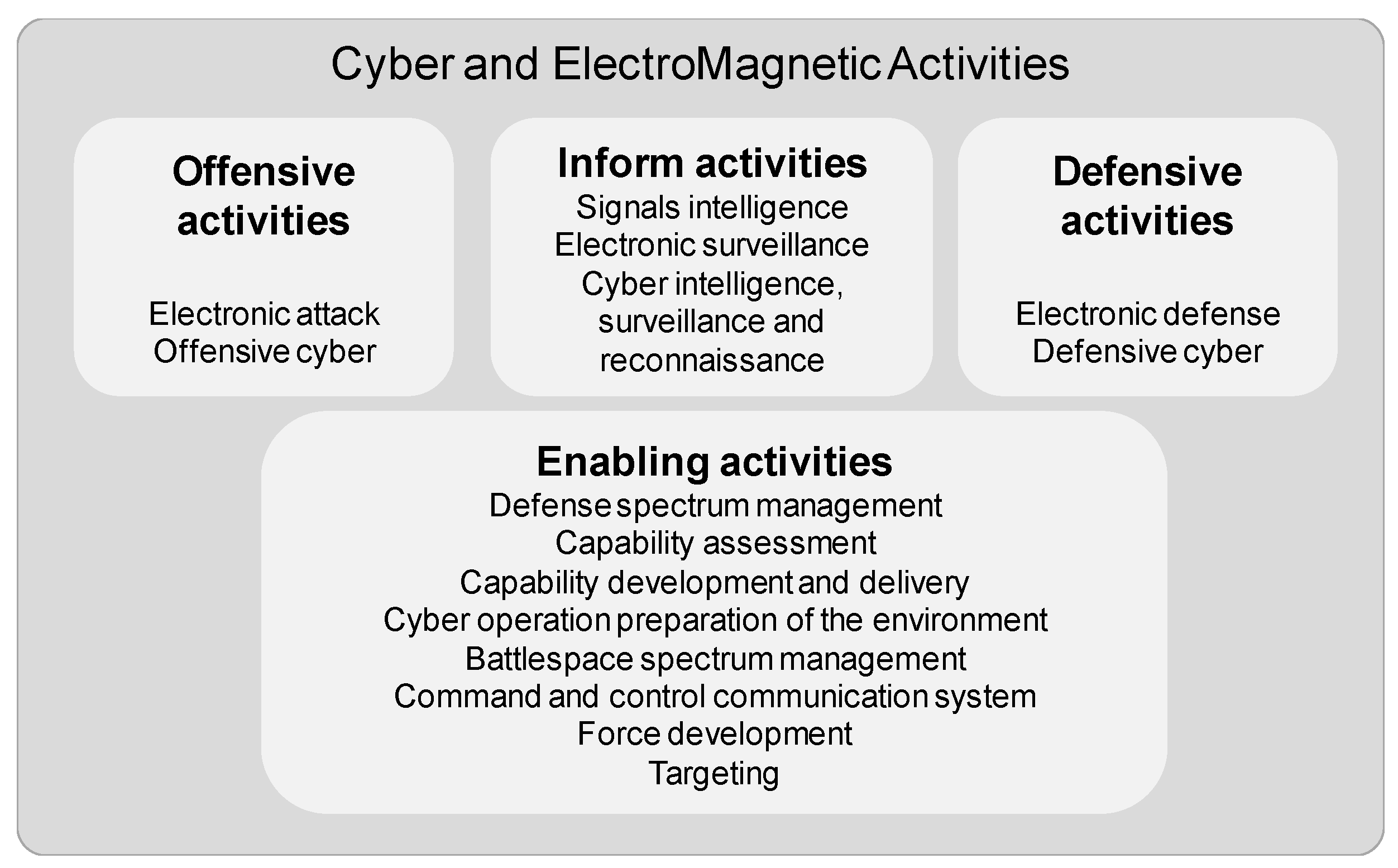
CEMA is defined as the synchronization and coordination of offensive, defensive, informing, and enabling activities across the electromagnetic environment and cyberspace, as depicted in
Figure 3. CEMA operations are divided into cyberspace operations, EW, and spectrum management operations, as presented in
Figure 4 [
17], and include internet communication networks, computer systems, and embedded processes/controllers.
Military operations of the U.S. Army, such as information management, operation, command transmission, and situational awareness, can be conducted anywhere through the DODIN, in places, i.e., homes, temporary residences, camps, and base stations. However, when conducting operations in cyberspace, a plan for risk management must be prepared. Risk management is a critical decision-making process to identify hazards, control risks, and increase operational effectiveness and mission-achievability. The U.S. Army faces multiple, simultaneous, and continuous threats in cyberspace.
Table 3 lists the sample threat capabilities in cyberspace and EW [
18].
Moreover, EW systems have achieved many advances owing to the development of ICT technology. They have been developed to operate by interlocking/integrating with multiple EW systems rather than an individual system that operates in a single form; therefore, they provide advanced functionalities, including the characteristics of cyberspace where necessary information is exchanged by sharing network assets.
Most of the studies have considered cyberspace as an actual physical battlefield and evaluated its impact on military operations. This paper presents a method for assessing the effect on cyberspace in terms of ES systems that conduct electromagnetic activities in cyberspace, rather than assessing the impact of physical operations on military activities in cyberspace.