Hesitant Fuzzy Sets Based Symmetrical Model of Decision-Making for Estimating the Durability of Web Application
Abstract
1. Introduction
- Estimate web application durability that will deliver rules and strategies for development of durable web application.
- Hesitant fuzzy sets based AHP-TOPSIS technique is adopted to evaluate the durability of web application. Hesitant fuzzy sets based AHP technique and hesitant fuzzy sets based TOPSIS technique are well known and popular during solving multi-criteria decision making related problems and provide precise and efficient results.
- The set of characteristics of durability used in this research work to assess durability of web application through unified approach of hesitant fuzzy based AHP and TOPSIS is unique.
- Six different versions of an institutional web application are taken as alternatives to evaluate the real time impact and validate the results.
- This study’s empirical initiative aims at providing insights about determining how formal and well-proven durability characteristics are followed throughout the development life cycle of web application.
2. Materials and Methods
2.1. Durability of Web Application
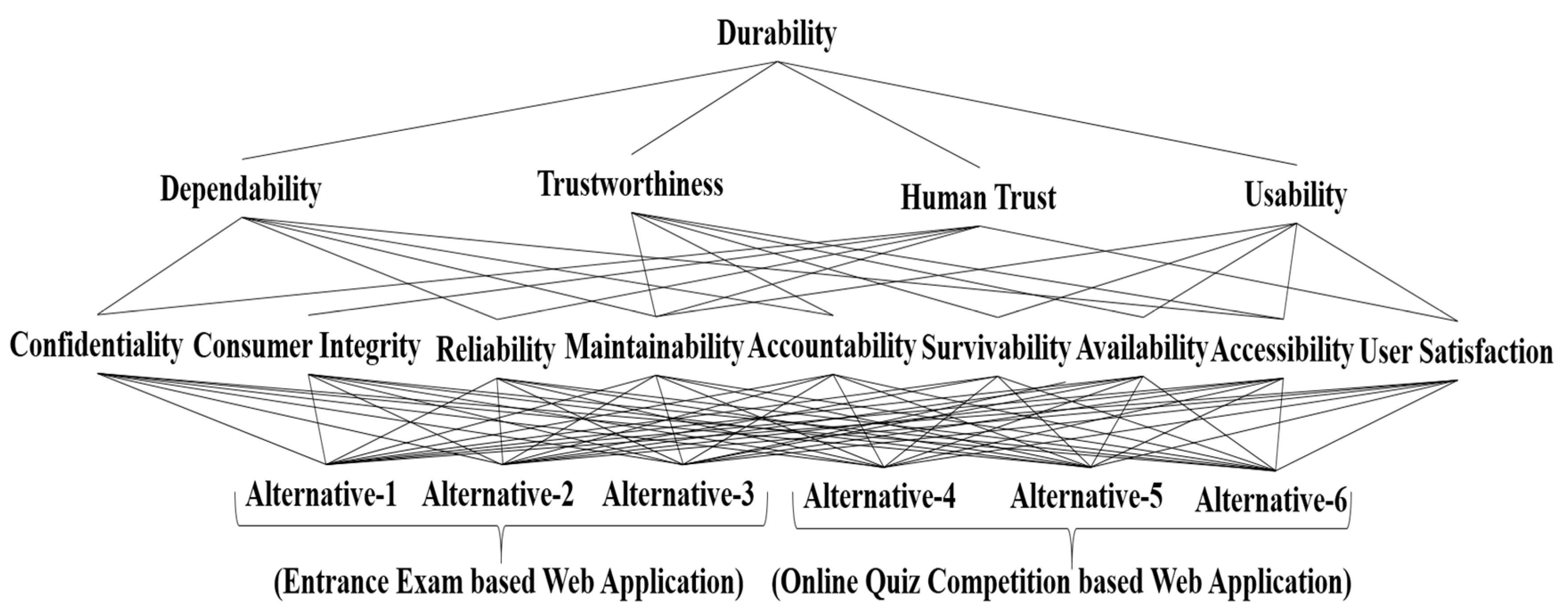
- Dependability: The system is said to be dependable if a computer works as expected and the user is confident at the same time about its working. Describing the significance of this factor in durability is an effective way to construct web application. A web application’s durability factor is also inherited by dependability. It inherits the service life and working process of web application. On the other hand, by underlining the definition of dependability factor, it is clearly illustrated that the software service life span is important for user’s expectations. Hence, in these terms, the web application’s durability will be stronger with the help of dependable software. There are many dependability characteristics but web application durability affects only a few of them which are mentioned in Figure 1.
- Trustworthiness: According to the defining terms of this factor, if web application can prevent, tackle and survive the condition of attacks, failure, and other harmful situations, then it will possess trustworthiness. Trustworthiness ensures that the software will perform as expected. There are many trustworthiness characteristics but web application durability affects only a few of them which are mentioned in Figure 1.
- Human Trust: Trust in human to human operations is one of the most significant characteristics for long serviceability in web applications. In web application terms, human trust is identified as the consumer’s trust in the developer. The characteristics that strengthen each other are web application durability and human trust. There are many human trust characteristics but web application durability affects only a few of them which are mentioned in Figure 1.
- Usability: If a web application interface is simple or easy to use, then it automatically means that is usable. Accessibility, availability, survivability, maintainability, and ultimately satisfaction are the five main enhancements that make for a usable web application, as per the end-users’ experience. Further, the characteristics that strengthen each other are web application durability and usability. There are many usability characteristics but web application durability affects only a few of them which are mentioned in Figure 1.
- Confidentiality: It is an ability to manage and provide data only to the authorized users.
- Consumer Integrity: Integrity is an ability of application that prevents and manages the originality of information within the web application.
- Reliability: It is an ability that shows the performance consistency of application in a controlled condition for a specified time period.
- Maintainability: Is the ability that defines rearrangements and patching in web applications for a specified course of work.
- Accountability: Accountability assures the role and amenableness of every node or entity of users in web application.
- Survivability: Is the ability of web application to fulfill its desired objective, whether it is in an attack situation or failure.
- Availability: It assures the presence of information 24 × 7 in a web application for its authorized users.
- Accessibility: Is the ability of web applications to control user information rights within the web application environment.
- User Satisfaction: It assures customer satisfaction and demands in a web application by timely upgradation.
2.2. Methodology
- To define alternatives and criteria in TOPSIS, the following written formulas are applied as and n criteria
- Denotes the experts in TOPSIS, similarly, k is used to display numeric count of experts.
- In TOPSIS methodology, the equation is used to represent HF matrix.
- To evaluate the criteria and effect of outcomes, the standards are written for TOPSIS are:
- = between medium and good (bt M&G)
- = at most medium (am M)
- = at least good (al G)
- = between very bad and medium (bt VB&M)
- (EGH (btM&G)) = T (0.3300, 0.5000, 0.6700, 0.8300)
- (EGH (amM)) = T (0.0000, 0.0000, 0.3500, 0.6700)
- (EGH (alG)) = T (0.5000, 0.8500, 1.0000, 1.0000)
- (EGH (btVB&M)) = T (0.0000, 0.3000, 0.3700, 0.6700)
3. Data Analysis and Results
3.1. Robustness Assessment
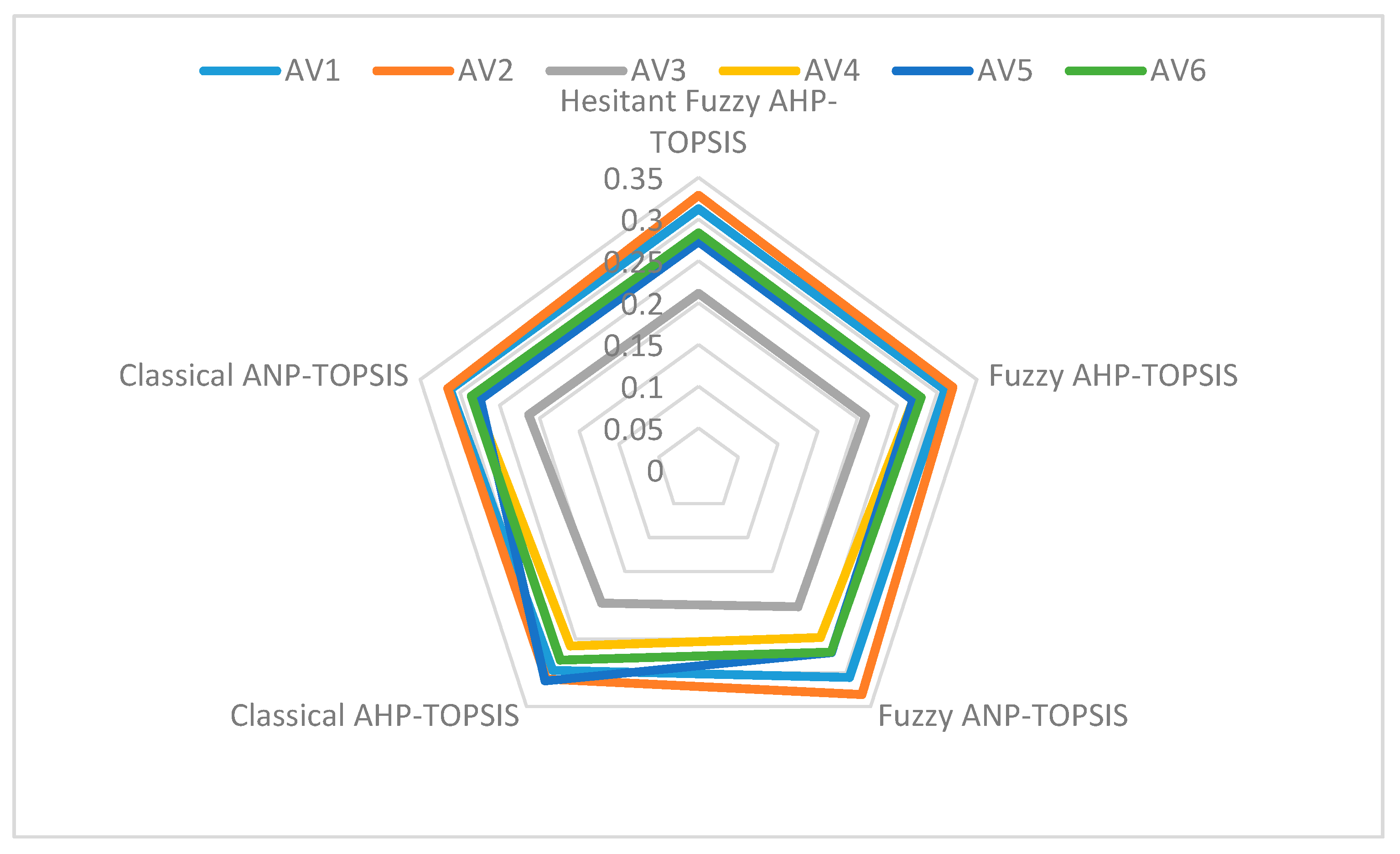
3.2. Comparison with Other Pair-Wise Techniques
4. Conclusions
- Maintaining the durability of web applications gives cost-related enhancements and provides low-cost investment in web application management.
- The findings of the proposed work will facilitate the developers’ task who can refer to the results and employ the stated methodology for enhancing the durability of web application instead of focusing on its application-level characteristics.
- The assessment section of this paper portrays that trustworthiness is the most important priority factor for durability enhancement in web applications. Therefore, it is automatically proven that focusing on trustworthiness can give high durability in web applications.
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Tekinerdogan, B.; Sozer, H.; Aksit, M. Software architecture reliability analysis using failure scenarios. J. Syst. Softw. 2008, 81, 558–575. [Google Scholar] [CrossRef]
- FCW Workshop. Durable Cost Savings in Government IT. 2016. Available online: https://fcw.com/articles/2016/04/22/cost-savings-oped.aspx (accessed on 20 October 2018).
- Thomas, B. Cisco Global Cloud Index 2015–2020. Available online: https://www.cisco.com/c/dam/m/en_us/service-provider/ciscoknowledgenetwork/files/622_11_15-16-Cisco_GCI_CKN_2015-2020_AMER_EMEAR_NOV2016.pdf (accessed on 10 August 2020).
- Lambert, S. SaaS Industry Market Report: Key Global Trends & Growth Forecasts. Finances Online. 2018. Available online: https://financesonline.com/2018-saas-industry-market-report-key-global-trends-growth-forecasts/ (accessed on 4 September 2018).
- Sommardahl, B. Durable Software. Awkward Coder Learning to Behave in Public 5–8. 2013. Available online: https://www.durable-north-america.com/service/duraprint-software.html (accessed on 24 August 2020).
- Kumar, R.; Khan, A.I.; Abushark, Y.B.; Alam, M.M.; Agrawal, A.; Khan, R.A. A Knowledge Based Integrated System of Hesitant Fuzzy Set, AHP and TOPSIS for Evaluating Security-Durability of Web Applications. IEEE Access 2020, 8, 48870–48885. [Google Scholar] [CrossRef]
- Chong, C.Y.; Lee, S.P.; Ling, T.C. Prioritizing and fulfilling quality attributes for virtual lab development through application of fuzzy analytic hierarchy process and software development guidelines. Malays. J. Comput. Sci. 2014, 27, 1–19. [Google Scholar]
- Khan, S.A.; Alenezi, M.; Agrawal, A.; Kumar, R.; Khan, R.A. Evaluating Performance of Software Durability through an Integrated Fuzzy-Based Symmetrical Method of ANP and TOPSIS. Symmetry 2020, 12, 493. [Google Scholar] [CrossRef]
- Agrawal, A.; Zarour, M.; Alenezi, M.; Kumar, R.; Khan, R.A. Security durability assessment through Fuzzy Analytic Hierarchy process. PeerJ Comput. Sci. 2019, 5, e2115. [Google Scholar] [CrossRef]
- Cevik-Onar, S.; Oztaysi, B.; Kahraman, C. Strategic decision selection using hesitant fuzzy TOPSIS and interval type-2 fuzzy AHP: A case study. Int. J. Comput. Intell. Syst. 2014, 7, 1002–1021. [Google Scholar] [CrossRef]
- Wang, C.N.; Thanh, N.V.; Su, C.C. The Study of a Multicriteria Decision Making Model for Wave Power Plant Location Selection in Vietnam. Processes 2019, 7, 650. [Google Scholar] [CrossRef]
- Kahraman, C. (Ed.) Fuzzy Multi-Criteria Decision Making: Theory and Applications with Recent Developments; Springer Science & Business Media: Berlin, Germany, 2008; Volume 16. [Google Scholar]
- Roy, B.; Misra, S.K. An Integrated Fuzzy ANP and TOPSIS Methodology for Software Selection under MCDM Perspective. Int. J. Innov. Res. Comput. Commun. Eng. 2018, 6, 492–501. [Google Scholar]
- Tavana, M.; Zandi, F.; Katehakis, M.N. A hybrid fuzzy group ANP–TOPSIS framework for assessment of e-government readiness from a CiRM perspective. Inf. Manag. 2013, 50, 383–397. [Google Scholar] [CrossRef]
- Li, B.Z.; Bi, R. The Application of Fuzzy-ANP in Evaluation Index System of Computer Security. Key Eng. Mater. 2010, 439–440, 754–759. [Google Scholar] [CrossRef]
- Kumar, R.; Khan, S.A.; Agrawal, A.; Khan, R.A. Measuring the security attributes through fuzzy analytic hierarchy process: Durability perspective. ICIC Express Lett. 2018, 12, 615–620. [Google Scholar]
- Hahn, W.J.; Seaman, S.L.; Bikel, R. Making decisions with multiple attributes: A case in sustainability planning. Graziadio Bus. Rev. 2012, 15, 365–381. [Google Scholar]
- Cusick, J.J. Durable Ideas in Software Engineering: Concepts, Methods and Approaches from My Virtual Toolbox; Bentham Science Publishers: Sharjah, UAE, 2013; Available online: https://www.amazon.com/Durable-Ideas-Software-Engineering-Approaches-ebook/dp/B00E7TCBEI (accessed on 16 August 2020).
- Ensmenger, N. When good software goes bad: The surprising durability of an ephemeral technology. In Proceedings of the MICE Mistakes, Ignorance, Contingency and Error in Science and Technology, Munich, Germany, 2–4 October 2014; pp. 1–16. [Google Scholar]
- Kelty, C.; Erickson, S. The Durability of Software; Meson Press: Lüneburg, Germany, 2015; Volume 1, pp. 1–13. [Google Scholar]
- Torra, V.; Narukawa, Y. On hesitant fuzzy sets and decision. In Proceedings of the 2009 IEEE International Conference on Fuzzy Systems, Jeju Island, Korea, 20–24 August 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 1378–1382. [Google Scholar]
- Rodriguez, R.M.; Martinez, L.; Herrera, F. Hesitant fuzzy linguistic term sets for decision making. IEEE Trans. Fuzzy Syst. 2011, 20, 109–119. [Google Scholar] [CrossRef]
- Rodriguez, R.M.; Martinez, L.; Torra, V.; Xu, Z.S.; Herrera, F. Hesitant fuzzy sets: State of the art and future directions. Int. J. Intell. Syst. 2014, 29, 495–524. [Google Scholar] [CrossRef]
- Beg, I.; Rashid, T. Multi-criteria trapezoidal valued intuitionistic fuzzy decision making with Choquet integral based TOPSIS. Opsearch 2014, 51, 98–129. [Google Scholar] [CrossRef]
- Xia, M.; Xu, Z. Hesitant fuzzy information aggregation in decision making. Int. J. Approx. Reason. 2011, 52, 395–407. [Google Scholar] [CrossRef]
- Saaty, T.L. The Analytic Network Process. In Encyclopedia of Operations Research and Management Science; Springer: Berlin/Heidelberg, Germany, 2001. [Google Scholar] [CrossRef]
- Hwang, C.L.; Lai, Y.J.; Liu, T.Y. A new approach for multiple objective decision making. Comput. Oper. Res. 1993, 20, 889–899. [Google Scholar] [CrossRef]
- Feenstra, R.C.; Knittel, C.R. Re-assessing the U.S. quality adjustment to computer prices: The role of durability and changing software. In Working Paper Series-Department of Economics; NBER: Cambridge, MA, USA, 2004; pp. 2–50. [Google Scholar]
| Rank | Linguistic Term | Abbreviation | Triangular Hesitant Fuzzy Number |
|---|---|---|---|
| 10 | Absolutely High Importance | AHI | (7.0000, 9.0000, 9.0000) |
| 9 | Very High Importance | VHI | (5.0000, 7.0000, 9.0000) |
| 8 | Essentially High Importance | ESHI | (3.0000, 5.0000, 7.0000) |
| 7 | Weakly High Importance | WHI | (1.0000, 3.0000, 5.0000) |
| 6 | Equally High Importance | EHI | (1.0000, 1.0000, 3. 0000) |
| 5 | Exactly Equal | EE | (1.0000, 1. 0000, 1.0000) |
| 4 | Equally Low Importance | ELI | (0.3300, 1.0000, 1.0000) |
| 3 | Weakly Low Important | WLI | (0.2000, 0.3300, 1.0000) |
| 2 | Essentially Low Importance | ESLI | (0.1400, 0.2000, 0.3300) |
| 1 | Very Low Importance | VLI | (0.1100, 0.1400, 0.2000) |
| 0 | Absolutely Low Importance | ALI | (0.1100, 0.1100, 0.1400) |
| Characteristics of Level 1 | Local Weights | Characteristics of Level 2 | Local Weights | Global Weights | Defuzzified Weights | Normalized Weights |
|---|---|---|---|---|---|---|
| C1 | 0.03000, 0.08000, 0.09000, 0.15000 | C11 | 0.07600, 0.21800, 0.45500, 1.03100 | 0.00228, 0.01744, 0.04095, 0.15465 | 0.04562 | 0.051725 |
| C12 | 0.03500, 0.09700, 0.19800, 0.51300 | 0.00105, 0.00776, 0.01782, 0.07695 | 0.02153 | 0.024408 | ||
| C13 | 0.05900, 0.20800, 0.34800, 1.26300 | 0.00177, 0.01664, 0.03132, 0.18945 | 0.04786 | 0.054263 | ||
| C14 | 0.03500, 0.09700, 0.19800, 0.51300 | 0.00105, 0.00776, 0.01782, 0.07695 | 0.02153 | 0.024408 | ||
| C15 | 0.03100, 0.07800, 0.12100, 0.39000 | 0.00093, 0.00624, 0.01089, 0.05850 | 0.01562 | 0.017705 | ||
| C2 | 0.11000, 0.28000, 0.33000, 0.51000 | C21 | 0.03500, 0.09700, 0.19800, 0.51300 | 0.00385, 0.02716, 0.06534, 0.26163 | 0.07508 | 0.085130 |
| C22 | 0.03300, 0.12900, 0.21200, 0.78100 | 0.00363, 0.03612, 0.06996, 0.39831 | 0.10235 | 0.116051 | ||
| C23 | 0.03100, 0.07800, 0.12100, 0.39000 | 0.00341, 0.02184, 0.03993, 0.19890 | 0.05431 | 0.061578 | ||
| C24 | 0.03500, 0.09070, 0.19080, 0.51300 | 0.00385, 0.02540, 0.06296, 0.26160 | 0.07370 | 0.083566 | ||
| C25 | 0.02200, 0.07300, 0.11300, 0.50300 | 0.00242, 0.02044, 0.03729, 0.25653 | 0.06240 | 0.070755 | ||
| C3 | 0.07000, 0.12000, 0.13000, 0.25000 | C31 | 0.07600, 0.21800, 0.45500, 1.03100 | 0.00532, 0.02616, 0.05915, 0.25775 | 0.07228 | 0.081957 |
| C32 | 0.03500, 0.09700, 0.19800, 0.51300 | 0.00245, 0.01164, 0.02574, 0.12825 | 0.03424 | 0.038827 | ||
| C33 | 0.07600, 0.21800, 0.45050, 1.03100 | 0.00532, 0.02616, 0.05857, 0.25775 | 0.07209 | 0.081736 | ||
| C34 | 0.03100, 0.07800, 0.12100, 0.39000 | 0.00217, 0.00936, 0.01573, 0.09750 | 0.02498 | 0.028318 | ||
| C35 | 0.03500, 0.09700, 0.19800, 0.51300 | 0.00245, 0.01164, 0.02574, 0.12825 | 0.03424 | 0.038827 | ||
| C4 | 0.04000, 0.04000, 0.05000, 0.11000 | C41 | 0.03100, 0.07800, 0.12100, 0.39000 | 0.00124, 0.00312, 0.00605, 0.04290 | 0.01041 | 0.011807 |
| C42 | 0.03500, 0.09700, 0.19800, 0.51300 | 0.00140, 0.00388, 0.00990, 0.05643 | 0.01423 | 0.016137 | ||
| C43 | 0.12000, 0.26000, 0.58000, 1.43000 | 0.00480, 0.01040, 0.02900, 0.15730 | 0.04015 | 0.045525 | ||
| C44 | 0.06000, 0.12000, 0.40000, 0.60000 | 0.00240, 0.00480, 0.02000, 0.06600 | 0.019667 | 0.022299 | ||
| C45 | 0.12000, 0.25000, 0.57000, 1.42000 | 0.00480, 0.01000, 0.02850, 0.15620 | 0.039667 | 0.044977 |
| S. No. | Characteristics of Level 1 | Global Weights | Defuzzified Weights | Normalized Weights | |
|---|---|---|---|---|---|
| 1 | Dependability | 0.03000, 0.08000, 0.09000, 0.15000 | 0.086666667 | 0.148148148 | C1 |
| 2 | Trustworthiness | 0.11000, 0.28000, 0.33000, 0.51000 | 0.306666667 | 0.524216524 | C2 |
| 3 | Human Trust | 0.07000, 0.12000, 0.13000, 0.25000 | 0.136666667 | 0.233618234 | C3 |
| 4 | Usability | 0.04000, 0.04000, 0.05000, 0.11000 | 0.055000000 | 0.094017094 | C4 |
| S. No. | Characteristics of Level 2 | Global Weights | Defuzzified Weights | Normalized Weights | |
|---|---|---|---|---|---|
| 1 | Confidentiality | 0.00760, 0.04360, 0.10010, 0.41240 | 0.117900 | 0.133682 | C11+C31 |
| 2 | Consumer Integrity | 0.00245, 0.01164, 0.02574, 0.12825 | 0.034243 | 0.038827 | C32 |
| 3 | Reliability | 0.00637, 0.03392, 0.076385, 0.3347 | 0.093613 | 0.106145 | C12+C33 |
| 4 | Maintainability | 0.00903, 0.05628, 0.11844, 0.59148 | 0.158325 | 0.179519 | C13+C21+C34+C41 |
| 5 | Accountability | 0.00468, 0.04388, 0.08778, 0.47526 | 0.123877 | 0.140459 | C14+C22 |
| 6 | Survivability | 0.00481, 0.02572, 0.04983, 0.25533 | 0.068540 | 0.077715 | C23+C42 |
| 7 | Availability | 0.00865, 0.035796, 0.091964, 0.41893 | 0.113850 | 0.129090 | C24+C43 |
| 8 | Accessibility | 0.00575, 0.03148, 0.06818, 0.38103 | 0.097683 | 0.110759 | C15+C25+C44 |
| 9 | User Satisfaction | 0.00725, 0.02164, 0.05424, 0.28445 | 0.073910 | 0.083804 | C35+C45 |
| Durability Characteristics/Alternatives | AV1 | AV2 | AV3 | AV4 | AV5 | AV6 |
|---|---|---|---|---|---|---|
| Confidentiality | 1.1800, 2.8200, 4.8200, 6.4500 | 2.0900, 3.7300, 5.7300, 6.4500 | 2.8200, 4.6400, 6.6400, 8.7200 | 1.5500, 3.1800, 5.1800, 6.7200 | 1.4500, 3.1800, 5.1800, 7.7200 | 2.4500, 4.2700, 6.2700, 8.6200 |
| Consumer Integrity | 0.8200, 2.2700, 4.2700, 6.6500 | 2.9100, 4.6400, 6.0000, 6.4500 | 1.4500, 3.0000, 4.9100, 5.4500 | 1.1800, 2.8200, 4.8200, 6.4500 | 2.0900, 3.7300, 5.7300, 6.4500 | 2.0900, 3.7300, 5.7300, 6.4500 |
| Reliability | 2.4500, 4.2700, 6.2700, 8.6500 | 3.1800, 5.1800, 7.1000, 8.6500 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.8200, 2.2700, 4.2700, 6.6500 | 3.0000, 4.8200, 6.8200, 7.6500 | 3.0000, 4.8200, 6.8200, 7.6500 |
| Maintainability | 1.1800, 2.8200, 4.8200, 6.4500 | 2.4500, 4.4500, 6.4500, 7.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.4500, 4.2700, 6.2700, 8.6500 | 3.9100, 5.9100, 7.8200, 8.6500 | 3.9100, 5.9100, 7.8200, 8.6500 |
| Accountability | 0.8200, 2.2700, 4.2700, 6.6500 | 3.0000, 4.8200, 6.8200, 7.6500 | 2.9100, 4.6400, 6.0000, 6.4500 | 1.4500, 3.0000, 4.9100, 5.4500 | 1.1800, 2.8200, 4.8200, 6.4500 | 2.0900, 3.7300, 5.7300, 6.4500 |
| Survivability | 2.4500, 4.2700, 6.2700, 8.6500 | 3.9100, 5.9100, 7.8200, 8.6500 | 3.1800, 5.1800, 7.1000, 8.6500 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.8200, 2.2700, 4.2700, 6.6500 | 3.0000, 4.8200, 6.8200, 7.6500 |
| Availability | 5.3600, 6.3600, 7.1200, 8.5100 | 3.7300, 5.7300, 7.5500, 8.6500 | 2.4500, 4.4500, 6.4500, 7.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.4500, 4.2700, 6.2700, 8.6500 | 3.9100, 5.9100, 7.8200, 8.6500 |
| Accessibility | 5.1200, 7.1400, 7.7200, 8.5900 | 3.1500, 5.1500, 6.9100, 7.8400 | 2.8200, 4.6400, 6.6400, 7.8400 | 1.5500, 3.1800, 5.1800, 6.5400 | 1.4500, 3.1800, 5.1800, 6.2500 | 2.4500, 4.2700, 6.2700, 8.2600 |
| User Satisfaction | 2.9100, 4.6400, 6.0000, 6.4500 | 1.4500, 3.0000, 4.9100, 5.4500 | 1.1800, 2.8200, 4.8200, 6.4500 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.4500, 4.2700, 6.2700, 8.6500 | 3.9100, 5.9100, 7.8200, 8.6500 |
| Durability Characteristics/Alternatives | AV1 | AV2 | AV3 | AV4 | AV5 | AV6 |
|---|---|---|---|---|---|---|
| Confidentiality | 0.2940, 0.4840, 0.5630, 0.7420 | 0.4830, 0.6199, 0.7030, 0.8390 | 0.3250, 0.4680, 0.5550, 0.6370 | 0.6040, 0.8120, 0.8580, 0.9690 | 0.6390, 0.8160, 0.5890, 0.9670 | 0.6200, 0.8720, 0.9360, 0.9890 |
| Consumer Integrity | 0.2490, 0.4130, 0.5320, 0.7410 | 0.3250, 0.4680, 0.5550, 0.6370 | 0.5540, 0.8040, 0.8800, 0.9580 | 0.6110, 0.7720, 0.8560, 0.9450 | 0.3800, 0.5740, 0.7220, 0.0820 | 0.6120, 0.8500, 0.9170, 0.9680 |
| Reliability | 0.3460, 0.5530, 0.6640, 0.8170 | 0.2750, 0.4560, 0.5330, 0.7330 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.1000, 0.1920, 0.3840 | 0.5500, 0.5500, 0.5500, 0.5500 | 0.4520, 0.6680, 0.7610, 0.8980 |
| Maintainability | 0.4370, 0.6360, 0.7360, 0.8580 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.2940, 0.4840, 0.5630, 0.7420 | 0.4830, 0.6199, 0.7030, 0.8390 | 0.3460, 0.5530, 0.6640, 0.8170 | 0.2750, 0.4560, 0.5330, 0.7330 |
| Accountability | 0.6390, 0.8160, 0.5890, 0.9670 | 0.2310, 0.3810, 0.5480, 0.7362 | 0.4830, 0.6199, 0.7030, 0.8390 | 0.3460, 0.5530, 0.6640, 0.8170 | 0.4370, 0.6360, 0.7360, 0.8580 | 0.3340, 0.5240, 0.6180, 0.7800 |
| Survivability | 0.6110, 0.7720, 0.8560, 0.9450 | 0.3800, 0.5740, 0.7220, 0.0820 | 0.3250, 0.4680, 0.5550, 0.6370 | 0.6040, 0.8120, 0.8580, 0.9690 | 0.6390, 0.8160, 0.5890, 0.9670 | 0.2310, 0.3810, 0.5480, 0.7362 |
| Availability | 0.5590, 0.5590, 0.5590, 0.5590 | 0.4230, 0.6490, 0.7640, 0.8800 | 0.2040, 0.3220, 0.4370, 0.5470 | 0.5540, 0.8040, 0.8800, 0.9580 | 0.6110, 0.7720, 0.8560, 0.9450 | 0.3800, 0.5740, 0.7220, 0.0820 |
| Accessibility | 0.0350, 0.0350, 0.0350, 0.0350 | 0.3460, 0.5530, 0.6640, 0.8170 | 0.4370, 0.6360, 0.7360, 0.8580 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.1000, 0.1920, 0.3840 | 0.5500, 0.5500, 0.5500, 0.5500 |
| User Satisfaction | 0.2940, 0.4840, 0.5630, 0.7420 | 0.4830, 0.6199, 0.7030, 0.8390 | 0.3460, 0.5530, 0.6640, 0.8170 | 0.5540, 0.8040, 0.8800, 0.9580 | 0.6110, 0.7720, 0.8560, 0.9450 | 0.3800, 0.5740, 0.7220, 0.0820 |
| Durability Characteristics/Alternatives | AV1 | AV2 | AV3 | AV4 | AV5 | AV6 |
|---|---|---|---|---|---|---|
| Confidentiality | 0.0570, 0.0850, 0.1080, 0.1310 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0428, 0.0590, 0.0640, 0.0680 | 0.0344, 0.0570, 0.0820, 0.1100 | 0.0470, 0.0740, 0.0920, 0.1120 | 0.0434, 0.0510, 0.0660, 0.0690 |
| Consumer Integrity | 0.0371, 0.0616, 0.0790, 0.1100 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0080, 0.0120, 0.0160, 0.0210 | 0.1150, 0.1670, 0.1830, 0.1990 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.0120, 0.0180, 0.0210, 0.0240 |
| Reliability | 0.0630, 0.0979, 0.1140, 0.1310 | 0.0610, 0.0870, 0.1010, 0.1200 | 0.0087, 0.0135, 0.0170, 0.0210 | 0.0774, 0.1180, 0.1440, 0.1730 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0080, 0.0120, 0.0160, 0.0210 |
| Maintainability | 0.0120, 0.0180, 0.0210, 0.0240 | 0.1250, 0.1690, 0.1850, 0.2010 | 0.1480, 0.1891, 0.2060, 0.2240 | 0.0630, 0.0979, 0.1140, 0.1310 | 0.0610, 0.0870, 0.1010, 0.1200 | 0.0190, 0.0325, 0.0380, 0.0510 |
| Accountability | 0.0080, 0.0120, 0.0160, 0.0210 | 0.1150, 0.1670, 0.1830, 0.1990 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.0120, 0.0180, 0.0210, 0.0240 | 0.1250, 0.1690, 0.1850, 0.2010 | 0.1480, 0.1891, 0.2060, 0.2240 |
| Survivability | 0.0854, 0.0930, 0.0930, 0.0986 | 0.0371, 0.0616, 0.0790, 0.1100 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0080, 0.0120, 0.0160, 0.0210 | 0.1150, 0.1670, 0.1830, 0.1990 | 0.1420, 0.1790, 0.1980, 0.2190 |
| Availability | 0.0890, 0.0960, 0.0960, 0.1030 | 0.0630, 0.0979, 0.1140, 0.1310 | 0.0610, 0.0870, 0.1010, 0.1200 | 0.0087, 0.0135, 0.0170, 0.0210 | 0.0774, 0.1180, 0.1440, 0.1730 | 0.1330, 0.1680, 0.1840, 0.2080 |
| Accessibility | 0.0010, 0.0060, 0.0060, 0.0130 | 0.0516, 0.0820, 0.0990, 0.1220 | 0.0580, 0.0850, 0.0950, 0.1180 | 0.0230, 0.0370, 0.0430, 0.0550 | 0.0090, 0.0230, 0.0450, 0.0590 | 0.0870, 0.0940, 0.0940, 0.1010 |
| User Satisfaction | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0080, 0.0120, 0.0160, 0.0210 | 0.1150, 0.1670, 0.1830, 0.1990 | 0.0630, 0.0979, 0.1140, 0.1310 | 0.0610, 0.0870, 0.1010, 0.1200 | 0.0190, 0.0325, 0.0380, 0.0510 |
| Alternatives | d+i | d−i | ||
|---|---|---|---|---|
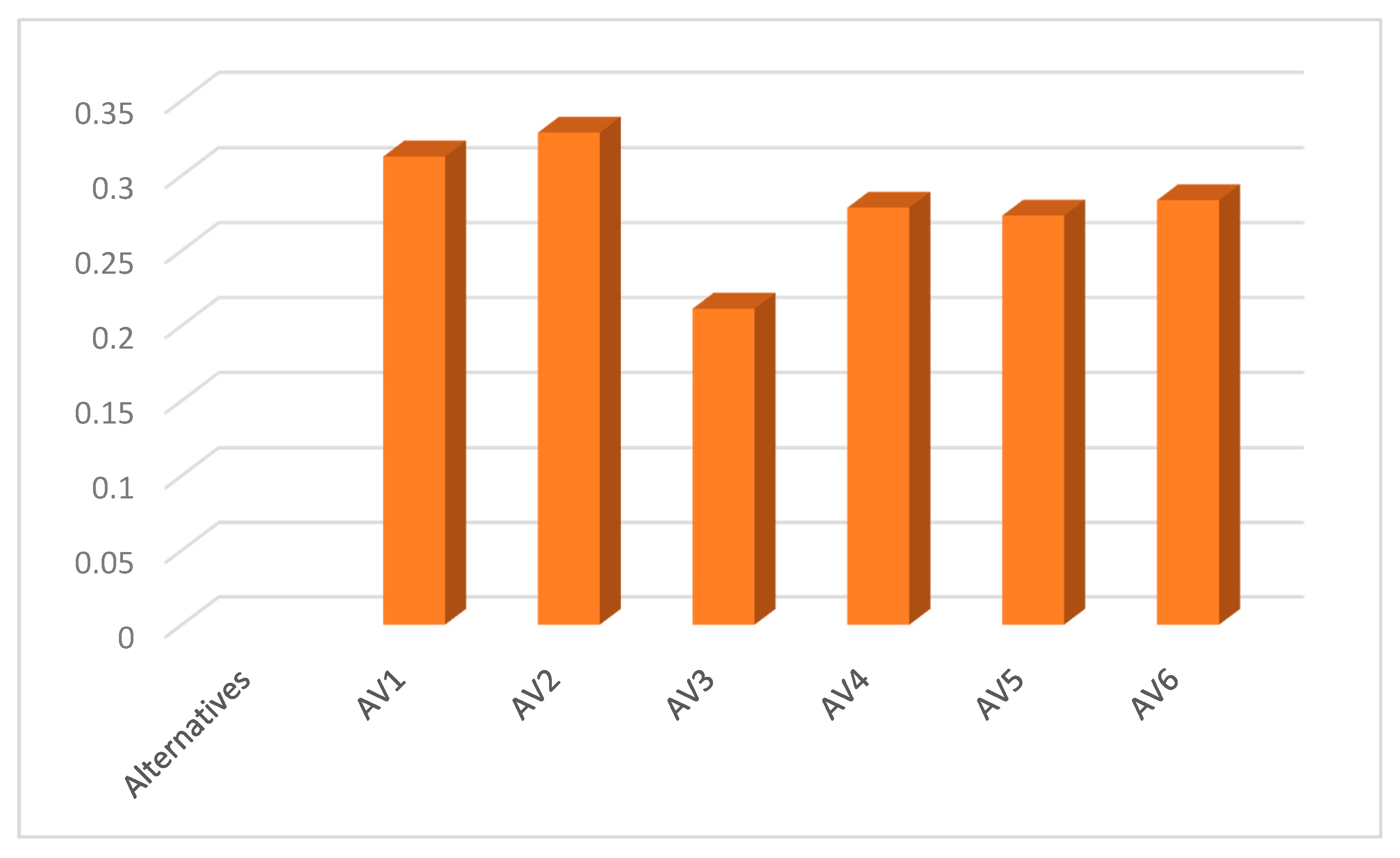
| Version 1 | AV1 | 0.16154 | 0.07965 | 0.31254 |
| Version 2 | AV2 | 0.24264 | 0.12132 | 0.32854 |
| Version 3 | AV3 | 0.24525 | 0.07524 | 0.21126 |
| Version 4 | AV4 | 0.45548 | 0.16854 | 0.27854 |
| Version 5 | AV5 | 0.48745 | 0.18123 | 0.27325 |
| Version 6 | AV6 | 0.15874 | 0.06565 | 0.28352 |
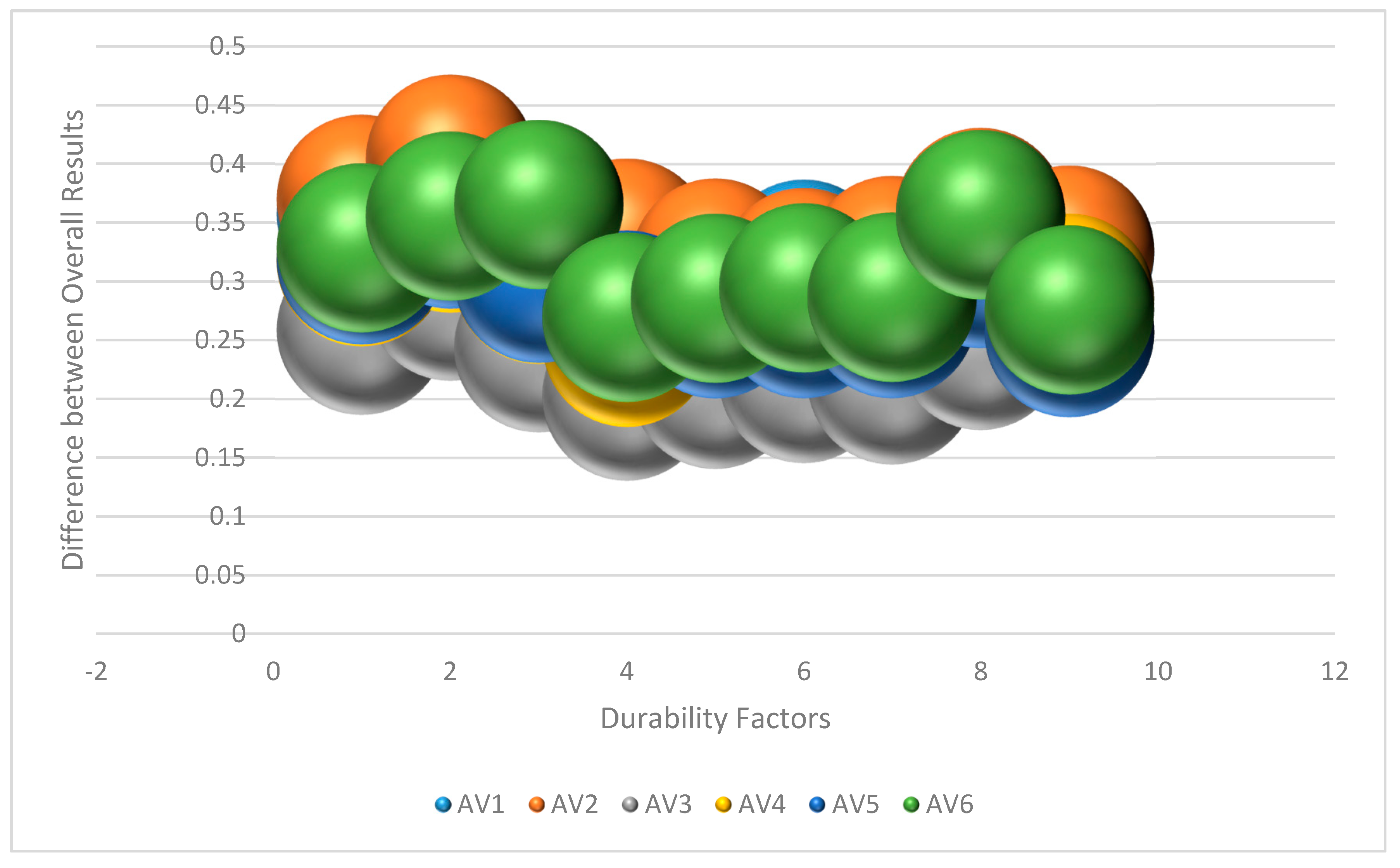
| Alternatives | Original Weights | Confidentiality | Consumer Integrity | Reliability | Maintainability | Accountability | Survivability | Availability | Accessibility | User Satisfaction | |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Version 1 | AV1 | 0.31254 | 0.35735 | 0.39869 | 0.34674 | 0.30778 | 0.31226 | 0.31457 | 0.31475 | 0.34967 | 0.32354 |
| Version 2 | AV2 | 0.32854 | 0.36984 | 0.40387 | 0.35963 | 0.33254 | 0.31545 | 0.30749 | 0.31769 | 0.35859 | 0.32658 |
| Version 3 | AV3 | 0.21126 | 0.25857 | 0.28747 | 0.24364 | 0.20242 | 0.21256 | 0.21749 | 0.21632 | 0.24567 | 0.25687 |
| Version 4 | AV4 | 0.27854 | 0.31695 | 0.34565 | 0.30194 | 0.24823 | 0.28325 | 0.29267 | 0.28654 | 0.34524 | 0.28547 |
| Version 5 | AV5 | 0.27325 | 0.31856 | 0.34887 | 0.30274 | 0.27125 | 0.27256 | 0.27267 | 0.27267 | 0.31548 | 0.25648 |
| Version 6 | AV6 | 0.28352 | 0.32859 | 0.35562 | 0.36547 | 0.26945 | 0.28574 | 0.29457 | 0.28659 | 0.35687 | 0.27584 |
| Alternatives | Hesitant Fuzzy AHP-TOPSIS | Fuzzy AHP-TOPSIS | Fuzzy ANP-TOPSIS | Classical AHP-TOPSIS | Classical ANP-TOPSIS | |
|---|---|---|---|---|---|---|
| Version 1 | AV1 | 0.31254 | 0.31002 | 0.30712 | 0.29672 | 0.31235 |
| Version 2 | AV2 | 0.32854 | 0.32003 | 0.33223 | 0.30944 | 0.31534 |
| Version 3 | AV3 | 0.21126 | 0.21002 | 0.20248 | 0.19714 | 0.21362 |
| Version 4 | AV4 | 0.27854 | 0.27004 | 0.24812 | 0.26057 | 0.28244 |
| Version 5 | AV5 | 0.27325 | 0.27006 | 0.27023 | 0.31214 | 0.27457 |
| Version 6 | AV6 | 0.28352 | 0.28001 | 0.26958 | 0.28125 | 0.28555 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sahu, K.; Alzahrani, F.A.; Srivastava, R.K.; Kumar, R. Hesitant Fuzzy Sets Based Symmetrical Model of Decision-Making for Estimating the Durability of Web Application. Symmetry 2020, 12, 1770. https://doi.org/10.3390/sym12111770
Sahu K, Alzahrani FA, Srivastava RK, Kumar R. Hesitant Fuzzy Sets Based Symmetrical Model of Decision-Making for Estimating the Durability of Web Application. Symmetry. 2020; 12(11):1770. https://doi.org/10.3390/sym12111770
Chicago/Turabian StyleSahu, Kavita, Fahad A. Alzahrani, R. K. Srivastava, and Rajeev Kumar. 2020. "Hesitant Fuzzy Sets Based Symmetrical Model of Decision-Making for Estimating the Durability of Web Application" Symmetry 12, no. 11: 1770. https://doi.org/10.3390/sym12111770
APA StyleSahu, K., Alzahrani, F. A., Srivastava, R. K., & Kumar, R. (2020). Hesitant Fuzzy Sets Based Symmetrical Model of Decision-Making for Estimating the Durability of Web Application. Symmetry, 12(11), 1770. https://doi.org/10.3390/sym12111770






