Abstract
In this paper, an improved encryption algorithm based on numerical methods and rotation–translation equation is proposed. We develop the new encryption-decryption algorithm by using the concept of symmetric key instead of public key. Symmetric key algorithms use the same key for both encryption and decryption. Most symmetric key encryption algorithms use either block ciphers or stream ciphers. Our goal in this work is to improve an existing encryption algorithm by using a faster convergent iterative method, providing secure convergence of the corresponding numerical scheme, and improved security by a using rotation–translation formula.
1. Introduction
Cryptography is a practice and study of techniques of hidden data transfer so that only the intended receivers can extract and read the data [1]. It is the study of mathematical methods related to different aspects of informational security such as data origin, entity authentication, data integrity and confidentiality. The source data, which is to be protected by cryptography, is called plaintext. The procedure of transforming plaintext into an unreadable form termed ciphertext is called encryption. Decryption is the reverse process, recovering the plaintext back from a ciphertext. A cryptographic system is a set of algorithms, seeded by key that encrypt given messages into ciphertext and recover them back into input data. The scheme for a secret key encryption is first proposed by Shannon [2].
There are two categories of key-based cryptographic algorithms: symmetric key (secret key) cryptography and public key (asymmetric key) cryptography. In the first category, a sender and recipient share a private key known only to both of them. The same key is used for encryption and decryption. The most commonly used symmetric algorithms are AES (Advanced Encryption Standard) [3], Cha Cha [4], Blowfish [5], and IDEA (International Data Encryption Algorithm) [6]. By contrast, for asymmetric key cryptography, two keys are used: the first one is made publicly available to senders for encrypting plaintext while the second key is kept secret and is used by the receivers for decrypting the ciphertext. The most ordinarily exploited asymmetric schemes are the Rivest–Shamir–Adleman (RSA) cryptosystem [7] and ECC (Elliptic-curve cryptography) [8]. Symmetric encryption schemes are usually faster than public key counterparts and thus are preferred for encrypting big data.
In symmetric key cryptography, either stream ciphers or block ciphers can be used. An example of stream cipher is the Vigenere Cipher. These types of ciphers encrypt the letters or digits (typically bytes) of a message one at a time, while block ciphers take a number of bits and encrypt them as a single unit. Until now, many symmetric data encryption algorithms have been proposed. Some of them use classical schemes for text encryption. In [9], an extension of a public key cryptographic scheme to support a private key cryptographic scheme which is a mix of AES and ECC is presented. Plain text encryption based on AES, Blowfish, and SALSA20 is designed and experimentally evaluated in [10].
Some of them use chaotic equations for text encryption. In Reference [11], a novel scheme for digital image encryption based on a mix of chaos theory and DNA calculation is presented. In [12], a chaos-based pseudorandom generation scheme based on a six-dimensional chaotic system is proposed. A text encryption architecture is given. Novel symmetric data encryption algorithms based on logistic chaotic formula are presented in [13,14,15]. A chaotic logistic map filtered with binary function is proposed to text encryption scheme in Reference [16]. In [17], a chaos-based encryption technique based on logistic, pinchers, and sine-circle maps is proposed. An algorithm of chaotic data encryption system by using private characteristic of electrocardiogram (ECG) signal and logistic map is designed in [18]. In [19,20], the chaotic behaviour of a Chua system is used in novel text encryption scheme designs. A novel pseudorandom bit generation scheme based on rotation equations is proposed in [21]. The technique has good statistical properties measured by test packages. A novel encryption method based on modified pulsed-coupled spiking neurons circuit is presented in Reference [22]. In [23], a modified quadratic map for numeric sensor data encryption is proposed.
2. Symmetric Key Encryption Algorithms Based on Numerical Methods
One of the first published works that consider symmetric key encryption algorithm based on numerical methods is by Ghosh in [24] (see also [25,26]), where it is shown that any nonlinear function with one variable can be defined as a key. The encryption process then is defined as finding the solution of the equation
where represents the numerical code of the ith symbol in the plaintext (e.g., the ASCII code). The function must be chosen in such a way that the corresponding formula (1) has at least one real root for any i. Then, the set of roots represents the ciphertext. On the receiver side, each entry is decoded by substituting it into giving rise to the plaintext character (the value must be appropriately rounded to recover ). In [24], as a key function , the authors use a cubic polynomial and, for the numerical solution of equations , they use the Newton’s iterative method. We have to mention that, in solving nonlinear Equation (1), we can use different iterative methods. Analogous to this algorithm, an example of a public key cryptosystem based on numerical methods is considered in [27].
It is important to say that the main weaknesses of such algorithms can be summarized in the following:
- Lack of rules on how to choose the function f and suitable iterative method so that the convergence of the process is always guaranteed.
- Vulnerability to attack because in these types of algorithms the same letter is encoded with the same real number of each occurrence in the plaintext.
Our aim in the present work is to develop a new algorithm that solves the disadvantages mentioned above. In order to achieve this, the new scheme will be based on employing numerical iterative methods and rotation–translation formula.
3. On Numerical Methods and Rotation–Translation Equation
3.1. On Numerical Methods for Solving Nonlinear Equations
Although the Newton’s iterative method
is one of the most popular and commonly used methods, numerical analysis offers many iterative methods that can be used in the stage of solution of Equation (1). In general to calculate the roots of nonlinear equations (of the type (1)), we have to use approximate (iterative) methods. When studying an iterative method, two of the most important aspects to consider are:
- the convergence speed of the iteration,
- an interval of convergence and the rules for choosing the initial approximations.
Most of the known iterative algorithms for solving nonlinear equations are only locally convergent, i.e., before using such a method, we need to locate the unknown root at a sufficiently small interval. Even if the root sought is located at the appropriate interval, if we do not choose the initial approximation in a proper way, the process may not be convergent. Usually, iterative methods of this type require the following convergence conditions:
- need to have an interval containing a single root of f, and
- the derivatives and must not have zeros in the interval .
Then, the corresponding iterative process converges to the sought root for an initial approximation which is the end of the interval , where (or ).
For some examples of more computationally efficient and higher order iterative methods, we refer the reader to [28].
In the encryption algorithm that we will introduce later, we will use the following iterative function
where and . This iterative algorithm is explored by Jarrat in [29], and it is known as Jarrat’s method (see also [30]).
The reason we prefer iteration method (3) over method (2) is its faster convergence. The order of convergence of Jarrat’s method is four, while the one of Newton’s method is only two (see [30]). In addition, method (3) has higher computational efficiency, although at each step of the iteration one value of f and two values of are calculated (while in the Newton’s method, one value of f and one value of are calculated). Thus, if the function f is a polynomial, then calculating the value of the function f is always more complex than calculating its derivative .
3.2. Base of Rotation–Translation Equation
In order to avoid the vulnerability to statistical attack, we include additional randomness by using the following space contraction formula based on rotation–translation equation of the form [31]
where the angle of rotation is
The translation value is , the space contraction value is , and rotation values are and . The rotation–translation Equation (4) with initial conditions , is presented in Figure 1.
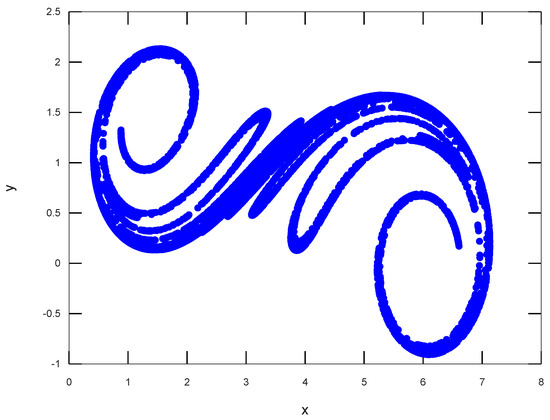
Figure 1.
Space contraction.
4. Proposed Encryption Algorithm Based on Numerical Method and Rotation–Translation Equation
Here, we describe an encryption algorithm based on space contraction and numerical method. Any nonlinear function or polynomial f with one variable can be defined as part of a key.
We consider plaintext P with byte length of L. The initial values and from Equation (4), and an initial iteration number , are determined. The rotation–translation formula, Equation (4), is iterated for times.
The proposed algorithm based on numerical method and space contraction is given below:
- Read the symbols from the plaintext data and get the ASCII values of the different symbols;
- Construct a system of L nonlinear equations by subtracting the ASCII values from the function f and equate with zero;
- Solve individually the nonlinear equations and put the results into an array B;
- The loop of Equation (4) continues, and as an output, two real numbers and are generated. We take the sum of and to produce the real number , which is put into an array R.
- Return to Step 4 until a stream of real numbers R with length L is reached.
- We get the sum of the two arrays B and R to produce E, the output array of real numbers.
Remark 1.
In Step 2 of Encryption algorithm, it is desirable that the function or polynomial f is such that each equation of the type has at least one real root, and it is easy to determine the initial approximation, which guarantees the convergence of the iterative process.
4.1. Approaches for Choosing a Nonlinear Function
In the following, we consider two example functions that are suitable for selecting in the above algorithm.
4.1.1. Nonlinear Function
Let has the following form
where p is a real parameter such that . For its first derivative,
we conclude that for all , i.e., the function is monotonically increasing for all . This and the limits
show that the function has only one real root. From the second derivative of f
and because for , it follows that the function is convex for .
Therefore, all these properties are also valid for the functions
where is an integer value (the corresponding ASCII code). Then, for any i, the function is monotonous, convex, and has a real root in the interval . Indeed, it can be shown that each one function has a real root in the finite interval .
4.1.2. Polynomial Function
We consider a fifth degree monic polynomial having the following form:
where p and q are real parameters such that . From the fundamental theorem of algebra, it follows that has at least one real root. Using the Descartes’ rules of sign, we can prove that has no negative real root, hence it has at least one real positive root (see Appendix A). Examining the first two derivatives of f, it can be shown that the function is monotonically increasing, convex and has a real root in the interval , for any . By using the bounding theorems (see Appendix A), it can be shown that has a real root in the finite interval .
4.2. An Example of Encryption
In order to demonstrate the proposed algorithm, we will use the following example:
The text to be encrypted: “Shumen university”.
As a key function, we use the polynomial
which is obtained by Equation (7) in the case of . During the encryption process (Step 3 of the Algorithm), we have to solve in series nonlinear equations of the type
where represents the ASCII code of the i-th character in the text, i.e., . From the analysis of the polynomial (7) and using the bounding theorems for the roots of polynomials, we deduce that Equation (8) has a real root in the interval for any . Moreover, this interval is such that the iterative process (3) is convergent to the solution for any initial approximation . For this reason, we use the same initial approximation for each Equation (8) obtained during the encryption process, namely the middle point of the interval: .
We solve all the equations by iterative function (3) and by using the following stopping criteria
- , and
- ,
where .
As a result, for all the equations, the stopping criteria are reached after three iterations. For comparison, if we use the Newton iterative method (2) instead of the Jarrats’ method for solving the corresponding equations, with the same initial approximation, we get six iterations for each equation, see Table 1.

Table 1.
Number of iterations for Jarrats’method (JM) and Newton method (NM), and generated arrays.
The output array of real numbers E is in the last column of Table 1, and this is the encrypted text that the recipient receives.
4.3. Brute-Force Attack Analysis
The set of all initial values constitutes the key size. The key size of the novel encryption algorithm has the following initial key values , , and at least three real coefficients of the polynomial f (for monic polynomial f of degree ). The two seeds and are constructed by randomly choosing two floating-point values that belonging to the intervals and , respectively. The novel encryption algorithm does not propose weak keys. As stated in the IEEE Standard for floating-point arithmetic [32], the computational precision of the 64-bit floating point variable is about . The key size of the novel encryption is , which is sufficient enough to defeat brute-force attack [33]. The key space is comparable to state-of-the-art chaos-based encryption algorithms; for example, [10,13,16].
4.4. Statistical Test Analysis of the Proposed Encryption
In an attempt to evaluate randomness of the improved encryption algorithm, we used NIST [34], ENT [35], and PractRand [36] statistical test applications. The output numbers from array E are converted to bytes as follows: , where calculates the integer part of e, truncating the value at the decimal point, calculates the absolute value of e, and calculates the reminder after division. The bytes are produced. Using the improved encryption, sequences of 125,000 bytes are produced.
The NIST suite software (version sts-2.1.2) includes 15 statistical tests: monobit, block frequency, cumulative sums forward and reverse, runs, longest run of ones, rank, Fourier, non-overlapping templates, overlapping templates, universal, approximate entropy, serial one and two, linear complexity, random excursion, and random excursion variant.
The output results of the first 13 tests are in Table 2. The minimum hit rate for each statistical test with the excluding of the random excursion variant test is approximately 980 for a sample size of 1000 byte stings. The minimum hit rate for the random excursion variant test is approximately 600 for a sample size of 614 byte strings. The random excursion test outputs 8 p-values which are tabulated in Table 3. The random excursion variant test calculates 18 randomness probability numbers: p-values, and they are in Table 4.

Table 2.
NIST test suite results.

Table 3.
NIST Random excursion test results.

Table 4.
NIST Random excursion variant test results.
The improved encryption algorithm passed successfully all the NIST tests.
The ENT application includes six tests to bit or byte sequences. We tested a stream of 125,000,000 bytes (1,000,000,000 bits) of the improved encryption and tabulated the output results in Table 5. The novel encryption passed successfully all the ENT tests.

Table 5.
ENT test results.
The third suite is PractRand. We tested our improved encryption algorithm for strings up to 1 GB (bytes) in length, passing all statistical tests successfully as shown in Table 6.

Table 6.
PractRand test results.
The different statistical tests clearly show the high quality of the proposed algorithm. Table 7 summarizes some of the computed values of our proposed scheme with other algorithms. The performance test of the novel scheme is based on the average response time with data size of 1 MB. The execution is done on mobile Dell Inspiron computer i7-3630QM (2.4 GHz, 8GB RAM).

Table 7.
Comparison of our improved symmetric key encryption with other algorithms.
Based on the good test outputs, we can infer that the novel text encryption based on numerical method and rotation–translation formula has satisfying statistical characteristics and provides a reasonable level of security.
5. Conclusions
We have presented an improved encryption algorithm based on numerical method and rotation–translation formula. The new method uses a faster convergent iterative algorithm and adds additional randomness by using the space contraction equation. Two exemplary ways of constructing nonlinear functions or polynomials with corresponding properties are described. In the examples considered, we demonstrate how to determine the interval containing the desired root and in which the iterative method is guaranteed to be convergent. Our security analysis shows that the improved encryption scheme can be successfully used for information security.
Author Contributions
B.S. and G.N. wrote and edited the manuscript. All authors have read and agreed to the published version of the manuscript.
Funding
The paper is partially supported by the National Scientific Program “Information and Communication Technologies for a Single Digital Market in Science, Education and Security (ICTinSES)”, financed by the Ministry of Education and Science, Bulgaria for Borislav Stoyanov.
Acknowledgments
The authors are grateful to the reviewer’s valuable comments that significantly improved the scientific paper.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A.
Appendix A.1. Real Roots Counting of Polynomials
Consider a monic polynomial of degree n
From the fundamental theorem of algebra, it follows that f has n real or complex roots, counting multiplicities. If the coefficients are all real, then the complex roots occur in conjugate pairs.
Using the following Descartes’ rules of sign, we can count the number of real positive zeros of f.
Descartes’ rules
Let p be the number of variations in the sign of the coefficients (where and the zero coefficients are ignored). Let m be the number of real positive zeros of f. Then,
- ;
- is an even integer.
A negative zero of , if exists, is a positive zero of .
Appendix A.2. Bounds of Real Roots of Polynomials
The first result in the theory of the location of polynomial zeros is due to Gauss, which is improved by Cauchy in [39], where he proves the following theorem.
Theorem A1 (Cauchy).
Let
be a polynomial with complex coefficients, where and . Then, all the zeros of lie inside the circle of radius
about the origin.
Another bound given by Lagrange is:
Let
be a polynomial with complex coefficients, where and . Then, all the zeros of lie inside the circle of radius
about the origin.
The next theorem is about bounding positive real roots of polynomials with real coefficients due to Cauchy.
Theorem A2 (Cauchy).
Let
be a polynomial with real coefficients, where and and which has strictly negative coefficients. Then, every positive real root of is no larger than r:
More recent and sharper results are obtained by Joyal, Labelle, and Rahman [40] by proving.
Theorem A3.
If , then all the zeros of the monic polynomial
are contained in the disc
References
- Stallings, W. Cryptography and Network Security: Principles and Practice; Pearson: Upper Saddle River, NJ, USA, 2017. [Google Scholar]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Daemen, J.; Rijmen, V. The Rijndael block cipher: AES proposal. In Proceedings of the First, Candidate Conference (AeS1), Rome, Italy, 22–23 March 1999; pp. 343–348. [Google Scholar]
- Bernstein, D.J. ChaCha, a variant of Salsa20. In Proceedings of the Workshop Record of SASC, Lausanne, Switzerland, 13–14 February 2008; Volume 8, pp. 3–5. [Google Scholar]
- Schneier, B. Description of a new variable-length key, 64-bit block cipher (Blowfish). In Fast Software Encryption; Anderson, R., Ed.; Springer: Berlin/Heidelberg, Germany, 1994; pp. 191–204. [Google Scholar]
- Lai, X.; Massey, J.L. A Proposal for a New Block Encryption Standard. In Advances in Cryptology—EUROCRYPT ’90; Damgård, I.B., Ed.; Springer: Berlin/Heidelberg, Germany, 1991; pp. 389–404. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Adleman, L.M. Cryptographic Communications System and Method. U.S. Patent 4,405,829, 20 September 1983. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Mathur, N.; Bansode, R. AES Based Text Encryption Using 12 Rounds with Dynamic Key Selection. Procedia Comput. Sci. 2016, 79, 1036–1043. [Google Scholar] [CrossRef]
- Panda, M.; Nag, A. Plain Text Encryption Using AES, DES and SALSA20 by Java Based Bouncy Castle API on Windows and Linux. In Proceedings of the 2015 Second International Conference on Advances in Computing and Communication Engineering, Rohtak, India, 1–2 May 2015; pp. 541–548. [Google Scholar] [CrossRef]
- Babaei, M. A novel text and image encryption method based on chaos theory and DNA computing. Natural Comput. 2013, 12, 101–107. [Google Scholar] [CrossRef]
- Min, L.; Lan, X.; Hao, L.; Yang, X. A 6 Dimensional Chaotic Generalized Synchronization System and Design of Pseudorandom Number Generator with Application in Image Encryption. In Proceedings of the 2014 Tenth International Conference on Computational Intelligence and Security, Yunnan, China, 15–16 November 2014; pp. 356–362. [Google Scholar] [CrossRef]
- Murillo-Escobar, M.; Abundiz-Pérez, F.; Cruz-Hernández, C.; López-Gutiérrez, R. A novel symmetric text encryption algorithm based on logistic map. In Proceedings of the International Conference on Communications, Signal Processing and Computers, Guilin, China, 5–8 August 2014; Volume 32, pp. 49–53. [Google Scholar]
- Murillo-Escobar, M.; Cruz-Hernández, C.; Cardoza-Avendaño, L.; Méndez-Ramírez, R. A novel pseudorandom number generator based on pseudorandomly enhanced logistic map. Nonlinear Dyn. 2017, 87, 407–425. [Google Scholar] [CrossRef]
- Volos, C.K.; Kyprianidis, I.; Stouboulos, I. Text Encryption Scheme Realized with a Chaotic Pseudo-Random Bit Generator. J. Eng. Sci. Technol. Rev. 2013, 6, 9–14. [Google Scholar] [CrossRef]
- Wang, X.Y.; Gu, S.X. New chaotic encryption algorithm based on chaotic sequence and plain text. IET Inf. Secur. 2014, 8, 213–216. [Google Scholar] [CrossRef]
- Akgül, A.; Kaçar, S.; Aricıoğlu, B.; Pehlivan, I. Text encryption by using one-dimensional chaos generators and nonlinear equations. In Proceedings of the 2013 IEEE 8th International Conference on Electrical and Electronics Engineering (ELECO), Bursa, Turkey, 28–30 November 2013; pp. 320–323. [Google Scholar]
- Chen, C.; Lin, C. Text encryption using ECG signals with chaotic Logistic map. In Proceedings of the 2010 5th IEEE Conference on Industrial Electronics and Applications, Taichung, Taiwan, 15–17 June 2010; pp. 1741–1746. [Google Scholar] [CrossRef]
- Volos, C.K.; Andreatos, A.S. Secure text encryption based on hardware chaotic noise generator. J. Appl. Math. Bioinform. 2015, 5, 15–35. [Google Scholar]
- Giakoumis, A.; Volos, C.K.; Munoz-Pacheco, J.M.; del Carmen Gomez-Pavon, L.; Stouboulos, I.N.; Kyprianidis, I.M. Text encryption device based on a chaotic random bit generator. In Proceedings of the 2018 IEEE 9th Latin American Symposium on Circuits Systems (LASCAS), Puerto Vallarta, Mexico, 25–28 February 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Stoyanov, B.; Kordov, K. Image Encryption Using Chebyshev Map and Rotation Equation. Entropy 2015, 17, 2117–2139. [Google Scholar] [CrossRef]
- Ge, R.; Yang, G.; Wu, J.; Chen, Y.; Coatrieux, G.; Luo, L. A Novel Chaos-Based Symmetric Image Encryption Using Bit-Pair Level Process. IEEE Access 2019, 7, 99470–99480. [Google Scholar] [CrossRef]
- Nesa, N.; Ghosh, T.; Banerjee, I. Design of a chaos-based encryption scheme for sensor data using a novel logarithmic chaotic map. J. Inf. Secur. Appl. 2019, 47, 320–328. [Google Scholar] [CrossRef]
- Ghosh, A.; Saha, A. A Numerical Method Based Encryption Algorithm With Steganography. Comput. Sci. Inf. Technol. 2013, 3, 149–157. [Google Scholar] [CrossRef]
- Othman, H.; Hassoun, Y.; Owayjan, M. Entropy model for symmetric key cryptography algorithms based on numerical methods. In Proceedings of the 2015 International Conference on Applied Research in Computer Science and Engineering (ICAR), Beirut, Lebanon, 8–9 October 2015; pp. 1–2. [Google Scholar] [CrossRef]
- Hassoun, Y.; Othman, H. Symmetric Key Cryptography Algorithms Based on Numerical Methods. In Proceedings of the NumAn 2014 Conference, Crete, Greece, 22–27 June 2014; pp. 151–155. [Google Scholar]
- AL-Siaq, I.R. Public Key Cryptosystem Based on Numerical Methods. Glob. J. Pure Appl. Math. 2017, 13, 3105–3112. [Google Scholar]
- Traub, J.F. Iterative Methods for the Solution of Equations; Prentice-Hall Series in Automatic Computation; Prentice-Hall: Englewood Cliffs, NJ, USA, 1982. [Google Scholar]
- Jarrat, P. Some fourth order multipoint iterative methods for solving equations. Math. Comput. 1966, 20, 434–437. [Google Scholar] [CrossRef]
- Nedzhibov, G.H.; Hasanov, V.I.; Petkov, M.G. On some families of multi-point iterative methods for solving nonlinear equations. Numer. Algorithms 2006, 42, 127–136. [Google Scholar] [CrossRef]
- Skiadas, C.H.; Skiadas, C. Chaotic Modelling and Simulation: Analysis of Chaotic Models, Attractors and Forms; Chapman and Hall/CRC: London, UK, 2008. [Google Scholar]
- IEEE Standard for Floating-Point Arithmetic; IEEE Std 754-2008; IEEE Computer Society: New York, NY, USA, 2008; pp. 1–70. [CrossRef]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E.; Leigh, S.; Levenson, M.; Vangel, M.; Banks, D.; Heckert, A.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Application. In NIST Special Publication 800-22: Revision 1a, Lawrence E. Bassham III; NIST: Gaithersburg, MD, USA, 2010. [Google Scholar]
- Walker, J. ENT: A Pseudorandom Number Sequence Test Program; Fourmilab: Switzerland, 2008. [Google Scholar]
- Doty-Humphrey, C. PractRand: C++ Library of Pseudo-Random Number Generators And Statistical Tests for RNGs. 2014. Available online: http://pracrand.sourceforge.net/ (accessed on 17 December 2019).
- Abubaker, S.; Wu, K. DAFA—A Lightweight DES Augmented Finite Automaton Cryptosystem. In Security and Privacy in Communication Networks; Keromytis, A.D., Di Pietro, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 1–18. [Google Scholar]
- Mushtaq, M.F.; Jamel, S.; Disina, A.H.; Pindar, Z.A.; Shakir, N.S.A.; Deris, M.M. A Survey on the cryptographic encryption algorithms. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 333–344. [Google Scholar]
- Cauchy, A. Exercises de Mathematiques; IV Annee de Bure Freres: Paris, France, 1829. [Google Scholar]
- Joyal, G.L.; Rahman, Q.I. On the Location of Zeros of Polynomials. Can. Math. Bull. 1967, 10, 53–63. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).