Abstract
The security issue on the physical layer is of significant challenge yet of paramount importance for 5G communications. In some previous works, transmit power allocation has already been studied for orthogonal frequency division multiplexing (OFDM) secure communication with Gaussian channel inputs for both a single user and multiple users. Faced with peak transmission power constraints, we adopt discrete channel inputs (e.g., equiprobable Quadrature Phase Shift Keying (QPSK) with symmetry) in a practical communication system, instead of Gaussian channel inputs. Finite-alphabet inputs impose a more significant challenge as compared with conventional Gaussian random inputs for the multiuser wiretap OFDM systems. This paper considers the joint resource allocation in frequency-domain artificial noise (AN) assisted multiuser wiretap OFDM channels with discrete channel inputs. This security problem is formulated as nonconvex sum secrecy rate optimization by jointly optimizing the subcarrier allocation, information-bearing power, and AN-bearing power. To this end, with a suboptimal subcarrier allocation scheme, we propose an efficient iterative algorithm to allocate the power between the information and the AN via the Lagrange duality method. Finally, we carry out some numerical simulations to demonstrate the performance of the proposed algorithm.
1. Introduction
Recent years have witnessed the rapid development of various 5G communication technologies provided with the high data rate. Wireless services, despite broad popularity, find it challenging to shield transmitted signals from eavesdroppers and are vulnerable to being overheard on the communication link. Therefore, users’ privacy concerns and information security issues have received more and more considerable attention (see, e.g., [1,2,3,4,5], and the references therein).
In the realm of traditional wireless information security, encryption-based approaches such as symmetric key schemes (see, e.g., [6,7]) and public key schemes (see, e.g., [8,9,10,11]) at higher protocol layers are entrusted to improve the security of wireless networks. With the drastically increasing computation capability of an eavesdropper and the discovery of some encryption cracking algorithms, the basic assumption of “security based on computational complexity” is seriously challenged.
Toward this end, physical layer security has arisen as a novel and attractive alternative in wireless communications. The theoretical foundation for physical layer security techniques has been provided in [12,13,14,15]. A network, including a legitimate transmitter (LT), a legitimate receiver (LR) and a passive eavesdropper (PE), was referred to as the wiretap channel introduced by Wyner in [13]. The associated notion of secrecy rate was developed to characterize the achievable transmission rate at which one LT could reliably send a secret message to one LR while keeping one PE unable to obtain any information. Based on these works, various advanced techniques, such as beamforming, precoding, power allocation, and artificial noise design, have been developed to achieve the secrecy rate in multiple-input-multiple-output (MIMO) orthogonal frequency-division multiplexing (OFDM) systems (see, e.g., [16,17,18,19]). References [20,21,22] showed that the secrecy rate could be improved significantly via appropriate subcarrier (SC) assignment and power allocation in the multiuser wiretap OFDM channels.
As a quite efficient technique to improve physical layer security, artificial noise (AN), which is generated in the transmit design, was proposed to degrade eavesdroppers’ receptions. The original AN scheme in [19] was presented for multiple-antenna transmission. Then, spatial AN [23,24,25], temporal AN [26,27], and frequency-domain AN [28,29] were developed to maximize the secrecy rate in the wiretap channel. Recently, a huge body of literature has been based on real interference alignment with non-Gaussian inputs. It turns out that interference alignment proposed in [30] plays a central role in achieving the optimal secure degrees of freedom (d.o.f.) and is an alternative but insightful technology for both Gaussian inputs and a discrete constellation. However, existing results for the multiuser wiretap OFDM channels focus on a simple scenario where the transmitter employs Gaussian distribution inputs. Moreover, Gaussian symbols are not realizable in practice because of the arbitrarily large peak transmit power and the infinite detection complexities. Thus, communication signals are likely to be finite alphabet symbols. This limitation reveals that the achievable secrecy rate for discrete inputs would significantly differ from that under the Gaussian input assumption (see, e.g., [31,32,33,34]). In [29], the sum secrecy rate for the random Gaussian codebook is optimized for the frequency-domain AN-aided multiuser OFDM systems, while the signals under finite-alphabet constellations constraint are not considered. Therefore, it is of importance to investigate the effect of arbitrary input distribution on the sum secrecy rate in multiuser wiretap OFDM channels.
In this paper, inspired by the reasons mentioned above, we consider the optimal resource allocation with discrete channel inputs in the AN-aided multiuser wiretap OFDM channels, as shown in Figure 1. Different from the Gaussian inputs [29], we develop a frequency-domain AN methodology with finite-alphabet symbols to jointly optimize the SC allocation and the power allocation of information signals and AN signals. Exploiting the transmission diversity provided by the frequency-domain AN addition and removal method, we aim at generating independent AN on each SC at the LT and canceling it at each LR such that only the PE is degraded. We make the assumption that the LT has public knowledge of instantaneous channel state information (CSI) associated with multiple LRs and the PE. This assumption may be valid in certain scenarios where the LRs and the PE are peer nodes in the system. The formulated problem can be treated as a mixed integer programming problem, which is non-convex. To cope with this question, we develop a joint design algorithm for information power, AN power, and SC allocation based on the Lagrange dual method. In the case of discrete finite-alphabet inputs, numerical results are presented to show that the proposed method can boost the secrecy rate considerably.
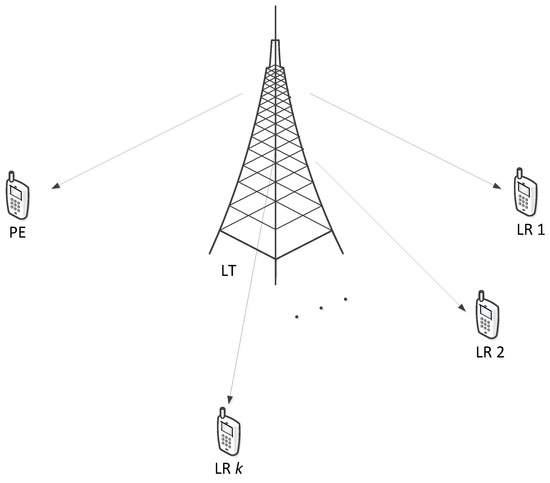
Figure 1.
Illustration of a multiuser wiretap orthogonal frequency-division multiplexing (OFDM) system, including one legitimate transmitter (LT), K legitimate receivers (LRs) and one passive eavesdropper (PE).
The rest of this paper is organized as follows. In Section 2, we establish the system model with finite-alphabet input constraints in the frequency-domain AN-aided multiuser wiretap OFDM channels and then formulate the optimization problem on the sum secrecy rate considered in this paper. In Section 3, a resource allocation algorithm for discrete inputs based on the Lagrange duality method is presented to tackle the optimization problem. Section 4 illustrates simulation results to demonstrate the performance of proposed algorithms. Finally, we draw the conclusion in Section 5.
We use bold lowercase letters and uppercase letters to denote vectors and matrices, respectively. represents the set of complex numbers. denotes that x is a complex Gaussian random variable with zero mean and variance . denotes the mutual information between random variables x and y. is defined as , and denotes the first derivative of at the point .
2. System Model and Problem Formulation
In this paper, we consider a frequency-domain AN-aided multiuser OFDM system with N SCs for finite-alphabet constellations in the wiretap channels, as illustrated in Figure 1. The system consists of one LT, K LRs and one PE, all with a single transmit antenna. We denote the sets of SCs and multiple users as and , respectively. It is assumed that the LT perfectly knows the CSIs on SC of the LRs as well as the PE. This is practically valid in scenarios where the eavesdropper cooperates with its peer nodes at some time but is not trusted by the legitimate nodes during a certain time. In this situation, the CSI of the eavesdropper can be obtained by monitoring the possible transmission activities of the eavesdropper (see, e.g., [29,35] and the references therein for identical assumptions). We denote and as the frequency channel coefficients over SC i from the LT to the LR k and the PE, respectively. Since the redundancy is provided by the asymmetry between the filter shapes for the LT and the LR, we further consider the time slotted OFDM symbols by assuming that the wireless channel remains constant over each time slot, but can vary from one-time slot to another.
In this system, one LT sends confidential information to K LRs in the presence of one PE. As a control center, the LT performs the SC allocation and then notifies all LRs of the corresponding SCs for them by signals. We denote as the SC assignment indicator for the LR k over the SC i, which means when the LR k can communicate on the SC i, while , otherwise. Herein, any SC only can be assigned to at most one LR, i.e., .
To degrade the channel performance at the PE against its eavesdropping, the LT adds AN signals to the transmit signals. We adopt the “key” distribution method for generating and removing AN in the frequency domain with practical complexity, as shown in Figure 2 (see, e.g., [28,29,36,37,38] and the references therein for the similar setting). By leveraging the independence and short-term reciprocity of the wireless channels, the LT sends the corresponding keys with the secret method (see [39] for more details) at each time. This novel frequency domain AN scheme differs from the traditional AN in the frequency domain, which cannot improve the secrecy rate of single-antenna wiretap channels (see, e.g., [26,29] and the references therein for the proof). With the distribution method, the key is secretly sent without being wiretapped by the PE. Accordingly, the PE does not have the ability to cancel AN used at each SC, but the LR does.
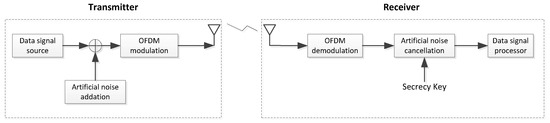
Figure 2.
Block diagram of an OFDM transmitter and receiver with artificial noise (AN) addition and cancellation procedure in a wiretap channel.
As the sum of a confidential information signal and an AN signal , the transmitted signal from the LT to the LR k over the SC i is expressed by
where and denote the corresponding transmit power of and , respectively. It is apparent that when . Then we assume that and denote a complex discrete random variable and a complex Gaussian random variable with zero mean and unit variance, which are also statistically independent across the SC, respectively.
Then, following the system block diagram in Figure 2, the corresponding signals received by the LR k and the PE (which is wiretapping all the LRs) over the SC i can be expressed as
where and denote zero-mean independently and identically distributed (i.i.d.) Additive White Gaussian Noise (AWGN) samples with variance and , respectively. Without loss of generality, it is assumed that .
Based on the above AN design scheme, the AN can be removed at the LR k over each SC before decoding the confidential information signal , but not possibly at the PE. Then, after the AN removal, the received signals of the LR k and the PE over SC i can be equivalently written by
According to [16], the achievable secrecy rate of the LR k associated with the signal model in Equations (4) and (5) can be obtained as
with .
Under the transmit power constraint, the sum secrecy rate optimization problem can be formulated as
where is denoted as the sum secrecy rate, is denoted as the power allocation of information signal, is denoted as the SC allocation for LRs, is denoted as the power allocation of AN signal, and P in Equation (7b) is the achievable maximal transmit power.
3. Optimal Solution
Note that the optimization Equation (7) is a mixed integer programming and thus is non-convex, which is difficult to tackle. In order to reduce the complexity of solving the Equation (7), we adopt the suboptimal SC allocation scheme in [22] is given by
Then, considering the above SC allocation, we can recast the optimization problem in Equation (7) as
where is given by Equation (8).
Herein, we consider the Lagrange duality method to tackle the problem in Equation (9) asymptotically optimally. Using the result in [40,41], we can obtain that the duality gap becomes zero in the order of for OFDM-based power allocation Equation (9) as N goes to infinity, due to the mild condition that the channel has a finite delay spread. The partial Lagrange of the Equation (9) is formulated by
where is the Lagrange multiplier associated with Equation (9b).
The dual problem is given by
where denotes the optimal dual objective value and the dual function for the Equation (9) is expressed as
Notice that is a convex function in [42] and its subgradient
where and are the optimal solutions to Equation (9) for fixed . We can update efficiently the dual variable with bisection method and the associated solution in Equation (12) with the obtained primal solution, respectively.
Then, we can observe that the maximization in Equation (12) can be decomposed into N independent subproblems, rewritten as
where is obtained by
According to the constraint in Equation (7f), for fixed i, only one term among is non-zero. Therefore, we can simplify the solution of the problem in Equation (15).
In what follows, since the objective function of the Equation (15) is not concave in , we exploit the coordinate descent method [43] to tackle the Equation (15). In particular, we obtain the maximization in Equation (15) with respect to (w.r.t.) for given and that w.r.t. for given. We present the details as follows.
3.1. Update of with Given
With given, the optimal of the Equation (15) can be obtained via simple line search [42], expressed by
3.2. Update of with Given
Next, we consider the optimization of Equation (15) for a given . Since the solution obtained by Equation (16) ensures the term is nonnegative, it is easy to verify that the optimization problem in Equation (15) is equivalent to
where
Now we adopt a successive convex approximation (SCA) method where the original problem is converted into a sequence of semi-definite program (SDP) problems. The SCA method ensures the stability and the guarantee of the convergence.
Let such that , then the first derivative of w.r.t. is expressed as [44]
Using the expression in Equation (19), we can obtain the first-order approximation to at the point :
with and denoting the one solved in the previous iteration. Therefore, Equation (17) can be reformulated with the above first-order approximation:
Furthermore, we show that the approximated Equation (21) can be treated as a convex SDP. Omitting all the terms not depending on and , Equation (21) can be equivalently cast as
Considering nonnegative MMSE, we can recast the problem in Equation (22) as
According to Shur complement [42], Equation (23) can be rewritten by
It is easy to verify that we apply convex solvers (e.g., CVX [45]) to solve Equation (24) which is a standard SDP.
We prove the convergence of the proposed SCA algorithm. Let in Equation (20) denote the first-order convex approximation of the function . As a consequence, we can obtain that
where Equation (25a) holds by substituting with in Equation (20), Equation (25b) is due to the optimality of at the next iteration, and Equation (25c) is due to the concavity of w.r.t. [46]. Hence, according to [47], the proposed SCA algorithm will converge to a point leading to a locally optimal solution of Equation (17), which satisfies KKT conditions of the original Equation (17). Finally, Algorithm 1 summarizes the joint power allocation algorithm of artificial noise and information signals for solving Equation (9) based on the Lagrange dual method and the SCA algorithm is summarized in step 2.2 of the Algorithm 1.
| Algorithm 1: Joint power allocation of artificial noise and information signals for solving Equation (9). |
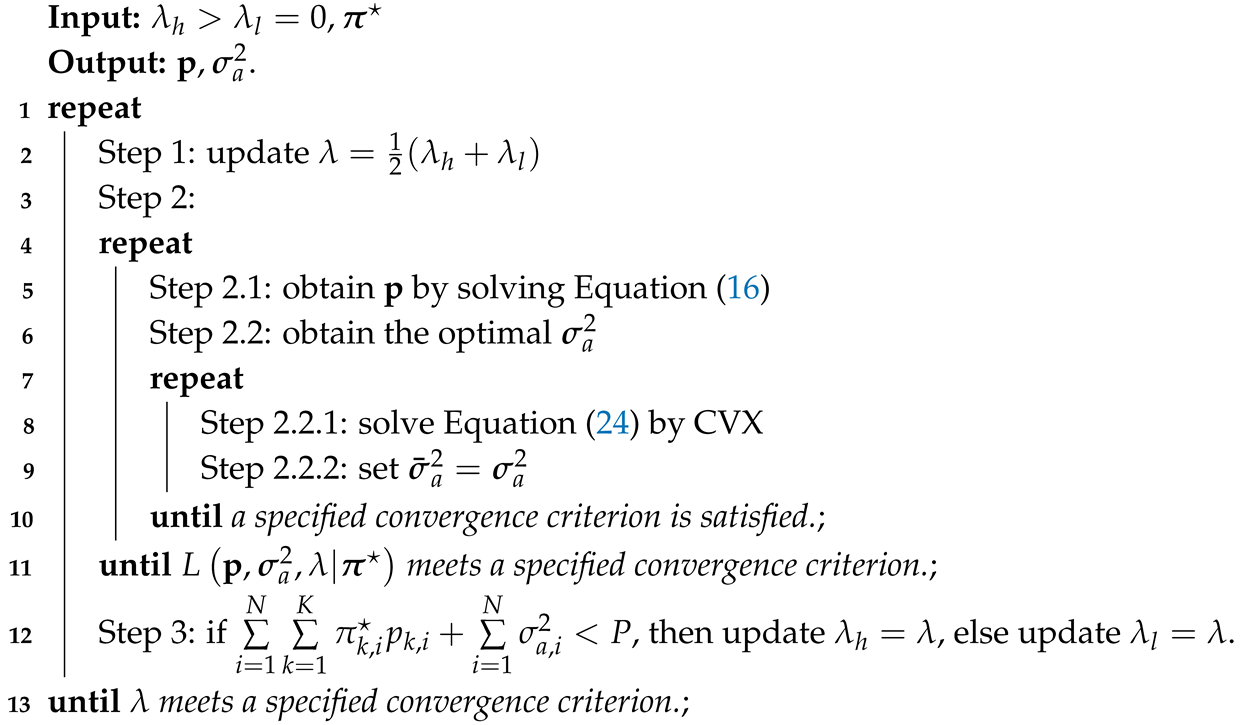 |
3.3. Computational Complexity Analysis
In this subsection, we analyze the computational complexity of the proposed algorithm. The computational complexity of the proposed depends on the number of iterations and the complexity involved at each iteration. Precisely, in every iteration, the computational complexity is mainly due to Equation (24). In addition, the optimization of through solving the SDP in Equation (24) requires operations [48].
4. Numerical Results
In this section, we provide some numerical results to demonstrate the efficacy of our proposed algorithm, including the effects of AN and the multiuser diversity. Then, we consider that the OFDM system has SCs with both Gaussian (denoted by “Gau”) and Quadrature Phase Shift Keying (QPSK) inputs. In the simulation setup, the channel coefficients only consist of small-scale fading, which is modeled as Rayleigh fading. Each channel realization is assumed to be composed of 8 i.i.d. Rayleigh fading paths with the maximum time delay of 7 samples and the unit channel power. The numerical results are averaged over 50 channel realizations for each simulation point, with SNR = P in which artificial noise power is included in the total transmit power P. Finally, all the numerical results are performed on a standard PC with CPU CoRe i7-770 3.6 GHz and 16 GB memory.
First, we analyze the convergence of the proposed algorithm and compare it with the upper bound, which is obtained by the classical water-filling [49] under the transmission without PE. From Figure 3, the result shows a monotonically increasing behavior of the devised algorithm with increasing number of iterations. Meanwhile, the sum secrecy rate of the proposed algorithm is about 0.52 away from the upper bound. This is because there are some LRs’ channels which are worse than the PE’s channels (i.e., ).
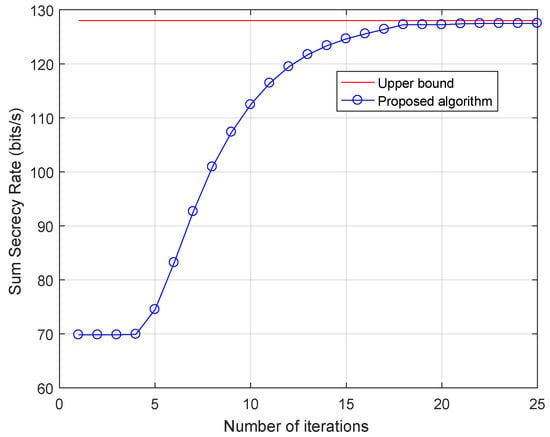
Figure 3.
The convergence of the proposed algorithm, .
Second, we analyze the sum secrecy rate performance for the proposed algorithm. The proposed suboptimal SC assignment in Equation (8) is compared with the fixed SC assignment, while the joint power allocation of artificial noise and data signals is optimized by Algorithm 1 for QPSK inputs (denoted by “QPSK, AN”). Moreover, we compare the proposed algorithm with Algorithm 2 in [22] for Gaussian inputs (denoted by “Gau, AN”). For performance comparison, we also consider the transmissions without PE (denoted by “QPSK, no PE” for QPSK inputs and “Gau, no PE” for Gaussian) which is the upper bound obtained by the classical water-filling [49] and without using AN which can be easily obtained by in Step 2.2 of the Algorithm 1 for discrete inputs (denoted by “QPSK, no AN”) and by of the Algorithm 2 in [22] for Gaussian inputs (denoted by “Gau, no AN”), as benchmarks, respectively.
Figure 4 illustrates the sum secrecy rate of various LRs’ number versus the SNR for QPSK and Gaussian inputs obtained by the different algorithms in the case of suboptimal SC assignment scheme. As expected, Figure 4a depicts that compared to Gaussian inputs, discrete inputs for current practical systems suffer a significant loss in secrecy performance. Then, Figure 4b shows the zoomed version associated with Figure 4a for only QPSK inputs. As shown in Figure 4b, we can observe a monotonically increasing sum secrecy rate of the proposed algorithm with SNR increasing. Furthermore, at all the SNR region, the sum secrecy rate of 10 LRs is among the best, better than that of 4 LRs, significantly outperforming that of 2 LRs. In addition, for 2 LRs, 4 LRs, and 10 LRs, the amount of performance difference between “QPSK, no PE” and “QPSK, AN” have almost identical behavior as the sum secrecy rate. This is because that, the multiuser diversity, gained by suboptimal SC assignment scheme, makes the LRs’ channels better than the PE’s channels (i.e., ). In addition, the sum secrecy rate of 10 LRs almost reaches the performance of “no PE” in the high SNR area. Moreover, the performance of the devised Algorithm is expectantly better than that of the “no AN” algorithm, especially in high SNR regime. The reason for this is that the use of AN can degrade the CSI of the LT-PE link to improve LRs’ secrecy rates. These are also identical to the observations in [20,22]. Figure 4c presents the zoomed version of 10 LRs associated with Figure 4a for QPSK inputs and Gaussian inputs. It can be observed from this figure that the amount of performance difference between “no PE” and “AN” for Gaussian inputs saturates in the high SNR regime, but it tends to be smaller for QPSK inputs.
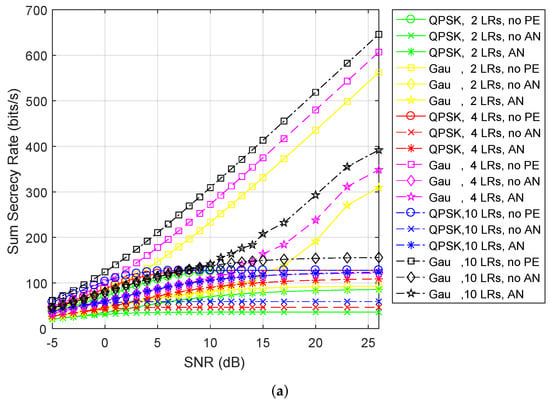
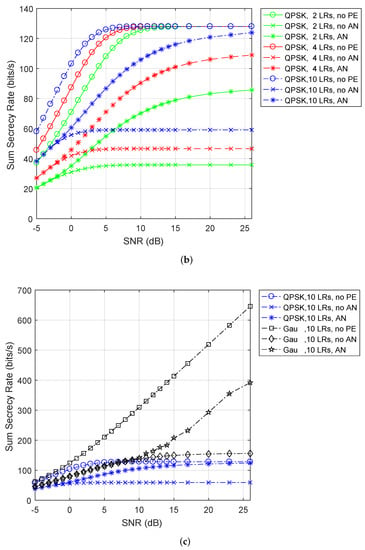
Figure 4.
(a) Sum secrecy rate for both Gaussian and Quadrature Phase Shift Keying (QPSK) inputs. (b) Sum secrecy rate of various LRs’ number for QPSK inputs. (c) Sum secrecy rate of 10 LRs for Gaussian and QPSK inputs. The SC assignment scheme in Equation (8).
Next, if we consider the fixed SC assignment, shown as in Figure 5, we can observe that the performance of sum secrecy rate corresponding to 2 LRs, 4 LRs and 10 LRs for various algorithms are almost identical, respectively. This also verifies the penalty for ignorance of the SC allocation can be quite large in practice.
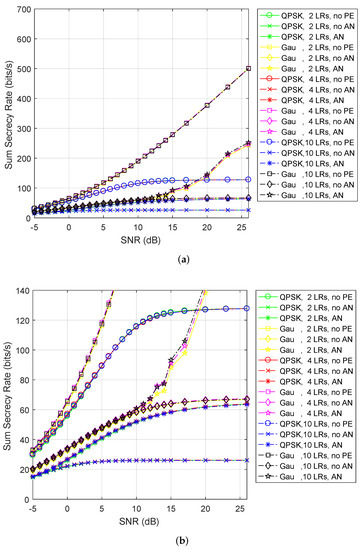
Figure 5.
(a) Sum secrecy rate for both Gaussian and QPSK inputs. (b) Low sum secrecy rate for both Gaussian and QPSK inputs. The fixed subcarrier (SC) assignment scheme.
Finally, Figure 6 further presents the power ratio of artificial noise calculated using the devised algorithm. Besides, the power ratio of artificial noise is denoted by
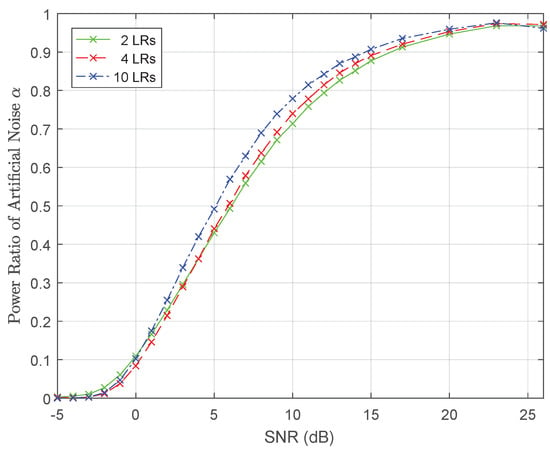
Figure 6.
The AN ratio in the total transmit power for Algorithm 1.
We can observe from this figure that, for any number of LRs, the power ratio allocated to artificial noise increases monotonically as SNR increases. The results indicate that the frequency-domain AN can degrade the performance of the PE.
5. Conclusions
In this paper, we investigate the multiuser wiretap OFDM channels with AN in the frequency domain under the discrete input constraints, which are deployed in current practical wireless systems. Within the generation and removal framework of the frequency-domain AN, we maximize the sum secrecy rate associated with all LRs for finite-alphabet inputs by jointly optimizing the SC allocation as well as the transmit power for information signals and AN signals over SCs. We have presented a Lagrange dual algorithm to tackle the non-convex joint optimization problem. Numerical results suggest that the proposed algorithm further improves the sum secrecy rate for finite-alphabet inputs, mainly due to the AN and multiuser diversity gain, especially in the high SNR region.
Author Contributions
Conceptualization, L.F., B.T., Q.J. and F.L.; Methodology, L.F. and B.T.; Software, L.F. and C.Y.; Validation, L.F. and C.Y.; Formal analysis, L.F. and C.Y.; Investigation, L.F., F.L. and C.Y.; Resources, B.T., Q.J. and F.L.; Data Curation, L.F. and F.L.; Writing—Original Draft Preparation, L.F. and B.T.; Writing—Review & Editing, L.F., B.T., Q.J., F.L. and C.Y.; Visualization, L.F. and B.T.; Supervision, B.T. and Q.J.; Project Administration, B.T. and Q.J.; Funding Acquisition, B.T.
Funding
This work was supported in part by the National Natural Science Foundation of China under Grant 61671453, in part by the Anhui Provincial Natural Science Foundation under Grant 1608085MF123, and in part by the Young Elite Scientist Sponsorship Program under Grant 17-JCJQ-QT-041.
Acknowledgments
L.F. would like to thank Haohao Qin in [20] for the helpful comments on their research stimulations. L.F. wishes to thank Xiang Chen in [22] for the valuable contact with Haohao Qin. L.F. also wants to thank Yongpeng Wu in [50] and Meng Zhang in [29] for pointing his attention to the works of Weiliang Zeng et al. [51] and the subgradient method, respectively.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Renna, F.; Laurenti, N.; Poor, H.V. Physical-Layer Secrecy for OFDM Transmissions Over Fading Channels. IEEE Trans. Inf. Forensic Secur. 2012, 7, 1354–1367. [Google Scholar] [CrossRef]
- Tsai, S.H.; Poor, H.V. Power Allocation for Artificial-Noise Secure MIMO Precoding Systems. IEEE Trans. Signal Process. 2014, 62, 3479–3493. [Google Scholar] [CrossRef]
- Jameel, F.; Wyne, S.; Kaddoum, G.; Duong, T.Q. A Comprehensive Survey on Cooperative Relaying and Jamming Strategies for Physical Layer Security. IEEE Commun. Surv. Tutor. 2018. [Google Scholar] [CrossRef]
- Jang, U.; Lim, H.; Kim, H. Privacy-Enhancing Security Protocol in LTE Initial Attack. Symmetry 2014, 6, 1011–1025. [Google Scholar] [CrossRef]
- Liu, Y.; Li, L.; Alexandropoulos, G.C.; Pesavento, M. Securing Relay Networks with Artificial Noise: An Error Performance-Based Approach. Entropy 2017, 19, 384. [Google Scholar] [CrossRef]
- Alvarez, R.; Andrade, A.; Zamora, A. Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption. Symmetry 2018, 10, 705. [Google Scholar] [CrossRef]
- Rajesh, S.; Paul, V.; Menon, V.G.; Khosravi, M.R. A Secure and Efficient Lightweight Symmetric Encryption Scheme for Transfer of Text Files between Embedded IoT Devices. Symmetry 2019, 11, 293. [Google Scholar] [CrossRef]
- Massey, J.L. An Introduction to Contemporary Cryptology. IEEE Proc. 1988, 76, 533–549. [Google Scholar] [CrossRef]
- Wallace, J.W.; Sharma, R.K. Automatic Secret Keys From Reciprocal MIMO Wireless Channels: Measurement and Analysis. IEEE Trans. Inf. Forensic Secur. 2010, 5, 381–392. [Google Scholar] [CrossRef]
- Fan, C.I.; Tseng, Y.F. Anonymous Multi-Receiver Identity-Based Authenticated Encryption with CCA Security. Symmetry 2015, 7, 1856–1881. [Google Scholar] [CrossRef]
- Ahmad, M.; Al Solami, E.; Wang, X.Y.; Doja, M.N.; Beg, M.M.S.; Alzaidi, A.A. Cryptanalysis of an Image Encryption Algorithm Based on Combined Chaos for a BAN System, and Improved Scheme Using SHA-512 and Hyperchaos. Symmetry 2018, 10, 266. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication Theory of Secrecy Systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Leung-yan-cheong, S.K.; Hellman, M.E. The Gaussian wire-tap channel. IEEE Trans. Inf. Theory 1978, 24, 451–456. [Google Scholar] [CrossRef]
- Csiszar, I.; Korner, J. Broadcast channels with confidential messages. IEEE Trans. Inf. Theory 1978, 24, 339–348. [Google Scholar] [CrossRef]
- Li, Z.; Yates, R.; Trappe, W. Secrecy Capacity of Independent Parallel Channels. In Securing Wireless Communications at the Physical Layer; Springer: Boston, MA, USA, 2010; pp. 1–18. [Google Scholar]
- Khisti, A.; Wornell, G.W. Secure Transmission With Multiple Antennas I: The MISOME Wiretap Channel. IEEE Trans. Inf. Theory 2010, 56, 3088–3104. [Google Scholar] [CrossRef]
- Jorswieck, E.A.; Wolf, A. Resource allocation for the wire-tap multi-carrier broadcast channel. In Proceedings of the 2008 International Conference on Telecommunications, St. Petersburg, Russia, 16–19 June 2008; pp. 1–6. [Google Scholar] [CrossRef]
- Goel, S.; Negi, R. Guaranteeing secrecy using artificial noise. IEEE Trans. Wirel. Commun. 2008, 7, 2180–2189. [Google Scholar] [CrossRef]
- Qin, H.H.; Chen, X.; Zhong, X.F.; He, F.; Zhao, M.; Wang, J. Joint Power Allocation and Artificial Noise Design for Multiuser Wiretap OFDM Channels. In Proceedings of the 2013 IEEE International Conference on Communications, Budapest, Hungary, 9–13 June 2013. [Google Scholar] [CrossRef]
- Karachontzitis, S.; Timotheou, S.; Krikidis, I.; Berberidis, K. Security-Aware Max-Min Resource Allocation in Multiuser OFDMA Downlink. IEEE Trans. Inf. Forensic Secur. 2015, 10, 529–542. [Google Scholar] [CrossRef]
- Chen, X.; Qin, H.H.; Xiao, L.M. Joint Resource Allocation and Artificial Noise Design for Multiuser Wiretap OFDM Channels. J. Commun. Netw. 2017, 19, 451–460. [Google Scholar] [CrossRef]
- Zhou, X.Y.; McKay, M.R. Secure Transmission with Artificial Noise over Fading Channels: Achievable Rate and Optimal Power Allocation. IEEE Trans. Veh. Technol. 2010, 59, 3831–3842. [Google Scholar] [CrossRef]
- Li, Q.; Ma, W.K. Optimal and Robust Transmit Designs for MISO Channel Secrecy by Semidefinite Programming. IEEE Trans. Signal Process. 2011, 59, 3799–3812. [Google Scholar] [CrossRef]
- Liao, W.C.; Chang, T.H.; Ma, W.K.; Chi, C.Y. QoS-Based Transmit Beamforming in the Presence of Eavesdroppers: An Optimized Artificial-Noise-Aided Approach. IEEE Trans. Signal Process. 2011, 59, 1202–1216. [Google Scholar] [CrossRef]
- Qin, H.H.; Sun, Y.; Chang, T.H.; Chen, X.; Chi, C.Y.; Zhao, M.; Wang, J. Power Allocation and Time-Domain Artificial Noise Design for Wiretap OFDM with Discrete Inputs. IEEE Trans. Wirel. Commun. 2013, 12, 2717–2729. [Google Scholar] [CrossRef]
- Cheng, D.H.; Gao, Z.Z.; Liu, F.; Liao, X.W. A General Time-domain Artificial Noise Design for OFDM AF Relay Systems. In Proceedings of the 2015 IEEE/CIC International Conference on Communications, Shenzhen, China, 2–4 November 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Xing, H.; Liu, L.; Zhang, R. Secrecy Wireless Information and Power Transfer in Fading Wiretap Channel. IEEE Trans. Veh. Technol. 2016, 65, 180–190. [Google Scholar] [CrossRef]
- Zhang, M.; Liu, Y.; Zhang, R. Artificial Noise Aided Secrecy Information and Power Transfer in OFDMA Systems. IEEE Trans. Wirel. Commun. 2016, 15, 3085–3096. [Google Scholar] [CrossRef]
- Motahari, A.S.; Oveis-Gharan, S.; Maddah-Ali, M.A.; Khandani, A.K. Real Interference Alignment: Exploiting the Potential of Single Antenna Systems. IEEE Trans. Inf. Theory 2014, 60, 4799–4810. [Google Scholar] [CrossRef]
- Xiao, C.S.; Zheng, Y.R.; Ding, Z. Globally Optimal Linear Precoders for Finite Alphabet Signals Over Complex Vector Gaussian Channels. IEEE Trans. Signal Process. 2011, 59, 3301–3314. [Google Scholar] [CrossRef]
- Atallah, M.; Kaddoum, G. Secrecy Analysis in Wireless Network with Passive Eavesdroppers by Using Partial Cooperation. IEEE Trans. Veh. Technol. 2019. [Google Scholar] [CrossRef]
- Vuppala, S.; Tolossa, Y.J.; Kaddoum, G.; Abreu, G. On the Physical Layer Security Analysis of Hybrid Millimeter Wave Networks. IEEE Trans. Commun. 2018, 66, 1139–1152. [Google Scholar] [CrossRef]
- Fan, L.H.; Tang, B.; Huang, Z.R.; Jiang, Q.X. Designing Constant-Envelope Transmissions for Secret Communications in MISO Wiretap Channels. IEEE Access 2019, 7, 17791–17797. [Google Scholar] [CrossRef]
- Li, L.X.; Chen, Z.; Petropulu, A.P.; Fang, J. Linear Precoder Design for an MIMO Gaussian Wiretap Channel with Full-Duplex Source and Destination Nodes. IEEE Trans. Inf. Forensic Secur. 2018, 13, 421–436. [Google Scholar] [CrossRef]
- Al-Talabani, A.; Deng, Y.S.; Nallanathan, A.; Nguyen, H.X. Enhancing Secrecy Rate in Cognitive Radio Networks via Stackelberg Game. IEEE Trans. Commun. 2016, 64, 4764–4775. [Google Scholar] [CrossRef]
- Xu, D.; Li, Q. Improving physical-layer security for primary users in cognitive radio networks. IET Commun. 2017, 11, 2303–2310. [Google Scholar] [CrossRef]
- Moon, J.; Lee, H.; Song, C.; Lee, S.; Lee, I. Proactive Eavesdropping With Full-Duplex Relay and Cooperative Jamming. IEEE Trans. Wirel. Commun. 2018, 17, 6707–6719. [Google Scholar] [CrossRef]
- Koorapaty, H.; Hassan, A.A.; Chennakeshu, S. Secure information transmission for mobile radio. IEEE Commun. Lett. 2000, 4, 52–55. [Google Scholar] [CrossRef]
- Seong, K.; Mohseni, M.; Cioffi, J.M. Optimal Resource Allocation for OFDMA Downlink Systems. In Proceedings of the 2006 IEEE International Symposium on Information Theory, Seattle, WA, USA, 9–14 July 2006; pp. 1394–1398. [Google Scholar] [CrossRef]
- Yu, W.; Lui, R. Dual methods for nonconvex spectrum optimization of multicarrier systems. IEEE Trans. Commun. 2006, 54, 1310–1322. [Google Scholar] [CrossRef]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: New York, NY, USA, 2013. [Google Scholar]
- Bertsekas, D. Nonlinear Programming; Athena Scientific: Belmont, MA, USA, 1999. [Google Scholar]
- Guo, D.N.; Shamai, S.; Verdu, S. Mutual information and minimum mean-square error in Gaussian channels. IEEE Trans. Inf. Theory 2005, 51, 1261–1282. [Google Scholar] [CrossRef]
- Grant, M.; Boyd, S. CVX: Matlab Software for Disciplined Convex Programming. 2017. Available online: https://cvxr.com/cvx (accessed on 27 May 2019).
- Guo, D.N.; Wu, Y.H.; Shamai, S.; Verdu, S. Estimation in Gaussian Noise: Properties of the Minimum Mean-Square Error. IEEE Trans. Inf. Theory 2011, 57, 2371–2385. [Google Scholar] [CrossRef]
- Marks, B.R.; Wright, G.P. A general inner approximation algorithm for nonconvex mathematical programs. Oper. Res. 1978, 26, 681–683. [Google Scholar] [CrossRef]
- Luo, Z.Q.; Ma, W.K.; So, A.M.C.; Ye, Y.Y.; Zhang, S.Z. Semidefinite Relaxation of Quadratic Optimization Problems. IEEE Signal Process. Mag. 2010, 27, 20–34. [Google Scholar] [CrossRef]
- Lozano, A.; Tulino, A.M.; Verdu, S. Optimum power allocation for parallel Gaussian channels with arbitrary input distributions. IEEE Trans. Inf. Theory 2006, 52, 3033–3051. [Google Scholar] [CrossRef]
- Wu, Y.; Ng, D.W.K.; Wen, C.K.; Schober, R.; Lozano, A. Low-Complexity MIMO Precoding for Finite-Alphabet Signals. IEEE Trans. Wirel. Commun. 2017, 16, 4571–4584. [Google Scholar] [CrossRef]
- Zeng, W.L.; Xiao, C.S.; Wang, M.X.; Lu, J.H. Linear Precoding for Finite-Alphabet Inputs Over MIMO Fading Channels With Statistical CSI. IEEE Trans. Signal Process. 2012, 60, 3134–3148. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).