An Efficient Essential Secret Image Sharing Scheme Using Derivative Polynomial
Abstract
1. Introduction
- (1)
- Same-sized shadows.
- (2)
- Smaller-sized shadows.
- (3)
- Effectiveness.
2. Preliminaries
2.1. Secret Image Sharing Scheme
2.1.1. Sharing Phase
2.1.2. Recovery Phase
2.2. Essential Secret Image Sharing Scheme
2.2.1. Sharing Phase
2.2.2. Recovery Phase
3. Review and Analysis of Li et al.’s Scheme
3.1. Review Li et al.’s Scheme
3.1.1. Sharing Phase
| Algorithm 1 Sharing phase of Li et al.’s scheme |
| Input: A secret image and a pair of the parameter. Output: shadows: , , …, are essential shadows; , , …, are non-essential shadows. |
| (A1-1): Permute to by ; /*: a reversible permutation operation */ (A1-2): Generate the intermediate shadows , , …, , by applying -SIS scheme on ; (A1-3): Compute the mask shadow , where denotes the bit-wise XOR operation; (A1-4): Generate essential shadows , , …, and non-essential shadows , , …, ; |
3.1.2. Recovery Phase
| Algorithm 2 Recovery phase of the Li et al.’s scheme |
| Input: essential shadows and any non-essential shadows. /* say essential shadows are , , …, and non-essential shadows are , , …, */ Output: The secret image . |
| (A2-1): Collect essential shadows to compute the mask shadow ; (A2-2): Compute intermediate shadows , , …, , as: , , …, and , …, ; (A2-3): Since there are , , …, , the permuted image can be obtained by employing Lagrange’s interpolation; (A2-4): Acquire the secret image by ; the corresponding inverse-permutation of |
3.2. Analysis Li et al.’s Scheme
4. The Proposed Scheme
4.1. Sharing Phase
| Algorithm 3 Sharing phase of the proposed scheme |
| Input: A secret image and a pair of the parameters . Output: shadows: , , …, are essential shadows; , , …, are non-essential shadows. |
| (A3-1): Obtain the permuted image by ; (A3-2): Generate the intermediate shadows by applying -SIS scheme on ; (A3-3): Construct the function , and the outputs are essential shadows, where ; (A3-4): Calculate -th derivative of to obtain , and the outputs are non-essential shadows, where ; |
4.2. Recovery Phase
| Algorithm 4 Recovery phase of the proposed scheme |
| Input: Any at least shadows and no less than essential shadows included. Output: The secret image . |
| (A4-1): The function can be reconstructed by any involved shadows including at least essential shadows; (A4-2): The intermediate shadows , , …, can be reconstructed by the function ; (A4-3): The permuted secret image can be reconstructed by , , …, ; (A4-4): Acquire the original secret image by ; |
5. Analysis
5.1. The Security Analysis
- (1)
- Threshold condition: .
- (2)
- Essentiality condition: .
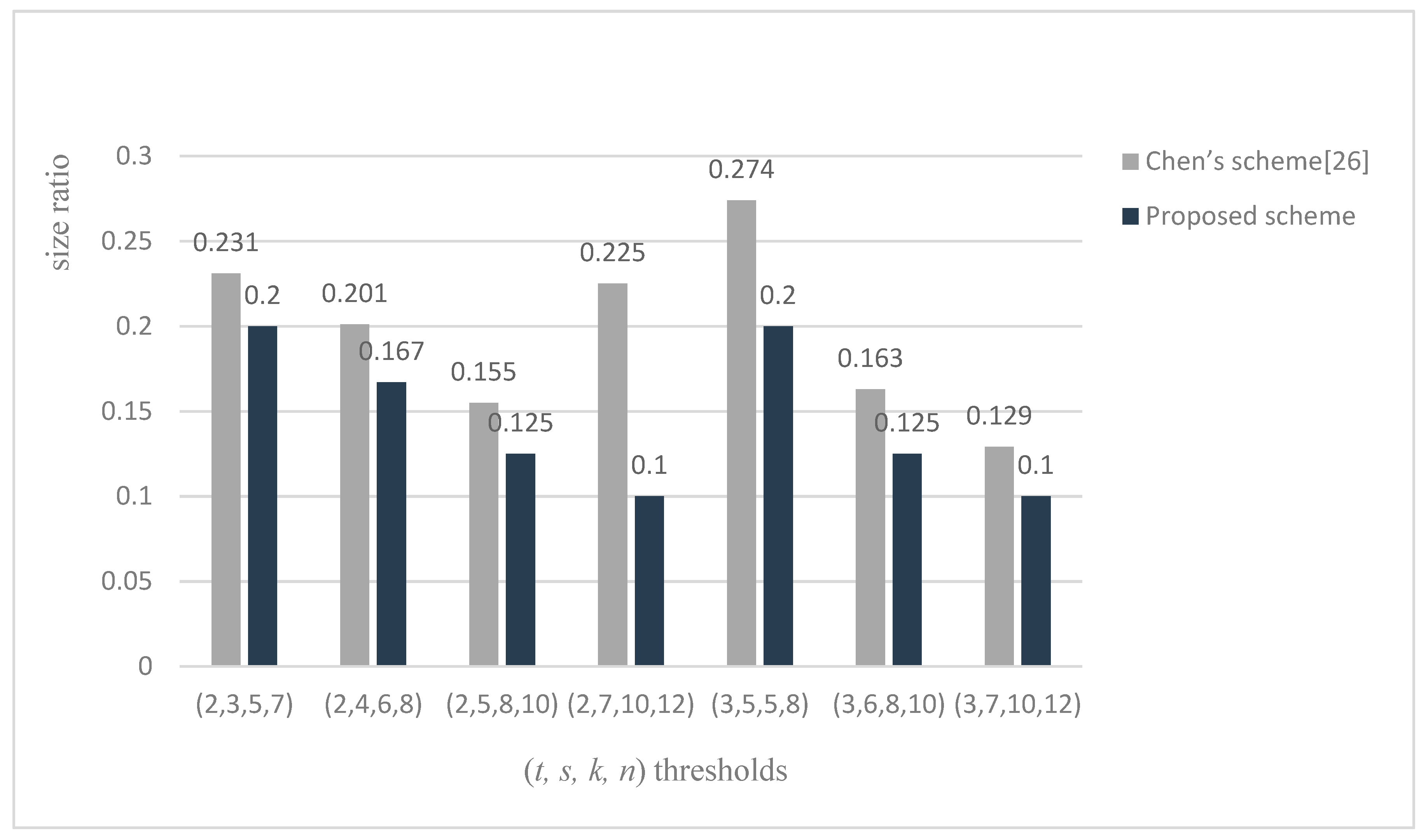
5.2. The Analysis of Shadow Size Ratio
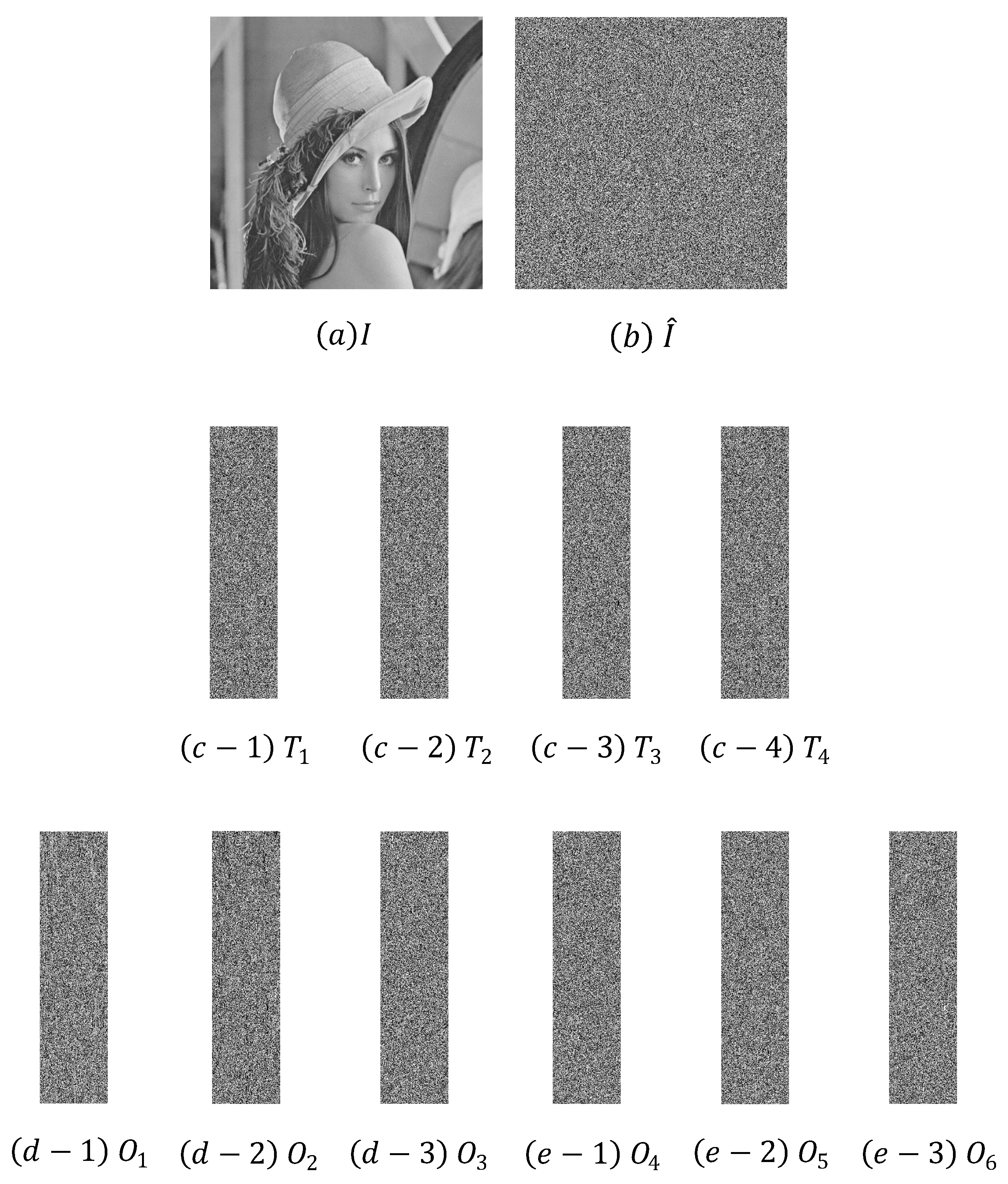
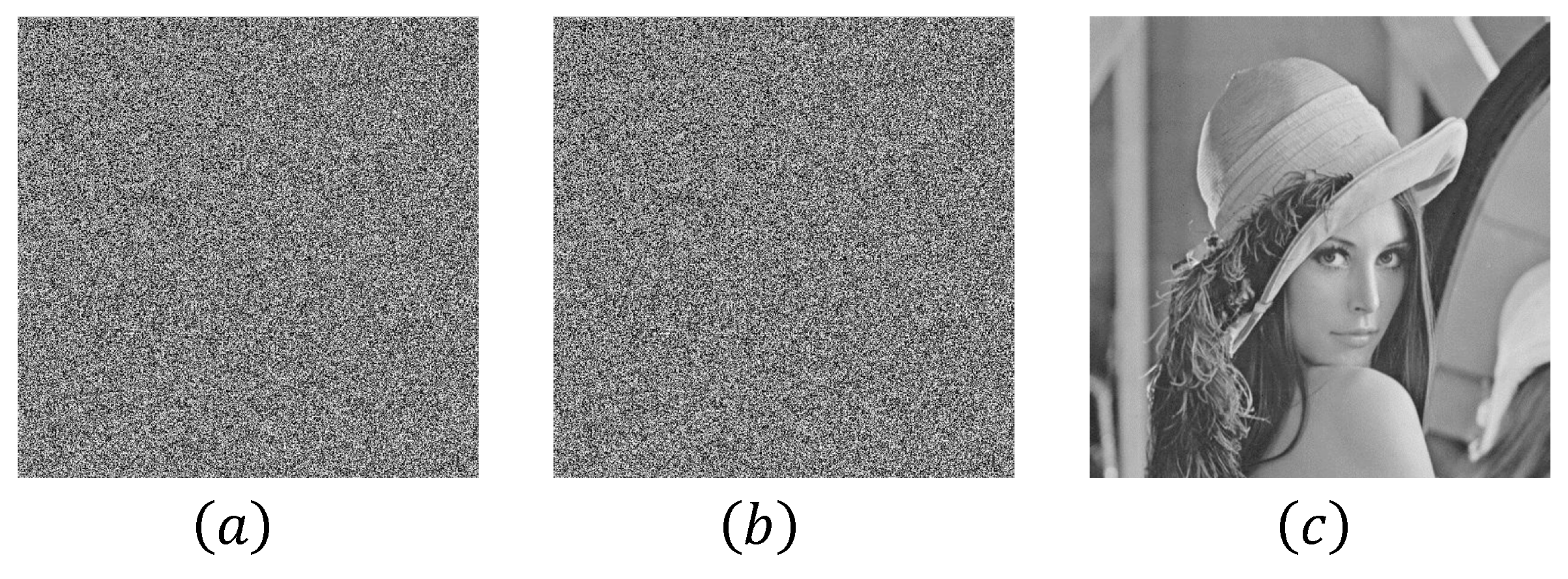
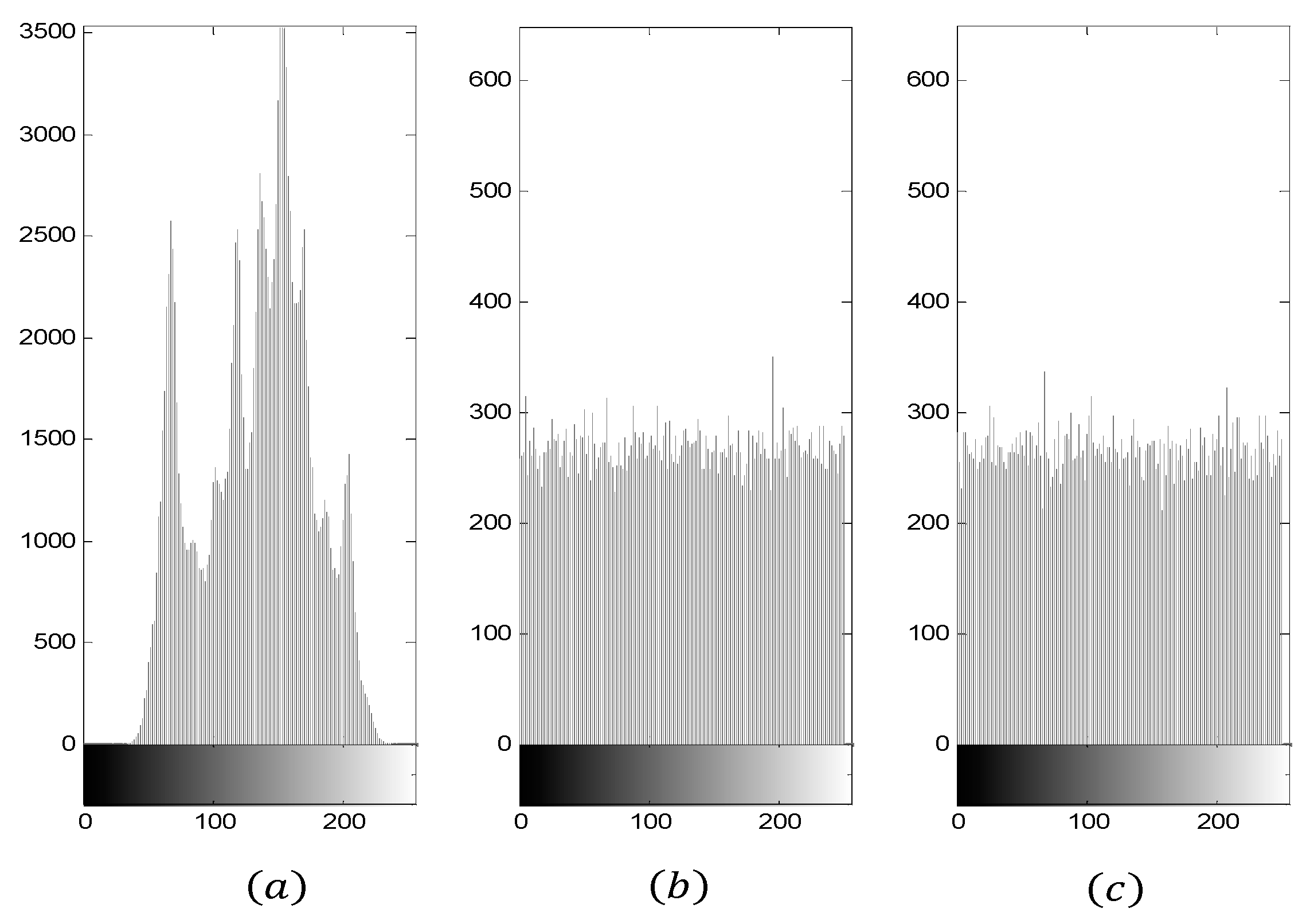
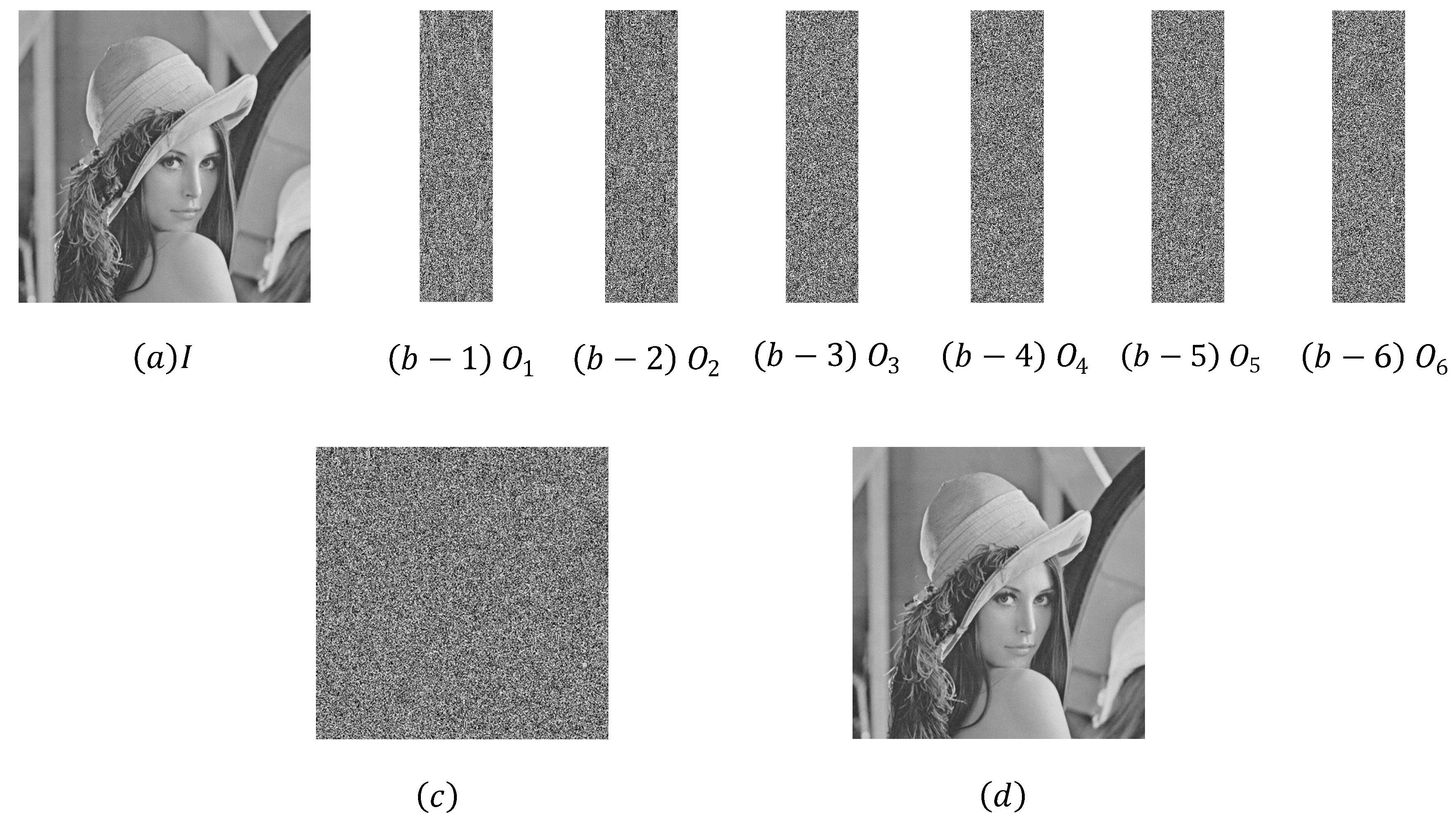
6. Simulation Results and Comparison
6.1. Simulation Results
6.2. Comparison
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Liu, Y.; Guo, W.; Fan, C.I.; Chang, L.; Cheng, C. A practical privacy-preserving data aggregation (3PDA) scheme for smart grid. IEEE Trans. Ind. Inform. 2018. [Google Scholar] [CrossRef]
- Liu, Y.N.; Wang, Y.P.; Wang, X.F.; Xia, Z.; Xu, J.F. Privacy-preserving raw data collection without a trusted authority for IoT. Comput. Netw. 2018. [Google Scholar] [CrossRef]
- Jia, X.; Wang, D.; Nie, D.; Luo, X.; Sun, J.Z. A new threshold changeable secret sharing scheme based on the Chinese Remainder Theorem. Inf. Sci. 2019, 473, 13–30. [Google Scholar] [CrossRef]
- Thien, C.C.; Lin, J.C. Secret image sharing. Comput. Gr. 2002, 26, 765–770. [Google Scholar] [CrossRef]
- Wu, K.S. A secret image sharing scheme for light images. EURASIP J. Adv. Signal Process. 2013, 2013, 49. [Google Scholar] [CrossRef]
- Kanso, A.; Ghebleh, M. An efficient (t, n)–threshold secret image sharing scheme. Multimed. Tools Appl. 2017, 76, 16369–16388. [Google Scholar] [CrossRef]
- Liu, Y.N.; Zhong, Q.; Shen, J.; Chang, C.-C. A novel image protection scheme using bit-plane compression and secret sharing. J. Chin. Inst. Eng. 2017, 40, 161–169. [Google Scholar] [CrossRef]
- Liu, Y.N.; Zhong, Q.; Xie, M.; Chen, Z.-B. A novel multiple-level secret image sharing scheme. Multimed. Tools Appl. 2018, 77, 6017–6031. [Google Scholar] [CrossRef]
- Liu, Y.N.; Wu, Z. An improved threshold multi-level image recovery scheme. J. Inf. Secur. Appl. 2018, 40, 166–172. [Google Scholar] [CrossRef]
- Jia, X.; Wang, D.; Chu, Q.; Chen, Z. An efficient XOR-based verifiable visual cryptographic scheme. Multimed. Tools Appl. 2018, 1–17. [Google Scholar] [CrossRef]
- Jia, X.; Wang, D.; Nie, D.; Zhang, C. Collaborative visual cryptography schemes. IEEE Trans. Circuits Syst. Video Technol. 2018, 28, 1056–1070. [Google Scholar] [CrossRef]
- Shyu, S.J.; Chuang, C.C.; Chen, Y.R.; Lai, A.F. Weighted threshold secret image sharing. In Proceedings of the Pacific-Rim Symposium on Image and Video Technology, Tokyo, Japan, 13–16 January 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 988–998. [Google Scholar]
- Chen, C.C.; Chen, C.C.; Lin, Y.C. Weighted modulated secret image sharing method. J. Electron. Imaging 2009, 18, 043011. [Google Scholar] [CrossRef]
- Li, M.; Ma, S.; Guo, C. A novel weighted threshold secret image sharing scheme. Secur. Commun. Netw. 2015, 8, 3083–3093. [Google Scholar] [CrossRef]
- Lin, S.J.; Chen LS, T.; Lin, J.C. Fast-weighted secret image sharing. Opt. Eng. 2009, 48, 077008. [Google Scholar] [CrossRef]
- Tassa, T. Hierarchical threshold secret sharing. J. Cryptol. 2007, 20, 237–264. [Google Scholar] [CrossRef]
- Guo, C.; Chang, C.C.; Qin, C. A hierarchical threshold secret image sharing. Pattern Recognit. Lett. 2012, 33, 83–91. [Google Scholar] [CrossRef]
- Pakniat, N.; Noroozi, M.; Eslami, Z. Secret image sharing scheme with hierarchical threshold access structure. J. Vis. Commun. Image Represent. 2014, 25, 1093–1101. [Google Scholar] [CrossRef]
- Li, P.; Yang, C.N.; Wu, C.C.; Kong, Q.; Ma, Y. Essential secret image sharing scheme with different importance of shadows. J. Vis. Commun. Image Represent. 2013, 24, 1106–1114. [Google Scholar] [CrossRef]
- Yang, C.N.; Li, P.; Wu, C.C.; Cai, S.R. Reducing shadow size in essential secret image sharing by conjunctive hierarchical approach. Signal Process. Image Commun. 2015, 31, 1–9. [Google Scholar] [CrossRef]
- Chen, S.K. Essential secret image sharing with increasable shadows. Opt. Eng. 2016, 55, 013103. [Google Scholar] [CrossRef]
- Chen, C.C.; Chen, S.C. Two-layered structure for optimally essential secret image sharing scheme. J. Vis. Commun. Image Represent. 2016, 38, 595–601. [Google Scholar] [CrossRef]
- Li, P.; Yang, C.N.; Zhou, Z. Essential secret image sharing scheme with the same size of shadows. Digit. Signal Process. 2016, 50, 51–60. [Google Scholar] [CrossRef]
- Chen, C.C.; Tsai, Y.H. An Expandable Essential Secret Image Sharing Structure. J. Inf. Hiding Multimed. Signal Process. 2016, 7, 135–144. [Google Scholar]
- Chen, C.C. Essential secret image sharing scheme with equal-sized shadows generation. J. Vis. Commun. Image Represent. 2018, 52, 143–150. [Google Scholar] [CrossRef]
- Li, P.; Liu, Z.; Yang, C.N. A construction method of (t, k, n)-essential secret image sharing scheme. Signal Process. Image Commun. 2018, 65, 210–220. [Google Scholar] [CrossRef]

| [21] | [23] | [24] | [25] | [26] | Proposed Scheme | |
|---|---|---|---|---|---|---|
| Same-size shadows | No | No | Yes | Yes | Yes | Yes |
| [24] | [25] | [26] | Proposed Scheme | |
|---|---|---|---|---|
| Essential shadow size ratio | ||||
| Non-essential shadow size ratio |
| [24] | [25] | [26] a | Proposed Scheme | ||
|---|---|---|---|---|---|
| Essential shadow size ratio | 0.5 | ||||
| Non-essential shadow size ratio | 0.5 | ||||
| Essential shadow size ratio | 0.333 | ||||
| Non-essential shadow size ratio | 0.333 | ||||
| Essential shadow size ratio | 0.2 | ||||
| Non-essential shadow size ratio | 0.2 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Z.; Liu, Y.-N.; Wang, D.; Yang, C.-N. An Efficient Essential Secret Image Sharing Scheme Using Derivative Polynomial. Symmetry 2019, 11, 69. https://doi.org/10.3390/sym11010069
Wu Z, Liu Y-N, Wang D, Yang C-N. An Efficient Essential Secret Image Sharing Scheme Using Derivative Polynomial. Symmetry. 2019; 11(1):69. https://doi.org/10.3390/sym11010069
Chicago/Turabian StyleWu, Zhen, Yi-Ning Liu, Dong Wang, and Ching-Nung Yang. 2019. "An Efficient Essential Secret Image Sharing Scheme Using Derivative Polynomial" Symmetry 11, no. 1: 69. https://doi.org/10.3390/sym11010069
APA StyleWu, Z., Liu, Y.-N., Wang, D., & Yang, C.-N. (2019). An Efficient Essential Secret Image Sharing Scheme Using Derivative Polynomial. Symmetry, 11(1), 69. https://doi.org/10.3390/sym11010069






