Abstract
In large-area wireless sensor networks with hierarchical cluster-based routing protocols, the average number of clusters, k, and the transmission range for the control messages, R, significantly affect the network lifespan. We analyze energy consumption in depth as a function of , taking into account the energy dissipation of cluster head nodes and the member nodes, separately. To achieve joint optimization of , we adopt derivative-free Nelder–Mead Simplex method. Computer simulations have shown that our approach effectively reduces energy consumption of sensor nodes in the process of clustering and data transmission in large-area sensor fields. Our optimization can be applied to existing cluster-based routing schemes to maximize their energy efficiency.
1. Introduction
Ad-hoc wireless sensor network (WSN) is a core technology of Internet of Things (IoT) with a wide range of applications including smart home networking and industrial internet of things (IIoT) [1,2]. In IoT environments, the WSNs have large area with many sensor nodes compared with conventional application specific sensor networks. We need more sophisticated energy-efficient routing protocols than conventional ones targeted for relatively small-area WSNs.
WSN is a collection of large numbers of sensor nodes deployed over a large area with a central base station (BS) that collects sensing data. Sensor nodes are characterized by limited sensing, computing and communication capabilities. Moreover, in WSN based IoT environments, several hundreds or thousands of sensor nodes are randomly deployed with limited battery power, which are difficult to be recharged. To overcome limitations from these characteristics, a great emphasis is placed on scalability and efficient energy consumption of WSN in every design aspects including routing protocols, network topology, security key management, etc.
Based on the deployment of nodes, routing protocols can be divided into two types: flat routing and hierarchical routing, which is also called cluster-based routing. In flat routing protocols, all sensor nodes play identical roles in conveying sensing data to the BS. Cluster-based or hierarchical routing protocols refer to routing protocols in which the nodes are grouped into clusters, where a cluster is composed of a cluster head (CH) and one or more member nodes. Cluster-based routing protocols take advantage of load balancing and reducing communication volume in a distributed manner to prolong the network lifespan of WSN. Low Energy Adaptive Clustering Hierarchy (LEACH) [3] is a most widely adopted cluster-based routing protocol for WSN, by virtue of its simplicity and energy efficiency as a fully decentralized scheme.
There has been a lot of research work related to energy consumption in cluster-based routing protocols. In single hop communication, the CH collects data from its member nodes and directly sends these data to the BS, as in LEACH [3]. If the network area is small, then the entire sensor field can be covered by the transmission range of any node in the field, and single hop protocols are advantageous due to minimum overhead and minimum delay. However, cluster-based routing protocols with single hop protocols [4,5,6,7,8,9] are not suitable for IoT environments based on large-area WNS, due to their short lifespan.
Multi-hop communication is more energy efficient approach to routing protocols for large-area sensor networks. In multi-hop cluster-based routing protocols, the CH sends its data via some intermediate nodes to the BS, if necessary. In LEACH-D protocol [10], connectivity density factor and energy factor are considered in computing the threshold value for the CH selection phase. Although it shows improvement in terms of scalability and energy consumption, it still has hotspot problem with difference in cluster sizes. This hotspot problem is addressed in FZ-LEACH protocol [11] to enhance the lifespan of the network. However, the main drawback of FZ-LEACH is non-optimality in the selection of zone heads. This drawback is improved in IFZ-LEACH [12], in which CH divides the sensor field intofar zone and non-far zone to select the zone head from the far zone based on maximum residual energy. However, it suffers from scalability and network complexity. In DL-LEACH [13], the network is divided into several layers and the nodes in lower layers make distance-base determine whether they are to transmit data via CHs or to send data to the BS directly. It has achieved a good improvement in energy consumption with moderate-size sensor networks. However, it suffers from short node lifespan in large-scale or large-area networks. In CL-LEACH [14], the node with residual energy greater than the threshold value performs the tasks of a relay node for multi-hop communication. Broken links are detected by route maintenance and substituted by some new paths in the existing route. The main drawbacks of this protocol are message overheads and complexity. In P-LEACH [15], a mobile base station (BS) is considered instead of a fixed BS. It uses a cluster-based prediction by activating a small number of nodes during the tracking of the mobile BS in the field, which is divided into three regions: partition cluster, communication quadrangle, and four-partition-cluster structure.
Aside from data routing protocol issues, the authors of [16] presented a survey on cluster-based group key agreement (GKA) protocols for WSN security issues, and assessed and measured the efficiency of each GKA protocol in terms of its energy consumption.
Cluster-based routing protocols divide the sensor nodes into an average of k clusters. In conventional WSN, we used the parameter k as a sub-optimized fixed value by rule of thumb, which worked well enough with small-area sensor networks. In large-area WSNs, k needs to be optimized with increased number of sensor nodes. Decentralized cluster-based routing protocols use control messages for cluster head advertisement, join request, message transmission scheduling, etc. In LEACH algorithm [17] and most of its variants, nodes send control messages with maximum power to reach the entire network to ensure that the messages can be received by nodes farthest away in the sensor field. Using this non-optimized max-distance transmission range of R for the control messages, together with another sub-optimized fixed value of k, is one of the main causes of limited improvements in lifespan of large area sensor network in IoT [18,19].
Referring to a survey paper over a hundred of cluster-based routing protocols [20], we found some approaches [21,22] to optimization of k, without compromising decentralized-clustering features. In [21], the authors investigated the optimization of k using a genetic algorithm, in which, however, the improvement significantly degraded by increasing the size of sensor field from 50 m to 100 m, which are still not big enough to be applied in IoT. In [22], uneven probabilities are applied to the election of CH nodes, while using suboptimal k determined by rule of thumb. In general, we could hardly find cluster-based routing protocols with optimization of R, the transmission range for control messages, or with joint optimization of . In this paper, we investigate a joint optimization of by in-depth analyses of energy consumption during clustering processes and data transmission in sensor nodes.
Table 1 is a list of symbols and notations used in this paper.

Table 1.
Symbols and notations.
2. Preliminaries
2.1. Energy Consumption Model
We adopt the energy consumption model stated in [3]. Each sensor node is assumed to perform power control depending on the distance between the transmitter and receiver. To transmit an l-bit message over a distance d (m), a sensor node dissipates energy (J) by
and the corresponding receiver node expends (J) in the process of receiving this message,
where = 50 (nJ/bit) represents the energy in the circuitry per bit; = 10 (pJ/bit/m2) and = 0.0013 (pJ/bit/m4) denote the energy dissipation in the transmission amplifier needed to achieve an acceptable signal-to-noise ratio according to the free space model (Friss) and the multi-path model, respectively; and (m). The energy for data aggregation per bit is set as = 5 (nJ/bit). Given two nodes communicating with each other, we also assume symmetry of the forward and reverse path power dissipation, i.e., the same amount of energy is consumed in the forward and reverse paths.
2.2. Cluster-Based Hierarchical Routing
It is assumed that there are N sensor nodes deployed in a circular-shaped field with radius of L (m). The distribution of the sensor nodes is uniformly random within this area, and the deployment is independent for different nodes. All nodes are assumed to have the same sensing ability and the same initial amount of energy. The sensing data are forwarded to a remote base station (BS) by performing the employed routing protocol. The BS is assumed to be at the border or outside of the sensing area.
In cluster-based routing protocols, time line is divided into rounds. Each round begins with the set-up phase, which is composed of CH selection and control message communications. A random number of CHs are elected in the set-up phase of each round. The number of CHs in a round is a random variable whose expectation is k. Conventional algorithms have estimated the value of k to be 5 by rule of thumb. Rounds, , are grouped together in such a manner that rounds from to form a group of rounds (GOR), rounds from to form another GOR, and so on. Let G be the set of nodes that have not been CHs within current GOR. Then, in round r, node i () chooses to become a CH with the probability of
According to Equation (3), each node serves as a CH one time in a GOR. CH selection is followed by three sequential steps of transmitting control messages: (i) CHs for this round broadcast advertisement (ADV) messages; (ii) non-CH nodes transmit join-request (Join-REQ) messages; and (iii) CHs send TDMA scheduling messages to their members. This ends the set-up phase of a round.
The set-up phase is followed by the steady-state phase in which the CHs gather, aggregate, and route the data from sensors within their cluster. If a non-CH node has failed to join a cluster in a round, it transmits its DATA to the base station (BS) directly for that round. Each member node of a cluster transmits DATA to its CH. CH nodes then perform data aggregation and finally send the aggregated data to the BS.
2.3. Problem Statement
In conventional LEACH-based algorithms, DATA messages are transmitted under power control. However, the control messages including ADV, Join-REQ, and TDMA are assumed to be transmitted with the fixed power enough to reach over a maximum distance of in the field. This fixed transmission range, , would be inappropriate for IoT based on large-area WSN. Furthermore, this non-optimized, max-distance transmission radius, , for control messages have caused us to set the number of clusters, k, to be a sub-optimal value [3], which is used as the rule of thumb thereafter. It is observed that the sub-optimal value also significantly shorten the network lifespan especially when L becomes large.
We now write the problem statement as follows. Assume we have N sensor nodes over a circular-shaped sensor field with radius (e.g., ). Our goal in this paper is to jointly optimize the average number k of CH nodes and transmission radius R () for the control messages to minimize overall energy consumption in a round or to maximize the sensor network lifespan.
3. Energy Consumption Analysis
Consider the circular-shaped sensor field with radius of L (m) in Figure 1. The center of the sensor field is the origin (0, 0) of the coordinate system. Let S denote distance of BS from the center of the sensor field. The base station (BS) is considered to be at the border or outside of the sensor field at coordinate (S, 0). Within the sensor field, we have a node at r () (m) away from the origin (0, 0). Each node has transmission radius R () for control messages including ADV, Join-REQ, and TDMA messages.
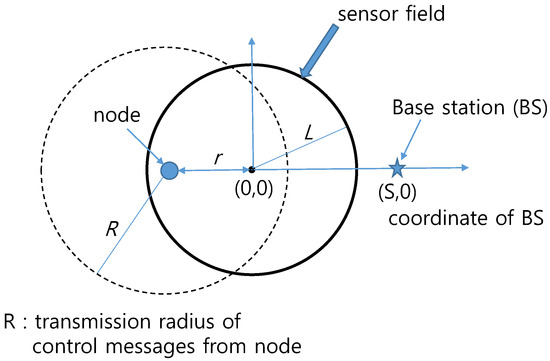
Figure 1.
Sensor field and control-message transmission range.
Consider a node marked at r () (m) away from the origin in Figure 1. Using a dashed circle, we show the transmission radius R (m) of control messages for the marked node. Inside of the sensor field, the area covered by the transmission range of the marked node is called effective area of the marked node. In the case of , the marked node is close to the center of the sensor field. In this case, the transmission range depicted by the dashed circle includes the entire sensor field as in Figure 2a; and the effective area of the marked node is exactly the same as the entire sensor field. However, in the case of , the sensor field is covered in part by the transmission range of the marked node as in Figure 2b, and the effective area of the node is the intersection of the two partially overlapping circles.
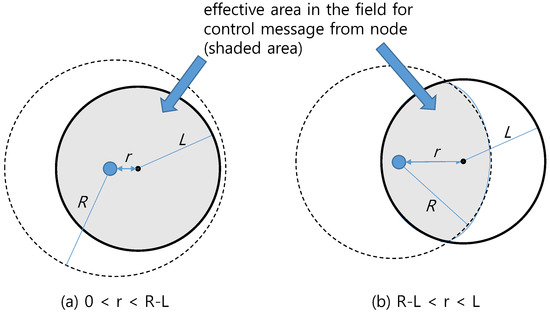
Figure 2.
Effective area of control-message.
By assuming symmetrical propagation channel between any two nodes, a node can hear ADV messages from other nodes which only reside in its effective area. The effective area of a node at r (m) away from the origin, with transmission range R, is calculated by (see Appendix A for its derivation)
where
is the intersection area of the two partially overlapped circles. The expectation, , of the effective area is given by (see Appendix B for its derivation)
It is noted that Equation (5) is calculated by taking into account both the total inclusion and partial overlap cases to obtain the expectation of transmission range of an arbitrary node.
Given k and R, we consider the probability that a node hears ADV messages from n CHs as the probability that a node has n CHs in its effective area. We model this probability as the spatial Poisson process, which is a stationary two-dimensional Poisson point process successfully adopted in modeling wireless sensor networks [23,24,25]:
where the density, the number of sensor nodes per unit area,
is the average number of CHs within unit area. A node can join a cluster if it has heard from one of more CHs. Therefore, the probability that a node fails to join a cluster for the current round is given by the probability of hearing zero ADV message:
The length of ADV, Join-REQ, TDMA, and DATA messages are denoted by , , , and , respectively (in bits). Among them, lengths , , and are fixed. However, the length of a TDMA schedule message, , depends on the number of member nodes in the current cluster, and the number of members, again, depends on . The expected number of non-CH nodes which successfully join clusters is
which, after dividing by k, gives the expected number of member nodes in a cluster. We have
where 16 is assumed to be the number of bits to represent each node ID. In the following subsections, we analyze the overall amounts of energy that are expended by the nodes in a round as a function of k and R.
3.1. Energy Dissipation by Non-CH Nodes
In this subsection, we analyze the expected amount of energy consumed by non-CH nodes in a round. First, consider sending Join-REQ messages with transmission radius of R. Since we have and assume
the expectation of energy dissipation by a non-CH node sending a Join-REQ message is given by
Modeling each of k clusters as a circle with the expectation of radius, , we calculate the area of each cluster as
from which
If we have then and vice versa. Let denote the distance from a member node to its CH. The expected amount of energy consumed by a member node while sending a DATA message to its CH is calculated by
where, using Equation (10),
and
We assume that the base station (BS) resides at coordinate where . A non-CH node, failing to join a cluster, sends a DATA message to the BS directly, consuming the amount of energy . Let denote the distance from a node to the BS. With large fields, will be dominated by nodes with , as follows.
where
The expectation of the number of CHs seen by a non-CH node is
The energy consumed by a non-CH node while receiving ADV messages is
A non-CH node receives a TDMA scheduling message from its CH by expending energy :
where is given in Equation (8).
Consequently, the expectation of total energy expended by all non-CH nodes in a round is given by
3.2. Energy Dissipation by CH Nodes
We now analyze the expected amount of energy expended by CH nodes in a round. First, consider sending ADV and TDMA messages with transmission radius of R. Average amount of energy consumption by a CH node while transmitting ADV and TDMA messages are
and
respectively.
The average number of member nodes of a CH is . The expected data-aggregation energy by a CH node is
A CH node sends aggregated data to the BS by expending
where is calculated as in Equation (13).
In LEACH-based clustering protocol, a CH node receives other CHs’ ADV messages, although they are just dumped; we ignore the energy related to this step. A CH node will hear Join-REQ messages from all non-CH nodes in its control-message range, to check if they are destined for itself or not. Therefore, while a CH node receives Join-REQ messages, it consumes :
A CH requires energy during receiving DATA from its member nodes as follows:
Consequently, the expectation of the total energy expended among all CH nodes in a round is given by
Finally, the expected amount of energy consumption in a round is
4. Optimization of
Our goal is to find the optimized and to minimize as in:
We note that can be calculated as a real number, which can be readily applied to the LEACH algorithm by using rounding off form for the place of in the cluster-selection probability (Equation (3)).
Although is high-order differentiable, getting gradients or Hessian matrix is expensive and complicated. Since is observed to have convex-downward shape, as shown by the simulation presented below, we choose Nelder–Mead (N-M) Simplex algorithm [26,27], as a derivative-free optimization method. We suggest constructing the initial simplex as the following three vertices, , , and :
where and are 5% value of and , respectively. In the first simplex , k is chosen to be 5 and R is taken as the mid-point of interval . Large-area sensor networks with large number of sensor nodes often show the optimum values of , which are greater than by conventional rule of thumb. Therefore, we suggest that both the second simplex and the third, , have , instead of using conventional initialization with for and, for .
The N-M optimization algorithm starts with the three vertices , , and . The function takes on values , , and . The function values are to be compared to determine the best vertex, second best vertex, and the worst vertex. For N-M simplex transformations, we have used the standard values, 1, 1/2, 1, and 1/2 for the reflection, expansion, contraction, and shrink transformation, respectively. According to the N-M implementation in [27], we iteratively continue the ordering, centroid, and transformation steps of N-M algorithm with given termination tests to obtain the optimization value of .
It is noted that the computational procedure for our proposed optimization described in this paper is not carried out by the sensor nodes, but is carried out at the base station (BS) and/or at the management center, which are assumed to have enough computational capabilities being supplied with sufficient power. The optimized parameters calculated at the management center can be implemented as a design parameter during the firmware installation for sensor nodes. The optimized parameters calculated at the BS can be broadcast to the sensor nodes deployed in the field through the wireless channel.
5. Performance Evaluation
In the performance evaluation, we used the lengths of messages as in the LEACH code [17]: , , and (bits). We considered or . We carried extensive simulations with large sizes of sensor fields, , compared with the typical size of 100 m considered in most existing WSN routing protocols [3,18,19,20,21]. The unit of L and R is meters. We assumed , i.e., the BS is on the boundary of the field.
With our derived energy function , Nelder–Mead Simplex algorithm converged in an average of 50 iterations taking around 50 ms on a CPU running at 3.10 GHz. In Figure 3, we show a contour plot of with and . We also show the locations of initial simplex and the final optimized simplex after 54 iterations. The marks connected with dotted lines between and show the path of simplex transformations from the iterations of N-M optimization. A closer investigation on the convergence behavior of the N-M optimization process is shown in Appendix C. We observed that the iterations have 3 expansions, 9 reflections, 6 outside-contractions, and 36 inside-contractions out of a total of 54 transformations. Overall, 66% of transformations are inside-contractions, which means the energy function has a very good shape for optimization.
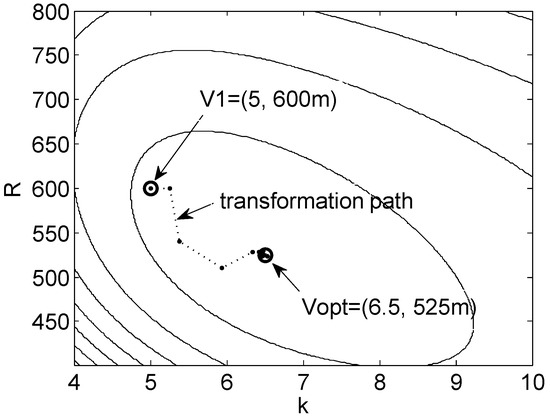
Figure 3.
Contour of energy function () and N-M transformation path from initial simples to optimized simplex .
We evaluated our proposed optimization by simulation with the LEACH code [17] from the originator, which runs on NS2 and has been verified in the literature, to obtain higher level of objectivity of our simulation results. For each scenario, we ran 100 simulations with different seed numbers to obtain narrow confidence intervals.
In Table 2, we compare average energy consumption per node in a round with measure (mJ/node/round), between the original LEACH [3] and the LEACH with our optimization. Each value was obtained from several hundreds of rounds with all N nodes alive in the cluster-based routing algorithms. The larger are N and L, the higher is the percentage of energy savings. We also show the optimized parameters in the table as compared with the fixed values of in the existing LEACH-based algorithms. It was observed that the optimum number k of clusters is dominated by N. On the other hand, R is mainly affected by the size, L, of sensor field.

Table 2.
Energy consumption per node in a round.
Figure 4 shows simulation results with and . Every node had an initial energy of 10 (J). The original LEACH [3] takes by rule of thumb, and to make sure that the entire sensor field is covered by any sensor node. In the figure, we show the number of nodes alive over simulation time in rounds. In the original LEACH [3], the average node lifespan is 110 rounds. Our proposed optimization, shown as “LEACH with Optimization”, takes and and outperforms the original, non-optimized LEACH [3] with an average node lifespan of 178 rounds, which is an increment of 62%. A genetic algorithm based optimization, LEACH-GA [21], does not take into account the energy dissipation for control messages, and yields an optimized value of , which resulted in quick energy depletion in our simulation environment with large area sensor field.
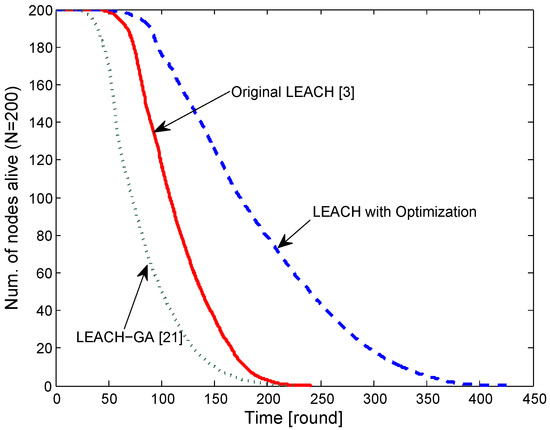
Figure 4.
Number of nodes alive ( m).
In Figure 5, we show how much our optimization improves another LEACH-based algorithm, LEACH-DT [22], which applies uneven probabilities to nodes in CH selection depending on the distance to the BS. LEACH-DT [22] uses the same parameters and (m) as in the original LEACH. LEACH-DT itself outperforms the original LEACH, as shown in the figure. We could further improve LEACH-DT by running it with our optimized parameters and , i.e., we used uneven CH-selection probabilities while keeping the average of 6.5 CHs in each round and setting the transmission radius for control messages to be 525 m. This improved LEACH-DT significantly, as shown in the curve “LEACH-DT with Optimization”.
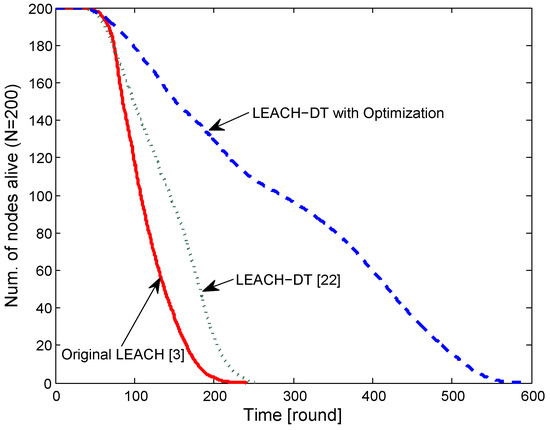
Figure 5.
Number of nodes alive ( m).
In Table 3, we compare performance in terms of time to percentage-node-death in rounds among the schemes compared in Figure 5. Our proposed optimization improved the network lifespan in terms of all criteria, 1–90%, in the table. We note that our optimization helps LEACH and LEACH-DT improve energy efficiency by increasing the lifespan dramatically with optimization. Consequently, our proposed optimization is expected to help existing cluster-based routing protocols to further improve in terms of network lifespan.

Table 3.
Time to percent-node-death.
6. Conclusions
We have analyzed the expectation of energy dissipation in a round as a function of k and R to obtain joint optimization values of . We have analyzed the amount of energy dissipation of CH nodes and non-CH nodes to derive the expectation of energy consumption in a round as a function of system design parameters with given network parameters including the number of sensor nodes N and the radius L of the sensor field. Our analyzed energy function is computationally tractable for derivative-free optimization algorithms, among which we adopt Nelder–Mead (N-M) simplex algorithm in our proposed scheme. The optimization procedure converges quickly enough for the BS or management center to run the optimization algorithm in real time. Our proposed method outperforms existing non-optimized LEACH-based schemes in terms of average node lifespan by saving the energy consumption by several tens of percent. Our optimization approach is expected to help existing cluster-based algorithms to further improve their energy efficiency.
Funding
This work was supported by the 2015 Research Fund of the University of Seoul.
Conflicts of Interest
The author declares no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| IoT | Internet of Things |
| WSN | Wireless Sensor Network |
| IIoT | Industrial Internet of Things |
| LEACH | Low Energy Adaptive Clustering Hierarchy |
| CH | Cluster head |
| BS | Base station |
| GOR | Group of Rounds |
| ADV | Advertisement |
| Join-REQ | Join-request |
| TDMA | Time division multiple access |
Appendix A. Derivation of Effective Area A(r,R)
In this appendix, we outline the derivation of Equation (4), the effective area. First, in the case of , the sensor field is totally included in the transmission range, and the effective area is the area of sensor field itself, . Second, if we have , then the two circles of transmission range and sensor field are partially overlapped. In this case, the effective area is the intersection area, , of the two circles, as explained in the remainder of this appendix.
As in Figure A1a, let and be the two circles of radii R and L, respectively, whose centers are at a distance r () from each other. In this appendix, we temporarily use a Cartesian coordinate system with origin at the center of circle with R such that the center of with L is at , as in Figure A1a.
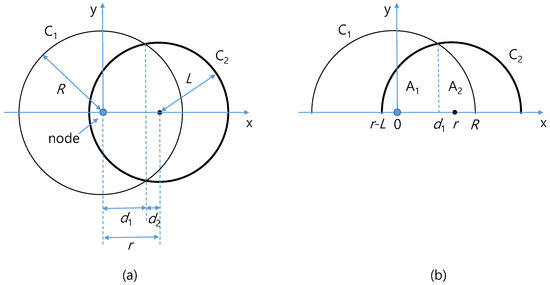
Figure A1.
Two intersecting circles with radius R and with radius L. (a) Overlapping of sensor field and transmission range; (b) Upper half of the intersection area.
The circles and are described by the following equations, respectively:
We have at the two intersection points. Replacing x with and isolating on both equations above, we have
Solving for , we have
As in Figure A1a, let , or
We calculate the upper-half areas, and , of the segments from circles and , respectively, as in Figure A1b. We have
The computation of these integrals is straightforward. Before we proceed, notice first that
This is the same as Equation (A8) if we apply the substitutions and . Therefore, by computing , we immediately obtain as well. We have
The indefinite integral of is straightforward by using integration by parts:
Therefore, we have
Using Equation (A11) on Equation (A9) yields
where we used the fact that for any in . As discussed above, we can now obtain directly by doing the substitutions and on the expression for on Equation (A12)
Finally, intersection area is computed as twice of the sum of and
Appendix B. Expectation of Effective Area
In this appendix, we derive the expectation (Equation (5)) of effective area. The expectation, , of the effective area of a node can be obtained by averaging the effective area over the entire sensor field, which can be represented in a polar coordinate system:
To calculate Equation (A17), we need to have the corresponding indefinite integrals. For the first integration out of the three integrals in Equation (A17), we have
Appendix C. Convergence Behavior of the Optimization
In this appendix, we show the convergence behavior of the N-M optimization process in terms of iteration, function counts, function values, and N-M procedures with and .
In Table A1, “Func-Count” means the number of function evaluations and “Procedure” means the type of transformation in N-M optimization algorithm. We use the convergence criteria of for to terminate the iteration.

Table A1.
Optimization process.
Table A1.
Optimization process.
| Iteration | Func-Count | Procedure | |
|---|---|---|---|
| 1 | 3 | 4.6879 | initial simplex |
| 2 | 5 | 4.63203 | expand |
| 3 | 7 | 4.50425 | expand |
| 4 | 9 | 4.50425 | contract inside |
| 5 | 11 | 4.40857 | expand |
| 6 | 12 | 4.40857 | reflect |
| 7 | 13 | 4.40857 | reflect |
| 8 | 14 | 4.40857 | reflect |
| 9 | 16 | 4.40857 | contract inside |
| ..... | ..... | ..... | ..... |
| 51 | 95 | 4.40667 | contract inside |
| 52 | 97 | 4.40667 | contract inside |
| 53 | 99 | 4.40667 | contract inside |
| 54 | 101 | 4.40667 | contract inside |
References
- Ghayvat, H.; Mukhopadhyay, S.; Gui, X.; Suryadevara, N. WSN- and IoT-based smart homes and their extension to smart buildings. Sensors 2015, 15, 10350–10379. [Google Scholar] [CrossRef] [PubMed]
- Zhou, M.; Zhao, M.; Liu, A.; Ma, M.; Wang, T.; Huang, C. Fast and efficient data forwarding scheme for tracking mobile targets in sensor networks. Symmetry 2017, 9, 269. [Google Scholar] [CrossRef]
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Essam, M.; Shaaban, E. Enhancing S-LEACH security for wireless sensor networks. Int. J. Appl. Comput. 2011, 4, 101–107. [Google Scholar]
- Manzoor, B.; Javaid, N.; Rehman, O.; Akbar, M.; Nadeem, Q.; Iqbal, A.; Ishfaq, M. Q-LEACH: A new routing protocol for WSNs. Procedia Comput. Sci. 2013, 19, 926–931. [Google Scholar] [CrossRef]
- Wang, A.; Yang, D.; Sun, D. A clustering algorithm based on energy information and cluster heads expectation for wireless sensor networks. Comput. Electr. Eng. 2012, 38, 662–671. [Google Scholar] [CrossRef]
- Abdulsalam, H.M.; Ali, B.A. W-LEACH based dynamic adaptive data aggregation algorithm for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2013, 9, 1–11. [Google Scholar] [CrossRef]
- Sasikala, A.S.D.; Sangameswaran, N. Improving the energy efficiency of LEACH protocol using VCH in wireless sensor network. Int. J. Eng. Dev. Res. 2015, 3, 918–924. [Google Scholar]
- Batra, P.K.; Kant, K. LEACH-MAC: A new cluster head selection algorithm for wireless sensor networks. Wirel. Netw. 2016, 22, 49–60. [Google Scholar] [CrossRef]
- Liu, Y.; Xu, K.; Luo, Z.; Chen, L. A reliable clustering algorithm based on LEACH protocol in wireless mobile sensor networks. In Proceedings of the International Conference on Mechanical and Electrical Technology, Singapore, 10–12 September 2010; pp. 692–696. [Google Scholar]
- Katiyar, V.; Chand, N.; Gautam, G.C.; Kumar, A. Improvement in LEACH protocol for large-scale wireless sensor networks. In Proceedings of the International Conference on Emerging Trends in Electrical and Computer Technology, Nagercoil, India, 23–24 March 2011; pp. 1070–1075. [Google Scholar]
- Kim, D.S.; Cha, H.S.; Yoo, S. Improve far-zone LEACH protocol for energy conserving. In Proceedings of the International Conference on Wireless Communications, Networking and Mobile Computing, Shanghai, China, 21–23 September 2012; pp. 1–4. [Google Scholar]
- Lee, J.Y.; Jung, K.D.; Moon, S.J.; Jeong, H.Y. Improvement on LEACH protocol of a wide-area wireless sensor network. Multimedia Tools Appl. 2017, 76, 19843–19860. [Google Scholar] [CrossRef]
- Marappan, P.; Rodrigues, P. An energy efficient routing protocol for correlated data using CL-LEACH in WSN. Wirel. Netw. 2016, 22, 1415–1423. [Google Scholar] [CrossRef]
- Cho, S.; Han, L.; Joo, B.; Han, S. P-LEACH: An efficient cluster-based technique to track mobile sinks in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2014, 2014, 803656. [Google Scholar] [CrossRef]
- Klaoudatou, E.; Konstantinou, E.; Kambourakis, G.; Gritzalis, S. A survey on cluster-based group key agreement protocols for WSNs. IEEE Commun. Surv. Tutor. 2011, 13, 429–442. [Google Scholar] [CrossRef]
- MIT uAMPS LEACH ns Extentions. Available online: http://www2.ece.rochester.edu/projects/wcng/code.html (accessed on 1 December 2018).
- Khediri, S.E.L.; Nasri, N.; Wei, A.; Kachouri, A. A new approach for clustering in wireless sensors networks based on LEACH. Procedia Comput. Sci. 2014, 32, 1180–1185. [Google Scholar] [CrossRef]
- Devika, G.; Karegowda, A. A programatic study of LEACH and its decendant routing protocols in WSN. Int. J. Comput. Intell. Inform. 2015, 4, 300–307. [Google Scholar]
- Singh, S.K.; Kumar, P.; Singh, J.P. A survey on successors of LEACH protocol. IEEE Access 2017, 5, 4298–4328. [Google Scholar] [CrossRef]
- Liu, J.L.; Ravishankar, C.V. LEACH-GA: Genetic algorithm-based energy-efficient adaptive clustering protocol for wireless sensor networks. Int. J. Mach. Learn. Comput. 2011, 1, 79–85. [Google Scholar] [CrossRef]
- Kang, S.H.; Nguyen, T. Distance based thresholds for cluster head selection in wireless sensor networks. IEEE Commun. Lett. 2012, 16, 1396–1399. [Google Scholar] [CrossRef]
- Ram, S.S.; Manjunath, D.; Iyer, S.K.; Yogeshwaran, D. On the path coverage properties of random sensor networks. IEEE Trans. Mobile Comput. 2007, 6, 494–506. [Google Scholar] [CrossRef]
- Liu, B.; Towsley, D. A study on the coverage of large-scale networks. In Proceedings of the IEEE International Conference on Mobile Ad-hoc and Sensor Systems, Fort Lauderdale, FL, USA, 25–27 October 2004; pp. 475–483. [Google Scholar]
- Zhang, H.; Hou, J. On deriving the upper bound of α-lifetime for large sensor networks. In Proceedings of the 5th ACM International Symposium on Mobile Ad-Doc Networking and Computing, Tokyo, Japan, 24–26 May 2004; pp. 121–132. [Google Scholar]
- Lagarias, J.C.; Reeds, J.A.; Wright, M.H.; Wright, P.E. Convergence Properties of the Nelder–Mead Simplex Method in Low Dimensions. SIAM J. Optim. 1998, 9, 112–147. [Google Scholar] [CrossRef]
- Gao, F.; Han, L. Implementing the Nelder–Mead simplex algorithm with adaptive parameters. Comput. Optim. Appl. 2012, 51, 259–277. [Google Scholar] [CrossRef]
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).