Lossless and Efficient Polynomial-Based Secret Image Sharing with Reduced Shadow Size
Abstract
1. Introduction
2. Preliminaries
2.1. Polynomial-Based Secret Image Sharing
2.2. PSIS with Lossless Recovery
2.3. Generalized Arnold Permutation
3. The Proposed Scheme
3.1. Design Concept
3.2. The Permutation Process
- In Step 2, the formula to select the six numbers is fixed in advance.
| Algorithm 1 The permutation process |
| Input: An image I with size of . |
| Output: A permuted image with size of |
| Step 1. Count the numbers of each grayscale pixel value in the image I and sort them in ascending order. |
| Step 2. Select three small numbers , , () and three large numbers , , () from the order according to a certain formula. |
| Step 3. Generate the three parameters , and as Equation (6). |
| Step 4. Evaluate the conversion matrix M as Equation (7) or Equation (8). |
| Step 5. For each pixel P with the position in the image I, map P to a new position according to Equation (9). |
| Step 6. Output the permuted image . |
3.3. The Sharing Process
- In Step 1, each section consists of pixels due to the first coefficients in Equation (5) are utilized to embed secret values in Step 2 and each value consists of two adjacent pixel values in Step 3. Besides, to guarantee all pixels can be processed, the width of the image, N, should be an integer multiple of .
- In Step 4, the last coefficient is randomly assigned to improve the security.
- In Steps 5–7, we evaluate n shared values of each section. The screening operation occurs in Step 7 to guarantee none of the shared values is larger than 65,535.
- In Step 8, we obtain shared pixels of each section.
- A sharing phase consists of Steps 3–8. In total, there are sharing phases, and shared pixels for each shadow image are generated.
| Algorithm 2 The proposed threshold PSIS scheme |
| Input: A permuted secret image with size of ; Threshold parameters ; n different serial numbers . |
| Output:n shadow images . |
| Step 1. Divide the image S into non-overlapping sections, each of which consists of adjacent pixels. |
| Step 2. For each -pixel section , , , repeat Steps 3–8 until all sections have been processed. |
| Step 3. Assign the coefficients as follows.
|
| Step 4. Generate a random integer from as the coefficient . |
| Step 5. For each serial number , , repeat Steps 6–7 until all n shared values have been evaluated. |
| Step 6. Evaluate the shared value as follows.
|
| Step 7. If , return to Step 4 and redo Steps 4–7. Else continue. |
| Step 8. For each shared value , , generate two adjacent pixels in shadow image as follows.
|
| Step 9. Output n shadow images . |
3.4. The Recovery Process
- In Step 1, we take the first two non-used adjacent pixels from each of the k shadow images, to form a set with k pairs of shared pixels. The number of all sets is .
- Steps 2, 3 and 4 are the inverse operations of Steps 8, 6 and 3 in Algorithm 2, respectively.
- A recovery phase consists of Steps 2–4. In each recovery phase, we retrieve a -pixel section of the permuted secret image as mentioned in Algorithm 2. In total, there are recovery phases.
| Algorithm 3 Secret image recovery of the proposed scheme |
| Input:k shadow images with size of ; Threshold parameters ; k different serial numbers . |
| Output: A reconstructed permuted secret image . |
| Step 1. For each two non-overlapping adjacent pixels and in each shadow image , , , , repeat Steps 2–4 until all pairs pixels of the k shadow images have been processed. |
| Step 2. Evaluate the k shared values , , as follows. |
| Step 3. Use the k serial numbers, k shared values and the Lagrange’s interpolation to obtain the coefficients in the the linear equations as Equation (10). |
| Step 4. Obtain the pixels corresponding to as follows. |
| Step 5. Obtain all pixels and reconstruct the permuted secret image . |
| Step 6. Output . |
4. Performance Analyses
4.1. Lossless Recovery Analysis
4.2. Threshold Analysis
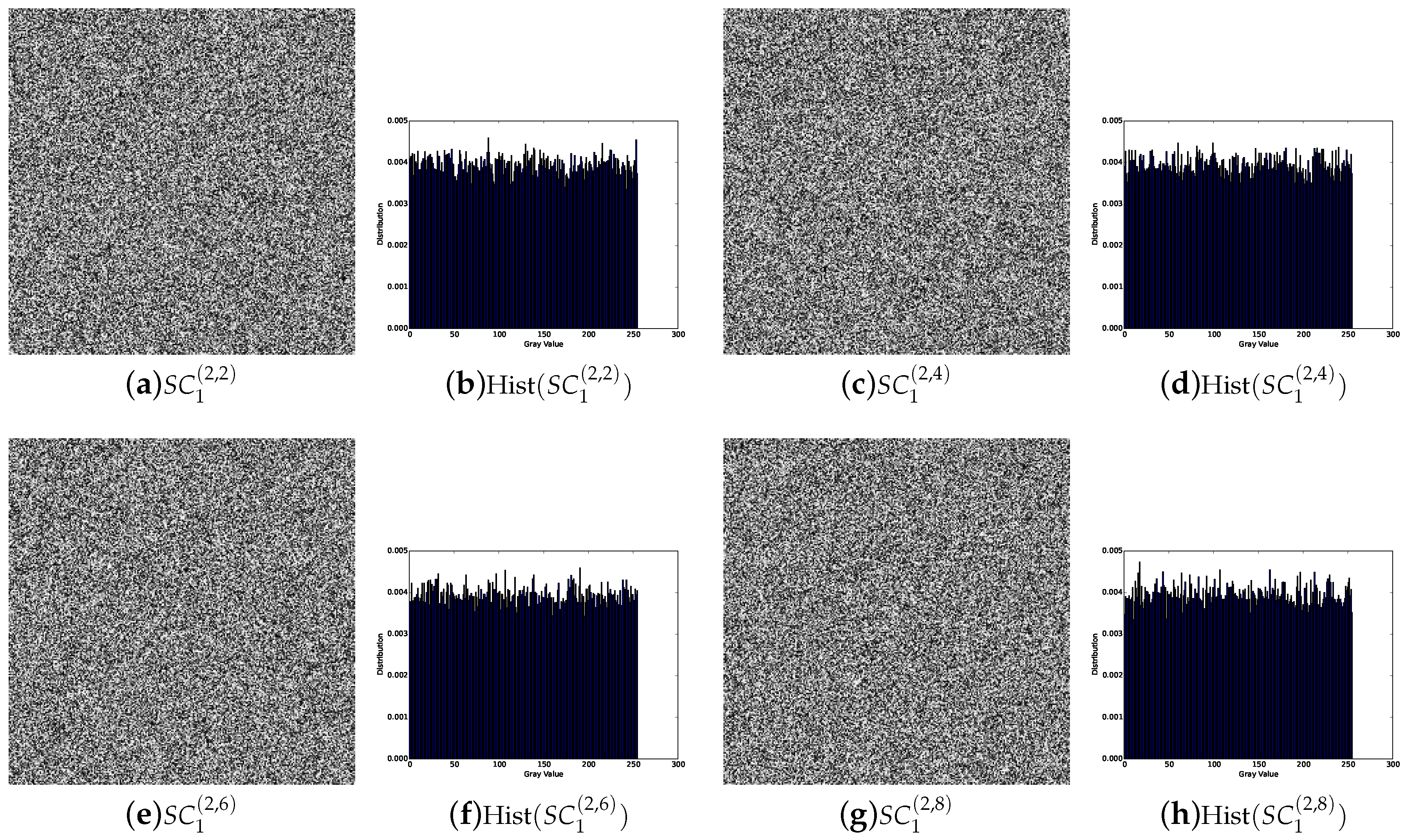
4.3. Security Analysis
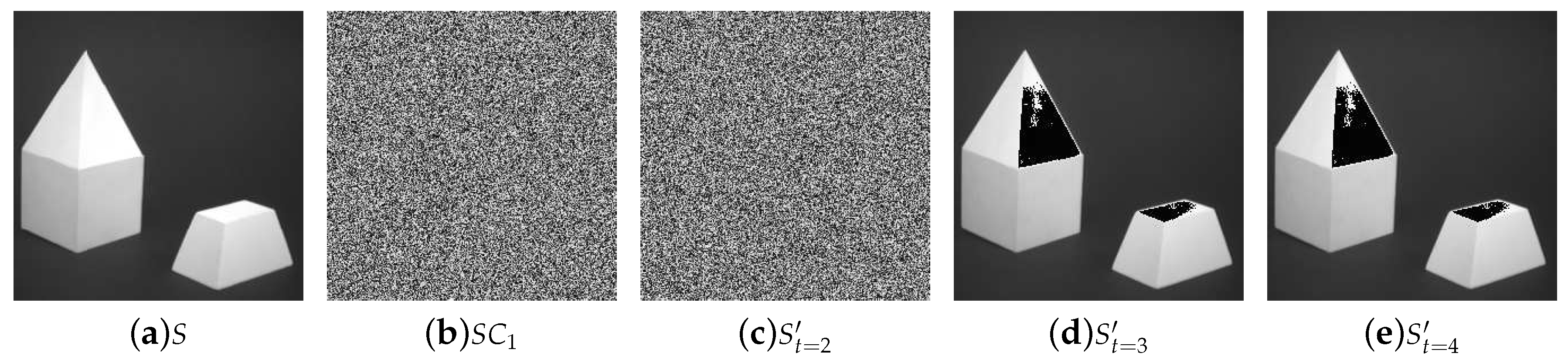
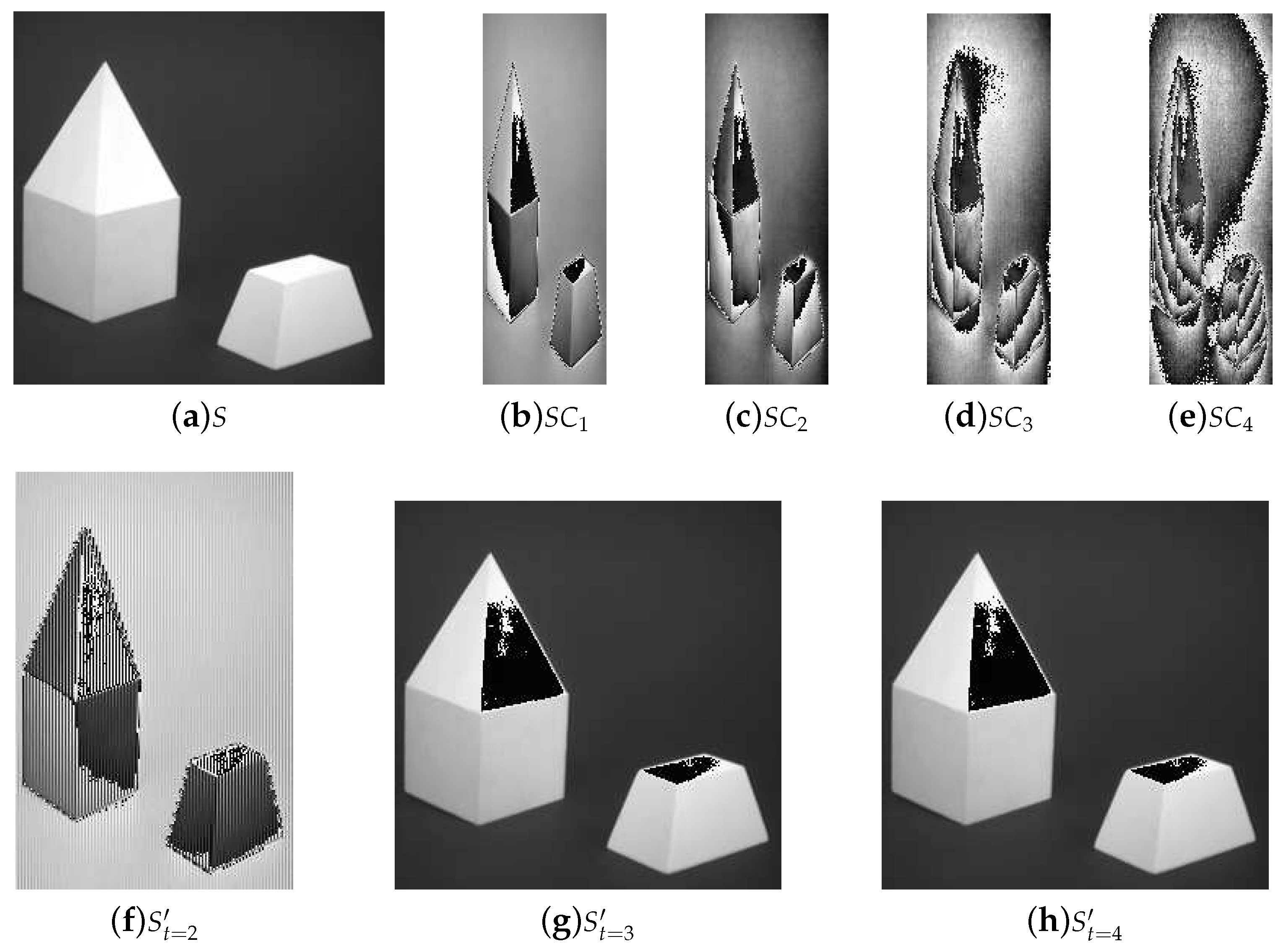
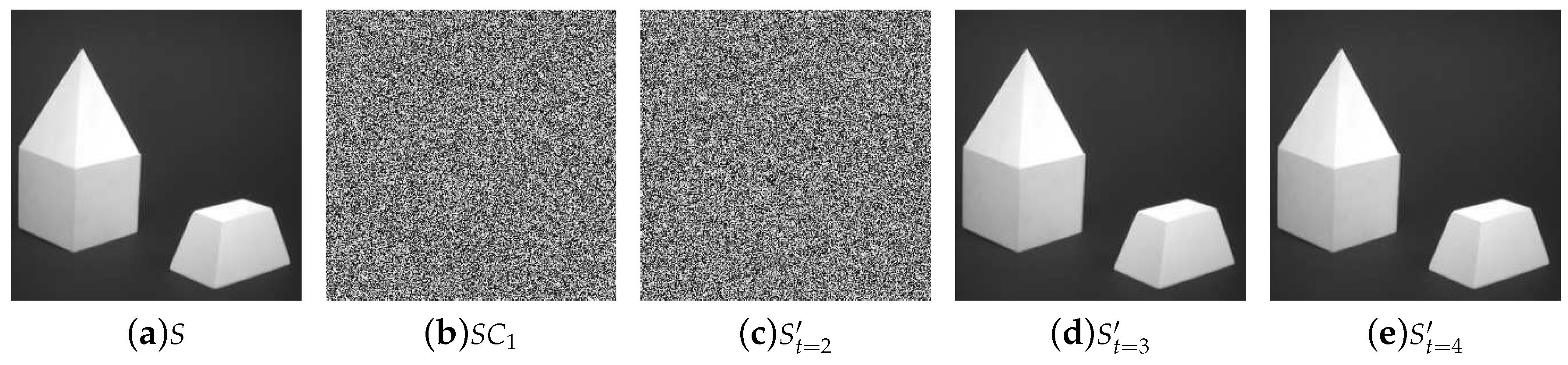
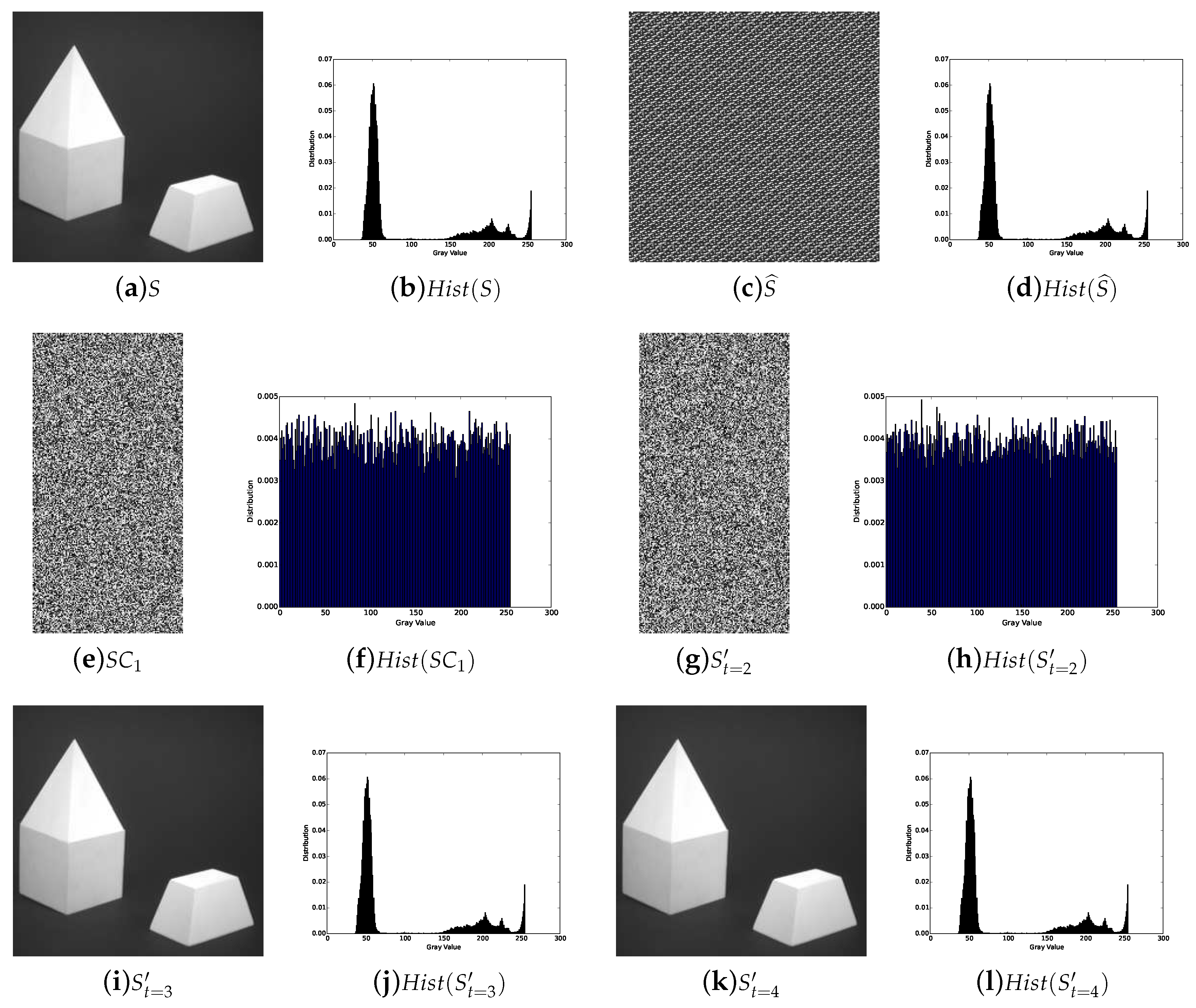
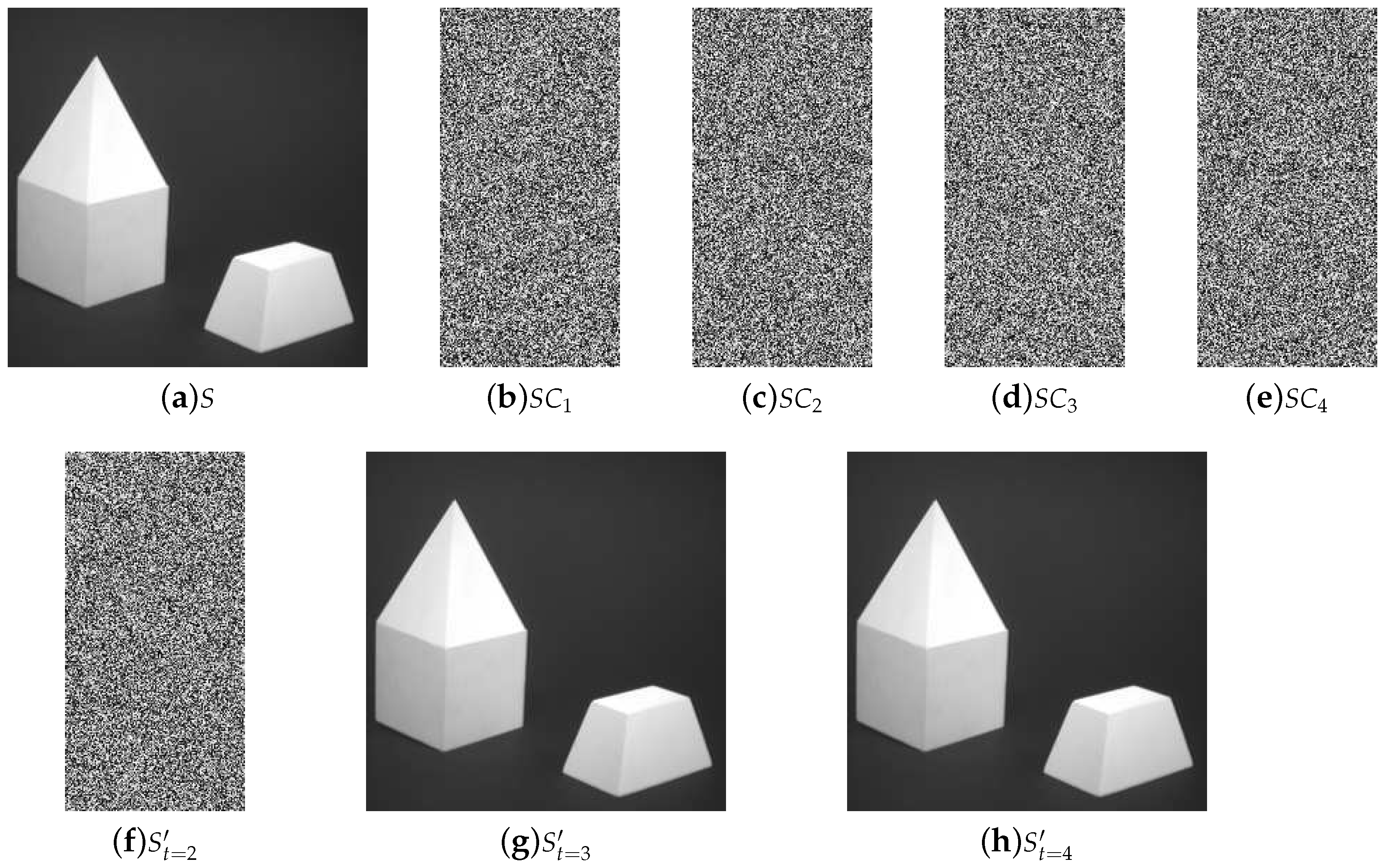
5. Experiments and Comparisons
5.1. Image Illustration
- Lossless recovery: The secret image can be reconstructed losslessly with k or more shadow images.
- Security: The shadow images are noisy-like, thus every single shadow is secure. Furthermore, there is no leakage of secret information from recovered images with less than k shadow images, which shows security of our scheme.
- Reduced shadow size: In the proposed threshold PSIS, the size of each shadow image is of that of the secret image.
5.2. Comparisons with Related Works
- Lossless recovery: Classic PSISs can only achieve lossy recovery, while several other PSISs including our scheme with different solutions can achieve lossless recovery.
- Shadow size: Except Thien-and-Lin’s and Our proposed PSISs, shadow size generated by other PSISs are the same or more than that of the secret image. The size of our PSIS is a little larger than that of Thien-and-Lin’s, but the security and lossless recovery can be guaranteed. Furthermore, we can also utilize partial bits of the coefficient to embed more secret values and assign remainder bits randomly, to further reduce the shadow size as well as to improve the efficiency.
- Random pixel expansion: Random pixel expansion may occur in Thien-and-Lin’s lossless PSIS, so its generated shares can only be stored as data rather than images. In our scheme, n noise-like shares with size of of that of the secret image are generated, which can be still stored as images.
- Pre-encryption and decryption: Thien-and-Lin’s PSIS needs extra pre-encryption to avoid the leakage of secret information, so it results in more costs. Our scheme needs no extra permutation if there is no higher level of security requirement in general application scenarios.
- Computational complexity: In some PSISs, there is extra recombination or decryption after the recovery process, so only the complexity of secret recovery process is calculated here. Only the constant coefficient needs to be calculated by the Lagrange interpolation as the secret value in Shamir’s PSISs, while two or more coefficients as secret values in Thien-and-Lin’s, Ding and coworkers’ and Our PSISs should be computed by solving equations. Therefore, the complexity of the latter PSISs is larger than that of the former PSISs. Yang and coworkers’ PSIS is based on Galois Field GF(), which lacks the theoretical calculation of computational complexity. However, the complexity of computations based on Galois Field GF() is much larger than that of computations based on integers.
- The running time of our scheme is much shorter than that of Shamir’s and Ding and coworkers’ schemes, which indicates our scheme is more efficient than Shamir’s and Ding and coworkers’ schemes.
- The running time of our scheme is little longer than Thien-and-Lin’s scheme. However, if the permutation process is removed in our scheme, the running time is approximately equal to or even slightly shorter than that of Thien-and-Lin’s scheme. In fact, our scheme without permutation is sufficient to ensure security in general application scenarios.
- We can modify our scheme, specifying one pixel value as a secret value and 257 as the prime, with the same principle. As a result, the running time becomes longer than our original scheme’s. Therefore, to a certain degree, decreasing the number of secret values has improved the efficiency of sharing and recovery.
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Naor, M.; Shamir, A. Visual cryptography. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin, Germany, 1994; pp. 1–12. [Google Scholar]
- Weir, J.; Yan, W. A comprehensive study of visual cryptography. In Transactions on Data Hiding and Multimedia Security V; Springer: Berlin, Germany, 2010; pp. 70–105. [Google Scholar]
- Yan, X.; Liu, X.; Yang, C.N. An enhanced threshold visual secret sharing based on random grids. J. Real-Time Image Process. 2015, 14, 61–73. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Xie, D.; Li, L.; Peng, H.; Yang, Y. A Secure and Efficient Scalable Secret Image Sharing Scheme with Flexible Shadow Sizes. PLoS ONE 2017, 12, e0168674. [Google Scholar] [CrossRef] [PubMed]
- Thien, C.C.; Lin, J.C. Secret image sharing. Comput. Graph. 2002, 26, 765–770. [Google Scholar] [CrossRef]
- Lin, P.Y.; Chan, C.S. Invertible secret image sharing with steganography. Pattern Recognit. Lett. 2010, 31, 1887–1893. [Google Scholar] [CrossRef]
- He, J.; Lan, W.; Tang, S. A secure image sharing scheme with high quality stego-images based on steganography. Multimed. Tools Appl. 2017, 76, 7677–7698. [Google Scholar] [CrossRef]
- Mao, Q.; Bharanitharan, K.; Chang, C.C. Novel Lossless Morphing Algorithm for Secret Sharing via Meaningful Images. J. Inf. Hiding Multimed. Signal Process. 2016, 7, 1168–1184. [Google Scholar]
- Yang, C.N.; Ciou, C.B. Image secret sharing method with two-decoding-options: Lossless recovery and previewing capability. Image Vis. Comput. 2010, 28, 1600–1610. [Google Scholar] [CrossRef]
- Li, P.; Yang, C.N.; Kong, Q.; Ma, Y.; Liu, Z. Sharing more information in gray visual cryptography scheme. J. Vis. Commun. Image Represent. 2013, 24, 1380–1393. [Google Scholar] [CrossRef]
- Li, P.; Yang, C.N.; Wu, C.C.; Kong, Q.; Ma, Y. Essential secret image sharing scheme with different importance of shadows. J. Vis. Commun. Image Represent. 2013, 24, 1106–1114. [Google Scholar] [CrossRef]
- Guo, C.; Chang, C.C.; Qin, C. A hierarchical threshold secret image sharing. Pattern Recognit. Lett. 2012, 33, 83–91. [Google Scholar] [CrossRef]
- Chen, C.C.; Tsai, Y.H. An Expandable Essential Secret Image Sharing Structure. J. Inf. Hiding Multimed. Signal Process. 2016, 7, 135–144. [Google Scholar]
- Chen, W.K.; Chen, H.P.; Tso, H.K. A Friendly and Verifiable Image Sharing Method. J. Netw. Intell. 2016, 1, 46–51. [Google Scholar]
- Zhou, Z.; Yang, C.N.; Cao, Y.; Sun, X. Secret Image Sharing Based on Encrypted Pixels. IEEE Access 2018, 6, 15021–15025. [Google Scholar] [CrossRef]
- Wu, X.; Yang, C.N.; Zhuang, Y.T.; Hsu, S. Improving recovered image quality in secret image sharing by simple modular arithmetic. Signal Process. Image Commun. 2018, 66, 42–49. [Google Scholar] [CrossRef]
- Bao, L.; Yi, S.; Zhou, Y. Combination of Sharing Matrix and Image Encryption for Lossless (k,n)-Secret Image Sharing. IEEE Trans. Image Process. 2017, 26, 5618–5631. [Google Scholar] [CrossRef] [PubMed]
- Liu, L.; Lu, Y.; Yan, X.; Wang, H. Greyscale-images-oriented progressive secret sharing based on the linear congruence equation. Multimed. Tools Appl. 2017, 1–28. [Google Scholar] [CrossRef]
- Yan, X.; Lu, Y.; Liu, L.; Wan, S.; Ding, W.; Liu, H. Chinese Remainder Theorem-Based Secret Image Sharing for (k, n) Threshold. In Proceedings of the International Conference on Cloud Computing and Security, Nanjing, China, 16–18 June 2017; Springer: Berlin, Germany, 2017; pp. 433–440. [Google Scholar]
- Lin, S.J.; Lin, J.C. VCPSS: A two-in-one two-decoding-options image sharing method combining visual cryptography (VC) and polynomial-style sharing (PSS) approaches. Pattern Recognit. 2007, 40, 3652–3666. [Google Scholar] [CrossRef]
- Ulutas, G.; Nabiyev, V.V.; Ulutas, M. Polynomial approach in a secret image sharing using quadratic residue. In Proceedings of the International Symposium on Computer and Information Sciences, Guzelyurt, Northern Cyprus, 14–16 September 2009; pp. 586–591. [Google Scholar]
- Yang, C.N.; Chen, T.S.; Yu, K.H.; Wang, C.C. Improvements of image sharing with steganography and authentication. J. Syst. Softw. 2007, 80, 1070–1076. [Google Scholar] [CrossRef]
- Ding, W.; Liu, K.; Yan, X.; Liu, L. Polynomial-Based Secret Image Sharing Scheme with Fully Lossless Recovery. Int. J. Digit. Crime Forens. IJDCF 2018, 10, 120–136. [Google Scholar] [CrossRef]
- Jin, D.; Yan, W.Q.; Kankanhalli, M.S. Progressive color visual cryptography. J. Electr. Imaging 2005, 14, 033019. [Google Scholar] [CrossRef]
- Li, P.; Ma, P.J.; Su, X.H.; Yang, C.N. Improvements of a two-in-one image secret sharing scheme based on gray mixing model. J. Vis. Commun. Image Represent. 2012, 23, 441–453. [Google Scholar] [CrossRef]
- Qi, D.; Wang, D.; Yang, D. Matrix transformation of digital image and its periodicity. Prog. Nat. Sci. Mater. Int. 2001, 11, 548–549. [Google Scholar]

| Schemes | Lossless Recovery | Shadow Size | Random Pixel Expansion | Pre-Encryption and Decryption | Computational Complexity |
|---|---|---|---|---|---|
| Shamir et al. [4] | No | 1 | No | No | |
| Thien-and-Lin (lossy) [6] | No | No | Yes | ||
| Thien-and-Lin (lossless) [6] | Yes | Yes | Yes | ||
| Yang et al. [23] | Yes | 1 | No | No | High |
| Ding et al. [24] | Yes | 1 | No | No | |
| Our PSIS | Yes | No | Yes | ||
| Our PSIS (without permutation) | Yes | No | No |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, X.; Lu, Y.; Yan, X.; Wang, Y.; Liu, L. Lossless and Efficient Polynomial-Based Secret Image Sharing with Reduced Shadow Size. Symmetry 2018, 10, 249. https://doi.org/10.3390/sym10070249
Zhou X, Lu Y, Yan X, Wang Y, Liu L. Lossless and Efficient Polynomial-Based Secret Image Sharing with Reduced Shadow Size. Symmetry. 2018; 10(7):249. https://doi.org/10.3390/sym10070249
Chicago/Turabian StyleZhou, Xuan, Yuliang Lu, Xuehu Yan, Yongjie Wang, and Lintao Liu. 2018. "Lossless and Efficient Polynomial-Based Secret Image Sharing with Reduced Shadow Size" Symmetry 10, no. 7: 249. https://doi.org/10.3390/sym10070249
APA StyleZhou, X., Lu, Y., Yan, X., Wang, Y., & Liu, L. (2018). Lossless and Efficient Polynomial-Based Secret Image Sharing with Reduced Shadow Size. Symmetry, 10(7), 249. https://doi.org/10.3390/sym10070249





