Fuzzy-Based Multi-Modal Query-Forwarding in Mini-Datacenters
Abstract
1. Introduction
- ➢
- A duplication/aggregation query flow model,
- ➢
- A multi-modal query forwarding mechanism, and
- ➢
- A fuzzy logic intelligence-based dynamic query forwarding selection.
- ➢
- The ratio of fitted gateways to the deployed gateways, and
- ➢
- The ratio of overloaded gateways to fitted gateways.
- (i).
- Modeling IoT-WSN as a mini-datacenter,
- (ii).
- Modeling the query-response task-flow within the proposed mini-datacenter,
- (iii).
- Deriving a relationship between redundancy, reliability, backlog, and buffer occupancy to account for the influence of these factors on query forwarding, and
- (iv).
- Defining fuzzy membership functions to select the granular forwarding strategies to manage the query flow.
2. Related Work
3. Mini-Datacenter
4. Modeling the Query Flow Within the Mini-Datacenter
4.1. Modeling Coarse-Grain Forwarding
4.2. Modeling Fine-Grain Forwarding
4.2.1. Modeling Redundancy
- ➢
- When the buffer capacity of the gateway is less than or equal to half of the maximum capacity, the fitness is equal to 1, representing a state where the gateway has sufficient capacity.
- ➢
- As the buffer occupancy increases from 50 to 100%, the fitness value decreases proportionally.
- ➢
- Once the buffer is full, the fitness becomes equal to 0, indicating that the respective gateway cannot accept further data. This formulation ensures that gateways with sufficient buffer space are preferred for redundancy, while those nearing saturation are gradually excluded from the forwarding process.
4.2.2. Modeling Reliability
4.3. Fuzzy Modeling of Granular Selection in Query Forwarding
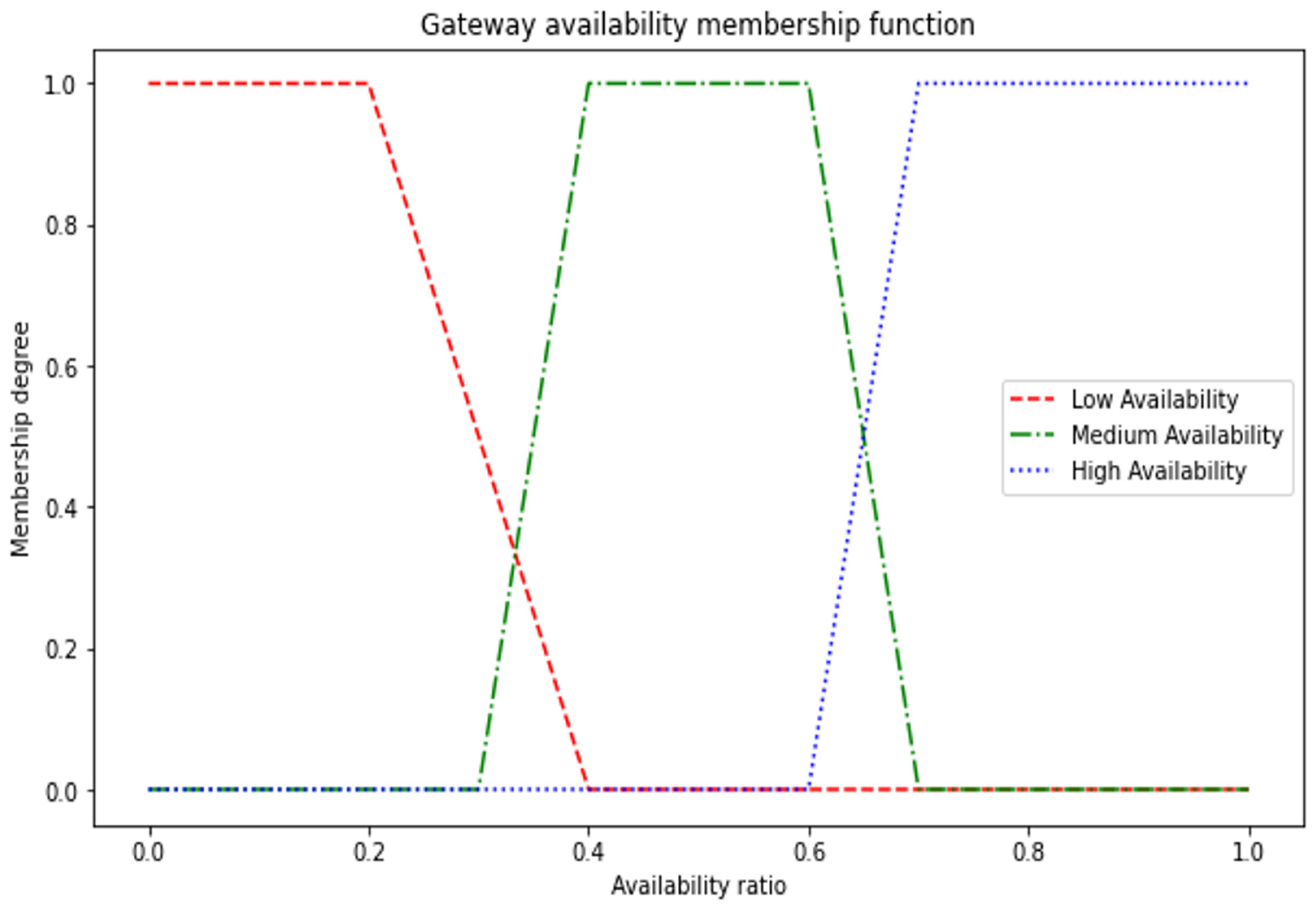
4.3.1. Modeling Fuzzy Input Parameters
4.3.2. Modeling Rules
4.3.3. Modeling Output Membership Function
5. Proposed Methodology
6. Results and Discussion
6.1. Query Forwarding Behavior Within Mini-Datacenter
6.1.1. Buffer Occupancy Nearing Saturation
6.1.2. Buffer Occupancy with Medium Occupancy
6.1.3. Fuzzy Logic Intelligence in Query Forwarding
6.2. Behavior of Mini-Datacenter Under Higher Nodes
6.3. Statistical Evaluation of Reliability in Scalable Mini-Datacenter
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Al Kez, D.; Foley, A.M.; Laverty, D.; Del Rio, D.F.; Sovacool, B. Exploring the Sustainability Challenges Facing Digitalization and Internet Data Centers. J. Clean. Prod. 2022, 371, 133633. [Google Scholar] [CrossRef]
- Gianfagna. Datacenter Journey: Data Volume Growth and Moore’s Law. 2022. Available online: https://www.synopsys.com/blogs/chip-design/data-volume-growth-and-moores-law.html (accessed on 17 December 2024).
- Choudhary, A. Internet of Things: A comprehensive overview, architectures, applications, simulation tools, challenges and future directions. Discov. Internet Things 2024, 4, 31. [Google Scholar] [CrossRef]
- Corallo, A.; Crespino, A.M.; Del Vecchio, V.; Lazoi, M.; Marra, M. Understanding and Defining Dark Data for the Manufacturing Industry. IEEE Trans. Eng. Manag. 2023, 70, 700–712. [Google Scholar] [CrossRef]
- Vailshery, L.S. Number of Internet of Things Connected Devices Worldwide from 2019 to 2033, by Vertical. 2024. Available online: https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide (accessed on 18 December 2024).
- Manyika, J.; Chui, M.; Bughin, J.; Dobbs, R.; Bisson, P.; Marrs, A. Disruptive Technologies: Advances That Will Transform Life, Business, and the Global Economy; McKinsey Global Institute: San Francisco, CA, USA, 2013. [Google Scholar]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Alam, T. A Reliable Communication Framework and Its Use in Internet of Things (IoT). Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2018, 34, 50–456. Available online: https://ssrn.com/abstract=3619450 (accessed on 18 December 2024).
- Saini, K.; Pandey, U.; Raj, P. Edge computing challenges and concerns. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2022; Volume 127, pp. 259–278. [Google Scholar]
- Ergen, M.; Saoud, B.; Shayea, I.; El-Saleh, A.A.; Ergen, O.; Inan, F.; Tuysuz, M.F. Edge computing in future wireless networks: A comprehensive evaluation and vision for 6G and beyond. ICT Express 2024, 10, 1151–1173. [Google Scholar] [CrossRef]
- Rimal, B.P.; Van, D.P.; Maier, M. Mobile-Edge Computing Versus Centralized Cloud Computing Over a Converged FiWi Access Network. IEEE Trans. Netw. Serv. Manag. 2017, 14, 498–513. [Google Scholar] [CrossRef]
- Feng, J.; Liu, Z.; Wu, C.; Ji, Y. Mobile Edge Computing for the Internet of Vehicles: Offloading Framework and Job Scheduling. IEEE Veh. Technol. Mag. 2019, 14, 28–36. [Google Scholar] [CrossRef]
- Anawar, M.R.; Wang, S.; Zia, M.A.; Jadoon, A.K.; Akram, U.; Raza, S.; Zhang, X. Fog Computing: An Overview of Big IoT Data Analytics. Wirel. Commun. Mob. Comput. 2018, 2018, 7157192. [Google Scholar] [CrossRef]
- Al-Dulaimy, A.; Jansen, M.; Johansson, B.; Trivedi, A.; Iosup, A.; Ashjaei, M.; Galletta, A.; Kimovski, D.; Prodan, R.; Tserpes, K.; et al. The Computing Continuum: From IoT to the Cloud. Internet Things 2024, 27, 101272. [Google Scholar] [CrossRef]
- Búr, M.; Varró, D. Evaluation of distributed query-based monitoring over data distribution service. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 674–679. [Google Scholar]
- Sivanathan, A.; Sherratt, D.; Gharakheili, H.H.; Radford, A.; Wijenayake, C.; Vishwanath, A.; Sivaraman, V. Characterizing and classifying IoT traffic in smart cities and campuses. In Proceedings of the IEEE Conference on Computer Communications Workshops, Atlanta, GA, USA, 1–4 May 2017. [Google Scholar]
- Kammerer, K.; Pryss, R.; Hoppenstedt, B.; Sommer, K.; Reichert, M. Process-Driven and Flow-Based Processing of Industrial Sensor Data. Sensors 2020, 20, 5245. [Google Scholar] [CrossRef] [PubMed]
- Alizadeh MGreenberg, A.; Maltz, D.A.; Padhye, J.; Patel, P.; Prabhakar, B.; Sengupta, S.; Sridharan, M. Datacenter TCP. ACM SIGCOMM Comput. Commun. Rev. 2010, 40, 63–74. [Google Scholar] [CrossRef]
- Li, W.; Zeng, C.; Hu, J.; Chen, K. Towards fine-grained and practical flow control for datacenter networks. In Proceedings of the IEEE 31st International Conference on Network Protocols, Reykjavik, Iceland, 10–13 October 2023. [Google Scholar]
- IEEE 802.1 Qbb-Priority-based Flow Control. Available online: https://1.ieee802.org/dcb/802-1qbb/ (accessed on 21 January 2025).
- Li, Y.; Miao, R.; Liu, H.H.; Zhuang, Y.; Feng, F.; Tang, L.; Cao, Z.; Zhang, M.; Kelly, F.; Alizadeh, M.; et al. Hpcc: High precision congestion control. In Proceedings of the ACM Special Interest Group on Data Communication, Beijing, China, 19–24 August 2019; pp. 44–58. [Google Scholar]
- Mittal, R.; Lam, V.T.; Dukkipati, N.; Blem, E.; Wassel, H.; Ghobadi, M.; Vahdat, A.; Wang, Y.; Wetherall, D.; Zats, D. Timely: Rtt-based Congestion Control for the Datacenter. ACM SIGCOMM Comput. Commun. Rev. 2015, 45, 537–550. [Google Scholar] [CrossRef]
- Al-Fares, M.; Radhakrishnan, S.; Raghavan, B.; Huang, N.; Vahdat, A. Hedera: Dynamic flow scheduling for datacenter networks. In Proceedings of the Networked Systems Design and Implementation, San Jose, CA, USA, 28–30 April 2010. [Google Scholar]
- Tuchin, A.E.; Sasabe, M.; Kasahara, S. A simple algorithm of centralized flow management for datacenters. In Proceedings of the 22nd Asia-Pacific Conference on Communications, Yogyakarta, Indonesia, 25–27 August 2016; pp. 268–273. [Google Scholar]
- He, K.; Rozner, E.; Agarwal, K.; Felter, W.; Carter, J.; Akella, A. Presto: Edge- based load balancing for fast datacenter networks. ACM SIGCOMM Comput. Commun. Rev. 2015, 45, 465–478. [Google Scholar] [CrossRef]
- Vanini, E.; Pan, R.; Alizadeh, M.; Taheri, P.; Edsall, T. Let it flow: Resilient asymmetric load balancing with flowlet switching. In Proceedings the of 14th Symposium on Networked System Design and Implementation, Boston, MA, USA, 27–29 March 2017. [Google Scholar]
- Alizadeh, M.; Edsall, T.; Dharmapurikar, S.; Vaidyanathan, R.; Chu, K.; Fingerhut, A.; Lam, V.T.; Matus, F.; Pan, R.; Yadav, N.; et al. CONGA: Distributed Congestion-Aware Load Balancing for Datacenters. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 503–514. [Google Scholar] [CrossRef]
- Barka, E.; Kerrache, C.; Hussain, R.; Lagraa, N.; Lakas, A.; Bouk, S. Trusted Lightweight Communication Strategy for Flying Named Data Networking. Sensors 2018, 18, 2683. [Google Scholar] [CrossRef]
- Djedouboum, A.C.; Abba Ari, A.A.; Gueroui, A.M.; Mohamadou, A.; Aliouat, Z. Big Data Collection in Large-Scale Wireless Sensor Networks. Sensors 2018, 18, 4474. [Google Scholar] [CrossRef]
- Gusev, M.; Dustdar, S. Going Back to the Roots—The Evolution of Edge Computing: An IoT Perspective. IEEE Internet Comput. 2018, 22, 5–15. [Google Scholar] [CrossRef]
- Saqlain, M.; Piao, M.; Shim, Y.; Lee, J.Y. Framework of an IoT-based Industrial Data Management for Smart Manufacturing. J. Sens. Actuator Netw. 2019, 8, 25. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Bit, S.D. A Secure Fog-Based Architecture for Industrial Internet of Things and Industry 4.0. IEEE Trans. Ind. Inform. 2021, 17, 2316–2324. [Google Scholar] [CrossRef]
- Kim, D.S.; Hoa, T.D.; Thien, H.T. On the Reliability of Industrial Internet of Things from Systematic Perspectives: Evaluation Approaches, Challenges, and Open Issues. IETE Tech. Rev. 2022, 39, 1277–1308. [Google Scholar] [CrossRef]
- Srinivas, J.; Qyser, A.A.M.; Reddy, B.E. Exploiting geo distributed datacenters of a cloud for load balancing. In Proceedings of the IEEE International Advance Computing Conference, Bangalore, India, 12–13 June 2015. [Google Scholar]
- Uddin, M.Y.; Ahmad, S. A review on edge to cloud: Paradigm shift from large datacenters to small centers of data everywhere. In Proceedings of the International Conference on Inventive Computation Technologies, Coimbatore, India, 26–28 February 2020; pp. 318–322. [Google Scholar]
- Dong, Y.; Xu, G.; Ding, Y.; Meng, X.; Zhao, J. ‘Joint-Me’ Task Deployment Strategy for Load Balancing in Edge Computing. IEEE Access 2019, 7, 99658–99669. [Google Scholar] [CrossRef]
- Abughazalah, M.; Alsaggaf, W.; Saifuddin, S.; Sarhan, S. Centralized vs. Decentralized Cloud Computing in Healthcare. Appl. Sci. 2024, 14, 7765. [Google Scholar] [CrossRef]
- Tayyaba, S.; Ashraf, M.W.; Alquthami, T.; Ahmad, Z.; Manzoor, S. Fuzzy-Based Approach Using IoT Devices for Smart Home to Assist Blind People for Navigation. Sensors 2020, 20, 3674. [Google Scholar] [CrossRef]
- Khan, S.A.; Lim, H. Novel Fuzzy Logic Scheme for Push-Based Critical Data Broadcast Mitigation in VNDN. Sensors 2022, 22, 8078. [Google Scholar] [CrossRef]
- Raman, R.; Kumar, V.; Pillai, B.G.; Verma, A.; Rastogi, S.; Meenakshi, R. Integration of fuzzy model with the IOT model to achieve better health (medical) care design system. In Proceedings of the International Conference on Advance Computing and Innovative Technologies in Engineering, Greater Noida, India, 14–15 May 2024; pp. 820–825. [Google Scholar]
- Kait, R.; Kaur, S.; Sharma, P.; Ankita, C.; Kumar, T.; Cheng, X. Fuzzy logic-based Trusted Routing Protocol using Vehicular Cloud Networks for Smart Cities. Expert Syst. 2025, 42, e13561. [Google Scholar] [CrossRef]
- Habib, S.J.; Marimuthu, P.N. Scheduling sensors’ tasks with imprecise timings within wireless sensor networks. In Proceedings of the IEEE Wireless Communication and Networking Conference, Sydney, Australia, 18–21 April 2010. [Google Scholar]
- Habib, S.J.; Marimuthu, P.N. Incorporating imprecise computations in scheduling of aggregated data within wireless sensor networks. In Proceedings of the 24th IEEE International Conference on Advanced Information Networking and Applications Workshops, Perth, Australia, 20–23 April 2010. [Google Scholar]
- Habib, S.J.; Marimuthu, P.N. Data aggregation at the gateways through sensors’ tasks scheduling in wireless sensor networks. IET Wirel. Sens. Syst. 2011, 1, 171–178. [Google Scholar] [CrossRef]
- Habib, S.J.; Marimuthu, P.N. Fuzzy analysis for assessing trust space within wireless sensor networks, information systems and technologies. In In Proceedings of the 10th World Conference on Information Systems and Technologies, Budva, Montenegro, 12–14 April 2022. [Google Scholar]
- Habib, S.J.; Marimuthu, P.N. A Fuzzy Framework for Self-Aware Wireless Sensor Networks. J. Eng. Res. 2023, 11, 68–78. [Google Scholar] [CrossRef]
- Habib, S.J.; Marimuthu, P.N. Self-aware opportunistic transmissions for energy management within wireless sensor networks. In Proceedings of the International Conference on Smart Applications, Communications and Networking, Palapye, Botswana, 12–14 September 2022. [Google Scholar] [CrossRef]
- Gill, P.; Jain, N.; Nagappan, N. Understanding network failures in datacenters: Measurement, analysis, and implications. In Proceedings of the ACM SIGCOMM Conference, Toronto, ON, Canada, 15–19 August 2011. [Google Scholar]














| No. | Output | Forwarding Technique | ||
|---|---|---|---|---|
| 1 | Low | Low | Low | Coarse |
| 2 | Low | Medium | Low | Coarse |
| 3 | Low | High | Low | Coarse |
| 4 | Medium | Low | Medium | Fine |
| 5 | Medium | Medium | Medium | Fine |
| 6 | Medium | High | Medium | Fine |
| 7 | High | Low | High | Fine |
| 8 | High | Medium | High | Fine |
| 9 | High | High | Low | Coarse |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Habib, S.J.; Marimuthu, P.N. Fuzzy-Based Multi-Modal Query-Forwarding in Mini-Datacenters. Computers 2025, 14, 261. https://doi.org/10.3390/computers14070261
Habib SJ, Marimuthu PN. Fuzzy-Based Multi-Modal Query-Forwarding in Mini-Datacenters. Computers. 2025; 14(7):261. https://doi.org/10.3390/computers14070261
Chicago/Turabian StyleHabib, Sami J., and Paulvanna Nayaki Marimuthu. 2025. "Fuzzy-Based Multi-Modal Query-Forwarding in Mini-Datacenters" Computers 14, no. 7: 261. https://doi.org/10.3390/computers14070261
APA StyleHabib, S. J., & Marimuthu, P. N. (2025). Fuzzy-Based Multi-Modal Query-Forwarding in Mini-Datacenters. Computers, 14(7), 261. https://doi.org/10.3390/computers14070261






