Ethereum Smart Contracts Under Scrutiny: A Survey of Security Verification Tools, Techniques, and Challenges
Abstract
1. Introduction
- Classification and Analysis of Smart Contract Verification Methods: We systematically classify verification methods into static analysis, dynamic analysis, formal verification, and hybrid approaches, offering a comprehensive review of their capabilities, benefits, and limitations. The objective of our study is to evaluate and compare these methods in terms of their accuracy, scalability, and practical applications to learn more about their advantages and disadvantages when it comes to detecting vulnerabilities.
- Evaluation of Existing Smart Contract Verification Tools: We perform a comparative analysis of widely used verification tools such as Mythril, Slither, Oyente, Securify, and others, examining their detection accuracy, precision, efficiency, false positive rates, and usability. This analysis emphasizes the strengths and weaknesses of the existing tools and offers recommendations for the use of appropriate verification methods tailored to specific security requirements.
- Identification of Security Challenges in Smart Contracts: We detail the most prevalent and evolving vulnerabilities in Ethereum smart contracts, such as re-entrancy attacks, integer overflows/underflows, front-running, and logical errors. We illustrate the shortcomings of current verification methods and point out opportunities for improvement by presenting an examination of real-world exploit case studies.
- Discussion on the Integration of AI and Machine Learning in Smart Contract Verification: The growing intricacy of smart contracts presents scalability and adaptability issues for conventional verification methods. In this survey, we investigate how cutting-edge AI-driven techniques can improve vulnerability detection, minimize false positives, and improve security assessment automation.
- Future Research Directions and Open Challenges: Our survey proposes critical research challenges that must be addressed to improve the resilience and scalability of verification methods. This involves enhancing automation in formal verification, minimizing computational overhead, incorporating cross-chain security protocols, and creating adaptive verification frameworks that can evolve with the dynamic nature of Ethereum ecosystems.
2. Background
2.1. Blockchain Technology and Ethereum Smart Contracts
2.2. Challenges in Smart Contract Verification
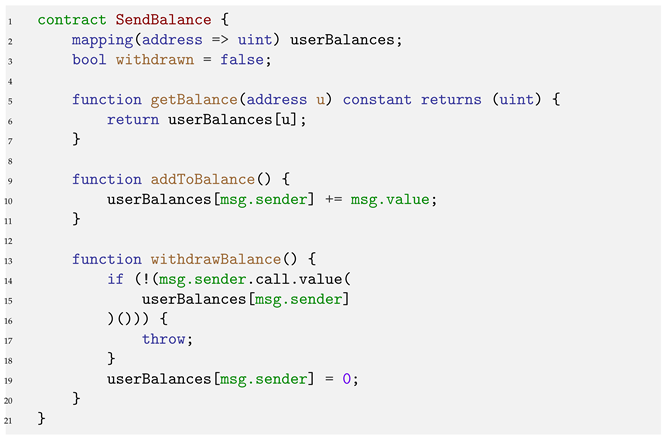
| Listing 1. An example Solidity Contract. The contract implements a simple bank account that contains a re-entrancy bug [22]. |
 |
2.3. Other Blockchain Platforms and Smart Contracts
2.3.1. Hyperledger Fabric
2.3.2. Cardano
3. Systematic Review Methodology
3.1. Research Questions
- RQ1: What are the most significant reviews in the literature that consider the use of formal methods for detecting vulnerabilities in Ethereum smart contracts?
- RQ2: What methods are used to detect vulnerabilities in Ethereum smart contracts?
- RQ3: What tools are available for vulnerability detection in Ethereum smart contracts?
- RQ4: What are the current trends in this area?
- RQ5: What aspects require further attention or research?
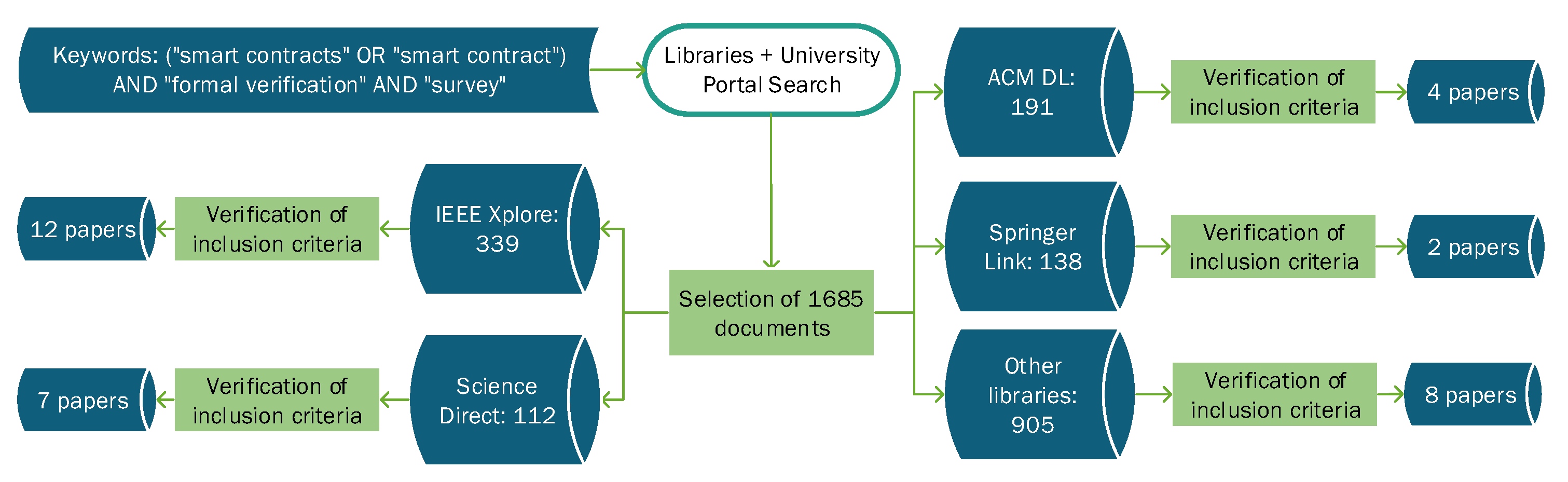
3.2. Search and Queries
3.3. Paper Selection
- Published in English between 2019 and 2024.
- Related to Ethereum smart contracts.
- Related to smart contract vulnerability verification methods and/or tools.
- Review papers, or containing a significant section surveying related work.
3.4. Data Extraction
4. Selected Surveys and Systematic Literature Reviews
4.1. Presentation of Related Surveys
4.2. Trend Synthesis
4.2.1. Emergence of Machine Learning Approaches
4.2.2. Classification of Verification Methods and Evaluation Criteria
4.3. Limitations of Existing Surveys
- Limited Scope of Classification: Many surveys classify verification methods into broad categories but do not provide an exhaustive and in-depth taxonomy. There is a lack of a precise classification taking into account factors such as scalability, accuracy, and practical use.
- Absence of Empirical Evaluation: Although several review studies have addressed smart contract verification technologies and tools, they did not include experimental validation or comparative evaluation. This gap raises questions regarding the effectiveness of these technologies in detecting major and evolving vulnerabilities.
- Overemphasis on Formal Verification: Numerous review studies mainly investigate formal verification methods but overlook hybrid methods that combine static and dynamic analysis to improve security assurance. Since formal verification is costly in terms of computation and demands specialized expertise, a broader viewpoint is necessary to support practical development processes.
- Lack of AI and Machine Learning Integration: Given the growing significance of AI in cybersecurity, the security of smart contracts could utilize advanced learning models. However, only a limited number of studies have explored AI-based techniques to detect vulnerabilities and perform automated security assessments.
- Outdated Coverage of Emerging Threats: Blockchain technology is advancing rapidly, leading to the emergence of security attacks such as cross-chain vulnerabilities, gas optimization exploits, and MEV (Miner Extractable Value) attacks. Numerous current surveys fail to include these recent advancements, rendering their results less applicable to today’s security challenges.
5. Methods for Smart Contract Verification
5.1. Static Analysis
5.1.1. Abstract Interpretation
5.1.2. Control Flow Graphs
5.1.3. Symbolic Execution
5.1.4. Taint Analysis
5.2. Dynamic Analysis
5.2.1. Concolic Testing
5.2.2. Fuzzing
5.2.3. Mutation Testing
5.2.4. Model-Based Testing
5.2.5. Search-Based Testing
5.3. Formal Verification
5.3.1. Model Checking
| Model Checker | References | Performance | Ease of Use |
|---|---|---|---|
| nuXmv [92] | [81,82] | Efficient for small models; state explosion for large ones | Moderate; requires manual abstraction |
| NuSMV [93] | [94,95] | Similar to nuXmv; scalability issues persist | Moderate; manual modeling needed |
| PRISM [96] | [84,98] | High for probabilistic models | Moderate; stochastic abstraction is complex |
| CORRAL [101] | [100] | Efficient for bounded checks; limited scope | Moderate; steep configuration |
| SPIN [102] | [103,104,105] | High accuracy; performance varies with complexity | Moderate; requires PROMELA translation |
| CPN/TCPN Tools | [85,106,107] | Very high accuracy; efficiency drops with complexity | High; intuitive graphical tools |
| BIP Framework [109] | [108,109] | Moderate | Moderate; custom configuration often needed |
| MCMAS [112] | [111] | Efficient for multi-agent models | Moderate; game-theoretic setup required |
| MCK [114] | [113] | Good for atomic swaps | Moderate; tailored for specific cases |
| FDR [116] | [115] | High accuracy in concurrent verification | Low; steep learning curve |
5.3.2. Theorem Proving
| Prover | References | Advantages | Limitations |
|---|---|---|---|
| Isabelle/HOL | [86,88] | Precise higher-order logic formalization; supports code extraction | Limited automation; high manual effort; steep learning curve |
| Coq | [87,117,118] | Supports symbolic execution and certified code extraction | Limited automation; high manual effort; steep learning curve |
| Why3 | [83] | Integrated deductive verification environment | May require rewriting; less mature in smart contracts |
| Event-B | [120] | Enables stepwise refinement for verification | Restricted to a Solidity subset; translation overhead |
5.3.3. Formal Semantic
5.3.4. Refinement-Type Systems
5.4. Machine Learning
5.5. Discussion
5.5.1. Static Analysis
5.5.2. Dynamic Analysis
5.5.3. Formal Verification
5.5.4. Machine Learning
5.5.5. Integrative Approaches
5.5.6. Summary
6. Automatic Tools for Verifying Smart Contracts
6.1. Static Analysis Tools
6.2. Dynamic Analysis Tools
| Tool | Language | Repository | Input |
|---|---|---|---|
| ContractLarva | Haskell | [167] | Solidity |
| ModCon | Javascript | [168] | Solidity |
| Solitor | Java | [169] | Solidity |
| Vultron(ContraMaster) | Javascript | [161,170] | Solidity |
| ContractFuzzer | Go | [171] | Bytecode |
| sFuzz | C++ | [172] | Bytecode |
| SODA | Go | [173] | Bytecode |
| EASYFLOW | Go | [174] | Bytecode or Solidity |
| ECFChecker | Go | [175] | Solidity |
6.3. Tools for Both Static and Dynamic Analysis
6.4. Machine Learning Tools
6.5. Discussion
7. Threats to Validity in the Elaboration of a Survey on Smart Contract Verification Studies
7.1. Construct Validity: Ensuring a Comprehensive and Accurate Representation
7.2. Internal Validity: Minimizing Bias and Ensuring Reliable Inferences
7.3. External Validity: Generalizability and Real-World Applicability
8. Limitations
- Ethereum-Centric Focus: This review mainly concentrates on analysis tools and verification techniques for smart contracts specifically designed for the Ethereum blockchain, which, despite being the most extensively studied platform, does not cover the entire smart contract ecosystem. Other blockchain networks that support smart contracts and have specific verification mechanisms that were not included in this study include Binance Smart Chain (BSC), Solana, Polkadot, Hyperledger Fabric, and Avalanche [50]. Future research should broaden the review’s scope to encompass security analysis frameworks and verification tools across various blockchain platforms. Performing cross-chain analysis might reveal platform-specific limitations and effective strategies for more comprehensive security applications.
- Exclusion of Emerging and Preprint Research: Preprint studies and recently created tools that have not been fully tested in real-world settings are excluded from this review, which primarily concentrates on peer-reviewed publications and well-established technologies. Because blockchain security is developing rapidly, some cutting-edge tools and techniques may not be included in this review. To track and incorporate new advancements as they occur, a systematic living review approach or a continuously updated survey could be used. Additionally, including data from security audit organizations, GitHub repositories, and industry investigations might help maintain a more updated view.
- Limited Discussion on Scalability and Performance of Analysis Tools: While this review discusses a number of smart contract verification techniques, it does not provide a comprehensive evaluation of their scalability or efficiency in managing large-scale smart contract ecosystems, such as gaming platforms or high-frequency DeFi applications that process thousands of transactions per second. Future studies should evaluate existing technologies in real-time blockchain transactions and large-scale deployments [204]. Comparative analysis of execution time, detection accuracy, and processing speed can help developers select the most efficient tools for specific applications.
- Absence of Comprehensive Empirical Evaluation: Many of the techniques under consideration have been tested in controlled academic settings, but little is known about how well they operate in real-world decentralized apps (DApps). The industry’s use of these techniques, false positive rates, and practical implementation remain mostly unexplored. The effectiveness of these techniques may be verified by collaborating with blockchain security companies and conducting real-world case studies on deployed smart contracts [201]. Engaging with developers, security auditors, and industry experts can help to further link scholarly research with real-world applications.
- Challenges in Formal Verification Adoption: Even though formal verification techniques offer a high level of assurance regarding the accuracy of smart contracts, their use is still limited due to their complexity, extensive demand on time, and formal method knowledge requirements. Automation-based formal verification techniques that facilitate the verification process for non-experts should be the focus of future research. Adoption and accessibility may be enhanced by the application of AI-driven theorem proving and user-friendly formal verification systems.
- Ongoing Evolution of Smart Contract Standards and Attack Vectors: The security landscape of smart contracts is always changing, as new vulnerabilities and attack vectors appear. Techniques and resources that are useful now might become outdated as malicious actors develop more advanced attack methods. To address this issue, it can be helpful to constantly track evolving attack patterns and develop adaptable security systems that use AI to identify vulnerabilities automatically. Security will be further enhanced by establishing collaborations between industry and academia to maintain an up-to-date database of vulnerabilities and best practices.
- Lack of Comprehensive Evaluation Metrics for Security Tools: Existing smart contract verification tools employ various methodologies and assessment metrics, making it more difficult to compare their effectiveness objectively. Creating standardized assessment metrics for security tools, like detection accuracy, false positive/negative rates, computational efficiency, and scalability, would improve the comparison and choice of tools. A publicly maintained benchmark dataset for verifying smart contracts could enhance reproducibility in research efforts.
9. Conclusions and Future Research Directions
- Standardized Evaluation and Benchmark Development: Future work should focus on defining consistent evaluation metrics, such as detection accuracy, false positive/false negative rates, resource consumption, and scalability, to enable reproducible and tool-agnostic comparisons. Furthermore, developing standardized benchmark datasets that include real-world contracts and a diverse range of vulnerabilities will be essential to comprehensively assess the effectiveness of smart contract verification tools and guide their improvement.
- Graph-Based Approaches: Smart contract security can benefit from advanced graph-based learning techniques, which have been shown to be effective in various domains [205,206]. Future tools should integrate Graph Neural Networks (GNNs) and Large Language Models (LLMs), which leverage vast amounts of textual and code data, to detect complex vulnerabilities by correlating static code structures with runtime anomalies.
- Explainable AI (XAI) for Smart Contract Verification: Numerous AI-driven security solutions operate as black-box systems, which hinders their trustworthiness and acceptance. Incorporating explainable AI (XAI) methods [207], such as SHAP (Shapley Additive Explanations) and LIME (Local Interpretable Model-Agnostic Explanations) with interactive visualization dashboards, will improve transparency and foster trust among developers and auditors.
- Comparative Platform Analysis: Future research should conduct a systematic comparative study of major blockchain platforms: Ethereum, Hyperledger Fabric, Cardano, and others, examining their trust models (permissionless versus permissioned architectures), consensus mechanisms (for example, Ethereum’s PoS post Merge versus Hyperledger Fabric’s pluggable PBFT/Raft and Cardano’s Ouroboros PoS), and tool ecosystems (availability of DSL, formal verification frameworks, and auditing toolchains). Such a study would illuminate how platform-specific design choices affect security guarantees, developer ergonomics, and regulatory compliance [208].
- Cross-Platform Smart Contract Security and Verification Frameworks: Future research must expand beyond Ethereum/Solidity to encompass diverse blockchain environments (Binance Smart Chain, Polkadot, Solana, Cardano, and Hyperledger Fabric), each demanding customized security and verification methods. The following research directions will require interdisciplinary approaches, combining blockchain-specific insights with advances in AI and distributed systems:
- –
- –
- Cardano (Marlowe and Plutus): Leverage Marlowe’s DSL designed for financial contracts, which incorporates formal semantics and enables rigorous static analysis through the Marlowe Playground’s SMT-based verification to ensure financial invariants [210,211]. In addition, efforts should explore the formal verification of Plutus smart contracts, address stake-based vulnerabilities, and optimize gas usage in its layered architecture.
- –
- –
- Polkadot (ink!): Build with cargo contract and verify bytecode through the Sirato service, ensuring reproducible audit logs, and adhere to on-chain governance and key management guidelines [214].
- –
- Binance Smart Chain: Adapt Mythril and Slither to cover EVM vulnerabilities with low false positives.
- –
- Cross-Chain: Adopt unified benchmarks and metadata schemas (e.g., Chainlink CCIP) and shared test suites to secure end-to-end multi-chain DApps [215].
- Domain-Specific Languages for Secure Contracts:Emerging DSLs such as Marlowe and Plutus (Cardano) and Scilla (Zilliqa) offer significant promise for enhancing smart contract security. These languages, grounded in functional or formally verified paradigms, provide features such as formal termination guarantees, strong static-type systems, and integrated verification frameworks [216]. By design, they aim to eliminate broad classes of vulnerabilities common in general-purpose languages like Solidity. Although not comprehensive solutions, these DSLs represent viable and increasingly practical approaches to mitigating security risks. Future research should empirically evaluate their security guarantees, expressiveness, and usability compared to their general-purpose counterparts. Furthermore, the development of automated translation tools between DSLs and mainstream languages and the ability to verify formal cross-language verification constitute a valuable direction to advance secure blockchain development.
- Formal Verification Adaptability in Multi-Chain Environments: As blockchain ecosystems evolve toward interoperability and cross-chain functionality, formal verification approaches must be re-evaluated in light of diverse consensus models, runtime semantics, and language paradigms. Future work should focus on developing cross-platform benchmarks to evaluate existing frameworks (for example, the K framework and the compositional semantics of DAML), optimizing abstraction layers for computational efficiency, and integrating AI-driven techniques to automate specification synthesis. Such efforts will improve formal verification scalability and applicability, ensuring robust security for interoperable decentralized applications in DeFi and beyond.
- Real-World Empirical Validation: Many existing verification methods are tested in controlled environments rather than in real-world decentralized applications (DApps). Future research should collaborate with the blockchain security organizational industry to evaluate verification tools in smart contracts deployed, measuring their effectiveness under real-world conditions.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Bhutta, M.N.M.; Khwaja, A.A.; Nadeem, A.; Ahmad, H.F.; Khan, M.K.; Hanif, M.A.; Song, H.; Alshamari, M.; Cao, Y. A Survey on Blockchain Technology: Evolution, Architecture and Security. IEEE Access 2021, 9, 61048–61073. [Google Scholar] [CrossRef]
- Hasan, D.; Driss, M. SUBLμME: Secure blockchain as a service and microservices-based framework for IoT environments. In Proceedings of the 2021 IEEE/ACS 18th International Conference on Computer Systems and Applications (AICCSA), Tangier, Morocco, 30 November–3 December 2021; pp. 1–9. [Google Scholar]
- Sadad, A.; Khan, M.A.; Ghaleb, B.; Khan, F.A.; Driss, M.; Boulila, W.; Ahmad, J. Distributed twins in edge computing: Blockchain and IOTA. In Proceedings of the 2023 International Wireless Communications and Mobile Computing (IWCMC), Marrakesh, Morocco, 19–23 June 2023; pp. 327–332. [Google Scholar]
- Abbas, S.M.A.; Khan, M.A.; Boulila, W.; Kouba, A.; Khan, M.S.; Ahmad, J. UAVs and Blockchain Synergy: Enabling Secure Reputation-based Federated Learning in Smart Cities. IEEE Access 2024, 12, 154053. [Google Scholar]
- Wadhwa, S.; Gupta, D.; Rani, S.; Driss, M.; Boulila, W. Empowering drones in vehicular network through fog computing and blockchain technology. PLoS ONE 2025, 20, e0314420. [Google Scholar] [CrossRef] [PubMed]
- Hewa, T.M.; Hu, Y.; Liyanage, M.; Kanhare, S.S.; Ylianttila, M. Survey on blockchain-based smart contracts: Technical aspects and future research. IEEE Access 2021, 9, 87643–87662. [Google Scholar] [CrossRef]
- Flipside Crypto. Flipside|The Platform for Intelligent Blockchain Growth. 2024. Available online: https://flipsidecrypto.xyz/ (accessed on 1 May 2024).
- Mehar, M.I.; Shier, C.L.; Giambattista, A.; Gong, E.; Fletcher, G.; Sanayhie, R.; Kim, H.M.; Laskowski, M. Understanding a revolutionary and flawed grand experiment in blockchain: The DAO attack. J. Cases Inf. Technol. 2019, 21, 19–32. [Google Scholar] [CrossRef]
- Palladino, S. The Parity Wallet Hack Explained. July 2017. Available online: https://blog.openzeppelin.com/on-the-parity-wallet-multisig-hack-405a8c12e8f7 (accessed on 30 May 2025).
- Ramos, S.; Pianese, F.; Leach, T.; Oliveras, E. A great disturbance in the crypto: Understanding cryptocurrency returns under attacks. Blockchain Res. Appl. 2021, 2, 100021. [Google Scholar] [CrossRef]
- Bernauer, A.; Faro, S.; Hämmerle, R.; Huschenbett, M.; Kiefer, M.; Lochbihler, A.; Mäki, J.; Mazzoli, F.; Meier, S.; Mitchell, N.; et al. Daml: A smart contract language for securely automating real-world multi-party business workflows. arXiv 2023, arXiv:2303.03749. [Google Scholar]
- Al-Azzoni, I.; Iqbal, S. Access Control Verification in Smart Contracts Using Colored Petri Nets. Computers 2024, 13, 274. [Google Scholar] [CrossRef]
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. ISO: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/27001 (accessed on 30 May 2025).
- American Institute of Certified Public Accountants. 2017 Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy (With Revised Points of Focus—2022). AICPA, 2022. Available online: https://www.aicpa-cima.com/resources/download/2017-trust-services-criteria-with-revised-points-of-focus-2022 (accessed on 30 May 2025).
- National Institute of Standards and Technology. Security and Privacy Controls for Information Systems and Organizations. NIST Special Publication 800-53, Revision 5; September 2020. Available online: https://doi.org/10.6028/NIST.SP.800-53r5 (accessed on 30 May 2025).
- Rozario, A.M.; Vasarhelyi, M.A. Auditing with Smart Contracts. Int. J. Digit. Account. Res. 2018, 18, 1–27. [Google Scholar] [CrossRef]
- Malatji, M. Management of enterprise cyber security: A review of ISO/IEC 27001: 2022. In Proceedings of the 2023 International Conference on Cyber Management and Engineering (CyMaEn), Bangkok, Thailand, 26–27 January 2023; pp. 117–122. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://assets.pubpub.org/d8wct41f/31611263538139.pdf (accessed on 30 May 2025).
- Buterin, V. A Next-Generation Smart Contract and Decentralized Application Platform. White Paper. 2014. Available online: https://blockchainlab.com/pdf/Ethereum_white_paper-a_next_generation_smart_contract_and_decentralized_application_platform-vitalik-buterin.pdf (accessed on 30 May 2025).
- Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In Proceedings of the Principles of Security and Trust: 6th International Conference, POST 2017, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2017, Uppsala, Sweden, 22–29 April 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 164–186. [Google Scholar]
- Nikolić, I.; Kolluri, A.; Sergey, I.; Saxena, P.; Hobor, A. Finding the greedy, prodigal, and suicidal contracts at scale. In Proceedings of the 34th Annual Computer Security Applications Conference, San Juan, PR, USA, 3–7 December 2018; pp. 653–663. [Google Scholar]
- Luu, L.; Chu, D.H.; Olickel, H.; Saxena, P.; Hobor, A. Making smart contracts smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 254–269. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Kiayias, A.; Russell, A.; David, B.; Oliynykov, R. Ouroboros: A provably secure proof-of-stake blockchain protocol. In Proceedings of the 37th International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 357–388. [Google Scholar]
- Cardano Documentation. Plutus Smart Contracts. 2025. Available online: https://docs.cardano.org/developer-resources/smart-contracts/plutus (accessed on 12 May 2025).
- Kitchenham, B. Procedures for performing systematic reviews. Keele UK Keele Univ. 2004, 33, 1–26. [Google Scholar]
- Liu, J.; Liu, Z. A survey on security verification of blockchain smart contracts. IEEE Access 2019, 7, 77894–77904. [Google Scholar] [CrossRef]
- Praitheeshan, P.; Pan, L.; Yu, J.; Liu, J.; Doss, R. Security analysis methods on Ethereum smart contract vulnerabilities: A survey. arXiv 2019, arXiv:1908.08605. [Google Scholar]
- Rouhani, S.; Deters, R. Security, performance, and applications of smart contracts: A systematic survey. IEEE Access 2019, 7, 50759–50779. [Google Scholar] [CrossRef]
- Murray, Y.; Anisi, D.A. Survey of formal verification methods for smart contracts on blockchain. In Proceedings of the 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Island, Spain, 24–26 June 2019; pp. 1–6. [Google Scholar]
- Di Angelo, M.; Salzer, G. A survey of tools for analyzing ethereum smart contracts. In Proceedings of the 2019 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPCON), Newark, CA, USA, 4–9 April 2019; pp. 69–78. [Google Scholar]
- Tolmach, P.; Li, Y.; Lin, S.W.; Liu, Y.; Li, Z. A survey of smart contract formal specification and verification. ACM Comput. Surv. 2021, 54, 1–38. [Google Scholar] [CrossRef]
- Hu, B.; Zhang, Z.; Liu, J.; Liu, Y.; Yin, J.; Lu, R.; Lin, X. A Comprehensive Survey on Smart Contract Construction and Execution: Paradigms, Tools and Systems. arXiv 2020, arXiv:2008.13413. [Google Scholar] [CrossRef] [PubMed]
- Imeri, A.; Agoulmine, N.; Khadraoui, D. Smart Contract modeling and verification techniques: A survey. In Proceedings of the 8th International Workshop on ADVANCEs in ICT Infrastructures and Services, Cancun, Mexico, 27–29 January 2020; pp. 1–8. [Google Scholar]
- Wang, Z.; Jin, H.; Dai, W.; Choo, K.K.R.; Zou, D. Ethereum smart contract security research: Survey and future research opportunities. Front. Comput. Sci. 2020, 15, 152802. [Google Scholar] [CrossRef]
- Almakhour, M.; Sliman, L.; Samhat, A.E.; Mellouk, A. Verification of smart contracts: A survey. Pervasive Mob. Comput. 2020, 67, 101227. [Google Scholar] [CrossRef]
- Munir, S.; Taha, W. Pre-deployment Analysis of Smart Contracts—A Survey. arXiv 2023, arXiv:2301.06079. [Google Scholar]
- Qian, P.; Liu, Z.; He, Q.; Huang, B.; Tian, D.; Wang, X. Smart contract vulnerability detection technique: A survey. arXiv 2022, arXiv:2209.05872. [Google Scholar]
- Kushwaha, S.S.; Joshi, S.; Singh, D.; Kaur, M.; Lee, H.N. Systematic review of security vulnerabilities in ethereum blockchain smart contract. IEEE Access 2022, 10, 6605–6621. [Google Scholar] [CrossRef]
- Kushwaha, S.S.; Joshi, S.; Singh, D.; Kaur, M.; Lee, H.N. Ethereum smart contract analysis tools: A systematic review. IEEE Access 2022, 10, 57037–57062. [Google Scholar] [CrossRef]
- Piantadosi, V.; Rosa, G.; Placella, D.; Scalabrino, S.; Oliveto, R. Detecting functional and security-related issues in smart contracts: A systematic literature review. Softw. Pract. Exp. 2023, 53, 465–495. [Google Scholar] [CrossRef]
- Rameder, H.; Di Angelo, M.; Salzer, G. Review of automated vulnerability analysis of smart contracts on Ethereum. Front. Blockchain 2022, 5, 814977. [Google Scholar] [CrossRef]
- Zhou, H.; Milani Fard, A.; Makanju, A. The state of ethereum smart contracts security: Vulnerabilities, countermeasures, and tool support. J. Cybersecur. Priv. 2022, 2, 358–378. [Google Scholar] [CrossRef]
- Ndiaye, M.; Konate, K. Security Strengths and Weaknesses of Blockchain Smart Contract System: A Survey. Int. J. Inf. Commun. Eng. 2022, 16, 134–143. [Google Scholar]
- Marijan, D.; Lal, C. Blockchain verification and validation: Techniques, challenges, and research directions. Comput. Sci. Rev. 2022, 45, 100492. [Google Scholar] [CrossRef]
- Huang, Y.; Bian, Y.; Li, R.; Zhao, J.L.; Shi, P. Smart contract security: A software lifecycle perspective. IEEE Access 2019, 7, 150184–150202. [Google Scholar] [CrossRef]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart contract: Attacks and protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Tang, X.; Zhou, K.; Cheng, J.; Li, H.; Yuan, Y. The vulnerabilities in smart contracts: A survey. In Proceedings of the Advances in Artificial Intelligence and Security: 7th International Conference, ICAIS 2021, Dublin, Ireland, 19–23 July 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 177–190. [Google Scholar]
- Chen, H.; Pendleton, M.; Njilla, L.; Xu, S. A survey on ethereum systems security: Vulnerabilities, attacks, and defenses. ACM Comput. Surv. 2020, 53, 1–43. [Google Scholar] [CrossRef]
- Vacca, A.; Di Sorbo, A.; Visaggio, C.A.; Canfora, G. A systematic literature review of blockchain and smart contract development: Techniques, tools, and open challenges. J. Syst. Softw. 2021, 174, 110891. [Google Scholar] [CrossRef]
- Fekih, R.B.; Lahami, M.; Jmaiel, M.; Bradai, S. Formal Verification of Smart Contracts Based on Model Checking: An Overview. In Proceedings of the 2023 IEEE International Conference on Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE), Paris, France, 14–16 December 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Khan, Z.A.; Namin, A.S. A Survey of Vulnerability Detection Techniques by Smart Contract Tools. IEEE Access 2024, 12, 70870–70910. [Google Scholar] [CrossRef]
- Zhu, H.; Yang, L.; Wang, L.; Sheng, V.S. A Survey on Security Analysis Methods of Smart Contracts. IEEE Trans. Serv. Comput. 2024, 17, 4522–4539. [Google Scholar] [CrossRef]
- Deng, Y.; Wang, L.; Wang, L.; Li, J.; Yong, Q. A Survey on Automatic Discover Approach by Using Static Analysis for Smart Contract Vulnerability. In Proceedings of the 2023 International Conference on Networking and Network Applications (NaNA), Qingdao, China, 18–21 August 2023; pp. 163–168. [Google Scholar] [CrossRef]
- Vidal, F.R.; Ivaki, N.; Laranjeiro, N. Vulnerability detection techniques for smart contracts: A systematic literature review. J. Syst. Softw. 2024, 217, 112160. [Google Scholar] [CrossRef]
- Wu, H.; Peng, Y.; He, Y.; Fan, J. A Review of Deep Learning-Based Vulnerability Detection Tools for Ethernet Smart Contracts. CMES-Comput. Model. Eng. Sci. 2024, 140, 1. [Google Scholar] [CrossRef]
- Olivieri, L.; Spoto, F. Software verification challenges in the blockchain ecosystem. Int. J. Softw. Tools Technol. Transf. 2024, 26, 431–444. [Google Scholar] [CrossRef]
- Elakaş, A.; Sözer, H.; Şafak, I.; Kalkan, K. A systematic mapping on software testing for blockchains. Clust. Comput. 2024, 27, 7111–7126. [Google Scholar] [CrossRef]
- Garfatta, I.; Klai, K.; Gaaloul, W.; Graiet, M. A Survey on Formal Verification for Solidity Smart Contracts. In Proceedings of the 2021 Australasian Computer Science Week Multiconference, Dunedin, New Zealand, 1–5 February 2021. [Google Scholar] [CrossRef]
- Jiao, T.; Xu, Z.; Qi, M.; Wen, S.; Xiang, Y.; Nan, G. A survey of ethereum smart contract security: Attacks and detection. Distrib. Ledger Technol. Res. Pract. 2024, 3, 1–28. [Google Scholar] [CrossRef]
- Cousot, P.; Cousot, R. Abstract interpretation: A unified lattice model for static analysis of programs by construction or approximation of fixpoints. In Proceedings of the 4th ACM SIGACT-SIGPLAN Symposium on Principles of Programming Languages, Los Angeles, CA, USA, 17–19 January 1977; pp. 238–252. [Google Scholar]
- Tsankov, P.; Dan, A.; Drachsler-Cohen, D.; Gervais, A.; Buenzli, F.; Vechev, M. Securify: Practical security analysis of smart contracts. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 67–82. [Google Scholar]
- Pasqua, M.; Benini, A.; Contro, F.; Crosara, M.; Dalla Preda, M.; Ceccato, M. Enhancing Ethereum smart-contracts static analysis by computing a precise Control-Flow Graph of Ethereum bytecode. J. Syst. Softw. 2023, 200, 111653. [Google Scholar] [CrossRef]
- King, J.C. Symbolic execution and program testing. Commun. ACM 1976, 19, 385–394. [Google Scholar] [CrossRef]
- Feist, J.; Mounier, L.; Bardin, S.; David, R.; Potet, M.L. Finding the needle in the heap: Combining static analysis and dynamic symbolic execution to trigger use-after-free. In Proceedings of the 6th Workshop on Software Security, Protection, and Reverse Engineering, Los Angeles, CA, USA, 5–6 December 2016; pp. 1–12. [Google Scholar]
- Tripp, O.; Pistoia, M.; Fink, S.J.; Sridharan, M.; Weisman, O. TAJ: Effective taint analysis of web applications. ACM Sigplan Not. 2009, 44, 87–97. [Google Scholar] [CrossRef]
- Bose, P.; Das, D.; Chen, Y.; Feng, Y.; Kruegel, C.; Vigna, G. Sailfish: Vetting smart contract state-inconsistency bugs in seconds. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 23–25 May 2022; pp. 161–178. [Google Scholar]
- Sen, K. Concolic testing. In Proceedings of the 22nd IEEE/ACM International Conference on Automated Software Engineering, Atlanta, GA, USA, 5–9 November 2007; pp. 571–572. [Google Scholar]
- Wang, S.J.; Yao, J.; Pei, K.; Takahashi, H.; Yang, J. Detecting Buggy Contracts via Smart Testing. arXiv 2024, arXiv:2409.04597. [Google Scholar]
- Sutton, M.; Greene, A.; Amini, P. Fuzzing: Brute Force Vulnerability Discovery; Pearson Education: London, UK, 2007; ISBN 978-0-321-44611-4. [Google Scholar]
- Shou, C.; Liu, J.; Lu, D.; Sen, K. Llm4fuzz: Guided fuzzing of smart contracts with large language models. arXiv 2024, arXiv:2401.11108. [Google Scholar]
- DeMillo, R.A.; Lipton, R.J.; Sayward, F.G. Hints on test data selection: Help for the practicing programmer. Computer 1978, 11, 34–41. [Google Scholar] [CrossRef]
- Petrović, G.; Ivanković, M.; Fraser, G.; Just, R. Does mutation testing improve testing practices? In Proceedings of the 2021 IEEE/ACM 43rd International Conference on Software Engineering (ICSE), Madrid, Spain, 25–28 May 2021; pp. 910–921. [Google Scholar]
- Liu, Y.; Li, Y.; Lin, S.W.; Yan, Q. ModCon: A model-based testing platform for smart contracts. In Proceedings of the 28th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering, Virtual Event, 8–13 November 2020; pp. 1601–1605. [Google Scholar]
- Suvorov, D.; Ulyantsev, V. Smart contract design meets state machine synthesis: Case studies. arXiv 2019, arXiv:1906.02906. [Google Scholar]
- Liu, S.; Xu, Y.; Yang, X.; Hui, B.; Hu, F. Variable-State-Trigger: A Formal Model of Smart Contracts Based on Conditional Response and Finite State Automata and Its Application. Electronics 2024, 13, 4680. [Google Scholar] [CrossRef]
- Xu, H.; Fan, J.; Han, L. Smart contract vulnerability detection based on adaptive genetic algorithm. In Proceedings of the Fourth International Conference on Applied Mathematics, Modelling, and Intelligent Computing (CAMMIC 2024), Kaifeng, China, 3–5 May 2024; Volume 13219, pp. 978–984. [Google Scholar]
- Driessen, S.; Di Nucci, D.; Monsieur, G.; Tamburri, D.A.; Heuvel, W.J.v.d. Automated test-case generation for solidity smart contracts: The AGSolT approach and its evaluation. arXiv 2021, arXiv:2102.08864. [Google Scholar]
- Dijkstra, E.W. The humble programmer. Commun. ACM 1972, 15, 859–866. [Google Scholar] [CrossRef]
- Matsuo, S. How formal analysis and verification add security to blockchain-based systems. In Proceedings of the 2017 Formal Methods in Computer Aided Design (FMCAD), Vienna, Austria, 2–6 October 2017; pp. 1–4. [Google Scholar]
- Mavridou, A.; Laszka, A. Tool demonstration: Fsolidm for designing secure ethereum smart contracts. In Proceedings of the Principles of Security and Trust: 7th International Conference, POST 2018, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2018, Thessaloniki, Greece, 14–20 April 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 270–277. [Google Scholar]
- Mavridou, A.; Laszka, A.; Stachtiari, E.; Dubey, A. VeriSolid: Correct-by-design smart contracts for Ethereum. In Proceedings of the Financial Cryptography and Data Security: 23rd International Conference, FC 2019, Frigate Bay, St. Kitts and Nevis, 18–22 February 2019; Revised Selected Papers 23. Springer: Berlin/Heidelberg, Germany, 2019; pp. 446–465. [Google Scholar]
- Nehaï, Z.; Bobot, F. Deductive proof of industrial smart contracts using Why3. In Proceedings of the Formal Methods. FM 2019 International Workshops, Porto, Portugal, 7–11 October 2019; Revised Selected Papers, Part I 3. Springer: Berlin/Heidelberg, Germany, 2020; pp. 299–311. [Google Scholar]
- Bao, T.; Liu, Y. A privacy-preserving framework for smart contracts based on stochastic model checking. In Proceedings of the 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Shenyang, China, 20–22 October 2021; pp. 460–467. [Google Scholar]
- Duo, W.; Xin, H.; Xiaofeng, M. Formal analysis of smart contract based on colored petri nets. IEEE Intell. Syst. 2020, 35, 19–30. [Google Scholar] [CrossRef]
- Amani, S.; Bégel, M.; Bortin, M.; Staples, M. Towards verifying ethereum smart contract bytecode in Isabelle/HOL. In Proceedings of the 7th ACM SIGPLAN International Conference on Certified Programs and Proofs, Los Angeles, CA, USA, 8–9 January 2018; pp. 66–77. [Google Scholar]
- Annenkov, D.; Spitters, B. Towards a smart contract verification framework in Coq. arXiv 2019, arXiv:1907.10674. [Google Scholar]
- Hirai, Y. eth-isabelle: Formalising the Ethereum Virtual Machine in Isabelle/HOL. 2017. Available online: https://github.com/pirapira/eth-isabelle (accessed on 20 September 2024).
- Emerson, E.A. The beginning of model checking: A personal perspective. In 25 Years of Model Checking; Springer: Berlin/Heidelberg, Germany, 2008; pp. 27–45. [Google Scholar]
- Baier, C.; Katoen, J.P. Principles of Model Checking; MIT Press: Cambridge, MA, USA, 2008. [Google Scholar]
- Mavridis, A. FSolidM/VeriSolid Framework. Available online: https://github.com/anmavrid/smart-contracts (accessed on 8 February 2024).
- Cavada, R.; Cimatti, A.; Dorigatti, M.; Griggio, A.; Mariotti, A.; Micheli, A.; Mover, S.; Roveri, M.; Tonetta, S. The nuXmv symbolic model checker. In Proceedings of the Computer Aided Verification: 26th International Conference, CAV 2014, Held as Part of the Vienna Summer of Logic, VSL 2014, Vienna, Austria, 18–22 July 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 334–342. [Google Scholar]
- Cimatti, A.; Clarke, E.; Giunchiglia, F.; Roveri, M. NuSMV: A new symbolic model checker. Int. J. Softw. Tools Technol. Transf. 2000, 2, 410–425. [Google Scholar] [CrossRef]
- Nehai, Z.; Piriou, P.Y.; Daumas, F. Model-checking of smart contracts. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 980–987. [Google Scholar]
- Unal, D.; Hammoudeh, M.; Kiraz, M.S. Policy specification and verification for blockchain and smart contracts in 5G networks. ICT Express 2020, 6, 43–47. [Google Scholar] [CrossRef]
- Kwiatkowska, M.; Norman, G.; Parker, D. PRISM: Probabilistic symbolic model checker. In Proceedings of the 12th International Conference on Modelling Techniques and Tools for Computer Performance Evaluation, London, UK, 14–17 April 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 200–204. [Google Scholar]
- Mazurek, L. ethver: Ethereum Smart Contract Versioning Tool. Available online: https://github.com/lukmaz/ethver (accessed on 24 February 2024).
- Mazurek, Ł. EthVer: Formal verification of randomized Ethereum smart contracts. In Proceedings of the Financial Cryptography and Data Security. FC 2021 International Workshops: CoDecFin, DeFi, VOTING, and WTSC, Virtual Event, 5 March 2021; Revised Selected Papers 25. Springer: Berlin/Heidelberg, Germany, 2021; pp. 364–380. [Google Scholar]
- Microsoft. VeriSol: Formal Verification for Solidity Smart Contracts. Available online: https://github.com/microsoft/verisol (accessed on 25 February 2024).
- Wang, Y.; Lahiri, S.K.; Chen, S.; Pan, R.; Dillig, I.; Born, C.; Naseer, I. Formal specification and verification of smart contracts for Azure blockchain. arXiv 2018, arXiv:1812.08829. [Google Scholar]
- Lal, A.; Qadeer, S.; Lahiri, S.K. A solver for reachability modulo theories. In Proceedings of the Computer Aided Verification: 24th International Conference, CAV 2012, Berkeley, CA, USA, 7–13 July 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 427–443. [Google Scholar]
- Ben-Ari, M. Principles of the Spin Model Checker; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Bai, X.; Cheng, Z.; Duan, Z.; Hu, K. Formal modeling and verification of smart contracts. In Proceedings of the 2018 7th International Conference on Software and Computer Applications, Kuantan, Malaysia, 8–10 February 2018; pp. 322–326. [Google Scholar]
- Yang, Z.; Dai, M.; Guo, J. Formal modeling and verification of smart contracts with SPIN. Electronics 2022, 11, 3091. [Google Scholar] [CrossRef]
- Osterland, T.; Rose, T. Model checking smart contracts for ethereum. Pervasive Mob. Comput. 2020, 63, 101129. [Google Scholar] [CrossRef]
- Liu, Z.; Liu, J. Formal verification of blockchain smart contract based on colored petri net models. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; Volume 2, pp. 555–560. [Google Scholar]
- He, Y.; Dong, H.; Wang, R.; Wu, H. Formal Verification of Smart Contract Based on Timed Colored Petri Net. In Proceedings of the 2022 11th International Conference on Networks, Communication and Computing, Beijing, China, 9–11 December 2022; pp. 321–327. [Google Scholar]
- Abdellatif, T.; Brousmiche, K.L. Formal verification of smart contracts based on users and blockchain behaviors models. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–5. [Google Scholar]
- Basu, A.; Bozga, M.; Sifakis, J. Modeling heterogeneous real-time components in BIP. In Proceedings of the Fourth IEEE International Conference on Software Engineering and Formal Methods (SEFM’06), Pune, India, 11–15 September 2006; pp. 3–12. [Google Scholar]
- Maksimov, D.; Yakimov, I.; Kuznetsov, A. Statistical model checking for blockchain-based applications. In Proceedings of the IOP Conference Series: Materials Science and Engineering, Krasnoyarsk, Russia, 18–21 November 2019; IOP Publishing: Bristol, UK, 2020; Volume 734, p. 012152. [Google Scholar]
- Nam, W.; Kil, H. Formal verification of blockchain smart contracts via atl model checking. IEEE Access 2022, 10, 8151–8162. [Google Scholar] [CrossRef]
- Lomuscio, A.; Raimondi, F. MCMAS: A model checker for multi-agent systems. In Proceedings of the International Conference on Tools and Algorithms for the Construction and Analysis of Systems, Vienna, Austria, 25 March–2 April 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 450–454. [Google Scholar]
- van der Meyden, R. On the specification and verification of atomic swap smart contracts. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Republic of Korea, 14–17 May 2019; pp. 176–179. [Google Scholar]
- Gammie, P.; Van Der Meyden, R. MCK: Model checking the logic of knowledge. In Proceedings of the Computer Aided Verification: 16th International Conference, CAV 2004, Boston, MA, USA, 13–17 July 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 479–483. [Google Scholar]
- Qu, M.; Huang, X.; Chen, X.; Wang, Y.; Ma, X.; Liu, D. Formal verification of smart contracts from the perspective of concurrency. In Proceedings of the Smart Blockchain: First International Conference, SmartBlock 2018, Tokyo, Japan, 10–12 December 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 32–43. [Google Scholar]
- FDR2 User Manual. Failures-Divergence Refinement. 2010. Available online: http://www.cs.ox.ac.uk/projects/concurrency-tools/download/fdr2manual-2.94.pdf (accessed on 30 May 2025).
- Annenkov, D.; Milo, M.; Nielsen, J.B.; Spitters, B. Extracting Smart Contracts Tested and Verified in Coq. In Proceedings of the 10th ACM SIGPLAN International Conference on Certified Programs and Proofs, New York, NY, USA, 17–19 January 2021; pp. 105–121. [Google Scholar] [CrossRef]
- Yang, Z.; Lei, H.; Qian, W. A hybrid formal verification system in coq for ensuring the reliability and security of ethereum-based service smart contracts. IEEE Access 2020, 8, 21411–21436. [Google Scholar] [CrossRef]
- Yang, Z.; Lei, H. Fether: An extensible definitional interpreter for smart-contract verifications in coq. IEEE Access 2019, 7, 37770–37791. [Google Scholar] [CrossRef]
- Zhu, J.; Hu, K.; Filali, M.; Bodeveix, J.P.; Talpin, J.P.; Cao, H. Formal simulation and verification of solidity contracts in event-b. In Proceedings of the 2021 IEEE 45th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 12–16 July 2021; pp. 1309–1314. [Google Scholar]
- Jiao, J.; Lin, S.W.; Sun, J. A Generalized Formal Semantic Framework for Smart Contracts. In Proceedings of the Fundamental Approaches to Software Engineering (FASE), Dublin, Ireland, 25–30 April 2020; Volume 20, pp. 75–96. [Google Scholar]
- Tan, B.; Mariano, B.; Lahiri, S.K.; Dillig, I.; Feng, Y. SolType: Refinement types for arithmetic overflow in solidity. Proc. ACM Program. Lang. 2022, 6, 1–29. [Google Scholar] [CrossRef]
- Jiang, F.; Chao, K.; Xiao, J.; Liu, Q.; Gu, K.; Wu, J.; Cao, Y. Enhancing smart-contract security through machine learning: A survey of approaches and techniques. Electronics 2023, 12, 2046. [Google Scholar] [CrossRef]
- Leroy, X.; Blazy, S.; Kästner, D.; Schommer, B.; Pister, M.; Ferdinand, C. CompCert-a formally verified optimizing compiler. In Proceedings of the ERTS 2016: Embedded Real Time Software and Systems, 8th European Congress, Toulouse, France, 27–29 January 2016. [Google Scholar]
- Kezadri Hamiaz, M.; Pantel, M.; Thirioux, X.; Combemale, B. Correct-by-construction model driven engineering composition operators. Form. Asp. Comput. 2016, 28, 409–440. [Google Scholar] [CrossRef]
- Nielsen, E.H.; Annenkov, D.; Spitters, B. Formalising decentralised exchanges in Coq. In Proceedings of the 12th ACM SIGPLAN International Conference on Certified Programs and Proofs, Boston, MA, USA, 16–17 January 2023; pp. 290–302. [Google Scholar]
- Ethereum Foundation. Remix IDE: Ethereum Smart Contract Development Environment. Available online: https://github.com/ethereum/remix-ide (accessed on 8 February 2024).
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. Smartcheck: Static analysis of ethereum smart contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothia, Sweden, 27 May–3 June 2018; pp. 9–16. [Google Scholar]
- Palkeo. Pakala: Yet Another EVM Symbolic Execution Tool. Available online: https://www.palkeo.com/en/projets/ethereum/pakala.html (accessed on 24 February 2024).
- Grieco, G.; Song, W.; Cygan, A.; Feist, J.; Groce, A. Echidna: Effective, usable, and fast fuzzing for smart contracts. In Proceedings of the 29th ACM SIGSOFT International Symposium on Software Testing and Analysis, Virtual Event, 18–22 July 2020; pp. 557–560. [Google Scholar]
- Groce, A.; Grieco, G. Echidna-parade: A tool for diverse multicore smart contract fuzzing. In Proceedings of the 30th ACM SIGSOFT International Symposium on Software Testing and Analysis, Virtual Event, Aarhus, Denmark, 11–17 July 2021; pp. 658–661. [Google Scholar]
- Nassirzadeh, B.; Sun, H.; Banescu, S.; Ganesh, V. Gas gauge: A security analysis tool for smart contract out-of-gas vulnerabilities. In Proceedings of the International Conference on Mathematical Research for Blockchain Economy, Vilamoura, Portugal, 12–14 July 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 143–167. [Google Scholar]
- Li, Z.; Wu, H.; Xu, J.; Wang, X.; Zhang, L.; Chen, Z. Musc: A tool for mutation testing of ethereum smart contract. In Proceedings of the 2019 34th IEEE/ACM International Conference on Automated Software Engineering (ASE), San Diego, CA, USA, 10–15 November 2019; pp. 1198–1201. [Google Scholar]
- Peng, C.; Akca, S.; Rajan, A. SIF: A framework for solidity contract instrumentation and analysis. In Proceedings of the 2019 26th Asia-Pacific Software Engineering Conference (APSEC), Putrajava, Malaysia, 2–5 December 2019; pp. 466–473. [Google Scholar]
- Feist, J.; Grieco, G.; Groce, A. Slither: A static analysis framework for smart contracts. In Proceedings of the 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 17 May 2019; pp. 8–15. [Google Scholar]
- Hajdu, Á.; Jovanović, D. solc-verify: A modular verifier for solidity smart contracts. In Proceedings of the Verified Software. Theories, Tools, and Experiments: 11th International Conference, VSTTE 2019, New York City, NY, USA, 13–14 July 2019; Revised Selected Papers 11. Springer: Berlin/Heidelberg, Germany, 2020; pp. 161–179. [Google Scholar]
- Protofire. Solhint: Solidity Linter. Available online: https://protofire.github.io/solhint/ (accessed on 25 February 2024).
- Praitheeshan, P.; Pan, L.; Zheng, X.; Jolfaei, A.; Doss, R. SolGuard: Preventing external call issues in smart contract-based multi-agent robotic systems. Inf. Sci. 2021, 579, 150–166. [Google Scholar] [CrossRef]
- Zhang, P.; Xiao, F.; Luo, X. Soliditycheck: Quickly detecting smart contract problems through regular expressions. arXiv 2019, arXiv:1911.09425. [Google Scholar]
- Honig, J.J.; Everts, M.H.; Huisman, M. Practical mutation testing for smart contracts. In Proceedings of the International Workshop on Data Privacy Management, International Workshop on Cryptocurrencies and Blockchain Technology, Luxembourg, 26–27 September 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 289–303. [Google Scholar]
- Frank, J.; Aschermann, C.; Holz, T. ETHBMC: A bounded model checker for smart contracts. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020; pp. 2757–2774. [Google Scholar]
- Revere, R. solgraph: Visualize Solidity Control Flow for Smart Contracts. Available online: https://github.com/raineorshine/solgraph (accessed on 13 February 2024).
- Kolluri, A.; Nikolic, I.; Sergey, I.; Hobor, A.; Saxena, P. Exploiting the laws of order in smart contracts. In Proceedings of the 28th ACM SIGSOFT International Symposium on Software Testing and Analysis, Beijing, China, 15–19 July 2019; ACM: New York, NY, USA, 2019; pp. 363–373. [Google Scholar]
- Veloso, N. Conkas: Ethereum Smart Contract Security Analysis. Available online: https://github.com/nveloso/conkas (accessed on 26 February 2024).
- Chen, J.; Xia, X.; Lo, D.; Grundy, J.; Luo, X.; Chen, T. Defectchecker: Automated smart contract defect detection by analyzing evm bytecode. IEEE Trans. Softw. Eng. 2021, 48, 2189–2207. [Google Scholar] [CrossRef]
- Norvill, R.; Pontiveros, B.B.F.; State, R.; Cullen, A. Visual emulation for Ethereum’s virtual machine. In Proceedings of the NOMS 2018—2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–4. [Google Scholar]
- Grishchenko, I.; Maffei, M.; Schneidewind, C. Ethertrust: Sound static analysis of ethereum bytecode. Tech. Univ. Wien Tech. Rep. 2018, 1–41. Available online: https://www.netidee.at/sites/default/files/2018-07/staticanalysis.pdf (accessed on 31 May 2025).
- Albert, E.; Gordillo, P.; Livshits, B.; Rubio, A.; Sergey, I. Ethir: A framework for high-level analysis of ethereum bytecode. In Proceedings of the International Symposium on Automated Technology for Verification and Analysis, Los Angeles, CA, USA, 7–10 October 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 513–520. [Google Scholar]
- Torres, C.F.; Steichen, M. The art of the scam: Demystifying honeypots in ethereum smart contracts. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 1591–1607. [Google Scholar]
- Grech, N.; Kong, M.; Jurisevic, A.; Brent, L.; Scholz, B.; Smaragdakis, Y. MadMax: Analyzing the out-of-gas world of smart contracts. Commun. ACM 2020, 63, 87–95. [Google Scholar] [CrossRef]
- Mueller, B. Smashing Smart Contracts. In Proceedings of the 9th HITB Security Conference, Amsterdam, The Netherlands, 9–13 April 2018; Available online: https://github.com/muellerberndt/smashing-smart-contracts/blob/master/smashing-smart-contracts-1of1.pdf (accessed on 31 May 2025).
- Ventuzelo, P. Octopus: Ethereum Smart Contract Security Analysis Tool. Available online: https://github.com/FuzzingLabs/octopus (accessed on 26 February 2024).
- Torres, C.F.; Schütte, J.; State, R. Osiris: Hunting for integer bugs in ethereum smart contracts. In Proceedings of the 34th Annual Computer Security Applications Conference, San Juan, PR, USA, 3–7 December 2018; pp. 664–676. [Google Scholar]
- Suiche, M. Porosity: Decompiler and Security Analysis Tool for Ethereum Smart Contracts. Available online: https://github.com/msuiche/porosity (accessed on 8 February 2024).
- PNF Software. JEB Ethereum Plugin Documentation. Available online: https://www.pnfsoftware.com/jeb/manual/ethereum/ (accessed on 31 May 2025).
- Chinen, Y.; Yanai, N.; Cruz, J.P.; Okamura, S. RA: Hunting for re-entrancy attacks in ethereum smart contracts via static analysis. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Virtual, 2–6 May 2020; pp. 327–336. [Google Scholar]
- Krupp, J.; Rossow, C. teEther: Gnawing at ethereum to automatically exploit smart contracts. In Proceedings of the 27th USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 1317–1333. [Google Scholar]
- Brent, L.; Jurisevic, A.; Kong, M.; Liu, E.; Gauthier, F.; Gramoli, V.; Holz, R.; Scholz, B. Vandal: A scalable security analysis framework for smart contracts. arXiv 2018, arXiv:1809.03981. [Google Scholar]
- Azzopardi, S.; Ellul, J.; Pace, G.J. Monitoring Smart Contracts: ContractLarva and Open Challenges Beyond. In Proceedings of the Runtime Verification, Limassol, Cyprus, 10–13 November 2018; Colombo, C., Leucker, M., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 113–137. [Google Scholar]
- Stegeman, L. Solitor: Runtime Verification of Smart Contracts on the Ethereum Network. Master’s Thesis, University of Twente, Enschede, The Netherlands, 2018. Available online: http://essay.utwente.nl/76902/ (accessed on 31 May 2025).
- Wang, H.; Li, Y.; Lin, S.W.; Ma, L.; Liu, Y. Vultron: Catching vulnerable smart contracts once and for all. In Proceedings of the 2019 IEEE/ACM 41st International Conference on Software Engineering: New Ideas and Emerging Results (ICSE-NIER), Montreal, QC, Canada, 25–31 May 2019; pp. 1–4. [Google Scholar]
- Jiang, B.; Liu, Y.; Chan, W.K. Contractfuzzer: Fuzzing smart contracts for vulnerability detection. In Proceedings of the 33rd ACM/IEEE International Conference on Automated Software Engineering, Montpellier, France, 3–7 September 2018; pp. 259–269. [Google Scholar]
- Nguyen, T.D.; Pham, L.H.; Sun, J.; Lin, Y.; Minh, Q.T. sfuzz: An efficient adaptive fuzzer for solidity smart contracts. In Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering, Seoul, Republic of Korea, 27 June–19 July 2020; pp. 778–788. [Google Scholar]
- Chen, T.; Cao, R.; Li, T.; Luo, X.; Gu, G.; Zhang, Y.; Liao, Z.; Zhu, H.; Chen, G.; He, Z.; et al. SODA: A Generic Online Detection Framework for Smart Contracts. In Proceedings of the NDSS, San Diego, CA, USA, 23–26 February 2020. [Google Scholar]
- Gao, J.; Liu, H.; Liu, C.; Li, Q.; Guan, Z.; Chen, Z. Easyflow: Keep ethereum away from overflow. In Proceedings of the 2019 IEEE/ACM 41st International Conference on Software Engineering: Companion Proceedings (ICSE-Companion), Montreal, QC, Canada, 25–31 May 2019; pp. 23–26. [Google Scholar]
- Grossman, S.; Abraham, I.; Golan-Gueta, G.; Michalevsky, Y.; Rinetzky, N.; Sagiv, M.; Zohar, Y. Online detection of effectively callback free objects with applications to smart contracts. Proc. ACM Program. Lang. 2017, 2, 1–28. [Google Scholar] [CrossRef]
- Pace, G. ContractLarva: A Tool for Runtime Monitoring of Ethereum Smart Contracts. Available online: https://github.com/gordonpace/contractLarva (accessed on 8 February 2024).
- NTU SRSLab. ModCon: Ethereum Smart Contract Modification Detection Tool. Available online: https://github.com/ntu-SRSLab/ModCon (accessed on 26 February 2024).
- Stegeman, L. Solitor: Ethereum Smart Contract Runtime Monitoring Tool. Available online: https://github.com/LarsStegeman/EthereumRuntimeMonitoring (accessed on 26 February 2024).
- NTU SRSLab. Vultron: Ethereum Smart Contract Vulnerability Detection Tool. Available online: https://github.com/ntu-SRSLab/vultron (accessed on 26 February 2024).
- Bell, G. ContractFuzzer: Fuzz Testing Tool for Ethereum Smart Contracts. Available online: https://github.com/gongbell/ContractFuzzer (accessed on 13 February 2024).
- Tai, D. sFuzz: Ethereum Smart Contract Fuzz Testing Tool. Available online: https://github.com/duytai/sFuzz (accessed on 27 February 2024).
- PandAbox Development. SODA: Solidity Contract Data Analyzer. Available online: https://github.com/pandabox-dev/SODA (accessed on 27 February 2024).
- Gao, J. EasyFlow: Ethereum Smart Contract Static Analysis Tool. Available online: https://github.com/Jianbo-Gao/EasyFlow (accessed on 27 February 2024).
- Grinberg, S. ECFChecker. Available online: https://github.com/shellygr/ECFChecker (accessed on 21 February 2024).
- Akca, S.; Rajan, A.; Peng, C. SolAnalyser: A Framework for Analysing and Testing Smart Contracts. In Proceedings of the 2019 26th Asia-Pacific Software Engineering Conference (APSEC), Putrajaya, Malaysia, 2–5 December 2019; pp. 482–489. [Google Scholar]
- Mossberg, M.; Manzano, F.; Hennenfent, E.; Groce, A.; Grieco, G.; Feist, J.; Brunson, T.; Dinaburg, A. Manticore: A user-friendly symbolic execution framework for binaries and smart contracts. In Proceedings of the 2019 34th IEEE/ACM International Conference on Automated Software Engineering (ASE), San Diego, CA, USA, 10–15 November 2019; pp. 1186–1189. [Google Scholar]
- di Angelo, M.; Durieux, T.; Ferreira, J.F.; Salzer, G. SmartBugs 2.0: An Execution Framework for Weakness Detection in Ethereum Smart Contracts. In Proceedings of the 38th IEEE/ACM International Conference on Automated Software Engineering (ASE), Luxembourg, 11–15 September 2023. [Google Scholar]
- Akca, S. SolAnalyser: Solidity Smart Contract Security Analyzer. Available online: https://github.com/sefaakca/SolAnalyser (accessed on 25 February 2024).
- Trail of Bits. Manticore: Symbolic Execution Tool for Analysis of Smart Contracts and Binaries. Available online: https://github.com/trailofbits/manticore (accessed on 8 February 2024).
- Nikolić, I. MAIAN: A Novel Mitigation for Reentrancy Attacks. Available online: https://github.com/ivicanikolicsg/MAIAN (accessed on 8 February 2024).
- SmartBugs. SmartBugs: Smart Contract Static Analysis. Available online: https://github.com/smartbugs/smartbugs (accessed on 24 February 2024).
- Pierro, A. SPASO (PArser for SOlidity). Available online: https://github.com/aphd/paso (accessed on 22 March 2024).
- Pierro, G.A.; Tonelli, R. PASO: A Web-Based Parser for Solidity Language Analysis. In Proceedings of the 2020 IEEE International Workshop on Blockchain Oriented Software Engineering (IWBOSE), London, ON, Canada, 18 February 2020; pp. 16–21. [Google Scholar] [CrossRef]
- Gao, Z.; Jiang, L.; Xia, X.; Lo, D.; Grundy, J. Checking smart contracts with structural code embedding. IEEE Trans. Softw. Eng. 2020, 47, 2874–2891. [Google Scholar] [CrossRef]
- Camino, R.; Torres, C.F.; Baden, M.; State, R. A Data Science Approach for Honeypot Detection in Ethereum. arXiv 2019, arXiv:1910.01449. [Google Scholar]
- Zhuang, Y.; Liu, Z.; Qian, P.; Liu, Q.; Wang, X.; He, Q. Smart Contract Vulnerability Detection using Graph Neural Network. In Proceedings of the IJCAI, Yokohama, Japan, 7–15 January 2021; pp. 3283–3290. [Google Scholar]
- Qian, P. GNNSCVulDetector: Graph Neural Network-Based Smart Contract Vulnerability Detector. Available online: https://github.com/Messi-Q/GNNSCVulDetector (accessed on 21 February 2024).
- Liu, Z.; Qian, P.; Wang, X.; Zhu, L.; He, Q.; Ji, S. Smart contract vulnerability detection: From pure neural network to interpretable graph feature and expert pattern fusion. arXiv 2021, arXiv:2106.09282. [Google Scholar]
- Qian, P.; Liu, Z.; He, Q.; Zimmermann, R.; Wang, X. Towards automated reentrancy detection for smart contracts based on sequential models. IEEE Access 2020, 8, 19685–19695. [Google Scholar] [CrossRef]
- Yu, X.; Zhao, H.; Hou, B.; Ying, Z.; Wu, B. Deescvhunter: A deep learning-based framework for smart contract vulnerability detection. In Proceedings of the 2021 International Joint Conference on Neural Networks (IJCNN), Rome, Italy, 30 June–5 July 2021; pp. 1–8. [Google Scholar]
- Ashizawa, N.; Yanai, N.; Cruz, J.P.; Okamura, S. Eth2Vec: Learning contract-wide code representations for vulnerability detection on Ethereum smart contracts. In Proceedings of the 3rd ACM International Symposium on Blockchain and Secure Critical Infrastructure, Melbourne, Australia, 10–14 July 2022; Volume 3, p. 100101. [Google Scholar] [CrossRef]
- Nguyen, H.H.; Nguyen, N.M.; Xie, C.; Ahmadi, Z.; Kudendo, D.; Doan, T.N.; Jiang, L. MANDO: Multi-level heterogeneous graph embeddings for fine-grained detection of smart contract vulnerabilities. In Proceedings of the 2022 IEEE 9th International Conference on Data Science and Advanced Analytics (DSAA), Online, 13–16 October 2022; pp. 1–10. [Google Scholar]
- Liu, Z.; Qian, P.; Wang, X.; Zhuang, Y.; Qiu, L.; Wang, X. Combining graph neural networks with expert knowledge for smart contract vulnerability detection. IEEE Trans. Knowl. Data Eng. 2021, 35, 1296–1310. [Google Scholar] [CrossRef]
- He, J.; Balunović, M.; Ambroladze, N.; Tsankov, P.; Vechev, M. Learning to Fuzz from Symbolic Execution with Application to Smart Contracts. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 531–548. [Google Scholar] [CrossRef]
- Su, J.; Dai, H.N.; Zhao, L.; Zheng, Z.; Luo, X. Effectively Generating Vulnerable Transaction Sequences in Smart Contracts with Reinforcement Learning-guided Fuzzing. In Proceedings of the 37th IEEE/ACM International Conference on Automated Software Engineering, Rochester, MI, USA, 10–14 October 2023. [Google Scholar] [CrossRef]
- Zhang, Z.; Lei, Y.; Yan, M.; Yu, Y.; Chen, J.; Wang, S.; Mao, X. Reentrancy vulnerability detection and localization: A deep learning based two-phase approach. In Proceedings of the 37th IEEE/ACM International Conference on Automated Software Engineering, Rochester, MI, USA, 10–14 October 2022; pp. 1–13. [Google Scholar]
- Tann, W.J.W.; Han, X.J.; Gupta, S.S.; Ong, Y.S. Towards safer smart contracts: A sequence learning approach to detecting security threats. arXiv 2018, arXiv:1811.06632. [Google Scholar]
- Liao, J.W.; Tsai, T.T.; He, C.K.; Tien, C.W. Soliaudit: Smart contract vulnerability assessment based on machine learning and fuzz testing. In Proceedings of the 2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Granada, Spain, 22–25 October 2019; pp. 458–465. [Google Scholar]
- HajiHosseinKhani, S.; Lashkari, A.H.; Oskui, A.M. Unveiling vulnerable smart contracts: Toward profiling vulnerable smart contracts using genetic algorithm and generating benchmark dataset. Blockchain Res. Appl. 2024, 5, 100171. [Google Scholar] [CrossRef]
- Ren, M.; Yin, Z.; Ma, F.; Xu, Z.; Jiang, Y.; Sun, C.; Li, H.; Cai, Y. Empirical evaluation of smart contract testing: What is the best choice? In Proceedings of the 30th ACM SIGSOFT International Symposium on Software Testing and Analysis, Virtual Event, Aarhus, Denmark, 11–17 July 2021; pp. 566–579. [Google Scholar]
- Durieux, T.; Ferreira, J.F.; Abreu, R.; Cruz, P. Empirical review of automated analysis tools on 47,587 ethereum smart contracts. In Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering, Seoul, Republic of Korea, 27 June–19 July 2020; pp. 530–541. [Google Scholar]
- Ghaleb, A.; Pattabiraman, K. How effective are smart contract analysis tools? Evaluating smart contract static analysis tools using bug injection. In Proceedings of the 29th ACM SIGSOFT International Symposium on Software Testing and Analysis, Virtual Event, 18–22 July 2020; pp. 415–427. [Google Scholar]
- Khan, D.; Jung, L.T.; Hashmani, M.A. Systematic literature review of challenges in blockchain scalability. Appl. Sci. 2021, 11, 9372. [Google Scholar] [CrossRef]
- Khlifi, M.K.; Boulila, W.; Farah, I.R. Graph-based deep learning techniques for remote sensing applications: Techniques, taxonomy, and applications—A comprehensive review. Comput. Sci. Rev. 2023, 50, 100596. [Google Scholar] [CrossRef]
- Ammar, A.; Koubaa, A.; Benjdira, B.; Nacar, O.; Sibaee, S. Prediction of Arabic Legal Rulings Using Large Language Models. Electronics 2024, 13, 764. [Google Scholar] [CrossRef]
- Schwalbe, G.; Finzel, B. A comprehensive taxonomy for explainable artificial intelligence: A systematic survey of surveys on methods and concepts. Data Min. Knowl. Discov. 2024, 38, 3043–3101. [Google Scholar] [CrossRef]
- Álvarez, I.A.; Gramlich, V.; Sedlmeir, J. Unsealing the secrets of blockchain consensus: A systematic comparison of the formal security of proof-of-work and proof-of-stake. arXiv 2024, arXiv:2401.14527. [Google Scholar]
- Lv, P.; Wang, Y.; Wang, Y.; Zhou, Q. Potential risk detection system of hyperledger fabric smart contract based on static analysis. In Proceedings of the 2021 IEEE Symposium on Computers and Communications (ISCC), Athens, Greece, 5–8 September 2021; pp. 1–7. [Google Scholar]
- Lamela Seijas, P.; Nemish, A.; Smith, D.; Thompson, S. Marlowe: Implementing and analysing financial contracts on blockchain. In Proceedings of the Financial Cryptography and Data Security: FC 2020 International Workshops, AsiaUSEC, CoDeFi, VOTING, and WTSC, Kota Kinabalu, Malaysia, 14 February 2020; Revised Selected Papers 24. Springer: Berlin/Heidelberg, Germany, 2020; pp. 496–511. [Google Scholar]
- Chakravarty, M.; Kireev, R.; MacKenzie, K.; McHale, V.; Müller, J.; Nemish, A.; Nester, C.; Jones, M.P.; Thompson, S.; Valentine, R.; et al. Functional Blockchain Contracts. 2019. Available online: https://americanblockchainpac.org/wp-content/uploads/2022/03/Functional-Blockchain-Contracts.pdf (accessed on 31 May 2025).
- Solana Foundation. X-Ray: Open-Source Static Analyzer for Solana Smart Contracts. 2024. Available online: https://solanacompass.com/learn/breakpoint-24/bp-2024-technical-talk-open-source-x-ray-solana-smart-contract-static-analysis (accessed on 31 May 2025).
- Solana Documentation. Radar–Static Analysis Tool for Anchor Rust Programs. 2025. Available online: https://solana.com/docs/toolkit/test-suite/security-scanner (accessed on 31 May 2025).
- Web3 Labs. Ink! Verifier Service. Ensures Reproducible Bytecode Verification for Ink! Contracts. 2023. Available online: https://github.com/web3labs/ink-verifier-image (accessed on 31 May 2025).
- Chainlink. Cross-Chain Interoperability Protocol (CCIP). 2025. Available online: https://chain.link/cross-chain (accessed on 6 May 2025).
- Input Output Global (IOG). Marlowe. 2025. Available online: https://docs.cardano.org/developer-resources/smart-contracts/marlowe (accessed on 5 May 2025).
| Ref | Title | Year | Type | Formal Verification | Static Analysis | Dynamic Analysis | Machine Learning | Open Access Tools | # Tools |
|---|---|---|---|---|---|---|---|---|---|
| [27] | A survey on security verification of blockchain smart contracts | 2019 | Survey | ✓ | ✓ | 12 | |||
| [28] | Security analysis methods on Ethereum smart contract vulnerabilities: a survey | 2019 | Survey | ✓ | ✓ | ✓ | ✓ | 8 | |
| [29] | Security, performance, and applications of smart contracts: A systematic survey | 2019 | SLR | ✓ | ✓ | 9 | |||
| [30] | Survey of formal verification methods for smart contracts on blockchain | 2019 | Survey | ✓ | 2 | ||||
| [31] | A survey of tools for analyzing Ethereum smart contracts | 2019 | SLR | ✓ | ✓ | 27 | |||
| [32] | A survey of smart contract formal specification and verification | 2020 | Survey | ✓ | ✓ | ✓ | 34 | ||
| [33] | A Comprehensive Survey on Smart Contract Construction and Execution: Paradigms, Tools and Systems | 2020 | SLR | ✓ | ✓ | ✓ | 22 | ||
| [34] | Smart Contract modeling and verification techniques: A survey | 2020 | Survey | ✓ | 7 | ||||
| [35] | Ethereum smart contract security research: survey and future research opportunities | 2015–2019 | SLR | ✓ | ✓ | ✓ | ✓ | 9 | |
| [36] | Verification of smart contracts: A survey | 2020 | Survey | ✓ | ✓ | ✓ | 25 | ||
| [37] | Pre-deployment Analysis of Smart Contracts—A Survey | 2023 | SLR | ✓ | ✓ | ✓ | ✓ | 6 | |
| [38] | Smart contract vulnerability detection technique: A survey | 2022 | Survey | ✓ | ✓ | ✓ | ✓ | 23 | |
| [39] | SLR of security vulnerabilities in Ethereum blockchain smart contract | 2016–2021 | SLR | ✓ | 20 | ||||
| [40] | Ethereum smart contract analysis tools: A systematic review | 2022 | SLR | ✓ | ✓ | ✓ | ✓ | 86 | |
| [41] | Detecting functional and security-related issues in smart contracts: A systematic literature review | 2015–2020 | SLR | ✓ | ✓ | ✓ | ✓ | ✓ | 26 |
| [42] | Review of automated vulnerability analysis of smart contracts on Ethereum | 2022 | SLR | ✓ | ✓ | ✓ | ✓ | 20 | |
| [43] | The state of Ethereum smart contracts security: Vulnerabilities, countermeasures, and tool support | 2022 | Survey | ✓ | ✓ | ✓ | 11 | ||
| [44] | Security Strengths and Weaknesses of Blockchain Smart Contract System: A Survey | 2022 | Survey | ✓ | ✓ | ✓ | 28 | ||
| [45] | Blockchain verification and validation: Techniques, challenges, and research directions | 2022 | Survey | ✓ | ✓ | 30 | |||
| [46] | Smart contract security: A software lifecycle perspective | 2019 | Survey | ✓ | ✓ | ✓ | 18 | ||
| [47] | Smart contract: Attacks and protections | 2020 | Survey | ✓ | ✓ | 10 | |||
| [48] | The vulnerabilities in smart contracts: A survey | 2021 | Survey | ✓ | ✓ | ✓ | 20 | ||
| [49] | A survey on Ethereum systems security: Vulnerabilities, attacks, and defenses | 2020 | Survey | ✓ | ✓ | ✓ | 51 | ||
| [50] | A systematic literature review of blockchain and smart contract development: Techniques, tools, and open challenges | 2016–2020 | SLR | ✓ | ✓ | ✓ | ✓ | 26 | |
| [51] | Formal Verification of Smart Contracts based on Model Checking: An Overview | 2024 | Survey | ✓ | 8 | ||||
| [52] | A Survey of Vulnerability Detection Techniques by Smart Contract Tools | 2024 | Survey | ✓ | ✓ | ✓ | ✓ | 41 | |
| [53] | A Survey on Security Analysis Methods of Smart Contracts | 2024 | Survey | ✓ | ✓ | ✓ | ✓ | 78 | |
| [54] | A Survey on Automatic Discover Approach by Using Static Analysis for Smart Contract Vulnerability | 2023 | Survey | ✓ | ✓ | ✓ | ✓ | 1 | |
| [55] | Vulnerability detection techniques for smart contracts: A systematic literature review | 2024 | Survey | ✓ | ✓ | ✓ | ✓ | 86 | |
| [56] | A Review of Deep Learning-Based Vulnerability Detection Tools for Ethernet Smart Contracts | 2024 | Survey | ✓ | ✓ | 20 | |||
| [57] | Software verification challenges in the blockchain ecosystem | 2024 | Survey | ✓ | ✓ | ✓ | 0 | ||
| [58] | A systematic mapping on software testing for blockchains | 2012–2022 | SLR | 14 | |||||
| [59] | A Survey on Formal Verification for Solidity Smart Contracts | 2021 | Survey | ✓ | ✓ | 4 | |||
| [60] | A Survey of Ethereum Smart Contract Security: Attacks and Detection | 2024 | Survey | ✓ | ✓ | ✓ | ✓ | 14 |
| Method | Advantages | Limitations |
|---|---|---|
| Static Analysis | Detects issues early without execution; applicable to Solidity and bytecode. Sound guarantees are possible with precise abstractions. | Susceptible to false positives/negatives. Does not capture runtime behavior. |
| Dynamic Analysis | Observes actual execution, revealing runtime vulnerabilities. Techniques like concolic testing and fuzzing improve path exploration. | Computationally intensive and time-consuming. Coverage is limited by input quality and simulated conditions. |
| Formal Verification | Provides mathematical proofs of correctness. High assurance for critical applications. | Resource-intensive with scalability challenges. Requires specialized expertise and accurate specifications. |
| Machine Learning | Processes large datasets to identify subtle, unseen vulnerability patterns. Adapts as more data become available. | Performance hinges on training data quality. Limited interpretability; risk of false positives/negatives. |
| Tool | Language | Repository |
|---|---|---|
| Remix | JavaScript | https://github.com/ethereum/remix-ide, accessed on 17 April 2025. |
| SmartCheck | Java | https://github.com/smartdec/smartcheck, accessed on 17 April 2025. |
| Pakala | Python | https://github.com/palkeo/pakala, accessed on 17 April 2025. |
| Echidna | Haskell | https://github.com/crytic/echidna, accessed on 17 April 2025. |
| GasGauge | Python | https://github.com/gasgauge, accessed on 17 April 2025. |
| MuSc | Java | https://github.com/belikout/MuSC-Tool-Demo-repo, accessed on 17 April 2025. |
| SIF | C++ | https://github.com/chao-peng/SIF, accessed on 17 April 2025. |
| Slither | Python | https://github.com/crytic/slither, accessed on 17 April 2025. |
| Solc-Verify | C++ | https://github.com/SRI-CSL/solidity, accessed on 17 April 2025. |
| Solhint | Java | https://protofire.github.io/solhint/, accessed on 17 April 2025. |
| SolidityCheck | C++ | https://github.com/xf97/SolidityCheck, accessed on 17 April 2025. |
| Vertigo | Python | https://github.com/JoranHonig/vertigo, accessed on 17 April 2025. |
| ETHBMC | Rust | https://github.com/RUB-SysSec/EthBMC, accessed on 17 April 2025. |
| Solgraph | JavaScript | https://github.com/raineorshine/solgraph, accessed on 17 April 2025. |
| ETHRACER | Python | https://github.com/aashishkolluri/Ethracer, accessed on 17 April 2025. |
| Conkas | Python | https://github.com/nveloso/conkas, accessed on 17 April 2025. |
| Tool | Language | Repository |
|---|---|---|
| DefectChecker | Java | https://github.com/Jiachi-Chen/DefectChecker, accessed on 17 April 2025. |
| E-EVM | Python | https://github.com/pisocrob/E-EVM, accessed on 17 April 2025. |
| EtherTrust | Java | https://github.com/SecPriv/EtherTrust, accessed on 17 April 2025. |
| EthIR | Python | https://github.com/costa-group/EthIR, accessed on 17 April 2025. |
| HoneyBadger | Python | https://github.com/christoftorres/HoneyBadger, accessed on 17 April 2025. |
| MadMax | Gigahose IR | https://github.com/nevillegrech/MadMax, accessed on 17 April 2025. |
| Mythril | Python | https://github.com/Consensys/mythril, accessed on 17 April 2025. |
| Octopus | Python | https://github.com/FuzzingLabs/octopus, accessed on 17 April 2025. |
| Osiris | Python | https://github.com/christoftorres/Osiris, accessed on 17 April 2025. |
| Oyente | Python | https://github.com/enzymefinance/oyente, accessed on 17 April 2025. |
| Porosity | C++ | https://github.com/msuiche/porosity, accessed on 17 April 2025. |
| RA | Python | https://github.com/wanidon/RA, accessed on 17 April 2025. |
| Securify | Java | https://github.com/eth-sri/securify2, accessed on 17 April 2025. |
| TeEther | Python | https://github.com/nescio007/teether, accessed on 17 April 2025. |
| Vandal | Python | https://github.com/usyd-blockchain/vandal, accessed on 17 April 2025. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kezadri Hamiaz, M.; Driss, M. Ethereum Smart Contracts Under Scrutiny: A Survey of Security Verification Tools, Techniques, and Challenges. Computers 2025, 14, 226. https://doi.org/10.3390/computers14060226
Kezadri Hamiaz M, Driss M. Ethereum Smart Contracts Under Scrutiny: A Survey of Security Verification Tools, Techniques, and Challenges. Computers. 2025; 14(6):226. https://doi.org/10.3390/computers14060226
Chicago/Turabian StyleKezadri Hamiaz, Mounira, and Maha Driss. 2025. "Ethereum Smart Contracts Under Scrutiny: A Survey of Security Verification Tools, Techniques, and Challenges" Computers 14, no. 6: 226. https://doi.org/10.3390/computers14060226
APA StyleKezadri Hamiaz, M., & Driss, M. (2025). Ethereum Smart Contracts Under Scrutiny: A Survey of Security Verification Tools, Techniques, and Challenges. Computers, 14(6), 226. https://doi.org/10.3390/computers14060226







