An Efficient Detection Mechanism of Network Intrusions in IoT Environments Using Autoencoder and Data Partitioning
Abstract
1. Introduction
1.1. Motivation
1.2. Background
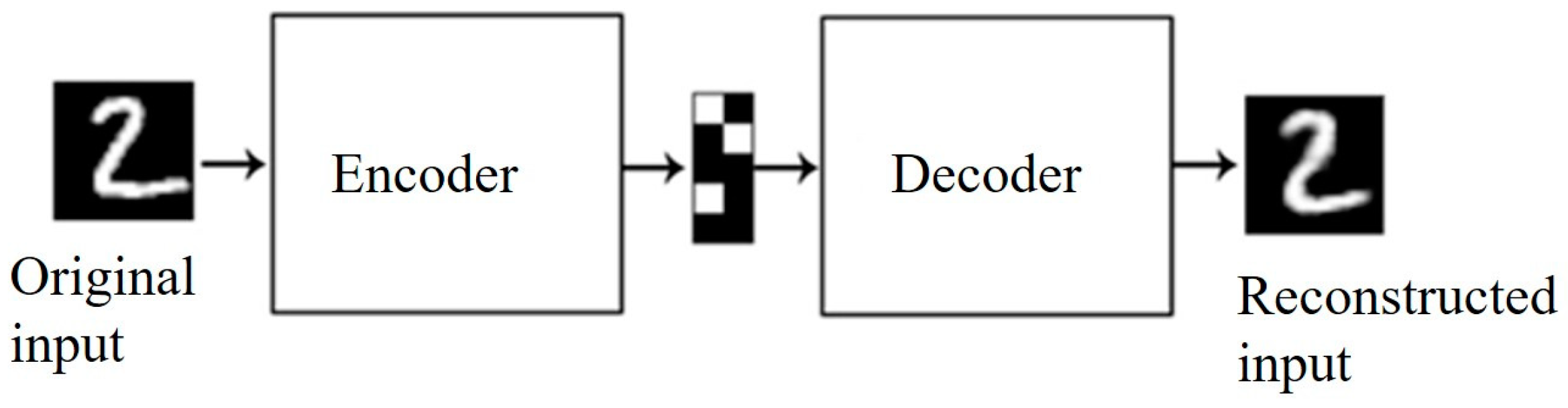
1.2.1. Autoencoder and Its Application to Intrusion Detection
1.2.2. On-Device Learning Anomaly Detector
1.2.3. Multiple Autoencoders Joint Decision-Making
1.3. Contributions
- Conducted research on the papers related to the field of intrusion detection, identified their shortcomings, and improved the schemes of relevant papers.
- Introduced the concept of paired autoencoders, where an autoencoder trained on attack data is paired with another trained on normal data.
- Partitioned the data into multiple regions to reduce the complexity of data distribution in each region and improve the detection performance. For this purpose, multiple autoencoders are used for initial data prediction, and based on the prediction results, the data are partitioned.
- Leveraged the threshold characteristics of the autoencoders to precisely detect data types within each region.
- Validated our proposal on the public dataset (NSL-KDD), even when dealing with traffic that contains a mix of different types of attacks.
- Boldly introduced the use of autoencoders trained on positive data to assist in the collaborative judgment of autoencoders trained on negative data and mitigate the potential side effects (such as an increased false positive rate) through data partitioning and secondary detection. According to our investigation, this approach is unprecedented.
2. Related Work
2.1. Literature Review
2.2. Challenges in This Study
3. Proposal: Paired-Autoencoder and 2-Layer Detection
3.1. Overviews
3.2. Training Multiple Autoencoders Using Attack Data and Normal Data, Respectively
3.3. First Layer—Data Partitioning
- If all paired autoencoders classify the data as normal, then the data are classified into the quasi-normal region.
- If any paired autoencoder determines the data to be abnormal (i.e., both the autoencoder trained with normal data and the autoencoder trained with attack data classify the data as abnormal), then the data are classified into the quasi-attack region.
- Otherwise, if the performance of the data on any paired autoencoder is in the intersection, then the data are classified into the divergence region.
- In all other cases, the data are classified into the undetermined region. For example, when there is a pair of autoencoders where the one trained on normal data classifies the data as an attack and the one trained on attack data classifies the data as non-attack.
- Data falls within the intersection only in one set of paired autoencoders for one kind of attack;
- Data falls within the intersection in multiple sets of paired autoencoders.
3.4. Second Layer—Precise Detection
4. Experiments
4.1. Dataset
- Basic features: Describes the basic attributes of a single TCP connection, such as duration, protocol type, service type, etc. These features are derived from basic information at the IP and TCP layers.
- Content features: Describes features related to the contents of the data packets, such as the number of failed login attempts, number of access control files, etc. These features are mainly used to detect U2R and R2L attacks, as these attacks often involve spoofing or abnormal login behaviors.
- Time-based traffic features: Traffic features are calculated based on a time window, such as the time interval between connections, the number of connections to the same service within a time window, etc. These features help detect DoS and Probe attacks, as these attacks often manifest as a large number of connection requests in a short period.
- Host-based traffic features: Statistical features are based on the host, such as the number of connections to the same host, the number of connections to the same host within a specific time window, etc. These features are used to identify attack behaviors targeting a single host.
4.2. Data Preprocessing
4.3. Model Training and Selecting
4.4. Evaluation Metrics
- (1)
- Overall Accuracy and Overall F1-Score: Accuracy is used to measure the overall correctness of a model’s classifications, suitable for datasets with balanced class distributions. F1-Score is useful for evaluating model performance on imbalanced datasets, particularly when balancing precision and recall is important. They can be calculated using the following formulas:where , , F and F are the counts of True Positives, True Negatives, False Positives, and False Negatives, respectively, calculated over the entire test set.
- (2)
- Within-Region Accuracy: Assume that after the first layer of data partitioning, no precise detection is performed, and data in the quasi-normal region, divergence region, and indeterminate region are all predicted as normal (because these regions contain more normal labels than attack labels), while data in the quasi-attack region are all predicted as attacks. Record the accuracy within each region under this assumption (the ratio of correctly predicted data to the total data in the region) and compare it with the accuracy within each region after introducing precise detection to demonstrate the improvement brought by precise detection. The calculation formula is shown as follows:where , , F and F are the counts of True Positives, True Negatives, False Positives, and False Negatives, respectively, calculated within the test set of the region.
- (3)
- Training Duration and Model Size: Compare the training duration and model size with several commonly used machine learning models to demonstrate the lightweight nature of the proposed model.
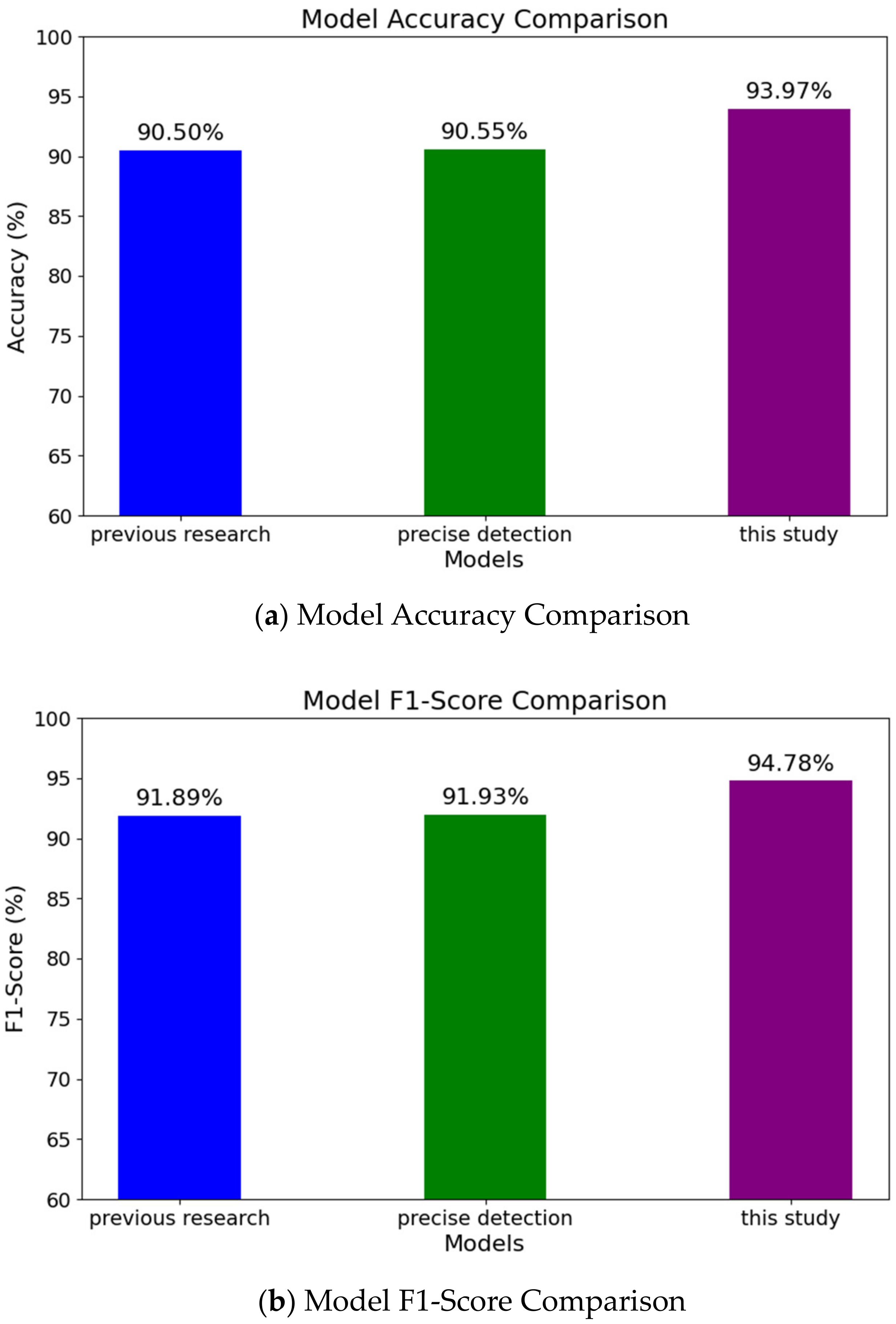
4.5. Experiment Results: Overall Accuracy and Overall F1-Score
- (1)
- The original method has already achieved 90.49% accuracy and 91.89% F1-Score.
- (2)
- Simply adding precise detection only brings a slight improvement.
- (3)
- By combining data partitioning from the first layer with precise detection from the second layer, the model’s performance is significantly improved.
- (4)
- It can also be calculated from the confusion matrix that, compared with the original case, the false negative rate (FNR) and false positive rate (FPR) of the model have decreased from 7.77% and 10.65% to 5.17% and 6.64%, respectively.
- (1)
- It provides more selectable autoencoders to serve as classifiers for precise detection;
- (2)
- The distribution of data in each region in the feature space becomes simpler, making classification easier.
4.6. Experiment Result: Within-Region Accuracy
4.7. Training Time and Model Size Analysis
5. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Abdul-Qawy, A.S.; Pramod, P.J.; Magesh, E.; Srinivasulu, T. The internet of things (iot): An overview. Int. J. Eng. Res. Appl. 2015, 5, 71–82. [Google Scholar]
- Gartner Says Worldwide IoT Security Spending Will Reach $1.5 Billion in 2018. Available online: https://www.gartner.com/en/newsroom/press-releases/2018-03-21-gartner-says-worldwide-iot-security-spending-will-reach-1-point-5-billion-in-2018 (accessed on 8 October 2024).
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the mirai botnet. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Khan, R.; Maynard, P.; McLaughlin, K.; Laverty, D.; Sezer, S. Threat analysis of blackenergy malware for synchrophasor based real-time control and monitoring in smart grid. In Proceedings of the 4th International Symposium for ICS & SCADA Cyber Security Research 2016, Belfast, UK, 23–25 August 2016; BSC: London, UK, 2016; pp. 53–63. [Google Scholar]
- Farwell, J.P.; Rohozinski, R. Stuxnet and the future of cyber war. Survival 2011, 53, 23–40. [Google Scholar] [CrossRef]
- Stanislav, M.; Beardsley, T. Hacking iot: A case study on baby monitor exposures and vulnerabilities. Rapid7 Report 2015. Available online: https://information.rapid7.com/iot-baby-monitor-research.html (accessed on 8 October 2024).
- Eskandari, M.; Janjua, Z.H.; Vecchio, M.; Antonelli, F. Passban IDS: An intelligent anomaly-based intrusion detection system for IoT edge devices. IEEE Internet Things J. 2020, 7, 6882–6897. [Google Scholar] [CrossRef]
- Nguyen, T.D.; Marchal, S.; Miettinen, M.; Fereidooni, H.; Asokan, N.; Sadeghi, A.R. DÏoT: A federated self-learning anomaly detection system for IoT. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–9 July 2019; pp. 756–767. [Google Scholar]
- Rumelhart, D.E.; Hinton, G.E.; Williams, R.J. Learning representations by back-propagating errors. Nature 1986, 323, 533–536. [Google Scholar] [CrossRef]
- Le Cun, Y.; Fogelman-Soulié, F. Modèles connexionnistes de l’apprentissage. Intellectica 1987, 2, 114–143. [Google Scholar] [CrossRef]
- Choi, H.; Kim, M.; Lee, G.; Kim, W. Unsupervised learning approach for network intrusion detection system using autoencoders. J. Supercomput. 2019, 75, 5597–5621. [Google Scholar] [CrossRef]
- Ieracitano, C.; Adeel, A.; Morabito, F.C.; Hussain, A. A novel statistical analysis and autoencoder driven intelligent intrusion detection approach. Neurocomputing 2020, 387, 51–62. [Google Scholar] [CrossRef]
- Tsukada, M.; Kondo, M.; Matsutani, H. A neural network-based on-device learning anomaly detector for edge devices. IEEE Trans. Comput. 2020, 69, 1027–1044. [Google Scholar] [CrossRef]
- Huang, G.B.; Zhu, Q.Y.; Siew, C.K. Extreme learning machine: A new learning scheme of feedforward neural networks. In Proceedings of the 2004 IEEE International Joint Conference on Neural Networks (IEEE Cat. No. 04CH37541), Budapest, Hungary, 25–29 July 2004; Volume 2, pp. 985–990. [Google Scholar]
- Qin, Y.; Kondo, M. Federated Learning-Based Network Intrusion Detection with a Feature Selection Approach; IPSJ SIG Technical Report (in Japanese). In Proceedings of the 2021 International Conference on Electrical, Communication, and Computer Engineering (ICECCE), Kuala Lumpur, Malaysia, 12–13 June 2021; pp. 1–7. [Google Scholar]
- NSL_KDD Dataset. Available online: https://www.kaggle.com/datasets/hassan06/nslkdd (accessed on 8 October 2024).
- Ioulianou, P.; Vasilakis, V.; Moscholios, I.; Logothetis, M. A Signature-based Intrusion Detection System for the Internet of Things. Information and Communication Technology Form. 11–13 July 2018. Available online: https://eprints.whiterose.ac.uk/133312/ (accessed on 8 October 2024).
- Li, W.; Tug, S.; Meng, W.; Wang, Y. Designing collaborative blockchained signature-based intrusion detection in IoT environments. Future Gener. Comput. Syst. 2019, 96, 481–489. [Google Scholar] [CrossRef]
- Sheikh, N.U.; Rahman, H.; Vikram, S.; AlQahtani, H. A lightweight signature-based IDS for IoT environment. arXiv 2018, arXiv:1811.04582. [Google Scholar]
- Lo, W.W.; Layeghy, S.; Sarhan, M.; Gallagher, M.; Portmann, M. E-graphsage: A graph neural network based intrusion detection system for iot. In Proceedings of the NOMS 2022 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 25–29 April 2022; pp. 1–9. [Google Scholar]
- Zhou, X.; Liang, W.; Li, W.; Yan, K.; Shimizu, S.; Kevin, I.; Wang, K. Hierarchical adversarial attacks against graph-neural-network-based IoT network intrusion detection system. IEEE Internet Things J. 2021, 9, 9310–9319. [Google Scholar] [CrossRef]
- Almiani, M.; AbuGhazleh, A.; Al-Rahayfeh, A.; Atiewi, S.; Razaque, A. Deep recurrent neural network for IoT intrusion detection system. Simul. Model. Pract. Theory 2020, 101, 102031. [Google Scholar] [CrossRef]
- Wang, M.; Yang, N.; Weng, N. Securing a smart home with a transformer-based iot intrusion detection system. Electronics 2023, 12, 2100. [Google Scholar] [CrossRef]
- Fraihat, S.; Makhadmeh, S.; Awad, M.; Al-Betar, M.A.; Al-Redhaei, A. Intrusion detection system for large-scale IoT NetFlow networks using machine learning with modified Arithmetic Optimization Algorithm. Internet Things 2023, 22, 100819. [Google Scholar] [CrossRef]
- Breiman, L. Random forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Quinlan, J.R. Induction of decision trees. Mach. Learn. 1986, 1, 81–106. [Google Scholar] [CrossRef]
- Amin, J.; Sharif, M.; Gul, N.; Raza, M.; Anjum, M.A.; Nisar, M.W.; Bukhari, S.A.C. Brain tumor detection by using stacked autoencoders in deep learning. J. Med. Syst. 2020, 44, 32. [Google Scholar] [CrossRef] [PubMed]
- Vařeka, L.; Mautner, P. Stacked autoencoders for the P300 component detection. Front. Neurosci. 2017, 11, 302. [Google Scholar] [CrossRef] [PubMed]
- KDD Cup Dataset. Available online: https://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html (accessed on 8 October 2024).
- Bala, R.; Nagpal, R. A review on kdd cup99 and nsl nsl-kdd dataset. Int. J. Adv. Res. Comput. Sci. 2019, 10, 64. [Google Scholar] [CrossRef]





| Type of Attack Data | Selected Feature |
|---|---|
| DoS | protocol_type, flag, wrong_fragment, num_compromised, root_shell, num_shells, same_srv_rate |
| Probe | logged_in, num_root, num_shells, in_host_login, srv_rerror_rate, srv_serror_rate, srv_diff_host_rate |
| R2L | service, urgent, num_root, num_shells, num_access_files, is_guest_login, srv_serror_rate |
| U2R | flag, land, hot, num_failed_login, logged_in, num_compromised, su_attempted, num_root, num_file_creations, num_outbound_cmds, is_guest_login, same_srv_rate, dst_host_srv_count |
| Research | Model/Method | Limitations |
|---|---|---|
| Novel signature-based IDS [17] | Composed of IDS sensors near the sensor end and IDS routers responsible for running detection modules and firewalls | Signature-based methods cannot detect unknown attacks. Moreover, in the IoT environment, edge devices may not be able to support large signature databases. |
| CBSigIDS (collaborative blockchained signature-based intrusion detection system) [18] | Block-chain | |
| DNA sequence pattern matching algorithm [19] | ||
| E-GraphSAGE (based on a GNN) [20] | GNN (graph neural network) | All the methods adopted are supervised learning. |
| New hierarchical adversarial attack generation method [21] | GNN | |
| Network intrusion detection model in fog computing environment [22] | Two-layer detection structure with deep recurrent neural networks of different internal structures and parameter settings | |
| Intrusion detection system for smart homes based on Transformer [23] | Transformer | |
| Combining feature selection algorithms (AOA, WSO, GWO, BAT) with machine learning models like RF, NB, DT [24] | RF, NB, DT | |
| Deep learning model for brain tumor detection [27] | Two layers of sparse autoencoders (SAEs) and softmax layer | Large models are difficult to deploy in IoT environments. The softmax function may be less effective for network traffic data with ambiguous classification boundaries. |
| Stacked autoencoders for P300 detection in brain-computer interfaces [28] | Stacked autoencoders | Four hidden layers and a varying number of units make it relatively large in IoT environments. |
| This study |
|
| Region | Selected Autoencoder | |
|---|---|---|
| Quasi-normal region | DoS_pos | |
| Quasi-attack region | DoS_pos | |
| Undetermined region | U2R_neg | |
| Divergence region | Region1 | R2L_neg |
| Region2 | U2R_neg | |
| Region3 | DoS_pos | |
| Region4 | R2L_neg | |
| Region5 | R2L_neg | |
| (a) Confusion Matrix of Previous Research [15] | ||
| Attack (Predicted) | Normal (Predicted) | |
| Attack (Actual) | 12,136 | 696 |
| Normal (Actual) | 1446 | 8265 |
| (b) Confusion Matrix of Precise Detection Models | ||
| Attack (Predicted) | Normal (Predicted) | |
| Attack (Actual) | 12,143 | 689 |
| Normal (Actual) | 1442 | 8269 |
| (c) Confusion Matrix of This Study (Both Layers) | ||
| Attack (Predicted) | Normal (Predicted) | |
| Attack (Actual) | 12,350 | 482 |
| Normal (Actual) | 878 | 8833 |
| Region | Without Precise Detection | With Precise Detection | Increase Magnitude |
|---|---|---|---|
| Quasi-Normal Region | 93.18% | 96.31% | 3.13% |
| Quasi-Attack Region | 89.84% | 94.66% | 4.82% |
| Divergence Region | 68.37% | 89.05% | 20.68% |
| Undertermined Region | 96.48% | 96.48% | 0 |
| Model | Without Precise Detection | Model Size |
|---|---|---|
| RF | 12.6 s | 2.29 MB |
| SVM(kernel = linear) | 20 min+ | |
| This Study | 42.3 s | 484 KB |
| Previous Research | 29.5 s | 242 KB |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xiao, Y.; Feng, Y.; Sakurai, K. An Efficient Detection Mechanism of Network Intrusions in IoT Environments Using Autoencoder and Data Partitioning. Computers 2024, 13, 269. https://doi.org/10.3390/computers13100269
Xiao Y, Feng Y, Sakurai K. An Efficient Detection Mechanism of Network Intrusions in IoT Environments Using Autoencoder and Data Partitioning. Computers. 2024; 13(10):269. https://doi.org/10.3390/computers13100269
Chicago/Turabian StyleXiao, Yiran, Yaokai Feng, and Kouichi Sakurai. 2024. "An Efficient Detection Mechanism of Network Intrusions in IoT Environments Using Autoencoder and Data Partitioning" Computers 13, no. 10: 269. https://doi.org/10.3390/computers13100269
APA StyleXiao, Y., Feng, Y., & Sakurai, K. (2024). An Efficient Detection Mechanism of Network Intrusions in IoT Environments Using Autoencoder and Data Partitioning. Computers, 13(10), 269. https://doi.org/10.3390/computers13100269






