Adaptive Barrage Jamming Against SAR Based on Prior Information and Scene Segmentation
Abstract
1. Introduction
1.1. Background
1.2. Previous Work
1.2.1. Deceptive Jamming
1.2.2. Barrage Jamming
1.3. Main Contributions of This Paper
- In this paper, scene prior information is fully combined with barrage jamming methods. The ROI is divided according to the acquired prior information. The jamming power is allocated according to the importance of different targets in the ROI. The utilization efficiency of jamming power is effectively improved in this way, and a better jamming effect can be achieved with limited jamming power.
- In this paper, a frequency response function of a jammer, which is a two-step process integrating position modulation function with jamming coverage function, is proposed to jam targets in the SAR image. Important targets are better protected by generating corresponding response functions for different sub-scenes.
- In this paper, the jamming gain and measurement of the proposed method are analyzed in detail. Then, the simulation experiment was carried out. Firstly, the point target and target simulation experiments of the traditional convolution jamming method are extended. Then, a simulation experiment is conducted using the method proposed in this paper. Simulation results show that the proposed method not only overcomes the limitations of uncontrollable jamming position and coverage of traditional jamming methods but also effectively improves the utilization efficiency of jamming power.
1.4. Organization of This Paper
2. Model and Method
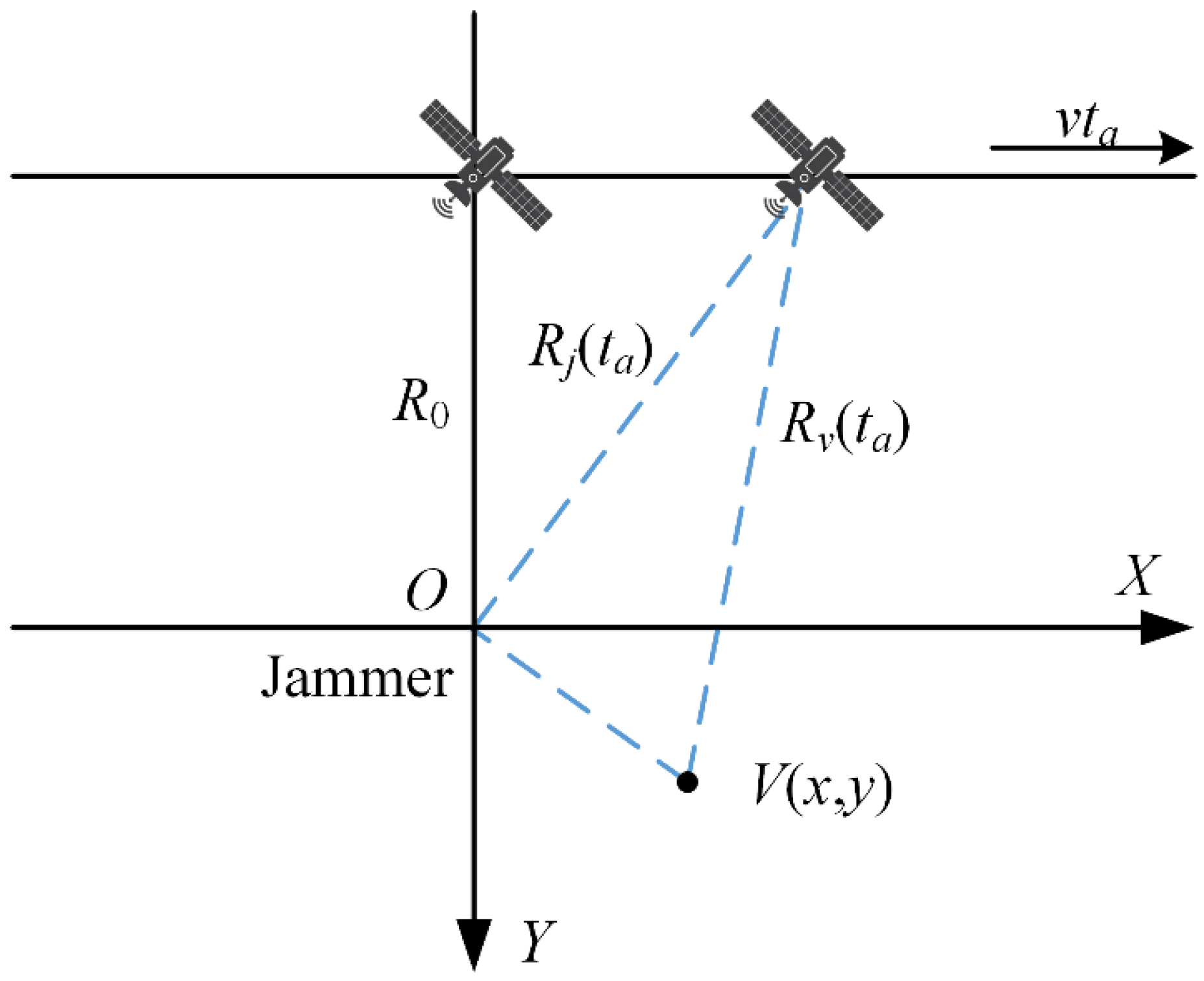
2.1. SAR Jamming Geometric Model
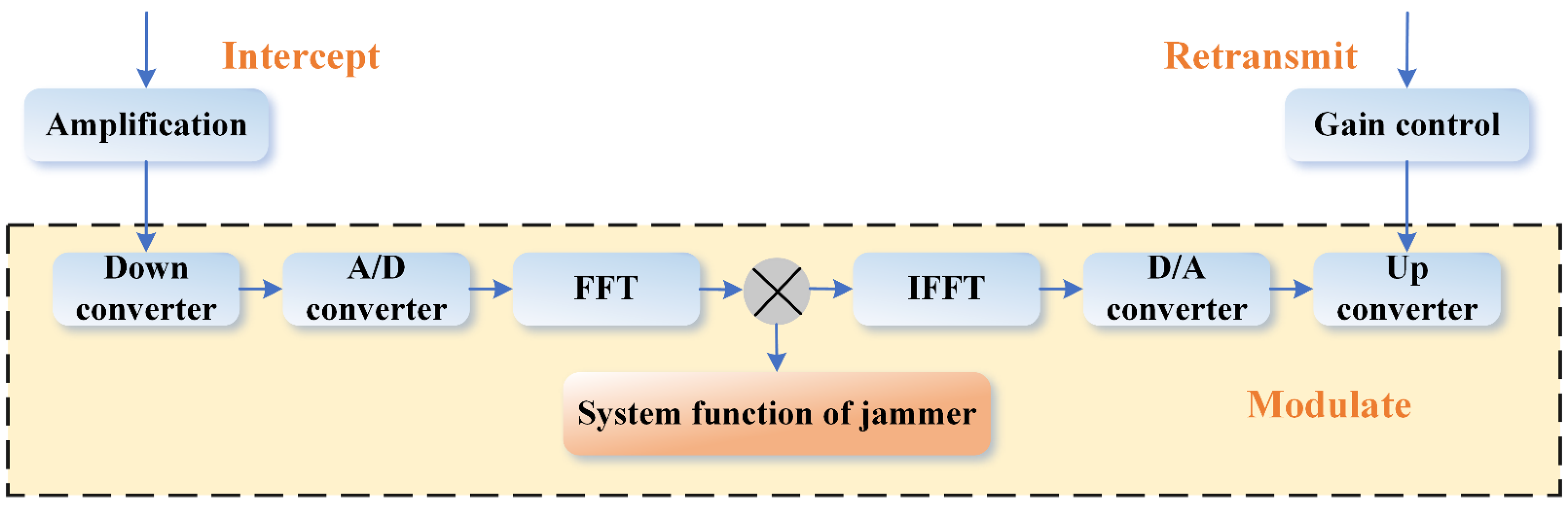
2.2. Noise Convolution Jamming Principle
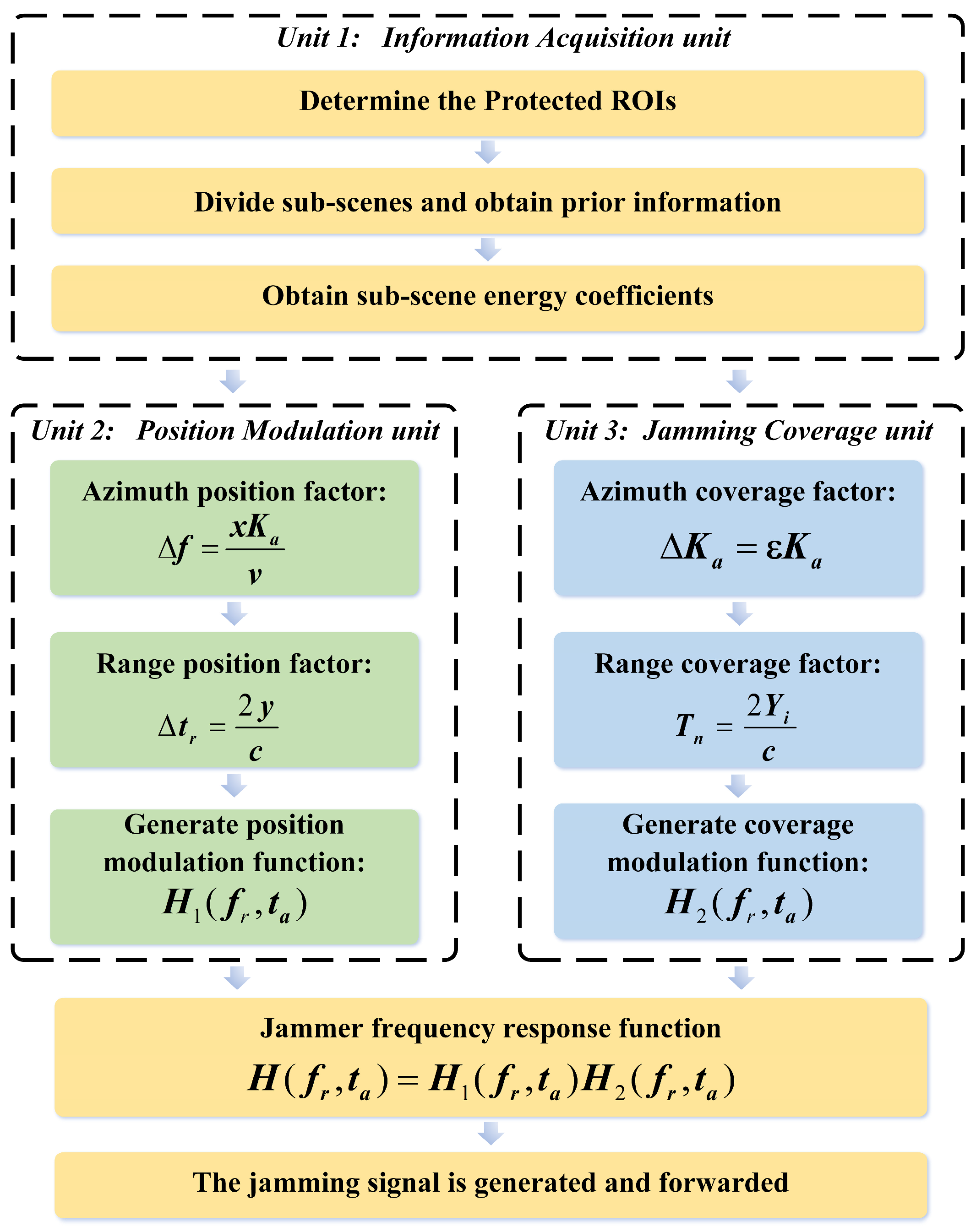
2.3. Proposed Method
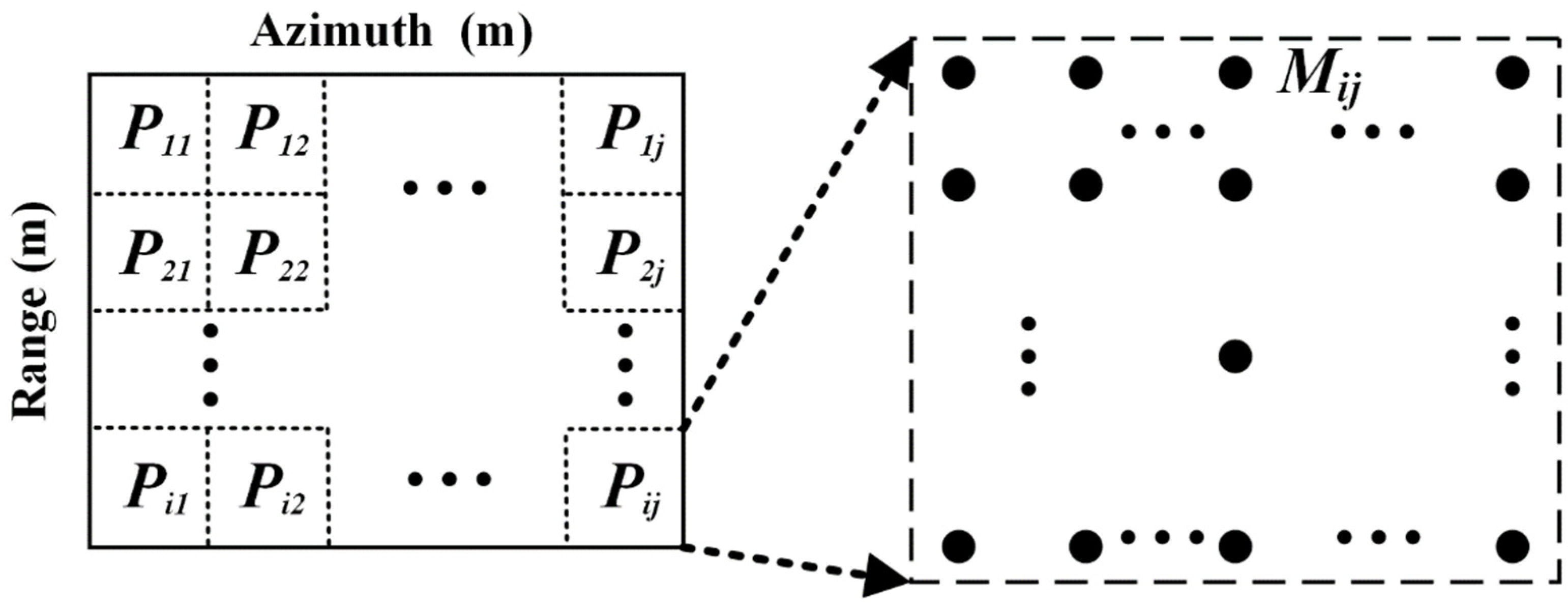
2.3.1. Information Acquisition Unit
2.3.2. Position Modulation Unit
2.3.3. Jamming Coverage Unit
3. Signal Imaging Process and Analysis
3.1. Analysis of Jamming Gain
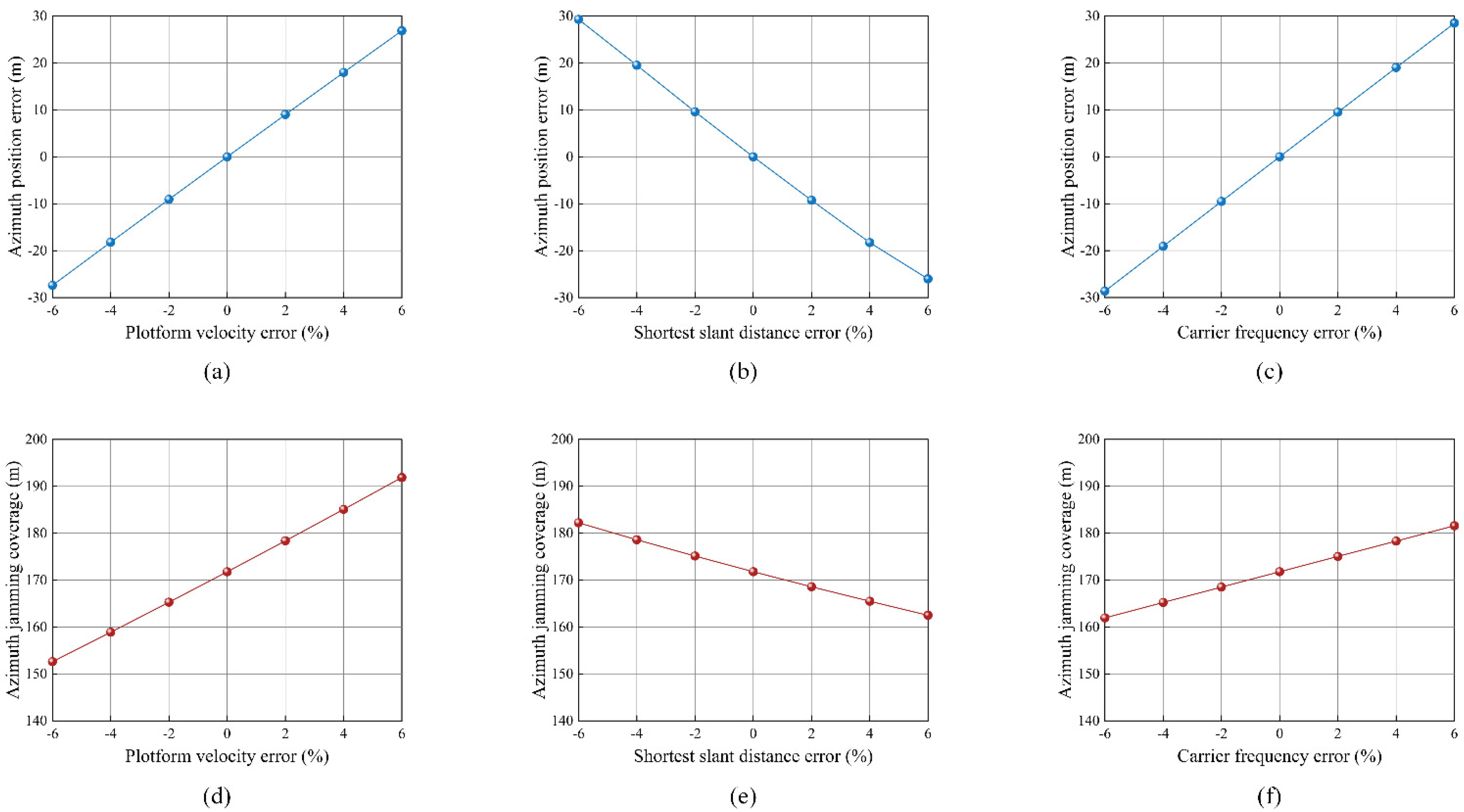
3.2. Analysis of Measurement Error
3.2.1. Platform Velocity Error
3.2.2. Shortest Slant Distance Error
3.2.3. Carrier Frequency Error
4. Simulation and Results
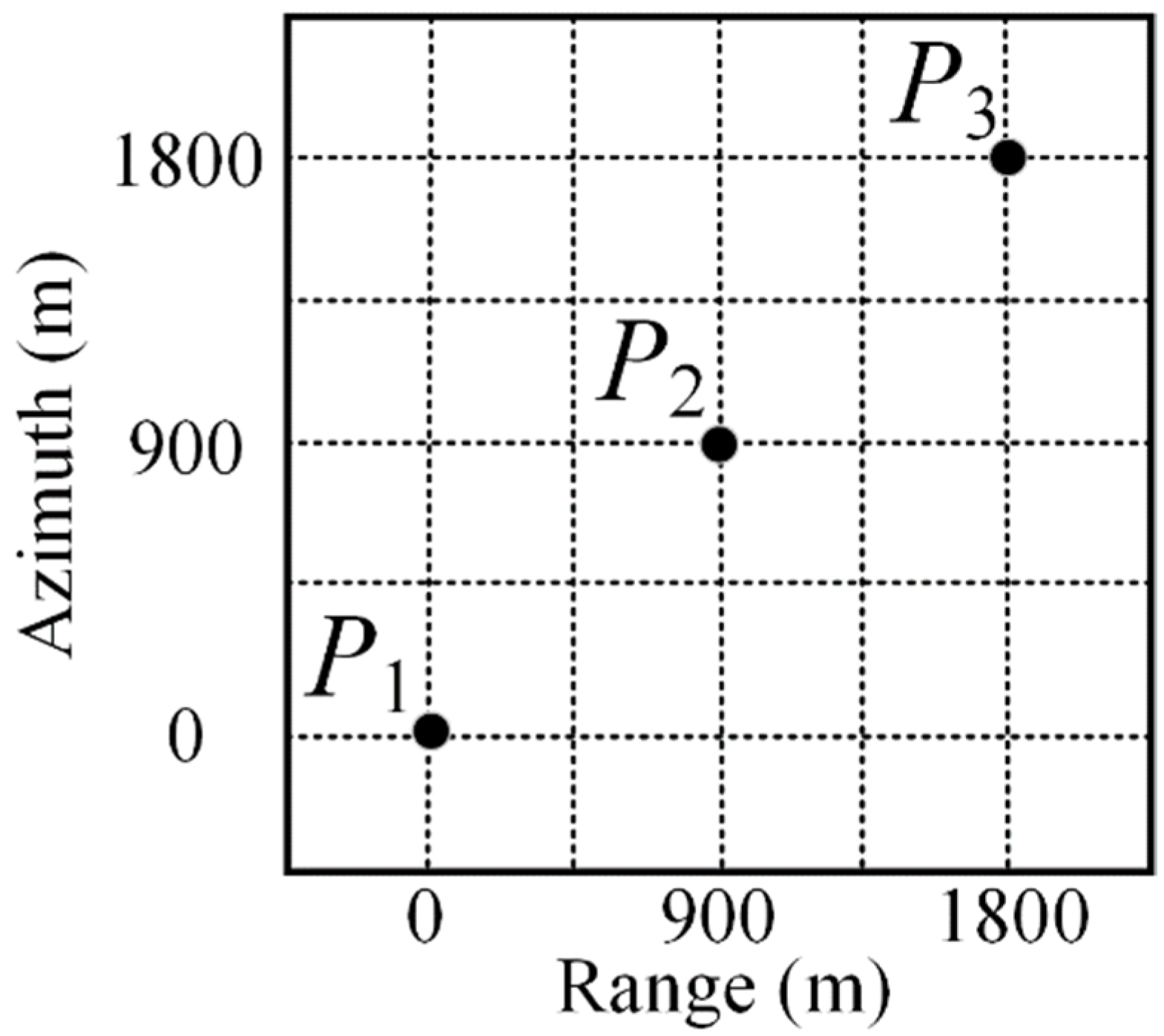
4.1. Point Target Simulation Experiment
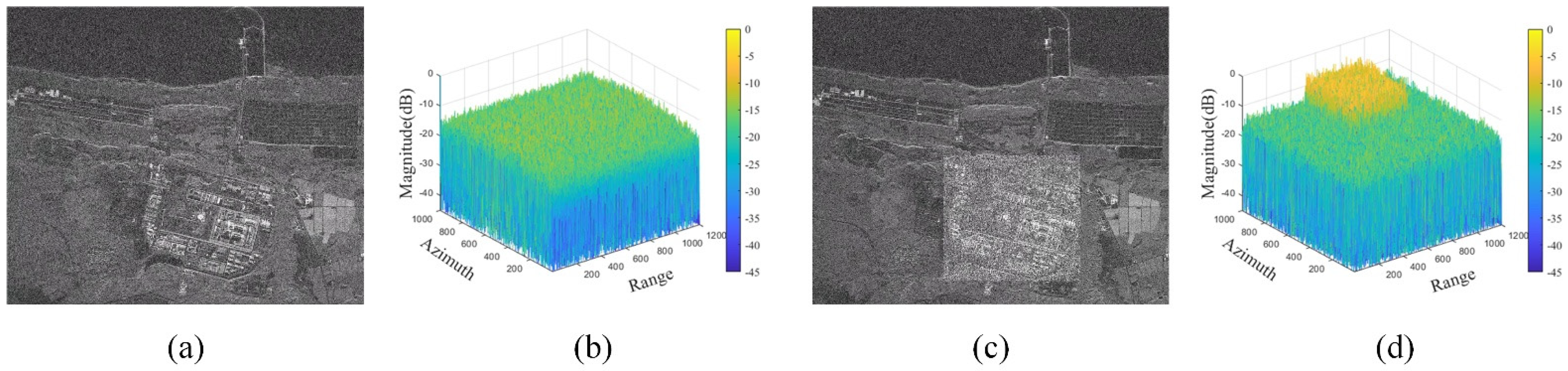
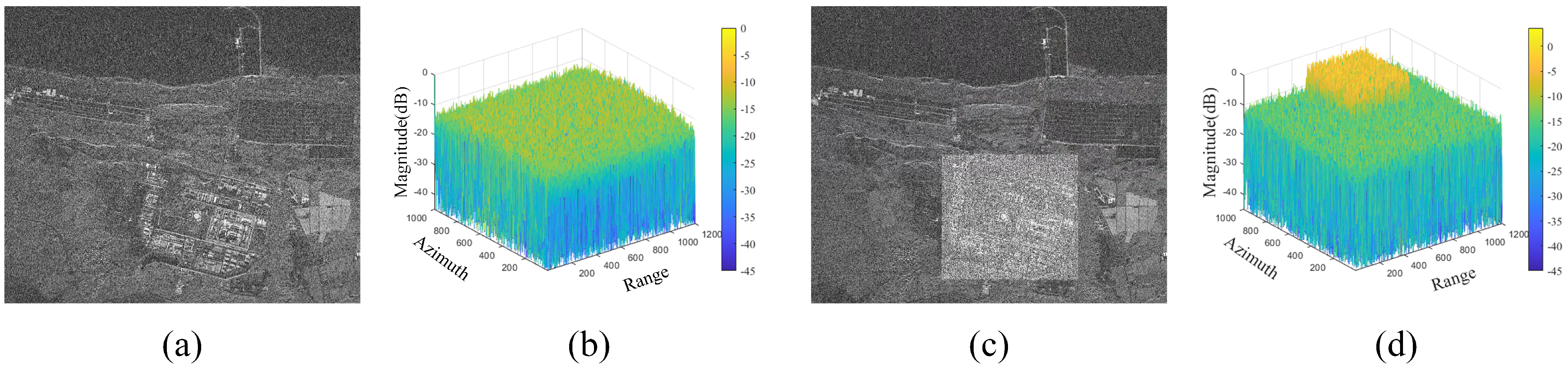
4.2. Area Target Simulation Experiment
| Methods | |||
|---|---|---|---|
| Convolution jamming | 0.2377 | 0.1845 | 0.1396 |
| Propose method | 0.2206 | 0.1677 | 0.1271 |
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Reigber, A.; Scheiber, R.; Jager, M.; Prats-Iraola, P.; Hajnsek, I.; Jagdhuber, T.; Papathanassiou, K.P.; Nannini, M.; Aguilera, E.; Baumgartner, S.; et al. Very-high-resolution airborne synthetic aperture radar imaging: Signal processing and applications. Proc. IEEE 2013, 101, 759–783. [Google Scholar]
- Moreira, A.; Prats-Iraola, P.; Younis, M.; Krieger, G.; Hajnsek, I.; Papathanassiou, K.P. A tutorial on synthetic aperture radar. IEEE Geosci. Remote Sens. Mag. 2013, 1, 6–43. [Google Scholar]
- Li, N.; Lv, Z.; Guo, Z. Pulse RFI mitigation in synthetic aperture radar data via a three-step approach: Location, notch, and recovery. IEEE Trans. Geosci. Remote Sens. 2022, 60, 1–17. [Google Scholar]
- Cai, Y.; Li, J.; Yang, Q.; Liang, D.; Liu, K.; Zhang, H.; Lu, P.; Wang, R. First demonstration of RFI mitigation in the phase synchronization of LT-1 bistatic SAR. IEEE Trans. Geosci. Remote Sens. 2023, 61, 1–19. [Google Scholar] [CrossRef]
- Fu, Z.; Zhang, H.; Zhao, J.; Li, N.; Zheng, F. A modified 2-D notch filter based on image segmentation for RFI mitigation in synthetic aperture radar. Remote Sens. 2023, 15, 846. [Google Scholar] [CrossRef]
- Li, N.; Zhang, H.; Lv, Z.; Min, L.; Guo, Z. Simultaneous screening and detection of RFI from massive SAR images: A case study on European Sentinel-1. IEEE Trans. Geosci. Remote Sens. 2022, 60, 1–17. [Google Scholar]
- Sun, H.; Shimada, M.; Xu, F. Recent advances in synthetic aperture radar remote sensing—Systems, data processing, and applications. IEEE Geosci. Remote Sens. Lett. 2017, 14, 2013–2016. [Google Scholar]
- Zhou, F.; Sun, G.; Bai, X.; Bao, Z. A novel method for adaptive SAR barrage jamming suppression. IEEE Geosci. Remote Sens. Lett. 2012, 9, 292–296. [Google Scholar] [CrossRef]
- Cheng, Y.; Zhu, D.; Jin, G.; Zhang, J.; Niu, S.; Wang, Y. A novel intrapulse repeater mainlobe-jamming suppression method with MIMO-SAR. IEEE Geosci. Remote Sens. Lett. 2022, 19, 1–5. [Google Scholar]
- Bang, H.; Wang, W.-Q.; Zhang, S.; Liao, Y. FDA-based space–time–frequency deceptive jamming against SAR imaging. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 2127–2140. [Google Scholar] [CrossRef]
- Bai, B.; Liu, Y.; Song, L.; Li, X.; Ding, Y.; Zhang, X. Passive radar jamming: A novel method using time-varying plasma. IEEE Access 2019, 7, 120082–120088. [Google Scholar]
- Li, Y.; Huang, D.; Xing, S.; Wang, X. A review of synthetic aperture radar jamming technique. J. Radars 2020, 9, 753–764. [Google Scholar]
- Huang, Y.; Zhao, B.; Tao, L.; Chen, Y.; Hong, W. Review of synthetic aperture radar interference suppression. J. Radars 2020, 9, 86–106. [Google Scholar]
- Sun, Q.; Shu, T.; Tang, M.; Yu, K.-B.; Yu, W. Effective moving target deceptive jamming against multichannel SAR-GMTI based on multiple jammers. IEEE Geosci. Remote Sens. Lett. 2020, 17, 441–445. [Google Scholar]
- Chang, X.; Li, Y.; Zhao, Y. An improved scattered wave deceptive jamming method based on a moving jammer beam footprint against a three-channel short-time SAR GMTI. IEEE Sens. J. 2021, 21, 4488–4499. [Google Scholar]
- Cheng, D.; Liu, Z.; Guo, W.; Gao, S.; Li, N. A repeater-type SAR deceptive jamming method based on joint encoding of amplitude and phase in the intra-pulse and inter-pulse. Remote Sens. 2022, 14, 4597. [Google Scholar] [CrossRef]
- Dong, C.; Chang, X. A novel scattered wave deceptive jamming against three channel SAR GMTI. IEEE Access 2018, 6, 53882–53889. [Google Scholar]
- Huang, B.; Wang, W.-Q.; Zhang, S.; Wang, H.; Gui, R.; Lu, Z. A novel approach for spaceborne SAR scattered-wave deceptive jamming using frequency diverse array. IEEE Geosci. Remote Sens. Lett. 2020, 17, 1568–1572. [Google Scholar]
- Zhang, J.; Dai, D.; Xing, S.; Xiao, S.; Pang, B. A Novel Barrage Repeater Jamming against SAR-GMTI. In Proceedings of the 10th European Conference on Antennas and Propagation, Davos, Switzerland, 10–15 April 2016; pp. 1–5. [Google Scholar]
- Cheng, D.; Li, N.; Shu, G.; Guo, Z. Multiple-Phases-Sectionalized-Modulation SAR Barrage Jamming Method Based on NLFM Signal. In Proceedings of the 2022 IEEE International Conference on Image Processing, Bordeaux, France, 16–19 October 2022; pp. 3046–3050. [Google Scholar]
- Garmatyuk, D.S.; Narayanan, R.M. ECCM capabilities of an ultrawideband bandlimited random noise imaging radar. IEEE Trans. Aerosp. Electron. Syst. 2002, 38, 1243–1255. [Google Scholar] [CrossRef]
- Liu, Q.; Xing, S.; Wang, X.; Dong, J.; Dai, D. A strip-map SAR coherent jammer structure utilizing periodic modulation technology. Prog. Electromagn. Res. B 2011, 28, 111–128. [Google Scholar] [CrossRef]
- Wang, W.; Cai, J. A technique for jamming bi- and multistatic SAR systems. IEEE Geosci. Remote Sens. Lett. 2007, 4, 80–82. [Google Scholar] [CrossRef]
- Wang, S.; Yu, L.; Ni, J.; Zhang, G. A study on the active deceptive jamming to the SAR. Acta Electron. Sin. 2003, 31, 1900. [Google Scholar]
- Liu, Y.-X.; Zhang, Q.; Xiong, S.-C.; Wang, H.-B.; Yuan, H.; Luo, Y. A Multiple-False-Target ISAR Shape Deception Jamming Method Based on Improved Template Multiplication Modulated Time-Delay Algorithm and Sub-Nyquist Sampling. Remote Sens 2023, 15, 5015. [Google Scholar]
- Sun, G.; Zhou, F.; Xing, M.; Bao, Z. Deceptive-jamming technology against the SAR based on the deceptive scene and real-time analyses. J. Xidian Univ. 2009, 36, 813–818. [Google Scholar]
- Zhou, F.; Zhao, B.; Tao, M.; Bai, X.; Chen, B.; Sun, G. A large scene deceptive jamming method for space-borne SAR. IEEE Trans. Geosci. Remote Sens. 2013, 51, 4486–4495. [Google Scholar]
- Yang, K.; Ye, W.; Ma, F.; Li, G.; Tong, Q. A large-scene deceptive jamming method for space-borne SAR based on time-delay and frequency-shift with template segmentation. Remote Sens. 2019, 12, 53. [Google Scholar] [CrossRef]
- Yang, K.; Ye, W.; Wu, X.; Ma, F.; Li, G. Fast generation of deceptive jamming signal against space-borne SAR. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2020, 13, 5580–5596. [Google Scholar]
- Chang, X.; Dong, C. A barrage noise jamming method based on double jammers against three-channel SAR GMTI. IEEE Access 2019, 7, 18755–18763. [Google Scholar]
- Wang, Y.; Liu, G.; Ma, X.; Song, C.; Jin, G.; Li, L. A Convolution Modulation Jamming Method Based on the Optimal Combination of Noise Templates. IEEE Geosci. Remote Sens. Lett. 2024, 21, 1–5. [Google Scholar]
- Liu, Y.; Wang, W.; Dai, S.; Rao, B.; Wang, G. Transmitter Power Comparison between Incoherent Noise and Coherent Deceptive Jamming against Synthetic Aperture Radar. In Proceedings of the 2017 IEEE Microwaves, Radar and Remote Sensing Symposium, Kiev, Ukraine, 29–31 August 2017; pp. 279–284. [Google Scholar]
- Chen, T.; Zhe, Z. Research on Smart Noise Frequency Modulation Jamming Technology Based on Convolution Modulation. In Proceedings of the 2024 9th International Conference on Electronic Technology and Information Science (ICETIS), Hangzhou, China, 17–19 May 2024; pp. 195–199. [Google Scholar]
- Abouelfadl, A.; Samir, A.M.; Ahmed, F.M.; Asseesy, A.H. Performance Analysis of LFM Pulse Compression Radar under Effect of Convolution Noise Jamming. In Proceedings of the 2016 33rd National Radio Science Conference, Aswan, Egypt, 22–25 February 2016; pp. 282–289. [Google Scholar]
- Gong, S.; Wei, X.; Li, X.; Ling, Y. Mathematic principle of active jamming against wideband LFM radar. J. Syst. Eng. Electron. 2015, 26, 50–60. [Google Scholar]
- Hao, H.; Zeng, D.; Ge, P. Research on the Method of Smart Noise Jamming on Pulse Radar. In Proceedings of the 2015 Fifth International Conference on Instrumentation and Measurement, Computer, Communication and Control, Qinhuangdao, China, 18–20 September 2015; pp. 1339–1342. [Google Scholar]
- Gong, S.; Wei, X.; Li, X.; Ling, Y. Two-dimensional discretized coherent noise jamming method to wideband LFM radar. Prog. Electromagn. Res. Lett. 2014, 49, 15–22. [Google Scholar] [CrossRef]
- Ammar, M.A.; Hassan, H.A.; Abdel-Latif, M.S.; Elgamel, S.A. Performance evaluation of SAR in presence of multiplicative noise jamming. In Proceedings of the 2017 34th National Radio Science Conference (NRSC), Alexandria, Egypt, 13–16 March 2017; pp. 213–220. [Google Scholar]
- Zhang, Y. Technology of Smart Noise Jamming Based on Multiplication Modulation. In Proceedings of the 2011 International Conference on Electric Information and Control Engineering, Wuhan, China, 15–17 April 2011; pp. 4557–4559. [Google Scholar]
- Ye, W.; Ruan, H.; Zhang, S.; Yan, L. Study of Noise Jamming Based on Convolution Modulation to SAR. In Proceedings of the 2010 International Conference on Computer, Mechatronics, Control and Electronic Engineering, Changchun, China, 24–26 August 2010; pp. 169–172. [Google Scholar]
- Zhou, C. Study of convolution jamming technology of synthetic aperture radar. Shipboard Electron. Countermeas. 2013, 35, 6–10. [Google Scholar]
- Fang, M.; Wang, G.; Lei, L. Study on 2D Noise Convolution Modulation Jamming to SAR. Mod. Def. Technol. 2014, 42, 139–144+160. [Google Scholar]
- Jiang, J.; Wu, Y.; Wang, H.; Chen, J. A dense false target jamming technique against SAR-GMTI. Shipboard Electron. Countermeas. 2016, 39, 9–14. [Google Scholar]
- Huang, D.; Xing, Q.; Li, Y.; Liu, Y.; Xiao, S. Smart jamming method against SAR based on multiplication modulation. Syst. Eng. Electron. 2020, 43, 3160–3168. [Google Scholar]
- Huang, D.; Xing, S.; Liu, Y.; Li, Y.; Xiao, S. Fake SAR signal generation method based on noise convolution modulation. J. Radars 2020, 9, 898–907. [Google Scholar]
- Wang, Y.; Liu, Z.; Huang, Y.; Li, N. Multitarget Barrage Jamming Against Azimuth Multichannel HRWS SAR via Phase Errors Modulation of Transmitted Signal. IEEE Geosci. Remote Sens. Lett. 2024, 21, 1–5. [Google Scholar] [CrossRef]



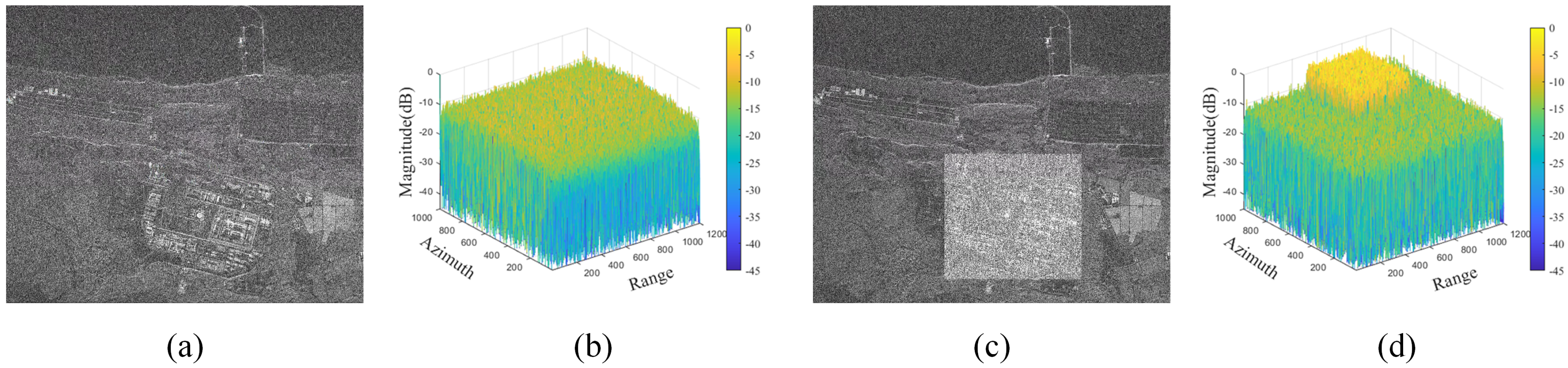
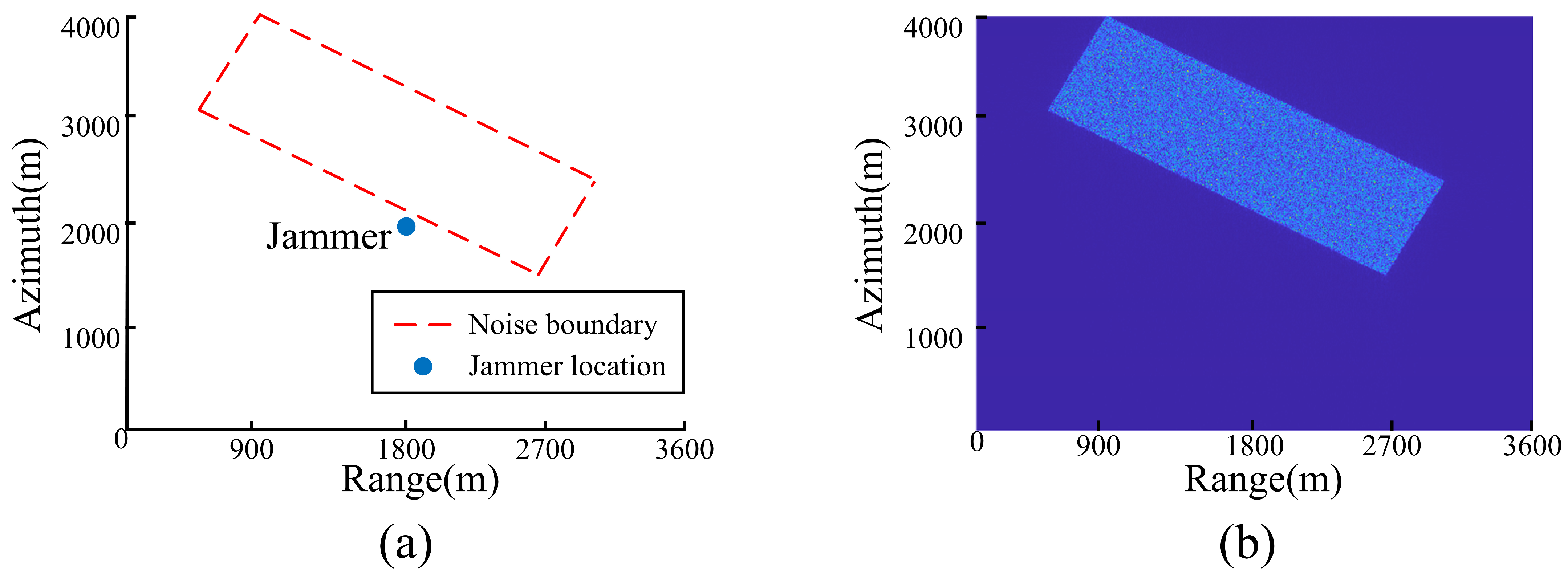
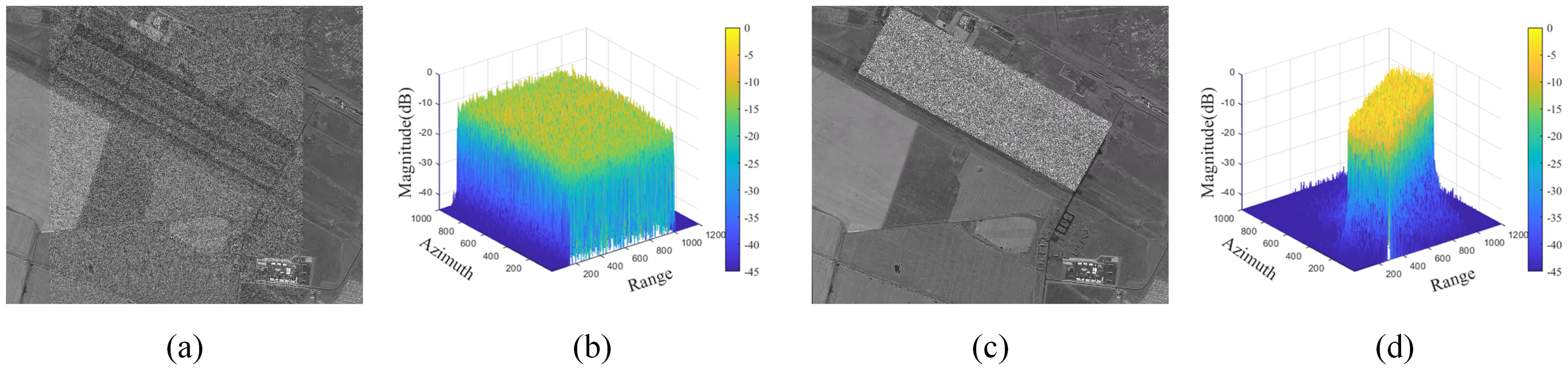
| Parameters | Values |
|---|---|
| Carrier frequency | 5.4 GHz |
| Platform velocity | 6637 m/s |
| Pulse width | 51 μs |
| Band width | 42 MHz |
| Pulse repetition frequency | 1663 Hz |
| Closest slant range | 800 km |
| Antenna length | 12.3 m |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Guo, Z.; Wang, L.; Liu, Z.; Fu, Z.; Li, N.; Zhang, X. Adaptive Barrage Jamming Against SAR Based on Prior Information and Scene Segmentation. Remote Sens. 2025, 17, 1303. https://doi.org/10.3390/rs17071303
Guo Z, Wang L, Liu Z, Fu Z, Li N, Zhang X. Adaptive Barrage Jamming Against SAR Based on Prior Information and Scene Segmentation. Remote Sensing. 2025; 17(7):1303. https://doi.org/10.3390/rs17071303
Chicago/Turabian StyleGuo, Zhengwei, Longyuan Wang, Zhenchang Liu, Zewen Fu, Ning Li, and Xuebo Zhang. 2025. "Adaptive Barrage Jamming Against SAR Based on Prior Information and Scene Segmentation" Remote Sensing 17, no. 7: 1303. https://doi.org/10.3390/rs17071303
APA StyleGuo, Z., Wang, L., Liu, Z., Fu, Z., Li, N., & Zhang, X. (2025). Adaptive Barrage Jamming Against SAR Based on Prior Information and Scene Segmentation. Remote Sensing, 17(7), 1303. https://doi.org/10.3390/rs17071303








