1. Introduction
Underwater communications have attracted much interest in recent years due to the rapid development of ocean exploration. Reliable data transmission among nodes is the basis of many underwater applications, such as tsunami warning, ecological monitoring, off-shore oil exploration, etc. [
1]. Compared to other media, acoustic waves are the only means of achieving reliable underwater transmission over a long distance. However, underwater acoustic (UWA) communications also face some difficulties compared to their terrestrial counterparts. The characteristics of UWA channels include large delay and Doppler spread, high path attenuation, limited bandwidth, and long propagation delay, which severely reduce the reliability of underwater transmissions.
Generally speaking, redundancy and retransmission are the two main approaches to enable a robust communication link. Retransmission schemes such as automatic repeat request (ARQ) are widely used in terrestrial wireless communications. However, the long propagation delay caused by the slow speed of acoustic waves (approximately 1500 m/s) in water makes the standard ARQ scheme very inefficient in UWA communications. Thus, there have been many modified ARQ schemes proposed for UWA communications, such as the go-back
N scheme, the stop-and-wait (S&W) scheme and the selective repeat (SR) scheme [
2,
3]. These modified ARQ schemes improve the efficiency compared to standard ARQ, but not well enough. This is because the sender always remains idle when it is waiting for the receiver’s acknowledgement (ACK) messages in these schemes. As a result, they are still quite inefficient when the propagation time is long enough. In [
4,
5], a juggling-like ARQ scheme (J-ARQ) is proposed to further improve the channel utilization, where the sender reserves a fixed gap for the ACK reception after each transmission. In this way, the sender still could transmit the data when it is awaiting the ACK. However, the fixed transmission and reception duration are used in the J-ARQ scheme to avoid conflict, which will lead to a decrease in transmission efficiency when the transmitter does not have an infinite amount of data waiting to be transmitted [
5].
Compared to retransmission, the redundancy strategy alternatively seeks an attempt to improve the quality of each transmission. A common redundancy technique is forward error control (FEC), which can lower the bit error rate (BER) at the cost of reducing the data rate. For example, bit-level channel coding schemes, such as low-density parity codes [
6] and convolutional codes [
7], have been widely used in the physical layer of UWA communications. In contrast, in this paper we investigate another FEC technique, which is performed on the packet level and designed for the link layer [
8,
9,
10,
11,
12,
13,
14,
15,
16,
17]. Its mechanism is that the sender sends multiple coded packets which are encoded by original packets. The receiver can recover the original packets correctly if there are enough coded packets successfully received. Rateless codes [
18,
19,
20], as a good packet-coding technology, have been used in UWA communications. These codes are so named since the sender can generate unlimited coded packets to ensure that the original packets can be fully recovered. In [
12], a kind of rateless code, Raptor code, is used in UWA communications. The coding rate is optimized to maximize the throughput over UWA channels. In [
13], a cross-layer FEC scheme which combines both the physical layer FEC and the packet layer FER is extended based on [
12].
So far, there have been many works which combine the redundancy strategy and retransmission strategy based on the rateless codes. In [
5], rateless code is used in the J-ARQ scheme. In [
10], an HARQ scheme is proposed, named segmented data reliable transport (SDRT), to achieve reliable data transmission in UWA sensor networks by employing Tornado codes. In this scheme, the sender keeps sending the packets until it receives an ACK. In order to reduce the energy consumption for unnecessary transmission, a window control mechanism is further proposed to estimate the expected number of packets actually needed. With the information, the sender just transmits a pre-estimated number of encoder packets (i.e., the window size), and then slows down the transmission to wait for an ACK. In [
11], an underwater hybrid ARQ (UW-HARQ) is proposed which uses an NACK to feed back the receive state. Random linear packet coding (RLPC) is used as a rateless code in [
14,
15,
16]. In [
14], the optimal number of coded packets is investigated for a half-duplex link to minimize the time (or energy) required for the transmission of a group of packets. In [
15], joint power and rate control for an acoustic link employing random linear packet coding is considered to achieve a prespecified outage/reliability criterion. To this end, ref. [
16] extends the work in [
15] by grouped packet coding and increases its throughput efficiency based on the S&W ARQ scheme. The sender transmits a super-group packets and waits for an ACK. This could improve efficiency by packing multiple packets together.
In this paper, we propose two adaptive packet-coding schemes to achieve reliable UWA communications. We consider the time variations of UWA channels, which are ignored in most works. Since we focus on the link level performance, we model the channel state by a finite-state Markov chain (FSMC) [
21]. Some works use FSMC to model the UWA channels [
22,
23,
24,
25,
26,
27,
28]. In [
22,
23], Preisig used a two-state FSMC channel model with known transition probabilities to evaluate energy-efficient schedulers for underwater acoustic point-to-point links based on experimental data. As compared to existing works, our main contributors are summarized as follows:
- (1)
We first propose an S&W ARQ scheme with RLPC (RLPC-ARQ). In the RLPC-ARQ scheme, the number of successfully transmitted packets in each transmission and the channel state information (CSI) are fed back to the sender in the ACK messages. The sender dynamically adjusts the coding rate based on the ACK messages to fit the time variations of UWA channels by choosing the optimal number of packets in each transmission. Meanwhile, considering the long propagation delay and the error-prone characteristic of UWA communications, we set a maximum number of retransmissions to avoid infinite retransmission. The problem is formulated as a finite horizon optimization problem. A dynamic programming (DP) algorithm is proposed to obtain the optimal number of packets in each transmission.
- (2)
We also propose a modified juggling-like ARQ scheme for the RLPC system (RLPC-J-ARQ) to deal with the long propagation of UWA channels. In the RLPC-J-ARQ scheme, two data blocks are alternately transmitted at the sender; there is no need to stop and wait for the ACK. Different from the J-ARQ scheme in [
5] for which the duration of each transmission is fixed, the RLPC-J-ARQ scheme adopts adjustable transmission duration by exploiting the characteristics of the rateless code. The rateless code is only used when there is not enough data to transmit to avoid idleness. In addition, we also consider the effect of channel variation. In this case, the standard DP algorithm does not work. Thus, we also propose a two-step DP algorithm to find out the optimal number of packets in each transmission.
The rest of this paper is organized as follows.
Section 2 presents the basic system model. We formulate the optimization problem in
Section 3. We propose the optimization solution based on the principle of DP in
Section 4.
Section 5 proposes the RLPC-J-ARQ scheme.
Section 6 proposes a two-step DP approach to find out the optimal solution of the RLPC-J-ARQ scheme.
Section 7 provides numerical results for the proposed solutions and
Section 8 concludes the paper.
2. System Model
We consider a point-to-point system operating in a half-duplex manner without interference from other nodes. The sender collects
information packets. Each packet has
symbols and
is a constant number during the transmission. These information packets are first divided into multiple blocks, each containing
W packets. In this paper, we only consider the FEC technique in the packet level. The
W original packets in each block are then encoded based on the RLPC [
14,
15,
16] to generate sufficient coded packets. We assume that the data is delay constrained, which means the receiver should receive the data before the deadline. Otherwise, the data becomes useless.
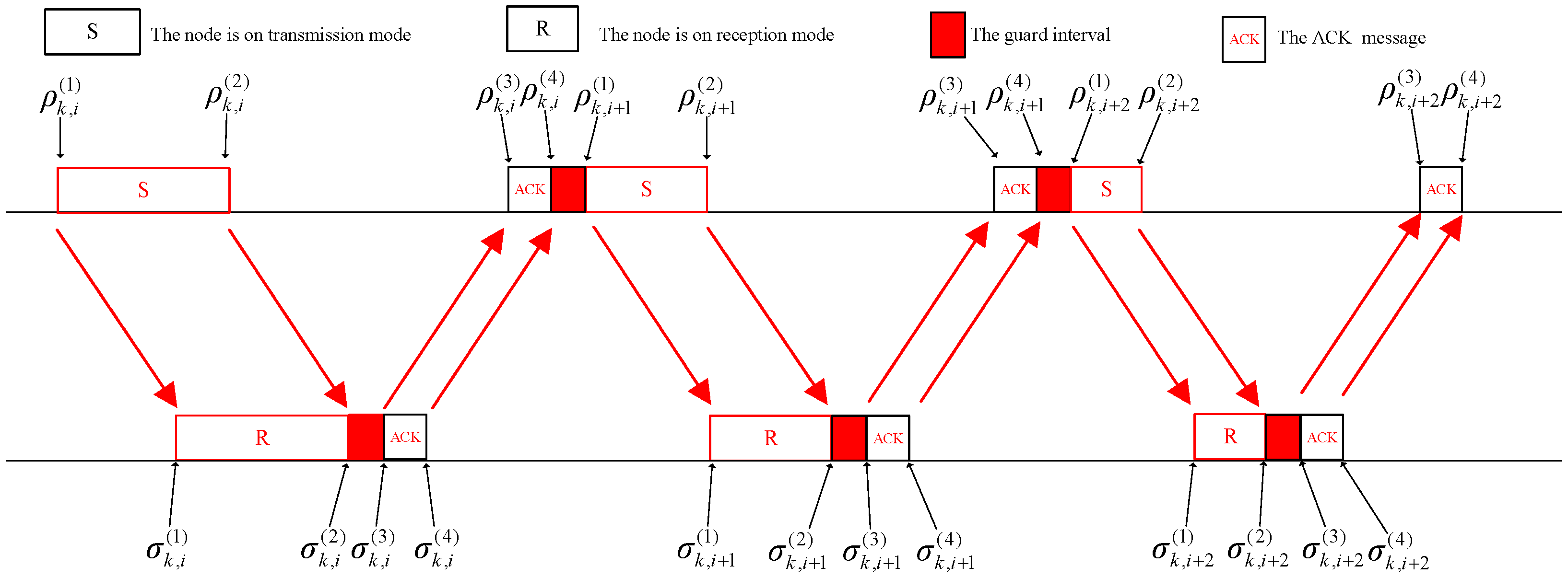
We first consider an S&W ARQ scheme with RLPC, which is illustrated in
Figure 1. The coded packets from different blocks are transmitted in sequence. Let
denotes the number of transmitted packets for the
k-th block in the
i-th transmission. Let
and
denote the beginning and ending time instants of the
k-th block in the
i-th transmission. Hence, the relationship between them is
where
is the time duration of a coded packet,
is the symbol duration.
Let
denote the propagation delay. Then, the transmitted signal is received after
duration,
, where
d is the distance between the transceiver pair, and
c is the sound speed in water. Let
and
denote the beginning and ending time instants of the received signal at the receiver. Then, we have
When the receiver completes the receiving process, there is a guard interval, , for the receiver node to process the data and change the mode. Next, the receiver responds with an ACK. According to the characteristic of RLPC, the receiver can recover the original information if there are enough coded packets successfully received. Thus, we do not need to retransmit the unsuccessful packets in the following transmission. In the following transmission, the sender will send enough other coded packets. It is noted that the other coded packets are also generated from the same information packets. There is the main different from the traditional ARQ scheme. Hence, the ACK contains the number of successfully received packets in the current transmission and some pilot symbols used for channel estimation at the sender.
The BER e depends on the channel coding rate, the modulation order, the channel state, and the codeword length. In this paper, these parameters are fixed except the channel state. Thus, the packet error probability (PEP) is only connected with the channel state.
As mentioned above, we focus on the link level performance, so we model the channel state by a finite-state Markov chain (FSMC) [
22,
24,
25]. Assume the channel state is constant during the
i-th transmission. Let
denote the CSI when the
k-th block is transmitted at the
i-th transmission, which is quantized into
L levels, i.e.,
. The state transition probabilities
are assumed known.
Let
denote the probability that
coded packets have been successfully received when
coded packets are transmitted under the channel state
. Then,
Let
and
denote the beginning and ending time points for the ACK at the receiver. Then, the relationship is given as
where
is the time duration of ACK.
The sender will receive the corresponding ACK after
time duration. Let
and
denote the beginning and ending time points for the received ACK at the sender. Then,
The sender could estimate the CSI based on the pilot symbols in the ACK and decode the feedback messages . We use a low rate channel code for ACK messages to improve the reliability of feedback messages. To reduce the complexity of the problem, we assume the feedback messages are error-free.
There is also a guard interval for the sender to process the ACK and change the mode. In this way, the
i-th transmission for the
k-th block is done. Hence, the total time duration for the
i-th transmission is given as
where
is fixed for each transmission.
If the receiver has received enough coded packets to recover the original information from the k-th block, the sender will send the coded packets from another block in the next transmission. Otherwise, the sender determines the number of transmitted coded packets in the -th transmission based on the feedback ACK. Thus, the data rate of packet coding is not constant during the transmission. The sender dynamically adjusts the rate based on the current transmission result to adapt to the time variation of UWA channels.
3. Problem Formulation
Assume that the receiver has successfully demodulated
packets from the
k-th block in the previous
transmissions according to the feedback messages. Then,
is given by
According to the characteristics of RLPC, the information packets can be recovered correctly if [
15,
16]
Then, according to (
8), we have
Let
denote the minimum number of packets needed to guarantee correct decoding. Thus, the probability of
W information packets can be received correctly after the
i-th transmission is given by
It is obvious that the number of transmitted packets during the
i-th transmission,
, cannot exceed a maximal level, denoted by
. Then,
Our objective is to minimize the total transmission time of data blocks for delay-constrained applications by adjusting the packet-coding rate. Since the packet error is a stochastic process, there are certainly cases where the information cannot be received correctly after many transmissions, especially for error-prone UWA channels. However, considering the significant propagation delay of UWA channels, too many retransmissions is unacceptable in a practical communications system. Thus, we should set a maximal number of retransmissions, M.
To make sure that
W information packets can be received correctly after
M transmissions, we add a penalty term for the
M-th transmission. In this way, the transmission time of the
M-th transmission is given by
where
C is a large value. This setting implies that if the information cannot be recovered correctly after M transmissions, it will incur a large cost.
Then, the objective function is given by
where
is discount factor. Consider the cost of storage space and number overhead,
.
Naturally, there is a trade-off between the coding rate and the transmission time. Generally speaking, sending more coded packets will improve the reliability of each transmission. Moreover, it will reduce the probability of retransmission and then reduce the total transmission time. However, if we send too many packets in each transmission, the sending time also increases, which also decreases efficiency. Thus, there is an optimal coding rate for each transmission to minimize the total transmission time.
4. Optimal Solution
In our problem, the state of the
i-th transmission is dependent on the result of
-th transmission. Meanwhile, since packet error is a stochastic process, this problem can be seen as a sequential decision-making problem. This problem can be solved by the finite-horizon DP [
24,
25,
29] approach.
Let
denote the state of the system at the
i-th transmission for the
k-th block, where
denotes the number of coded packets successfully received in the all
transmissions.
is the feedback channel state of the
-th transmission for the
k-th block. Let
denote the feasible set of the
action given the current state
. Then,
In this case, the upper limit of is constant. Thus, we let .
The probability that the system state
will transfer to state
when action
is taken is given as
The expected cost incurred from the
M-th transmission is given by
The first term of (
19) is the cost of the
M-th transmission, the second term is the expectation of penalty term due to the incomplete transfer after
M transmissions. It depends on the result of the
M-th transmission according to (
14).
Based on the Bellman equation [
29], the optimal solution can be obtained by recursively computing
,
, …,
. The expected cost incurred from the
i-th transmission to termination is given by
The first term in (
21) represents the expected cost of current transmission. The second term in (
21) is the expected future cost accumulated from the
-th transmission to the
M-th transmission.
The DP approach includes two steps. In step 1, the sender calculates the (
21) to find the optimal
for each system state
and records it as a lookup table. In step 2, the sender chooses the optimal
of the current state based on the lookup table.
5. RLPC-J-ARQ Scheme
In the RLPC-ARQ scheme, the sender idles for a round-trip time while waiting for the ACK. This is quite inefficient for UWA communications, which have a long propagation delay. Ref. [
5] proposed the J-ARQ to solve this problem. However, the block size of J-ARQ is fixed, which leads to the analysis in [
5]; it cannot be directly applied in this problem. Essentially, the J-ARQ scheme uses the time that the feedback information is transmitted in the channel to send the following data blocks. According to this idea, we propose a RLPC-J-ARQ in our problem.
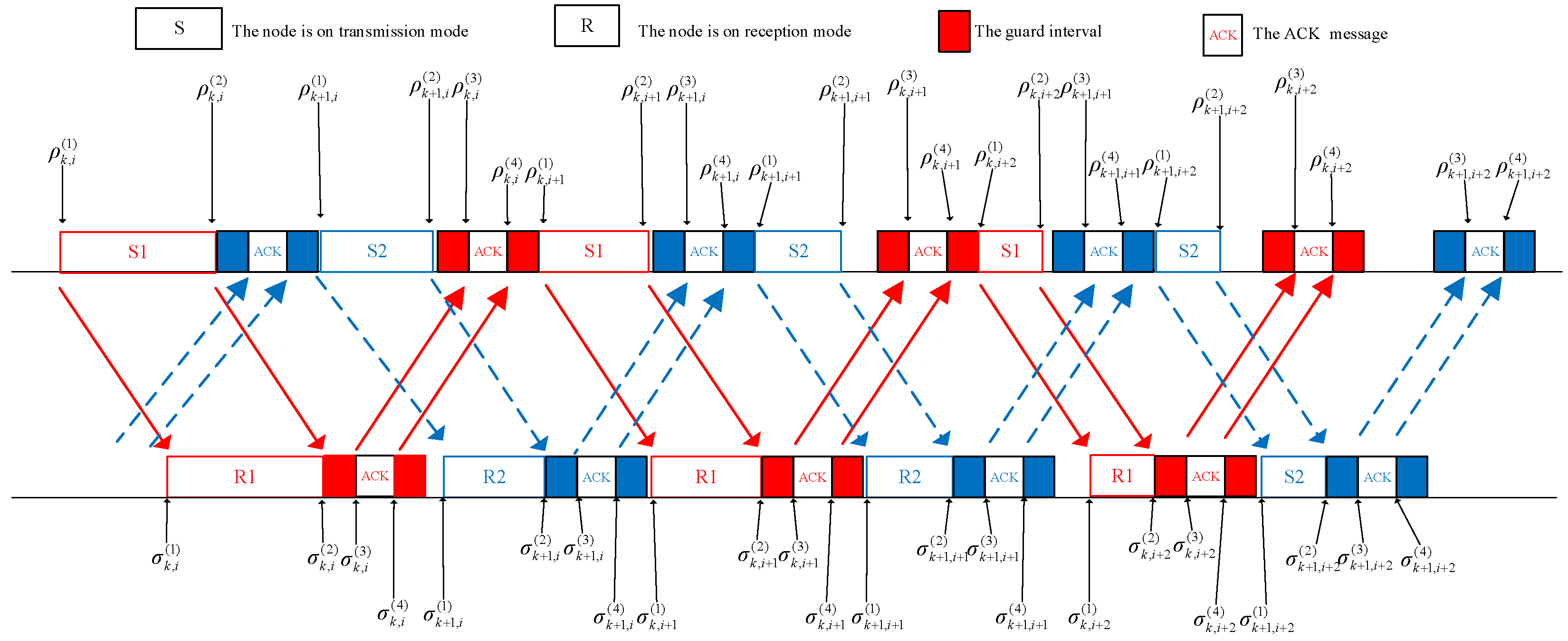
Figure 2 illustrates the transmission style of the RLPC-J-ARQ scheme. We only consider that two blocks are transmitted simultaneously. The sender leaves a gap after sending
coded packets for receiving the ACK messages. Similarly, a guard interval is reserved for the node to change the mode. Next, the sender sends
data packets for the (
k + 1)-th block. In this way, the transmitter could send more data blocks than the RLPC-ARQ scheme.
In
Figure 2,
and
represent the time points for the sender and receiver with the
-th block, respectively. The relationship between the time instants
and
are similar to those of the
k-th block. According to
Figure 2, there are some constraints about the time instants to avoid the collision. At the sender, we have
According to (1), (2), (4) and (5), the relationship between
and
is given as
At the receiver, there is the same relationship and . Similarly, there is the same relationship for the -th block.
Thus, according to the relationship in (
24), (
22) can be rewritten as
After further straightforward deduction, we have
Similar results can be obtained for the receiver, (
23) can be rewritten as
For the first transmission,
, the constraints at the sender are given by
Let
; according to (
28), the constraints about the initial time instant of the
-th block are given as
We set
. Namely, the sender sends the packets from the
-th block immediately once it is allowed to send. Meanwhile, the number of packets from the
-th block is also restricted,
To sum up, the constraints in our problem are as follows
According to (
31), the number of transmitted packets for the
-th block at the
i-th transmission does not exceed that of for the
k-th block at the
i-th transmission. The number of transmitted packets for the
k-th block at the
-th transmission doe not exceed that of for the
-th block at the
i-th transmission. If
or
, of course, there are no constraints about the
or
. Thus, the maximum number of transmitted packets in the
-th transmission are given by
There is a difference from the RLPC-ARQ scheme. In the RLPC-ARQ scheme, the sender can adjust the number of transmitted packets freely based on the feedback ACK. However, in this case, the number of transmitted packets in each transmission is monotone decreasing.
The transmission time duration for the
i-th transmission is also different. For the first transmission, the transmission time duration is given by
For the
i-th (
) transmission, if
, according to
Figure 2, the transmission time duration for the
i-th transmission is given by
In this case, it seems that the transmission time duration for the
i-th transmission has nothing to do with the number of transmitted packets from the
k-th block. However,
still affects the transmission time duration according to the constraints in (
31).
If
and
, the transmission time duration should be
However, it is difficult to calculate
since it connects with the number of transmitted packets in the first
transmissions. Thus, we let
approximate
,
In the same way, for the
M-th transmission, we also set the penalty term,
and
, where
is given in (
14).
The objective function is also given by
This problem is different from the problem in (
15). There are two parameters that need to be optimized for each transmission. At the begin of the
i-th transmission for the
k-th block, the sender does not receive the feedback message of the
-th transmission for the
-th block. Namely, the sender only knows part of the transmission result of the
-th transmission. Apparently, The standard DP approach is not suitable for this case. We propose a two-step DP approach to solve this problem.
6. Proposed Two-Step DP Approach
In each transmission, we separately define the system state for the k-th block and the -th block. For the k-th block, the system state is , , , , , where is the maximum number of transmitted packets for the k-th block. For the i-th transmission of the -th block, the sender already knows the transmission result of the -th transmission. Thus, the system state is , , , , .
As analyzed above, the problem for the RLPC-J-ARQ scheme is also a sequential decision-making problem. Thus, it could also be solved based on the DP approach. The main difference is that the and depend on the and , as given in (32) and (33), respectively. In other words, the state of the i-th transmission is not only related to the -th transmission, but also to .
Based on the idea of DP, we propose a two-step DP approach which computes the cost in two steps for each transmission. The proposed method still adopts recursive computing based on the Bellman equation. It is similar to the RLPC-ARQ scheme; we first calculate the cost of the M-th transmission, the i-th transmission and finally the first transmission. In each transmission, we first calculate the cost of the -th block. Then, the overall cost of the current transmission is calculated.
6.1. The Cost of the M-th Transmission
At the
M-th transmissions of the
-th block, the system state
,
,
,
,
. The expected cost of the
-th block at the
M-th transmission is similar to (
19), which can be computed as
where
is the transmission time duration for the
-th block. The expectation of penalty is given by
Next, we consider the expected cost for the overall M-th transmission, . At this point, the sender knows the system state , , , , .
It is clear that the calculation of highly depends on and . The state is different if and are larger or less than M. Thus, the calculation of is different with different and . So, the analysis of different situations is as follows.
If
and
, it is obvious that
If
and
, the transmission of the
k-th block is finished. Then,
. It degenerates into the problem in the RLPC-ARQ scheme. At this time, only the
-th block may need to be transmitted. It relies on the transmission result of the
-th transmission for the
-th block. According to (
32),
. Thus,
Note that .
If
and
, then
. This problem also degenerates into the former problem.
If
and
, then the expected cost for the overall
M-th transmission is given by
The first and second term in (
45) are the cost from the
k-th block; the third term is from the
-th block.
As analyzed in (
35), if
, the number of
does not affect the cost. Thus, in this case,
If
, then
. According to (
37), the expected additional transmission time duration for the
M-th transmission of the
k-th block is
. The corresponding probability is given by
To summarize, if
and
, the first term of (
45) is
The second term of (
45) is similar to (
41). The third term of (
45) is
In summary, the cost of the
M-th transmission is given as
6.2. The Cost of the i-th Transmission
For the
i-th transmission, the system state for the
-th block is
,
,
,
,
. The expected cost incurred from the
i-th transmission of the
-th block to termination is given as Equation (
51).
The conditional expectation in (
51) is given as
It is interesting that (
52) does not seem to have much to do with
. The transition probability mainly depends on the channel state
and the transmitted packets of
. However,
affects
by limiting the range of
in (
52).
For the
k-th block, the system state is
,
,
,
,
. The expected cost incurred from the
i-th transmission to termination is given by (
53). Similarly, we have
also has no influence on transfer probability and affects
by limiting the range of
.
6.3. The Cost of the First Transmission
For
,
,
,
,
,
. Note that
and the transmitter have no feedback information about the channels. Thus, we use the steady-state probability to present the probability. Then, we have
where
Similarly,
,
,
,
,
; the cost for the overall
M transmissions is given as
where
The two-step DP approach also first finds the optimal solution for each state and records it into a table. Then, the sender chooses the optimal
and
according to system state. The details of the proposed optimal two-step DP policy are summarized in Algorithm 1.
| Algorithm 1: The proposed two-step DP algorithm. |
- 1:
Let , , , , . - 2:
Calculate , , , , , , based on ( 39) and save in the table. - 3:
Let , , , , . - 4:
Calculate , , , , , , based on ( 50) and save in the table. - 5:
. - 6:
while - 7:
Let , , , , . - 8:
Calculate , , , , , based on ( 51) and save in the table - 9:
Let , , , , . - 10:
Calculate , , , , , based on ( 53) and save in the table - 11:
Find the optimal (, ) to maximize - 12:
; - 13:
end while - 14:
for; ; do - 15:
Find the optimal (, ) based on line 9. - 16:
Update the and . - 17:
end for
|
7. Simulation Results and Discussions
In this section, we analyze the performance of the proposed packet-coding scheme with the SR ARQ scheme. In the SR ARQ scheme, the transmitter sends W packets in each transmission and waits for the ACK messages. The transmitter retransmits the failed packets and the new packets to form a new group of packets in the next transmission.
Unless otherwise specified, the simulation parameters of the system are presented in
Table 1. We consider BPSK modulation and the UWA channels as a Markov Chain model. The communication link often exhibits ON/OFF behaviour in UWA communications. Therefore, we could model the channels as a two-state Markov Chain model [
22,
24]: “Bad (0)” and “Good (1)”. The BERs under the good and the bad channel conditions are
and
, respectively. The transition matrix of the channel state is [
24]
The steady-state probabilities are given by
whereas
. The steady-state probabilities could be used as the probabilities of CSI at the initial transmission, which does not have the feedback messages. In addition, we define a memory parameter
to present the time correlation of channel states. Then, the transition matrix of the channel state can be computed by
and
. In the simulation, we set
and
according to the experiment data given in [
23].
The PEP
depends on the length of packet
and the BER
e; it can be calculated from the equilibrium distribution of the generalized Pareto renewal process [
5]
where
is the shape parameter of the generalized Pareto distribution. In this paper, we use
.
For the J-ARQ scheme, the number of transmitted groups during a round-trip time is given by
We evaluate the performance based on the throughput efficiency, which is given by
where
is the probability of packet loss;
is the total transmission time duration.
As shown in [
5], the performance of the J-ARQ scheme depends on the number of source data. Thus, we first study the impact of the number of source data.
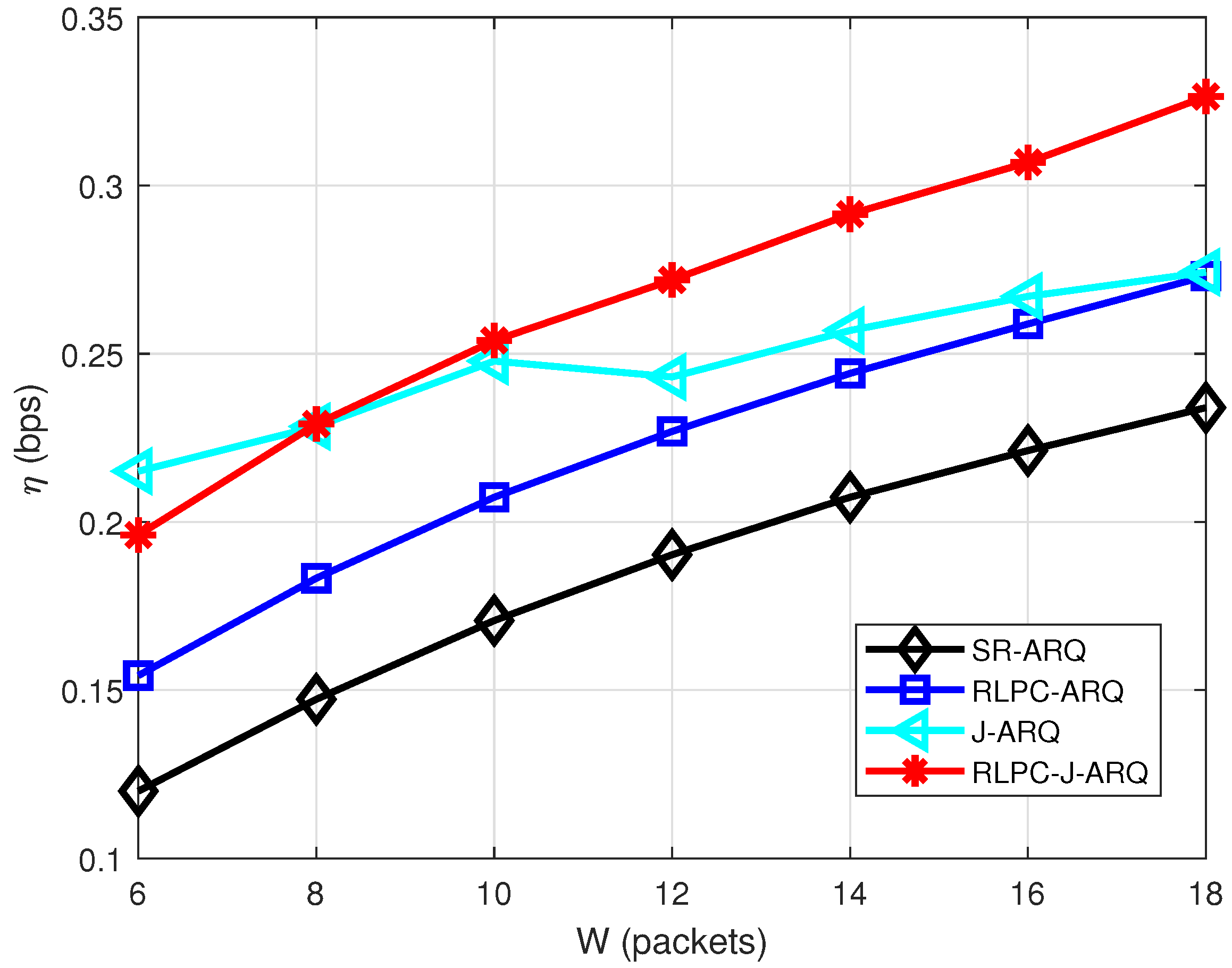
Figure 3 illustrates the throughput efficiency as a function of the number of source data packets
. From
Figure 3, we find the SR-ARQ scheme has the lowest throughput efficiency in all schemes. The throughput efficiency performance of conventional J-ARQ increases with the length of source data. If the sender has enough source data, the J-ARQ scheme has the best throughput efficiency. The performance of the RLPC-ARQ scheme and RLPC-J-ARQ is independent of data length. The throughput efficiency of RLPC-J-ARQ is better than RLPC-ARQ since it takes full advantage of the transmission time. When the data length is short, the performance of J-ARQ is worse than that of the RLPC-J-ARQ scheme. In the RLPC-J-ARQ scheme, the transmission duration is adjustable. Thus, it has a better performance when
is not big enough.
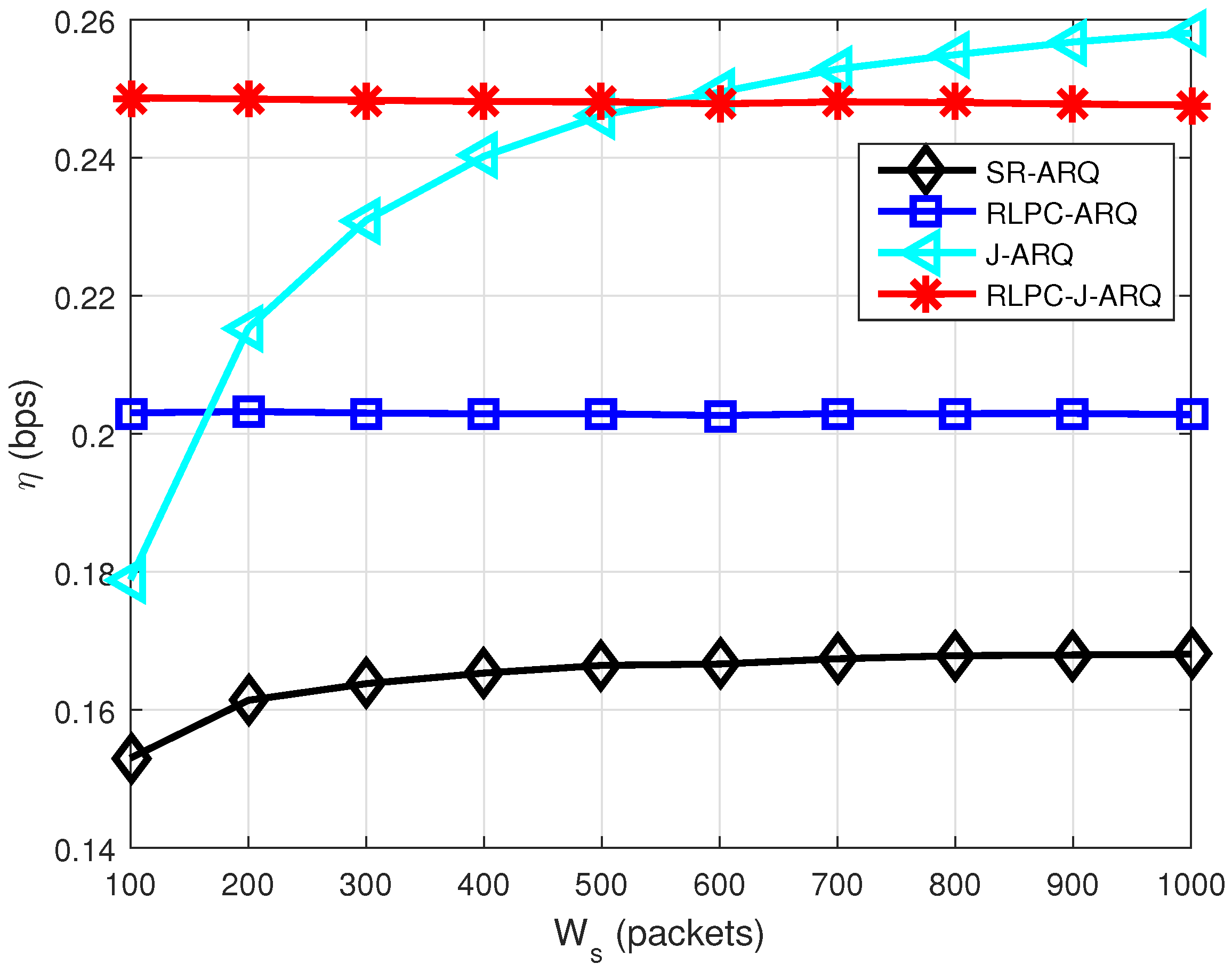
Figure 4 illustrates the throughput efficiency as a function of block size
W. In this simulation,
. The throughput efficiency of all schemes increases with the increase of
W. The proposed RLPC schemes are still better than the corresponding ARQ schemes. That makes sense since a bigger
W means the transmitter could send more packets during a transmission; it reduces the number of ACKs. There is a turning point for the J-ARQ scheme. This is because
will decrease with the increase in group size
W. When
,
and it turns to
for
. The throughput efficiency of the J-ARQ scheme decreases as
becomes smaller since it leads to more idle time.
Figure 5 shows the impact of transmission distance on throughput efficiency. Naturally, the throughput efficiency decreases with the increase of
d, since it leads to an increase in propagation delay
. The performance of the RLPC-ARQ scheme is always better than the SR-ARQ scheme. For the J-ARQ scheme, the throughput efficiency becomes larger at
m because
becomes larger. The transmitter sends two group packets during a round-trip time with
m, while it sends three groups with
m. The same situation also occurs at
m. For the RLPC-J-ARQ scheme, the performance continuously decreases since we only consider that two blocks are transmitted simultaneously. However, its throughput efficiency is still better than that of the J-ARQ scheme when
d is less than 7000 m.
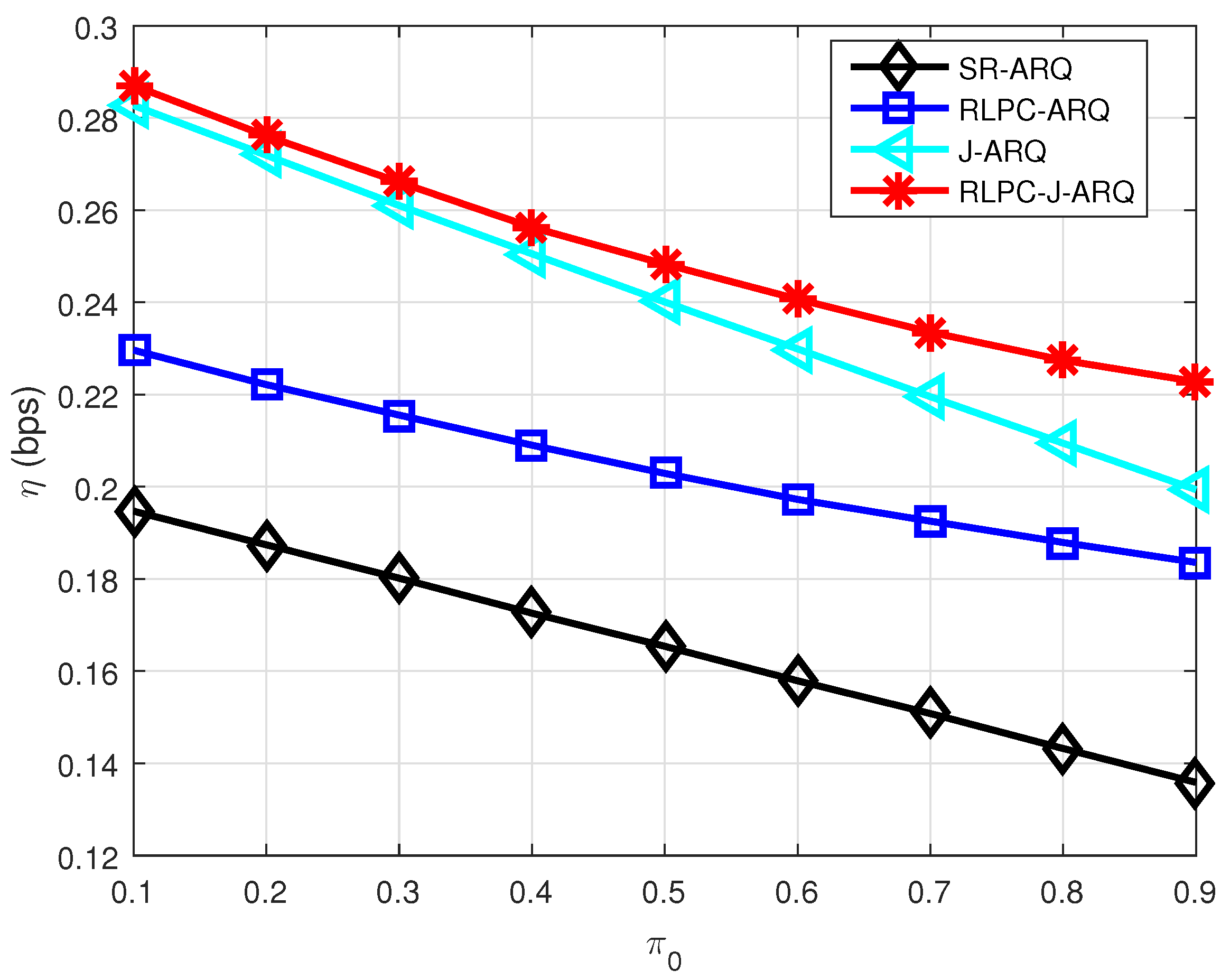
Finally, we analyze the impact of steady-state probability
, which reflects the effect of UWA channels.
Figure 6 illustrates the throughput efficiency as a function of steady-state probability
. From
Figure 6, we find the performance of all schemes will deteriorate with the increase of
. A larger
means the channel is more likely to be bad. The performance gain between with RLPC and without RLPC also increase as
increase. This is because the RLPC schemes under the bad channel could improve the successful decode probability by increasing the transmitted packets to reduce the retransmission. However, the conventional ARQ schemes need to retransmit many times. Thus, the superiority of RLPC schemes is more reflected in the case of poor channels. After all, the conventional ARQ scheme also does not need to be retransmitted when the channel is good.
This paper proposed two ARQ schemes with RLPC for UWA communications. The limitations of the proposed method are as follows. First, the sender knows the transition matrix of the channel state in advance, which needs to do a lot of experiments. Second, the proposed methods were based on the DP algorithm. The computational complexity is very high with a large system state. Thus, it is better to solve the problem with deep learning method.
8. Conclusions
This work investigates the adaptive packet coding for reliable UWA communications. This paper proposes two schemes based on two different ARQs. The first scheme is based on the conventional S&W ARQ scheme. The sender chooses the optimal number of packets in each transmission according to the feedback transmission result about the last transmission. We also set maximum retransmission times to avoid infinite retransmission considering the error-prone characteristic of UWA channels. This problem is formulated as a finite horizon optimization and solved with the DP algorithm. To overcome the impact of long propagation delay, we propose the modified juggling-like ARQ scheme for RLPC. Compared with the standard J-ARQ scheme, the transmission duration of the proposed scheme is variant and adapts to the rateless characteristics of the random linear packet coding. A two-step DP algorithm is proposed to find out the optimal solution. Simulation results demonstrate the performance gain of the proposed schemes as well as the impact of various practical factors such as data length, group size, channel steady-state distribution and transmission distance.