1. Introduction
Small and medium-sized enterprises (SMEs) face significant challenges in data management, primarily due to a lack of resources and robust security systems. This deficiency makes them an easy target for cyberattacks and hinders compliance with data protection regulations [
1,
2]. Although digitalization has accelerated the growth of many of these enterprises, efforts to strengthen their security mechanisms remain insufficient, exposing them to serious risks such as data breaches and economic losses [
3].
In this context, blockchain technology has emerged as a promising solution to strengthen data management in SMEs. Its capability to create distributed and immutable records ensures the integrity and traceability of information [
4,
5]. By enabling process automation through smart contracts, blockchain not only enhances operational efficiency but also reduces reliance on intermediaries, which can contribute to greater security in daily operations [
6,
7].
However, these technological advancements have been accompanied by an increase in the complexity of cyberattacks, underscoring the urgent need for SMEs to adopt measures such as blockchain to protect their sensitive information and ensure continuity in their processes [
8].
According to Luukkonen and Ülgen [
9], the lack of an adequate cybersecurity system and vulnerabilities in information transfer processes have increased the risks of sensitive data leakage. Moreover, SMEs have become a target for cyber attackers, who view them as entry points to larger corporations. Given this scenario, it is crucial to strengthen the security of information channels to protect both their own assets and those of their business partners. Therefore, the problem addressed by this study is that SMEs in Lima Metropolitana face high risks in data management due to a lack of effective security measures, highlighting the need for an approach that secures these processes more safely and efficiently.
In Latin America, more than 63 billion cyberattack attempts were recorded in the first half of 2023, with Peru experiencing 3.0 billion intrusion attempts, underscoring the urgent need to implement robust solutions, such as blockchain, to protect sensitive data [
10]. In the Peruvian context, a study conducted by Microsoft and Marsh [
11] reveals a concerning reality: 6 out of 10 companies allocate only 10% or less of their IT budget to cybersecurity. Additionally, since the onset of the pandemic, 31% of companies have reported an increase in cyberattacks [
12]. These figures highlight the vulnerability of Peruvian SMEs to digital threats, emphasizing the urgent need to strengthen their security measures to protect the integrity of their information.
Various studies have explored how blockchain technology can enhance security in the management of sensitive data across different sectors. The study by Wang and Qin [
13] proposed a framework based on Hyperledger Fabric to improve privacy and interoperability in the management of medical data. It utilizes smart contracts for granular access control, tailored to user roles, thereby achieving more secure and efficient management of health information.
Raghav and Bhola [
14] developed a blockchain platform for medical data management focused on preserving privacy through decentralized storage, thereby avoiding single points of failure and resisting attacks. Additionally, it implements mechanisms to conceal sensitive information from unauthorized users.
Finally, in the study by Daah and Qureshi [
15], a security framework for the financial industry was presented, based on the Zero Trust model and blockchain, which strengthens transactions with multiple layers of security, including identity management, network security, and data protection, adding robust verification against information tampering.
While efforts to enhance data security through blockchain are valuable, it is important to recognize that most of this work has focused on specific sectors and has not adequately addressed the unique challenges faced by small and medium-sized enterprises (SMEs). These challenges include inadequate or non-existent information management systems, infrastructures that are vulnerable to cyber threats, and the need for scalable and customizable solutions for secure data transfer. In particular, there is a noticeable gap in solutions specifically tailored to meet the needs of Peruvian SMEs, especially in developing countries. This study aims to bridge this gap by introducing a novel, sustainable cloud architecture that not only enables these enterprises to safeguard their data but also supports long-term scalability and adaptability. By doing so, it helps enhance their competitiveness in an increasingly digitalized and security-conscious business landscape [
16].
Therefore, the aim of this study is to design a cloud architecture based on blockchain focused on improving the security of file transfer processes in SMEs. The proposal seeks to integrate good cybersecurity practices with emerging technologies such as blockchain to create a secure, transparent, and auditable environment, as well as consent management and the implementation of access control mechanisms that prevent both external and internal attacks. In addition, it focuses on designing a cloud architecture that incorporates cutting-edge technologies to protect sensitive SME data during its transfer.
The article is organized into 7 sections.
Section 2 reviews the relevant literature related to the research topic.
Section 3 presents the research proposal, while
Section 4 focuses on the validation process.
Section 5 and
Section 6 present the results and discussion, respectively. Finally,
Section 7 outlines the conclusions and future work.
2. Related Works
2.1. Blockchain
Blockchain technology has emerged as a reliable solution for data management and protection, particularly in scenarios requiring high levels of security and privacy. For instance, Riesco et al. [
17] demonstrate the use of blockchain through smart contracts on Ethereum to promote the sharing of cyber threat intelligence. Their simulations highlighted the advantages of this system; however, they also revealed limitations, such as transaction costs and storage constraints. These challenges are critical when designing scalable solutions for SMEs, underscoring the importance of balancing benefits with practicality.
In a similar vein, Liu et al. [
18] propose a blockchain-based auditing solution that removes third-party involvement, enhancing data integrity verification through smart contracts and the quad Merkle hash tree method. This innovative approach highlights blockchain’s potential to ensure secure and reliable cloud data auditing. Moreover, it aligns with the objectives of our study, which aims to develop practical solutions tailored for smaller-scale enterprises.
Building on this, Guo et al. [
19] explored the integration of blockchain with federated learning to enhance privacy in data sharing. Their paradigm introduces sandboxes and state channels, which create secure processing environments while improving system efficiency. This integration serves as a useful reference for our BLOCKSAGE framework, which also emphasizes combining blockchain with advanced technologies to address security and scalability challenges faced by small and medium-sized businesses.
2.2. Data Management and Protection
Innovative applications of blockchain technology have significantly advanced secure data management. For instance, Feng and Yang [
20] developed a scheme using zero-knowledge proofs and smart contracts to ensure privacy in IIoT data exchanges. By incorporating proxy re-encryption, their approach aligns closely with our framework’s focus on leveraging encryption technologies like IPFS to secure sensitive data. Similarly, Tian and Jian [
21] proposed a blockchain-based framework to protect smart grids, integrating P2P networks, asymmetric encryption, and smart contracts. This comprehensive solution addresses trust issues and eliminates single points of failure, principles that also underpin the Zero Trust model applied in our study.
Another notable contribution comes from Wu et al. [
22], who tackled quantum resilience through a post-quantum threshold algorithm. By distributing private keys across nodes, their method prevents key leakage and enhances future-proof security. Although quantum resistance falls outside the scope of our research, their emphasis on robust encryption reflects our shared commitment to safeguarding sensitive data. Similarly, Yang et al. [
23] examined blockchain-based access control in cloud environments, offering a framework that prevents unauthorized access and enhances privacy. This focus aligns with our efforts to redefine access control for small and medium-sized businesses using decentralized technologies.
2.3. Data Management and Protection in SMEs
Data management challenges specific to smaller businesses have been extensively documented. For example, Chetna et al. [
24] identified persistent issues related to information control and ownership within intra- and inter-organizational processes. To address these concerns, they developed a blockchain-based platform that leverages smart contracts to ensure data authenticity and security at access points. These principles resonate with our BLOCKSAGE architecture, which seeks to enhance organizational competitiveness while preserving data ownership.
Additionally, Zheng et al. [
25] introduced a blockchain-based model to facilitate real-time data sharing among smaller enterprises, large corporations, and financial institutions. Their dynamic evolutionary game model highlights blockchain’s ability to foster trust and improve economic outcomes. These findings reinforce the practical relevance of our system, which similarly promotes trust through decentralized mechanisms.
In a broader context, Khan et al. [
26] presented a framework combining blockchain, AI, and IIoT to streamline digital operations. Their approach enhances system interoperability, security, and efficiency, reflecting our own focus on leveraging scalable APIs and secure processes to optimize organizational performance. Furthermore, Jain et al. [
27] adapted Ostrom’s common goods governance principles to blockchain, fostering transparency and trust within clusters of small businesses. This aligns closely with our goal of promoting trust through decentralized solutions. Finally, Wong et al. [
28] analyzed blockchain adoption among enterprises in Malaysia, identifying barriers and benefits such as improved transparency, cost reduction, and supply chain optimization. These insights echo feedback from participants in our study, underscoring the feasibility and relevance of blockchain-based solutions like BLOCKSAGE.
3. BLOCKSAGE SME Model
3.1. Model
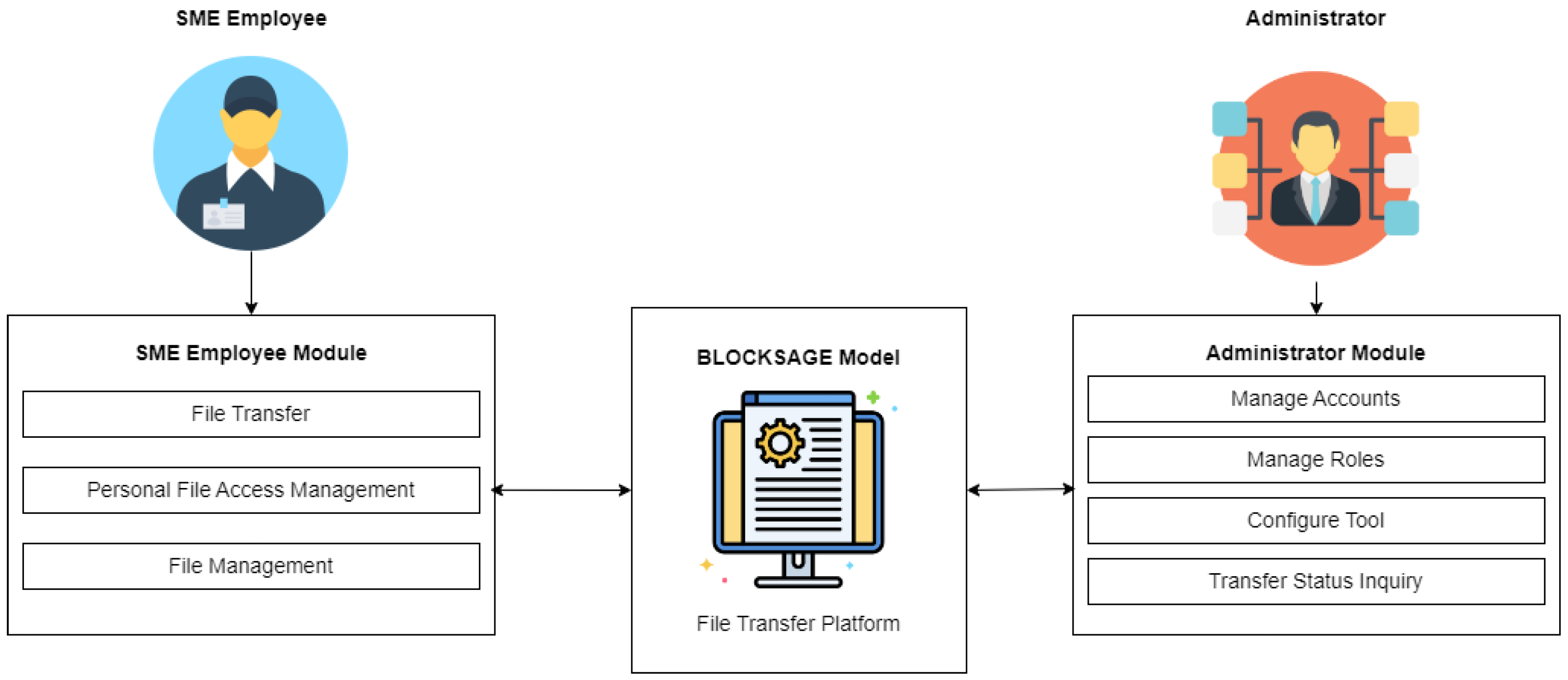
The BLOCKSAGE model proposed is a blockchain-based architecture using Hyperledger Fabric (HF) that provides both flexibility and security in managing sensitive data (see
Figure 1). HF serves as the core of the solution, managing transactions through smart contracts and distributed databases like CouchDB. This architecture allows SMEs to customize the solution according to their needs, leveraging scalable cloud services such as Google Cloud, AWS, or Microsoft Azure, which facilitates gradual adoption without compromising security.
With tools like Hyperledger Explorer, SMEs can audit the blockchain in real time, ensuring data traceability and control. The integration of REST API and LDAP servers enhances identity and access management, providing greater security in file transfers between employees and external entities. This approach enables SMEs to adopt a scalable infrastructure while maintaining high standards of operational security as they grow.
The BLOCKSAGE model builds upon and addresses limitations identified in prior studies. For instance, while Liu et al. [
18] emphasized the role of smart contracts and blockchain auditing to enhance data integrity, BLOCKSAGE extends these capabilities by integrating Hyperledger Explorer, enabling SMEs to perform real-time auditing and gain a comprehensive view of their data transactions. Furthermore, the use of distributed databases like CouchDB aligns with Guo et al.’s [
19] work on combining blockchain with advanced technologies to improve efficiency and scalability. By integrating REST APIs and LDAP for identity management, BLOCKSAGE complements the approaches explored by Yang et al. [
23], enhancing access control mechanisms specifically tailored to the needs of SMEs. This architecture not only addresses security and scalability challenges but also bridges the gap between theoretical models and practical implementations suitable for smaller enterprises.
BLOCKSAGE includes two main roles: the SME employee and the administrator, each with a specific module. The SME employee can perform file transfers, manage access to their personal files, and organize their files within the platform.
On the other hand, the administrator has the capability to manage accounts, assign roles, configure the tool, and monitor the status of file transfers. Both roles have access to the BLOCKSAGE file transfer platform, designed with a blockchain architecture, thereby ensuring the protection and traceability of sensitive data in every operation.
3.2. Implementation
3.2.1. Architecture
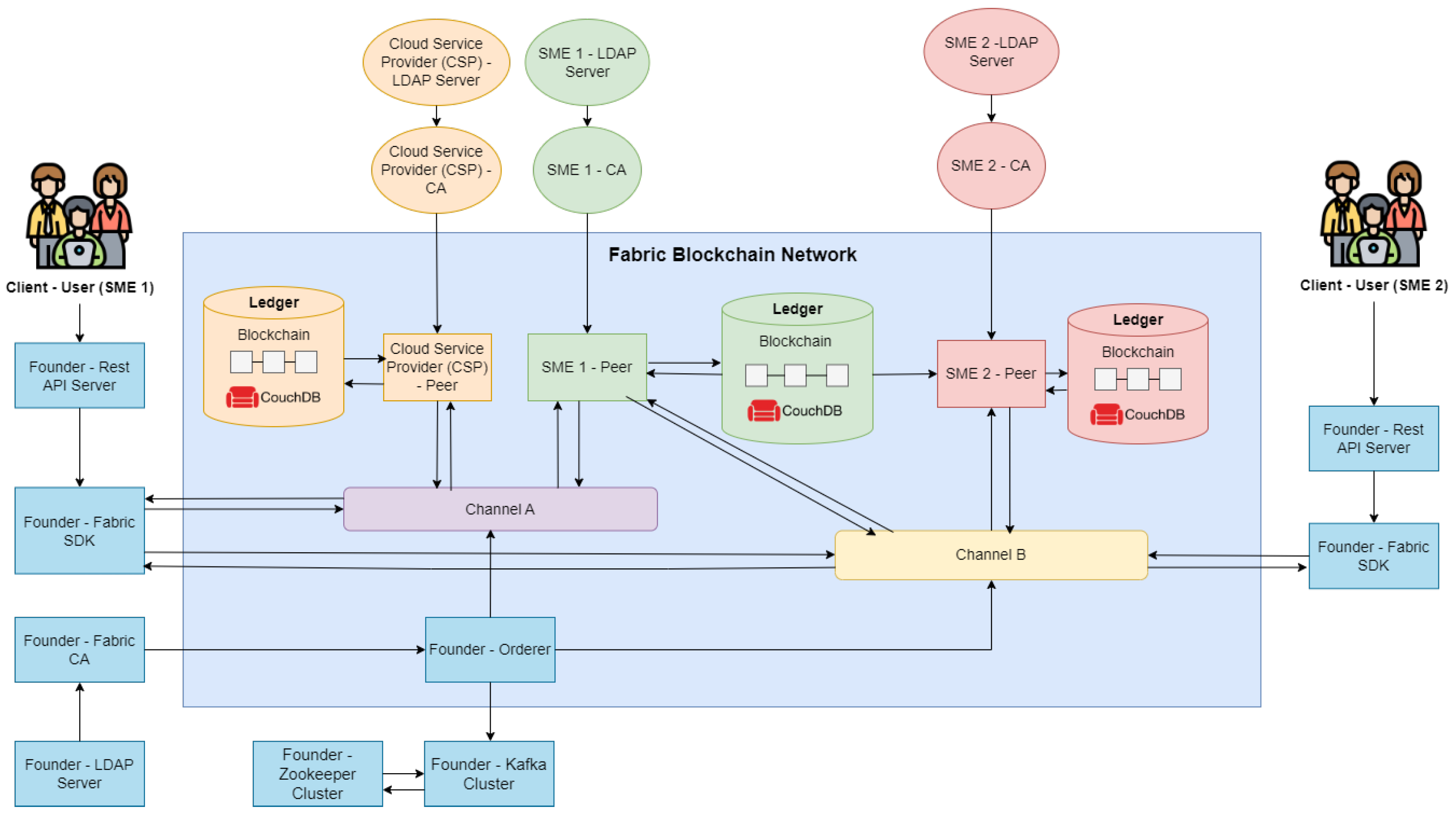
SMEs often lack a robust cloud infrastructure due to resource constraints [
29]; therefore, this section proposes a blockchain architecture as an integrated solution for secure file transfer. With regard to the Cloud Service Provider (CSP) (see
Figure 2), based on a blockchain network built on the HF framework, this infrastructure utilizes two peer nodes, one assigned to SMEs and the other to the CSP, both equipped with their respective Certification Authorities (CAs) and LDAP servers for identity management. User authentication is based on certificate issuance by Fabric’s CAs, while a private blockchain channel ensures secure communication between nodes.
The file transfer process begins when users create transactions, which are sent to the blockchain channel for validation and subsequent cloud storage. The validation and ordering of transactions are managed by an orderer server, which ensures that transactions are processed sequentially and grouped into blocks [
30]. The BLOCKSAGE SMEs architecture also includes an additional blockchain channel dedicated to data transfer between different companies. This channel has its own peer node, CAs, and LDAP server, facilitating secure and efficient communication among multiple entities, thus enhancing inter-company collaboration.
A key feature of this architecture is its focus on security and auditability. Advanced encryption is used to protect transferred and stored data, ensuring that only authorized users can access the information [
31]. At the same time, the use of blockchain guarantees transaction immutability, reducing the risk of tampering. This not only increases system security but also allows for transparent transaction auditing, facilitating compliance with current standards and regulations [
32].
3.2.2. Development
The development was divided into two parts: the first involved drafting a document outlining the reference framework and best practices for implementing the designed architecture in SMEs consulting the document. The second part consisted of developing a prototype aimed at serving as an example application that SMEs could implement to benefit from the advantages of access management, storage privacy, and secure file transfer technology.
BLOCKSAGE allows each SME to develop an API that connects with the architecture and, in turn, interacts with any user interface the company has or requires, whether it is a website, mobile application, ERP, etc. To demonstrate tangibly how companies could use the architecture, a Full Stack web application was developed using the React and Hardhat frameworks, along with smart contract coding in Solidity.
While BLOCKSAGE proposes using Hyperledger Fabric as the blockchain for architecture development, any blockchain network engine considered in the previously presented benchmark can be used. This will vary depending on the needs of each SME. For this prototype, private Ethereum nodes were used to emulate a company’s private network.
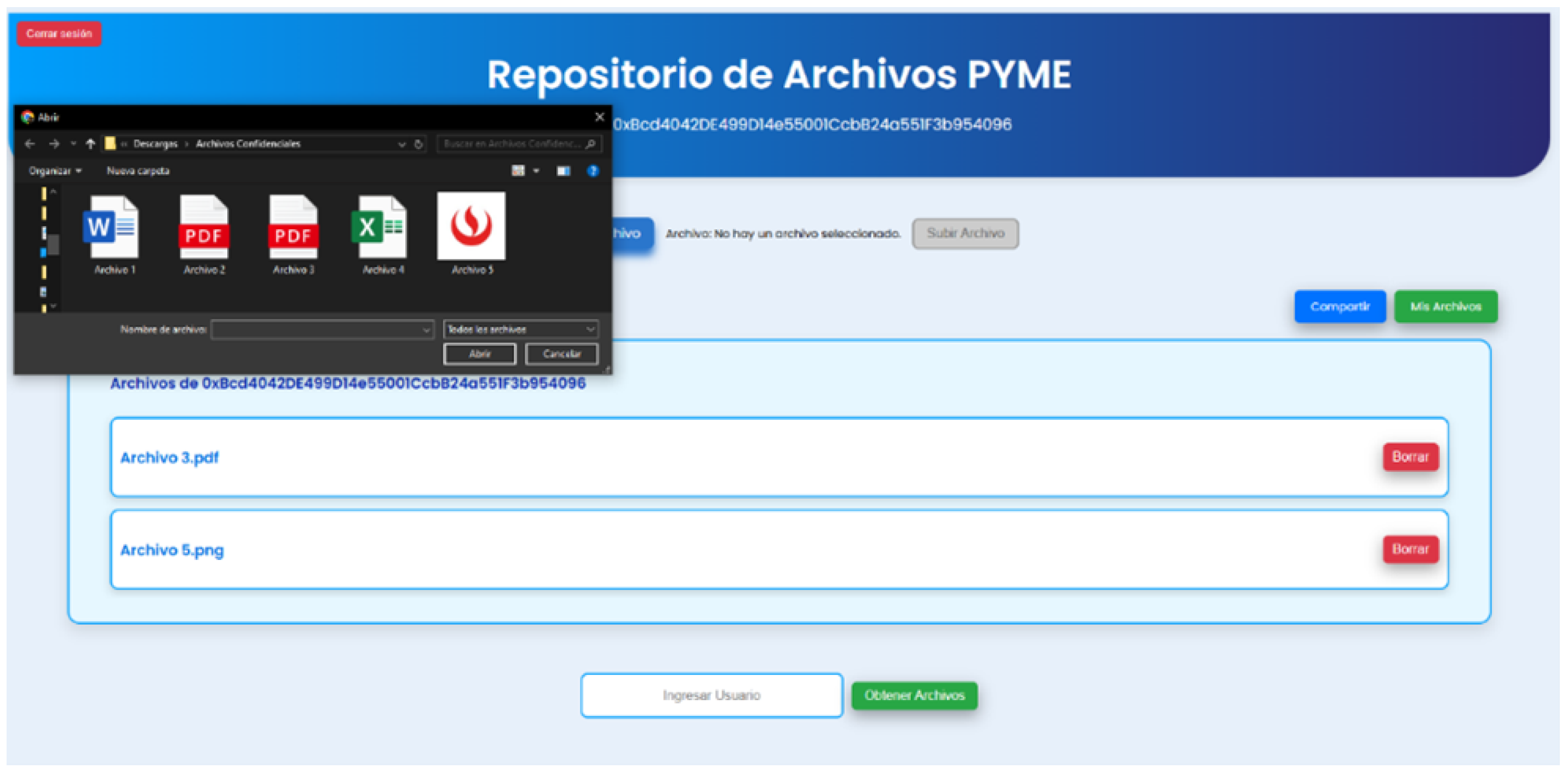
The page consists of a file repository that allows the SME to upload files and securely share them with any user with an address on the company’s network.
Figure 3 shows the main page and file upload functionality.
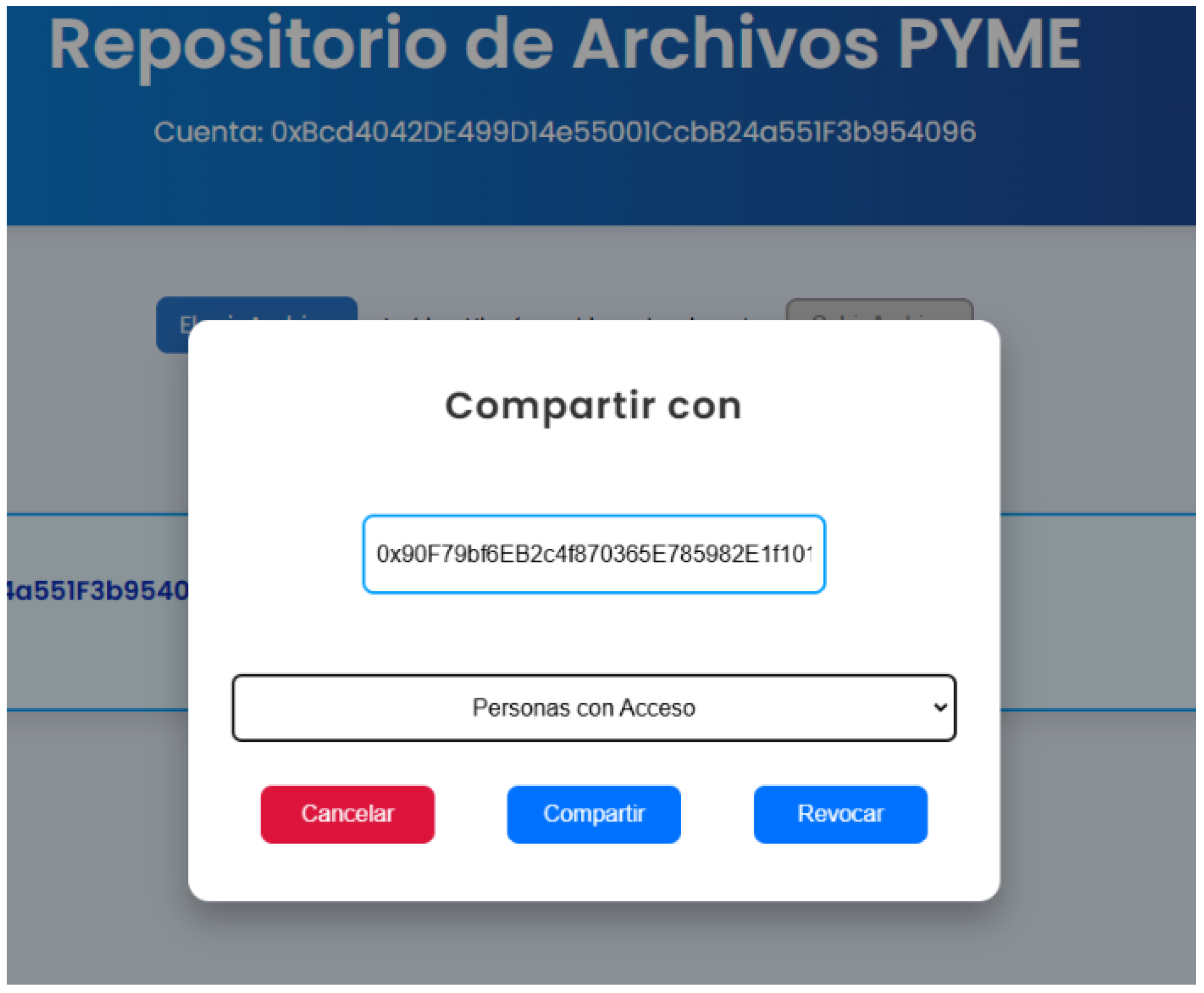
A notable feature of the proposal is the use of customizable smart contracts to grant and revoke user access to information. Each SME employee can designate who is permitted to download their files, with each process requiring approval, validation, and immutable registration on the blockchain. Additionally, each file uploaded to the platform is encrypted using the IPFS method via the Pinata API, which stores files with this protocol and enables access through metadata.
Figure 4 shows the screen that allows the use of access management functionalities in the repository.
4. Validation
4.1. Case Study
A case study was conducted with an SME in the organizational consulting sector. The company’s systems manager reviewed the documentation provided on BLOCKSAGE and conducted extensive testing with the prototype, concluding that the system’s access management capabilities improved data protection. The SME had previously faced security issues related to information leaks, largely due to file transfers via unprotected email. By incorporating the BLOCKSAGE system, the company gained customized methods for data access validation, along with an auditable log of each modification or access made, representing a significant improvement for its security needs. Furthermore, the SME valued the proposal’s effectiveness, acknowledging that the methods applied in the model positively contribute to the maturity of its sensitive information management processes, establishing a robust foundation for enhancing security standards in the medium to long term.
4.2. Usability and Satisfaction
To complement the evaluation of BLOCKSAGE, two Likert scale surveys were conducted (ranging from 1 to 5, where 1 is strongly disagree and 5 is strongly agree). The first survey was administered to three blockchain technology experts, and the second was based on feedback from various SMEs, which can be accessed through the following links, respectively:
https://forms.office.com/r/6pxQSBqLUa (accessed on 14 November 2024) (experts) and
https://forms.office.com/r/LitjEWmvL4 (accessed on 14 November 2024) (SMEs). The participants’ perceptions in key areas were measured, providing a clear view of the model’s effectiveness, functionality, and applicability. This process enabled the identification of strengths and potential areas for improvement, offering a comprehensive assessment of its viability for the SME business environment.
4.2.1. Usability and Satisfaction—Expert Judgment
This stage included the participation of experts in blockchain technologies and Web 3.0 projects, who possess extensive experience in using these networks to facilitate and improve processes within the companies they collaborate with and advise. Additionally, all of them had considerable knowledge and qualifications in cybersecurity and the SME ecosystem, enabling them to accurately assess the proposed solution’s effectiveness for data privacy.
Table 1 shows the characteristics of the respondents.
Table 2 details the questionnaire completed by the specialists following an interview in which they expressed their interest in the proposed solution, highlighting its relevance and effectiveness for the chosen market segment. They noted that the technology had already been used by large corporations, receiving favorable acceptance, but that for the SME segment, it remains a largely unexplored market with significant potential. Additionally, they emphasized the benefits of Hyperledger Fabric, particularly its robustness in encryption and transactions, as well as its traceability features, which are valuable for audit processes within organizations.
4.2.2. Usability and Satisfaction—SMEs
Following interviews with specialists and gathering their feedback on the proposed framework, the BLOCKSAGE model was presented to a group of 11 SMEs in Lima Metropolitana. These companies, which voluntarily participated in the study, represented diverse business models, market segments, and scales. Some were consulting firms, while others were retailers offering a wide variety of products. The companies were contacted through their IT departments, and it was confirmed that, as anticipated based on previous research, they lacked established or defined cybersecurity infrastructures and were highly vulnerable to cybersecurity threats. Additionally, the participants had minimal knowledge on how to mitigate these risks, underscoring the need for solutions like BLOCKSAGE to address these vulnerabilities through a sustainable and auditable cloud architecture. After reviewing the proposed framework, the SMEs completed a questionnaire (see
Table 3) to provide feedback across five key categories. This feedback allowed an assessment of the relevance of the conceptual model’s components in relation to the specific context of their organizations.
5. Results
5.1. Usability and Satisfaction—Expert Judgment
Upon completing the evaluation, the validation results with experts indicated a satisfaction level of 4.06 on the Likert scale, achieving a satisfaction rate of 76.67% in indicator evaluations (see
Table 4). Additionally, observations were made regarding the potential commercialization and distribution of the proposed model for SMEs. The specialists noted that solutions involving blockchain technologies are challenging to introduce into the job market, both at the micro and macro enterprise levels.
5.2. Usability and Satisfaction—SMEs
This same finding was observed in the validation results with the target audience. The components of the proposed model achieved an average satisfaction rating of 4.2 on the Likert scale and 80.08% in indicator evaluations (see
Table 5). Study participants showed strong interest in the technology’s benefits and determined that the architecture reduces the impact of cybersecurity risks identified by their IT departments.
Through the validation process presented, the relevance of the developed model in addressing cybersecurity vulnerabilities in SMEs was determined, demonstrating that the architecture meets the necessary technical characteristics for its implementation.
5.3. Consolidated Analysis of Usability and Satisfaction Results
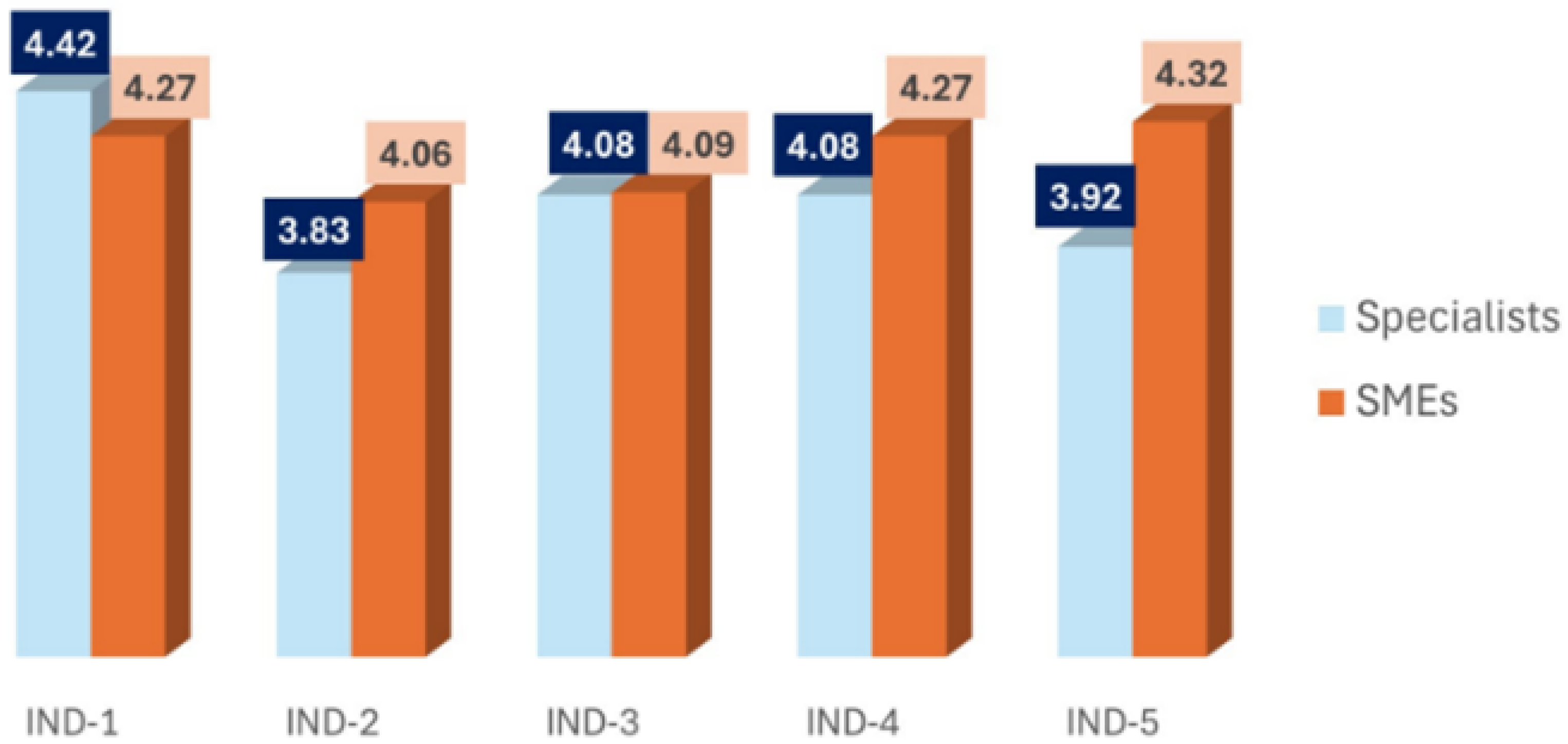
Figure 5 summarizes the results obtained from the individual analyses previously presented. This chart allows for a comparative and summarized visualization of the main findings, facilitating the interpretation and comparison of data obtained in each interviewed segment.
6. Discussion
The results obtained with the BLOCKSAGE model demonstrate its effectiveness and positive acceptance by both experts and SMEs in the sector. In comparison with previous studies, the model shares similarities with other approaches proposed in the literature, such as those by Liu et al. [
18] and Guo et al. [
19], where blockchain and smart contracts are also applied to ensure data integrity and improve secure information exchange. However, the model stands out by focusing specifically on the data security and protection needs of SMEs, a population with particular challenges, as identified by Chetna et al. [
24] and Zheng et al. [
25]. This distinctive approach allows the model to be perceived as a practical and effective solution, tailored to the resource limitations commonly faced by SMEs.
In the case study conducted, BLOCKSAGE demonstrated its ability to effectively manage, access, and audit every data modification, thereby strengthening security processes. This aligns with the approach of other models, such as that of Yang et al. [
23], which focus on access control in cloud environments. However, unlike models like those of Feng and Yang [
20], which rely on advanced techniques such as zero-knowledge proofs and smart contracts tailored for IoT contexts, BLOCKSAGE is specifically designed to meet the needs of SMEs in a more controlled environment. This distinction is crucial, as it allows SMEs to leverage a secure system without the high infrastructure and maintenance costs typically associated with larger-scale technologies, making BLOCKSAGE a particularly well-suited solution for smaller enterprises.
Lastly, regarding usability and user satisfaction, the high level of acceptance and satisfaction achieved in testing confirms that BLOCKSAGE is not only technologically effective but also accessible and viable for SMEs. The validation results indicated an average satisfaction of 4.06 (76.67%) among experts, who highlighted the model’s effectiveness in protecting sensitive data, although they noted the potential difficulty in marketing and distributing the solution due to the perceived complexity of blockchain technologies in the market. However, acceptance was even higher among the target SME audience, reaching an average of 4.2 on the Likert scale and a satisfaction level of 80.08%. Participants expressed strong interest in the benefits of the technology, particularly in how the model’s architecture helps reduce the cybersecurity risks identified in their IT operations.
These indicators reflect that users perceive the system as innovative, adaptable, and secure, although some experts noted initial resistance and a learning curve in adopting blockchain. Nonetheless, the model’s practical and low-cost approach could facilitate its adoption in the sector, supporting Khan et al. [
26] view on the importance of accessible and optimized solutions for blockchain use in SMEs. These results suggest that the BLOCKSAGE model could make a significant contribution to strengthening cybersecurity in this sector, providing a robust and adaptable tool to meet current business needs.
However, a critical insight emerged during the study: the Latin American labor market and ecosystem currently lack sufficient professionals skilled in the development and implementation of blockchain infrastructures. This shortage presents a significant barrier to the widespread adoption of the technology. While participants were satisfied with the security and long-term sustainability offered by blockchain, many expressed hesitancy about integrating it into their businesses in the near future. This reluctance is attributed to blockchain’s emerging status and limited market presence, which have yet to establish the confidence needed for broader acceptance. These findings suggest a potential cultural gap in the adoption of advanced technologies like blockchain within the SME sector.
Additionally, while participants appreciated the customizable and scalable architecture of BLOCKSAGE, the majority expressed a preference for solutions similar to the web-based file-sharing prototype, provided as Software-as-a-Service (SaaS). Such SaaS solutions would enable SMEs to leverage privacy and encryption features without the complexities and resource-intensive demands of directly managing blockchain infrastructure. This preference highlights the significance of delivering accessible and user-friendly implementations to support the adoption of advanced technologies in resource-constrained environments like SMEs.
7. Conclusions
The study aimed to evaluate the effectiveness and viability of blockchain technology for protecting sensitive information security in the SME segment of Lima Metropolitana. To this end, a cloud architecture was designed, proposing the implementation of private blockchain networks as an additional layer to the network and information infrastructure of companies. The result was BLOCKSAGE, a robust framework that provides SMEs with best practices for incorporating this architecture into their data storage and transfer processes.
Moreover, the architecture met its security requirements, leveraging the Zero Trust methodology for access management through customizable Smart Contracts and IPFS encryption for file integrity and confidentiality. Additionally, it offers the transparency and traceability capabilities of block explorers, which enable superior auditability.
The related works in cloud platforms based on blockchain has been fundamental in consolidating best practices in data management and protection, providing key solutions in areas such as security, privacy, and efficiency—especially in contexts requiring high levels of confidentiality, like the SME segment. In the general blockchain category, studies highlighted how the use of smart contracts on networks like Ethereum allows for automated audits and protects data integrity without intermediaries, using techniques like the quad Merkle hash tree. This inspired the use of private blockchain as an additional security layer in enterprise architectures, providing controlled and verifiable access to information.
On the other hand, data management and protection solutions in industrial sectors and smart grids highlighted the use of advanced methodologies such as Zero Trust and zero-knowledge proof encryption in the context of IIoT and advanced networks, ensuring both data confidentiality and integrity. Likewise, these security techniques were supported by the transparency and traceability inherent to blockchain technology, which enables robust audits through block explorers. Finally, studies focused on SMEs contributed governance models and mutual trust for inter-organizational data exchange and demonstrated that secure blockchain network environments are conducive to the safe exchange of information in inter-company channels.
Through a validation process involving both cybersecurity and blockchain specialists as well as SMEs, the BLOCKSAGE framework demonstrated significant interest and feasibility, with satisfaction levels of 76.67% and 80.08%, respectively. Stakeholders recognized the architecture’s potential in improving access management and securing file transfer processes, with particular appreciation for its scalability and long-term sustainability. However, participants noted the emerging stage of blockchain adoption within the sector and the limited resources and knowledge among SMEs, which currently hinder the full implementation of the proposed architecture.
Despite these challenges, the findings highlight that BLOCKSAGE offers a sustainable solution for SMEs by addressing critical cybersecurity gaps while being adaptable to their evolving needs. Many SMEs expressed a preference for solutions similar to the prototype web-based file-sharing app offered as a Software-as-a-Service (SaaS), due to its accessibility and reduced infrastructure demands. This preference reinforces the importance of delivering scalable and user-friendly solutions that not only enhance data security but also enable SMEs to gradually adopt advanced technologies in a way that supports their long-term growth. As blockchain technology continues to mature, frameworks like BLOCKSAGE will become essential in providing SMEs with a robust, scalable, and sustainable security infrastructure for the future, especially when made available through more accessible delivery models.
Author Contributions
Methodology, J.S.; Software, O.A. and O.V.; Validation, O.V.; Formal analysis, O.A.; Investigation, J.S.; Writing—original draft, O.A.; Writing—review & editing, J.S.; Supervision, J.S. All authors have read and agreed to the published version of the manuscript.
Funding
The authors would like to express their gratitude to the Dirección de Investigación of the Universidad Peruana de Ciencias Aplicadas (UPC) for their support of this research through the provided incentive. They also extend their thanks to all the individuals who participated in the validation process.
Institutional Review Board Statement
This study qualified for an IRB waiver from the Universidad Peruana de Ciencias Aplicadas. The research involved human participants solely for the purpose of completing non-medical questionnaires to gather their opinions. Given the non-invasive nature of the study, it did not require formal ethical review.
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- European Union Agency for Cybersecurity (ENISA). Cybersecurity Challenges in SMEs. Available online: https://www.enisa.europa.eu/topics/awareness-and-cyber-hygiene/smes-cybersecurity#:~:text=In%20a%20time%20of%20increased,chain%20they%20are%20connected%20to (accessed on 10 October 2024).
- Ramos, A.; Delgado, L. Desafíos en la Protección de Datos en las PYMEs Peruanas. Rev. Latinoam. Derecho Informático 2021, 12, 34–50. [Google Scholar]
- McKinsey & Company. Cybersecurity in Small Businesses: A Gap in Defense. Available online: https://www.mckinsey.com/capabilities/risk-and-resilience/our-insights/securing-small-and-medium-size-enterprises-whats-next (accessed on 15 October 2024).
- Gupta, S.; Yadav, A.; Dhillon, A. Blockchain technology in data management for small and medium enterprises: Security, efficiency, and transparency. J. Emerg. Technol. Account. 2021, 18, 56–73. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 10 October 2024).
- Swan, M. Blockchain: Blueprint for a New Economy; O’Reilly Media: Sebastopol, CA, USA, 2015. [Google Scholar]
- Kim, H.; Laskowski, M. Toward an ontology-driven blockchain design for supply-chain provenance. Intell. Syst. Account. Financ. Manag. 2018, 25, 18–27. [Google Scholar] [CrossRef]
- Rodríguez, S.; Rodríguez, S. Cultura Digital: Su Impacto en la Economía Moderna y los Negocios. Available online: https://labes-unizar.es/cultura-digital-su-impacto-en-la-economia-moderna-y-los-negocios/?expand_article=1 (accessed on 10 October 2024).
- Luukkonen, O.A.; Ülgen Sönmez, Y. Cybersecurity for Small and Medium-Sized Businesses. J. Sustain. Econ. Manag. Stud. 2023, 3, 21–38. [Google Scholar]
- Economía, R. Fortinet Informa que Perú fue el Objetivo de más de 3.000 Millones de Intentos de Ciberataques en el Primer Semestre de 2023—Revista Economía. Available online: https://www.revistaeconomia.com/fortinet-informa-que-peru-fue-el-objetivo-de-mas-de-3-000-millones-de-intentos-de-ciberataques-en-el-primer-semestre-de-2023/#google_vignette (accessed on 10 October 2024).
- News Center Microsoft Latinoamérica. Marsh y Microsoft: Ingeniería Social o Phishing es el Ciberataque que más Aumentó en Perú a Raíz de la Pandemia—News Center Latinoamérica. Available online: https://news.microsoft.com/es-xl/marsh-y-microsoft-ingenieria-social-o-phishing-es-el-ciberataque-que-mas-aumento-en-peru-a-raiz-de-la-pandemia/ (accessed on 11 October 2024).
- Latam Tivit. ¿Cómo Implementar la Seguridad Informática en las Empresas? Available online: https://latam.tivit.com/blog/seguridad-informatica-en-las-empresas (accessed on 11 October 2024).
- Wang, Q.; Qin, S. A Hyperledger Fabric-Based system framework for healthcare data management. Appl. Sci. 2021, 11, 11693. [Google Scholar] [CrossRef]
- Raghav, N.; Bhola, A.K. Secured platform for healthcare data: Privacy preservation based blockchain environment. J. Eng. Des. Technol. 2022, 22, 365–384. [Google Scholar] [CrossRef]
- Daah, C.; Qureshi, A.; Awan, I.; Konur, S. Enhancing Zero Trust Models in the Financial Industry through Blockchain Integration: A Proposed Framework. Electronics 2024, 13, 865. [Google Scholar] [CrossRef]
- Cisco. 2023 Cybersecurity Readiness Index. Available online: https://www.cisco.com/c/m/en_us/products/security/cybersecurity-reports/cybersecurity-readiness-index.html (accessed on 12 October 2024).
- Riesco, R.; Larriva-Novo, X.; Villagra, V.A. Cybersecurity threat intelligence knowledge exchange based on blockchain. Telecommun. Syst. 2019, 73, 259–288. [Google Scholar] [CrossRef]
- Liu, Z.; Ren, L.; Feng, Y.; Wang, S.; Wei, J. Data Integrity Audit Scheme based on Quad Merkle tree and blockchain. IEEE Access 2023, 11, 59263–59273. [Google Scholar] [CrossRef]
- Guo, S.; Zhang, K.; Gong, B.; Chen, L.; Ren, Y.; Qi, F.; Qiu, X. Sandbox Computing: A data privacy trusted sharing paradigm via blockchain and federated learning. IEEE Trans. Comput. 2022, 72, 800–810. [Google Scholar] [CrossRef]
- Feng, T.; Yang, P.; Liu, C.; Fang, J.; Ma, R. Blockchain Data Privacy Protection and Sharing Scheme Based on Zero-Knowledge Proof. Wirel. Commun. Mob. Comput. 2022, 1–11. [Google Scholar] [CrossRef]
- Tian, H.; Jian, Y.; Ge, X. Blockchain-based AMI framework for data security and privacy protection. Sustain. Energy Grids Netw. 2022, 32, 100807. [Google Scholar] [CrossRef]
- Wu, F.; Zhou, B.; Jiang, J.; Lei, T.; Song, J. Blockchain privacy protection based on post quantum threshold algorithm. Comput. Mater. Contin. 2023, 76, 957–973. [Google Scholar] [CrossRef]
- Yang, C.; Tan, L.; Shi, N.; Xu, B.; Cao, Y.; Yu, K. AuthPrivacyChain: A Blockchain-Based access control framework with privacy protection in cloud. IEEE Access 2020, 8, 70604–70615. [Google Scholar] [CrossRef]
- Gupta, C.; Gupta, V.; Fernandez-Crehuet, J.M. A blockchain-enabled solution to improve intra-inter organizational innovation processes in software small medium enterprises. Eng. Rep. 2023, 5, e12674. [Google Scholar] [CrossRef]
- Zheng, C.; Huang, X.; Xu, Y. The impact of blockchain on enterprises sharing real data based on dynamic evolutionary game analysis. Sustainability 2023, 15, 9439. [Google Scholar] [CrossRef]
- Khan, A.A.; Laghari, A.A.; Li, P.; Dootio, M.A.; Karim, S. The collaborative role of blockchain, artificial intelligence, and industrial internet of things in digitalization of small and medium-size enterprises. Sci. Rep. 2023, 13, 1656. [Google Scholar] [CrossRef]
- Jain, G.; Shrivastava, A.; Paul, J.; Batra, R. Blockchain for SME Clusters: An Ideation using the Framework of Ostrom Commons Governance. Inf. Syst. Front. 2022, 24, 1125–1143. [Google Scholar] [CrossRef] [PubMed]
- Wong, L.; Leong, L.; Hew, J.; Tan, G.W.; Ooi, K. Time to seize the digital evolution: Adoption of blockchain in operations and supply chain management among Malaysian SMEs. Int. J. Inf. Manag. 2020, 52, 101997. [Google Scholar] [CrossRef]
- Mishima, M. EY Perú: Más del 50% de Empresas Peruanas no Están Preparadas para los Desafíos del Futuro. Available online: https://www.ey.com/es_pe/news/2023/09/empresas-peruanas-no-preparadas-desafios-futuro (accessed on 14 October 2024).
- Fernandez, O. Coordinación Distribuida con Apache Zookeeper. Available online: https://aprenderbigdata.com/zookeeper/ (accessed on 14 October 2024).
- Google Cloud. ¿Qué es el Encriptado y cómo Funciona? Available online: https://cloud.google.com/learn/what-is-encryption?hl=es (accessed on 15 October 2024).
- Ventajas de Blockchain en la Seguridad de Datos. Available online: https://www.unknowngravity.com/articulos/ventajas-de-blockchain-en-la-seguridad-de-datos (accessed on 19 October 2024).
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).