Abstract
This paper presents threats emerging from the rise in implementation of emerging technologies, such as smart inverters, on everyday human life and their impact on sustainability. Focusing on household photovoltaic systems, this study provides a detailed analysis of the energy production and the trends in the photovoltaic market. A specific application on household photovoltaic systems located in Poland has been carried out in order to assess the potential danger arising from cyberattacks. As the number of distributed energy resources {XE “distributed energy resources”} on the grid increases, the need for smart inverter functionality has grown. In this framework, the present work includes a review of past cyberattacks and their repercussions on technologic developments of smart inverters and on society in general. Additionally, measures to ensure that smart inverter capabilities can be fully realized and to prevent cyberattacks are also discussed. Through the simulation of multiple experimental scenarios, remaining existing threats to the penetration of smart technologies aimed at enhancing grid reliability are identified. The results achieved provide strategic tools to address cybersecurity issues, including those of photovoltaic installations, as well as to promote countries’ energy independence.
1. Introduction
In the face of rapid and severe climate changes, integration of renewable energy sources (RES) in the existing energy system has become crucial for mitigating extreme weather effects and promoting the transition to a zero-emissions society [1]. However, the growth of RES in the energy mix of countries around the world also brings new challenges and threats. Recently, a dynamic development in the photovoltaic (PV) installation market has been detected. Observing the increasing share of PV in the EU energy mix [2,3], the safety, stability, and reliability of RE power generation in energy systems should be ensured.
Technological development, particularly the rapid implementation of wireless communication technologies, significantly contributes to more efficient management of RES [4]. Installations such as wind farms, solar power plants, and smart energy grids increasingly rely on remote monitoring solutions and automated control processes, allowing for the optimization of their operations and enhanced energy security [5]. However, despite many advantages, this process also introduces new types of risks, primarily in the form of cyber threats. Cyber threats such as data injection, Denial of Service (DoS) attacks, and hijacking are among those frequently discussed in the literature, including by Ekechukwu and Simpa [6]. Hackers are aware that any security system is only as strong as its weakest link [7]. Cybersecurity has therefore become an arms race, where a crucial aspect is the continuous updating and improvement of protection mechanisms.
In response to growing threats, Mohamed et al. [8] discussed the use of machine learning to detect intrusion attempts in renewable energy systems. They pointed out that artificial intelligence (AI) enables the analysis of vast amounts of data in real time, allowing for rapid detection of anomalies and automatic responses to attempted security breaches in renewable energy systems.
Additionally, Dygnatowski [7] drew particular attention to the indirect consequences of cyberattacks, analyzing a scenario involving attacks on oil refineries. His work showed that while the destruction of a single refinery results in its direct shutdown, a coordinated attack on several refineries could indirectly lead to fuel shortages across an entire region, subsequently paralyzing transport and triggering a cascade of effects. Similar threats could also arise in the context of RES infrastructure, such as household photovoltaic installations, which will be discussed in more detail later in this article.
It is also important to note that cyberattacks targeting RES influence public opinion and shape perceptions of sustainable development. Especially in the context of the war in Eastern Europe, each attack undermines public trust in the technology, challenges its reliability, and may even foster reluctance among certain social groups to invest public funds in sustainable energy sources [7,8,9].
Today, wars are conducted in a hybrid manner—not only on a physical battlefield but also in the digital realm. The ongoing armed conflict in Ukraine highlights the critical importance of cyber forces. Attempts to disrupt telecommunications, hacker attacks on the energy sector, and efforts to destabilize society through so-called fake news are the domains of modern warfare. In addition to many benefits in everyday life, business, and entertainment [10,11], the development of the Internet and digital technologies [12] brings many threats, problems, and challenges to the modern world [13].
The risks related to the impact of cyberattacks on energy systems, especially PV farms, should be assessed.
In this context, the present research study analyzes Polish dependency on PV systems and cybersecurity-related challenges. The work is organized as follows: after reviewing the current stage of RES, the emerging cyber threats are discussed, with a specific focus on Poland, other European countries, and household PV installations. The methodology used to carry out different simulations is presented together with the results achieved to estimate the scale and consequences of possible cyberattacks.
2. Cyberattacks and Their Repercussions on Technological Developments of Smart Inverters in the Residential Sector
2.1. Effects of Cyberattacks on Energy Systems
Cyberattacks in the energy sector are deliberate attempts to compromise the confidentiality, integrity, and availability of data and control systems. These attacks exploit vulnerabilities in hardware components, firmware updates, communication protocols, and user access mechanisms. As power grids increasingly incorporate distributed energy resources {XE “distributed energy resources”} (DERs), such as residential solar photovoltaic (PV) systems and smart inverters, the potential surface for cyberattacks expands significantly, especially due to the decentralized nature and limited cybersecurity of many edge devices.
In residential PV systems, smart inverters perform critical functions beyond basic energy conversion. They engage in grid support operations, such as voltage and frequency regulation, reactive power control, and real-time telemetry. Their connectivity to home networks or the internet, however, introduces vulnerabilities that attackers can exploit. These include malware injection, particularly via insecure firmware updates; ransomware that disables inverter functionalities; denial-of-service (DoS) attacks targeting communications between the inverter and utility; and supply chain attacks, where devices are compromised before reaching the customer [9].
The nature of smart inverters makes them particularly attractive targets. Many operate autonomously in coordination with utility-level energy management systems. Because of the required interoperability between utilities, aggregators, and third-party providers, they often use standard communication protocols like Modbus, DNP3, or IEEE 2030.5, which may lack robust authentication or encryption by default. These protocols have been shown to be susceptible to spoofing, replay attacks, and unauthorized command injection [14]. The National Institute of Standards and Technology (NIST) emphasizes that DER systems, due to their increasing reliance on open communication standards and real-time data exchange, face heightened cyber risks. According to NIST SP 800-82 Rev. 2, industrial control systems (ICS) used in energy environments must adopt specialized cybersecurity measures that consider the constraints of real-time operation and the potential physical consequences of attacks [15].
Experimental research shows that even relatively simple attacks, such as altering inverter setpoints (e.g., voltage or power factor references), can lead to rapid voltage deviations across a distribution feeder. In some cases, this can cascade into widespread disruptions, tripping protective devices, damaging equipment, or destabilizing adjacent portions of the grid. These risks are amplified in weakly meshed or cross-border interconnections, where local disturbances can propagate rapidly and uncontrollably [16]. Cyberattacks on distributed energy systems are evolving beyond traditional IT threats to include highly targeted manipulations of embedded controls and power electronics. Protecting DERs requires not only adopting best practices in cybersecurity (e.g., secure boot, patch management, intrusion detection) but also embedding security principles in the system architecture from the outset, which the industry refers to as “security by design” [17].
2.2. Cybersecurity in Europe: Trends and Perspectives
Europe has taken decisive action to bolster cybersecurity in the energy sector, recognizing that the rapid proliferation of distributed energy resources {XE “distributed energy resources”} (DERs), especially in residential environments, introduces vulnerabilities that may threaten grid stability and resilience. The European Union Agency for Cybersecurity (ENISA) is at the forefront of monitoring threat dynamics. In its ENISA Threat Landscape 2023 report, ENISA highlights ransomware, supply chain exploitation, and state-sponsored espionage as the most rapidly rising risks within energy infrastructure. Significantly, ENISA also reports that over 25% of documented incidents in the energy sector involved consumer-level DER assets, including residential photovoltaic systems and smart inverters connected via IoT or cloud-based services [18].
To manage these systemic risks, the European Union has enacted and proposed several regulatory frameworks:
- Directive (EU) 2016/1148 (NIS Directive) requires operators of essential services, including energy providers, to implement risk management and incident notification protocols. This directive forms the basis of national cybersecurity infrastructures throughout the member states [19].
- Regulation (EU) 2019/881 (Cybersecurity Act) creates the framework for EU-wide certification of ICT products and services, covering smart inverters and DER communication devices [20].
- The newly adopted Network Code on Cybersecurity formally integrates cybersecurity requirements into electricity grid operation protocols. It mandates risk assessments, reporting obligations, and supply chain security measures; it explicitly aims to achieve harmonized defense standards for cross-border electricity flows and DER devices [21].
As part of its governance model, the Code identifies high-impact entities, such as DER aggregators or large-scale inverter deployments, which are required to submit cybersecurity risk reports to national competent authorities, typically within four hours of attack recognition. This mechanism leverages existing CSIRTs and aligns with the revised NIS2 Directive. National-level responses complement EU-wide regulation. Germany’s BSI has established energy-sector CSIRT capabilities that focus on DER cybersecurity incidents. Its 2022 advisory surrounding a suspected inverter-targeting botnet (the “Sonnen Incident”) underscores how compromised residential inverters can participate in coordinated grid manipulation attempts [22]. Other member states, including Spain, Poland, and France, have likewise formed specialized CERT units and participated in research consortia, such as SecureGRID to manage risks emerging from residential DER deployments; however, public DER-focused incident reports are still limited [23].
Academic research also substantiates the vulnerability of smart inverters and DER components. The work by [18] provided a comprehensive risk evaluation of DER cybersecurity, showing how vulnerabilities at the firmware and protocol level, combined with DER heterogeneity, can escalate into large-scale grid threats.
Despite these substantial regulatory advances, challenges persist. Many DER devices originate from non-EU manufacturers and may not be subject to EU certification regimes. Device diversity and varying national adoption timelines complicate risk harmonization. Ongoing collaboration between regulators, manufacturers, utilities, and researchers will be crucial to close these gaps and ensure secure residential DER integration.
2.3. Cyberattacks on Household Critical Infrastructure and PV Installations: Risks and Vulnerabilities
Recent developments have revealed serious vulnerabilities in residential photovoltaic (PV) systems and smart inverters, exposing them to a range of cyber–physical threats. These include remote access exploits, supply chain compromises, firmware manipulation, and data falsification attacks. While some of the more dramatic real-world incidents (such as coordinated botnets or mass disconnections) have yet to be publicly confirmed, there is substantial, peer-reviewed, and investigative evidence demonstrating the feasibility and emergence of these threats. One of the most significant recent discoveries was the identification of undocumented communication radios embedded in certain Chinese-made solar inverters. In 2025, a Reuters investigation revealed that these inverters, deployed widely across the United States and Europe, contained hidden cellular or radio transceivers that were not disclosed in product documentation. These devices could potentially allow unauthorized remote control, even bypassing firewall protections, raising concerns about foreign control and grid manipulation in sensitive regions [24]. In Germany, the Federal Office for Information Security (BSI) raised formal concerns over inverter hardware and firmware used in the national grid, with particular attention to products from Sungrow and DEYE, major Chinese inverter vendors. A 2025 report by Clean Energy Wire summarized BSI’s findings, highlighting risks such as firmware backdoors, inadequate authentication mechanisms, and the potential for remote shutdown or setpoint tampering if exploited by an adversary [25]. Complementing these real-world concerns, academic research has demonstrated that firmware-level manipulation of smart inverters can result in both localized disruption and broader grid instability. A study by [26] recreated attacks using hardware-in-the-loop (HIL) simulations, showing that if attackers inject commands via modified firmware or unsecured communication protocols, they can cause voltage fluctuations, denial-of-service conditions, or inverter shutdowns that ripple across microgrids.
Another research effort introduced a nontraditional attack vector using electromagnetic interference (EMI) to disrupt inverter operation. Research by [27] demonstrated that carefully modulated EMI signals could affect the control logic of inverters by corrupting sensor readings. This method allows attackers to exploit the physical layer of PV systems without breaching any digital interface, potentially bypassing conventional cybersecurity tools entirely. A critical area of concern involves data integrity in distributed energy resource (DER) telemetry. Research by [28] introduced a false data injection (FDI) framework capable of manipulating DER output reports to grid operators. Using real-world market data, the study demonstrated how falsified inverter outputs could lead to mispriced electricity, artificial congestion, and destabilized demand–response actions. While no confirmed attack has occurred at scale, the paper warns that this type of manipulation could yield economic and operational disruption without requiring direct access to inverter firmware.
Smart inverters are fundamental in enabling seamless integration of household photovoltaic (PV) systems with the electric grid, yet this very connectivity exposes them to serious cybersecurity vulnerabilities. Indeed, the study by [29] emphasized that smart inverters play a major role in seamless grid integration while posing several security challenges like grid failure, blackouts, commercial energy losses, privacy, and safety issues. Attackers exploiting firmware flaws or unsecured interfaces may execute remote inverter disconnections, as modeling by [30] showed that a relatively low percentage of distributed PV would be sufficient to launch an impactful concerted attack on the grid. Likewise, real-time simulation of microgrids confirmed that adversarial disruptions targeting inverter-based microgrids can induce voltage, frequency, and current fluctuations that undermine system stability [31]. Unauthorized manipulation of setpoints via APIs or insecure cloud interfaces is also critical, as attackers could take advantage of these connections to obtain access and create fake commands significantly affecting the operational settings of the DER-utilized power grid. The study by [32] further explained that DoS, DDoS, data integrity attacks (DIAs), and MITM attacks allow for the manipulation of voltage control and load switching behavior, which could lead to prolonged and covert disruptions.
Smart inverters also transmit fine-grained telemetry, including time-stamped power generation and consumption data, which can be intercepted to infer household behavior or occupancy. According to [33], adversaries can obtain information, such as a consumer’s power consumption, and deduce the consumer’s daily routine and personal information, posing serious privacy threats.
Once a residential inverter is compromised, poor network segmentation can allow for lateral movement into more critical utility infrastructure. According to [34], the residential and commercial DER are further exposed to cyberattacks if connected to poorly secured home or building networks. Furthermore, fleets of vulnerable inverters can be weaponized and coordinated into botnets via default credentials or open ports. Such load-altering attacks may operate in synchrony across numerous devices to distort aggregate power flows and cause large-scale disruptions [35], resulting in damaging expensive assets, threatening human safety, and substantial disturbances to the distribution power grid operation. Broader survey literature on IoT-enabled LAAs (Licensed Assisted Accesses) underscores their systemic implications for grid frequency regulation and electricity markets [36]. Smart inverters link household PV installations with broader grid networks and introduce multi-layered risks, including generation disruption, operational command manipulation, data privacy breaches, lateral escalation into utility systems, and coordinated botnet attacks. Modeling studies, simulations, and real-world vulnerability disclosures demonstrate that even modest penetration can pose aggregate threats to grid resilience. These challenges reinforce the need to treat smart inverters as critical infrastructure and to integrate cybersecurity-by-design, robust firmware and API protections, network segmentation, and adherence to evolving regulatory and standardized frameworks across deployment and operations.
2.4. Risk Mitigation Strategies and Emerging Best Practices
Smart inverter cybersecurity can be significantly enhanced through a layered defense and emergent best practices, combining technical, operational, and regulatory controls. Recent work highlighted prevention via hardware-rooted trust, including deploying Trusted Execution Environments (TEEs), secure boot, and hardware security modules to protect firmware, cryptographic keys, and critical control operations—measures essential to prevent takeover of inverter logic and the injection of malicious commands [37]. Encryption and authentication of communication channels (e.g., TLS over SEP 2.0, mutual certificate authentication), together with granular role-based access control, defend against unauthorized setpoint changes and lateral intrusions. Intrusion detection and prevention systems (IDS/IPS), combined with hybrid model-based and data-driven analytics, enable real-time detection of false-data injection, integrity attacks, or unusual control behavior; these approaches leverage time-series data, phasor measurements, or neural network-based anomaly detectors validated in simulation and microgrid testbeds [38]. AI-based control strategies and reinforcement-learning approaches have also been proposed to actively adapt inverter control in response to detected anomalies, enabling mitigation of ongoing attack impacts [39].
At the systems level, strong network segmentation, including isolating PV inverter zones from home or utility enterprise networks, combined with deployment of Security Operations Centers (SOCs) or endpoint protection, helps limit lateral movement and detect unusual connections or behavior traceable to smart PV devices [40]. Firmware patch management, over-the-air (OTA) update verification, and regular penetration testing are critical practices widely recommended, with emphasis on eliminating default credentials and implementing vulnerability reporting mechanisms in line with ETSI EN 303 645 and NIST IR 8498 guidelines [41].
Defense-in-depth is further supported by adopting standard security frameworks tailored to DER deployments, including IoT baselines, solar-specific inverter guidelines (NIST IR 8498), and consumer IoT mandates (ETSI EN 303 645). Blockchain has been explored as a mechanism for immutable and auditable command logging or peer-to-peer energy transaction validation, providing tamper-evident controls over inverter setpoint changes or data-sharing systems [42]. Multi-agent microgrid assessments demonstrate the value of holistic threat modeling and contingency planning: designers should evaluate cascading failures, simulate composite attack scenarios, and embed resilience mechanisms (e.g., fallback control modes, fast load-shedding, DER reconfiguration) into microgrid controllers and VPP (virtual power plant) architectures [43].
Identified threats, their impacts and possible mitigation strategies are shown in Table 1.

Table 1.
Cybersecurity risks in smart inverters, along with mitigation strategies and impacts.
3. Development of RES and Emerging Cyber Threats in Poland
The PV installation market has been growing rapidly in recent years, reaching a record of 65.5 GW of new solar plant installations, with a total solar capacity of 338 GW in 2024 [50]. As shown in Figure 1, Poland is ranked among the first five countries with the highest PV solar capacity installed in Europe. In the projection to 2030, together with Germany, Spain, Italy and France, Poland is also expected to experience the highest growth in PV energy capacity [51].
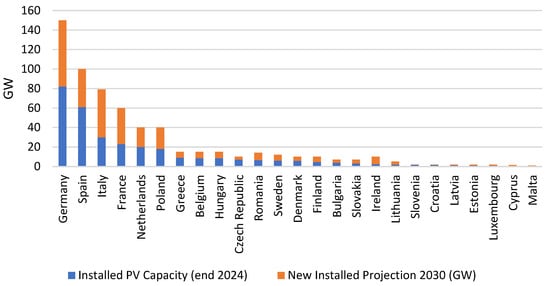
Figure 1.
EU 27 national solar PV installation and PV European market projection to 2030 [2].
Smart inverters (Figure 2) are advanced power electronic devices capable of two-way communication and autonomous decision-making to maintain the safety and security of the grid [52].
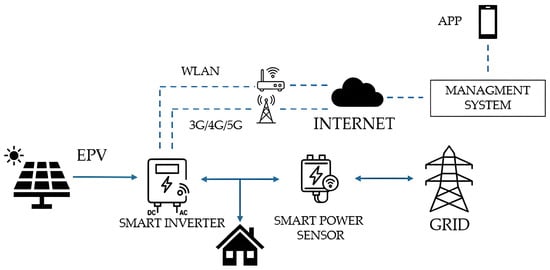
Figure 2.
Diagram of a smart home PV installation.
Smart inverters are usually used in micro-installations and often connected to the internet, enabling remote monitoring and control of PV systems. The significant penetration of RES in the network might cause adverse technical impacts on power grids. These weaknesses can be potentially addressed by smart inverters [53]. Despite their utility, the proper deployment of advanced grid functionality is crucial for the reliable use of these bidirectional communication devices [54]. However, this remote connection to the network increases the risk of potential threats.
Disconnecting a single household from the electricity network is not challenging, but it is conceivable that exploiting a vulnerability could disable inverters that use the same software or are made by the same manufacturer. Given the increasing number of installed PV systems, the negative impacts on the network can be significant [55].
In December 2015, there was a hacker attack on Ukraine’s power grid. This attack left approximately 230,000 consumers in the Ivano-Frankivsk region without electricity for four to six hours [56]. The attack targeted the main control station of the supplier Prykarpattya Oblenergo, causing the shutdown of 27 substations [57]. This issue emphasizes the importance of estimating the consequences of cyberattacks on critical infrastructure, especially during an ongoing armed conflict. In order to estimate possible cyberattack damage, it is crucial to perform rigorous analyses based on real data and to make calculations on the impact on the grid, the role of the affected installation, and potential equipment damage. However, due to the large number of variables, providing a numerical assessment is extremely difficult. In 2011, Gabriel Jakobson [58] proposed a methodology to approximate the consequences of a cyberattack on critical infrastructure by following the four steps below [59]:
- Detection of the attack point by identifying the probable target and the vulnerabilities that may be exploited by the attacker;
- Estimation of the direct impact of the attack on a given asset;
- Propagation of the cyberattack through the system;
- Assessment of the impact on high-level tasks.
Similarly, to evaluate the consequences of an attack on distributed energy resources {XE “distributed energy resources”} (DER) infrastructure, Qi et al. proposed a novel methodology [37]:
- Threat modeling—analyzing known vulnerabilities, exploits, and equipment, software, security, and communication systems;
- System modeling—gathering information such as system voltage, the number of customers, topologies, and protection systems (e.g., against overcurrent);
- Impact metrics—assessing resource loss (e.g., the amount of lost kWh), stability (voltage and frequency violations), and security (failures in protection systems).
In the above studies, the authors focused on energy loss, but since energy loss leads to costs, the economic factor should not be overlooked, as noted by Teymouri et al. Deliberate manipulation of grid voltage through attacks on DER inverters results in energy losses, leading to financial losses [60]. Liu et al. focused on microgrids based on hybrid inverters, discussing the financial losses caused by attacks on such devices [61].
As shown in the previous section, the review of the last ten years highlighted that cyberattacks on solar infrastructure are not only a threat but have also been more and more frequent. One of the first large-scale cyberattacks on PV farms occurred on 5 March 2019. It was a DoS attack on sPower, an independent power provider in Utah, USA. The DoS attack caused the firewall to continuously restart, resulting in 12 h of communication loss between energy-generating devices and sPower’s control center. Specific data on how many people were affected is not publicly available, but based on the declassified incident report, it is estimated that the number was fewer than 50,000. This attack on the USA—one of the most developed countries in the world—shows that such a threat is real, even for Poland.
In June of 2023, approximately 800 Contec SolarView Compact monitoring devices were hijacked [62]. It is highly likely that the attackers exploited a vulnerability first reported in May of 2022. However, the aim of attackers was to make use of devices’ computing power to spread the Mirai botnet, not to disturb grid operations [63]. Although the flaw was known to exist for over a year, Contec released a patch only after the attack, on 18 July 2023. Research showed that when the cyberattack occurred, more than two-thirds of all internet-facing SolarView devices were susceptible to this exploit. Although this incident did not cause major harm (limited to losing monitoring visibility), depending on what the device is connected to, potential repercussions could have been much worse. For example, in a home PV installation, SolarView could be used as a pivot point, granting attackers access to other elements of the target network.
Evidence from 2023, from Romania, illustrates an insider-driven cyber –physical vulnerability of small-scale photovoltaic systems: prosumers deliberately re-programming their inverters to bypass grid-code constraints. During the June 2023 National Energy Council conference, distribution operators warned that “indiscipline at connection, especially regarding inverter settings” was already widespread among the country’s >63,000 prosumers, many of whom had de-activated the mandatory volt–watt function that curtails real-power output during over-voltage events [64] Reportedly, some prosumers have been given special passwords that are needed to modify the inverter’s settings by installers [64] The immediate incentive for owners is higher revenue, as they can avoid curtailment during mid-day voltage peaks, but the system-level consequences are negative, including chronic over-voltage, harmonic distortion, unbalanced phase loading, and increased conductor losses. In extreme cases, uncontrolled PV injection can trip neighboring inverters, damage sensitive appliances, or prompt distribution companies to implement costly reinforcement [65]. This Romanian case demonstrates that cybersecurity for residential PV must address not only external attackers but also malicious or opportunistic configuration changes by authorized users, necessitating secure commissioning protocols and tamper-evident settings.
3.1. Trends in PV Installations in Poland
RES, especially PV systems, are increasingly replacing traditional methods of energy generation. Comparing data from previous years to the present, it is hard to overlook the upward trend in PV installations’ share of electricity production [66].
The PV share was calculated using the following formula:
where is the energy produced by photovoltaic installations (in MWh), and is the total energy produced by all methods (coal, coal derivatives, lignite, natural gas, oil, biomass, wind, photovoltaics, peak-pump power plants, hydroelectric flow-through, and reservoir power plants) (in [67]). In 2020, this share did not exceed 3% on a monthly basis. In 2022, it surpassed 10% for the first time, and in 2024, it exceeded 20% (Figure 3). Comparing May 2023 to May 2024, the shares increased by 5%, highlighting a noticeable trend of increasing energy production from PV [68].
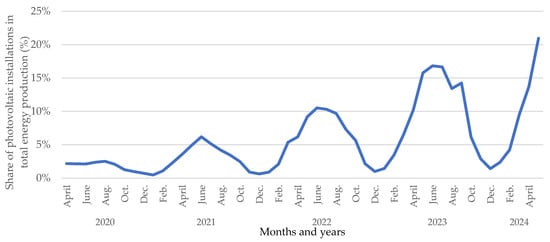
Figure 3.
The share (EPV) of photovoltaic installations in energy production over the months and years, based on PSE reports [67,68].
Details on hourly energy generation volumes and the hourly share of PV in total energy generation for the power grid are presented in Figure 4.
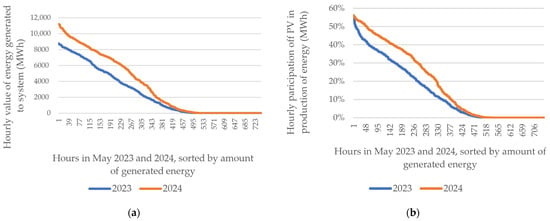
Figure 4.
(a) Comparison of hourly production between May 2023 and May 2024, based on PSE data [68,69]. (b) Comparison of the share in production between May 2023 and May 2024, based on PSE data [68,69].
Comparing May 2023 with May 2024, it is easy to observe an increase in both the share of production and the amount of energy generated. Even though the peak share in 2024, as in 2023, was over 50%, the overall share of PV in May 2024 was higher than in May 2023. The amount of energy generated also increased.
Based on the report “Photovoltaic Market in Poland 2024” [70] from the Institute for Renewable Energy (details in Figure 5), more than 60% of photovoltaic installations in Poland are micro-installations. According to the Renewable Energy Act, a micro-installation is one with a power output not exceeding 50 kW; these are typically home systems.
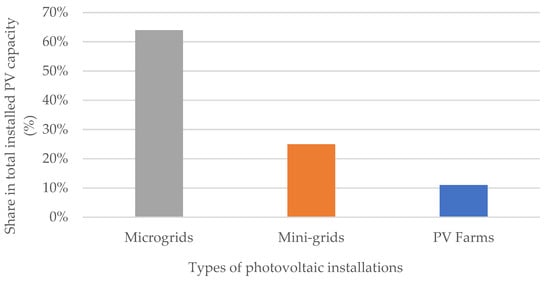
Figure 5.
Structure of photovoltaic installation capacities in Poland. Source: own study based on the Institute for Renewable Energy report “Photovoltaic Market in Poland 2024” [70].
Analyzing the data, it can be concluded that micro-installations are responsible for the vast majority of electricity production from PV sources in Poland (Figure 5), which is why this article focuses on them. At the end of June 2024, the number of connected micro-installations exceeded 1,469,000 [71] (Figure 6), compared to fewer than 160,000 in 2019.
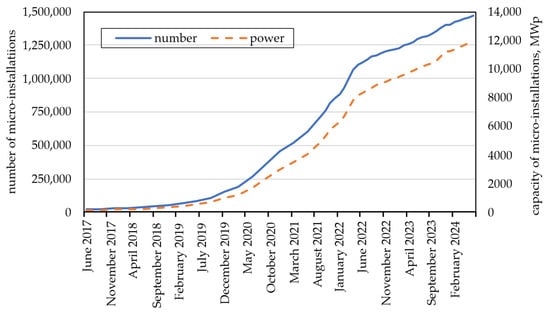
Figure 6.
Number and capacity of micro-installations in Poland, 2017–2024, based on PTPiREE data [72].
An analysis was also conducted on the most commonly used inverter brands in PV installations in Poland.
The inverter market is dominated by foreign manufacturers, with around one-third controlled by the Chinese tech giant Huawei [70]. The next two companies, Solplanet and Soffar Solar [70], which together account for 20% of the market, are also Chinese (Figure 7).
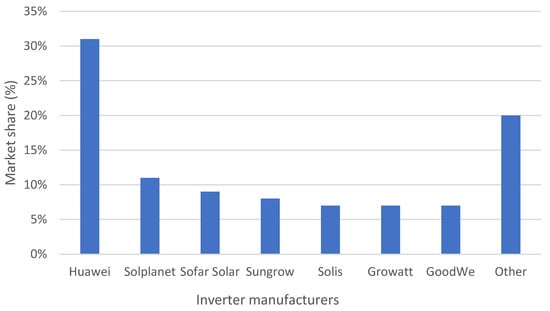
Figure 7.
The most frequently chosen inverter manufacturers in Poland in 2023, based on the Institute for Renewable Energy report “Photovoltaic Market in Poland 2024” [70].
The chart refers to inverters of farms of all sizes. However, knowing that 63% of PV installations in Poland are micro-installations, it can be assumed that the distribution of manufacturers remains consistent.
3.2. Opinion of Poles on RES and Its Impact on Sustainability
As previously indicated, the share of photovoltaics in energy production is increasing year by year. Despite this, Poland is currently struggling with high energy prices [73]. According to a report by the Institute of Public Affairs prepared by [73], over 80% of Poles believe the country is currently experiencing a severe energy crisis [73]. Most respondents identified Poland’s dependence on imported fossil fuels and the war in Ukraine as the main causes of this crisis. This trend is also reflected in a report by CBOS [74]. It can be observed that in April 2024, nearly 10% more of the respondents compared to the previous year believed that Poland should primarily rely on domestically mined coal. However, approximately 60% of respondents continued to be of opinion that Poland should gradually shift towards alternative energy sources.
According to a report prepared by Traczyk and Wittels from the organization “More in Common”, over half of the surveyed individuals believe climate change is happening and that it is human-induced. The same report also includes statistics on support for investment in RES; the vast majority of respondents (it can be assumed this includes Polish society) believe it to be a beneficial use of public funds. Nearly 70% of respondents also think that investments in renewable energy sources, such as photovoltaics and wind farms, will enhance Poland’s energy security [75].
Additionally, a CBOS survey shows that over half of Polish society thinks that both renewable and non-renewable energy sources should be developed simultaneously [74].
Based on the above analysis, it can be confidently stated that Poles are aware of the need for sustainable development and wish to invest in renewable energy sources. The conflict in Ukraine and the restrictions on fossil fuel supplies from Russia have demonstrated to Polish society the importance of independence and security in the energy sector, highlighting that sustainable energy sources can ensure these aspects.
3.3. Evolution of PV Technologies
Recent work showed that performance gains in lead-free AgBiS2 quantum-dot PVs now come less from changing compositions and more from how the films are built. By tightening inter-dot coupling and swapping long ligands for simple ammonium–iodide treatments, researchers formed dense, uniform AgBiS2 layers that reach around 8% PCE with encouraging stability. A complementary route uses solvent-assisted solid-state ligand exchange to cleanly pack CQDs and reduce trap states, delivering notable efficiency upticks alongside better operational robustness. Together, these studies point to a practical message: surface chemistry and processing windows are becoming the main levers for moving eco-friendly QD PVs from lab devices toward scalable thin-film manufacturing [76,77].
In addition to advances in absorber and device processing, recent studies have indicated that photodetectors and related optoelectronic devices may be integrated with photovoltaic modules to deliver dual functionality in smart PV systems. For example, a room-temperature-grown CsPbBr3 single-crystal photodetector in an asymmetric MSM structure exhibited broadband UV–visible responsivity up to 2.56 A/W and high detectivity (~1.24 × 1013 Hz½ W−1), with self-powered operation under zero bias via the built-in Schottky field (InGa/Au electrodes) [78]. Similarly, hybrid photodetectors built from perovskite/plasmonic architectures achieved high photocurrent and low dark current via Au nanorod enhancement and interface engineering, suitable for light monitoring and sensing tasks in PV environments [79]. Such devices show that PV modules could eventually become multifunctional optoelectronic platforms, combining energy harvesting and photonic sensing within a unified architecture.
While today’s micro-installations rarely include dedicated photodetectors, the integration of these components could provide benefits such as real-time monitoring, fault detection, or secure optical communication between modules. Because such photodetectors can share substrate or interface layers with solar cells, the incremental cost and complexity might be manageable in the future. Embedding photonic sensing elements could improve system responsiveness or anomaly detection without relying solely on networked sensors, making household PV installations more secure.
4. Methods and Methodology
To estimate the effects of a cyberattack on critical infrastructure, such as household PV installations, multiple simulations have been carried out by monitoring resources and time.
Additionally, an attempt was made to estimate the scale and consequences of such an attack by implementing the following methodology:
- I.
- Definition of the year of the analysis;
- II.
- Collection of data sources from the TSO;
- III.
- Definition of the time of cyberattacks (hour of the day);
- IV.
- Definition of consumption scenarios (maximum, minimum, and average PV solar production);
- V.
- Analysis of the results:
- Step 1: Definition of the year under analysis:
The data under analysis span the entire year 2023.
- Step 2: Collection of data sources from the TSO:
The analysis relied on data provided by the Polish Transmission System Operator, PSE (Polskie Sieci Elektroenergetyczne). Specifically, comprehensive hourly generation data for 2023 was obtained from PSE’s public reports and databases. This data includes the total electrical output of all sources and the portion generated by PV installations for each hour of the year. From these datasets, key metrics were derived, such as the share of PVs in total generation on an hourly and monthly basis, supporting scenario development. In addition to generation profiles, capacity and installation statistics were gathered to inform assumptions: according to the Institute for Renewable Energy’s 2024 report, about 63% of the total installed PV capacity in Poland consists of micro-installations (≤50 kW). This figure is critical for our model, since it characterizes the dominance of household-scale systems in national PV output. The inverter market share was also considered; notably, one-third of installed inverters in Poland are supplied by a single leading manufacturer (Huawei). Data on the number of micro-installations and their capacity growth were cross-checked with the Polish Distribution Operators’ association (PTPiREE) statistics. All raw datasets were pre-processed to identify representative and extreme conditions: an “average day” generation profile was computed by averaging PV output for each hour across 2023 (using Equation (2) in the text), and the days of lowest and highest PV generation in 2023 were identified (January 21 and July 9, respectively) from the PSE records. These processed data inputs form the basis of the three case study scenarios. Any necessary assumptions (e.g., treating one inverter as representing one prosumer installation, or using a fixed energy price of 500 PLN/MWh for impact valuation) are stated and reasoned in the scenario descriptions. By clearly documenting data sources and processing steps, this methodology ensures transparency and allows for reproducibility of the analysis by other researchers.
- Step 3: Definition of the time of cyberattacks (hour of the day):
Solar energy production is directly dependent on insolation. It can be assumed that any potential attacker targeting PV infrastructure would be aware of this fact. Therefore, in order to make any noticeable impact, potential cyberattacks will likely occur at the time when participation of solar energy in the energy production mix is the highest. The hour of 12:00 was selected as a hypothetical attack time. Analyzing the PSE energy production data from 2023 revealed that photovoltaic installations typically reached the highest share in energy production at this hour.
- Step 4: Definition of the scenarios:
The “Scenarios” refer to a set of specific data and assumptions selected to derive both extreme and average results.
Based on data provided by PSE [80], the Polish Electricity Transmission System Operator responsible for ensuring the reliable and safe delivery of electricity throughout Poland, three possible scenarios were determined:
- Average scenario: This scenario was simulated to analyze the average days of energy consumption in household PV systems.
- Optimistic scenario: This scenario was simulated to analyze the days with the highest solar energy production.
- Pessimistic scenario: This scenario was simulated to analyze the days with the lowest solar energy production.
5. Case Studies
To evaluate the impact of a coordinated cyberattack on household PV systems, three distinct case study scenarios were defined (Average, Optimistic, Pessimistic). Each scenario was built on a distinct set of departure assumptions regarding the solar generation conditions and the extent of inverter compromise. Common to all scenarios, we assumed that micro-installations contribute roughly 63% of total PV capacity, and that a single inverter manufacturer (the market leader) controls ~33% of the installed base. The attack was assumed to exploit a vulnerability in that manufacturer’s equipment, compromising a portion of those inverters. Below, we detail the specific assumptions for each scenario:
Average Scenario: This scenario represents typical operating conditions. It is based on an average day of PV production for 2023, constructed by averaging the PSE-reported PV generation for each hour across the entire year. The PV output at 11:00–12:00 (around solar noon) on this representative day is about 50% of the hourly generation capacity (see Figure 8 and Figure 9).
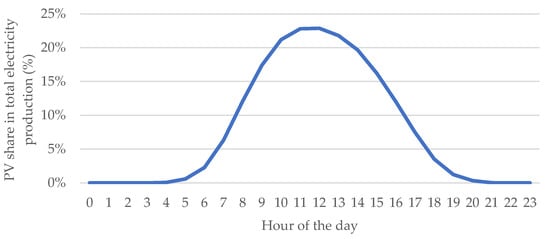
Figure 8.
Average scenario: PV share in electricity production, hour by hour, on an average day in 2023. Source: own study based on PSE data [67,80].
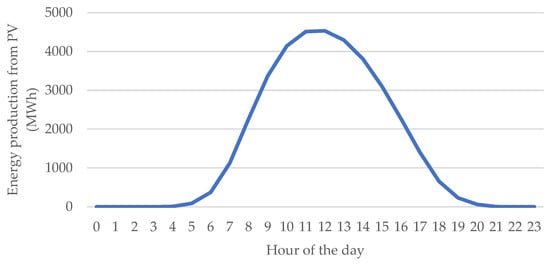
Figure 9.
Energy production by PV in MWh, hour by hour, average day in 2023, average scenario. Source: own study based on PSE data [6,7].
For the cyberattack, a moderate compromise was assumed: the attacker gained control of roughly 75% of the inverters produced by the target manufacturer. In other words, about one-quarter of that maker’s devices remained operative, while the rest (accounting for 25% of all PV capacity in Poland) were maliciously disconnected. This scenario’s assumptions reflect a realistically serious yet not total attack impact on a normal day.
- Optimistic Scenario: This best-case scenario examines an attack when solar output is at its lowest. It was set on 21 January 2023, which was identified as the day with the minimum PV generation of the year. During winter conditions, PV contributes only a small fraction of total electricity production. The attacker’s reach was also assumed to be limited: only 50% of the vulnerable manufacturer’s inverters were successfully taken over. Therefore, both the generation baseline and the extent of the attack were minimal in this scenario. The optimistic scenario envisions a situation where even if a cyberattack occurs, the impact is mitigated by low solar activity and a less effective breach, representing a mild disruption.
- Pessimistic Scenario: This worst-case scenario considers an attack under peak solar generation conditions. It was set on 9 July 2023, which was the day with the highest PV production of the year, when solar irradiance and PV outputs were at their maximum. In this scenario, the attacker was assumed to be highly effective, managing to compromise 90% of the target manufacturer’s inverters. This implies that nearly the entire fleet of that brand’s devices (which equates to about 30% of all PV capacity in Poland) was disabled. The pessimistic scenario combined a maximal generation period with an almost complete failure of a major inverter fleet, providing an estimate of the most severe consequences such a cyberattack could inflict on the power system.
6. Results and Discussions
This study focused on the analysis of three theoretical study cases called the average, pessimistic and optimistic scenarios, respectively. By exploiting a vulnerability in the equipment of the largest market producer, a portion of the inverters are taken over in these scenarios.
6.1. Average Scenario
The average scenario was based on the average day, calculated using PSE energy production data from 2023 [67,80]. For each hour of every day of the year, an average was calculated, as shown below:
The share of photovoltaics in energy production was calculated analogously to the chart in Figure 3.
The following assumptions were made: micro-installations make up 63% of the total capacity of all PV farms, the largest producer controls one-third of the inverter market, and access to 75% of that producer’s devices was gained.
Multiplying these numbers, control over 15.75% of the total electricity generated by PV farms in Poland was obtained. The attack took was assumed to take place from 11:00 to 12:00, the time when PV installations generate the most energy. The attack would instantaneously disconnect approximately 15.8% of Poland’s PV generation capacity (reflecting the fraction of total PV output under attacker control) (Figure 8). If executed over the peak solar hour (11:00–12:00), this equates to an energy loss of about 14,243 MWh, which is about 36% of total electricity generation (all sources) during that hour (Figure 9). At an assumed wholesale energy price of 500 PLN/MWh, the direct financial loss from the forgone production is estimated at roughly PLN 712,000. Approximately 367,000 inverters (and therefore, roughly the same number of prosumer households or small businesses) would be abruptly shut down by the attack, forcing those consumers to draw power from the grid at mid-day instead of using their PV supply.
Even in this average scenario, the sudden removal of over a third of generation during a peak hour could destabilize the grid balance. The affected regions might experience short-term voltage or frequency deviations, and the spike in demand for grid power could drive up spot electricity prices. Although the system would remain operable, service reliability could degrade for some customers (e.g., flicker or low voltage), and operational re-serves would be strained to compensate for the lost PV generation. This underlines that even a moderate-scale cyberattack on widely deployed inverters can have significant re-percussions for energy security.
6.2. Optimistic Scenario
In the optimistic scenario, the attack occurs on a day when the total value of energy produced is the lowest. Analyzing 2023, this day was January 21. The data was compiled based on information provided by PSE.
In this scenario, most of the assumptions from the average scenario were retained: micro-installations make up 63% of all PV farms, a vulnerability was exploited in devices from a manufacturer controlling one-third of the market, but only 50% of those devices were compromised.
In this scenario, the compromised inverters represent about 10.5% (total percentage given by multiplying the variables) of national PV generation (Figure 10). Because the attack was timed on a day of extremely low solar output, the absolute energy lost was only about 924 MWh (from 11:00 to 12:00), corresponding to a mere 0.2% of total generation during that hour (Figure 11). The financial impact was accordingly small (about PLN 46,000 lost) for the one-hour disruption. Roughly 245,000 inverters would go offline in this case, but since overall PV generation was minimal to begin with, most customers and the grid would hardly notice the change.
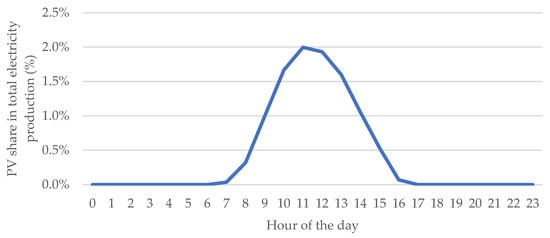
Figure 10.
Optimistic scenario: PV share in electricity production, hour by hour, 21 January 2023. Source: own study based on PSE data [67,80].
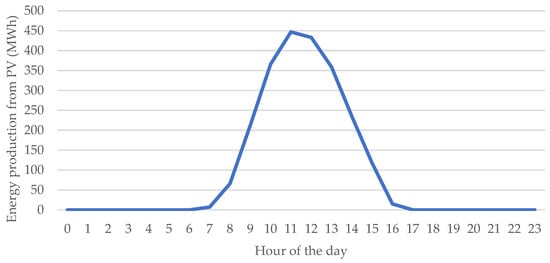
Figure 11.
Optimistic scenario: Energy production by PV in MWh, hour by hour, 21 January 2023. Source: own study based on PSE data [67,80].
The optimistic scenario shows a negligible system impact; the grid can easily with-stand the loss of PV generation because PVs were contributing little at that time. While around a quarter-million prosumers would lose their renewable supply temporarily, they would seamlessly be supported by the grid without major issues. There might be localized inconveniences (e.g., a small town with many prosumers could see a brief voltage dip), but widespread consequences would be avoided. This best case highlights that timing is critical: an attack during winter or low-sun periods greatly limits potential damage, providing a window of opportunity for grid operators to respond or for automated safeguards to kick in. Indeed, under such conditions, the cyberattack’s effect is not immediately serious for system stability or energy markets.
6.3. Pessimistic Scenario
In the pessimistic scenario, the attack occurs on a day when the total value of energy produced is the highest. Analyzing 2023, this day was July 9. The data was compiled based on information provided by PSE.
In this scenario, most of the assumptions from the average and optimistic scenarios were retained: micro-installations make up 63% of all PV farms, a vulnerability was exploited in devices from a manufacturer controlling one-third of the market, but access to 90% of those devices was gained.
The attack would seize control of nearly 18.9% (percentage given by multiplying the variables) of Poland’s PV generation, representing an immense capacity when it coincides with the year’s highest solar production day (Figure 12). The one-hour energy loss was projected to reach 34,147 MWh, which amounts to about 52% of total electricity generation during the critical noon hour (Figure 13). In other words, more than half of the power that should have been produced across the country in that hour would vanish. The economic cost of this lost energy is roughly PLN 1.71 million (for that hour alone). Moreover, an estimated 440,000 inverters would shut down simultaneously, cutting off nearly half a million prosumers.
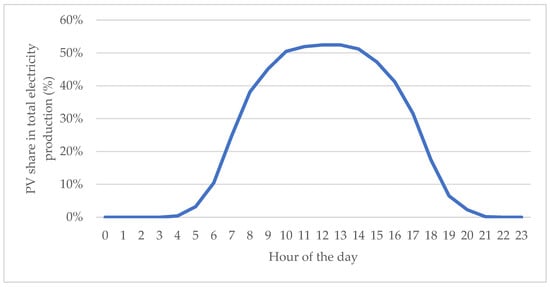
Figure 12.
Pessimistic scenario: PV share in electricity production, hour by hour, 9 July 2023. Source: own study based on PSE data [67,80].
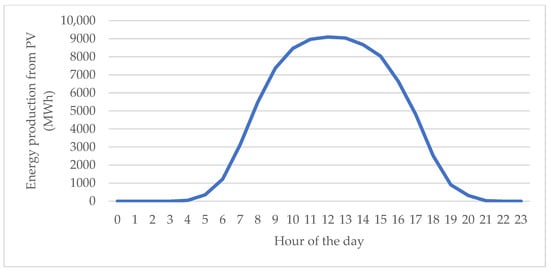
Figure 13.
Pessimistic scenario: Energy production by PV in MWh, hour by hour, 9 July 2023. Source: own study based on PSE data [67,80].
The pessimistic scenario illustrates an extreme but plausible worst case. The instantaneous loss of over 50% of generation would put the grid under severe stress, likely causing a sharp frequency drop and activating emergency response mechanisms (load shedding, activation of standby reserves, etc.). Electricity prices on short-term markets would skyrocket due to the supply deficit, and some areas could experience blackout conditions if the grid cannot rebalance quickly enough. Even where power remains on, the quality of supply would degrade, and critical services might be disrupted as generators and battery systems scramble to cover the shortfall. Such an event underscores the potential for large-scale outages and cascading failures if a coordinated cyberattack were able to simultaneously knock out a substantial fraction of DER inverters. The repercussions would be severe; not only would consumers lose locally generated power, but the overall grid could be destabilized, risking a broader blackout. This emphasizes the importance of cybersecurity measures for inverter-equipped PV fleets, especially as their penetration exceeds significant fractions of national generation capacity.
6.4. The Repercussions of a Cyberattack on Micro PV Infrastructure
Although a large-scale attack on PV micro-installations has never occurred, we can draw certain assumptions about the consequences of such an attack based on known failures and blackouts that have happened in the past. A prime example of a blackout incident is the 2025 Iberian Peninsula blackout. Although this grid incident is believed not to be related to a cyberattack, it portrayed what consequences that a disruption of grid operations could have on every aspect of modern life.
Effects of lack of electric energy were observable in nearly every sector, from finances to healthcare. People were unable to pay with payment cards, withdraw money from ATMs, or check their balances. The healthcare sector was paralyzed; healthcare facility employees were unable to check the digital records of patients. Although backup generators were working, they did not generate enough electricity to power all necessary equipment, leading to cold storage failures and jeopardizing medication requiring cold storage [81]. Telecommunication devices were compromised, impeding emergency contact.
This crisis aggravated the political situation in Spain. The prime minister was accused of incompetence in the management of Spain’s energy sector by the opposition [82]. This blackout highlighted how even non-malicious technical failures can create wide-ranging societal and political turmoil, repercussions that would likely be far greater in the case of a coordinated cyberattack. In the context of PV infrastructure, such an attack could lead not only to grid instability but also to cascading failures in distributed generation systems, complicating both detection and recovery efforts. Therefore, cybersecurity of renewable energy systems must be treated as an integral component of national energy security.
Focusing on power grid resilience against electromagnetic pulse disturbances is equally important in the context of cyberattacks, as these disturbances can cause irreversible physical damage to power system equipment and significant cyber disruptions in data acquisition and transmission. Devising strategies that could help prevent and counteract both physical and cyber vulnerabilities from electromagnetic pulse strikes is equally important to ensure the reliability of the power transmission system and avoid large-scale, long-duration power outages (blackouts) [83].
7. Conclusions
The analysis carried out provided a rough estimation of the outcomes of three theoretical scenarios (average, optimistic, pessimistic) to illustrate an increasingly real threat. The above results assume that the cyberattack was limited to one hour around mid-day. Longer-duration attacks or those coinciding with multiple peak hours could exacerbate the impacts further. Conversely, rapid detection and response mechanisms could mitigate some of the described consequences, which is an aspect for future work.
The armed conflict unfolding on Poland’s eastern border demonstrates how crucial uninterrupted energy production is for the stability of the state. Cybersecurity issues in the energy sector should be treated as a priority, including the cybersecurity of photovoltaic installations, given the rapid growth of these investments in Poland. Commercial PV farms typically have the budget to implement appropriate security measures; therefore, attention should be paid to micro-installations. Household photovoltaic power plants are gaining increasing popularity; however, the average owner typically lacks the technical means and expertise to adequately protect these systems against potential cyberattacks. Consequently, greater emphasis should be placed on ensuring the cybersecurity of micro-installations. Their growing prevalence and the inherent lack of centralized control may contribute to the destabilization of the power grid at various scales, potentially even leading to large-scale outages, such as blackouts.
Future research directions should include analyses of regional concentrations of specific inverter types or manufacturers, which often result from widespread adoption due to successful bids in government-subsidized programs.
Author Contributions
Conceptualization, B.T., L.M. and A.O.O.A.; methodology, B.T. and L.M.; validation, L.M. and P.O.; formal analysis, B.T., A.O.O.A., L.M. and P.O.; investigation, B.T.; writing—original draft preparation, B.T. and L.M.; writing—review and editing, P.O. and A.O.O.A.; visualization, L.M., B.T., A.O.O.A. and P.O.; supervision L.M., B.T. and P.O. All authors have read and agreed to the published version of the manuscript.
Funding
The funders had no role in the research design, data collection and analysis, manuscript preparation, or publication decision.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors on request.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AI | Artificial intelligence |
| API | Application programming interface |
| BSI | Federal Office for Information Security |
| CBOS | Centre for Public Opinion Research in Poland |
| CERT | Computer Emergency Response Team |
| CSIRT | Computer Security Incident Response Team |
| DERs | Distributed energy resources |
| DIA | Data integrity attacks |
| DNP3 | Distributed Network Protocol 3 |
| DoS | Denial of service |
| E | Energy |
| EMI | Electromagnetic interference |
| ENISA | European Union Agency for Cybersecurity |
| EU | European Union |
| FDI | False data injection |
| HIL | Hardware-in-the-loop |
| HPC | Hardware performance counter |
| ICS | Industrial control systems |
| IDS | Intrusion detection system |
| IEEE | Institute of Electrical and Electronics Engineers |
| IoT | Internet of things |
| IPS | Intrusion prevention system |
| LAA | Licensed Assisted Access |
| MITM | Man-in-the-middle |
| MLP | Multilayer perceptron |
| NIST | National Institute of Standards and Technology |
| OTA | Over-the-air |
| PSE | Polskie Sieci Elektroenergetyczne, the Polish TSO |
| PTPiREE | Polish Distribution Operators’ association |
| PV | Photovoltaic |
| RES | Renewable energy sources |
| RL | Reinforcement learning |
| s | Energy, MWh |
| SEP | Secure entry point |
| SOC | Security Operations Centers |
| TEE | Trusted Execution Environments |
| TLS | Transport Layer Security |
| TSO | Transmission System Operator |
| VPP | Virtual power plant |
| Greek: | Total energy produced by all sources |
References
- Hernandez, C.D.C.; Montuori, L.; Alcázar-Ortega, M.; Olczak, P. Extreme Climate Events and Energy Market Vulnerability: A Systematic Global Review. Appl. Sci. 2025, 15, 6210. [Google Scholar] [CrossRef]
- Balaras, C.; Dascalaki, E.; Psarra, I.; Cholewa, T. Primary Energy Factors for Electricity Production in Europe. Energies 2022, 16, 93. [Google Scholar] [CrossRef]
- Szczerbowski, R.; Kornobis, D. The proposal of an energy mix in the context of changes in Poland’s energy policy. Energy Policy J. 2019, 22, 5–18. [Google Scholar]
- Montuori, L.; Alcázar-Ortega, M.; Vargas-Salgado, C.; Mansó-Borràs, I. Enabling the natural gas system as smart infrastructure: Metering technologies for customer applications. In Proceedings of the 2020 Global Mosharaka Congress on Electrical Engineering (GMC ElecEng 2020), Valencia, Spain, 4–6 September 2020. [Google Scholar]
- Lodhi, E.; Liu, X.; Xiong, G.; Khan, M.A.; Lodhi, Z.; Nawaz, T.; Dilawar, A.; Tarkoma, S.; Wang, F. SmartPV-AIoT: An AIoT-Integrated Framework for Fault Diagnosis and Remote Monitoring in Photovoltaic Systems. Energy Convers. Manag. X 2025, 27, 101117. [Google Scholar] [CrossRef]
- Eze Ekechukwu, D.; Simpa, P. The Importance of Cybersecurity in Protecting Renewable Energy Investment: A Strategic Analysis of Threats and Solutions. Eng. Sci. Technol. J. 2024, 5, 1845–1883. [Google Scholar] [CrossRef]
- Dygnatowski, S. Cyber Security as a Foundation for the Security of Critical Infrastructure in the Context of Modern Threats. J. KONBiN 2020, 50, 309–320. [Google Scholar] [CrossRef]
- Mohamed, N.; El-Guindy, M.; Oubelaid, A.; Almazrouei, S.K. Smart Energy Meets Smart Security: A Comprehensive Review of AI Applications in Cybersecurity for Renewable Energy Systems. Int. J. Electr. Electron. Res. 2023, 11, 728–732. [Google Scholar] [CrossRef]
- Ahmed, I.; El-Rifaie, A.M.; Akhtar, F.; Ahmad, H.; Alaas, Z.; Ahmed, M.M.R. Cybersecurity in microgrids: A review on advanced techniques and practical implementation of resilient energy systems. Energy Strategy Rev. 2025, 58, 101654. [Google Scholar] [CrossRef]
- Stecuła, K. Analysis of Asymmetric VR Games—Steam Platform Case Study. Technol. Soc. 2024, 78, 102673. [Google Scholar] [CrossRef]
- Stecuła, K. Virtual Reality Applications Market Analysis—On the Example of Steam Digital Platform. Informatics 2022, 9, 100. [Google Scholar] [CrossRef]
- Wolniak, R.; Stecuła, K.; Aydın, B. Digital Transformation of Grocery In-Store Shopping-Scanners, Artificial Intelligence, Augmented Reality and Beyond: A Review. Foods 2024, 13, 2948. [Google Scholar] [CrossRef] [PubMed]
- Wolniak, R.; Stecuła, K. Artificial Intelligence in Smart Cities—Applications, Barriers, and Future Directions: A Review. Smart Cities 2024, 7, 1346–1389. [Google Scholar] [CrossRef]
- Czajkowski, A.; Remiorz, L.; Pawlak, S.; Remiorz, E.; Szyguła, J.; Marek, D.; Paszkuta, M.; Drabik, G.; Baron, G.; Paduch, J. Global Water Crisis: Concept of a New Interactive Shower Panel Based on IoT and Cloud Computing for Rational Water Consumption. Appl. Sci. 2021, 11, 4081. [Google Scholar] [CrossRef]
- Keith, S.; Victoria, P.; Suzanne, L.; Marshall, A.; Adam, H. Guide to Industrial Control Systems (ICS) Security; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015.
- U.S. Department of Energy’s Office of Cybersecurity. Cybersecurity Considerations for Distributed Energy Resources on the U.S. Electric Grid. 2022. Available online: https://www.energy.gov/sites/default/files/2022-10/Cybersecurity%20Considerations%20for%20Distributed%20Energy%20Resources%20on%20the%20U.S.%20Electric%20Grid.pdf (accessed on 30 July 2025).
- Oliver, D.; Lucas, T.; Lindani, M. A review on cybersecurity for distributed energy resources: Opportunities for South Africa. J. Infrastruct. Policy Dev. 2024, 8, 8631. [Google Scholar]
- Zografopoulos, I.; Hatziargyriou, N.D.; Konstantinou, C. Distributed Energy Resources Cybersecurity Outlook: Vulnerabilities, Attacks, Impacts, and Mitigations. IEEE Syst. J. 2023, 17, 6695–6709. [Google Scholar] [CrossRef]
- European Union. EUR-Lex. 2016. Available online: https://eur-lex.europa.eu/eli/dir/2016/1148/oj/eng (accessed on 30 July 2025).
- European Union. EUR-Lex. 2019. Available online: https://eur-lex.europa.eu/eli/reg/2019/881/oj/eng (accessed on 30 July 2025).
- European Union. Energy. 2024. Available online: https://energy.ec.europa.eu/news/new-network-code-cybersecurity-eu-electricity-sector-2024-03-11_en (accessed on 30 July 2025).
- ENTSO-E. ENCS. 2022. Available online: https://encs.eu/news/entso-e-and-eu-dso-entity-submit-network-code-on-cybersecurity-to-acer/ (accessed on 30 July 2025).
- Cryar, R.; Saleem, D.; Peterson, J.; Hupp, W. Gap Analysis of Supply Chain. February 2023. Available online: https://docs.nrel.gov/docs/fy23osti/84752.pdf (accessed on 30 July 2025).
- Mcfarlane, S. Rogue Communication Devices Found in Chinese Solar Power Inverters. Reuters, 15 May 2025. Available online: https://www.reuters.com/sustainability/climate-energy/ghost-machine-rogue-communication-devices-found-chinese-inverters-2025-05-14/ (accessed on 30 July 2025).
- Wehrmann, B. Solar PV Hardware Opens Door to Chinese Interference in German Power Supply Security—Agency. Clean Energy Wire, 20 January 2025. Available online: https://www.cleanenergywire.org/news/solar-pv-hardware-opens-door-chinese-interference-german-power-supply-security-agency (accessed on 30 July 2025).
- Kuruvila, A.P.; Zografopoulos, I.; Basu, K.; Konstantinou, C. Hardware-assisted detection of firmware attacks in inverter-based cyberphysical microgrids. Int. J. Electr. Power Energy Syst. 2021, 132, 107150. [Google Scholar] [CrossRef]
- Yang, F.; Dan, Z.; Pan, K..; Yan, C.; Ji, X.; Xu, W. ReThink: Reveal the Threat of Electromagnetic Interference on Power Inverters. In Proceedings of the Network and Distributed System Security (NDSS) Symposium 2025, San Diego, CA, USA, 24–28 September 2024. [Google Scholar] [CrossRef]
- Bragatto, T.; Bucarelli, M.A.; Bucarelli, M.S.; Carere, F.; Geri, A.; Maccioni, M. False Data Injection Impact on High RES Power Systems with Centralized Voltage Regulation Architecture. Sensors 2023, 23, 2557. [Google Scholar] [CrossRef] [PubMed]
- Awad, H.; Bayoumi, E.H.E. Next-Generation Smart Inverters: Bridging AI, Cybersecurity, and Policy Gaps for Sustainable Energy Transition. Technologies 2025, 13, 136. [Google Scholar] [CrossRef]
- Hui, X.; Karumba, S.; Chau, S.C.-K.; Ahmed, M. Destabilizing Power Grid and Energy Market by Cyberattacks on Smart Inverters. In Proceedings of the 16th ACM International Conference on Future and Sustainable Energy Systems, Rotterdam, The Netherlands, 17–20 June 2025. [Google Scholar]
- Topallaj, K.; McKerrell, C.; Ramanathan, S.; Zografopoulos, I. Impact Assessment of Cyberattacks in Inverter-Based Microgrids. arXiv 2025. [Google Scholar] [CrossRef]
- Harrou, F.; Taghezouit, B.; Bouyeddou, B.; Sun, Y. Cybersecurity of photovoltaic systems: Challenges, threats, and mitigation strategies: A short survey. Front. Energy Res. 2023, 11, 1274451. [Google Scholar] [CrossRef]
- Achaal, B.; Adda, M.; Berger, M.; Ibrahim, H.; Awde, A. Study of smart grid cyber-security, examining architectures, communication networks, cyber-attacks, countermeasure techniques, and challenges. Cybersecurity 2024, 7, 10. [Google Scholar] [CrossRef]
- Ghiasi, M.; Niknam, T.; Wang, Z.; Mehrandezh, M.; Dehghani, M. A comprehensive review of cyber-attacks and defense mechanisms for improving security in smart grid energy systems: Past, present and future. Electr. Power Syst. Res. 2023, 215, 108975. [Google Scholar] [CrossRef]
- Comșiț, A.-M.; Cotfas, D.T.; Cotfas, A.P.A. A Review of Smart Photovoltaic Systems Which Are Using Remote-Control, AI, and Cybersecurity Approaches. Appl. Sci. 2024, 14, 7838. [Google Scholar] [CrossRef]
- Chu, Z.; Lakshminarayana, S.; Chaudhuri, B.; Teng, F. Mitigating Load-Altering Attacks Against Power Grids Using Cyber-Resilient Economic Dispatch. IEEE Trans. Smart Grid 2022, 14, 3164–3175. [Google Scholar] [CrossRef]
- Junjian, Q.; Adam, H.; Xiaonan, L.; Jiabhui, W.; Liu, C.-C. Cybersecurity for distributed energy resources and smart inverters. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 28–39. [Google Scholar] [CrossRef]
- Syrmakesis, A.D.; Hatziargyriou, N.D. Cyber resilience methods for smart grids against false data injection attacks: Categorization, review and future directions. Front. Smart Grids 2024, 3, 1397380. [Google Scholar] [CrossRef]
- Asad, A.K.; Omar, A.B.; Ahmed, S. Intelligent Anomaly Mitigation in Cyber-Physical Inverter-based Systems. In Proceedings of the 2021 IEEE Energy Conversion Congress and Exposition (ECCE), Vancouver, BC, Canada, 10–14 October 2021. [Google Scholar] [CrossRef]
- Simona, R.; Nicolae-Daniel, F.; Dragoș, P.; Răzvan, R. Securing Photovoltaic Systems as Critical Infrastructure: A Multi-Layered Assessment of Risk, Safety, and Cybersecurity. Sustainability 2025, 17, 4397. [Google Scholar] [CrossRef]
- McCarthy, J.; Marron, J.; Faatz, D.; Rebori-Carretero, D.; Wiltberger, J.; Urlaub, N. Cybersecurity for Smart Inverters: Guidelines for Residential and Light Commercial Solar Energy Systems; NIST Interagency/Internal Report (NISTIR): Gaithersburg, MD, USA, 2024. [CrossRef]
- Sumukh, S.; Srinivasan, M.K.; Williamson, S. Technological Perspective of Cyber Secure Smart Inverters Used in Power Distribution System: State of the Art Review. Appl. Sci. 2021, 11, 780. [Google Scholar] [CrossRef]
- Sakshi, M.; Anderson, K.; Miller, B.; Boyer, K.; Warren, A. Microgrid resilience: A holistic approach for assessing threats, identifying vulnerabilities, and designing corresponding mitigation strategies. Appl. Energy 2020, 264, 114726. [Google Scholar] [CrossRef]
- Ahmad, M.S.; Amr, Y.; Davor, S.; Hatem, Z.; Ehab, E.-S. Learning-Based Detection of Malicious Volt-VAr Control Parameters in Smart Inverters. In Proceedings of the 49th Annual Conference of the IEEE Industrial Electronics Society (IES), Singapore, 16–19 October 2023. [Google Scholar] [CrossRef]
- Ahmad, N.A.; Saif, A.-K.; Marwa, Q. Anomaly Detection in Smart Grids: A Survey From Cybersecurity Perspective. In Proceedings of the 2022 3rd International Conference on Smart Grid and Renewable Energy (SGRE), Doha, Qatar, 20–22 March 2022. [Google Scholar] [CrossRef]
- Preetha, T.; Michael, H.; Preston, M.; Ashley, E.; Jared, J. Anomaly Detection in a Smart Microgrid System Using Cyber-Analytics: A Case Study. Energies 2023, 16, 7151. [Google Scholar] [CrossRef]
- Samuel, K.; Chau, C.-K.; Hammond, P.; Mohi, A.; Helge, J. Systematic Study of Cybersecurity Threats for Smart Inverters. In Proceedings of the 15th ACM International Conference on Future and Sustainable Energy Systems, Singapore, 4–7 June 2024. [Google Scholar] [CrossRef]
- BoHyun, A.; Taesic, K.; Seerin, A.; Sudip, K.M.; Jay, J.; Alan, M.H.; Chris, F. An Overview of Cyber-Resilient Smart Inverters based on Practical Attack Models. In Proceedings of the 10th International Conference on Modern Power Systems (MPS), Cluj-Napoca, Romania, 21–23 June 2023. [Google Scholar] [CrossRef]
- Roberts, C.; Ngo, S.-T.; Milesi, A.; Peisert, S.; Arnold, D.; Saha, S.; Scaglione, A.; Johnson, N.; Kocheturov, A.; Fradkin, D. Deep Reinforcement Learning for DER Cyber-Attack Mitigation. In Proceedings of the 2020 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Tempe, AZ, USA, 11–13 November 2020. [Google Scholar] [CrossRef]
- Christophem, L. Solar Power Europe. Available online: https://www.solarpowereurope.org/insights/interactive-data/total-eu-27-solar-pv-capacity-a-growth-story (accessed on 1 August 2025).
- European Union. Energy. Available online: https://energy.ec.europa.eu/topics/renewable-energy/renewable-energy-directive-targets-and-rules/renewable-energy-directive_en (accessed on 1 August 2025).
- Vairavasundaram, I.; Varadarajan, V.; Pavankumar, P.J.; Kanagavel, R.K.; Ravi, L.; Vairavasundaram, S. A Review on Small Power Rating PV Inverter Topologies and Smart PV Inverters. Electronics 2021, 10, 1296. [Google Scholar] [CrossRef]
- Sampaio, M.F.; Oliveira, C.G.R.; London, J.B.A., Jr. Modeling of smart inverter functions executed by photovoltaic systems for power flow analysis. Electr. Power Syst. Res. 2025, 248, 111873. [Google Scholar] [CrossRef]
- Xin, Z.; Liuchen, C.; Riming, S.; Katelin, S. Power system support functions provided by smart inverters—A review. CPSS Trans. Power Electron. Appl. 2018, 3, 25–35. [Google Scholar] [CrossRef]
- Rondón-Cordero, V.H.; Montuori, L.; Alcázar-Ortega, M.; Siano, P. Advancements in hybrid and ensemble ML models for energy consumption forecasting: Results and challenges of their applications. Renew. Sustain. Energy Rev. 2025, 224, 116095. [Google Scholar] [CrossRef]
- Kim, Z. Inside the Cunning, Unprecedented Hack of Ukraine’s Power Grid. 2016. Available online: https://www.wired.com/2016/03/inside-cunning-unprecedented-hack-ukraines-power-grid/ (accessed on 2 November 2025).
- Pagliery, J. Scary questions in December 23rd Ukraine energy grid hack. 2016. [Google Scholar]
- Jakobson, G. Mission cyber security situation assessment using impact dependency graphs. In Proceedings of the 14th International Conference on Information Fusion, Chicago, IL, USA, 5–8 July 2011. [Google Scholar]
- Ye, J.; Giani, A.; Elasser, A.; Mazumder, S.K.; Farnel, C.L.; Mantooth, H.A.; Kim, T.; Liu, J.; Chen, B.; Seo, G.-S.; et al. A Review of Cyber–Physical Security for Photovoltaic Systems. IEEE J. Emerg. Sel. Top. Power Electron. 2022, 10, 4879–4901. [Google Scholar] [CrossRef]
- Teymouri, A.; Mehrizi-Sani, A.; Liu, C.-C. Cyber Security Risk Assessment of Solar PV Units with Reactive Power Capability. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018. [Google Scholar]
- Liu, X.; Shahidehpour, M.; Cao, Y.; Wu, L.; Wei, W.; Liu, X. Microgrid Risk Analysis Considering the Impact of Cyber Attacks on Solar PV and ESS Control Systems. IEEE Trans. Smart Grid 2017, 8, 1330–1339. [Google Scholar] [CrossRef]
- Baines, J. Actively Exploited Industrial Control Systems Hardware—SolarView Series—Blog—VulnCheck. 2023. Available online: https://www.vulncheck.com/blog/solarview-exploitation (accessed on 2 November 2025).
- Brumfield, C. Hijack of Monitoring Devices Highlights Cyber Threat to Solar Power Infrastructure. 2024. Available online: https://www.csoonline.com/article/2119281/hijack-of-monitoring-devices-highlights-cyber-threat-to-solar-power-infrastructure.html (accessed on 2 November 2025).
- Nicut, M. Prosumatorii Au Deja Capacități Instalate De 900 MW. Primesc Cu Mare Întârziere Banii Pe Energia Livrată, Stocarea Jest O Necesitate, Problemy Z Tensiunea În Rețele. 2023. Available online: https://www.economica.net/capacitate-prosumatori-baterii_678486.html (accessed on 2 November 2025).
- Dudău, R. Prosumatorii și Limitele Actuale ale Sistemelor de Distribuție. EPG—Think Tank. 2023. Available online: https://www.enpg.ro/prosumatorii-si-limitele-actuale-ale-sistemelor-de-distributie/ (accessed on 4 November 2025).
- Sowiński, R.; Komorowska, A. Forecasting electricity prices in the Polish Day-Ahead. Polityka Energetyczna Energy Policy J. 2025, 28, 211–230. [Google Scholar] [CrossRef]
- PSE Summary of Quantitative Data on the Functioning of the National Power System in 2023. 2024.
- PSE KSE Energy Power Demand. Available online: https://www.pse.pl/dane-systemowe/funkcjonowanie-kse/raporty-dobowe-z-pracy-kse/zapotrzebowanie-mocy-kse (accessed on 25 October 2025).
- Elektroenergetyczne, P.S. PPS operation—power generation of generating units. 2025. [Google Scholar]
- Institute for Renewable Energy (IEO). Photovoltaic Market in Poland 2024; Institute for Renewable Energy: Warsaw, Poland, 2024; Available online: https://ieo.pl/raport-rynek-fotowoltaiki-w-polsce-2024 (accessed on 25 October 2025).
- PTPiREE. Mikroinstalacje W Polsce. Stan NA 30 Czerwca; PTPiREE: Poznań, Poland, 2025. (In Polish) [Google Scholar]
- PTPiREE. Micro-Installations in Poland; PTPiREE: Poznań, Poland, 2025. [Google Scholar]
- Paulina, S.; Katarzyna, B.; Postawy, K.E. Opinie i oczekiwania Polek i Polaków. 2023. [Google Scholar]
- Michał, F.; Beata, R. Opinia Publiczna o Polityce Energetycznej. Available online: https://www.cbos.pl/SPISKOM.POL/2024/K_056_24.PDF (accessed on 25 October 2025).
- Wittels, M.; Traczyk, A. Polityka Klimatyczna z Ludzką Twarzą. Oczekiwania Polek i Polaków Wobec Zielonej Transformacji. 2024. Available online: https://www.moreincommon.pl/nasze-projekty/polityka-klimatyczna-z-ludzka-twarza (accessed on 25 October 2025).
- Zhong, Q.; Zhao, B.; Ji, Y.; Li, Q.; Yang, X.; Chu, M.; Hu, Y.; Li, L.; Li, S.; Xu, H.; et al. Solvent-Engineering-Assisted Ligand Exchange Strategy for High-Efficiency AgBiS2 Quantum Dot Solar Cells. Angew. Chem. Int. Ed. 2024, 63, e202412590. [Google Scholar] [CrossRef]
- Ji, Y.; Zhong, Q.; Zhao, B.; Li, Q.; Yang, X.; Chu, M.; Hu, Y.; Li, L.; Li, S.; Xu, H.; et al. Surface Engineering Enables Efficient AgBiS2 Quantum Dot Solar Cells. Nano Lett. 2024, 24, 10418–10425. [Google Scholar] [CrossRef]
- Su, L. Room Temperature Growth of CsPbBr3 Single Crystal for Asymmetric MSM Structure Photodetector. J. Mater. Sci. Technol. 2024, 187, 113–122. [Google Scholar] [CrossRef]
- Kwon, H.; Lim, J.W.; Kim, D.H. Plasmonic Perovskite Photodetector with High Photocurrent and Low Dark Current Mediated by Au NR/PEIE Hybrid Layer. J. Mater. Sci. Technol. 2025, 218, 45–53. [Google Scholar] [CrossRef]
- PSE. Dane Systemowe. 2024. Available online: https://www.pse.pl/dane-systemowe (accessed on 25 October 2025).
- Goiana-da-Silva, F.; Madureira-Fonseca, D.; Tude Graça, D.; Moitinho De Almeida, M.; Cabral Pinho, M.; Sá, J.; Moreira, R.; Cabral, L.; Pereira, N.; Nunes, A.M. When the lights went out: Impacts of the April 2025 Iberian blackout on the Portuguese National Health Service sovereignty—A reflection on national defence, health sovereignty, risk, and infrastructural dependency. Front. Public Health 2025, 13, 1630933. [Google Scholar] [CrossRef] [PubMed]
- PISM. Consequences of the Iberian Blackout Stretch Across Europe. Available online: https://pism.pl/publications/consequences-of-the-iberian-blackout-stretch-across-europe (accessed on 25 October 2025).
- Zhang, R.; Dehghanian, P.; Li, Y. AI-in-the-Loop Resilience Enhancement of Cyber–Physical Electric Power Systems Against Electromagnetic Pulse Attacks. IEEE Trans. Reliab. 2025, 1–15. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).