Securing Photovoltaic Systems as Critical Infrastructure: A Multi-Layered Assessment of Risk, Safety, and Cybersecurity
Abstract
1. Introduction
2. A Decade of PV Installations in Europe and Romania
3. Assessing the Security and Safety of PV Systems as Critical Energy Infrastructure in Romania
3.1. SWOT Analysis
3.1.1. Strengths
- (a)
- Sustainability and low environmental impact
- Produce clean energy, without CO2 emissions;
- Do not generate noise pollution or hazardous waste;
- Have a minimal impact on biodiversity, especially if they are harmoniously integrated into the landscape.
- (b)
- Energy efficiency and independence:
- Reduce dependence on fossil fuels and their price fluctuations;
- Can contribute to the energy independence of a country or region;
- Are scalable, and can be expanded according to needs.
- (c)
- Low long-term costs:
- After the initial investment, operating and maintenance costs are relatively low;
- PV panels have a lifespan of 25–30 years, offering long-term returns;
- Government subsidies and support schemes can make the investment even more profitable.
- (d)
- Easy installation and maintenance:
- Installing a PV system is faster compared to other types of power plants;
- Requires little maintenance, as the panels have no moving parts that wear out quickly.
- (e)
- Flexibility and diversification of land use:
- Can be installed on unproductive or unused land;
- Coexist with other activities, such as agriculture (agrivoltaics);
- Can be integrated into smart-grid networks to optimize consumption.
3.1.2. Weaknesses
- (a)
- Dependence on weather conditions. The efficiency of the panels decreases on cloudy or rainy days, and the energy production is zero at night.
- (b)
- The need for large land areas. To produce a significant amount of energy, PV fields require large areas of land, which can lead to deforestation or the reduction in agricultural land.
- (c)
- Relatively low efficiency. The conversion of solar energy into electricity is not 100% efficient, with most panels having efficiencies of 15–22%.
- (d)
- High initial costs. Although the prices of solar panels have decreased in recent years, the initial investment for a PV park remains significant.
- (e)
- Environmental impact. Although solar energy is considered clean, the production and disposal of PV panels can generate toxic waste and CO2 emissions.
- (f)
- Dependence on batteries for storage. To ensure continuous energy, storage systems (batteries) are needed, which are expensive and have their own environmental impact.
- (g)
- Issues related to grid integration. Production fluctuations can create difficulties in the stability of the electricity grid and require solutions to balance supply and demand.
- (h)
- Limited lifespan. PV panels have a lifespan of approximately 25–30 years, after which their efficiency decreases, requiring replacement and recycling.
- (i)
- Possible maintenance issues. Although they are relatively easy to maintain, the panels must be cleaned periodically and monitored for defects or loss of efficiency.
- (j)
- Impact on biodiversity. In certain cases, the construction of PV fields can affect local flora and fauna, especially in protected natural areas.
3.1.3. Opportunities
- (a)
- Economic opportunities
- Energy cost reduction—Own solar energy production can lead to lower costs for consumers and businesses;
- Profitable investments—The financial returns of PV fields are attractive due to the decrease in the prices of solar panels and their increase in efficiency;
- Job creation—The installation and maintenance of solar panels generates jobs in the renewable energy sector;
- Subsidies and financing—Governments and international organizations offer various financial support schemes for the development of renewable energy.
- (b)
- Environmental opportunities
- CO2 emission reduction—Solar energy is clean and contributes to reducing dependence on fossil fuels;
- Long-term sustainability—The sun is an inexhaustible resource, and its use does not negatively affect the environment;
- Reuse of degraded land—PV fields can be located on unproductive or abandoned land, giving it a new utility.
- (c)
- Technological Opportunities
- Innovations in energy storage—Modern batteries allow the storage of solar energy for use at night or on cloudy days;
- Integration into smart grids—PV fields can be connected to smart grids, optimizing energy distribution;
- Increased automation and efficiency—New technologies, such as artificial intelligence and cleaning robots, improve the performance and maintenance of solar fields.
- (d)
- Security Opportunities
3.1.4. Threats, Risks, Vulnerabilities, and Hazards
- Threats
- Natural factors—Storms, hail, wildfires, earthquakes, or floods can damage solar panels and park infrastructure;
- Vandalism and theft—Solar panels, inverters, and cables are attractive to thieves, and vandalism can affect energy production;
- Cyberattacks—Control and monitoring systems can be targets for cyberattacks, affecting the operation of the park;
- Regulations and policies—Changes in legislation, new taxes or land restrictions can threaten the economic viability of the project.
- Risks
- Decreased efficiency—Dust, dirt, or the degradation of panels over time can reduce energy production;
- Technical problems—Failures in inverters, connections, or energy storage system can affect the continuity of production;
- Dependence on weather conditions—The performance of a PV park depends directly on the intensity of sunlight, with a risk of lower production on cloudy days;
- Impact on the environment and biodiversity—Deforestation for the installation of the park or changes to the ecosystem can affect local fauna and flora;
- Unforeseen costs—Increased maintenance costs, repairs, or price changes to equipment can affect profitability.
- Vulnerabilities
- Physical security—A poorly protected park is vulnerable to vandalism and theft;
- Dependence on supply chains—Problems with suppliers of panels, inverters, or batteries can delay projects and increase costs;
- Lack of infrastructure—Connecting the park to the electricity grid can be difficult if the local infrastructure is not ready for such integration;
- Long payback period—The amortization of the initial costs can take years, and fluctuations in the price of electricity can affect profitability.
- Hazards
- Environmental impact
- Deforestation and habitat loss—PV fields are sometimes built on agricultural land or forests, affecting biodiversity;
- Impact on wildlife—Animals may be disturbed by changes in habitat or by the reflection of solar panels;
- Impact on soil and water—Changes to the land for the installation of panels can lead to erosion or changes in water runoff.
- Economic and social issues
- Agricultural land use—If installed on fertile land, they can reduce the agricultural area available for food production;
- Visual impact—PV fields can alter the landscape and may be considered unsightly by local communities;
- Noise and nuisance—Although the panels themselves do not produce noise, auxiliary equipment such as inverters and cooling systems can generate some level of noise pollution.
- Recycling and waste management issues
- Difficulty in recycling panels—Solar panel components (glass, silicon, heavy metals) are difficult to recycle, which may lead to environmental problems in the future;
- Use of rare materials—Panels contain metals such as cadmium or tellurium, the extraction of which may have a negative impact on the environment.
- Technical, safety, and security aspects
- Fire risk—Solar panels and electrical equipment can present hazards in case of overload or technical defects;
- Material degradation—Solar panels have a limited lifespan (around 25–30 years), and managing the resulting waste can be problematic;
- Electromagnetism—Some studies suggest that the equipment used in PV fields could generate electromagnetic fields, but the effects on health are still debated;
- Blackout risk—Some inverters can be remotely controlled by certain manufacturing companies, which makes the risk of disconnection of PV fields very likely and with a very serious gravity and impact on energy and national security.
3.1.5. Security, Safety, and Protection Measures
- Physical protection and security
- Fencing and access control—Installation of security fences and controlled access gates to prevent intrusion;
- Video surveillance systems—Use of surveillance cameras with motion detection and 24/7 monitoring;
- Detection sensors—Implementation of sensors to detect movement, vibration, or opening of panels;
- Security patrols—Presence of security personnel or drones for regular inspections;
- Anti-theft and anti-vandalism systems—GPS tracking devices for panels, alarms, and invisible markings for components.
- Electrical safety and equipment protection:
- Grounding system—Prevention of electric shock and protection of equipment against atmospheric discharges;
- Lightning protection—Installation of lightning rods and surge arresters;
- Circuit breakers and overload protection—Installing safety equipment to prevent short circuits and fires;
- Adequate ventilation and cooling—Preventing equipment from overheating through efficient cooling systems;
- Periodic maintenance and inspection—Checking connections, wiring, and panels to prevent failures.
- Protection against natural factors and disasters
- Wind and weather protection—Installation resistant to strong gusts, hail, and floods;
- Fire prevention—Using fire-retardant materials and a rapid-fire response plan;
- Weather monitoring—Alert systems for extreme conditions that can affect production and park safety.
3.2. Blackout Risk Assessment
3.2.1. Parts of the PV Systems
- PV panels
- Monocrystalline: Mono-Si;
- Polycrystalline: Poly-Si;
- Thin-film: Thin-Film;
- Bifacial: Captures light on both sides;
- Passivated Emitter Rear Cell (PERC) technology.
- Inverters
- Centralized: Used in large PV systems and connect several strings of solar panels to a single large inverter;
- String: Each string of panels has its own inverter and is used in large commercial and residential installations;
- Microinverters: Each panel has its own inverter and is used in residential systems and small PV systems;
- Hybrid: Can operate both with the electrical grid and with energy storage batteries and is used in solar PV systems that include energy storage solutions.
- Electricity meters
- Production measurement: Measures the electrical energy generated by PV panels;
- Auxiliary consumption measurement: Records the consumption of auxiliary equipment in the park (inverters, cooling systems, lighting, surveillance, etc.);
- Bidirectional: Monitors both the energy delivered to the grid and the energy consumed from the grid, being essential for self-consumption and grid injection systems;
- Smart meters: Allows real-time monitoring in integration with SCADA systems to optimize energy management.
- Electrical transformers
- Role:
- Voltage boosting: PV panels generate direct current (DC), converted into alternating current (AC) by inverters; this current usually has a voltage of 400 V ÷ 690 V, which must be raised to an appropriate level for efficient transport through the grid (e.g., 20 kV or 110 kV);
- Loss reduction: Increasing the voltage reduces losses on the power line and allows the efficient transport of electricity over long distances;
- Grid connection: Ensures compatibility between the PV park and the electricity distribution or transport network.
- Types:
- Boosters: Raise the voltage from the level generated by the inverters (400 V–690 V) to 20 kV or 110 kV, to allow injection into the grid.
- Distribution: Used to power auxiliary equipment in the park (monitoring systems, lighting, air conditioning, etc.).
- Isolation: Protects the system against faults and avoids the occurrence of ground fault currents.
- Power substations:
- Medium voltage: 20 kV;
- High voltage: 110 kV or 220 kV/400 kV.
- Electrical energy storage systems:
- Types:
- Electrochemical batteries: Li-ion, lithium–iron–phosphate, lead–acid, redox flow, etc.;
- Supercapacitors;
- Hydrogen;
- Pumped storage;
- Compressed air, etc.
- Benefits:
- Grid balancing: Reduces fluctuations caused by variations in solar intensity;
- Consumption maximization: Allows the use of the energy produced even when the panels are not generating electricity;
- Reduction in balancing costs: Minimizes the need to import electricity from other sources during peak hours;
- Energy security: Ensures constant power supply in microgrids or isolated areas.
- Electrical lines for discharging electrical energy into the distribution or transmission network
- Underground or overhead medium-voltage power lines;
- Underground or overhead high-voltage power lines.
- SCADA system:
- By system architecture:
- Centralized: All data are collected and processed in a single control center and provides complete visibility over the entire PV park;
- Distributed: Control is divided between several local nodes that communicate with each other, ensures redundancy and great flexibility, can operate independently in the event of a failure of the central system, and is suitable for large PV systems with multiple conversion stations.
- By type of communication and technology:
- Based on industrial protocol (Modbus, DNP3, IEC 61850): Uses communication protocols for industrial equipment and is compatible with most equipment used in solar energy (inverters, energy meters, weather sensors);
- Cloud-based (IoT—Enabled SCADA: Data are transmitted and processed in a cloud environment, allowing remote access, advanced data analysis, and integration with AI and machine learning.
- By automation level:
- Passive (monitoring, no control): Only collects data (generated power, temperature, solar radiation level), decisions are made by human operators and is used in smaller PV systems or in the initial phase of implementation;
- Active (monitoring and automated control): Can adjust system parameters in real time (optimizing the operation of inverters, changing the angle of solar panels), includes advanced functions such as energy efficiency management and protection against faults
- By scope:
- For Energy Management Systems (EMSs): Monitors and optimizes electricity production, integrates with battery systems for energy storage and helps balance the load on the grid;
- For diagnostics and predictive maintenance: Uses artificial intelligence algorithms to identify possible defects in equipment and can detect efficiency losses of PV panels caused by dirt or defects;
- For integration with the electrical grid: Ensures compliance with the requirements of grid operators and regulates voltage and frequency to avoid imbalances in the system.
3.2.2. Causes and Effects in Blackout Risk Scenario
- Causes
- (a)
- Natural risk factors
- Storms and extreme weather events: Strong winds, torrential rains, heavy snow, hail, and lightning, which can damage electrical systems and equipment in PV systems (PV panels, electrical inverters, electrical meters, electrical transformers, energy storage systems, electrical power evacuation lines);
- Earthquakes or landslides: These events can damage electrical and mechanical infrastructure;
- Extreme temperatures: Excessive heat or cold can overload the electrical grid or damage PV panels.
- (b)
- Technical risk factors:
- Defects or poor quality of PV panels;
- Damage to step-up transformers or overhead or underground cables: Age or wear of equipment;
- Overload in the PV park: Excessive electricity consumption in the power station;
- Short circuits in the electrical power lines or in the electrical power distribution panels;
- Efficiency, life span, and quality of energy equipment;
- Lack of electrical energy storage systems;
- Lack or precariousness of SCADA systems;
- Lack of or poor cybersecurity programs.
- (c)
- Human risk factors:
- Lack or precariousness of maintenance or repair work;
- Human errors in the operation or management of the PV park or electrical networks;
- Acts of vandalism, theft, or sabotage;
- Lack of investment;
- Wrong configuration: PV panels, inverters, transformers, electricity evacuation lines;
- Wrong maneuvers performed by operational or dispatching personnel;
- Lack of specialized and/or trained operational personnel;
- Lack of communication or poor communication with DET—Territorial Energy Dispatcher, or DEN—National Energy Dispatcher;
- Lack of working procedures during a crisis;
- Lack/non-compliance/ignorance of national/European procedures in case of serious damage (blackout);
- Lack of training in the field of risk management;
- Lack of physical security of PV systems;
- Lack of electricity in the distribution or transport networks: possible local, zonal, regional, or national blackout of the SEN (National Power System);
- Enormous material damage generated by the lack of electricity to critical consumers, households, and industries;
- Enormous material damage resulting from the interdependence of other systems on electricity;
- State of energy, economic, and national insecurity.
- Effects
- Lack of electricity in the distribution or transmission networks: possible local, zonal, regional, or national blackout of the SEN;
- Enormous material damage resulting from the lack of electricity to critical consumers, households, and industries;
- Enormous material damage resulting from the interdependence of other systems on electricity;
- State of energy, economic, and national insecurity.
3.2.3. The Probability Scale
3.2.4. The Severity of the Consequences
- Impact Analysis
- B.
- Assessing risk severity
3.2.5. Risk Management
3.2.6. Reevaluation of the Consequence Severity
3.2.7. Risk Level After Application of Mitigation Measures
4. Addressing PV Systems’ Vulnerabilities to Cyberattacks
4.1. Specific Cyber Threats in PV Systems
4.2. PV Key Components Vulnerable to Cyberattacks
4.3. A Brief Literature Review on Cyber Threats and Security Solutions in PV Systems
4.4. Cyber Incidents in Solar PV Systems
4.5. Common Vulnerabilities and Exposures (CVE) and Common Weakness Enumeration (CWE) in PV Systems
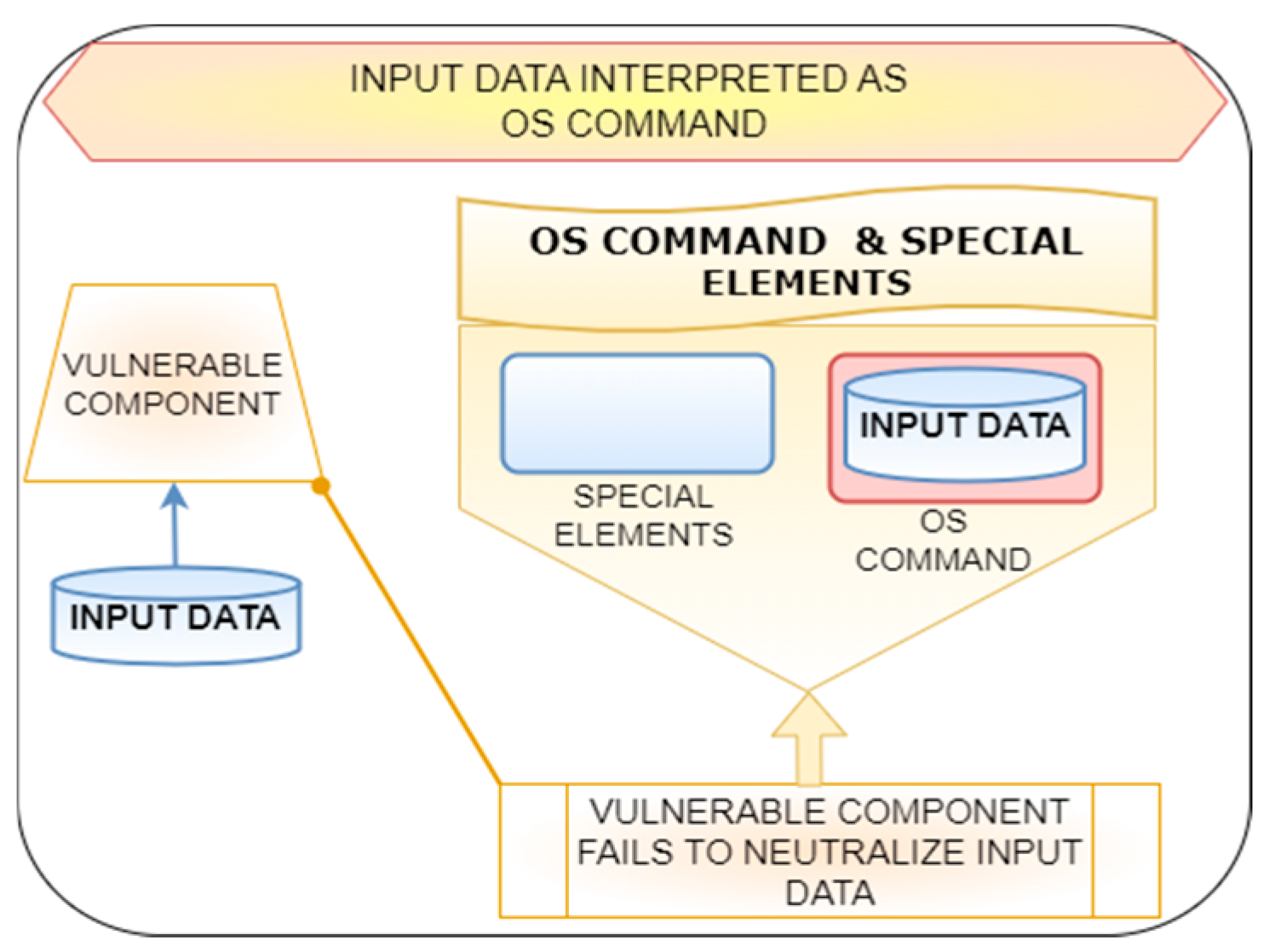
- Weakness ID: CWE-78—There is an improper neutralization of special elements used in an Operating System Command Injection (OSCI).
- 2.
- Weakness ID: CWE-306—Missing authentication for critical function (MACF).
- 3.
- Weakness ID: CWE-312—Cleartext storage of sensitive information (CSSI).
- 4.
- Weakness ID: CWE-352—Cross-Site Request Forgery (CSRF).
5. Strategies for Cyber Threats Mitigation in Solar PV Systems
5.1. Cybersecurity Risk Management in PV Systems
5.2. Security Policy for PV Systems
- All PV systems’ assets (solar panels, inverters, SCADA systems, monitoring platforms, sensors, and network infrastructure);
- Personnel (employees, contractors, and third-party service providers handling PV operations);
- Data security (grid connectivity, energy production data, remote monitoring, and communication channels).
- Install fencing, gates, and surveillance cameras (CCTV) around PV farms;
- Use motion sensors and intrusion alarms for unauthorized access detection;
- Maintain security patrols in high-risk areas;
- GPS tracking on high-value assets (inverters, transformers);
- Lightning protection systems for weather-related risks;
- Fire detection and suppression systems at critical sites.
- Encrypt energy production data before transmission;
- Ensure compliance with GDPR for personal data collected from monitoring systems;
- Store logs and audit trails for at least 1 year for forensic analysis;
- Conduct mandatory security training for all employees and contractors;
- Simulated phishing tests to improve awareness;
- Strict onboarding and offboarding procedures for access control.
5.3. Compulsory Security Measures
- Ensuring that all software and firmware in the system are up to date by regular updates and patch management;
- The use of MFA and enforce strong passwords for remote access to devices and control systems for a strong authentication;
- Encrypting data both at rest and during transmission to protect sensitive information.
- Isolate critical components (e.g., inverters, EMS) from less critical systems to reduce the attack surface using the network segmentation principle;
- Deploy IDS to monitor any unusual activity and potential cyberattacks in real time;
- Secure physical assets with locks, surveillance cameras, and restricted access areas to prevent tampering;
- Ensuring that PV components are sourced from reputable manufacturers with transparent security practices can reduce the risk of embedded vulnerabilities as part of a strong supply chain vigilance;
- Adhering to established cybersecurity standards and guidelines can enhance the resilience of PV systems against potential threats.
5.4. Cybersecurity Capability Maturity Model (C2M2) for PV Systems
- Risk Management (RISK)
- 2.
- Asset, Change, and Configuration Management (ASSET)
- 3.
- Identity and Access Management (ACCESS)
- 4.
- Threat and Vulnerability Management (THREAT)
- 5.
- Situational Awareness (SITUATION)
- 6.
- Information Sharing and Communications (SHARING)
- 7.
- Event and Incident Response, Continuity of Operations (RESPONSE)
- 8.
- Supply Chain and External Dependencies Management (DEPENDENCIES)
- 9.
- Workforce Management (WORKFORCE)
- 10.
- Cybersecurity Program Management (CYBER)
5.5. Practical Cybersecurity Measures for PV Systems
- Network Segmentation
- B.
- ADS
- C.
- Encryption Protocols
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AC | Alternating current |
| ANRE | National Energy Regulatory Authority |
| API | Application Programming Interface |
| C2M2 | Cybersecurity Capability Maturity Model |
| CIA | Confidentiality, integrity, and availability |
| CSRF | Cross-Site Request Forgery |
| CSSI | Cleartext storage of sensitive information |
| CVE | Common Vulnerabilities and Exposures |
| CVSS | Common Vulnerability Scoring System |
| CWE | Common Weakness Enumeration |
| DC | Direct current |
| DDoS | Distributed denial-of-service |
| DEN | National Energy Dispatcher |
| DER | Distributed Energy Resources |
| DET | Territorial Energy Dispatcher |
| DNP3 | Distributed Network Protocol |
| DNSC | National Cyber Security Directorate |
| DoS | Denial-of-service |
| DS&CS | Data storage and cloud system |
| DSU | Department of Emergency Situations |
| EMS | Energy Management System |
| FDI | False Data Injection |
| GHI | Global horizontal irradiation |
| GIS | Grid integration systems |
| HMI | Human–Machine Interface |
| IDS | Intrusion Detection System |
| IEA | International Energy Agency |
| IPS | Intrusion Prevention System |
| IRP | Incident response plan |
| IT | Information Technology |
| MACF | Missing authentication for critical function |
| MCS | Monitoring and Control System |
| MITM | Man-in-the-middle |
| ML | Machine learning |
| NIS2 | Network and Information System |
| NVD | National Vulnerability Database |
| OSCI | Operating System Command Injection |
| OT | Operational Technology |
| PID | Potential-Induced Degradation |
| PTFL | Parametric Time-Frequency Logic |
| PV | Photovoltaic |
| PVOUT | PV power output |
| ROI | Return on Investment |
| SCADA | Supervisory Control and Data Acquisition |
| SEN | National Power System |
| SM&IoT Ds | Smart Meter and IoT Devices |
| SRI | Intelligence Service in Romania |
| SSH | Secure shell |
| SWOT | Strengths, weaknesses, opportunities, threats |
| VAR | Voltage-ampere reactive |
References
- Fîță, N.D.; Obretenova, M.I.; Șchiopu, A.M. National Security–Elements Regarding the Optimisation of Energy Sector; LAP Lambert Academic Publishing: London, UK, 2024; ISBN 978-620-7-45693-2. [Google Scholar]
- Fîță, N.D.; Tătar, A.; Obretenova, M.I. Security Risk Assessment of Critical Energy Infrastructures; LAP Lambert Academic Publishing: London, UK, 2024; ISBN 978-620-7-45824-0. [Google Scholar]
- Fîță, N.D.; Obretenova, M.I.; Popescu, F.G. Romanian Power System–European Energy Security Generator; LAP Lambert Academic Publishing: London, UK, 2024; ISBN 978-620-7-46269-8. [Google Scholar]
- Fîță, D.N.; Petrilean, D.C.; Diodiu, I.L. Analysis of the National Power Grid from Romania in the Context of Identifying Vulnerabilities and Ensuring Energy Security. Renew. Energy Power Qual. J. (RE&PQJ) 2024, 22, 386. [Google Scholar] [CrossRef]
- Fîță, N.D.; Petrilean, D.C.; Diodiu, I.L.; Rada, A.C.; Schiopu, A.M.; Muresan-Grecu, F. Analysis of the Causes of Power Crises and Their Impacts on Energy Security. In Proceedings of the International Conference on Electrical, Computer and Energy Technologies (ICECET 2024), Sydney, Australia, 25–27 July 2024. [Google Scholar] [CrossRef]
- Dumitrașcu, M.; Grigorescu, I.; Vrînceanu, A.; Mocanu, I.; Mitrică, B.; Dumitrică, C.; Șerban, P. An Indicator-Based Approach to Assess and Compare the Environmental and Socio-Economic Consequences of PV Systems in Romania’s Development Regions. Environ. Dev. Sustain. 2024. [Google Scholar] [CrossRef]
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. ISO/IEC, 2022. Available online: https://www.iso.org/standard/27001 (accessed on 15 January 2025).
- Romanian Government. 155/2024; Emergency Ordinance No. 155/2024 on the Establishment of a Framework for the Cybersecurity of Networks and Information Systems in the National Civil Cyberspace; Official Gazette of Romania: Bucharest Romania, 2024. [Google Scholar]
- Laasri, S.; El Hafidi, E.M.; Mortadi, A.; Chahid, E.G. Solar-Powered Single-Stage Distillation and Complex Conductivity Analysis for Sustainable Domestic Wastewater Treatment. Environ. Sci. Pollut. Res. 2024, 31, 29321–29333. [Google Scholar] [CrossRef]
- El Hafidi, E.M.; Chahid, E.G.; Mortadi, A.; Laasri, S. Study on a New Solar-Powered Desalination System to Alleviate Water Scarcity Using Impedance Spectroscopy. Mater. Today Proc. 2024. [Google Scholar] [CrossRef]
- Rossi, R.; Mehan, B. EU Market Outlook for Solar Power 2024–2028. SolarPower Europe. 2024. Available online: https://www.solarpowereurope.org/insights/outlooks/eu-market-outlook-for-solar-power-2024-2028 (accessed on 20 March 2025).
- Kułyk, P.; Michałowska, M.; Szudra, P. Assessment of the Conditions for the Development of PV Investment in the Countries of the Visegrad Group–Comparative Study of the Researched Countries. Energy Rep. 2023, 10, 3929–3940. [Google Scholar] [CrossRef]
- Pasculescu, D.; Niculescu, T. Study of Transient Inductive-Capacitive Circuits Using Data Acquisition Systems. Int. Multidiscip. Sci. GeoConf. SGEM 2015, 2, 323–329. [Google Scholar]
- Pasculescu, V.M.; Radu, S.M.; Pasculescu, D.; Niculescu, T. Dimensioning the Intrinsic Safety Barriers of Electrical Equipment Intended to Be Used in Potentially Explosive Atmospheres Using the SimPowerSystems Software Package. Int. Multidiscip. Sci. GeoConf. SGEM 2013, 1, 417. [Google Scholar]
- Pana, L.; Grabara, J.; Pasculescu, D.; Pasculescu, V.M.; Moraru, R.I. Optimal Quality Management Algorithm for Assessing the Usage Capacity Level of Mining Transformers. Pol. J. Manag. Stud. 2018, 18, 233–244. [Google Scholar] [CrossRef]
- Ilieva-Obretenova, M. Information System Functions for SmartGrid Management. Sociol. Study 2016, 6, 96–104. [Google Scholar] [CrossRef]
- Ilieva-Obretenova, M. Impact of an Energy Conservation Measure on Reducing CO2 Emissions. Electrotech. Electron. (E+E) 2021, 56, 46–54. [Google Scholar]
- IEA. Approximately 100 million Households Rely on Rooftop Solar PV by 2030. International Energy Agency. 2022. Available online: https://www.iea.org/reports/approximately-100-million-households-rely-on-rooftop-solar-pv-by-2030 (accessed on 11 January 2025).
- Kumar, S. Recent Advances in Energy Storage Systems for Renewable Source Integration: A Technology Review. Sustainability 2022, 14, 5985. [Google Scholar] [CrossRef]
- Statista. Existing Capacity of Solar PV Worldwide by Select Country 2023. Statista 2024. Available online: https://www.statista.com/statistics/264629/existing-solar-pv-capacity-worldwide/ (accessed on 21 February 2025).
- IO Plus. Europe’s Solar Panel Installations Saw a Significant Slowdown in 2024. Available online: https://ioplus.nl/en/posts/europes-solar-panel-installations-saw-a-significant-slowdown-in-2024 (accessed on 15 February 2025).
- European Commission. REPowerEU: Affordable, Secure, and Sustainable Energy for Europe. Available online: https://commission.europa.eu/strategy-and-policy/priorities-2019-2024/european-green-deal/repowereu-affordable-secure-and-sustainable-energy-europe_en (accessed on 20 January 2025).
- U.S. Department of Energy. Solar Energy Technologies Office. Available online: https://www.energy.gov/eere/solar/ (accessed on 28 January 2025).
- Jowett, P. Romania’s 2024 Solar Additions Hit 1.7 GW. PV Magazine. 2025. Available online: https://www.pv-magazine.com/2025/01/31/romanias-2024-solar-additions-hit-1-7-gw/ (accessed on 25 February 2025).
- GlobalData. Available online: https://www.globaldata.com/ (accessed on 2 February 2025).
- Suri, M.; Betak, J.; Rosina, K.; Chrkavy, D.; Suriova, N.; Cebecauer, T.; Caltik, M.; Erdelyi, B. Global PV Power Potential by Country. In Energy Sector Management Assistance Program (ESMAP); World Bank Group: Washington, DC, USA, 2020; Available online: http://documents.worldbank.org/curated/en/466331592817725242 (accessed on 20 March 2024).
- Global Solar Atlas. Available online: https://globalsolaratlas.info/global-pv-potential-study (accessed on 10 February 2025).
- Niculescu, G.; Avăcăriței, G.; Mihăilescu, M.; Mihai, I.; Radu, V.; Dulamea, R.; Nagy-Bege, Z. Monitor of the Romanian PV Projects. Energynomics, March 2024. Available online: https://www.energynomics.ro/wp-content/uploads/2024/03/Report-Energynomics-PV-Monitor-March-2024-0.2.pdf (accessed on 25 March 2025).
- ANRE. Installed Powers. Available online: https://anre.ro/puteri-instalate/ (accessed on 1 February 2025).
- Top 5 Solar PV Plants in Development in Romania. Power Technology. Available online: https://www.power-technology.com/data-insights/top-5-solar-pv-plants-in-development-in-romania (accessed on 10 February 2025).
- AFM. Photovoltaic Systems Program. Available online: https://www.afm.ro/sisteme_fotovoltaice.php (accessed on 20 December 2024).
- Livoltek. Available online: https://livoltek.com/products/ (accessed on 10 February 2025).
- Enphase Support Portal. Available online: https://support.enphase.com/ (accessed on 5 February 2025).
- EnergyWorld. Romania Remains Extremely Deficient in Energy Storage. Available online: https://energyworld.ro/2025/02/06/romania-romania-remains-extremely-deficient-in-energy-storage/ (accessed on 5 March 2025).
- ISO 31000:2018; International Organization for Standardization. Risk Management—Guidelines; ISO: Geneva, Switzerland, 2018.
- Badica, M.N.; Marinescu (Badica), C.M.; Suditu, S.; Stoica, M.E. Identification, Evaluation and Minimization of Industrial Risks Relating to Gas Pipelines. E3S Web Conf. 2021, 225, 02004. [Google Scholar] [CrossRef]
- Teymouri, A.; Mehrizi-Sani, A.; Liu, C.-C. Cyber Security Risk Assessment of Solar PV Units with Reactive Power Capability. In Proceedings of the IECON 2018–44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 2872–2877. [Google Scholar] [CrossRef]
- Moldovan, D.; Riurean, S. Cyber-Security Attacks, Prevention and Malware Detection Application. J. Digit. Sci. 2022, 4, 3–23. [Google Scholar] [CrossRef] [PubMed]
- Riurean, P.; Bolog, G.; Riurean, S. The Rise of Sophisticated Phishing: How AI Fuels Cybercrime. J. Digit. Sci. 2024, 6, 15–25. [Google Scholar] [CrossRef] [PubMed]
- Johnson, J. Roadmap for PV System Cyber Security. Sandia National Laboratories, Report Number: SAND2017-13262. December 2017. Available online: https://www.researchgate.net/publication/322568290_Roadmap_for_PV_Cyber_Security (accessed on 15 March 2025).
- Walker, A.; Desai, J.; Saleem, D.; Gunda, T. Cybersecurity in PV Plant Operations; National Renewable Energy Laboratory (NREL): Golden, CO, USA, 2021; NREL/TP-5D00-78755. Available online: https://www.nrel.gov/docs/fy21osti/78755.pdf (accessed on 15 March 2025).
- Brumfield, C. Hijack of Monitoring Devices Highlights Cyber Threat to Solar Power Infrastructure. CSO Online 2024. Available online: https://www.csoonline.com/article/2119281/hijack-of-monitoring-devices-highlights-cyber-threat-to-solar-power-infrastructure.html (accessed on 5 May 2024).
- Ye, J.; Giani, A.; Elasser, A.; Mazumder, S.K.; Farnell, C.; Mantooth, H.A.; Kim, T.; Liu, J.; Chen, B.; Seo, G.-S.; et al. A Review of Cyber–Physical Security for PV Systems. IEEE J. Emerg. Sel. Top. Power Electron. 2022, 10, 4879–4901. [Google Scholar] [CrossRef]
- Călin, A.-M.; Cotfas, D.T.; Cotfas, P.A. A Review of Smart PV Systems Which Are Using Remote-Control, AI, and Cybersecurity Approaches. Appl. Sci. 2024, 14, 7838. [Google Scholar] [CrossRef]
- Naumann, V.; Lausch, D.; Hähnel, A.; Bauer, J.; Breitenstein, O.; Graff, A.; Werner, M.; Swatek, S.; Großer, S.; Bagdahn, J.; et al. Explanation of Potential-Induced Degradation of the Shunting Type by Na Decoration of Stacking Faults in Si Solar Cells. Sol. Energy Mater. Sol. Cells 2014, 120, 383–389. [Google Scholar] [CrossRef]
- Saber, A.M.; Youssef, A.; Svetinovic, D.; Zeineldin, H.; El-Saadany, E. Learning-Based Detection of Malicious Volt-VAR Control Parameters in Smart Inverters. In Proceedings of the IECON 2023–49th Annual Conference of the IEEE Industrial Electronics Society, Singapore, 16–19 October 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Farivar, M.; Neal, R.; Clarke, C.; Low, S.H. Optimal Inverter VAR Control in Distribution Systems with High PV Penetration. In Proceedings of the 2012 IEEE Power and Energy Society General Meeting, San Diego, CA, USA, 22–26 July 2012; pp. 1–7. [Google Scholar] [CrossRef]
- Sourav, S.; Biswas, P.P.; Chen, B.; Mashima, D. Detecting Hidden Attackers in PV Systems Using Machine Learning. arXiv 2022. [Google Scholar] [CrossRef]
- Lindström, M.; Sasahara, H.; He, X.; Sandberg, H.; Johansson, K.H. Power Injection Attacks in Smart Distribution Grids with PVs. arXiv 2020. [Google Scholar] [CrossRef]
- Zografopoulos, I.; Hatziargyriou, N.D.; Konstantinou, C. Distributed Energy Resources Cybersecurity Outlook: Vulnerabilities, Attacks, Impacts, and Mitigations. IEEE Syst. J. 2023, 17, 6695–6709. [Google Scholar] [CrossRef]
- Helin, T.F. Solar Cybersecurity Vulnerabilities: 6 Ways in Which Hackers Target Solar Installations. Helindata, 15 October 2024. Available online: https://www.helindata.com/blog/solar-cybersecurity-vulnerabilities (accessed on 20 March 2025).
- Asassfeh, M.; Samara, G.; Abu Zaid, A.; Abu Laila, D.; Al-Anzi, S.; Alqammaz, A.; Al Smadi, A.; Al-Shaikh, A.; Al-Mousa, M.R. Penetration Testing Overview-Opportunities and Ethical Considerations: Literature Notes. In Proceedings of the 2024 International Jordanian Cybersecurity Conference (IJCC), Amman, Jordan, 17–18 December 2024; pp. 131–135. [Google Scholar] [CrossRef]
- Paul, S.; Sanghvi, A.; Reynolds, T. Cybersecurity Assessment for a Behind-the-Meter Solar PV System: A Use Case for the DER-CF. In Proceedings of the 2023 IEEE PES Innovative Smart Grid Technologies Latin America (ISGT-LA), San Juan, PR, USA, 6–9 November 2023; pp. 90–94. [Google Scholar] [CrossRef]
- Harrou, F.; Taghezouit, B.; Bouyeddou, B.; Sun, Y. Cybersecurity of PV Systems: Challenges, Threats, and Mitigation Strategies: A Short Survey. Front. Energy Res. 2023, 11, 1274451. [Google Scholar] [CrossRef]
- Maghami, M.R.; Mutambara, A.G.O.; Gomes, C. Assessing Cyber-Attack Vulnerabilities of Distributed Generation in Grid-Connected Systems. Environ. Dev. Sustain. 2025. [Google Scholar] [CrossRef]
- Mustafa, A.; Poudel, B.; Bidram, A.; Modares, H. Detection and Mitigation of Data Manipulation Attacks in AC Microgrids. IEEE Trans. Smart Grid 2020, 11, 2588–2603. [Google Scholar] [CrossRef]
- Huang, T.; Wang, B.; Ramos-Ruiz, J.; Enjeti, P.; Kumar, P.R.; Xie, L. Detection of Cyberattacks in Renewable-Rich Microgrids Using Dynamic Watermarking. In Proceedings of the IEEE Power and Energy Society General Meeting, Montreal, QC, Canada, 2–6 August 2020. [Google Scholar] [CrossRef]
- Bai, X.; Liu, L.; Wei, D.; Cao, J. Research on Security Threat and Evaluation Model of New Energy Plant and Station. In Proceedings of the 2020 International Conference on Computer Communication and Network Security (CCNS), Xi’an, China, 21–23 August 2020. [Google Scholar] [CrossRef]
- Patel, A.; Roy, S.; Baldi, S. Wide-Area Damping Control Resilience Towards Cyberattacks: A Dynamic Loop Approach. IEEE Trans. Smart Grid 2021, 12, 3438–3447. [Google Scholar] [CrossRef]
- Zhang, J.; Guo, L.; Ye, J. Cyber-Attack Detection for PV Farms Based on Power-Electronics-Enabled Harmonic State Space Modeling. IEEE Trans. Smart Grid 2022, 13, 3929–3942. [Google Scholar] [CrossRef]
- Zhao, L.; Li, J.; Li, Q.; Li, F. A Federated Learning Framework for Detecting False Data Injection Attacks in Solar Farms. IEEE Trans. Power Electron. 2022, 37, 2496–2501. [Google Scholar] [CrossRef]
- Jones, C.B.; Chavez, A.; Hossain-McKenzie, S.; Jacobs, N.; Summers, A.; Wright, B. Unsupervised Online Anomaly Detection to Identify Cyberattacks on Internet Connected Photovoltaic System Inverters. In Proceedings of the 2021 IEEE Power Energy Conference Illinois (PECI), Urbana, IL, USA, 1–2 April 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Beg, O.A.; Nguyen, L.V.; Johnson, T.T.; Davoudi, A. Signal Temporal Logic-Based Attack Detection in DC Microgrids. IEEE Trans. Smart Grid 2019, 10, 3585–3595. [Google Scholar] [CrossRef]
- Shen, Y.; Wang, L.; Lau, J.P.; Liu, Z. A Robust Control Architecture for Mitigating Sensor and Actuator Attacks on PV Converters. In Proceedings of the 2019 IEEE PES GTD Grand International Conference and Exposition Asia (GTD Asia), Bangkok, Thailand, 19–23 March 2019. [Google Scholar] [CrossRef]
- Singh, V.K.; Govindarasu, M. A Cyber-Physical Anomaly Detection for Wide-Area Protection Using Machine Learning. IEEE Trans. Smart Grid 2021, 12, 3514–3526. [Google Scholar] [CrossRef]
- Guo, L.; Zhang, J.; Ye, J.; Coshatt, S.J.; Song, W. Data-Driven Cyber-Attack Detection for PV Farms via Time-Frequency Domain Features. IEEE Trans. Smart Grid 2022, 13, 1582–1597. [Google Scholar] [CrossRef]
- Rahim, F.A.; Ahmad, N.A.; Magalingam, P.; Jamil, N.; Cob, Z.C.; Salahudin, L. Cybersecurity Vulnerabilities in Smart Grids with Solar PV: A Threat Modelling and Risk Assessment Approach. Int. J. Sustain. Constr. Eng. Technol. 2023, 14, 210–220. [Google Scholar] [CrossRef]
- Melniciuc, I.A.; Lazăr, A.; Cabău, G.; Basaraba, R.A. Bitdefender Disclosure Report: Solarman Platform Vulnerability. Available online: https://blogapp.bitdefender.com/labs/content/files/2024/08/Bitdefender-PReport-solarman-creat7907.pdf (accessed on 29 December 2024).
- Kovacs, E. Vulnerabilities Exposed Widely Used Solar Power Systems to Hacking, Disruption. Available online: https://www.securityweek.com/vulnerabilities-exposed-widely-used-solar-power-systems-to-hacking-disruption/ (accessed on 29 December 2024).
- Cybersecurity and Solar Power Vulnerability. Available online: https://www.climatesolutionslaw.com/2025/02/cybersecurity-and-solar-power-vulnerability (accessed on 28 February 2025).
- Solar Power Stocks Fall on Concerns About Potential Hackers. Available online: https://www.investopedia.com/solar-power-stocks-fall-on-concerns-about-potential-hackers-8685365 (accessed on 20 October 2024).
- Finnish Utility Fortum’s Power Assets Targeted with Surveillance Cyberattacks. Available online: https://www.reuters.com/business/energy/finnish-utility-fortums-power-assets-targeted-with-surveillance-cyber-attacks-2024-10-10/ (accessed on 20 December 2024).
- Kurmayer, N.J. White Hat Hacker Shines Spotlight on Vulnerability of Solar Panels Installed in Europe. Available online: https://www.euractiv.com/section/energy-environment/news/hacker-shines-spotlight-on-vulnerability-of-solar-panels-installed-in-europe (accessed on 20 December 2024).
- Dutch Hackers Report Flaws in Enphase IQ Gateway Devices. PV Magazine. 5 September 2024. Available online: https://www.pv-magazine.com/2024/09/05/dutch-hackers-report-flaws-in-enphase-iq-gateway-devices/ (accessed on 23 December 2024).
- National Vulnerability Database. Available online: https://nvd.nist.gov/ (accessed on 28 February 2025).
- Common Vulnerabilities and Exposures (CVE). Available online: https://cve.mitre.org/ (accessed on 5 February 2025).
- Dubasi, Y.; Khan, A.; Li, Q.; Mantooth, A. Security vulnerability and mitigation in PV systems. In Proceedings of the 2021 IEEE 12th International Symposium on Power Electronics for Distributed Generation Systems (PEDG), Chicago, IL, USA, 28 June–1 July 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Cybersecurity and Infrastructure Security Agency (CISA). Advisory ICSA-25-044-16. Available online: https://www.cisa.gov/news-events/ics-advisories/icsa-25-044-16 (accessed on 12 February 2025).
- DNSC (Romanian National Cyber Security Directorate). Alertă: Vulnerabilități Critice de Securitate Cibernetică Identificate la Nivelul unor Produse mySCADA. Available online: https://dnsc.ro/citeste/alerta-vulnerabilitati-critice-de-securitate-cibernetica-identificate-la-nivelul-unor-produse-myscada (accessed on 8 February 2025).
- mySCADA. Available online: https://www.myscada.org/ (accessed on 20 February 2025).
- Common Weakness Enumeration (CWE). Available online: https://cwe.mitre.org/ (accessed on 20 February 2025).
- CVSS v3.1 Calculator. Available online: https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H (accessed on 20 February 2025).
- CVSS v4.0 Calculator. Available online: https://www.first.org/cvss/calculator/4.0#CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N (accessed on 20 February 2025).
- CVSS v3.1 Calculator. Available online: https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H (accessed on 20 February 2025).
- CVSS v4.0 Calculator. Available online: https://www.first.org/cvss/calculator/4.0#CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:H/SI:H/SA:H (accessed on 20 February 2025).
- NIST Cybersecurity Framework (CSF) 2.0; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024. [CrossRef]
- NIS 2 (Directive (EU) 2022/2555). the European Union’s Updated Framework for Cybersecurity. 2022. Available online: https://www.nis-2-directive.com/ (accessed on 15 January 2025).
- Antipova, T.; Riurean, S. Managing cyber resilience literacy for consumers. Int. J. Inform. Commun. Technol. 2025, 14, 122–131. [Google Scholar] [CrossRef]
- IEC 62443:2020; Security for Industrial Automation and Control Systems—Part 3-2: Security Risk Assessment for System design. International Electrotechnical Commission: Geneva, Switzerland, 2020.
- IEEE Std 1547.3-2023 (Revision of IEEE Std 1547.3-2007); IEEE Guide for Cybersecurity of Distributed Energy Resources Interconnected with Electric Power Systems. IEEE: Piscataway, NJ, USA, 2023; pp. 1–183. [CrossRef]
- Peng, S.; Liu, M.; Zuo, K.; Tan, W.; Deng, R. Stealthy data integrity attacks against grid-tied PV systems. In Proceedings of the 2023 IEEE 6th International Conference on Industrial Cyber-Physical Systems (ICPS), Wuhan, China, 8–11 May 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Riurean, S.; Antipova, T. Prebunking, an effective defense mechanism to strengthen consumers’ cyber awareness. Ann. Univ. Petrosani Electr. Eng. 2024, 26, 122–131. Available online: https://www.upet.ro/annals/electrical/doc/2024/Annals%20Electric%202024%20v1.pdf (accessed on 28 February 2025).
- India Smart Grid Forum. Available online: https://indiasmartgrid.org/upload/201705Wed174314.pdf (accessed on 28 February 2025).

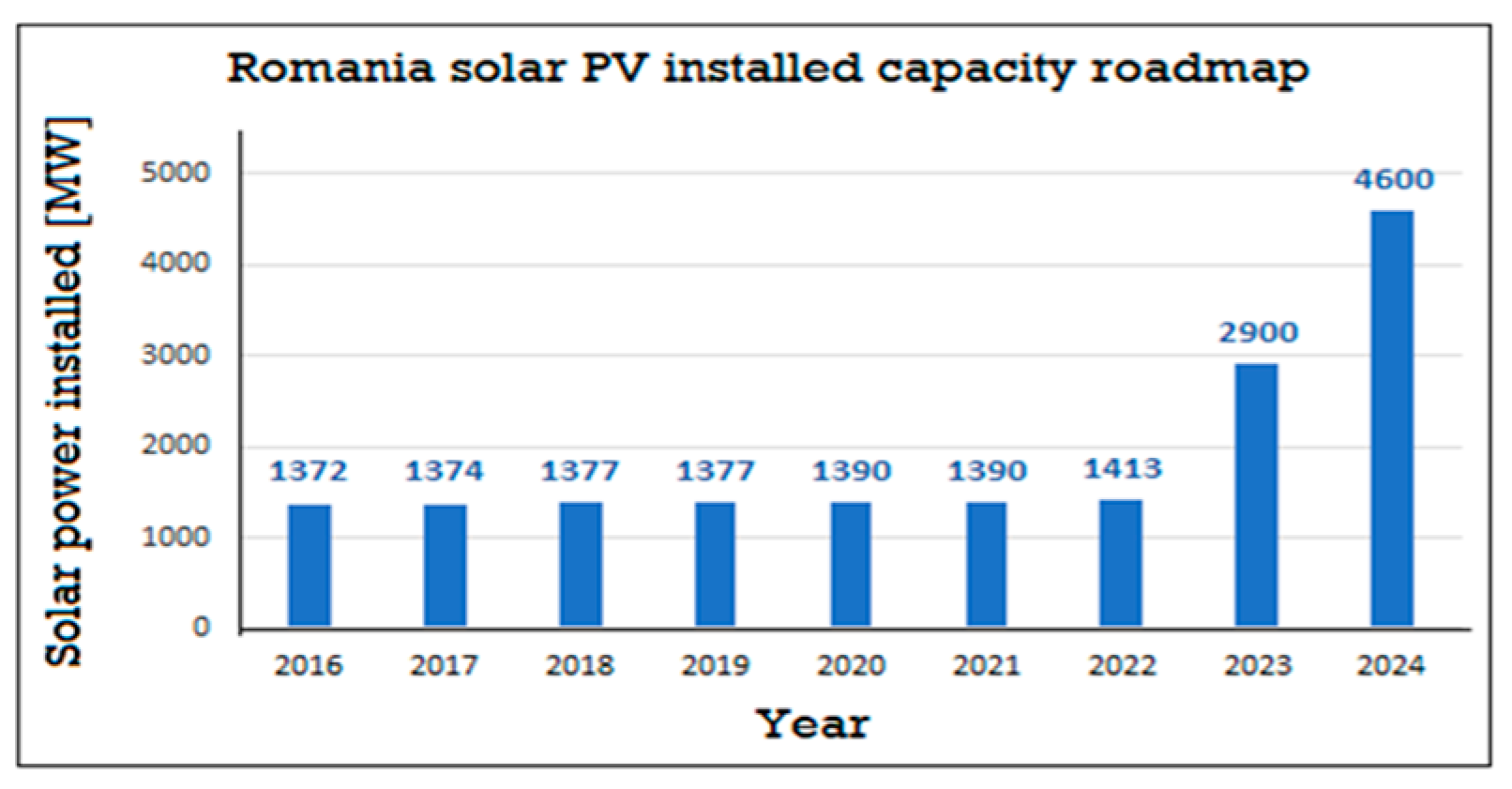
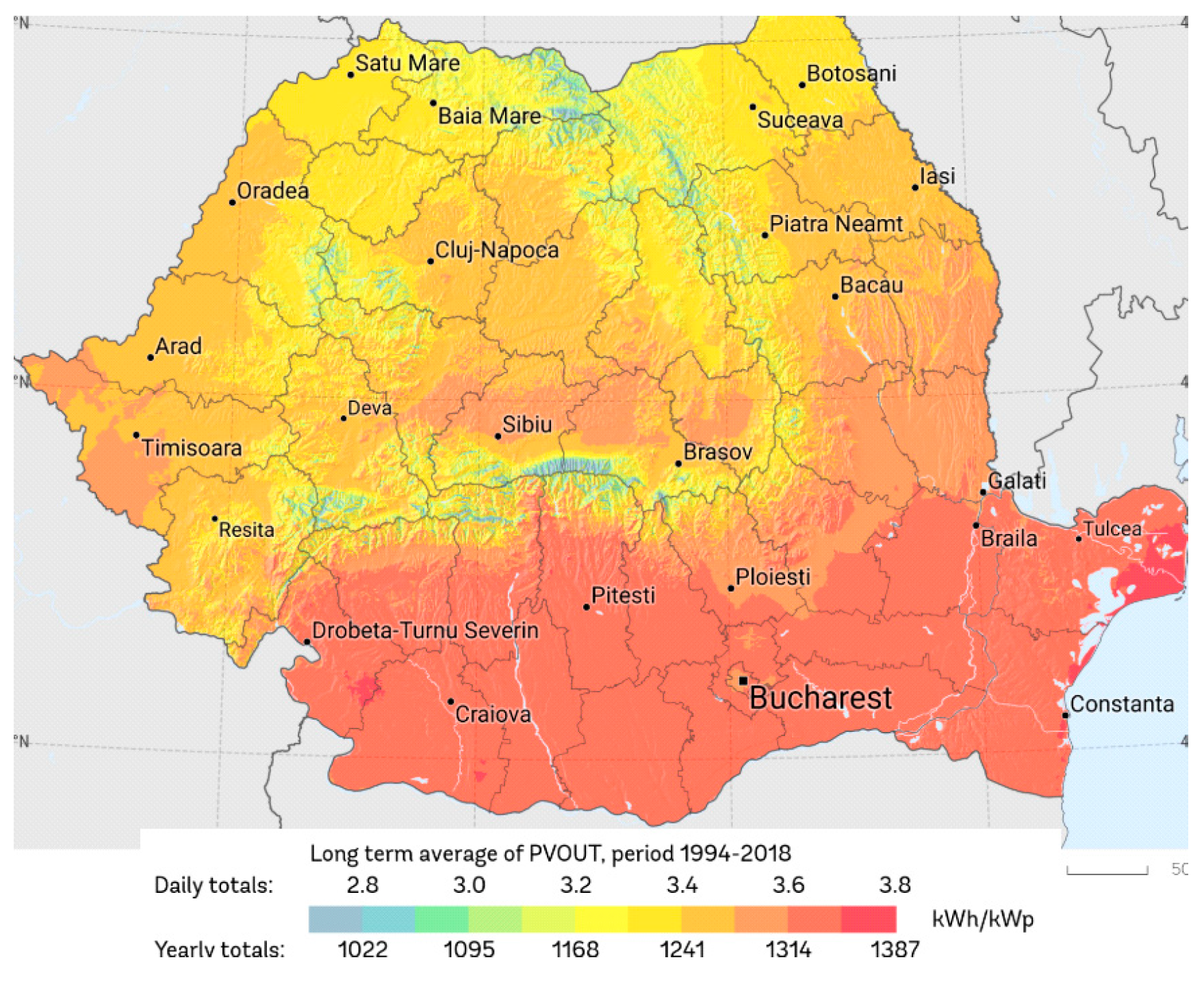
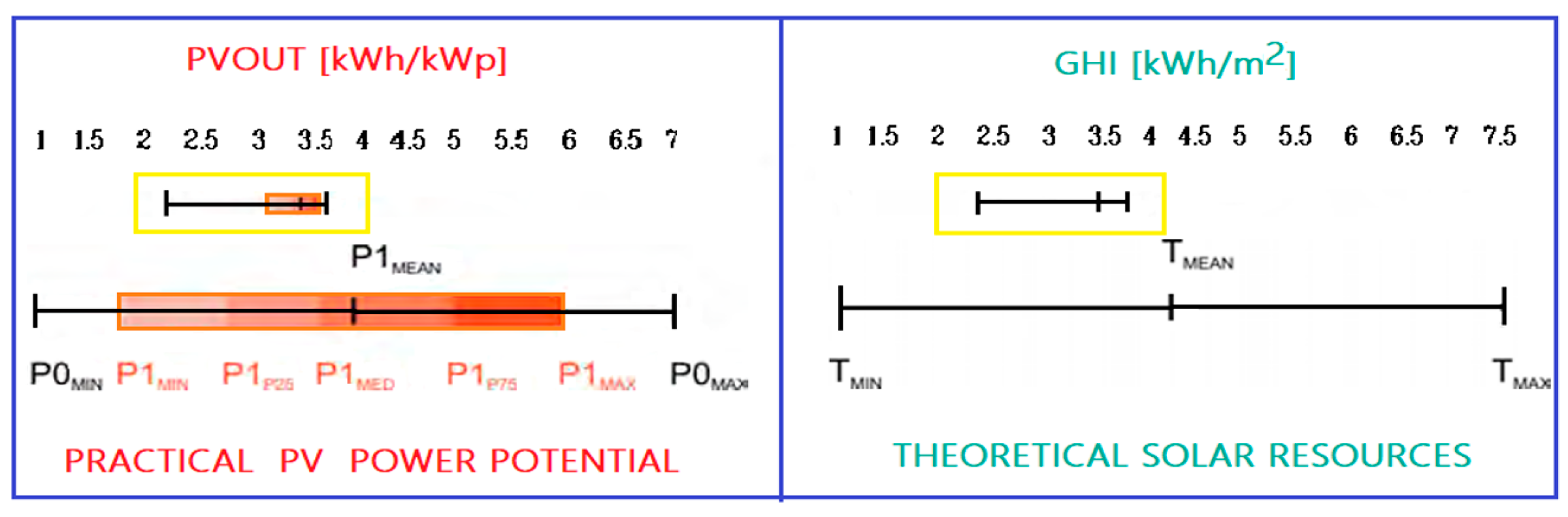

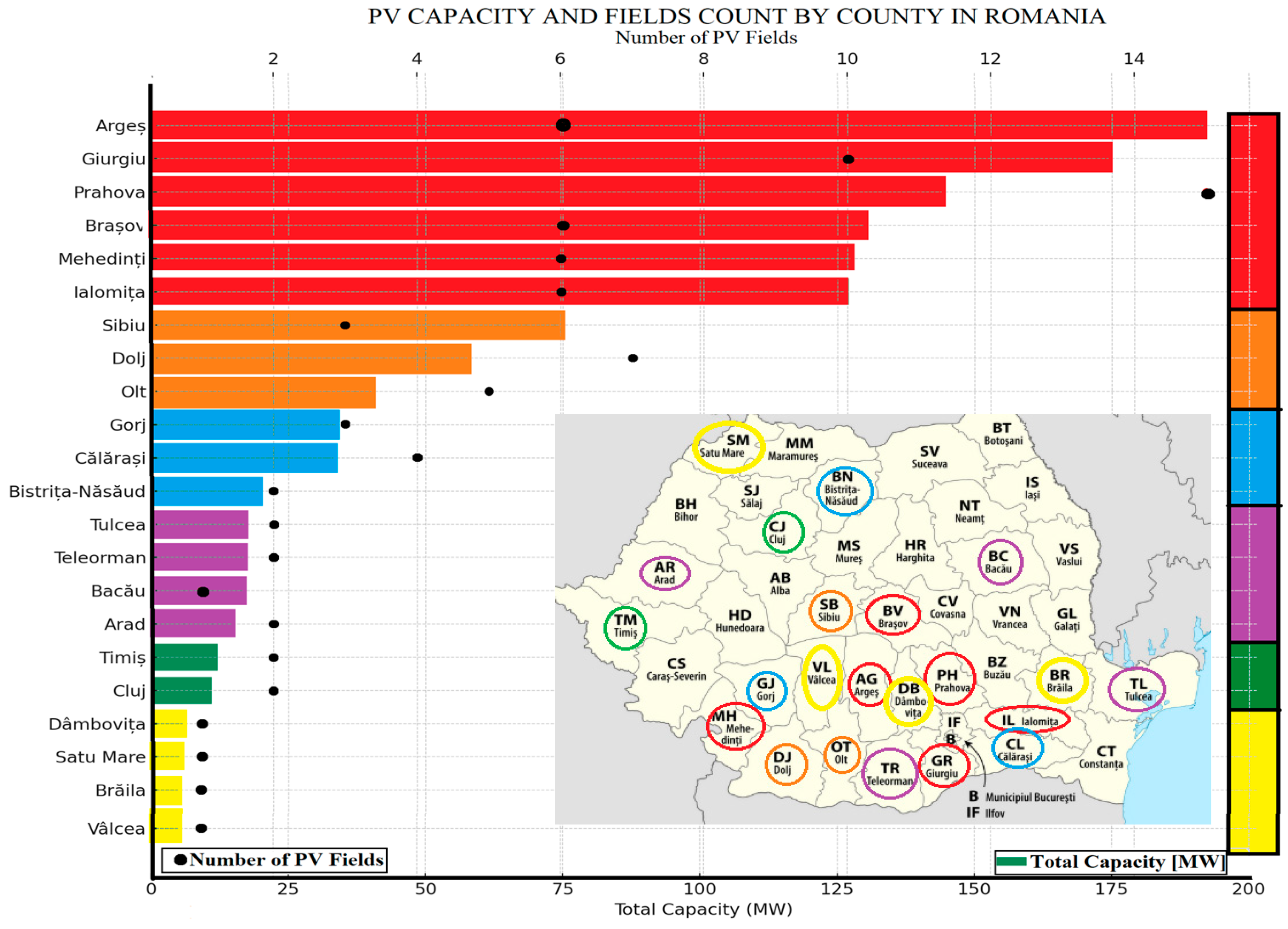





| Category | Power Range | Application | Characteristics | Cost per Watt ($) | Efficiency (%) | ROI (Years) |
|---|---|---|---|---|---|---|
Residential | <10 kW | Installed on rooftops of homes. |
| 2.50 ÷ 3.50 | 15 ÷ 22% | 5 ÷ 10 |
Commercial | <250 kW | Found on business buildings, schools, and shopping centers. |
| 1.50 ÷ 2.50 | 16 ÷ 22% | 4 ÷ 8 |
Industrial | <1000 kW (1 MW) | Used in factories, manufacturing plants, and data centers. |
| 1.20 ÷ 2.00 | 17 ÷ 23% | 3 ÷ 7 |
Utility-Scale | >1000 kW (1 MW+) | Large-scale, ground-mounted solar PV fields. |
| 0.90 ÷ 1.50 | 18 ÷ 24% | 2 ÷ 6 |
| Type of Energy | MW | % |
|---|---|---|
| Hydro | 6687.78 | 34.9810 |
| Wind | 3095.31 | 16.1903 |
| Coal | 2762.2 | 14.4479 |
| Hydrocarbons | 2713.78 | 14.1946 |
| Solar | 2307.35 | 12.0688 |
| Nuclear | 1413 | 7.3908 |
| Biomass | 106.27 | 0.5559 |
| Biogas | 22.46 | 0.1175 |
| Waste | 6.03 | 0.0315 |
| Residual Heat | 4.1 | 0.0214 |
| Geothermal | 0.05 | 0.0003 |
| County | Location (Commune) in Romania | Capacity [MW] |
|---|---|---|
| Dolj | Piscu Sadovei | 1500.00 |
| Dolj | near Calafat | 1050.00 |
| Arad | Pilu și Grăniceri | 1044.00 |
| (Grasshopper Romania Solar PV Field) | 1000.00 | |
| Teleorman | Băbăita | 710.00 |
| Level/ Associated Score | Definition of Probability | Periods | |
|---|---|---|---|
| 1. Very low | There is a very low probability of occurrence. Normal measures are required to monitor the evolution of the event. | over 13 years | |
| 2. Low | The event has a low probability of occurrence. Efforts are being made to reduce the probability and/or mitigate the impact. | 10 ÷ 12 years | |
| X | 3. Medium | The event has a significant probability of occurrence. Significant efforts are required to reduce the probability and/or mitigate the impact. | 7 ÷ 9 years |
| 4. High | The event has a probability of occurrence. Priority efforts are required to reduce the probability and mitigate the impact produced. | 4 ÷ 6 years | |
| 5. Very high | The event is considered imminent. Immediate and extreme measures are required to protect the objective, with evacuation to a safe location if the impact requires it. | 1 ÷ 3 years | |
| Risk Scenario: Blackout Risks | Level |
|---|---|
| Very low |
| Low | |
| Medium | |
| High | |
| Very high | |
| Very low |
| Low | |
| Medium | |
| High | |
| Very high | |
| Very low |
| Low | |
| Medium | |
| High | |
| Very high |
| Impacts | Level | Severity |
|---|---|---|
| Enormous damage caused by lack of electricity: lack of electricity in case of loss of this facility generated by photovoltaic fields | 1. Very low | Temporary |
| 2. Low | Significant damage | |
| 3. Medium | Average damage | |
| 4. High | High damage | |
| 5. Very high | Very heavy damage | |
| Enormous damage generated by the interdependence of other systems: it represents the volume of capital invested to carry out the photovoltaic field—critical infrastructure with other national public systems, such as: health, transport, industry, economy, etc. | 1. Very low | 0–10% of VIC |
| 2. Low | 11–20% of VIC | |
| 3. Medium | 21–30% of VIC | |
| 4. High | 31–40% of VIC | |
| 5. Very high | Over 41% of VIC | |
| Potential environmental damage: it represents environmental damage or losses resulting from the loss of this facility generated by photovoltaic fields, caused by fires, storms, flood, snow, etc. | 1. Very low | 0–20% |
| 2. Low | 21–40% | |
| 3. Medium | 41–60% | |
| 4. High | 61–80% | |
| 5. Very high | Over 81% | |
| High social impacts: it represents the loss of confidence of the population over photovoltaic fields as critical infrastructure | 1. Very low | 0–10% of PC |
| 2. Low | 11–20% of PC | |
| 3. Medium | 21–30% of PC | |
| 4. High | 31–40% of PC | |
| 5. Very high | Over 41% of PC |
| Level/Score | The Severity of the Consequences | |
|---|---|---|
| 1. Very low | The event causes a minor disruption to the activity, without material damage. | |
| 2. Low | The event causes minor property damage and limited disruption to business. | |
| 3. Medium | Injuries to personnel, and/or some loss of equipment, utilities, and delays in service provision. | |
| 4. High | Serious injuries to personnel, significant loss of equipment, facilities, and delays and/or interruption of service provision. | |
| X | 5. Very high | The consequences are catastrophic, resulting in fatalities and serious injuries to personnel, a major loss of equipment, facilities, and services, and interruption of service provision. |
| PR O B A B I L I T Y | Very high 5 | |||||
| High 4 | ||||||
| Medium 3 | Risk scenario | |||||
| Low 2 | ||||||
| Very low 1 | ||||||
| 0 | Very low 1 | Low 2 | Medium 3 | High 4 | Very high 5 | |
| Severity/Consequences | ||||||
| The calculated risk has the value 15 (probability 5 × severity 3). Therefore, there is a high risk of the event occurring. | Calculated Risk Level | |
| Level | Score | |
| Very low | 1–3 | |
| Low | 4–6 | |
| Medium | 7–12 | |
| High | 13–16 | |
| Very high | 17–25 | |
| Types of Risk | Proposed Measures |
|---|---|
|
|
|
|
|
|
| Risks | Identified | Results After Measurement Implementation |
|---|---|---|
| 1. Very low | 1. Very low |
| 2. Low | 2. Low | |
| 3. Medium | 3. Medium | |
| 4. High | 4. High | |
| 5. Very high | 5. Very high | |
| 1. Very low | 1. Very low |
| 2. Low | 2. Low | |
| 3. Medium | 3. Medium | |
| 4. High | 4. High | |
| 5. Very high | 5. Very high | |
| 1. Very low | 1. Very low |
| 2. Low | 2. Low | |
| 3. Medium | 3. Medium | |
| 4. High | 4. High | |
| 5. Very high | 5. Very high |
| Level/Score | The Severity of the Consequences | |
|---|---|---|
| 1. Very low | The event causes a minor disruption to the activity, without material damage. | |
| 2. Low | The event causes minor property damage and limited disruption to business. | |
| X | 3. Medium | Injuries to personnel and/or some loss of equipment, utilities, and delays in service provision. |
| 4. High | Serious injuries to personnel, significant loss of equipment, facilities, and delays and/or interruption of service provision. | |
| 5. Very high | The consequences are catastrophic resulting in fatalities and serious injuries to personnel, a major loss of equipment, facilities, and services, and interruption of service provision. | |
| P R O B A B I L I T Y | Very high 5 | |||||
| High 4 | ||||||
| Medium 3 | Risk scenario | |||||
| Low 2 | ||||||
| Very low 1 | ||||||
| 0 | Very low 1 | Low 2 | Medium 3 | High 4 | Very high 5 | |
| Severity/Consequences | ||||||
| The calculated risk has the value 9 (probability 3 × severity 3). Therefore, there is a medium risk of the event occurring according to the scenario analyzed. | Calculated Risk Level | |
| Level | Level | |
| Very low | Very low | |
| Low | Low | |
| Medium | Medium | |
| High | High | |
| Very high | Very high | |
| Score | Range | Severity | |
|---|---|---|---|
| From | To | ||
| None | 0 | 0 | |
| Low | 0.1 | 3.9 | |
| Medium | 4.0 | 6.9 | |
| High | 7.0 | 8.9 | |
| Critical | 9.0 | 10 | |
| Year | CWE | Explanation | CVE | Base Score | CVSS Severity |
|---|---|---|---|---|---|
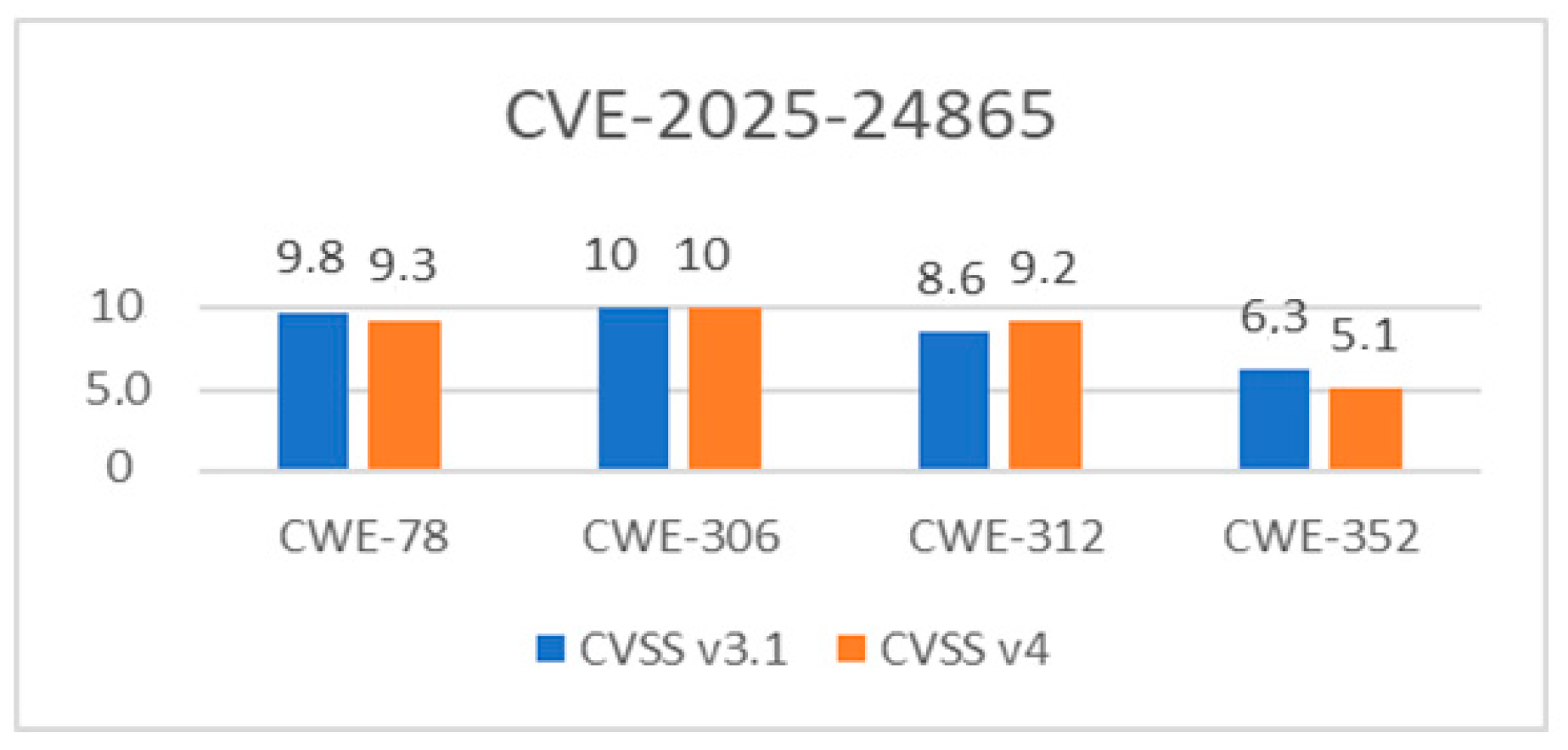
| 2025 | 306 | MACF | CVE-2025-24865 | 10 | critical |
| 312 | CSSI | ||||
| 352 | CSRF | ||||
| 78 | Improper neutralization of special elements used in an OS command (OSCI) | ||||
| 2022 | 603 | Use of client-side authentication | CVE-2022-33139 | 9.8 | critical |
| 287 | Improper authentication—SCADA system only uses client-side authentication, allowing adversaries to impersonate other users | ||||
| 2019 | 521 | Weak password requirements | CVE-2019-7676 | 7.2 | high |
| 79 | Improper neutralization of input during web page generation (‘cross-site scripting’ XSS) | CVE-2019-7677 | 6.1 | medium | |
| 22 | Improper limitation of a pathname to a restricted directory (‘path traversal’) | CVE-2019-7678 | 9.8 | critical | |
| CVE-2019-19229 | 6.5 | medium | |||
| 312 | CSSI | CVE-2019-19228 | 9.8 | critical | |
| 2018 | 200 | Exposure of sensitive information to an unauthorized actor | CVE-2018-12735 | 7.5 | high |
| CVE-2018-12927 | 7.5 | high | |||
| 2017 | noinfo | Insufficient information | CVE-2017-9851 | 7.5 | high |
| CVE-2017-9864 | 7.5 | high | |||
| 798 | Use of hardcoded credentials | CVE-2017-9852 | 9.8 | critical | |
| 521 | Weak password requirements—allows brute-force attacks on the password | CVE-2017-9853 | 9.8 | critical | |
| 311 | Missing encryption of sensitive data—lack of encryption compromises CIA | CVE-2017-9854 | 9.8 | critical | |
| 311 | Incorrect authorization | CVE-2017-9855 | 9.8 | critical | |
| 256 | Plaintext storage of a password—storing a password in plaintext may result in a system compromise | CVE-2017-9856 | 3.4 | low | |
| 287 | Improper authentication | CVE-2017-9857 | 8.1 | high | |
| CVE-2017-9860 | 9.8 | critical | |||
| 200 | Exposure of sensitive information to an unauthorized actor | CVE-2017-9858 | 7.5 | high | |
| CVE-2017-9862 | 7.5 | high | |||
| 327 | Use of a broken or risky cryptographic algorithm | CVE-2017-9859 | 9.8 | critical | |
| 74 | Improper neutralization of special elements in output used by a downstream component (‘injection’) | CVE-2017-9861 | 9.8 | critical | |
| 352 | CSRF | CVE-2017-9863 | 8.8 | high | |
| 2012 | 89 | Improper neutralization of special elements used in an SQL command | CVE-2012-5861 | 7.5 | high |
| 310 | Cryptographic issues | CVE-2012-5862 | - | high | |
| 264 | Permissions, privileges, and access control | CVE-2012-5863 | - | high |
| Control Area | Control Requirement | Standard Reference | Current Implementation Status | Gap Description | Risk Level | Recommended Action |
|---|---|---|---|---|---|---|
| Access Control (AC) | Implement MFA for remote access | ISO 27001 A.9.4.2/NIST PR.AC-7 | Not implemented | Remote access protected only by username/password | High | Implement MFA using tokens or authenticator apps |
| Asset Management(AM) | Maintain an up-to-date asset inventory | ISO 27001 A.8.1.1/NIST ID.AM-1 | Partially imple- mented | No centralized inventory of PV components | Medium | Deploy asset management system and conduct full inventory |
| Incident Response (IR) | Establish an incident response plan (IRP) and test it regularly | ISO 27001 A.16.1.1/NIST RS.RP-1 | Not implemented | No formal plan for responding to cyber incidents | High | Develop and regularly test an IRP |
| Step | Description | Explanation/Methods |
|---|---|---|
| Framing the Risk | Defining threats that give rise to overall risk | Threats may arise due to
|
| Assessing the Risk | Consider the severity of each threat identified | Quantitative assessment (e.g., financial loss) and/or qualitative assessment (e.g., impact on operations). |
| Responding to the Risk | Reduce exposure to the risks | Each risk needs to be eliminated, decreased, transferred, or accepted based on its assessed impact and available resources. |
| Planning for Incident Response | Developing and keeping incident response plans, defining roles, responsibilities, and procedures in clear terms | Conducting simulations and drills optimizes organizational preparedness. |
| Risk Monitoring | Risk management is continuous | Risks must still be monitored, and any remaining (accepted) risk should be monitored carefully to ensure that it remains acceptable. |
| Risk Type | Likelihood | Impact | Risk Level |
|---|---|---|---|
| Unauthorized remote access | High | Critical | High |
| Malware/ransomware attack | High | High | Critical |
| Physical theft or vandalism | Medium | High | High |
| Weather-related damage | Medium | Medium | Medium |
| Regulatory non-compliance | Low | High | Medium |
| Risk Category | Key Risks | Mitigation Policies |
|---|---|---|
| Natural Risk Factors |
|
|
| Technical Risks |
|
|
| Human Risk Factors |
|
|
| Cybersecurity Risks |
|
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Riurean, S.; Fîță, N.-D.; Păsculescu, D.; Slușariuc, R. Securing Photovoltaic Systems as Critical Infrastructure: A Multi-Layered Assessment of Risk, Safety, and Cybersecurity. Sustainability 2025, 17, 4397. https://doi.org/10.3390/su17104397
Riurean S, Fîță N-D, Păsculescu D, Slușariuc R. Securing Photovoltaic Systems as Critical Infrastructure: A Multi-Layered Assessment of Risk, Safety, and Cybersecurity. Sustainability. 2025; 17(10):4397. https://doi.org/10.3390/su17104397
Chicago/Turabian StyleRiurean, Simona, Nicolae-Daniel Fîță, Dragoș Păsculescu, and Răzvan Slușariuc. 2025. "Securing Photovoltaic Systems as Critical Infrastructure: A Multi-Layered Assessment of Risk, Safety, and Cybersecurity" Sustainability 17, no. 10: 4397. https://doi.org/10.3390/su17104397
APA StyleRiurean, S., Fîță, N.-D., Păsculescu, D., & Slușariuc, R. (2025). Securing Photovoltaic Systems as Critical Infrastructure: A Multi-Layered Assessment of Risk, Safety, and Cybersecurity. Sustainability, 17(10), 4397. https://doi.org/10.3390/su17104397








