Green Requirement Engineering: Towards Sustainable Mobile Application Development and Internet of Things
Abstract
1. Introduction
2. Background
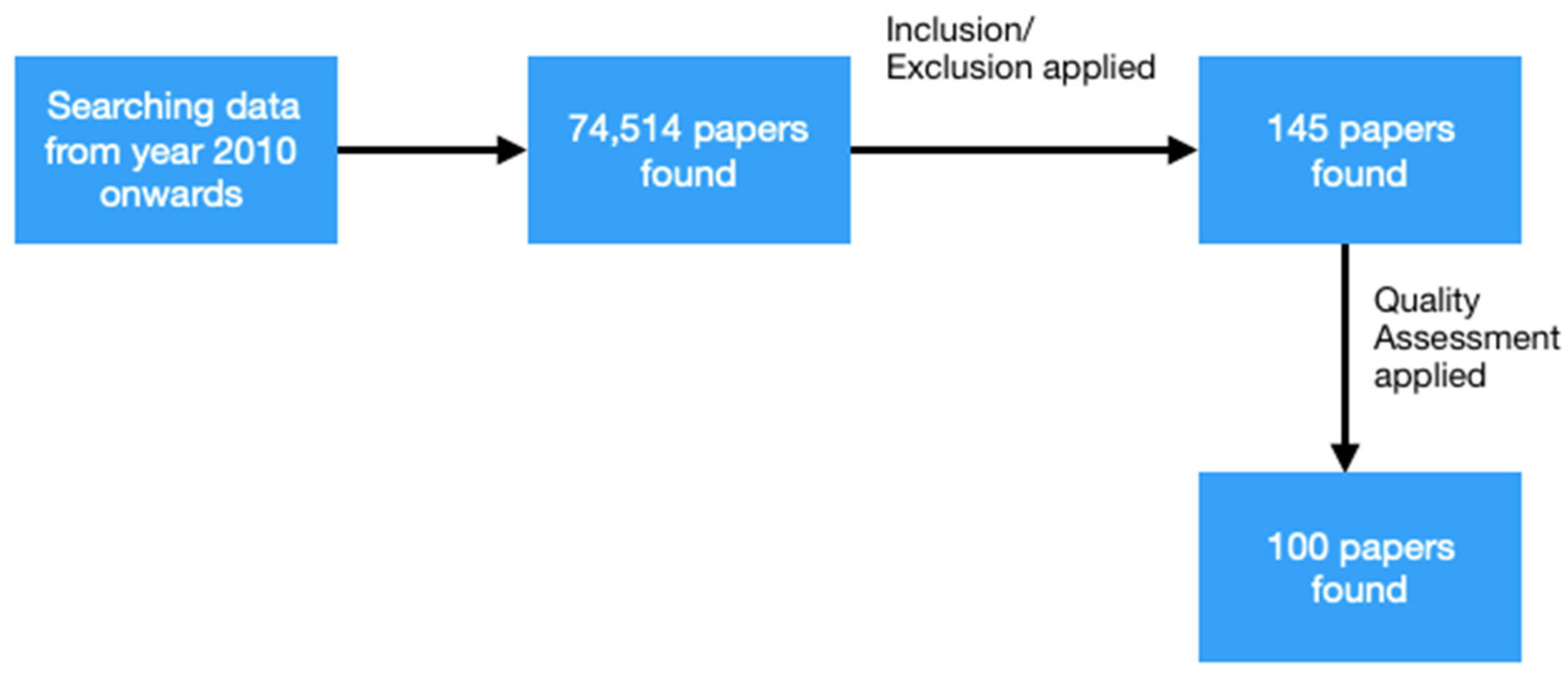
3. Research Methodology
3.1. Resources, Keywords, and Search Strings
3.2. Inclusion/Exclusion Criteria
4. Results and Discussions
4.1. Communication
4.1.1. Anonymous Communication
4.1.2. Lack of Requirement Effective Articulation
4.1.3. Lack of Verbal and Presentation Skills
4.1.4. Lack of Communication Participation
4.1.5. Low Bandwidth
4.1.6. Unavailability of Services for Network Connection
4.1.7. Heterogeneity in Terms of Involvement of Different Networks
4.1.8. Frequent Server Disconnections
4.1.9. Problems in Accessing Server Data
4.1.10. Data Communication Overheads
4.2. Requirement
4.2.1. Incomplete Requirement Gathering
4.2.2. Lack of Accurate Requirement Prioritization
4.2.3. Unstable Requirements
4.2.4. Change of User Needs and Understanding
4.2.5. Requirement Over-Scoping
4.2.6. Lack of Guideline Compliance
4.2.7. Inefficient Requirement Completion Time
4.2.8. Minimization of a Service Latency Problem
4.2.9. The Optimal Revenue Maximization Problem
4.2.10. Absence of High Quality-Of-Service Requirement for Computational Service Offloading
4.2.11. Inefficient Provisioning and Delivery of Mobile Application
4.2.12. Lack of Consideration of User and Applications Requirements for Offloading Decision Making
4.2.13. Incorrect Requirement Partitioning
4.2.14. Lack of Extraction of Useful Information
4.2.15. Inefficiency in Constructing Power Models
4.2.16. Issues in Terms of Energy Savings (Static Environment)
4.2.17. Complexity in Graphical User Interface (GUI) Testing
4.2.18. Lack of Appropriate Battery Life
4.2.19. Complexity in Evaluating Applications’ Performances
4.2.20. Time Consumption of Mobile Devices
4.2.21. Energy Consumption of Mobile Devices
4.2.22. Changing the Orientation of the Application
4.2.23. Inefficient Web Browsing on Mobile Systems
4.2.24. Problem with Touch Gesture and Embedded Sensor-Based Interfaces
4.2.25. Incorrect Requirements Identification
4.2.26. Diversity of Mobile Surroundings
4.2.27. Complexity in Bundling of HTTP Requests
4.2.28. Depletion of Battery Power
4.2.29. Event-Driven Structure
4.2.30. Complex Contextual Features
4.2.31. High Power Consumption of Smartphones
4.2.32. Surface Over-Heating of Smartphones
4.2.33. Impact of Delay on UX
4.2.34. Impact of Network on the Performance of Mobile Devices
4.2.35. Environmental Factors’ Impact on the Biometric Authentication Method
4.2.36. Lack of Power Requirement for Battery of Mobile Devices
4.2.37. Frequent Changing Requirements
4.2.38. Lack of Quality Assurance
4.2.39. Inadequate Applications Performance
4.3. Resources
4.3.1. Lack of Appropriate Resource Allocation
4.3.2. Platform Incompatibility
4.3.3. Service Selection Problem
4.3.4. DVFS-Control Problem
4.3.5. Lack of Resource Optimization
4.3.6. Energy Inefficiency
4.3.7. Inaccurate Task Scheduling
4.3.8. Limited Resources/Resources Lacking
4.3.9. VM-Migration Problem
4.3.10. Higher Resource Utilization by Mobile Cross-Platform Development Approaches
4.3.11. Lacking/Limited Computational Resources
4.3.12. Incorrect Estimation of Battery Life
4.3.13. Inaccurate Quantification Regarding Energy Consumption by the Application
4.3.14. Compatibility across Various Operating Systems
4.4. Security and Privacy
4.4.1. Lack of Asynchrony Retrofitting
4.4.2. Malware Detection Problem
4.4.3. Timing Attacks
4.4.4. Data Tampering While Offloading
4.4.5. Limitation of Profilers
4.4.6. CO in Terms of Network Connection Status and Bandwidth
4.4.7. Security w.r.t. Mobile Users
4.4.8. Data Security on the Cloud
4.4.9. Side-Glance Attack
4.4.10. Lack of Identification of Risky Actions and Vulnerabilities
4.4.11. OTP-Vulnerability
4.4.12. Inconsistent and Inefficient Testing
4.4.13. Lack of Configuration of Mobile Hybrid Applications
4.4.14. Unclear Requirements for Application Functionality toward Privacy Threats
4.4.15. Patching for Updating, Correction, or Improvement
4.4.16. Data Reconstruction Attack
4.4.17. Data Erasure
4.5. Stakeholders
4.5.1. Unawareness of Needs
4.5.2. Cultural and Language Barrier
4.5.3. Lack of Domain Knowledge
4.5.4. Ambiguities among Stakeholders
4.5.5. Intragroup Conflicts
4.5.6. Inefficient Response Time
4.5.7. Lack of Requirement Task Efficiency and Responsiveness
4.5.8. Lack of Development Standards and Practices Knowledge
4.5.9. Testing Issues for Practitioners
4.5.10. Ignorance of Usability
4.5.11. Impact of Screen Size on Usability
4.5.12. Poor User Experience
5. Threats to Validity
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Lin, Y. 10 Twitter Statistics Every Marketer Should Know in 2021. 2021. Available online: https://www.oberlo.com/blog/twitter-statistics (accessed on 13 January 2020).
- Costi. No Best Solutions to Top Mobile App Development Challenges. 2017. Available online: https://blog.intelligentbee.com/2017/09/04/best-solutions-top-mobile-app-development-challenges/ (accessed on 15 January 2020).
- Dar, H.; Lali, M.I.; Ashraf, H.; Ramzan, M.; Amjad, T.; Shahzad, B. A systematic study on software requirements elicitation techniques and its challenges in mobile application development. IEEE Access 2018, 6, 63859–63867. [Google Scholar] [CrossRef]
- Zanutto, D.; Lorenzini, E.C.; Mantellato, R.; Colombatti, G.; Sanchez-Torres, A. Software Engineering Issues for Mobile Application Development. In Proceedings of the International Astronautical Congress IAC, Naples, Italy, 1–5 October 2012; Volume 4, pp. 2577–2585. [Google Scholar]
- Liu, Z.; Gao, X.; Long, X. Adaptive random testing of mobile application. In Proceedings of the ICCET 2010 International Conference on Computers Engineering and Technology, Chengdu, China, 16–19 April 2010; Volume 2. [Google Scholar] [CrossRef]
- UsmanMalik, M.; Chaudhry, N.M.; Shahzad Malik, K. Evaluation of Efficient Requirement Engineering Techniques in Agile Software Development. Int. J. Comput. Appl. 2013, 83, 24–29. [Google Scholar] [CrossRef]
- Mandler, M. Coarse, Efficient Decision Making. J. Eur. Econ. Assoc. 2020, 18, 3006–3044. [Google Scholar] [CrossRef]
- Souza, V.E.S. Requirements-Based Software System Adaptation. Ph.D. Thesis, University of Trento, Trento, Italy, 2012. [Google Scholar]
- Soujanya, R.; Rupa, B. Test Cases and Testing Strategies for Mobile Apps—A Survey. Int. Res. J. Eng. Technol. 2017, 4, 3024–3027. [Google Scholar]
- Codemotion. Mobile or Web Development: Which Is the Best Career Path. 2022. Available online: https://www.codemotion.com/magazine/soft-skills/it-careers/mobile-or-web-development-which-is-the-best-career-path-to-choose-in-2022/ (accessed on 11 September 2022).
- Employees, G. How Hard Is Mobile App Development Compared to Web Development? 2021. Available online: https://medium.com/@globalemployees116/how-hard-is-mobile-app-development-compared-to-web-development-eae8def75247 (accessed on 1 January 2022).
- Nyakundi, H. What Is the Difference between a Website and a Web Application? 2021. Available online: https://www.freecodecamp.org/news/difference-between-a-website-and-a-web-application/ (accessed on 20 February 2022).
- Top 4 Mobile App Development Challenges and Solutions. 2020. Available online: https://www.nixsolutions.com/blog/top-4-mobile-app-development-challenges-solutions/ (accessed on 11 January 2022).
- Tuban, A. 7 Proven Steps of the Mobile App Development Lifecycle. 2020. Available online: https://technologyrivers.com/blog/mobile-app-development-lifecycle/ (accessed on 20 February 2022).
- Busch, Z. 6 Stages of the Mobile Development Lifecycle. 2019. Available online: https://learn.g2.com/mobile-development-lifecycle (accessed on 15 January 2021).
- Olson, S. 8 Steps to Understanding the Mobile App Development Lifecycle—BuildFire. Build Fire, 2016. Available online: https://buildfire.com/understanding-mobile-app-development-lifecycle/ (accessed on 24 September 2021).
- Shakarami, A.; Shahidinejad, A.; Ghobaei-Arani, M. A review on the computation offloading approaches in mobile edge computing: A game-theoretic perspective. Softw. Pract. Exp. 2020, 50, 1719–1759. [Google Scholar] [CrossRef]
- Shahidinejad, A.; Ghobaei-Arani, M. Joint computation offloading and resource provisioning for edge-cloud computing environment: A machine learning-based approach. Softw. Pract. Exp. 2020, 50, 2212–2230. [Google Scholar] [CrossRef]
- Usman, M.; Iqbal, M.Z.; Khan, M.U. An automated model-based approach for unit-level performance test generation of mobile applications. J. Softw. Evol. Process 2020, 32, e2215. [Google Scholar] [CrossRef]
- Nirumand, A.; Zamani, B.; Ladani, B.T. VAnDroid: A framework for vulnerability analysis of Android applications using a model-driven reverse engineering technique. Softw. Pract. Exp. 2019, 49, 70–99. [Google Scholar] [CrossRef]
- Cruz, L.; Abreu, R. EMaaS: Energy measurements as a service for mobile applications. In Proceedings of the 2019 IEEE/ACM 41st International Conference on Software Engineering: New Ideas and Emergind Results, ICSE-NIER, Montreal, QC, Canada, 29–31 May 2019; Volume 2019, pp. 101–104. [Google Scholar] [CrossRef]
- Kobayashi, R.; Adachi, K. Radio and Computing Resource Allocation for Minimizing Total Processing Completion Time in Mobile Edge Computing. IEEE Access 2019, 7, 141119–141132. [Google Scholar] [CrossRef]
- Wang, X.; Continella, A.; Yang, Y.; He, Y.; Zhu, S. LeakDoctor: Toward Automatically Diagnosing Privacy Leaks in Mobile Applications. In Proceedings of the ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies; Association for Computing Machinery: New York, NY, USA, 2019; Volume 3, pp. 1–25. [Google Scholar]
- Wang, X.; Qin, X.; Hosseini, M.B.; Slavin, R.; Breaux, T.D.; Niu, J. GUILeak: Tracing privacy policy claims on user input data for Android applications. In Proceedings of the 40th International Conference on Software Engineering (ICSE ’18), Gothenburg, Sweden, 27 May–3 June 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 37–47. [Google Scholar] [CrossRef]
- Amalfitano, D.; Riccio, V.; Paiva, A.C.R.; Fasolino, A.R. Why does the orientation change mess up my Android application? From GUI failures to code faults. Softw. Test. Verif. Reliab. 2018, 28, e1654. [Google Scholar] [CrossRef]
- Zhang, W.L.; Guo, B.; Shen, Y.; Li, D.G.; Li, J.K. An energy-efficient algorithm for multi-site application partitioning in MCC. Sustain. Comput. Inform. Syst. 2018, 18, 45–53. [Google Scholar] [CrossRef]
- AlJarrah, A.; Shehab, M. Cordovaconfig: A tool for mobile hybrid apps’ configuration. In ACM International Conference Proceeding Series; Association for Computing Machinery: New York, NY, USA, 2018; pp. 161–170. [Google Scholar] [CrossRef]
- Shu, J.; Zhang, Y.; Li, J.; Li, B.; Gu, D. Why data deletion fails? A study on deletion flaws and data remanence in android systems. ACM Trans. Embed. Comput. Syst. 2017, 16, 1–22. [Google Scholar] [CrossRef]
- Lin, Y.; Okur, S.; Dig, D. Study and refactoring of android asynchronous programming. In Proceedings of the 2015 30th IEEE/ACM International Conference on Automated Software Engineering ASE, Lincoln, NE, USA, 9–13 November 2015; Volume 2016, pp. 224–235. [Google Scholar] [CrossRef]
- Zein, S.; Salleh, N.; Grundy, J. A systematic mapping study of mobile application testing techniques. J. Syst. Softw. 2016, 117, 334–356. [Google Scholar] [CrossRef]
- Keele, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering. Technical Report, EBSE Technical Report EBSE-2007-01. Available online: https://www.elsevier.com/__data/promis_misc/525444systematicreviewsguide.pdf (accessed on 25 January 2023).
- Charmaz, K. Grounded theory: Methodology and theory. In International Encyclopedia of the Social & Behavioral Sciences; SAGE Publications, Inc.: Thousand Oaks, CA, USA, 2001; pp. 6396–6399. [Google Scholar]
- Vollsteedt, M.; Rezat, S. Compendium for Early Career Researchers in Mathematics Education; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar] [CrossRef]
- Ayyub, B. A Practical Guide on Conducting Expert-Opinion Elicitation of Probabilities and Consequences for Corps Facilities; Institute for Water Resources: Alexandria, VA, USA, 2001. [Google Scholar]
- Zhou, Y.; Zhang, H.; Huang, X.; Yang, S.; Babar, M.A.; Tang, H. Quality assessment of systematic reviews in software engineering: A tertiary study. In Proceedings of the EASE ’15: Proceedings of the 19th International Conference on Evaluation and Assessment in Software Engineering, Nanjing, China, 27–29 April 2015; pp. 1–14. [CrossRef]
- Sakai, K.; Sun, M.T.; Ku, W.S.; Wu, J. A framework for anonymous routing in delay tolerant networks. In Proceedings of the International Conference on Network Protocols ICNP, Toronto, ON, Canada, 10–13 October 2017; Volume 2017. [Google Scholar] [CrossRef]
- Dinh, H.T.; Lee, C.; Niyato, D.; Wang, P. A survey of mobile cloud computing: Architecture, applications, and approaches. Wirel. Commun. Mob. Comput. 2013, 13, 1587–1611. [Google Scholar] [CrossRef]
- Darwish, S.M.; El-Zoghabi, A.; El-Shnawy, A.G. Proactive cache replacement technique for mobile networks based on genetic programming. IET Netw. 2018, 7, 376–383. [Google Scholar] [CrossRef]
- Dutta, K.; Vandermeer, D. Caching to reduce mobile app energy consumption. ACM Trans. Web 2017, 12, 1–30. [Google Scholar] [CrossRef]
- Tien, C.W.; Huang, T.Y.; Huang, T.C.; Chung, W.H.; Kuo, S.Y. MAS: Mobile-Apps Assessment and Analysis System. In Proceedings of the 47th Annual IEEE/IFP International Conference Dependable Systems and Networks Workshop DSN-W, Denver, CO, USA, 26–29 June 2017; Volume 2017, pp. 145–148. [Google Scholar] [CrossRef]
- Samanta, A.; Chang, Z. Adaptive service offloading for revenue maximization in mobile edge computing with delay-constraint. IEEE Internet Things J. 2019, 6, 3864–3872. [Google Scholar] [CrossRef]
- Kumar, J.; Malik, A.; Dhurandher, S.K.; Nicopolitidis, P. Demand-Based Computation Offloading Framework for Mobile Devices. IEEE Syst. J. 2018, 12, 3693–3702. [Google Scholar] [CrossRef]
- Junior, W.; Oliveira, E.; Santos, A.; Dias, K. A context-sensitive offloading system using machine-learning classification algorithms for mobile cloud environment. Futur. Gener. Comput. Syst. 2019, 90, 503–520. [Google Scholar] [CrossRef]
- Goudarzi, M.; Zamani, M.; Haghighat, A.T. A fast hybrid multi-site computation offloading for mobile cloud computing. J. Netw. Comput. Appl. 2017, 80, 219–231. [Google Scholar] [CrossRef]
- Antonić, A.; Marjanović, M.; Pripužić, K.; Podnar Žarko, I. A mobile crowd sensing ecosystem enabled by CUPUS: Cloud-based publish/subscribe middleware for the Internet of Things. Futur. Gener. Comput. Syst. 2016, 56, 607–622. [Google Scholar] [CrossRef]
- Nguyen, Q.H.; Dressler, F. A smartphone perspective on computation offloading—A survey. Comput. Commun. 2020, 159, 133–154. [Google Scholar] [CrossRef]
- Yoon, C.; Lee, S.; Choi, Y.; Ha, R.; Cha, H. Accurate power modeling of modern mobile application processors. J. Syst. Archit. 2017, 81, 17–31. [Google Scholar] [CrossRef]
- Folino, G.; Pisani, F.S. Automatic offloading of mobile applications into the cloud by means of genetic programming. Appl. Soft Comput. J. 2014, 25, 253–265. [Google Scholar] [CrossRef]
- Ahmed, E.; Gani, A.; Sookhak, M.; Hamid, S.H.A.; Xia, F. Application optimization in mobile cloud computing: Motivation, taxonomies; open challenges. J. Netw. Comput. Appl. 2015, 52, 52–68. [Google Scholar] [CrossRef]
- Liu, Y.; Lee, M.J. Security-aware resource allocation for mobile cloud computing systems. In Proceedings of the International Conference on Computing and Communication Networks, ICCCN, Las Vegas, NV, USA, 3–6 August 2015; Volume 2015. [Google Scholar] [CrossRef]
- Goudarzi, M.; Zamani, M.; Toroghi Haghighat, A. A genetic-based decision algorithm for multisite computation off loading in mobile cloud computing. Int. J. Commun. Syst. 2017, 30, e3241. [Google Scholar] [CrossRef]
- Ali, A.; Maghawry, H.A.; Badr, N. Automated parallel GUI testing as a service for mobile applications. J. Softw. Evol. Process 2018, 30, e1963. [Google Scholar] [CrossRef]
- Xu, W.; Daneshmand, L. Cuckoo: Flexible compute-intensive task offloading in mobile cloud computing. Wirel. Commun. Mob. Comput. 2016, 2016, 421–433. [Google Scholar] [CrossRef]
- Fernandes, T.S.; Moreira, Á.F.; Cota, É. EPE-Mobile—A framework for early performance estimation of mobile applications. Softw. Pract. Exp. 2018, 48, 85–104. [Google Scholar] [CrossRef]
- Peng, K.; Huang, H.; Pan, W.; Wang, J. Joint optimisation for time consumption and energy consumption of multi-application and load balancing of cloudlets in mobile edge computing. IET Cyber-Phys. Syst. Theory Appl. 2020, 5, 196–206. [Google Scholar] [CrossRef]
- Mittal, S.; Mattela, V. A survey of techniques for improving efficiency of mobile web browsing. Concurr. Comput. Pract. Exp. 2019, 31, e5126. [Google Scholar] [CrossRef]
- Ahmad, R.W.; Kjeldskov, J.; Skov, M.B. A survey on energy estimation and power modeling schemes for smartphone applications. Int. J. Commun. Syst. 2017, 30, e3234. [Google Scholar] [CrossRef]
- Baride, S.; Dutta, K. A cloud based software testing paradigm for mobile applications. ACM SIGSOFT Softw. Eng. Notes 2011, 36, 1–4. [Google Scholar] [CrossRef]
- Lee, S.; Ha, T.; Lim, S.J. Finger gesture input utilizing the rear camera of a mobile phone: A perspective of mobile CAD. Hum. Factors Ergon. Manuf. 2018, 28, 69–80. [Google Scholar] [CrossRef]
- García-López, D.; Segura-Morales, M.; Loza-Aguirre, E. Improving the quality and quantity of functional and non-funtional requirements obtained during requirements elicitation stage for the development of e-commerce mobile applications: An alternative reference process model. IET Softw. 2020, 14, 148–158. [Google Scholar] [CrossRef]
- Zhou, B.; Dastjerdi, A.V.; Calheiros, R.N.; Buyya, R. An online algorithm for task offloading in heterogeneous mobile clouds. ACM Trans. Internet Technol. 2018, 18, 2981. [Google Scholar] [CrossRef]
- Li, D.; Lyu, Y.; Gui, J.; Halfond, W.G.J. Automated energy optimization of HTTP requests for mobile applications. In Proceedings of the International Conference of Software Engineering, Austin, TX, USA, 14–22 May 2016; Volume 14, pp. 249–260. [Google Scholar] [CrossRef]
- Moran, K.; Linares-Vasquez, M.; Bernal-Cardenas, C.; Vendome, C.; Poshyvanyk, D. CrashScope: A practical tool for automated testing of android applications. In Proceedings of the 2017 IEEE/ACM 39th International Conference on Software Engineering Companion ICSE-C, Buenos Aires, Argentina, 20–28 May 2017; Volume 2017, pp. 15–18. [Google Scholar] [CrossRef]
- Dai, Y.; Li, T.; Liu, B.; Song, M.; Chen, H. Exploiting Dynamic Thermal Energy Harvesting for Reusing in smartphone with mobile applications. In Proceedings of the International Conference on Architectural Support for Programming Languages and Operating Systems ASPLOS, Williamsburg, VA, USA, 24–28 March 2018; pp. 243–256. [Google Scholar] [CrossRef]
- Nikzad, N.; Radi, M.; Chipara, O.; Griswold, W.G. Managing the energy-delay tradeoff in mobile applications with tepus. In Proceedings of the 16th Annual Middleware Conference, Vancouver, BC, Canada, 7–11 December 2015; pp. 259–270. [Google Scholar] [CrossRef]
- Silva, B.M.C.; Rodrigues, J.J.P.C.; Kumar, N.; Proença, M.L.; Han, G. MobiCoop: An incentive-based cooperation solution for mobile applications. ACM Trans. Multimed. Comput. Commun. Appl. 2016, 12, 1–23. [Google Scholar] [CrossRef]
- Aras, S.; Gniady, C.; Venugopalan, H. MultiLock: Biometric-based graded authentication for mobile devices. In Proceedings of the ACM International Conference Proceeding Series; Association for Computing Machinery: New York, NY, USA, 2019; pp. 100–109. [Google Scholar] [CrossRef]
- Zhang, X.; Brankovic, S.R.; Chen, J.; Fu, X.I.N. Toward Customized Hybrid Fuel-Cell and Battery-powered. ACM Trans. Embed. Comput. Syst. 2019, 18, 1–20. [Google Scholar] [CrossRef]
- Hecht, G.; Benomar, O.; Rouvoy, R.; Moha, N.; Duchien, L. Tracking the software quality of android applications along their evolution. In Proceedings of the 2015 30th IEEE/ACM International Conference on Automated Software Engineering (ASE), Lincoln, NE, USA, 9–13 November 2015; pp. 236–247. [Google Scholar] [CrossRef]
- Hoque, M.A.; Siekkinen, M.; Khan, K.N.; Xiao, Y.; Tarkoma, S. Modeling, profiling, debugging the energy consumption of mobile devices. ACM Comput. Surv. 2015, 48, 723. [Google Scholar] [CrossRef]
- Holl, K.; Elberzhager, F. Quality assurance of mobile applications: A systematic mapping study. In Proceedings of the MUM ’16: Proceedings of the 15th International Conference on Mobile and Ubiquitous Multimedia, Rovaniemi, Finland, 12–15 December 2016; pp. 101–113. [CrossRef]
- Habchi, S.; Moha, N.; Rouvoy, R. The rise of android code smells: Who is to blame? In Proceedings of the 2019 IEEE/ACM 16th International Conference on Mining Software Repositories (MSR), Montreal, QC, Canada, 25–31 May 2019; pp. 445–456. [Google Scholar] [CrossRef]
- Kaewpuang, R.; Niyato, D.; Wang, P.; Hossain, E. A framework for cooperative resource management in mobile cloud computing. IEEE J. Sel. Areas Commun. 2013, 31, 2685–2700. [Google Scholar] [CrossRef]
- Usman, M.; Iqbal, M.Z.; Khan, M.U. A model-driven approach to generate mobile applications for multiple platforms. In Proceedings of the 2014 21st Asia-Pacific Software Engineering Conference, Jeju, Republic of Korea, 1–4 December 2014; pp. 111–118. [Google Scholar] [CrossRef]
- Gao, Y.; Liu, B. Energy Efficient and Delay Aware Service Selection in Mobile Edge Computing. In Proceedings of the 2020 IEEE 20th International Conference on Communication Technology (ICCT), Nanning, China, 28–31 October 2020; pp. 1546–1550. [Google Scholar] [CrossRef]
- Tian, Z.; Xu, J.; Li, H.; Maeda, R.K.V. Multidevice Collaborative Power Management through Decentralized Knowledge Sharing. IEEE Trans. Very Large Scale Integr. Syst. 2020, 28, 1128–1140. [Google Scholar] [CrossRef]
- Liu, Y.; Lee, M.J.; Zheng, Y. Adaptive Multi-Resource Allocation for Cloudlet-Based Mobile Cloud Computing System. IEEE Trans. Mob. Comput. 2016, 15, 2398–2410. [Google Scholar] [CrossRef]
- Kao, Y.W.; Lin, C.; Yang, K.A.; Yuan, S.-M. A web-based, offline-able, personalized runtime environment for executing applications on mobile devices. Comput. Stand. Interfaces 2012, 34, 212–224. [Google Scholar] [CrossRef]
- Ciman, M.; Gaggi, O. An empirical analysis of energy consumption of cross-platform frameworks for mobile development. Pervasive Mob. Comput. 2017, 39, 214–230. [Google Scholar] [CrossRef]
- Dorfer, T.; Demetz, L.; Huber, S. Impact of mobile cross-platform development on CPU, memory and battery of mobile devices when using common mobile app features. Procedia Comput. Sci. 2020, 175, 189–196. [Google Scholar] [CrossRef]
- Corral, L.; Janes, A.; Remencius, T. Potential advantages and disadvantages of multiplatform development frameworks—A vision on mobile environments. Procedia Comput. Sci. 2012, 10, 1202–1207. [Google Scholar] [CrossRef]
- Elgendy, I.A.; Zhang, W.; Tian, Y.C.; Li, K. Resource allocation and computation offloading with data security for mobile edge computing. Futur. Gener. Comput. Syst. 2019, 100, 531–541. [Google Scholar] [CrossRef]
- Rieger, C.; Majchrzak, T.A. Towards the definitive evaluation framework for cross-platform app development approaches. J. Syst. Softw. 2019, 153, 175–199. [Google Scholar] [CrossRef]
- Rieger, C.; Tian, A.M.B. Weighted Evaluation Framework for Cross-Platform App Development Approaches. In Information Systems: Development, Research, Applications, Education: 9th SIGSAND/PLAIS EuroSymposium 2016, Proceedings 9, Gdansk, Poland, 29 September 2016; Springer: Berlin/Heidelberg, Germany, 2016; Volume 2, pp. 18–39. [Google Scholar] [CrossRef]
- Zhang, G.A.; Gu, J.Y.; Bao, Z.H.; Xu, C.; Zhang, S.B. AGILE: A terminal energy efficient scheduling method in mobile cloud computing. Trans. Emerg. Telecommun. Technol. 2015, 26, 1323–1336. [Google Scholar] [CrossRef]
- Wang, Y.H.; Wu, I.C. An evaluation framework for cross-platform mobile application development tools. Softw. Pract. Exp. 2014, 45, 1331–1357. [Google Scholar] [CrossRef]
- Kim, S. One-on-one contract game–based dynamic virtual machine migration scheme for Mobile Edge Computing. Trans. Emerg. Telecommun. Technol. 2018, 29, e3204. [Google Scholar] [CrossRef]
- Kim, D.; Chon, Y.; Jung, W.; Kim, Y.; Cha, H. Accurate prediction of available battery time for mobile applications. ACM Trans. Embed. Comput. Syst. 2016, 15, 5423. [Google Scholar] [CrossRef]
- Mittal, R.; Kansal, A.; Chandra, R. Empowering developers to estimate app energy consumption. In Proceedings of the Mobicom ’12: Proceedings of the 18th Annual International Conference on Mobile Computing and Networking, Istanbul, Turkey, 2–26 August 2012; pp. 317–327. [CrossRef]
- Wei, L.; Liu, Y.; Cheung, S.C. Taming android fragmentation: Characterizing and detecting compatibility issues for android apps. In Proceedings of the ASE ’16: Proceedings of the 31st IEEE/ACM International Conference on Automated Software Engineering, Singapore, 3–7 September 2016; pp. 226–237. [CrossRef]
- Biørn-Hansen, A.; Grønli, T.M.; Ghinea, G. A survey and taxonomy of core concepts and research challenges in cross-platform mobile development. ACM Comput. Surv. 2019, 51, 1739. [Google Scholar] [CrossRef]
- Tong, F.; Yan, Z. A hybrid approach of mobile malware detection in Android. J. Parallel Distrib. Comput. 2017, 103, 22–31. [Google Scholar] [CrossRef]
- Meng, T.; Wolter, K.; Wu, H.; Wang, Q. A secure and cost-efficient offloading policy for Mobile Cloud Computing against timing attacks. Pervasive Mob. Comput. 2018, 45, 4–18. [Google Scholar] [CrossRef]
- Angin, P.; Bhargava, B.; Ranchal, R. A self-protecting agents based model for high-performance mobile-cloud computing. Comput. Secur. 2018, 77, 380–396. [Google Scholar] [CrossRef]
- Goel, D.; Jain, A.K. Mobile phishing attacks and defence mechanisms: State of art and open research challenges. Comput. Secur. 2018, 73, 519–544. [Google Scholar] [CrossRef]
- Mai, P.X.; Goknil, A.; Shar, L.K.; Pastore, F.; Briand, L.C.; Shaame, S. Modeling Security and Privacy Requirements: A Use Case-Driven Approach. Inf. Softw. Technol. 2018, 100, 165–182. [Google Scholar] [CrossRef]
- Mollah, M.B.; Azad, M.A.K.; Vasilakos, A. Security and privacy challenges in mobile cloud computing: Survey and way ahead. J. Netw. Comput. Appl. 2017, 84, 38–54. [Google Scholar] [CrossRef]
- Kamesh; Sakthi Priya, N. Securing mobile access with interactive image code and image key encryption. Secur. Commun. Netw. 2016, 5, 422–438. [Google Scholar] [CrossRef]
- Yerima, S.Y.; Sezer, S.; McWilliams, G. Analysis of Bayesian classification-based approaches for Android malware detection. IET Inf. Secur. 2014, 8, 25–36. [Google Scholar] [CrossRef]
- Lee, Y.K.; Bang, J.Y.; Safi, G.; Shahbazian, A.; Zhao, Y.; Medvidovic, N. A sealant for inter-app security holes in android. In Proceedings of the 2017 IEEE/ACM 39th International Conference on Software Engineering (ICSE), Buenos Aires, Argentina, 20–28 May 2017; pp. 312–323. [Google Scholar] [CrossRef]
- Ma, S.; Feng, R.; Li, J.; Liu, Y.; Nepal, S.; Bertino, E.; Deng, R.H.; Ma, Z.; Jha, S. An empirical study of SMS one-time password authentication in android apps. In Proceedings of the ACSAC ’19: Proceedings of the 35th Annual Computer Security Applications Conference, San Juan, Puerto Rico, 9–13 December 2019; pp. 339–354. [CrossRef]
- Namrud, Z.; Kpodjedo, S.; Talhi, C. AndroVul: A repository for android security vulnerabilities. In Proceedings of the CASCON ’19: Proceedings of the 29th Annual International Conference on Computer Science and Software Engineering, Toronto, ON, Canada, 4–6 November 2019; pp. 64–71.
- Hesenius, M.; Griebe, T.; Gries, S.; Gruhn, V. Automating UI tests for mobile applications with formal gesture descriptions. In Proceedings of the MobileHCI ’14: Proceedings of the 16th International Conference on Human-Computer Interaction with Mobile Devices & Services, Toronto, ON, Canada, 23–26 September 2014; pp. 213–222. [CrossRef]
- Russello, G.; Jimenez, A.B.; Naderi, H.; Van Der Mark, W. FireDroid: Hardening security in almost-stock android. In Proceedings of the ACSAC ’13: Proceedings of the 29th Annual Computer Security Applications Conference, New Orleans, LA, USA, 9–13 December 2013; pp. 319–328. [CrossRef]
- Arora, A.; Peddoju, S.K. Minimizing network traffic features for Android mobile malware detection. In Proceedings of the ICDCN ’17: Proceedings of the 18th International Conference on Distributed Computing and Networking, Hyderabad, India, 5–7 January 2017. [CrossRef]
- Mulliner, C.; Oberheide, J.; Robertson, W.; Kirda, E. PatchDroid: Scalable third-party security patches for android devices. In Proceedings of the ACSAC ’13: Proceedings of the 29th Annual Computer Security Applications Conference, New Orleans, LA, USA, 9–13 December 2013; pp. 259–268. [CrossRef]
- Bhat, P.; Dutta, K. A survey on various threats and current state of security in android platform. ACM Comput. Surv. 2019, 52, 1–35. [Google Scholar] [CrossRef]
- Wei, N.; AmiriSani, A. SchrodinText: Strong Protection of Sensitive Textual Content of Mobile Applications. IEEE Trans. Mob. Comput. 2020, 1233, 1. [Google Scholar] [CrossRef]
- Wang, P.; Tamura, S. Software Protection on the Go: A Large-Scale Empirical Study on Mobile App Obfuscation ACM Reference Format. In Proceedings of the 40th International Conference on Software Engineering, Gothenburg, Sweden, 27 May–3 June 2018; pp. 26–36. [Google Scholar]
- Capilla, R.; Kazman, R.; Romera, C.; Carrillo, C. Usability implications in software architecture: The case study of a mobile app. Softw. Pract. Exp. 2020, 50, 2145–2168. [Google Scholar] [CrossRef]
- Zhao, H.; Chen, M.; Qiu, M.; Gai, K.; Liu, M. A novel pre-cache schema for high performance Android system. Futur. Gener. Comput. Syst. 2016, 56, 766–772. [Google Scholar] [CrossRef]
- Dye, S.M.; Scarfone, K. A standard for developing secure mobile applications. Comput. Stand. Interfaces 2014, 36, 524–530. [Google Scholar] [CrossRef]
- Raptis, D.; Tselios, N.; Kjeldskov, J.; Skov, M.B. Does size matter? Investigating the impact of mobile phone screen size on users’ perceived usability, effectiveness and efficiency. In Proceedings of the MobileHCI ’13: Proceedings of the 15th International Conference on Human-Computer Interaction with Mobile Devices and Services, Munich, Germany, 27–30 August 2013; pp. 127–136. [CrossRef]
| Title | Author Name/Publication Year | Domain/Publication Type | Contributions | Limitations |
|---|---|---|---|---|
| “A review on the computation offloading approaches in mobile edge computing: A game-theoretic perspective” | Ali Shakarami/2020 [17] | Mobile edge computing/Research article | GT-based computation offloading approaches in the MEC environment are reported | The perspective of game theory is discussed only |
| “Joint computation offloading and resource provisioning for edge-cloud computing environment: A machine learning-based approach” | Ali Shahidinejad/2020 [18] | Mobile edge computing/Research article | An edge server provisioning approach using LSTM prediction to estimate the future workload and reinforcement learning technique to make the appropriate scaling decision | - |
| “An automated model-based approach for unit-level performance test generation of mobile applications” | Muhammad Usman/2020 [19] | Software testing/Research article | Mobile application model-based approach is formulated specifically for performance testing | The proposed approach is specific to variants of native apps |
| “VAnDroid: A framework for vulnerability analysis of Android applications using a model-driven reverse engineering technique” | Atefeh Nirumandv/2019 [20] | Computer science/Research article | VAnDroid framework is proposed regarding Android applications. The framework can be used for eliciting the security risks and vulnerabilities | The limited sample size for tool evaluation |
| “EMaaS: Energy measurements as a service for mobile applications” | Luis Cruz/2019 [21] | Software engineering/Conference paper | A system providing reliable energy measurements for mobile applications without requiring a complex setup, named EMaaS | The proposed system is not reliable for w.r.t. security and privacy |
| “Radio and Computing Resource Allocation for Minimizing Total Processing Completion Time in Mobile Edge Computing” | Ryuji Kobaya/2019 [22] | Research article | A scheme is proposed for computing resource allocation | Time as a resource is discussed for tasks to be decomposed |
| “LeakDoctor: Toward Automatically Diagnosing Privacy Leaks in Mobile Applications” | Xiaolei/2019 [23] | Research article | The leakDoctor approach is generated | Lacking privacy declaration scenarios |
| “GUILeak: Tracing Privacy Policy Claims on User Input Data for Android Applications” | Xiaoyin Wang/2018 [24] | Software engineering/Research article | Proposed a novel approach to protect privacy policy violations due to leaks of user input data | Inadequate validation sample |
| “A systematic study on software requirements elicitation techniques and its challenges in mobile application development” | Hafsa Dar/2018 [3] | Requirement engineering/Research article | Highlighting elicitation techniques and challenges in mobile application development | No unified model or framework was proposed |
| “Why does the orientation change mess up my Android application? From GUI failures to code faults” | Domenico Amalfitano/2018 [25] | Research article/Software testing | DOC framework is formulated that categories the failures related to GUI | Limited means for the application requirements leading to miscalculation of GUI failures |
| “An energy-efficient algorithm for multi-site application partitioning in MCC” | Wen-li Zhang/2018 [26] | Mobile cloud computing/Research article | Proposed multi-site application partitioning algorithm based on genetic algorithm | Only considered Wi-Fi environment where bandwidth rate is relatively stable |
| “Cordovaconfig: A tool for mobile hybrid apps’ configuration” | Abeer AlJarrah/2018 [27] | Conference paper/Security and privacy | Tool named as CORDOVACONFIG is developed that is used for mobile application configuration | The input was taken by the limited target audience; hence, authenticity can be a major issue |
| “Why does data deletion fail? A study on deletion flaws and data remanence in android systems” | JUNLIANG SHU/2017 [28] | Research article/Security and privacy | Framework named DataRaider is proposed that is used for recovering data from stored files. | Lack of effectiveness in disc encryption mechanism |
| “Study and refactoring of android asynchronous programming” | Yu Lin/2016 [29] | Conference Paper/Computer science | AsyncDroid tool is proposed that is focused on refactoring | Lack of mechanism for transforming communication modes |
| “A systematic mapping study of mobile application testing techniques” | Samer Zein/2016 [30] | Accepted manuscript/Software testing | Practitioners-based testing problems/challenges are reported | Validation of findings can be an issue towards result authenticity |
| URL | |
|---|---|
| IEEE Xplorer | https://ieeexplore.ieee.org (accessed on 15 January 2023) |
| ScienceDirect | https://www.sciencedirect.com/ (accessed on 17 January 2023) |
| WileyOnline | https://onlinelibrary.wiley.com/ (accessed on 23 January 2023) |
| ACM | https://dl.acm.org/ (accessed on 25 January 2023) |
| Springer | https://link.springer.com (accessed on 25 January 2023) |
| MDPI | https://www.mdpi.com (accessed on 25 January 2023) |
| Keywords | Synonyms |
|---|---|
| Green/Sustainable Requirement Engineering Process | Sustainable Requirement Engineering, Sustainable Requirements, Sustainable Requirement Gathering, Sustainable Requirement Inception, Sustainable Requirement Elicitation, Sustainable Requirement Prioritization, Sustainable Requirement Validation, Sustainable Requirement Specification |
| Sustainable Mobile Application Development | Sustainable Mobile Platform, Sustainable Mobile Applications, Sustainable Mobile Development |
| Challenges | Issues, Problems, Barriers |
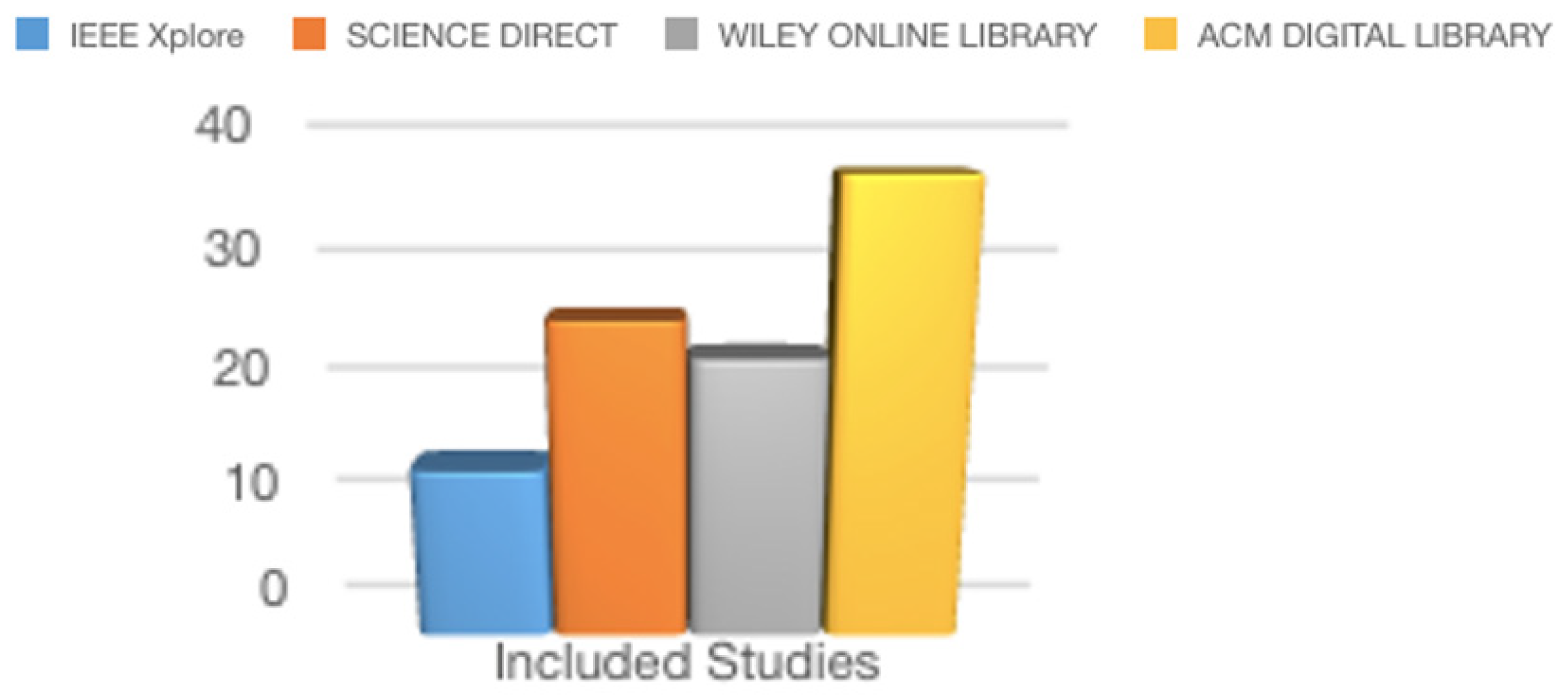
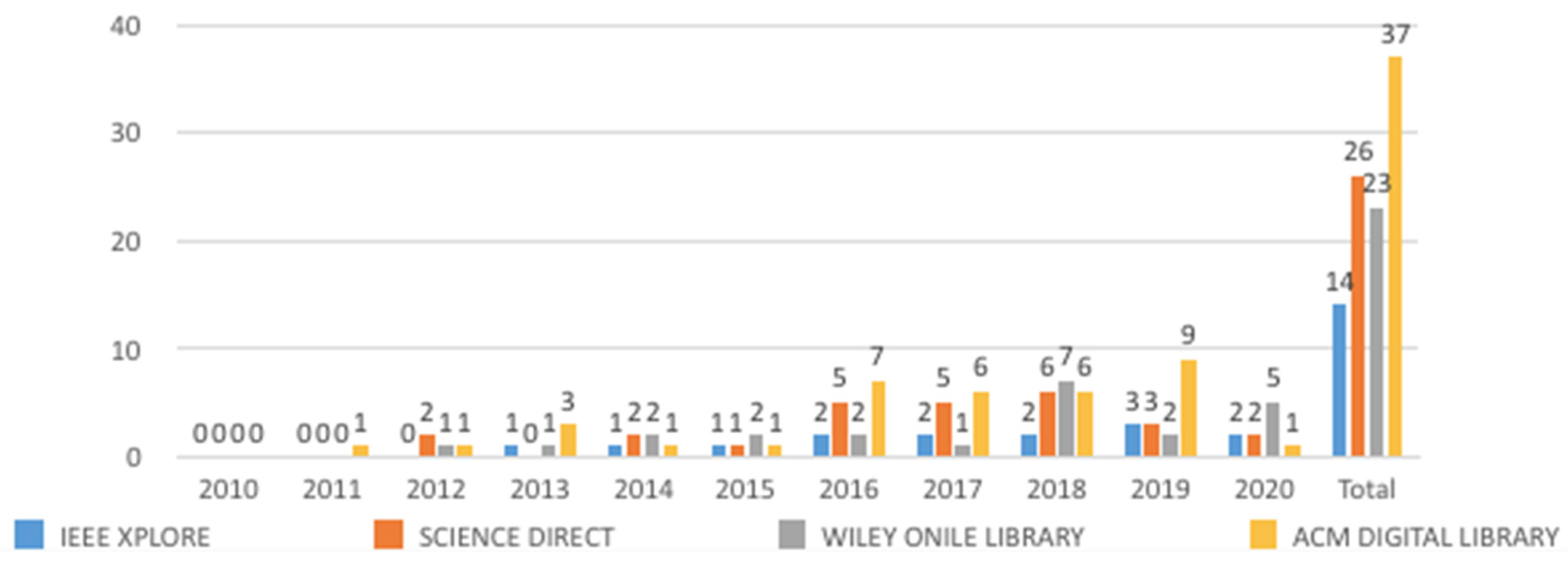
| Electronic Database | Papers Found | Stage 1: Title and Keyword | Stage 2: Abstract | Stage 3: Repeated | Stage 4: Full Paper Read | Stage 5: Quality Assessment |
|---|---|---|---|---|---|---|
| IEEE | 526 | 230 | 85 | 70 | 20 | 14 |
| ScienceDirect | 31,772 | 21,929 | 2198 | 1361 | 33 | 26 |
| WileyOnline | 27,531 | 2903 | 1473 | 94 | 47 | 23 |
| ACM | 14,685 | 788 | 518 | 50 | 45 | 37 |
| Springer | 326 | 63 | 34 | 8 | 2 | 0 |
| MDPI | 457 | 116 | 26 | 6 | 4 | 0 |
| Paper Id | Ref Number | Category | Challenge |
|---|---|---|---|
| X1 | [36] | Communication | Anonymous communication |
| X4 | [3] | Lack of effective requirement articulation | |
| X4 | [3] | Lack of verbal and presentation skills | |
| X4 | [3] | Lack of communication participation | |
| W3 | [37] | Low bandwidth | |
| W3 | [37] | Unavailability of services for network connection | |
| W3 | [37] | Heterogeneity in terms of the involvement of different networks | |
| W13 | [38] | Frequent server disconnections | |
| W13 | [38] | Problems in accessing server data | |
| A9 | [39] | Data communication overheads | |
| X4 | [3] | Requirements | Incomplete requirements gathering |
| X4 | [3] | Lack of accurate requirement prioritization | |
| X4, X11 | [3,40] | Unstable requirements | |
| X4 | [3] | Change of user needs and understanding | |
| X4 | [3] | Requirement over-scoping | |
| X11 | [40] | Guideline compliance | |
| X12 | [41] | The problem of minimization of service latency | |
| X12 | [41] | The optimal revenue maximization problem | |
| X12 | [41] | Absence of high quality-of-service requirement to offload the computational service offloading | |
| X13 | [42] | Inefficient provisioning and delivery of mobile application | |
| S1, S15, S14 | [17,43,44] | Lack of consideration of user and application requirements for offloading decision making | |
| S2, S4 | [26,45] | Incorrect requirement partitioning | |
| S4 | [45] | Lack of useful information extraction | |
| S8, S12, S21, S22 | [46,47,48,49] | Inefficiency in constructing power models | |
| W3 | [37] | CO issues in terms of energy savings (static environment) | |
| X6, S23, W7 | [50,51,52] | Complexity in GUI testing | |
| W8 | [53] | Lack of appropriate battery life | |
| W9 | [54] | Complexity in evaluating applications’ performances | |
| W11 | [55] | Time consumption of mobile devices | |
| W11, W18 | [56,57] | Energy consumption of mobile devices | |
| A1 | [58] | Diversity of mobile surroundings | |
| W15 | [20] | Changing the orientation of the app | |
| W17 | [56] | Inefficient web browsing on mobile systems | |
| W21 | [59] | Problem with touch gesture and embedded sensor-based interfaces | |
| W22, W23 | [60,61] | Incorrect requirement identification | |
| A7 | [62] | Complexity in bundling of HTTP requests | |
| A9 | [39] | Depletion of battery power | |
| A11 | [63] | Event-driven structure | |
| A11 | [63] | Complex contextual features | |
| A14 | [64] | High power consumption of smartphones | |
| A14 | [64] | Surface over-heating of smartphones | |
| A18 | [65] | Impact of delay on UX | |
| A20 | [38] | Impact of network on the performance of mobile devices | |
| A21, A27 | [66,67] | Environmental factors’ impacts on the biometric authentication method | |
| A25, A26, A32 | [68,69,70] | Lack of power requirement for battery of mobile devices | |
| A33 | [71] | Lack of quality assurance | |
| A26 | [69] | Frequent changing requirements | |
| A36 | [72] | Inadequate app performance | |
| W10, X3, A5 | [73,74,75] | Inefficient requirement completion time | |
| X2, X9, X11, W20, W13 | [18,38,40,73,76,77] | Resource | Lack of appropriate resource allocation |
| X3, S11, S13, S18, S22, S23, S25, S26 | [74,78,79,80,81,82,83,84] | Platform incompatibility | |
| W4 | [85] | Inaccurate task scheduling | |
| X5, W6 | [22,86] | Service selection problem | |
| X7 | [29] | DVFS-control problem | |
| X8, A5 | [75] | Lack of resource optimization | |
| X8, A5 | [75] | Energy inefficiency | |
| W4, W13 | [38,85] | Limited resources/resources lacking | |
| W12 | [87] | VM-migration problem | |
| S18 | [80] | Higher resource utilization by mobile cross-platform development approaches | |
| S23, A1 | [58,83] | Lacking/limited computational resources | |
| A3, A4 | [88,89] | Incorrect estimation of battery life | |
| A12, A13 | [23,24] | Lack of accurate quantification about the consumption of energy by the app | |
| A24, A27, A29 | [69,90,91] | Compatibility across various OS versions | |
| X10 | [29] | Security and Privacy | Lack of asynchrony retrofitting |
| S3, S6, | [92,93] | Malware detection problem | |
| S6 | [93] | Timing attacks | |
| S7, W14 | [94,95] | Tampering during offloading data | |
| S8 | [46] | Limitation of profilers | |
| W3 | [37] | CO in terms of network connection status and bandwidth | |
| W3 | [37] | Security w.r.t. mobile users | |
| W3, S24, A16 | [37,96,97] | Data security on the cloud | |
| W14, S19, W19 | [95,98,99] | Side-glance attack | |
| W15, A2 | [20,100] | Lack of identification of risky actions and vulnerabilities | |
| A4, A6 | [101,102] | OTP-vulnerability | |
| A8, A15 | [103,104] | Inconsistent and inefficient testing | |
| A10 | [27] | Lack of configuration of mobile hybrid apps | |
| S20, A16, A17 | [23,24,96] | Unclear requirements for app functionality toward privacy threats | |
| A19, A22, A30 | [105,106,107] | Patching for updating, correction, or improvement | |
| A34, A35, | [108,109] | Data reconstruction attack | |
| A28 | [28] | Data erasure | |
| X4 | [3] | Stakeholder | Unawareness of needs |
| X4 | [3] | Cultural and language barrier | |
| X4 | [3] | Lack of domain knowledge | |
| X4 | [3] | Ambiguities | |
| X4 | [3] | Conflicts | |
| X8, A5 | [65,75] | Response time inefficiency | |
| W23 | [110] | Ignorance of usability | |
| S5 | [111] | Lack of Requirement Task Efficiency and Responsiveness | |
| S9 | [112] | Lack of knowledge regarding development standards and practices | |
| S10 | [30] | Testing issues | |
| A31 | [113] | Impact of screen size on usability | |
| A36 | [72] | Poor user experience |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tanveer, M.; Khan, H.H.; Malik, M.N.; Alotaibi, Y. Green Requirement Engineering: Towards Sustainable Mobile Application Development and Internet of Things. Sustainability 2023, 15, 7569. https://doi.org/10.3390/su15097569
Tanveer M, Khan HH, Malik MN, Alotaibi Y. Green Requirement Engineering: Towards Sustainable Mobile Application Development and Internet of Things. Sustainability. 2023; 15(9):7569. https://doi.org/10.3390/su15097569
Chicago/Turabian StyleTanveer, Mahrukh, Huma Hayat Khan, Muhammad Noman Malik, and Youseef Alotaibi. 2023. "Green Requirement Engineering: Towards Sustainable Mobile Application Development and Internet of Things" Sustainability 15, no. 9: 7569. https://doi.org/10.3390/su15097569
APA StyleTanveer, M., Khan, H. H., Malik, M. N., & Alotaibi, Y. (2023). Green Requirement Engineering: Towards Sustainable Mobile Application Development and Internet of Things. Sustainability, 15(9), 7569. https://doi.org/10.3390/su15097569






