1. Introduction
Owing to the evolving advancement and fast progression in artificial technology, the ubiquitous computing method is a vital part of everyday life [
1]. The common aim of the ubiquitous method is a too-quick tight combination of its coexisting ambience, human beings, and information. To devise smart ambiences, an enhancement to security, performances, and sustainability of conventional policies was essential [
2]. As a community, computation resources must be treated as finite and precious, utilized if needed, and as effectually as possible. The Internet of Things (IoT) was based on interconnected smart gadgets, and different services were used to intergrade one network [
3]. This allows the smart devices to collect delicate data and executes important functions, and these gadgets link and interact with each other at the highest speed and make decisions based on the indicator information. The IoT atmospheres employ cloud service as the back-end top for processing information and maintaining remote control. Client users leverage web services or mobile applications to access information and control their gadgets. The IoT structures employ an enormous quantity of sensor nodes to extract significant data, and it can be scrutinized using the artificial intelligence (AI) method [
4,
5].
An IDS refers to a security methodology which majorly operates in the IoT network layer. An IDS positioned for an IoT network has the capability in the analyses data packets to produce responses realistically, examining data packets in dissimilar layers of IoT networks with dissimilar protocol stacks, and adapting to several methods in IoT systems [
5,
6]. An IDS can be advanced for IoT-related smart settings that need to operate in extreme circumstances of higher-volume data processing, less processing capability, and quicker response. Therefore, conventional IDS does not suit the IoT network [
7]. The security of IoT is a continuous and serious issue; thus, the progression of respective mitigating techniques and understanding of security vulnerabilities of IoT mechanisms is required. Machine learning (ML) techniques are widely used in the detection of several types of assaults, and they can support the network administrator in taking corresponding initiatives for preventing intrusion [
8]. However, several traditional ML approaches go to shallow learning and often highlight feature selection and engineering; it cannot proficiently solve the vast intrusion data classifying issues that appear in face of real-time network applications. Of the speedy advancement of the dataset, numerous classifying approaches may lead to diminished performance [
9]. Along with that, shallow learning cannot be suitable for predicting the need for high-dimension learning with huge data and intellectual analysis. Conversely, deep learners may have a possibility to derive superior representation from the data for generating better methods. Subsequently, IDS has encountered incredible progression after dropping into an unhurried period [
10].
This article presents intrusion detection using chaotic poor and rich optimization with a deep learning model (IDCPRO-DLM) for ubiquitous and smart environments. The presented IDCPRO-DLM model exploits the Z-score data normalization approach to scale the input data. In addition, the IDCPRO-DLM model designs a chaotic poor and rich optimization algorithm-related feature selection (CPROA-FS) approach for electing feature subsets. Moreover, the butterfly optimization algorithm (BOA) with a deep sparse autoencoder (DSAE) classification model is utilized to classify intrusions. The simulation analysis of the IDCPRO-DLM approach was tested employing a series of simulations.
The rest of the paper is organized as follows.
Section 2 provides the related works and
Section 3 offers the proposed model. Then,
Section 4 presents the result analysis and
Section 5 concludes the paper.
2. Related Works
Subbarayalu et al. [
11] modelled the operation behaviors of IoT events with timed AC and developed a new hybrid NIDS. A web server is incorporated into IoT devices for remote accessibility, and constraint application protocol can be applied in intra and inter -smart device transmission. In [
12], the authors presented various concepts for the security of wireless sensors in a smart environment. The suggested technique is dependent on electronic gadgets; the IDS minimizes the computation function of the sensor, thus increasing the efficacy. Similarly, the IDS presents the idea of a feedback signal and “trust table” applied for triggering the isolation and detection mechanisms in case of attack. Manimurugan et al. [
13] projected a DL-related DBN system for IDS. Regarding anomaly detection and attacks, the CICIDS 2017 data are exploited for the assessment results of the presented method.
Efstathopoulos et al. [
14] presented anomaly-based IDSs particularly developed for SG utilizing operation datasets from a real-time power plant. Especially important, various ML and DL methods have been deployed, presenting novel parameters and feature representations in a comparative analysis. Razib et al. [
15] developed a DL-driven software defined networking (SDN)-assisted IDS to fight emergent cyberattacks in IoT. The suggested algorithm is able to counter a remarkable class of less frequently and commonly occurring cyberattacks in IoT communication. In [
16], the authors determine exactly how supervised ML algorithms (RF, DT, KNN, and ridge classifiers) and DRNN are employed for developing a robust IDS in the IoMT environments to forecast and classify unpredicted cyberattacks. Normalization and preprocessing of network datasets are implemented. Then, the researchers optimized the feature using a bio-inspired PSO approach.
Moradi et al. [
17] designed the intelligent IDS (I-IDS) using the ML mechanism so that the attack is recognized in the IoT system. The algorithm is constructed based on the malicious and normal assaults on the information that was produced in IoT smart environments. For simulating these models, a testbed is constructed whereby a node MCU, a wireless router, and a DHT11 sensor have been employed. An adversarial or attacker system is constructed to implement sniffing and poisoning attacks via a laptop system. The node captures the sensor value and transfers the information to the ThinkSpeak framework in the normal phase through a wireless gateway in addition to the assault stage; then, the malicious attackers interpret the information, and change it whereas transferring from nodes to the ThinkSpeak server.
In [
18], the authors establish a novel extraction feature and selective manners for the IDS method utilizing the benefits of SI techniques. The authors propose an extraction feature process based on CNN. Then, the authors propose an alternative selective feature (FS) system utilizing the newly established SI technique, Aquila optimizer (AQU). Fatani et al. [
19] present an effective AI-based process for IDS in IoT methods. The authors present an extraction feature approach utilizing the CNNs for extracting significant features. In addition, the authors establish a novel selective feature model utilizing a novel different of the transient search optimizer (TSO) technique named TSODE, utilizing the operators of the differential evolution (DE) technique.
D’hooge et al.’s [
20] purposes for demonstrating that strong common performance could not typically follow a strong classifier on the current IDS databases. Binary classification approaches in a range of algorithmic families can be trained on the attack classes of CSE-CIC-IDS2018. Talaei Khoei and Kaabouch [
21] relates the efficacy of supervised and unsupervised learning approaches in detecting cybersecurity. The supervised approaches are classification and regression decision tree, gaussian naïve bayes, LR, light gradient boosting, C-SVM, and Alex neural network. The unsupervised approaches are PCA, variational autoencoder (VAE), and K-means.
3. The Proposed Model
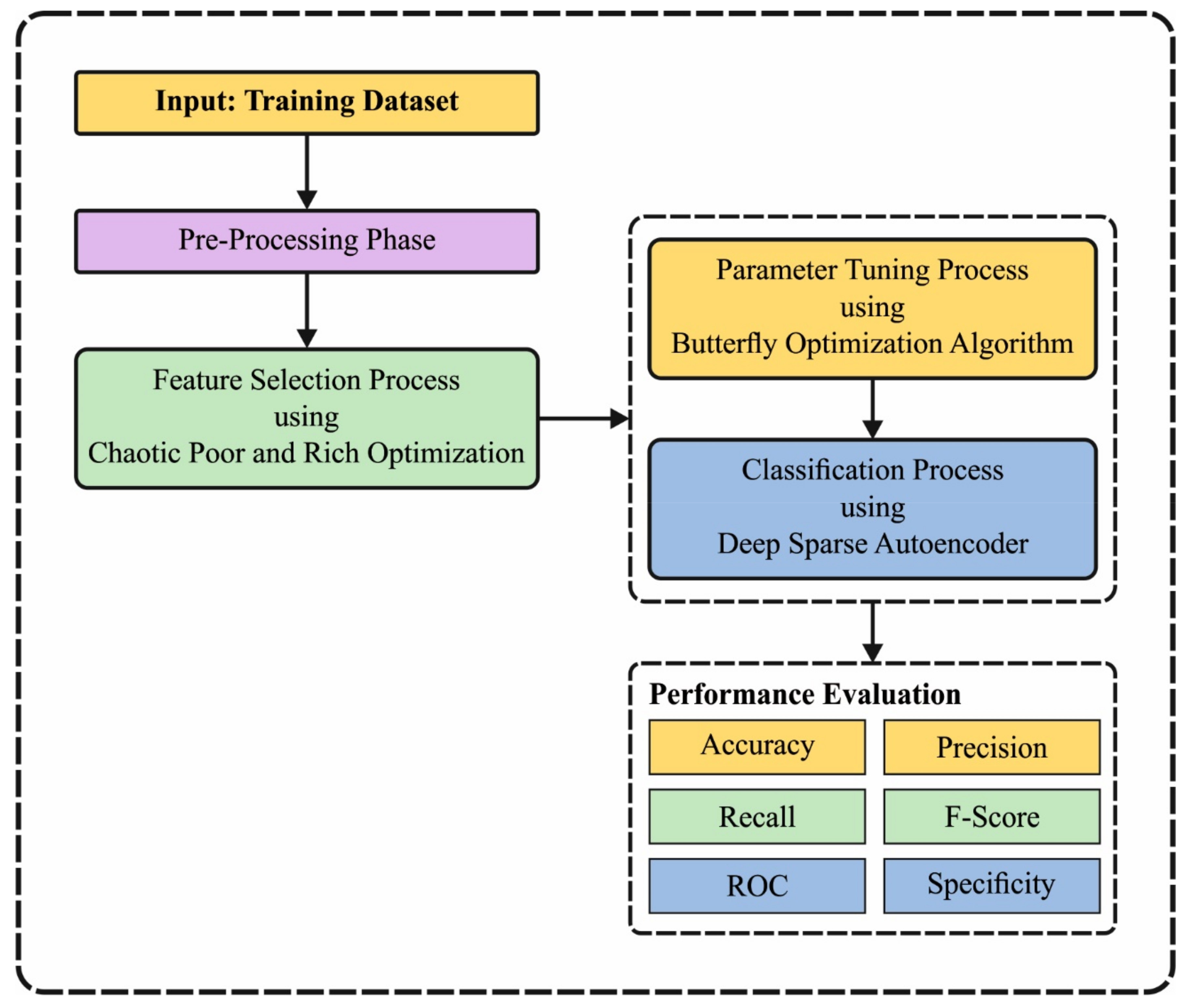
In this article, a novel IDCRPO-DLM methodology was developed for the recognition and classification of intrusion in smart environments. The presented IDCRPO-DLM methodology incorporates Z-score normalization, CRPOA-based feature subset selection, DSAE-based intrusion classification, and BOA-based hyperparameter tuning. The overall process is revealed in
Figure 1.
3.1. Data Pre-Processing
Primarily, the Z-score data normalization approach is exploited to scale the input data. It is a predictable normal and standard technique that denotes the sum of standard deviations (SD), and original data points were below or above the population mean. It possibly lies between
and
. This normalization of the dataset to mentioned scale converts all datasets with distinct scales to the default scale.
where
indicates the value of a particular instance,
represents the mean and
denotes SD.
3.2. Process Involved in CPROA-FS Technique
As soon as the input dataset is preprocessed, the IDCPRO-DLM model developed a CPROA-FS approach to elect feature subsets. Generally, the CPROA integrates the concepts of classical PROA with the chaotic map. PROA is a new bio-inspired meta-heuristic algorithm dependent upon the behavior of the poor and the rich. Since it suffers from low convergence speed and premature convergence, and easily traps in the local optimum, the CPROA is derived through the use of chaotic-based population initialization.
The PROA is reliant primarily on people’s wealth behaviors in society [
22]. In general, the grouping of persons according to their financial condition includes the two most important groups. The initial one consist of the poor economical class persons where wealth is lower than the average. The last one is richer economic class persons where wealth exceeds the average. In this study, the solution in poor populations shifts the way of globally optimal solutions in searching regions by learning from rich solutions in the population.
Now, each individual that exists in the population is determined as a binary vector and its length corresponds to the distinct feature number that exists in the input dataset. Where
,
refers to different features and every position of the solution maintains a binary value. The solution candidate encompasses poor and rich economical solutions. ‘N’ refers to population size. An ‘N’ solution is randomly produced with random numbers within zero and one. Next, the digitization method is applied to all the locations of the solution to transform the real value into binary values:
In Equation (13),
indicates an arbitrary number between zero and one. The solution candidate that exists in the population is sorted based on the objective function. The bottommost and topmost people in the population indicate poor and rich economic sets of persons. The major population of the PROA can be demonstrated in Equation (3).
People in a rich economical class shift in the way of improving the economical class gaps by observing the poor economical class. The poor people shift in the direction of decreasing the economical class by learning from the individuals in the rich class to increase their financial status. The features of rich and poor people are exploited for producing novel solutions. The motion of the rich solution is denoted by the following equation.
The motion of the poor solution is represented as follows.
In this study, the CPROA is derived through the use of a chaotic map into the PROA to enhance the arbitrary nature (diversity) to arrive at a global minimum and escape from trapping to the local minimum which results in fast convergence. The primary point of the chaotic map is an arbitrary number in [0, 1]. The CPROA-FS approach was used to identify the optimum feature subset that enhances the classification procedure. The solution vector assessments were unchangeable and ranged from zero to one. The fitness value of the solution can be represented in a binary form. It is given below.
where
displays FF to vector
sized
with 1/0 units that elaborate unelected or elected feature subsets,
denotes the total quantity of features.
means the classifier error, and
defines a constant tradeoff balancing from classifier error to quantity of selected feature sets. Herein, a classifying procedure becomes the chief objective and
.
3.3. DSAE-Based Classification Model
To detect and classify intrusions, the DSAE technique is applied. AE was an unsupervised feature learning NN which comprises hidden states that signify learned features, an input layer that represents input, and an output layer with a similar parameter to the input layer that signifies reconstruction term [
23]. The hidden and output layer forms the decoding network that is accountable for the reconstruction of the original input in the learned hidden representation code, while the hidden and input layers in the encoding network are accountable for converting the original input into hidden representation code. For every
input vector from dataset
, the
reconstructed vector and the
representation vector are determined in Equations (7) and (8), correspondingly, whereby
denotes the active function,
and
represent the weight matrixes, and
and
indicate the bias vector. In the SAE algorithm, the sigmoid function is utilized. The
reconstructed error among
and
is determined in Equation (10). The entire cost function of
instances is determined by Equation (10). The initial term of (10) indicates the reconstructed error of the entire dataset, and the next term is the regularized weight penalty that prevents overfitting by constraining the weight magnitude. The weight decay variable can be represented as
, the layer count of the network is denoted by
, the neuron count in
layer is indicated as
, and the weight connecting vectors among
-
neurons in
layer and
-
neuron in the
layer is referred to
:
However, the AE simply copies the input data even though the learned feature representation might perfectly rebuild the original input; the feature is not representative of classification and is redundant to a certain extent. In addition, the DSAE has a greater prospect to further learn representative and abstract features of the input than that of A [
23]. Equation (11) illustrates the total cost function of SAE, whereby
as previously shown in Equation (10), and the next is sparsity penalty term, whereby
denotes the average activation value of
hidden unit that is determined in Equation (12);
refers to an artificially provided smaller value named the sparsity variable, and parameter
indicates the sparsity penalty term utilized for controlling the relative significance among the penalty and reconstructed terms.
The DSAE aim is to future learn sparse and representative features that could remain and extract further data from the input rather than copying the input by minimalizing the cost function through the backpropagation (BP) model. The optimum set of variables , and are simultaneously learned through the reduction technique that is named the training model of DSAE.
3.4. Hyperparameter Tuning Using BOA
For optimal modification of the hyperparameters related to the DSAE method, the BOA was applied to it. The BOA is a nature-based inspired optimization technique to resolve optimization problems. It depends on the mating and food-searching behaviors of butterflies (BF) [
24]. The basic idea was to utilize the foraging approach of BF in nature which depends on a smaller sensor to determine the mating partner or nectar position. Power exponent (a), stimulus intensity (I), and sensory modality (c) are the three significant terms utilized for modelling the idea of processing and sensing the modality in the foraging process. It should be noted that sensory represents the energy form, whereby modality represents the raw input utilized by the sensor. In this study, the modality covering the fragrance (f) is expressed by a function of physical intensity in the following:
In Equation (13), the perceived magnitude of fragrances was indicated as , the sensory modality is indicated as , the stimulus intensity is characterized by , and the power exponent that depends on the modality that is accountable for various levels of absorption is denoted as . The parameters’ and values are lies within the interval of zero and one.
The initialization, iteration, and final phases are the three stages of BOA. Initially, the algorithm determines its solution space and the objective function. An initialized population of BF is created where the position is generated randomly in the solution space. Next, several iterations are implemented. Each BF in the solution space moves towards a novel position with the evaluated fitness value. Following, the BF fragrance can be produced at the position using Equation (14). The iteration state is repeated until the ending condition is satisfied. At last, the algorithm output of the optimal solution obtained the optimal fitness value.
Local and global searching stages are the two major strategies utilized in this study. In a global search, the BF moves towards the solution or fittest BF:
In Equation (15), the vector of solution for
-
BFs in
iteration is represented as
, the finest solution found in the existing iteration can be denoted by the term
, and the fragrance of
i-th BFs are denoted as
and
, which indicate a random integer between zero and one. Alternatively, the local search technique is modeled through:
In Equation (15), and indicate - and - BFs from a solution space. The pseudo-code of the BOA has been shown in Algorithm 1. The FF roles are an important part in the BOA system. It computes a positive digit to signify the development of candidate results. The classifier rate of rates has been assumed as FF. The rich solution contains a lower fitness value.
| Algorithm 1: Pseudo-code of BOA |
Initialization of sensor modality, power exponent, and (p) switching probability
Determine the fitness function dimension count
Produce the initialized population of BFs
while (end condition is not satisfied) do
for (every in the population) do
Evaluate fragrance for by utilizing Equation (13)
end for
Discover the optimal
for (all the in the population) do
Produce a number randomly from
if then
Move to the finest BF by utilizing Equation (14)
else
Randomly move by utilizing Equation (15)
end if
end for
Upgrade the value of
end while
Output the finest solution |
4. Performance Evaluation
The proposed model is simulated using Python 3.6.5 tool on PC i5-8600k, GeForce 1050Ti 4 GB, 16 GB RAM, 250 GB SSD, and 1 TB HDD. The performance validation of the IDCPRO-DLM model was performed using the CICIDS2017 dataset (
https://www.unb.ca/cic/datasets/ids-2017.html (accessed on 18 December 2022)). It is a network traffic dataset comprising a collection of benign and malicious traffic for network intrusion detection and traffic analysis. The CICIDS2017 dataset is gathered from a realistic network environment that includes traffic records from different protocols, such as TCP, UDP, ICMP, and HTTP. The dataset also includes network traffic records that have been captured from IoT devices, such as smart homes, wearable devices, and industrial control systems. It comprises data samples under diverse attacks such as Brute force attacks, DDoS attacks, normal attacks, botnet attacks, PortScan attacks, and infiltration attacks. The results are examined under 70% of training data and 30% of testing data.
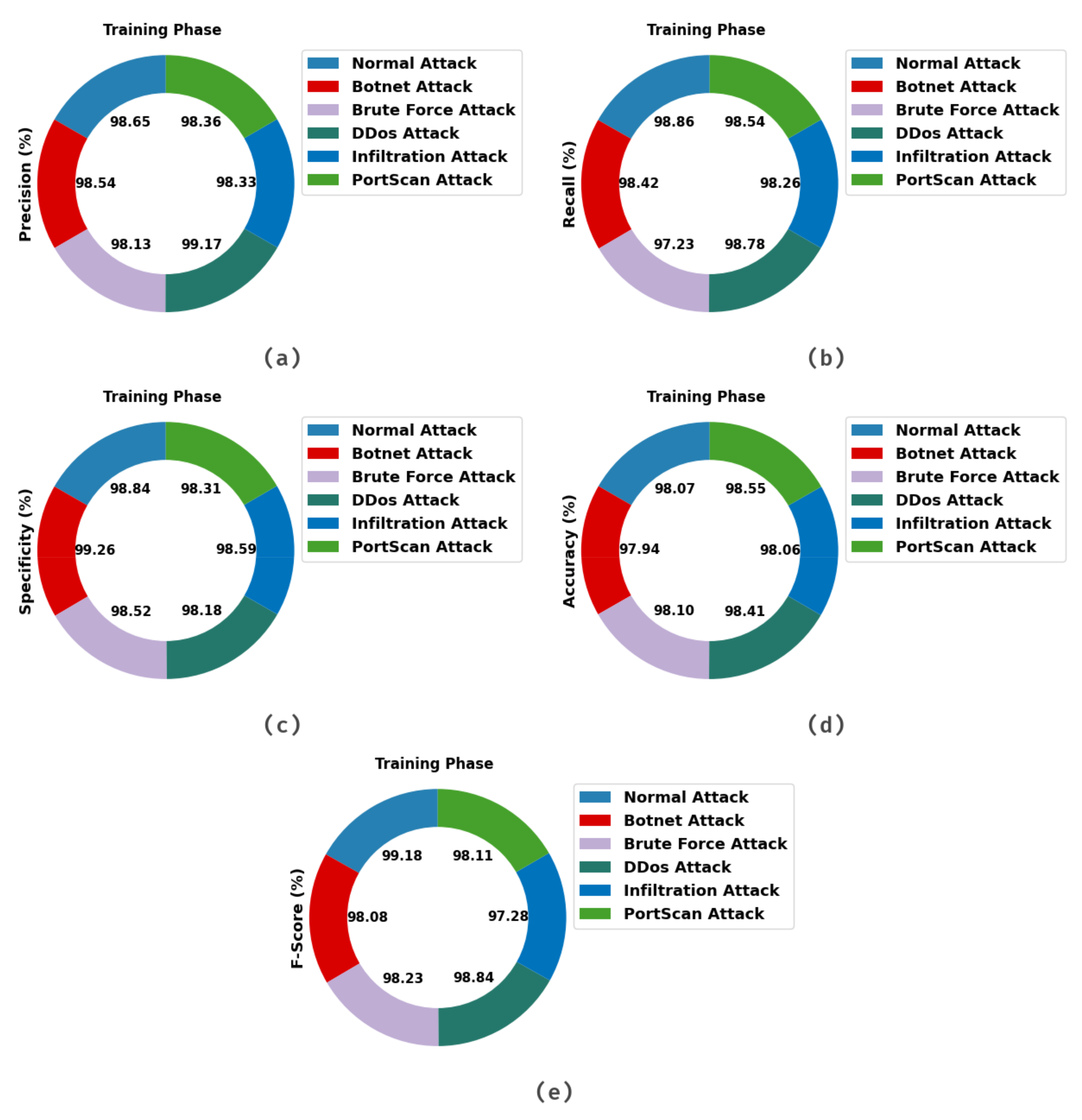
Table 1 and
Figure 2 report the classifier outcomes provided by the IDCPRO-DLM technique on training data. The outcomes implied that the IDCPRO-DLM approach has effectually classified the different kinds of attacks. For instance, the IDCPRO-DLM model has recognized normal attacks with
of 98.65%,
of 98.86%,
of 98.84%,
of 98.07%, and
of 99.18%. Simultaneously, the IDCPRO-DLM model has recognized botnet attacks with
of 98.54%,
of 98.42%,
of 99.26%,
of 97.94%, and
of 98.08%. Concurrently, the IDCPRO-DLM model has categorized DDoS attacks with
of 99.17%,
of 98.78%,
of 98.18%,
of 98.41%, and
of 98.84%. Moreover, the IDCPRO-DLM model has classified PortScan attacks with
of 98.36%,
of 98.54%,
of 98.31%,
of 98.55%, and
of 98.11%.
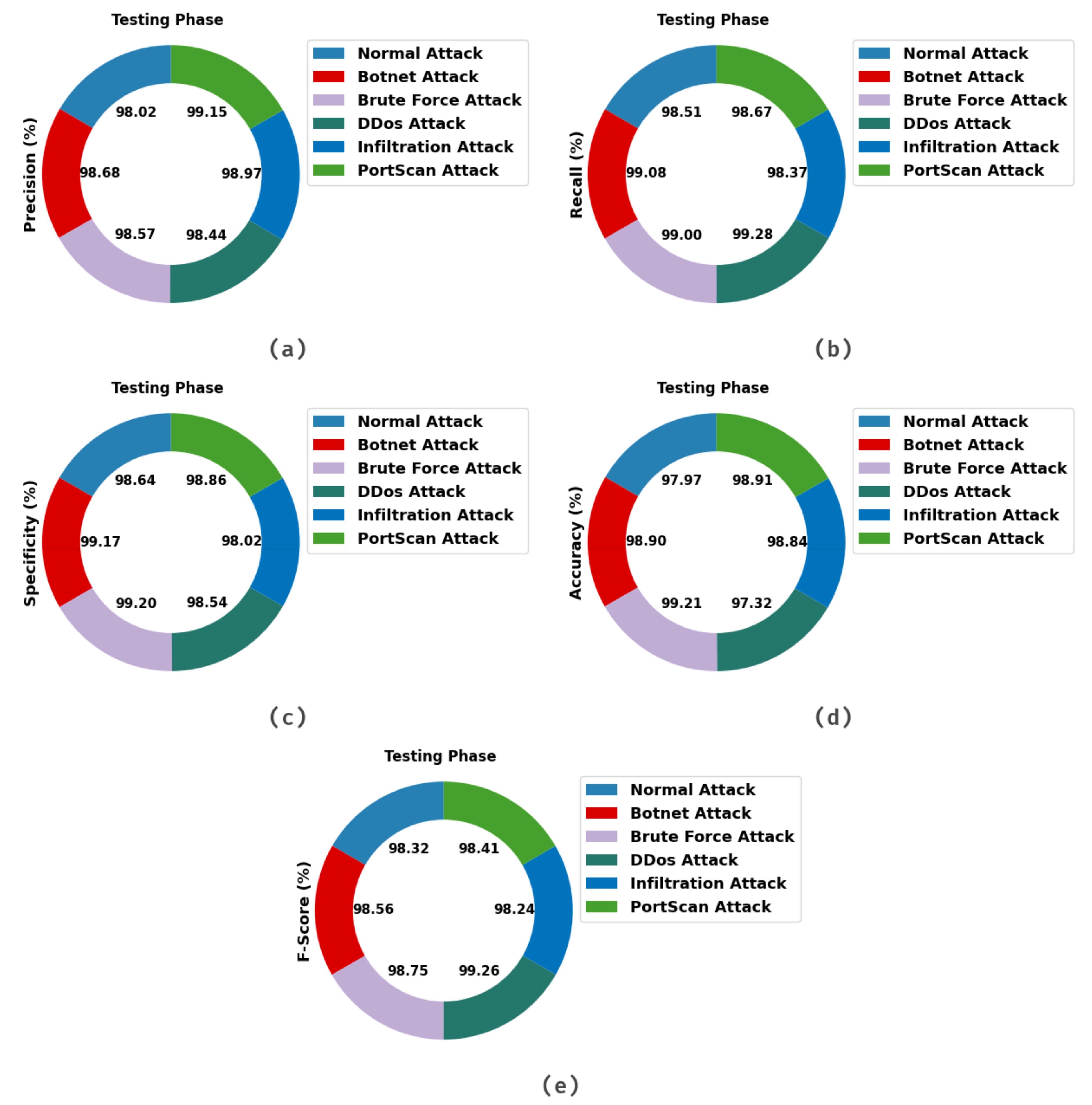
Table 2 and
Figure 3 show the classification outcomes given by the IDCPRO-DLM methodology on the testing dataset. The outcome indicates that the IDCPRO-DLM technique has effectively considered the diverse types of attacks. For example, the IDCPRO-DLM approach has identified normal attacks with
of 98.02%,
of 98.51%,
of 98.64%,
of 97.97%, and
of 98.32%. At the same time, the IDCPRO-DLM method has identified botnet attacks with
of 98.68%,
of 99.08%,
of 99.17%,
of 98.90%, and
of 98.56%. Simultaneously, the IDCPRO-DLM approach has classified DDoS attacks with
of 98.44%,
of 99.28%,
of 98.54%,
of 97.32%, and
of 99.26%. Furthermore, the IDCPRO-DLM method has categorized PortScan attacks with
of 99.15%,
of 98.67%,
of 98.86%,
of 98.91%, and
of 98.41%.
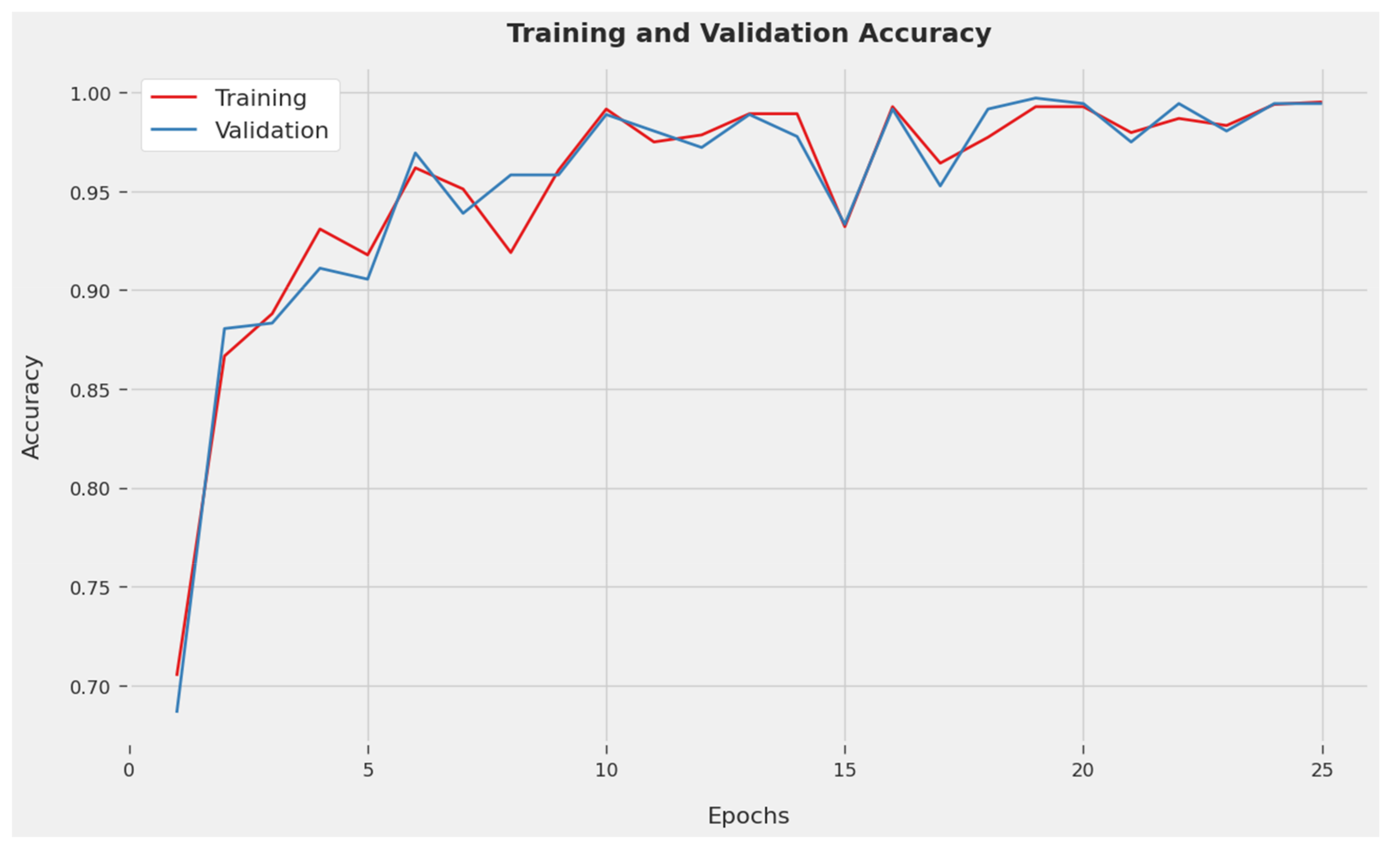
The TACY and VACY accomplished via the IDCPRO-DLM approach to the testing database are demonstrated in
Figure 4. The experimental result showed that the IDCPRO-DLM methodology has obtained higher values of TACY and VACY. Particularly of note, the VACY is higher than the TACY.
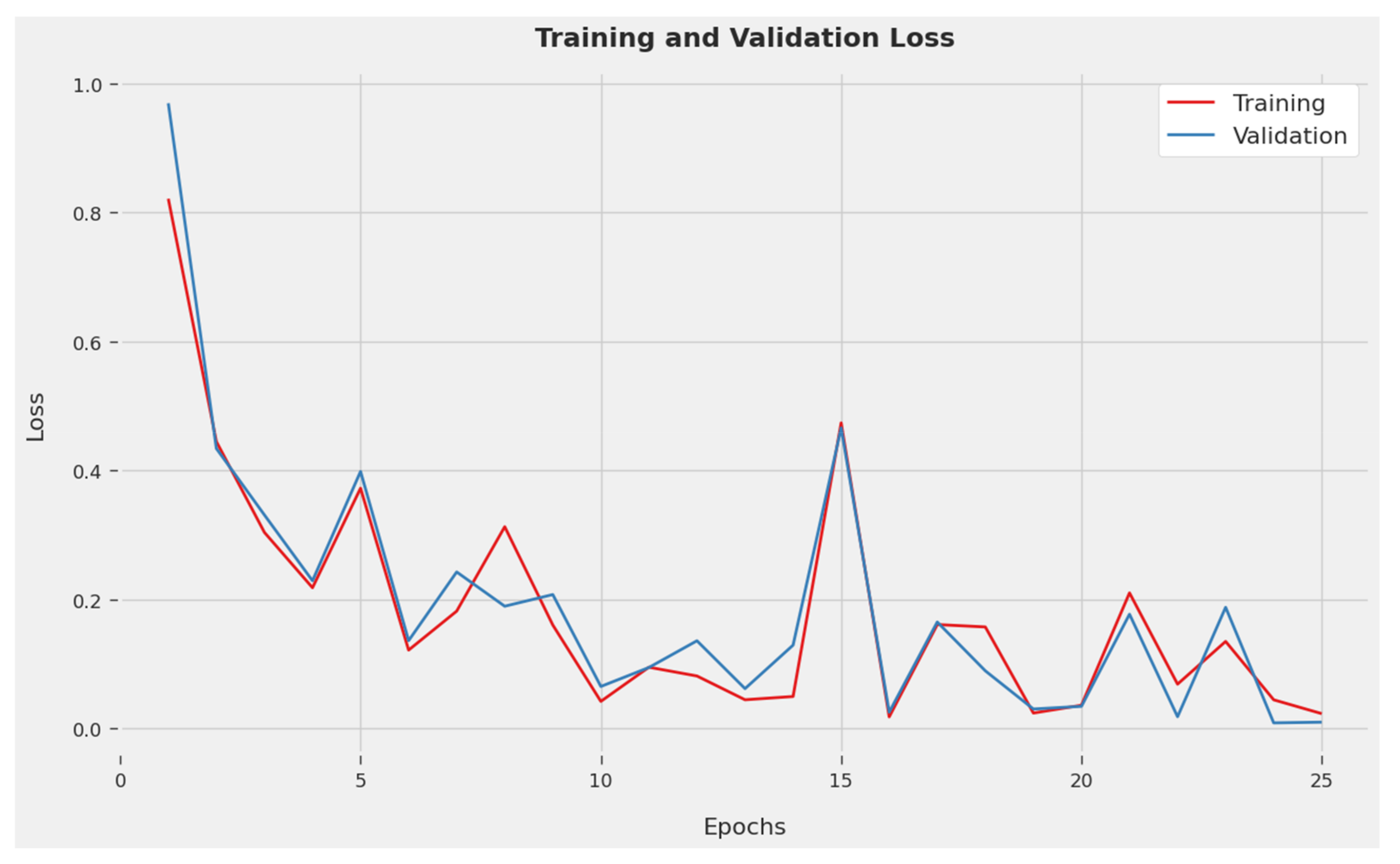
The TLOS and VLOS accomplished via the IDCPRO-DLM methodology on testing data are depicted in
Figure 5. The simulation result shows the IDCPRO-DLM method has obtained lesser values of TLOS and VLOS. To be specific, the VLOS is lower than the TLOS.
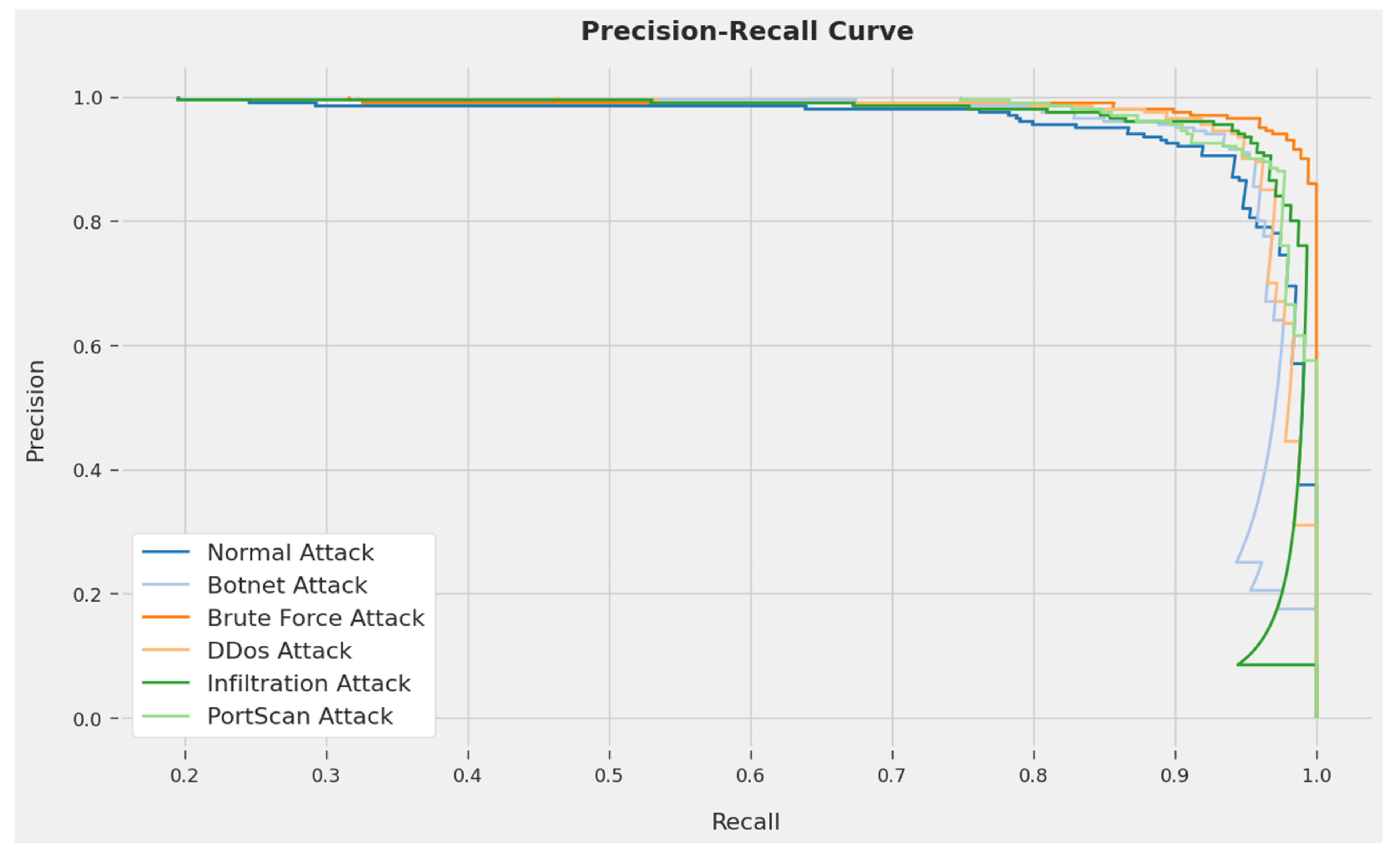
An evident precision–recall analysis of the IDCPRO-DLM system on testing data is demonstrated in
Figure 6. The figure demonstrates that the IDCPRO-DLM technique has resulted in improved values of precision–recall values in each class.
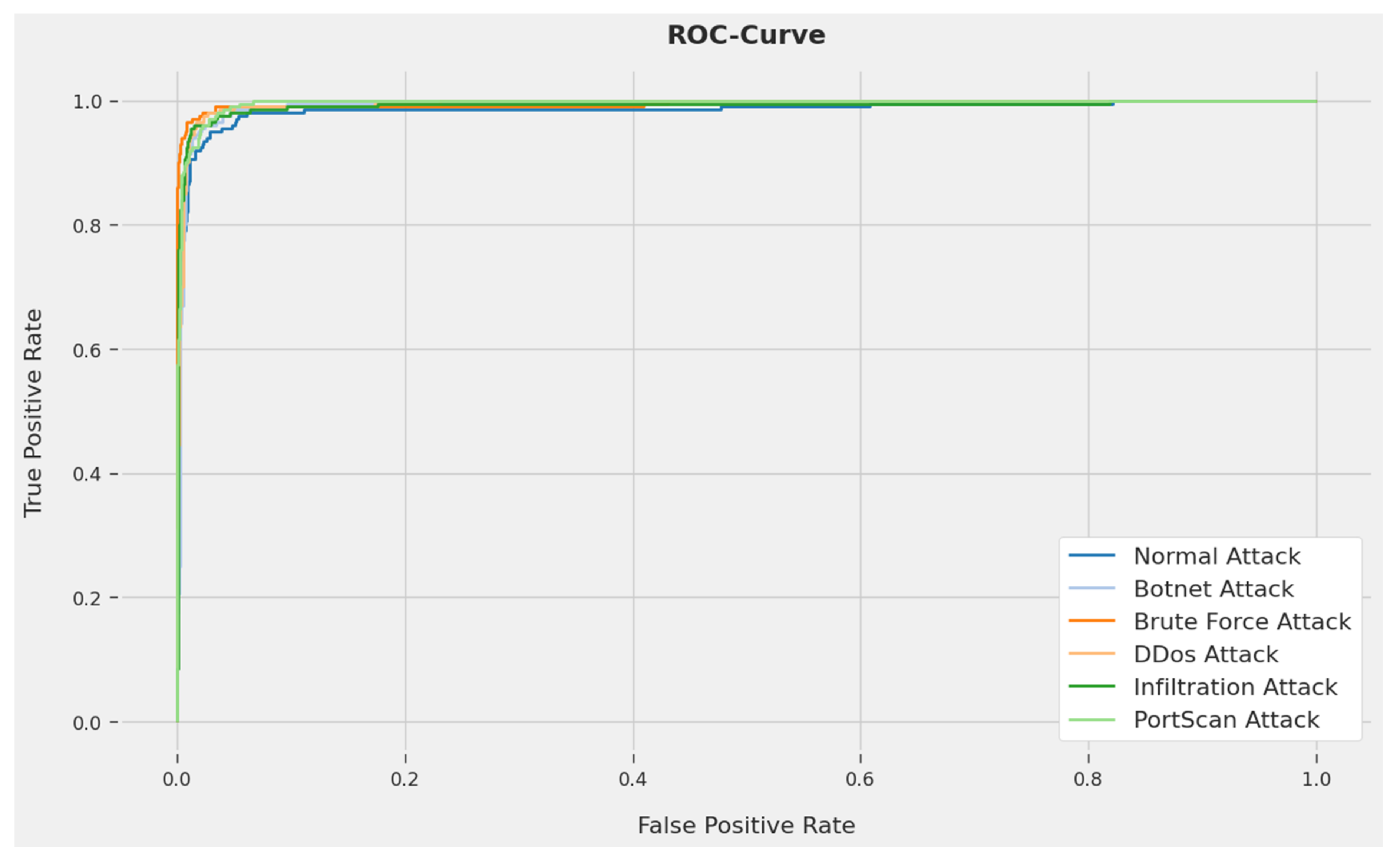
A comprehensive ROC analysis of the IDCPRO-DLM methodology on testing data is demonstrated in
Figure 7. The result indicates that the IDCPRO-DLM system has exhibited its capability in classifying dissimilar classes on testing datasets.
To ensure the enhanced performance of the IDCPRO-DLM algorithm, a detailed comparative analysis is made with recent approaches [
25] in
Table 3.
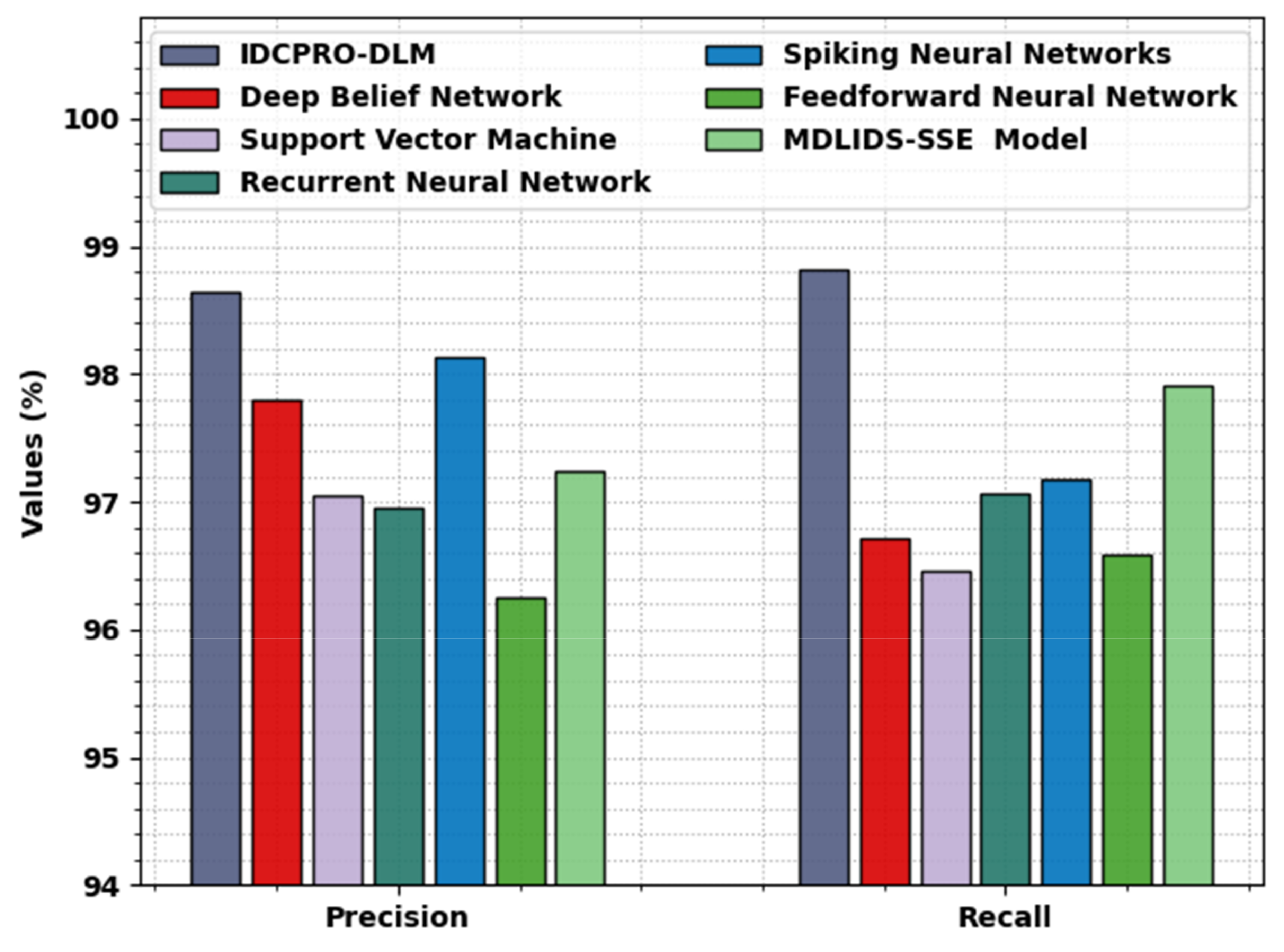
Figure 8 investigates a comparative analysis of the IDCPRO-DLM method with other techniques for
and
. The outcomes indicated that the IDCPRO-DLM method has shown increased values of
and
. For
, the IDCPRO-DLM method has rendered a higher
of 98.64%, whereas the DBN, SVM, RNN, SNN, FFNN, and MDLIDS-SSE models have reported a lower
of 97.80%, 97.05%, 96.96%, 98.14%, 96.26%, and 97.24%, respectively. Additionally, for
, the IDCPRO-DLM model has reached a maximum
of 98.82%, whereas the DBN, SVM, RNN, SNN, FFNN, and MDLIDS-SSE models have attained a minimum
of 96.72%, 96.46%, 97.07%, 97.18%, 96.58%, and 97.91%, respectively.
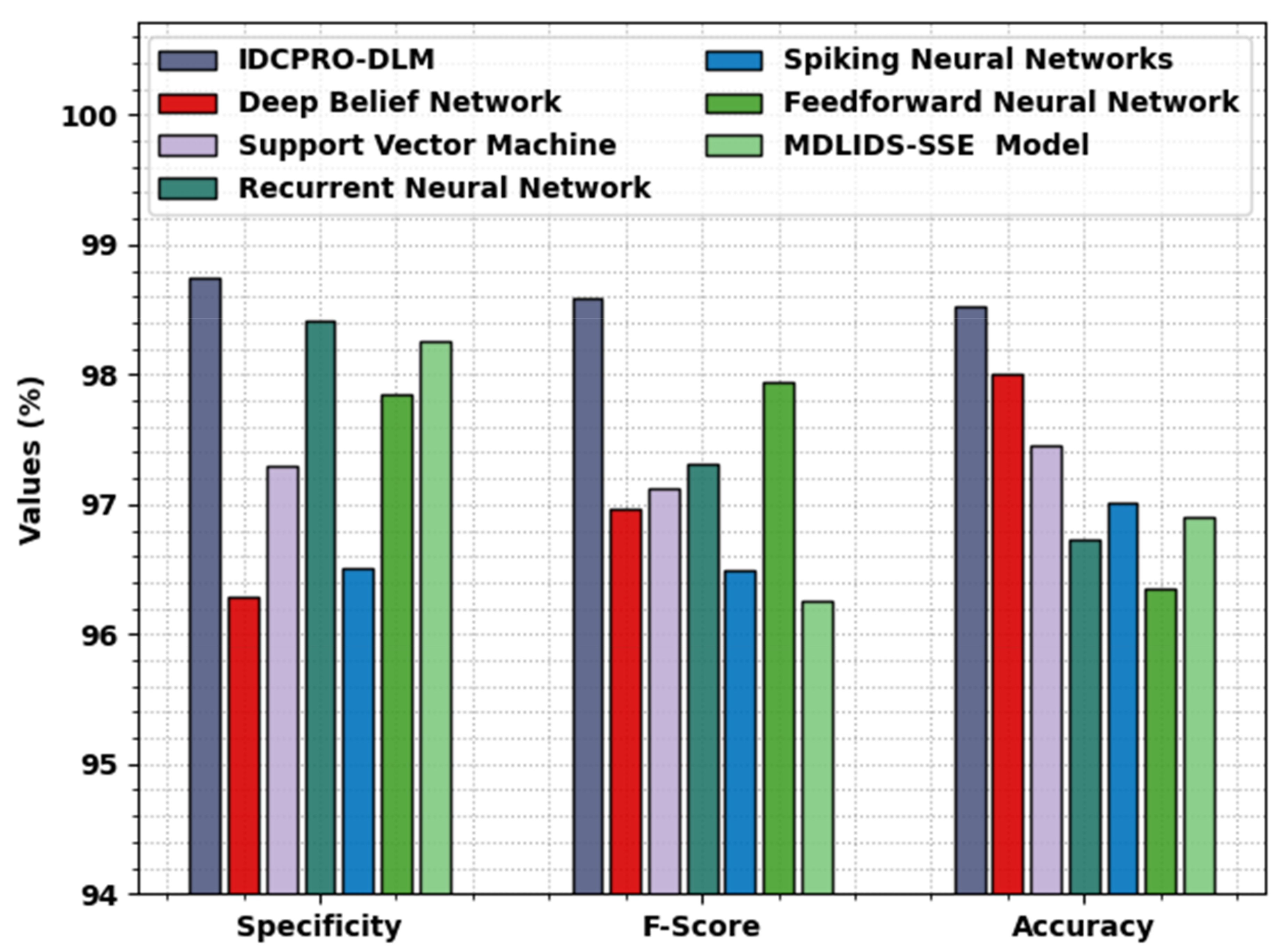
Figure 9 examines a result analysis of the IDCPRO-DLM with existing methods in terms of
,
, and
. The result indicates that the IDCPRO-DLM approach has demonstrated higher values of
,
, and
. Concerning
, the IDCPRO-DLM technique has offered an increased
of 98.74%, while the DBN, SVM, RNN, SNN, FFNN, and MDLIDS-SSE methodologies have exhibited lower
of 96.29%, 97.29%, 98.41%, 96.51%, 97.85%, and 98.26%, correspondingly. As well, concerning
, the IDCPRO-DLM approach has reached a maximal
of 98.53%, while the DBN, SVM, RNN, SNN, FFNN, and MDLIDS-SSE approaches have accomplished minimal
of 98%, 97.46%, 96.73%, 97.02%, 96.35%, and 96.91%, correspondingly. Thus, the experimental outcomes showed that the IDCPRO-DLM method has shown maximal performance over other models.