Radio Frequency Fingerprint-Based DSRC Intelligent Vehicle Networking Identification Mechanism in High Mobility Environment
Abstract
:1. Introduction
2. Related Works
- A novel RFF extraction method is proposed for the IEEE 802.11p preamble signal, which utilizes the ratio of the spectrum amplitudes of the superimposed short training sequence and long training sequence as the fingerprint feature. This method can effectively remove the channel interference and is less affected by noise and position movement, thus obtaining more stable device fingerprints.
- The random forest algorithm and sequential detection method are discussed to classify and identify RFF features, which adapt to the complex and changeable mobility environments and can improve the accuracy of recognition.
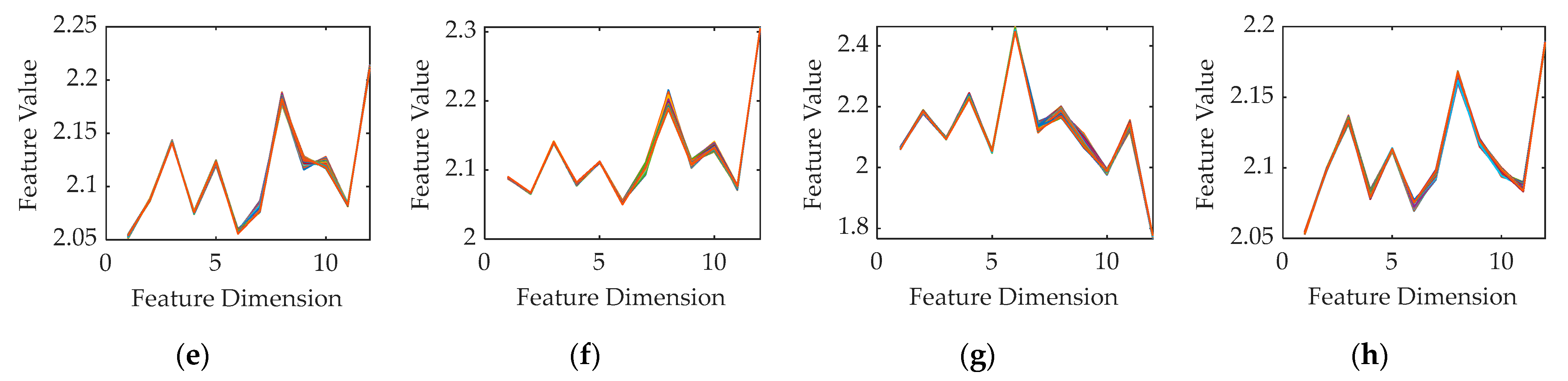
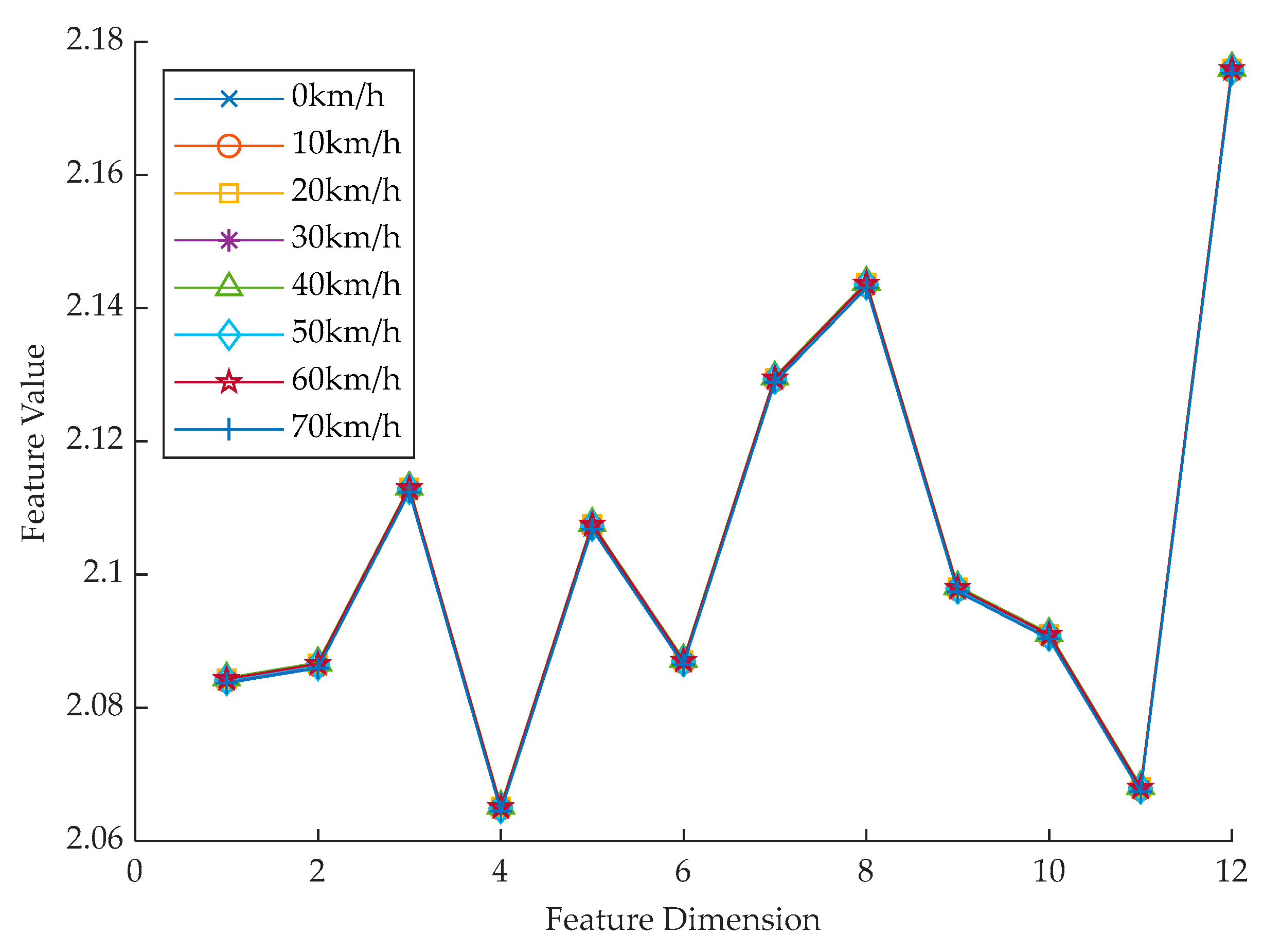
- For eight modules of the same model that can transmit IEEE 802.11p protocol signals, experiments are carried out in static state, indoor LOS moving state and partition NLOS moving state, and simulation are tested in a vehicle speed of 0–70 km/h to corroborate the stability and fine recognition performance of the extracted device RFF features in high mobility scenarios. After completing the signal acquisition and feature extraction, the identification accuracy rate of more than 99% can be achieved through the above classification and identification algorithm.
3. Signal Acquisition and Preprocessing
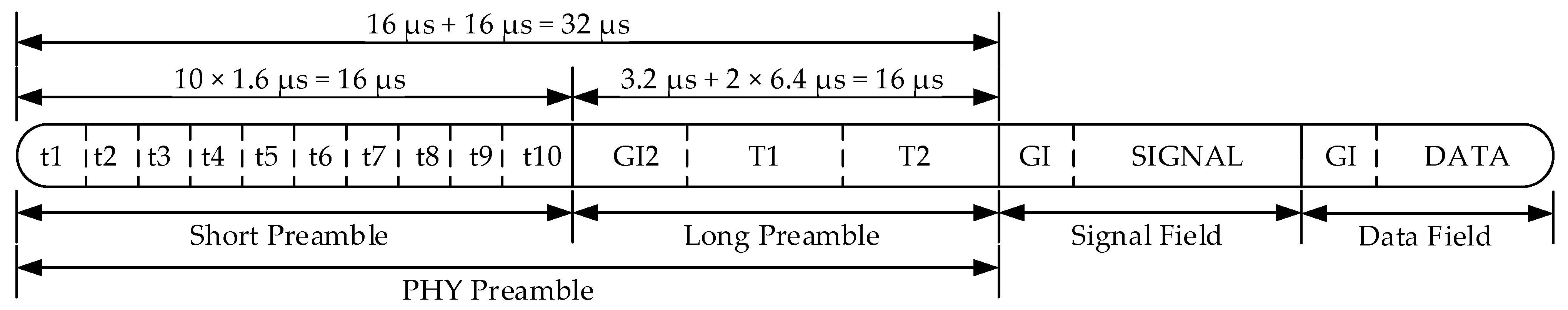
3.1. IEEE 802.11p OFDM PHY Frame
3.2. Signal Acquisition
3.3. Signal Preprocessing
4. RFF Extraction and Identification Methods
4.1. Preamble Field-Based RFF Extraction Method
4.2. Random Forest and Sequential Detection-Based RFF Identification Method
- Set the size of the training set as N, the tree number in the forest as , the number of iterations as K. For each tree, K groups of training sample sets with the size of N need to be randomly selected.
- Assuming that characteristic dimension of the sample is n, specify a constant m << n, and randomly select m dimensions from the n-dimension vector for each training set above.
- In the process of generating K groups of training set, the optimal characteristics are selected in each round of iteration. Then, the m-dimension characteristics are used to maximize the growth of each tree to obtain the model for each decision tree and the whole forest.
- Among the K classification models, the optimal random forest model is selected by using the idea of “out-of-bag estimation”. For the input test set data, the final classification result is given by synthesizing the decision results of each tree in the forest.
- First, the RFF features of devices and their statistical parameter sets are extracted to form the final feature vectors X, which are entered into the fingerprint database.
- Then, in the process of the signal collection and identification, the same length of signal is cut out from each frame newly collected, and its features are calculated in the same way to obtain the feature vector Y.
- Next, the feature vector Y is compared with the feature vectors X in the fingerprint database to calculate the similarity S. The similarity can be measured by correlation coefficient, Euclidean distance, Mahalanobis distance, etc.
- The feature vector of newly acquired signal frame whose similarity exceeds the threshold will be stored in the buffer area, indicating that this frame of received signal is subordinate to the devices in the database, and the buffered data will be used for the judgment of subsequent new frames. On the other hand, if the similarity does not reach the threshold, it means that this frame is exceptional data, which may originate from a non-registered device, and additional buffer area needs to be opened up to store it.
- The newly received frame data from the same device for the second time will not only be compared with the previously entered fingerprint database, but also with the data in the buffer area. With the increase of data in the buffer area, the judgment accuracy will correspondingly be improved. Furthermore, when the buffer area data reaches a certain amount, the stable feature vectors can be updated to the fingerprint database, so as to dynamically adjust the fingerprint feature vectors of the devices in the database.
5. Experiment Results and Discussion
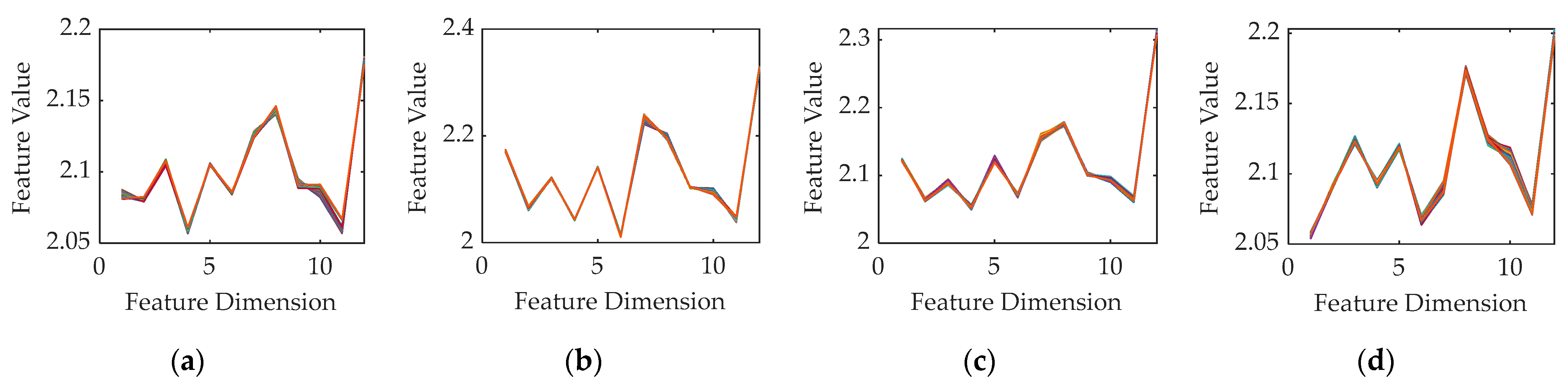
- Static state: The modules are placed at the four fixed static positions p1 to p4 marked in Figure 3. The distances between these four positions and the USRP are different, hence the received signal strength and the signal-to-noise ratios in each position are also different. At some points, there are obstacles in the path between the USRP and the transmitting modules with rich channel multipath effect, which is closer to the real communication environment. The reference signals for classifier training can be obtained in this state and can be also used for comparison with the moving state signals.
- Indoor LOS moving state: The to-be-identified communication modules are placed on the mobile trolley and the experimenter pushes the mobile trolley to walk arbitrarily in the laboratory shown in Figure 3. The average moving speed is 1 m/s, and the moving route and moving direction are random and irregular. As a result, the uncertainty of movement makes the wireless channel time-varying when the USRP receives the signal. In addition, another experimenter is allowed to walk around the laboratory freely during the movement process to simulate the disturbances by external movement. Since there is no wall obstruction in the room, it belongs to the moving multipath scene under the LOS situation.
- Partition NLOS moving state: The experimenter pushes the mobile trolley to randomly walk along the corridor separated by a wall with the laboratory as shown in Figure 3. The movement form is also an average of 1 m/s uniform motion with random moving path and moving direction including straight lines, curves, circles and other motion modes. In the whole partition wall experiment, there is no direct path between the receiving device and the transmitting device, and the signal needs to be transmitted through the wall. The experimental data in this state can be used to verify the devices classification and identification effect based on RFF features under the NLOS condition.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Huang, X.; Zhao, D.; Peng, H. Empirical Study of DSRC Performance Based on Safety Pilot Model Deployment Data. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2619–2628. [Google Scholar] [CrossRef] [Green Version]
- Zhao, Z.; Zhang, S.; Lu, Q.; Du, Z.; Ding, Y.; Shen, X. C-V2X Communication Standards: From LTE-V2X to NR-V2X; Posts & Telecom Press: Beijing, China, 2021; pp. 2–7. [Google Scholar]
- Anwar, W.; Franchi, N.; Fettweis, G. Physical Layer Evaluation of V2X Communications Technologies: 5G NR-V2X, LTE-V2X, IEEE 802. 11bd, and IEEE 802.11p. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, HI, USA, 22–25 September 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Hameed Mir, Z.; Filali, F. LTE and IEEE 802.11p for Vehicular Networking: A Performance Evaluation. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 89. [Google Scholar] [CrossRef] [Green Version]
- China Academy of Information and Communications Technology. White Paper on Vehicle Networking; China Academy of Information and Communications Technology: Beijing, China, 2018. [Google Scholar]
- Hu, A.; Li, G. Physical Layer Security in Wireless Communication: Survey. J. Data Acquis. Process. 2014, 29, 341–350. [Google Scholar] [CrossRef]
- Kebande, V.R.; Awaysheh, F.M.; Ikuesan, R.A.; Alawadi, S.A.; Alshehri, M.D. A Blockchain-Based Multi-Factor Authentication Model for Cloud-Enabled Internet of Vehicles. Sensors 2021, 21, 6018. [Google Scholar] [CrossRef] [PubMed]
- Sadiq, A.; Javaid, N.; Samuel, O.; Khalid, A.; Haider, N.; Imran, M. Efficient Data Trading and Storage in Internet of Vehicles using Consortium Blockchain. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020; pp. 2143–2148. [Google Scholar] [CrossRef]
- Gao, P.; Yang, R.; Gao, X. Research on “Cloud-Edge-End” Security Protection System of Internet of Things Based on National Secret Algorithm. In Proceedings of the 2019 IEEE 4th Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chengdu, China, 20–22 December 2019; pp. 1690–1693. [Google Scholar] [CrossRef]
- Wang, C.; Luo, W.; Mo, X.; Yang, W. Survey on Mutual Trust Authentication and Secure Communication of Internet of Vehicles. Comput. Sci. 2020, 47, 1–9. [Google Scholar] [CrossRef]
- Zhu, W.; Lin, J. Generating Correlated Digital Certificates: Framework and Applications. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1117–1127. [Google Scholar] [CrossRef]
- Agudo, I.; Montenegro-Gómez, M.; Lopez, J. A Blockchain Approach for Decentralized V2X (D-V2X). IEEE Trans. Veh. Technol. 2021, 70, 4001–4010. [Google Scholar] [CrossRef]
- Zeng, K.; Govindan, K.; Mohapatra, P. Non-cryptographic Authentication and Identification in Wireless Networks. IEEE Wirel. Commun. 2010, 17, 56–62. [Google Scholar] [CrossRef]
- Wang, N.; Wang, P.; Alipour-Fanid, A.; Jiao, L.; Zeng, K. Physical Layer Security of 5G Wireless Networks for IoT: Challenges and Opportunities. IEEE Internet Things J. 2019, 6, 8169–8181. [Google Scholar] [CrossRef]
- Yuan, H.L. Research on the Key Technologies of Wireless Network Physical Layer Authentication Based on RF Fingerprint. Ph.D. Dissertation, Southeast University, Nanjing, China, 2011. [Google Scholar]
- Li, G.; Yu, J.; Hu, A. Research on Physical-layer Security Based on Device and Channel Characteristics. J. Cryptologic Res. 2020, 7, 224–248. [Google Scholar] [CrossRef]
- Zeng, Y.; Chen, X.; Lin, Y.; Hao, X.; Xu, X.; Wang, L. Review of Radio Frequency Fingerprint Identification. Chin. J. Radio Sci. 2020, 35, 305–315. [Google Scholar] [CrossRef]
- Ali, A.; Uzundurukan, E.; Kara, A. Improvements on Transient Signal Detection for RF Fingerprinting. In Proceedings of the 2017 25th Signal Processing and Communications Applications Conference (SIU), Antalya, Turkey, 15–18 May 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Kennedy, I.; Scanlon, P.; Buddhikot, M. Passive Steady State RF Fingerprinting: A Cognitive Technique for Scalable Deployment of Co-Channel Femto Cell Underlays. In Proceedings of the 2008 3rd IEEE Symposium on New Frontiers in Dynamic Spectrum Access Networks, Chicago, IL, USA, 14–17 October 2008; pp. 1–12. [Google Scholar] [CrossRef]
- Wheeler, C.G.; Reising, D.R. Assessment of the Impact of CFO on RF-DNA Fingerprint Classification Performance. In Proceedings of the 2017 International Conference on Computing, Networking and Communications (ICNC), Silicon Valley, CA, USA, 26–29 January 2017; pp. 110–114. [Google Scholar] [CrossRef]
- Williams, M.; Munns, S.; Temple, M.; Mendenhall, M. RF-DNA Fingerprinting for Airport WiMax Communications Security. In Proceedings of the 2010 Fourth International Conference on Network and System Security, Melbourne, VIC, Australia, 1–3 September 2010; pp. 32–39. [Google Scholar] [CrossRef]
- Peng, L.; Hu, A.; Zhang, J.; Jiang, Y.; Yu, J.; Yan, Y. Design of a Hybrid RF Fingerprint Extraction and Device Classification Scheme. IEEE Internet Things J. 2019, 6, 349–360. [Google Scholar] [CrossRef]
- Chatterjee, B.; Das, D.; Maity, S.; Sen, S. RF-PUF: Enhancing IoT Security through Authentication of Wireless Nodes Using In-Situ Machine Learning. IEEE Internet Things J. 2019, 6, 388–398. [Google Scholar] [CrossRef] [Green Version]
- Zhou, X.; Hu, A.; Li, G.; Peng, L.; Xing, Y.; Yu, J. Design of a Robust RF Fingerprint Generation and Classification Scheme for Practical Device Identification. In Proceedings of the 2019 IEEE Conference on Communications and Network Security (CNS), Washington, DC, USA, 10–12 June 2019; pp. 196–204. [Google Scholar] [CrossRef]
- Xing, Y.; Hu, A.; Zhang, J.; Yu, J.; Li, G.; Wang, T. Design of a Robust Radio-Frequency Fingerprint Identification Scheme for Multimode LFM Radar. IEEE Internet Things J. 2020, 7, 10581–10593. [Google Scholar] [CrossRef]
- Wang, S.; Peng, L.; Fu, H.; Hu, A.; Zhou, X. A Convolutional Neural Network-Based RF Fingerprinting Identification Scheme for Mobile Phones. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 115–120. [Google Scholar] [CrossRef]
- IEEE Standard 802.11p-2010; IEEE Standard for Information Technology—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 6: Wireless Access in Vehicular Environments. IEEE: New York, NY, USA, 2010; 11p. [CrossRef]
- Fernandez, J.A.; Borries, K.; Cheng, L.; Vijaya Kumar, B.V.K.; Stancil, D.D.; Bai, F. Performance of the 802.11p Physical Layer in Vehicle-to-Vehicle Environments. IEEE Trans. Veh. Technol. 2012, 61, 3–14. [Google Scholar] [CrossRef]
- IEEE Standard 802.11-2016; IEEE Standard for Information Technology—Telecommunications and Information Exchange Between Systems—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEEE: New York, NY, USA, 2016. [CrossRef]
- Yu, J.; Li, G.; Hu, A. Time-domain Baseband Modeling of Radio Frequency Fingerprint for Zero-IF Digital Communication Transmitter. J. Terahertz Sci. Electron. Inf. Technol. 2021, 19, 603–616, 622. [Google Scholar] [CrossRef]
- Zhou, Z. Machine Learning; Tsinghua University Press: Beijing, China, 2016; pp. 178–181. [Google Scholar]


| Module Number | Experimental Scene | ||
|---|---|---|---|
| Static State | LOS Moving State | NLOS Moving State | |
| 1 | 100 | 100 | 99.60 |
| 2 | 100 | 100 | 100 |
| 3 | 100 | 100 | 100 |
| 4 | 100 | 100 | 100 |
| 5 | 100 | 100 | 99.50 |
| 6 | 100 | 100 | 98.70 |
| 7 | 100 | 100 | 100 |
| 8 | 100 | 100 | 100 |
| Overall Average | 100 | 100 | 99.73 |
| Module Number | Speeds (km/h) | |||||||
|---|---|---|---|---|---|---|---|---|
| 0 | 10 | 20 | 30 | 40 | 50 | 60 | 70 | |
| 1 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.90 |
| 2 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 |
| 3 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 |
| 4 | 100 | 100 | 100 | 99.50 | 100 | 100 | 99.90 | 96.70 |
| 5 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 |
| 6 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 |
| 7 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 |
| 8 | 100 | 100 | 100 | 99.25 | 100 | 94.95 | 97.55 | 99.45 |
| Overall Average | 100 | 100 | 100 | 99.84 | 100 | 99.37 | 99.68 | 99.51 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, T.; Hu, A.; Jiang, Y. Radio Frequency Fingerprint-Based DSRC Intelligent Vehicle Networking Identification Mechanism in High Mobility Environment. Sustainability 2022, 14, 5037. https://doi.org/10.3390/su14095037
Chen T, Hu A, Jiang Y. Radio Frequency Fingerprint-Based DSRC Intelligent Vehicle Networking Identification Mechanism in High Mobility Environment. Sustainability. 2022; 14(9):5037. https://doi.org/10.3390/su14095037
Chicago/Turabian StyleChen, Tianshu, Aiqun Hu, and Yu Jiang. 2022. "Radio Frequency Fingerprint-Based DSRC Intelligent Vehicle Networking Identification Mechanism in High Mobility Environment" Sustainability 14, no. 9: 5037. https://doi.org/10.3390/su14095037
APA StyleChen, T., Hu, A., & Jiang, Y. (2022). Radio Frequency Fingerprint-Based DSRC Intelligent Vehicle Networking Identification Mechanism in High Mobility Environment. Sustainability, 14(9), 5037. https://doi.org/10.3390/su14095037





