Application of New Technology in Education: Design and Implementation of Graduate Certificate Model Based on Intelligent Graph Element Technology
Abstract
1. Introduction
- (1)
- How to realize the digitization and informatization of college diploma;
- (2)
- How to prevent college diplomas from being counterfeited and forged; and
- (3)
- How to help the verifier obtain more information and improve the efficiency of the verification.
2. Literature Review
2.1. Figure Code Technology
2.1.1. Barcode Technology
2.1.2. Figure Code Technology
2.2. The Educational Application of Graph Coding Technology
2.2.1. Two-Dimensional Code Textbooks and Courses
2.2.2. University Books and Assets Management
2.2.3. Learning Record
2.2.4. Knowledge Payment
2.3. The Information Design of Graduation Certificate
3. Graduation Certificate System Model Based on IGET
3.1. Intelligent Graph Element Technology
3.1.1. Principles
3.1.2. Features
3.1.3. Educational Applications
3.2. Research Ideas
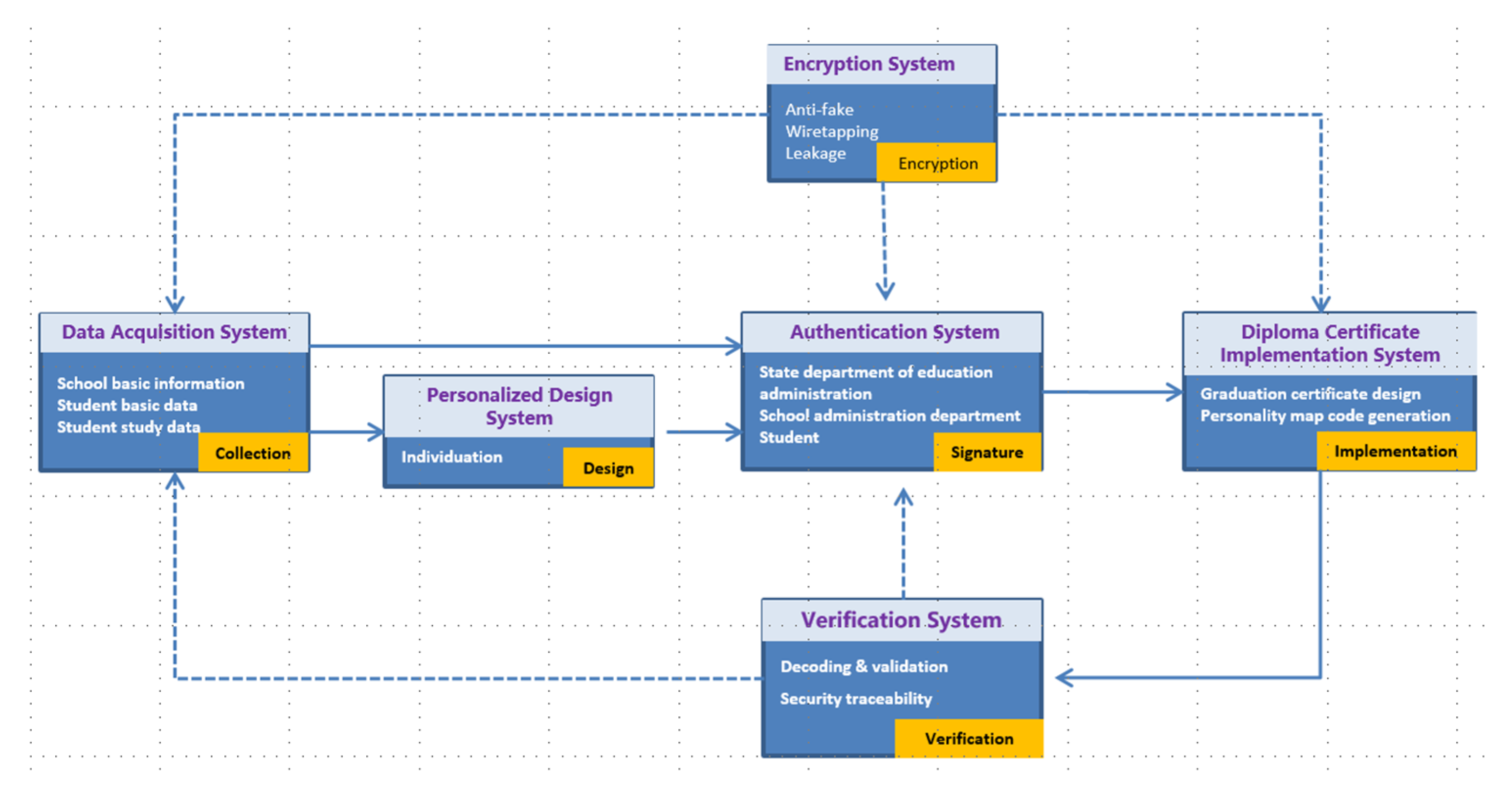
3.3. Mode of the Graduation Certificate Management System Based on IGET
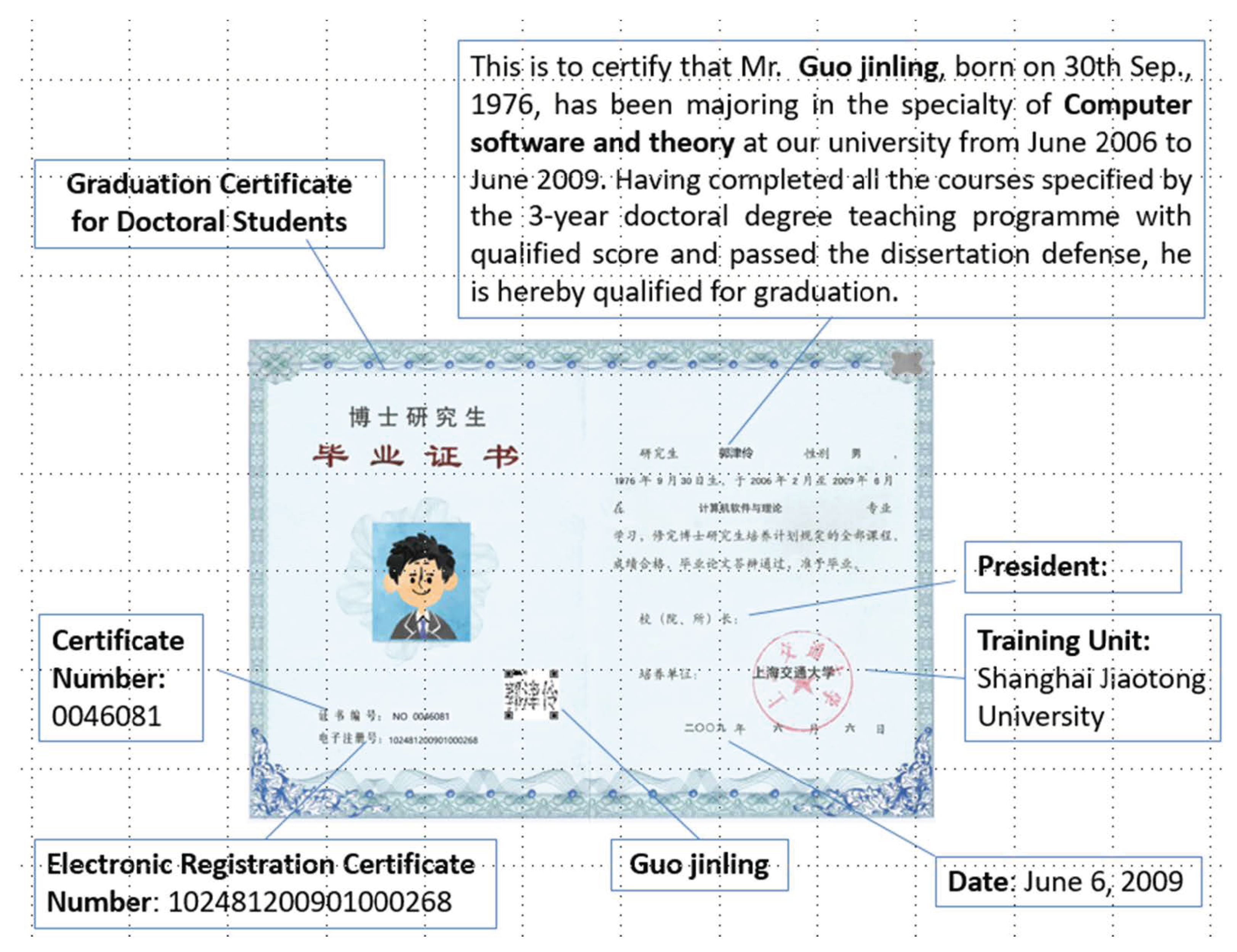
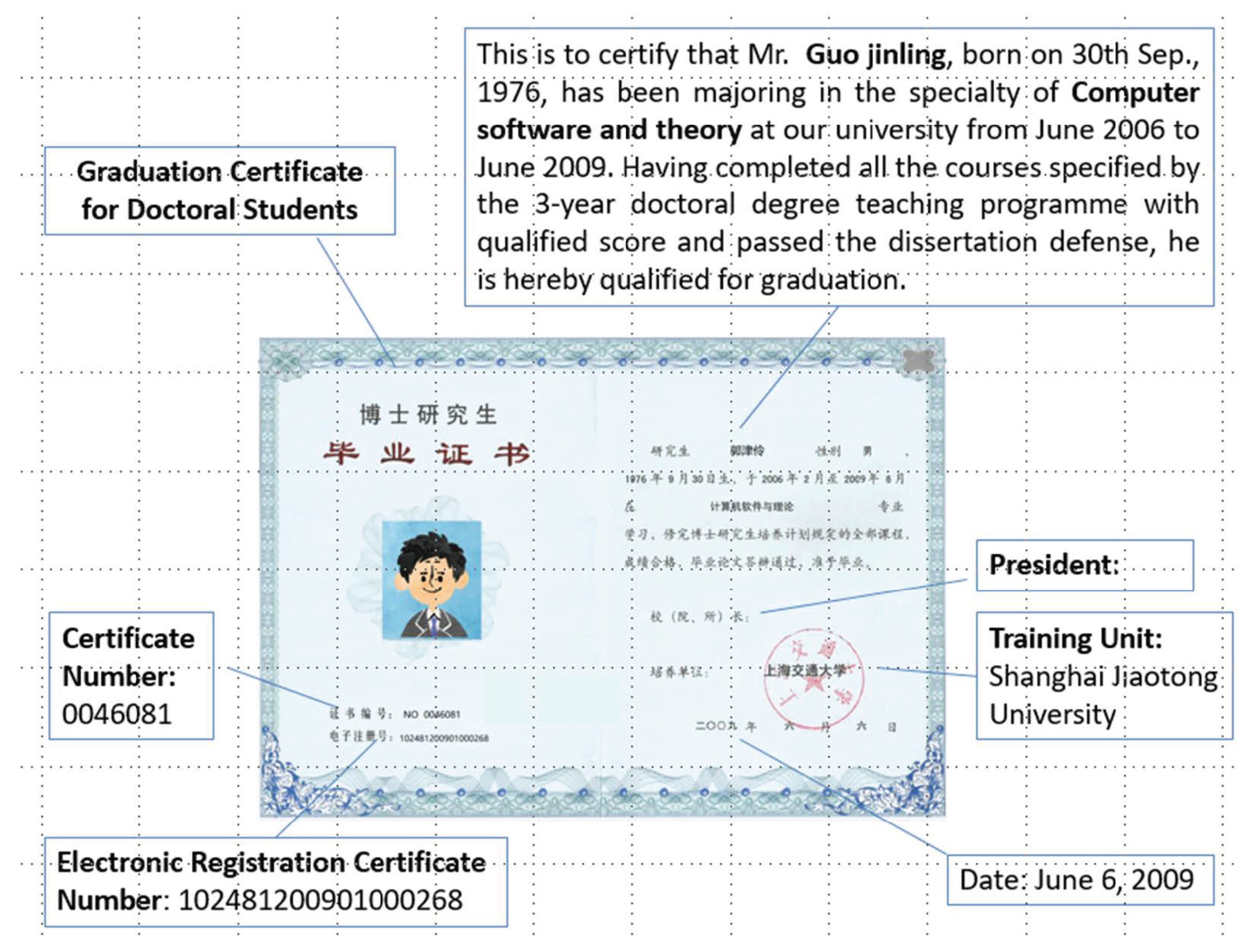
4. Realization of Graduation Certificate Case Based on IGET
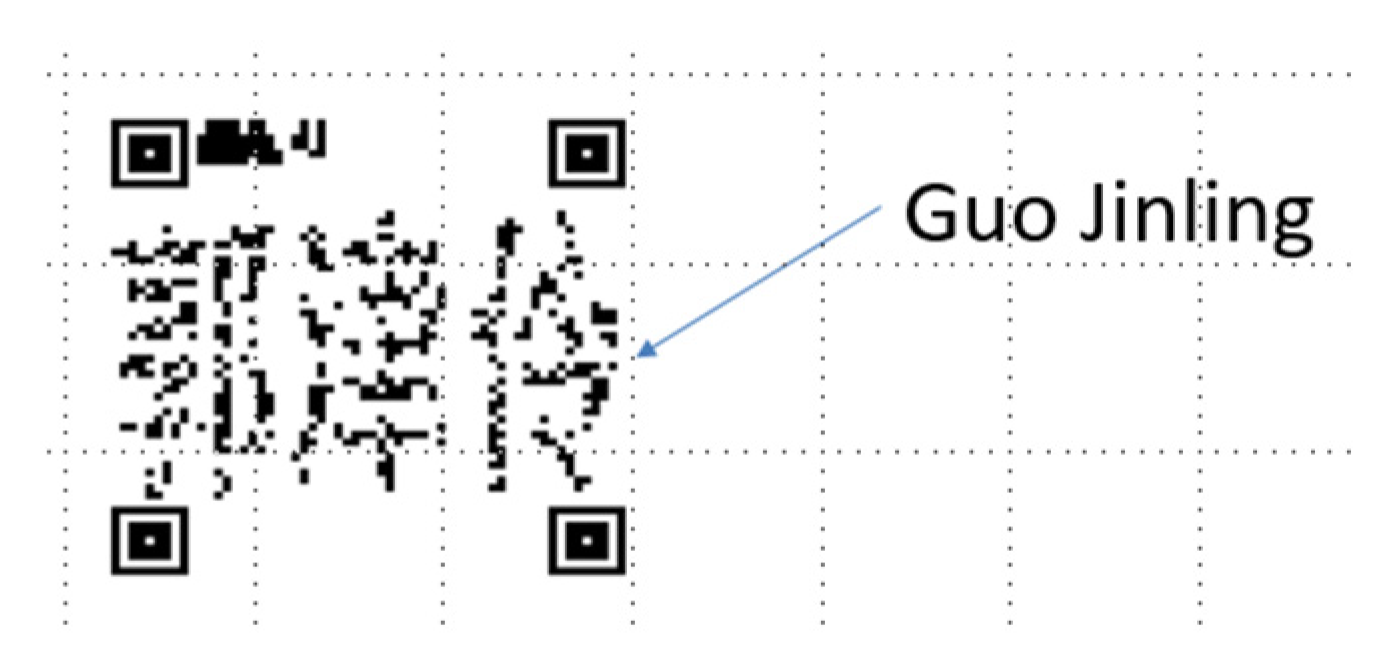
4.1. Graduation Certificate Encoding
4.2. Graduation Certificate Decoding
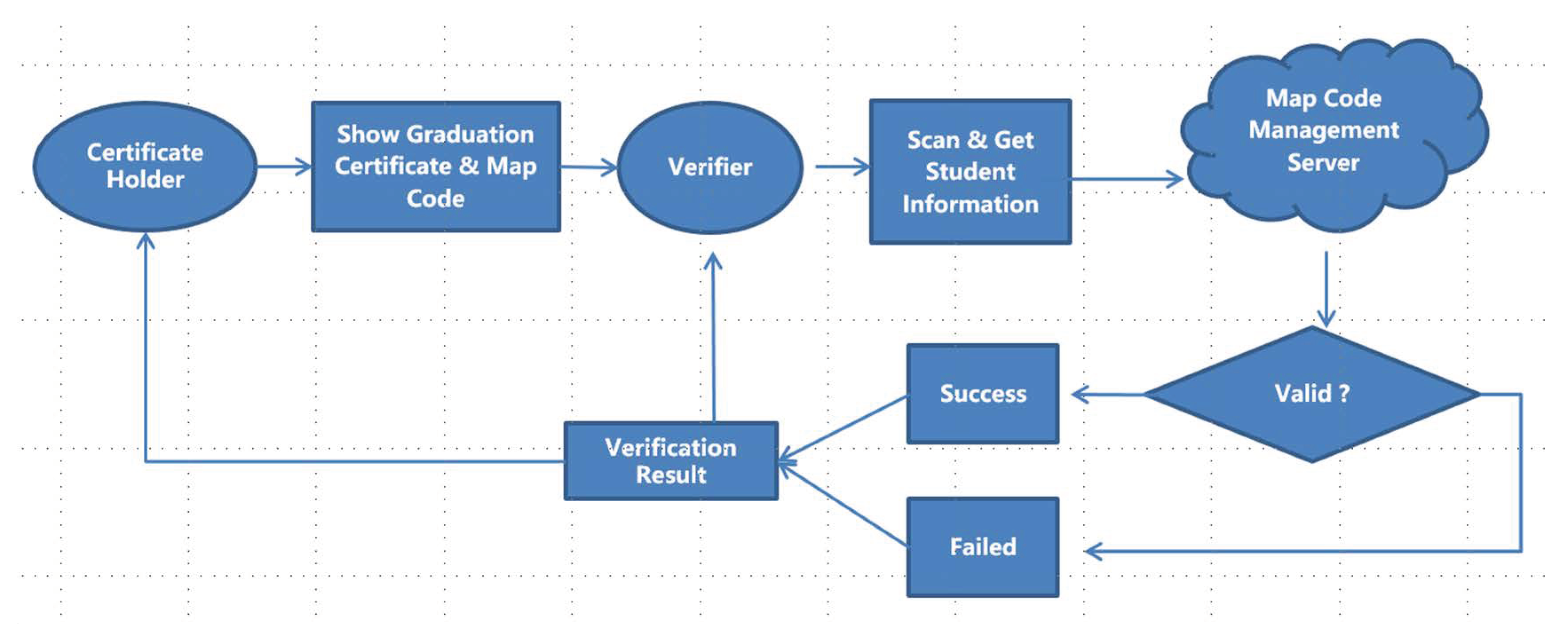
4.3. Graduation Certificate Verification
4.4. Performance Analysis of Graduation Certificate Based on IGET
- Anti-counterfeiting: The information in the smart image code on the certificate based on IGET is generated through structural encryption and special code formation rules, which cannot be tampered with or edited to ensure the exclusive rights of the diploma holder. At the same time, the smart code in the graduation certificate, using closed-source technology, cannot be copied by others. Even if it could be copied and forged, it could not be read. If the reader scans a fake certificate, the graph code management center will receive an alarm, so it is easy to crack down on counterfeiters. Therefore, the graduation certificate based on IGET can be anti-counterfeit and non-replicable, while the traditional certificate cannot.
- Amount of information: The amount of information on traditional graduation certificates is limited to the number of words on the certificates. However, the amount of information on the certificate based on IGET is large. In addition to the text on the certificate, a lot of information is stored in the intelligent code, which uses the basic elements of geometric graphics, shape relations, and colors as means of information expression, and there are N combinations, and the maximum storage of information can reach 2ⁿ ∗ Nⁿ. For the “0 and 1” encoding system, the maximum number of information stored is only 2ⁿ. Graduation certificates based on IGET have more information than traditional graduation certificates, and the information is easy to read.
- Verification efficiency: Traditional diplomas are difficult to identify. However, for a graduation certificate based on IGET, the naked eye can directly identify its authenticity. At the same time, scanning the code can also complete intelligent identification and verification, which is double anti-counterfeiting, simple, and convenient.
- Traceability: For traditional graduation certificates, tracing the origin of traditional diplomas is cumbersome. In China, the “Wang Xin” system can check authenticity of some graduation certificates using, but not all. For those who cannot use the “Wang Xin” system for verification, it will be troublesome and tedious to continue verification. For the graduation certificate based on IGET, certificate ownership is unique and has a root server, so it can be traced, and is simple and convenient.
- Data security: Traditional graduation certificates have no data confidentiality function. For the graduation certificate based on IGET, the storage, transmission, and presentation of students’ detailed information are integrated with encryption technology, so it is confidential and anti-counterfeiting. At the same time, through the establishment of verification correlation, each person has a unique code and a key with high information security, conducive to the protection of graduates’ personal information.
- Personalized design: Traditional graduation certificates cannot meet the personalized needs of students, but certificates with intelligent graphics can realize personalized and artistic designs for students and majors with special needs. The smart code style on the certificate based on IGET is also rich, which can generate text code, logo code, and art pattern code.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Smith, M.; Segura-Totten, M.; West, K.J. QR code lecture activity as a tool for increasing nonmajors biology students’ enjoyment of interaction with their local environment. J. Microbiol. Biol. Educ. 2018, 19, 19. [Google Scholar] [CrossRef] [PubMed]
- Normand, N.; Viard-Gaudin, C. A two-dimensional bar code reader. In Proceedings of the 12th IAPR International Conference on Pattern Recognition, Jerusalem, Israel, 9–13 October 1994; pp. 201–203. [Google Scholar]
- Robertson, C.; Green, T. Scanning the potential for using QR codes in the classroom. TechTrends 2012, 56, 11–12. [Google Scholar] [CrossRef]
- Ministry of Education. Circular of the Ministry of Education on the Issuance of Education Informatization 2.0 Action Plan. Available online: http://www.moe.gov.cn/srcsite/A16/s3342/201804/t20180425_334188.html (accessed on 13 April 2018).
- Alessandro, Z.; Gallo, I.; Albertini, S. Robust angle invariant ID barcode detection. 2nd Asian Conference on Pattern Recognition (ACPR2013). IEEE Comput. Soc. 2013, 11, 8. [Google Scholar]
- Tazaki, S.; Hirai, K.; Yamada, Y. Performance comparison of one dimensional code (qp) and two dimensional code with rate 2/4. ITE Tech. Rep. 1996, 20, 67–74. [Google Scholar]
- Sutheebanjard, P.; Premchaiswadi, W. QR-code generator. In Proceedings of the Eighth International Conference on ICT and Knowledge Engineering, Bangkok, Thailand, 24–25 November 2010; pp. 89–92. [Google Scholar]
- Gradel, K.; Edson, A.J. QR codes in higher ED: Fad or functional tool? J. Educ. Technol. Syst. 2012, 41, 45–67. [Google Scholar] [CrossRef]
- Munirah, M. Development of learning syntax model in determining structure pattern end of language based mobile learning QR code. In Proceedings of the International Conference on Interdisciplinary Language, Literature and Education, Yogyakarta, Indonesia, 10–11 October 2018. [Google Scholar]
- Suharianto-Pambudi, L.B.; Rahagiyanto, A.; Suyoso, G.E. Implementasi QR code untuk efisiensi waktu pemesanan menu makanan dan minuman di restoran maupun kafe. BIOS J. Teknol. Inf. Dan Rekayasa Komput. 2020, 1, 35–39. [Google Scholar] [CrossRef]
- Lu, N.S. The construction of monopoly management Quality Year. Lin’ Yearbook 2002, 13, 45–46. [Google Scholar]
- Sohu. Who Invented That QR Code You Scan Every Day? Available online: https://www.sohu.com/a/233936723_263053 (accessed on 3 June 2018).
- Tencent Cloud. How Many QR Codes Are Swept out by Wechat in a Year? Available online: https://cloud.tencent.com/developer/article/1042764 (accessed on 13 February 2018).
- Yeh, S.L.; Lin, K.T.; Lin, S.T. Color two-dimensional barcode patterns for extra encrypting sinusoidal-function scrambled data. Opt. Eng. 2016, 55, 063104. [Google Scholar] [CrossRef]
- Tencent. Three Dimensional Code Founder Chen Shengxu: Let Three-Dimensional Code to the World. Available online: https://fj.qq.com/a/20160804/019196.htm (accessed on 3 May 2016).
- Chen, W.I. How Much do You Know about Life’s “Binding” Two-Dimensional Code, Convenience and Risk? Available online: http://inanshan.sznews.com/content/2017-03/10/content_15627025_3.htm (accessed on 12 March 2017).
- Soulimane, G.; Kouninef, B.; Mohamed, S.; Djelti, M. QR codes and mobile technology used in the blended learning approach. Int. J. Technol. Diffusion. 2016, 7, 1–13. [Google Scholar] [CrossRef]
- Leone, S.; Leo, T. The synergy of paper-based and digital material for ubiquitous foreign language learners. Knowl. Manag. E-Learn. Int. J. 2011, 3, 319–341. [Google Scholar]
- Rahayu, S.; Andayani, E.P.; Chrisyarani, D.D.; Ladamay, I. The development of thematic modules based on strengthening character education (PPK) and Quick Response (QR) code. J. Phys. Conf. Ser. 2021, 1869, 012075. [Google Scholar] [CrossRef]
- Qian, X.Y. Application of two-dimensional code in textbooks published in the era of "Internet +" and practical thinking on the integration of “paper” and “number”—A case study of medical higher education textbooks. Sci. Technol. Commun. 2020, 5, 70–73. [Google Scholar]
- Chen, N.; Teng, D.C.; Lee, C.; Kinshuk. Augmenting paper-based reading activity with direct access to digital materials and scaffolded questioning. Comput. Educ. 2011, 57, 1705–1715. [Google Scholar] [CrossRef]
- Lee, J.-K.; Lee, I.-S.; Kwon, Y.-J. Scan & Learn! Use of quick response codes & smartphones in a biology field study. Am. Biol. Teach. 2011, 73, 485–492. [Google Scholar]
- Yip, T.; Melling, L.; Shaw, K.J. Evaluation of an online instructional database accessed by QR codes to support biochemistry practical laboratory classes. J. Chem. Educ. 2016, 93, 1556–1560. [Google Scholar] [CrossRef]
- Cai, J.S. Conception and implementation of standardization strategy in press and publication industry. Res. Publ. Distrib. 2006, 12, 19–22. [Google Scholar]
- China Book Business Newspaper. Two-Dimensional Code to Attack, will Set off the Book Industry Marketing? Available online: http://www.wenming.cn/book/pdjj/201210/t20121025_905138.shtml (accessed on 21 November 2012).
- Wang, Y.T. Accurate marketing of books based on two-dimensional code. Mod. Publ. 2014, 5, 41–43. [Google Scholar]
- Liu, H.Y. Teaching auxiliary publishing gradually into the “compound” era. China Publ. Media Bus. Dly. 2014, 5, 20. [Google Scholar]
- Rajendra, S.T.; Hemant, B.C. QR codes in print advertising: Elucidating Indian vogue using content analysis. Manag. Mark. 2013, 8, 353–362. [Google Scholar]
- Hau, G.B.; Siraj, S.; Alias, N.; Rauf, R.A.; Zakaria, A.R.; Darusalam, G. Research and trends in the field of technology-enhanced learning from 2006 to 2011: A content analysis of quick response code (QR-code) and its application in selected studies. Malays. Online J. Educ. Technol. 2013, 1, 54–72. [Google Scholar]
- Yamakami, T. A two-dimensional classification model of OSS: Towards successful management of the evolution of OSS. In Proceedings of the 13th International Conference on Advanced Communication Technology (ICACT2011), Gangwon, Korea, 13–16 February 2011; pp. 1336–1341. [Google Scholar]
- Dani, A.; Patil, R. QR code based library management system. J. Emerg. Technol. Innov. Res. 2020, 7, 1876–1883. [Google Scholar]
- Din, M.M.; Fazal Fazla, A. Integration of web-based and mobile application with QR code implementation for the library management system. J. Phys. Conf. Ser. 2021, 1860, 012018. [Google Scholar] [CrossRef]
- Lai, H.-C.; Chang, C.-Y.; Wen-Shiane, L.; Fan, Y.-L.; Wu, Y.-T. The implementation of mobile learning in outdoor education: Application of QR codes. Br. J. Educ. Technol. 2013, 44, E57–E62. [Google Scholar] [CrossRef]
- Latif, L.A.; Fadzil, M.; Munira, T.A.; San, N.M. Can the Use of QR codes enhance m-learning in a blended learning environment? J. Lifelong Learn. Soc. 2012, 8, 1–21. [Google Scholar] [CrossRef][Green Version]
- Li, F.Y.; He, Y.F.; Xue, Q.S. Progress, challenges and countermeasures of adaptive learning: A systematic review. Educ. Technol. Soc. 2021, 24, 238–255. [Google Scholar]
- Ali, N.; Santos, I.M.; Areepattamannil, S. Pre-service teachers’ perception of quick response (QR) code integration in classroom activities. Turk. Online J. Educ. Technol. 2017, 16, 93–100. [Google Scholar]
- Yang, J.F. Design and application of two-dimensional code service platform—A case study of two-dimensional code application service for digital education resources of higher Education Press. Mod. Educ. Technol. 2019, 7, 92–98. [Google Scholar]
- Liébana-Cabanillas, F.J.; Luna, I.R.; Montoro-Ríos, F.J. User behaviour in QR mobile payment system: The QR payment acceptance model. Technol. Anal. Strateg. Manag. 2015, 27, 1031–1049. [Google Scholar] [CrossRef]
- Sun, J.H.; Meng, M. Design of tropical fruit quality safety traceability system based on 2-dimensional bar code in manufacturing environment. Appl. Mech. Mater. 2013, 312, 511–515. [Google Scholar] [CrossRef]
- Li, F.Y. Research on the realization of graduation/degree certificate based on network technology. Res. Audio Vis. Educ. 2011, 3, 77–80. [Google Scholar]
- Lo, H. Quick response codes around us: Personality traits, attitudes toward innovation, and acceptance. J. Electron. Commer. Res. 2014, 15, 25. [Google Scholar]
- Hwang, G.J.; Fu, Q.K. Advancement and research trends of smart learning environments in the mobile era. Int. J. Mob. Learn. Organ. 2020, 14, 114–129. [Google Scholar] [CrossRef]
- Wang, T.C. Graph Module of Dynamic Geometry and Number; Hehai University Press: Nanjing, China, 2008. [Google Scholar]
- Hwang, G.J.; Xie, H.; Wah, B.W.; Gašević, D. Vision, challenges, roles and research issues of artificial intelligence in education. Comput. Educ. Artif. Intell. 2020, 1, 100001. [Google Scholar] [CrossRef]
- Li, F.Y.; He, Y.F.; Wang, T.C. Research on construction and exploration of personalized students growth system based on intelligent graph element technology. J. Distance Educ. 2021, 39, 42–51. [Google Scholar]
- Rabu, S.N.; Hussin, H.; Bervell, B. QR code utilization in a large classroom: Higher education students’ initial perceptions. Educ. Inf. Technol. 2018, 24, 359–384. [Google Scholar] [CrossRef]
- Thorne, T. Augmenting classroom practices with QR codes. TESOL J. 2016, 7, 746–754. [Google Scholar] [CrossRef]

| Performance Indicators | Traditional Diploma | Diploma Based on IGET |
|---|---|---|
| Anti-counterfeiting | Weak | Strong |
| Amount of information | Less | More, 2ⁿ ∗ Nⁿ |
| Verification efficiency | Low | High |
| Traceability | Low | High |
| Data privacy | Low | High |
| Personalized design | Low | High |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, F.; Xue, Q.; Xu, S.; Wang, T. Application of New Technology in Education: Design and Implementation of Graduate Certificate Model Based on Intelligent Graph Element Technology. Sustainability 2022, 14, 3781. https://doi.org/10.3390/su14073781
Li F, Xue Q, Xu S, Wang T. Application of New Technology in Education: Design and Implementation of Graduate Certificate Model Based on Intelligent Graph Element Technology. Sustainability. 2022; 14(7):3781. https://doi.org/10.3390/su14073781
Chicago/Turabian StyleLi, Fengying, Qingshui Xue, Shifeng Xu, and Tongchao Wang. 2022. "Application of New Technology in Education: Design and Implementation of Graduate Certificate Model Based on Intelligent Graph Element Technology" Sustainability 14, no. 7: 3781. https://doi.org/10.3390/su14073781
APA StyleLi, F., Xue, Q., Xu, S., & Wang, T. (2022). Application of New Technology in Education: Design and Implementation of Graduate Certificate Model Based on Intelligent Graph Element Technology. Sustainability, 14(7), 3781. https://doi.org/10.3390/su14073781





