1. Introduction
Smart power grid systems, such as the other types of modernized critical infrastructures, are currently attractive target of cyber attacks. Due to the fact that a power grid is arguably the most fundamental infrastructure that supports other critical infrastructures, attackers, including cyber terrorists and state-backed hackers, are motivated to attack the availability and stability of the power grid operation. While the cybersecurity for the critical infrastructure has been attracting efforts from both industry and academia, we have unfortunately witnessed a number of real world incidents in the past decade. Some of the incident almost resulted in a significant disaster (e.g., destruction of nuclear plants), and others actually caused large-scale power outage.
Due to the significance of incidents, a number of cybersecurity solutions have been proposed by academia as well as the industry to protect our critical infrastructure. For instance, in the power grid domain, IEC 62351 standards [
1] have been proposed by International Electrotechnical Commission (IEC) to define security specification for communication protocols such as IEC 61850, IEC 60870-5-104, and so forth. Moreover, cybersecurity technologies are proposed for securing modernized power grid systems, starting from intrusion detection systems to remote attestation [
2]. However, as illustrated by Tan [
2], each technology has advantages and disadvantages, and no single solution is perfect. Thus, it is desired to combine multiple, heterogeneous cybersecurity solutions that are complementary to each other, realizing defense in depth. In order to add additional layers of defense, deception technologies, which utilize “decoy” devices and/or network of them for deceiving attackers, are attracting attention.
Deception technologies can be categorized into two types: honeypot and in-network deception. The former is usually implemented as a realistic system infrastructure or devices that are intentionally exposed to the external network (e.g., the Internet) for luring attackers in the wild to collect threat intelligence. Honeypots are recently proposed and utilized in the industrial control systems domain, such as [
3,
4,
5,
6,
7,
8]. While honeypot in enterprise IT domains has a history already, solution for industrial control systems, or more broadly cyber-physical systems, are still in an early stage. More specifically, although success criteria for honeypot systems include “realism” in terms of both cyber and physical characteristics and behavior of the system, it is not trivial and, thus, is not pursued well except for a few examples, including [
9,
10]. Honeypots, particularly ones for industrial control systems, are typically implemented as the system completely isolated from the real system infrastructure, mainly due to necessity to avoid any negative impact on the real, production system. On the other hand, in-network deception technologies are blended in the real system infrastructure to monitor activities of persistent attackers in the infrastructure while misleading and/or confusing them with fake system topology and status information to mitigate or slow down the attacks. Technology of this sort for smart grid systems is still rare even in the academia, except for DecIED [
11] and DefRec [
12]. The latter requires deep integration of software-defined networking and, thus, requires major upgrades in the existing smart grid network architecture. On the other hand, the former can be integrated relatively easily by connecting a security appliance to the substation network and make application-level configuration changes on existing devices. Since these technologies are still new, to our knowledge, the effectiveness of them against real-world cybersecurity threats against real-world smart grid systems has not extensively studied yet.
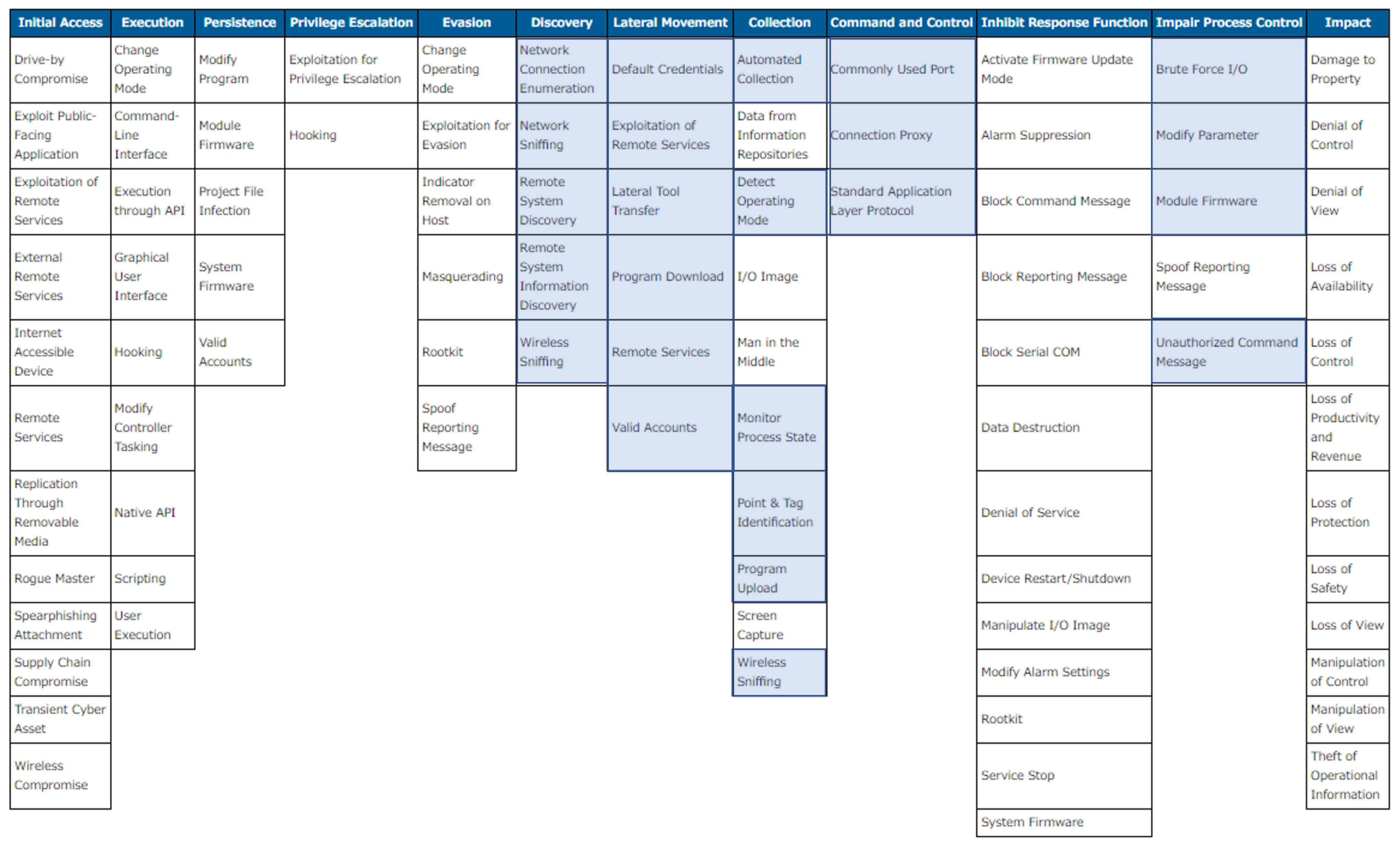
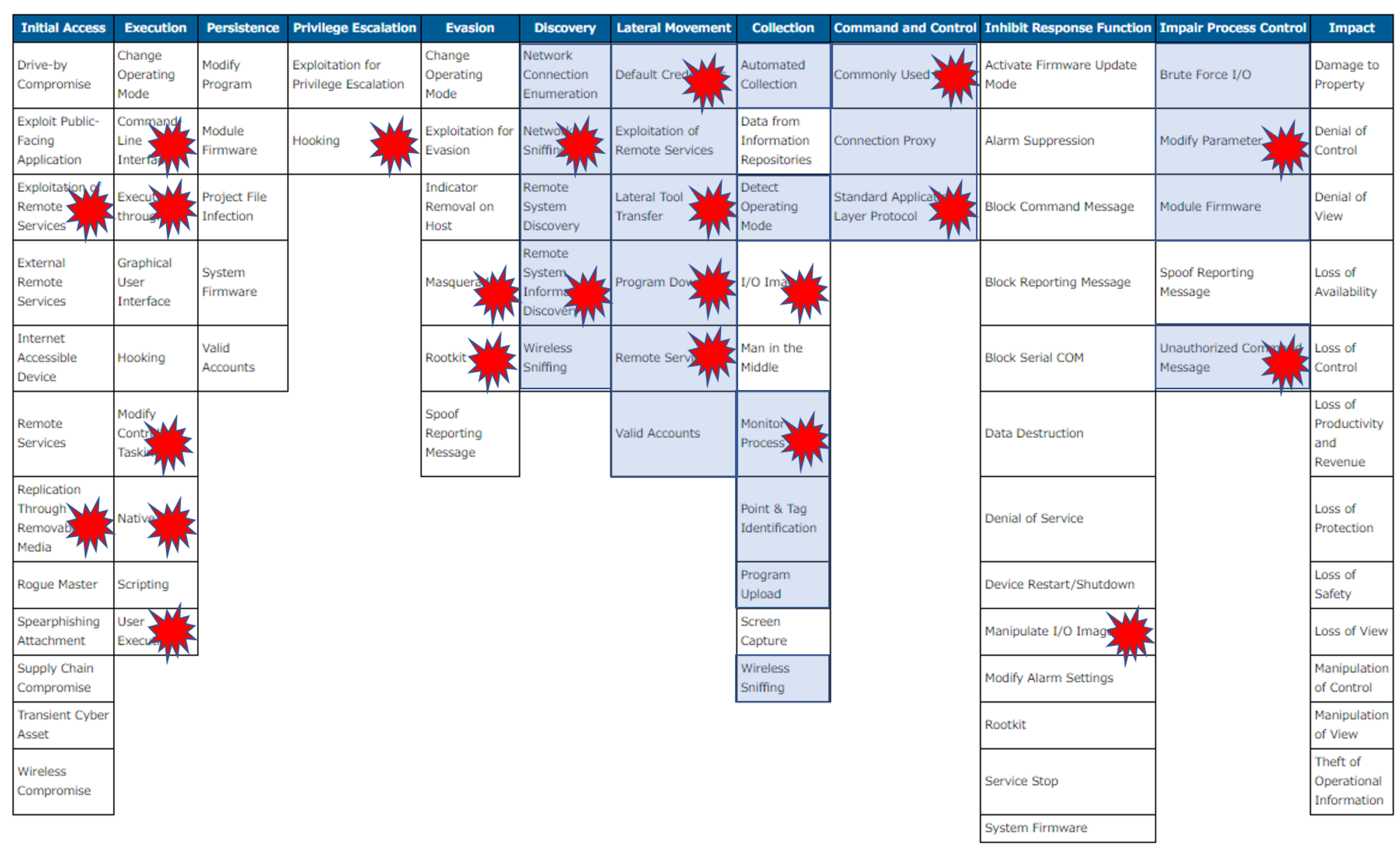
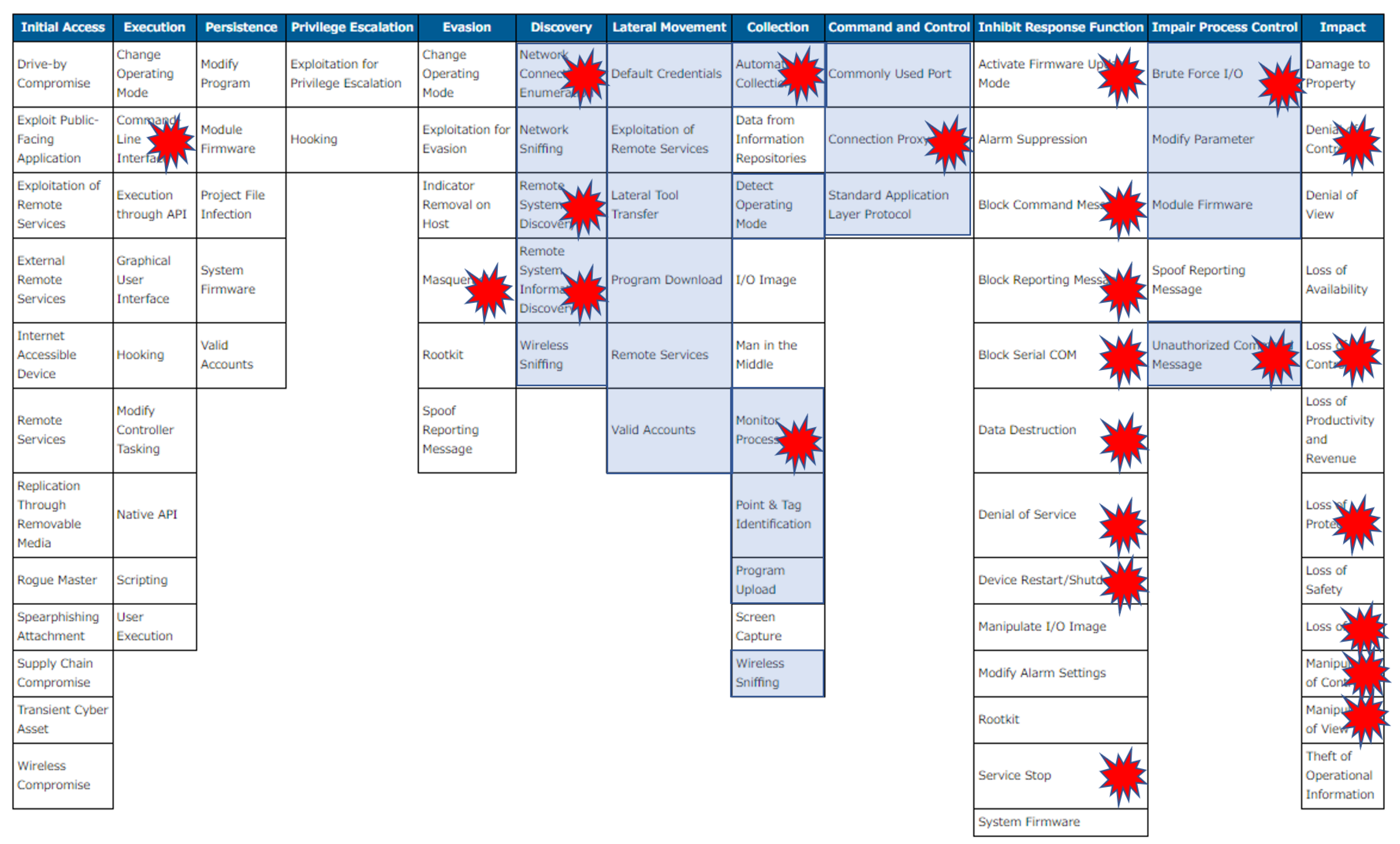
Therefore, in this paper, focusing on one specific in-network deception technology for smart grid systems we have developed, namely DecIED, we discuss the deployment strategies of the in-network deception technology towards its practical integration into a production environment. Then, using a MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) matrix for industrial control systems (ICS) [
13], which formulates cyber attack procedures and tactics at each attack phase, we discuss where and how technologies such as DecIED can contribute to mitigating attacks against ICS. We further discuss effectiveness against high-profile cyber incidents in power grid domains, such as Stuxnet [
14] and Ukraine incidents [
15]. To our knowledge, we are the first to evaluate in-network deception technologies for smart grid systems in terms of MITRE ATT&CK framework; thus, the discussion made in this paper guides the deployment of the in-network deception solutions into real-world smart grid systems to implement defense in depth.
The rest of this manuscript is organized as follows.
Section 2 elaborates modernized power grid systems based on IEC 61850 international standards. We then provide a summary of design and implementation of the deception technology for IEC 61850 compliant smart grid systems, called DecIED [
11], in
Section 3. Discussions on real-world deployment of deception technologies for smart grid systems as well as its effectiveness against high-profile, real-world incidents are made in
Section 4. Finally, we conclude the paper in
Section 5.
2. IEC 61850 Based Smart Grid Systems
IEC 61850 is the international standard for substation automation and monitoring and is widely adapted by many power grid operators. In this section, because DecIED [
11] relies on the characteristics and specification of IEC 61850 standards, we provide an overview of devices that are deployed in the IEC 61850 based smart power grid system. We then discuss communication protocols defined in IEC 61850, namely MMS (Manufacturing Messaging Specification), GOOSE (Generic Object Oriented Substation Event), and SV (Sampled Values).
2.1. ICS (Industrial Control Systems) Devices in Smart Grid
In the smart grid infrastructure, arguably substation is one of the most important components that is responsible for reliably delivering electricity from generator to consumers through control of power grid topology as well as transformation of voltage at stages. Smart grids consist of a large number of such substations. Substations are responsible for monitoring and control at different layers of power grid systems, such as generation, transmission, and distribution, and a power grid involves a large number of substations. For instance, even in a small country such as Singapore, there are over 10,000 substations, based on recent statistics.
In each substation, to realize timely and efficient management and monitoring, intelligent devices such as PLCs (programmable logic controllers) and IEDs (intelligent electronic devices) are deployed. They exchange measurements and status information with each other by using the computer network in ordre to implement a various protection functions that are necessary for preventing physical damages and grid instability [
16,
17,
18].
An IED is located at the boundary of the cyber side and physical side of the smart grid system. While they exchange IEC 61850 messages over computer network, they also interacts with physical power grid components in the substation, such as circuit breakers, transformers, and so forth. Communication among IEDs typically has stringent latency requirements [
19,
20,
21]. Communication models of IEC 61850-compliant IEDs will be elaborated in
Section 2.2.
PLCs are also often found in substation systems, and they implement logic for automated control based on power grid measurements and status [
22]. PLCs receive power grid measurements reported by IEDs, checks them against its logic and thresholds, and, when necessary, it sends out control commands to the IEDs. Such communication is typically performed by using the IEC 61850 MMS (Manufacturing Messaging Specification) protocol, which will be elaborated in
Section 2.2. In this manner, they can implement automated control that involves multiple IEDs. In this paper, we mainly focus on the design and implementation of deception IED devices, while a similar design is applicable for implementing deception PLC devices by internally using open-source implementation such as OpenPLC61850 [
23].
2.2. IEC 61850 Communication Models
International Electrotechnical Commission (IEC), which is an standard body working on standardization of power grid technologies, has defined the standardized communication to be used among devices in the substation network for substation automation, namely IEC 61850 [
24,
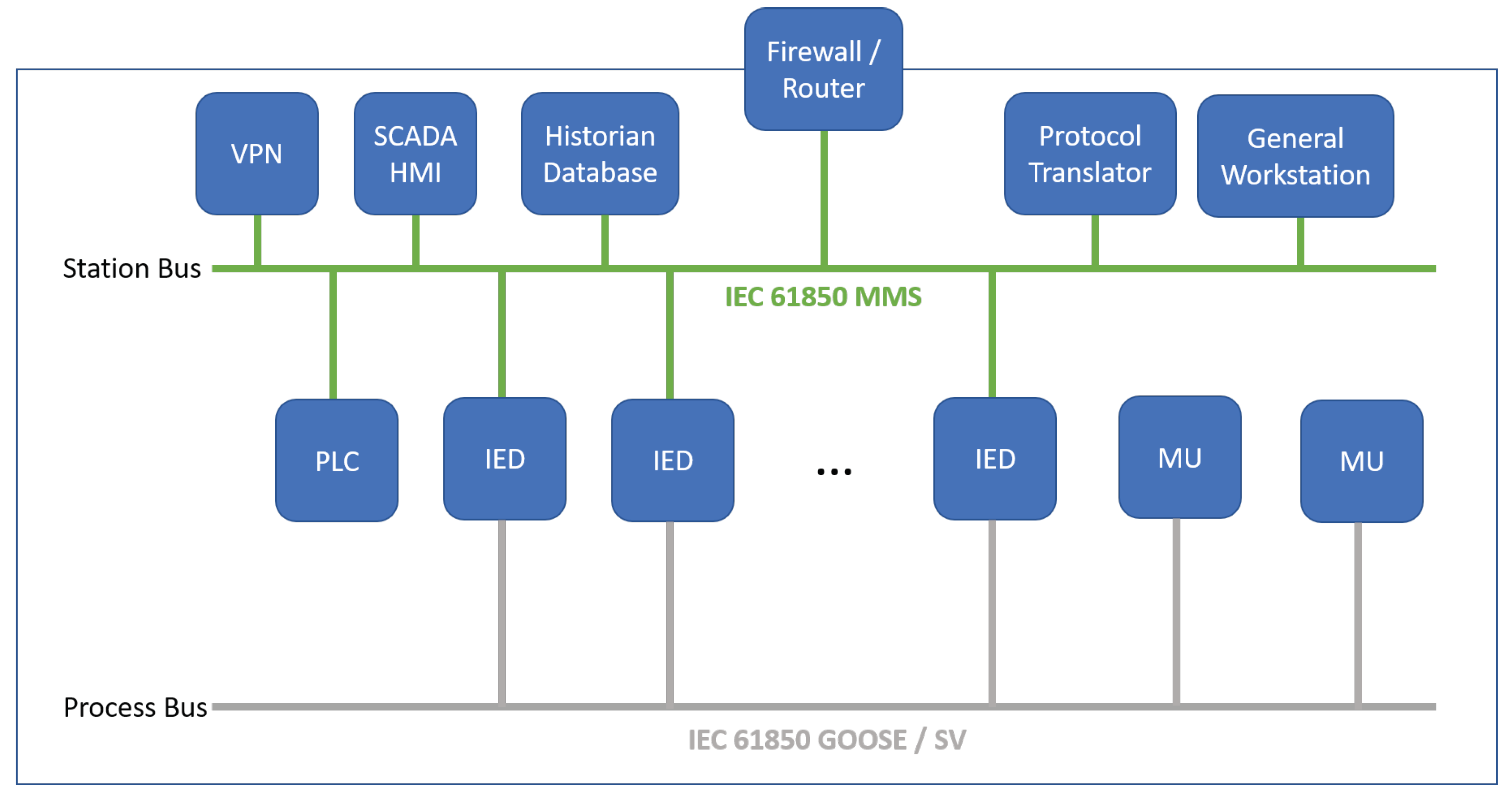
25]. As shown in
Figure 1, modernized substation systems that are designed with IEC 61850 standards, consists of multiple levels of network. SCADA/HMI (supervisory control and data acquisition/human–machine interface) and substation gateway are responsible for protocol translation between wide-area network and local-area network, general-purpose and engineering workstations, servers (e.g., VPN interfaces), routers, firewalls, and PLCs. Moreover, they are connected to “station bus” (or also called station-level network) while merging units (MUs), which are meters and sensors that collect power grid measurements, such as power flow, voltage, and frequency, and physical power grid devices that are connected to “process bus” (also called process-level network). IEDs are usually connected to both buses to interact with both the cyber and physical side of the smart grid system. Station-bus communication is performed via IEC 61850 MMS (Manufacturing Messaging Specification) protocol while the communication in the process bus utilizes IEC 61850 GOOSE (Generic Object Oriented Substation Event) and SV (Sampled Values) protocols. Communication observed in typical substation systems includes the following.
SCADA/HMI sends remote control commands and interrogation commands (i.e., request for measurements) to IEDs and PLCs using IEC 61850 MMS. While the former is observed only when a human operator takes an action, the latter is usually automated and periodic. PLCs also utilizes MMS protocol for querying measurements and status from IEDs, and if the input from IEDs matches a pre-programmed criteria, it sends out control commands for automated control. The MMS protocol is a unicast communication over TCP/IP, where IED works as the server and SCADA/HMI, PLCs, etc., work as clients. MMS also supports a periodic reporting service, in which IEDs periodically pushes reports to the requester by using the established TCP/IP session.
Process-bus communication is more time critical and requires lower latency (e.g., less than 2 ms for the most critical communication [
21]). Thus, IEC 61850 GOOSE and SV protocols used there employ link-layer multicast communication with a publisher–subscriber model [
26]. Each IED (and MUs) can play roles as either or both of publisher and subscriber. While the format of payload is very similar, the purposes of GOOSE and SV are different. The GOOSE protocol is utilized for announcing status updates (e.g., open/close status of circuit breaker that the IED is responsible for) with other IEDs. SV protocol, on the other hand, carries digitized analog measurements [
27] from the power grid, including voltage, current, etc. Both protocols are the key enablers for protection functions such as over/under-current protection, over/under-voltage protection, and differential protection. We can find another major difference between GOOSE and SV in terms of communication model. SV is always sent with a very high frequency and with fixed interval. For instance, in a 50 Hz power grid system, the specification requires that 4000 SV messages are sent for each data point. On the other hand, GOOSE is sent with a longer interval (hundreds of milliseconds to seconds) if there is no status update event. However, messaging frequency should be increased (up to a few milliseconds interval) to ensure timely delivery of the status change.
2.3. Cybersecurity Incidents against Modernized Power Grid systems
In this section, we briefly discuss the overview of notable cybersecurity incidents in the smart grid domain.
2.3.1. Stuxnet Worm
The first notable incident in power grid sectors is Stuxnet worm that targeted Iranian nuclear power plants in 2010 [
14]. Traditionally, the control system, including a SCADA (supervisory control and data acquisition) system or OT (operation technology) system, which is a system for monitoring and controlling physical plants, in industrial control systems is considered secure owing to so-called “air-gap,” which refers to its isolation from the other systems or network. However, Stuxnet worm succeeded in bypassing this air gap by taking advantage of its capability to infect via a USB drive. The USB drive carrying this malware was connected to a workstation in the SCADA infrastructure. Stuxnet targeted an engineering workstation that were used to manage PLCs in the system, which then maliciously re-configured PLCs to manipulate the rotation speed of the centrifuge units of the nuclear power plant. In addition, this sophisticated malware sent apparently normal data to the SCADA HMI (human machine interface) system to hide the situation.
2.3.2. Ukraine Power Plant Attack in 2015
In 2015, power plants in Ukraine was attacked by hackers [
15]. This was a very well prepared attack, and it is said that the attack started 6 months before the incident. The attacker first utilized a traditional cyber attack strategy. Phishing emails were sent to the targeted employees of power grid companies, and their computers were infected with a malware called BlackEnergy. The BlackEnergy malware conducted information gathering in the enterprise IT system to find meaningful information, such as the presence and configuration of VPN (virtual private network) interfaces to enable remote access to OT infrastructure as well as login credentials. Then, the attacker utilized such information to penetrate the OT infrastructure, bypassing the air gap in a manner different from Stuxnet. After having footprint in the OT systems, the attacker compromised SCADA control system, which was then remotely manipulated to inject malicious control commands to open a large number of circuit breakers. The attacker also deployed measures to delay the recovery actions. The incident, as a result, caused a massive power outage that lasted for hours.
2.3.3. CrashOverride/Industroyer
Ukrainian power plants were attacked again in 2015. In this incident, a malware called Industroyer or CrashOverride was utilized [
28]. One notable capability of the malware is that it alone can send messages compliant to standards used in the modernized power grid systems, such as IEC 61850 and IEC 60870, under the control by an remote attacker via command and control channel. This implies that, once this malware infects any of the devices in the power grid control system, an attacker could inject malicious control commands without compromising the SCADA HMI workstation, as was the case in 2015 incident discussed earlier.
2.3.4. Stealthy, False Data Injection Attacks
While it is not yet witnessed in real-world systems, stealthy attacks to confuse or mislead control systems by means of false, malicious data injection are attracting emerging attention [
29,
30,
31]. While malicious data injected into the target system may vary depending on target system components (e.g., state estimators and protection relays) as well as the purpose of attackers, the attack vector to be utilized before mounting such attacks would be either remote hacking of any of the devices in the control infrastructure or planting malwares in them. Once these are successfully performed, the compromised devices, either autonomously or under remote control by attackers via command and control channels, start sending fake data to disturb the system.
3. DecIED: Deception Technology for IEC 61850 Based Smart Grid
In-network deception is one type of cybersecurity solution that introduces a number of decoy (virtual) devices that are apparently indistinguishable from real devices in the real system. The aim of the in-network deception technology is to counter attackers or malware that have successfully penetrated into the infrastructure somehow. Specifically, by presenting the fake cyber-physical system view to the attacker, we can make the attackers’ reconnaissance activities difficult and less accurate. It is even possible to help us detect active probing by attackers or lateral movements by them. Due to the fact that the in-network deception solution for smart grid systems is almost non-existent, as a proof-of-concept solution to provide in-network deception for IEC 61850 compliant substation systems,
DecIED has been developed, which pretends to be a real, IEC 61850 compliant IED (also called a
base IED hereafter for description) [
11]. Below, we summarize requirements for deception devices for smart grid systems, and then discuss the system design for realizing these goals.
- 1.
Imitation of device characteristics visible to attackers;
- 2.
Imitation of communication model, patterns, and timings;
- 3.
Sufficient scalability and easy integration into existing infrastructure.
The first property is needing to look indistinguishable from attackers’ (including malware) perspective, who may be attempting to find target devices by means of network scanning. The information that an attacker can obtain by active or passive network scanning would include hardware (MAC) addresses, which include the identity of device vendors, open network ports and network serving running on the device, and device or OS fingerprints, which are calculated by inspecting protocol stack implementation of OS running on each device. For instance, by using a popular tool such as Nmap [
32], these can be made available to the attackers. DecIED addressed this challenge by studying real IED devices deployed in a smart grid security testbed [
22] to study such device characteristics. The device fingerprints collected from the real devices are also configured on the deception devices by using an open-source software called Honeyd [
4].
Secondly, in the industrial control systems, behaviours of devices, including communication patterns that are visible to attackers, are largely deterministic. For instance, SCADA HMI workstation would be periodically querying messages measurements and device status from all devices by using IEC 61850 MMS protocol. PLCs are also collecting information of power grid systems in the same manner for the sake of automated control. IEC 61850 GOOSE and SV protocols are utilized communication among IEDs. Deception devices also implement the same communication patterns. The important thing here is that the deception device should be equally interrogated by SCADA HMI and PLCs and also exchanging power grid measurements and statuses similar to real devices. To achieve this, it is mandatory for deception devices shares (or replicates) and the cyber-physical system view of the power grid system to imitate the real device. DecIED addressed this challenge by taking advantage of the IEC 61850 GOOSE and SV messages exchanged on the process bus. Due to the fact that these messages are sent over the link-layer multicast, the messages are received by all devices on the same network, including deception devices at the same time. Moreover, DecIED can be configured with the same internal logic as the real IED (i.e., how the measurements is processed and how the IED react to them) to imitate device behaviors.
Last but not the least, because one of the key success criteria for in-network deception is to deploy as many deception devices as possible, scalability is important. For instance, one of the strategy of deception technology is the
k-anonymous smoke screen [
33], which deploys
deception devices for each real device to lower the probability for an attacker to successfully pinpoint the real device; obviously, larger
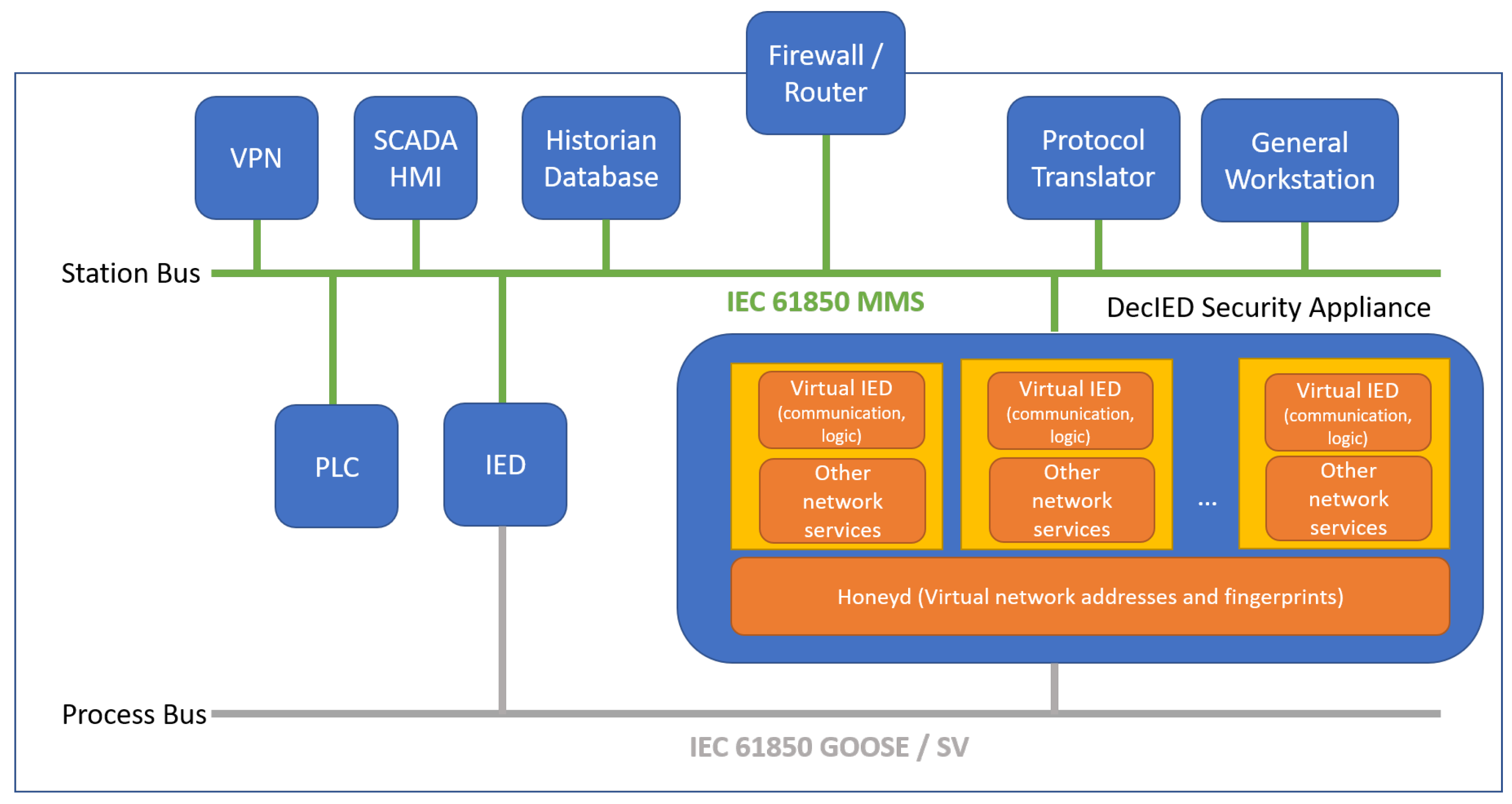
k implies better security. At the same time, it is also important that the solution can be easily deployed and integrated into the existing infrastructure. Due to the fact that update and upgrade of devices or infrastructure is a universal challenge in the industrial control systems, this property is crucial. In this direction, all DecIED deception devices are run on a single security appliance box (e.g., industrial PC) as light-weight processes, each of which binds virtual network interface equipped with different network addresses.
The architecture overview of DecIED is illustrated in
Figure 2. As demonstrated in [
11], the developed DecIED can realize an imitation of device characteristics and observable behaviours such as communication patterns. Moreover, in terms of scalability, we confirmed that more than 200 DecIED instances can stably run on a commodity industrial PC. Discussion on how the deployment of DecIED is possible without negatively affecting the existing, real system infrastructure is also included in the same paper. For a detailed discussion on design, implementation, and evaluation, we refer the interested readers to [
11]. The following section discusses how DecIED deployment can help counter or mitigate cybersecurity incidents that were witnessed in recent years.
5. Conclusions
Deception technologies are promising solutions that can provide an additional layer of security for protecting modernized industrial control systems, including smart power grid systems. On the other hand, such a technology in the industrial control system domain is still in its early stage. Therefore, it is not yet systematically studied where and how in-network deception technologies contribute in order to counter cyber attacks against industrial control systems. In this paper, we elaborated the positioning of in-network deception technologies in terms of the MITRE ATT&CK matrix. We further discussed one concrete implementation of in-network deception technologies for IEC 61850 based smart grid systems, DecIED, as well as deployment strategies based on state-of-the-art technology from academia to qualitatively evaluate the mitigation provided by it. Evaluation based on real-world cyberattack scenarios against smart grid is also provided. Based on our observation, in-network deception technologies, specifically DecIED [
11], are considered promising for countering high-profile security incidents that we have witnessed in the past decade. We hope the discussion made in this paper, along with the study on other types of cybersecurity solutions for smart grid [
2], will encourage and guide deployment planning of in-network deception solutions to effectively realize defense in depth.
Our future work includes the evaluation of in-network deception technologies against sophisticated/intelligent human attackers, which could utilize a number of heuristics and domain knowledge to identify decoy devices from real ones. Such an evaluation is possible by using it in a blue-team/red-team hacking competition events involving cybersecurity experts (similar to [
36]) or to deploy it as part of a honeypot, which is made accessible to real attackers or malware on the Internet.