Overview of Protocols and Standards for Wireless Sensor Networks in Critical Infrastructures
Abstract
1. Introduction
2. Critical Infrastructures
2.1. Critical Infrastructure Definition
2.1.1. The European Union Perspective
2.1.2. The United States Perspective
2.2. Critical Infrastructure Sectors
Core Sectors
- Finance
- Government/Public Administration
- Telecommunications
- Emergency/Rescue Services
- Energy
- Health Services
- Food
- Transportation
- Water Supply
2.3. Critical Infrastructures and Industry 4.0
3. Communication Technologies and Wireless Sensors Networks
3.1. Wireless Sensors Networks Categorization
3.1.1. Categorized by Physical Environment
- Underground: WSNs deployed beneath the Earth’s surface, often used in mining or geological monitoring.
- Terrestrial: these networks operate on land, making them suitable for a wide range of applications such as environmental sensing and smart agriculture.
- Underwater: submerged WSNs are essential for oceanographic research, aquatic habitat monitoring, and underwater exploration. Multimedia: these networks handle multimedia data and are valuable in applications like surveillance, video streaming, and multimedia content distribution.
- Mobile WSNs: mobile WSNs are dynamic and adaptable, making them ideal for scenarios like wildlife tracking, vehicular networks, or mobile healthcare solutions [23].
3.1.2. Categorized by Different Network Topologies
- Star: in a star topology, all sensors communicate directly with a central hub or gateway, offering simplicity in deployment.
- Mesh: sensors in a mesh network communicate through neighboring nodes, ensuring self-healing capabilities and redundancy.
- Tree: with a hierarchical structure, data flow from leaf nodes to a central sink node, enabling efficient data aggregation.
3.1.3. Categorized by Applications
- Health monitoring: WSNs play a crucial role in healthcare, employing advanced medical sensors to monitor patients both in hospital and at home. These WSNs facilitate real-time monitoring of vital signs through wearable hardware. The health applications of WSNs encompass patient-wearable monitoring, home assisting systems, and hospital patient monitoring.
- Urban: WSNs offer diverse sensing capabilities that open the door to obtaining extensive information about a specified area, whether indoor or outdoor. WSNs serve as a versatile tool for measuring the spatial and temporal characteristics of various phenomena within urban settings, presenting numerous applications. In the urban context, WSNs find widespread use in areas such as smart homes, smart cities, transportation systems, and structural health monitoring.
- Flora and fauna: The essential aspects of both plant life (flora) and animal life (fauna) are crucial for any nation. The primaries are greenhouse monitoring, crop monitoring, and livestock farming. The illustration also highlights the prevalent types of sensors commonly employed in these applications.
- Environmental: The use of WSNs can enhance environmental applications requiring constant monitoring in challenging and distant locations. This includes subcategories like water monitoring, air monitoring, and emergency alerting, each involving specific types of sensors. The subsequent subsection delves into the examination of WSNs designed for these environmental applications.
- Military: The military pioneered WSNs, with early research (such as Smart Dust in the late 1990s) aiming at creating minuscule yet efficient sensor nodes for espionage. Subsequent technological advancements expanded WSN applications in the military, with a focus on battlefield surveillance, combat monitoring, and intruder detection. Various sensor types are now commonly employed in these military WSN applications.
- Industrial: Industrial wireless sensor networks (IWSNs) present numerous benefits for facilitating the intricate and dynamic processes within industrial settings. Thanks to their effortless setup, unrestricted mobility, and smart data routing capabilities, IWSNs are emerging as a promising communication option for industrial applications [23,24,25,26].
3.2. Standards and Protocols
3.2.1. Standardization Organizations
- IEEE (Institute of Electrical and Electronics Engineers): On 1 January 1963, the American Institute of Electrical Engineers (AIEE) and the Institute of Radio Engineers (IRE) joined forces to establish the Institute of Electrical and Electronics Engineers (IEEE). Initially, IEEE boasted 150,000 members, with 140,000 based in the United States. As the early 21st century unfolded, IEEE’s influence spanned 39 societies, 130 journals, and over 300 annual conferences, with a focus on diverse areas like nanotechnologies, bioengineering, and robotics. From jet cockpits to medical imaging, electronics have become omnipresent. As of 2020, IEEE’s membership exceeded 395,000 across 160 countries, solidifying its status as the largest global technical professional organization through a network of units, publications, and conferences [27].
- ISO (International Organization for Standardization): In 1946, a gathering of 65 representatives from 25 nations convened to deliberate on the future of international standardization. This culminated in the official establishment of ISO in 1947, comprising 67 technical committees. Since its inception, ISO has regularly disseminated information on its technical committees and published standards and organizational updates. Functioning as an independent non-governmental international entity, ISO boasts a membership of 169 national standardization bodies. Through collaborative expertise, ISO facilitates the development of voluntary, consensus-driven, and globally pertinent international standards, fostering innovation and delivering solutions to worldwide challenges [28].
- CEN (European Committee for Standardization): CEN, the European Committee for Standardization, serves as a consortium uniting national standardization bodies from 34 European nations. This collaborative platform is dedicated to formulating European standards and technical documents across diverse products, materials, services, and processes. Recognized by the European Union and the European Free Trade Association, CEN, along with CENELEC and ETSI, is entrusted with the task of devising voluntary standards at the European level. In the interest of international and European standardization, CEN collaborates with CIE, aiming to leverage the knowledge and expertise within each organization through a formalized agreement [29].
- IEC (International Electrotechnical Commission): In 1906, the International Electrotechnical Commission (IEC) was established in London after a proposal at the 1904 International Electrical Congress. The congress recognized that the diversity in electrical systems worldwide was hindering progress. The IEC’s inaugural meeting included representatives from multiple countries, with Lord Kelvin elected as the first president. Today, the IEC, a global non-profit organization, unites over 170 countries and oversees 20,000 experts worldwide. Celebrating its centenary in 2006, the IEC has adapted to 21st-century technological advancements, establishing new technical committees for areas like fuel cells, assessment methods for human exposure to electric and electromagnetic fields (including 5G), avionics, electronic displays, nanotechnology, marine energy generation, solar thermal electric plants, printed electronics, electrical energy storage systems, wearable electronic devices, personal e-transporters, and more. This reflects the IEC’s commitment to staying current with evolving technologies and fostering standardization in diverse fields [30].
- IPC (Institute of Printed Circuits): Founded in the autumn of 1957, the Institute of Printed Circuits, or IPC, has remained committed to eliminating supply chain challenges, establishing industry standards, and fostering industry progress. As a worldwide trade association, IPC is devoted to enhancing the competitive excellence and financial prosperity of its electronics industry members. To achieve these goals, IPC will allocate resources to management improvement, technology enhancement programs, formulation of pertinent standards, and environmental conservation. IPC aspires to be a globally respected organization, recognized for leadership and its significant role in providing standards and quality programs for the electronics industry [31].
- ISO/IEC 27001
- ISO 27002
- ISO 15408
- IEC 62351 series
- IEC 62443 series
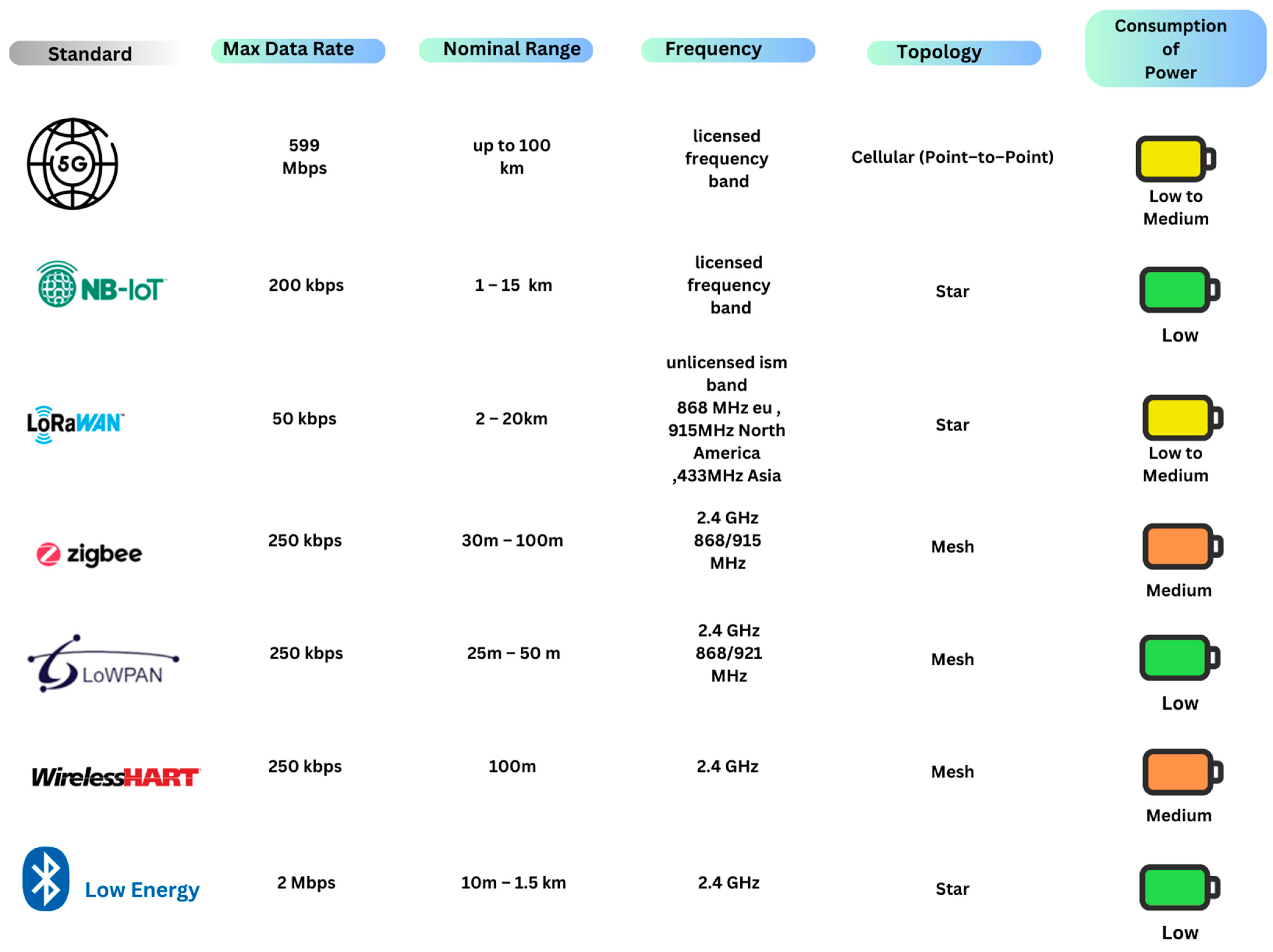
3.2.2. Wireless Protocols
- 4G Cellular (Fourth Generation)
- 5G Cellular (Fifth Generation)
- ZigBee
- Star topology: primarily utilized in home networks, it features a single coordinator device, with all other end devices communicating directly with it; however, a drawback is the vulnerability of the entire network if the coordinator malfunctions.
- Tree topology: Comprising a root and its dependent nodes where the coordinator acts as the root and end devices are placed on the last branches. While enabling the connection of more nodes and covering a larger area, this structure introduces transmission delays, and the failure of one node can impact others.
- Mesh topology: Representing the most intricate network structure, every device can communicate directly with another, either through direct links or intermediaries. This topology is considered superior for ZigBee networks, as it facilitates data continuity by allowing another device to take over if one node fails [45].
- NB-IoT
- LoRaWAN
- Bluetooth Low Energy
- WirelessHART
- 6LowPAN
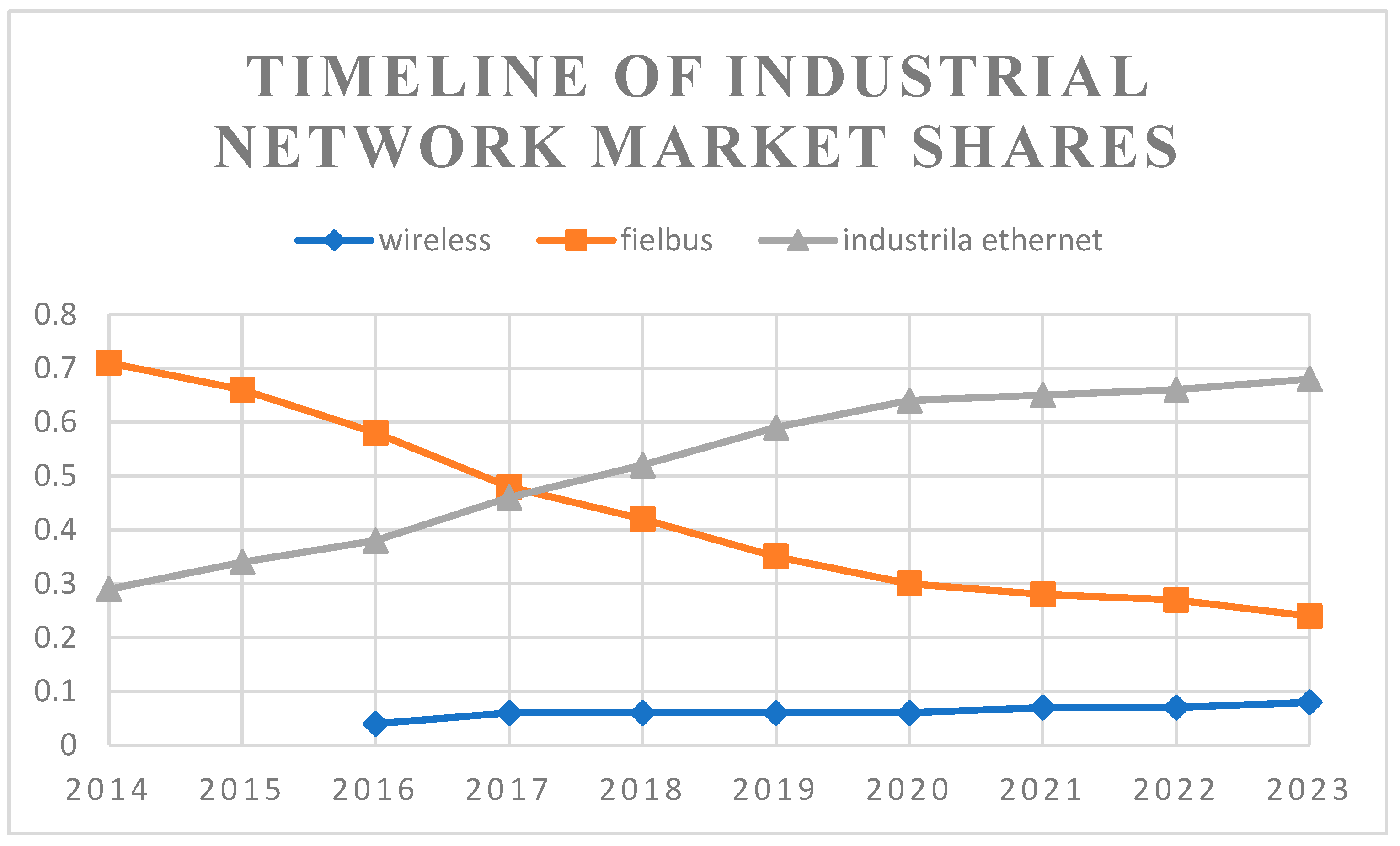
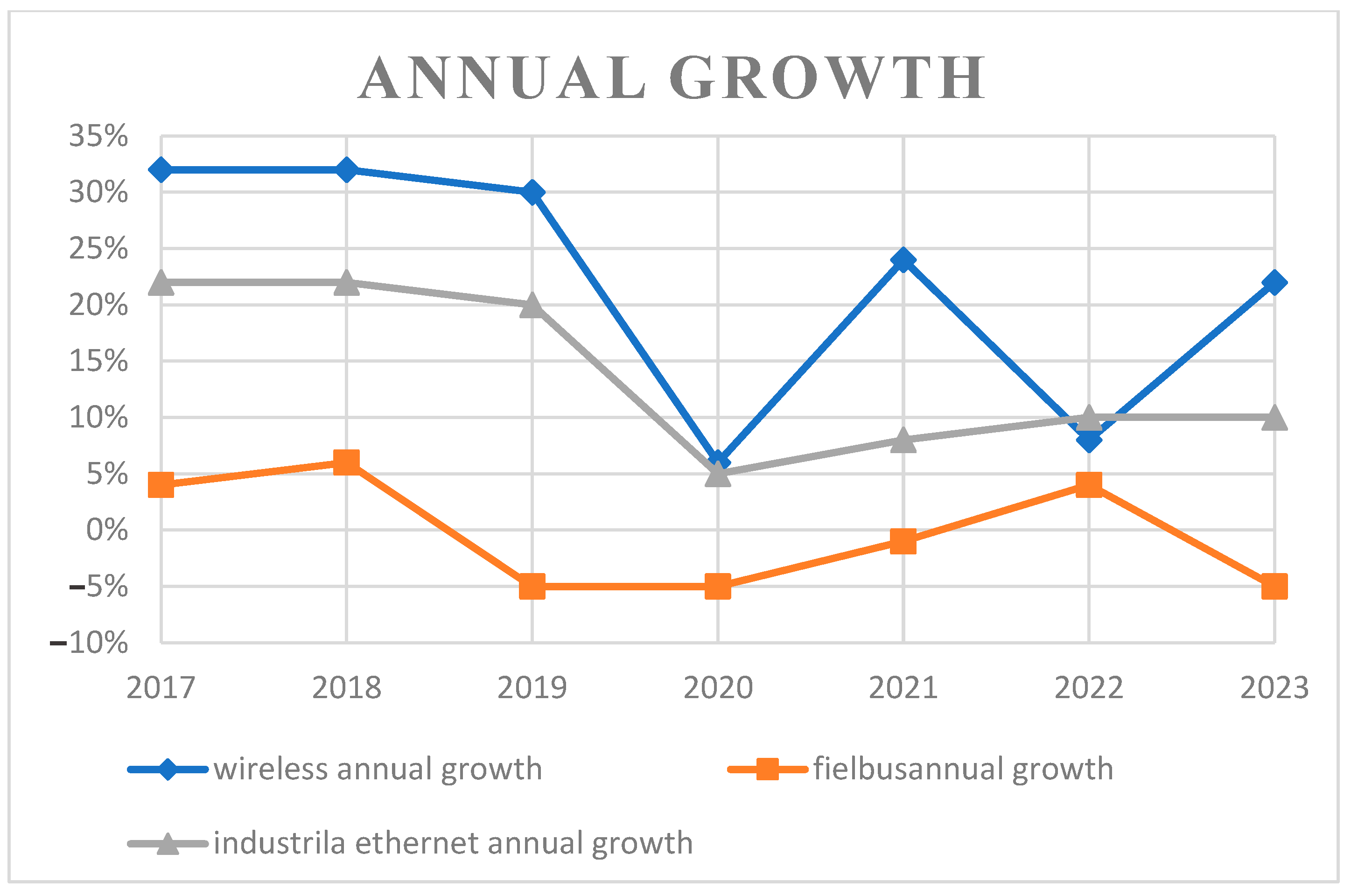
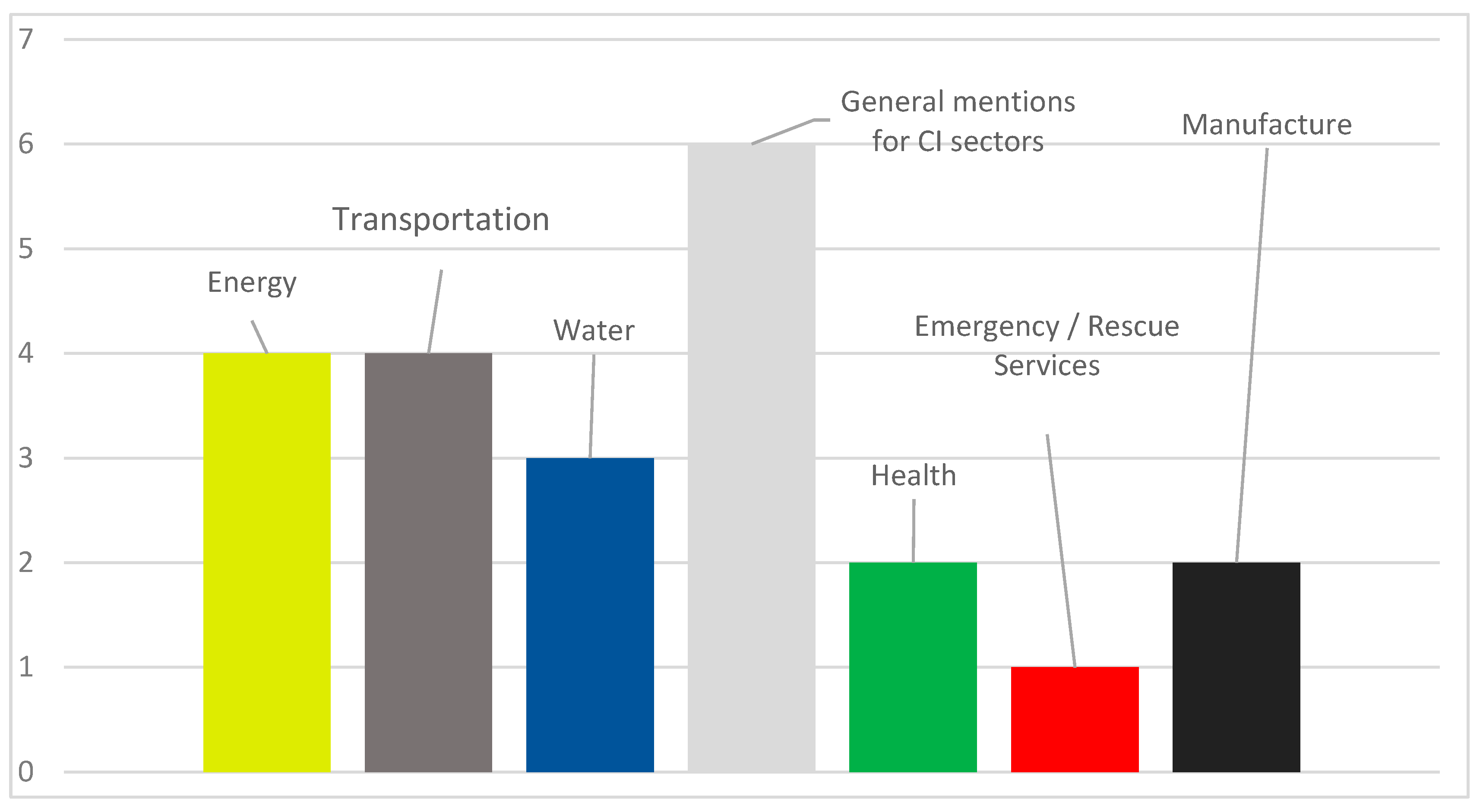
4. Bibliographic Research
5. Discussion
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- United Nations Office for Disaster Risk Reduction—Regional Office for Europe & Central Asia. Making Critical Infrastructure Resilient; United Nations Office for Disaster Risk Reduction—Regional Office for Europe & Central Asia: Brussels, Belgium, 2020. [Google Scholar]
- United States Department of Agriculture (USDA). USDA Rural Development FY 2022 Awards Rural Energy for America Program; United States Department of Agriculture: Washington, DC, USA, 2022; Volume 2023.
- Vogelman, S.J. The Fortnightlya Review of Middle East Regional Economic & Cultural News & Developments. Available online: https://atid-edi.com/category/fortnightly/ (accessed on 7 November 2023).
- Willis, R. European Investment Bank Pledges Record Funding for Europe’s Security Infrastructure, Vows More Support for Ukraine. Available online: https://www.eib.org/en/press/all/2023-227-eib-pledges-record-funding-for-europe-s-security-infrastructure-vows-more-support-for-ukraine (accessed on 1 December 2023).
- Florian Martens, S.K. Siemens to Invest More than US$500 million in U.S. Manufacturing for Critical Infrastructure in 2023. Available online: https://press.siemens.com/global/en/pressrelease/siemens-invest-more-us500-million-us-manufacturing-critical-infrastructure-2023 (accessed on 5 December 2023).
- Commission of the European Communities. Communication from the Commission on a European Programme for Critical Infrastructure Protection; Commission of the European Communities: Brussels, Belgium, 2006. [Google Scholar]
- European Parliament. Resilience of Critical Entities and Repealing Council Directive 2008/114/EC. Available online: https://eur-lex.europa.eu/eli/dir/2022/2557/oj (accessed on 14 September 2023).
- Moteff, J.; Parfomak, P. Critical Infrastructure Identification, Prioritization, and Protection, 2004. Available online: https://apps.dtic.mil/sti/citations/ADA454016 (accessed on 20 July 2023).
- Brunner, E.M.; Suter, M. International CIIP Handbook 2008/2009; Center for Security Studies (CSS), ETH Zürich: Zürich, Switzerland, 2008. [Google Scholar]
- A Proclamation on Critical Infrastructure Security and Resilience. Available online: https://www.whitehouse.gov/briefing-room/presidential-actions/2023/10/31/a-proclamation-on-critical-infrastructure-security-and-resilience-month-2023/ (accessed on 15 October 2023).
- Commission of the European Communities. Green Paper on a European Programme for Critical Infrastructure Protection; Commission of the European Communities: Brussels, Belgium, 2005. [Google Scholar]
- Council Directive 2008/114/EC of 8 December 2008 on the Identification and Designation of European Critical Infrastructures and the Assessment of the Need to Improve Their Protection. Available online: https://eur-lex.europa.eu/legal-content/en/TXT/?uri=CELEX:32008L0114 (accessed on 26 November 2023).
- Theoharidou, M.; Kandias, M.; Gritzalis, D. Securing Transportation-Critical Infrastructures: Trends and Perspectives. In Global Security, Safety and Sustainability & e-Democracy. e-Democracy ICGS3 2011 2011. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Georgiadis, C.K., Jahankhani, H., Pimenidis, E., Bashroush, R., Al-Nemrat, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 99. [Google Scholar]
- Wisniewski, M.; Gladysz, B.; Ejsmont, K.; Wodecki, A.; Van Erp, T. Industry 4.0 Solutions Impacts on Critical Infrastructure Safety and Protection–A Systematic Literature Review. IEEE Access 2022, 10, 82716–82735. [Google Scholar] [CrossRef]
- Davies, R. Industry 4.0, Digitalisation for Productivity and Growth; European Parliamentary Research Service: Brussels Belgium, 2015. [Google Scholar]
- Majstorovic, V.D.; Mitrovic, R. Industry 4.0 Programs Worldwide. In Proceedings of the 4th International Conference on the Industry 4.0 Model for Advanced Manufacturing, Belgrade, Serbia, 3–6 June 2019. [Google Scholar]
- Sisinni, E.; Mahmood, A. Wireless Communications for Industrial Internet of Things: The LPWAN Solutions. In Wireless Networks and Industrial IoT; Mahmood, N.H., Marchenko, N., Gidlund, M., Popovski, P., Eds.; Springer: Cham, Switzerland, 2021. [Google Scholar]
- Amit Shukla, H.K. Application of robotics in offshore oil and gas industry—A review part II. Robot. Auton. Syst. 2015, 75, 508–524. [Google Scholar] [CrossRef]
- Brucherseifer, E.; Winter, H.; Mentges, A.; Mühlhäuser, M.; Hellmann, M. Digital Twin conceptual framework for improving critical infrastructure resilience. At-Automatisierungstechnik 2021, 69, 1062–1080. [Google Scholar] [CrossRef]
- Laplante, P.; Amaba, B. Artificial Intelligence in Critical Infrastructure Systems. Computer 2021, 54, 14–24. [Google Scholar] [CrossRef]
- Wu, Y.; Dai, H.N.; Wang, H. Convergence of Blockchain and Edge Computing for Secure and Scalable IIoT Critical Infrastructures in Industry 4.0. IEEE Internet Things J. 2020, 8, 2300–2317. [Google Scholar] [CrossRef]
- Alqudhaibi, A.; Albarrak, M.; Aloseel, A.; Jagtap, S.; Salonitis, K. Predicting Cybersecurity Threats in Critical Infrastructure for Industry 4.0: A Proactive Approach Based on Attacker Motivations. Sensors 2023, 23, 4539. [Google Scholar] [CrossRef]
- Singh, M.K.; Amin, S.I.; Imam, S.A.; Sachan, V.K.; Choudhary, A. A Survey of Wireless Sensor Network and its types. In Proceedings of the 2018 International Conference on Advances in Computing, Communication Control and Networking (ICACCCN), Greater Noida, India, 12–13 October 2018. [Google Scholar]
- Kandris, D.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of Wireless Sensor Networks: An Up-to-Date Survey. Appl. Syst. Innov. 2020, 3, 14. [Google Scholar] [CrossRef]
- Sharma, S.; Kumar, D.; Kishore, K. Wireless Sensor Networks—A Review on Topologies and Node Architecture. Int. J. Comput. Sci. Eng. 2013, 1, 19–25. [Google Scholar]
- Yoo, S.E.; Kim, T. Industrial wireless sensor networks: Protocols and applications. Sensors 2020, 20, 5809. [Google Scholar] [CrossRef]
- History of IEEE. Available online: https://www.ieee.org/about/ieee-history.html?utm_source=linkslist_text&utm_medium=lp-about&utm_campaign=history (accessed on 12 November 2023).
- About of ISO. Available online: https://www.iso.org/about-us.html (accessed on 5 December 2023).
- About of CEN. Available online: https://www.cencenelec.eu/about-cen/ (accessed on 7 December 2023).
- About of IEC. Available online: https://www.iec.ch/history/how-why-iec-was-started (accessed on 5 December 2023).
- About of IPC. Available online: https://www.ipc.org/about-ipc (accessed on 9 December 2023).
- Lewis, A.M. Technology Certification for Critical Infrastructure Protection; EUR 26808; European Commission Joint Research Centre Institute for the Protection and Security of the Citizen: Brussels, Belgium, 2014. [Google Scholar]
- ISO/IEC 27001; Information Security Management Systems. ISO: Genève, Switzerland, 2022. Available online: https://www.iso.org/standard/27001 (accessed on 15 October 2023).
- ISO/IEC 27002:2022; Information Security Controls. ISO: Genève, Switzerland, 2022. Available online: https://www.iso.org/standard/75652.html (accessed on 15 October 2023).
- ISO/IEC 15408-1:2022; Evaluation Criteria for IT Security. ISO: Genève, Switzerland, 2022. Available online: https://www.iso.org/standard/72891.html (accessed on 15 October 2023).
- IEC 62351; Cyber Security: Understanding IEC 62351. IEC: Genève, Switzerland, 2023. Available online: https://www.iec.ch/blog/cyber-security-understanding-iec-62351 (accessed on 15 October 2023).
- IEC 62443; Understanding IEC 62443. IEC: Genève, Switzerland, 2021. Available online: https://www.iec.ch/blog/understanding-iec-62443 (accessed on 15 October 2023).
- Prepared Statement of Dave Whitehead, Vice President of R&D Schweitzer Engineering Laboratories. Available online: https://www.ferc.gov/sites/default/files/2020-08/Whitehead-SchweitzerEngineeringl.pdf (accessed on 15 October 2023).
- IEC TS 62686-1; International Electrotechnical Commission. IEC: Genève, Switzerland, 2020. Available online: https://webstore.iec.ch/preview/info_iects62686-1%7Bed3.0%7Den.pdf (accessed on 27 June 2023).
- IPC J-STD-001 and IPC-A-610. 2020. Available online: https://www.ipc.org/news-release/ipc-releases-new-h-revision-two-leading-standards-electronics-assembly-ipc-j-std-001 (accessed on 8 August 2023).
- Liu, Y.; Ma, X.; Li, Y.; Tie, Y.; Zhang, Y.; Gao, J. Water Pipeline Leakage Detection Based on Machine Learning and Wireless Sensor Networks. Sensors 2019, 19, 5086. [Google Scholar] [CrossRef]
- Adu-Manu, K.S.; Katsriku, F.A.; Abdulai, J.-D.; Engmann, F. Smart River Monitoring Using Wireless Sensor Networks. Wirel. Commun. Mob. Comput. 2020, 2020, 8897126. [Google Scholar] [CrossRef]
- Kumar, J.C.R.; Almasarani, A.; Majid, M.A. 5G-Wireless Sensor Networks for Smart Grid-Accelerating technology’s progress and innovation in the Kingdom of Saudi Arabia. Procedia Comput. Sci. 2021, 182, 46–55. [Google Scholar] [CrossRef]
- Corujo, D.; Quevedo, J.; Cunha, V.; Perdigão, A.; Silva, R.; Santos, D.; Aguiar, R.L.; Paixão, P.; Silva, P.E.; Antunes, R.; et al. An Empirical Assessment of the Contribution of 5G in Vertical Industries: A Case for the Transportation Sector. IEEE Access 2023, 11, 15348–15363. [Google Scholar] [CrossRef]
- Czeczot, G.; Rojek, I.; Mikołajewski, D. Analysis of Cyber Security Aspects of Data Transmission in Large-Scale Networks Based on the LoRaWAN Protocol Intended for Monitoring Critical Infrastructure Sensors. Electronics 2023, 12, 2503. [Google Scholar] [CrossRef]
- Ali, S.; Rehman, O.; Cha, K.; Balushi, T.A.; Nadir, Z. Performance Analysis of ZigBee-based IoT Prototype for Remote Monitoring in Power Grid Systems. In Proceedings of the 9th International Conference on Smart Media and Applications, Jeju, Republic of Korea, 17–19 September 2020; pp. 384–389. [Google Scholar]
- Singh, R.; Baz, M.; Narayana, C.; Rashid, M.; Gehlot, A.; Shaik, V.A.; Alshamrani, S.; Prashar, D.; Saeed, A. Zigbee and Long-Range Architecture Based Monitoring System for Oil Pipeline Monitoring with the Internet of Things. Sustainability 2021, 13, 10226. [Google Scholar] [CrossRef]
- Trigkas, A.; Sarigiannis, G.; Daousis, S.; Papageorgas, P.; Agavanakis, K.; Panagiotopoulos, K. NB-IoT for environmental monitoring and a fire early warning detection system in Mount Pentelicus. AIP Conf. Proc. 2022, 2437, 020069. [Google Scholar] [CrossRef]
- Villar Miguelez, C.; Monzon Baeza, V.; Parada, R.; Monzo, C. Guidelines for Renewal and Securitization of a Critical Infrastructure Based on IoT Networks. Smart Cities 2023, 6, 728–743. [Google Scholar] [CrossRef]
- Ugwuanyi, S.; Hansawangkit, J.; Irvine, J. NB-IoT Testbed for Industrial Internet of Things. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020; pp. 1–6. [Google Scholar]
- Haxhibeqiri, J.; De Poorter, E.; Moerman, I.; Hoebeke, J. A Survey of LoRaWAN for IoT: From Technology to Application. Sensors 2018, 18, 3995. [Google Scholar] [CrossRef]
- Daousis, S.; Sarigiannis, G.; Trigkas, A.; Agavanakis, K.; Papageorgas, P. The Blue Bee project: A proposal for the development of an internet of ships sensing network for environmental data collection and sharing. AIP Conf. Proc. 2022, 2437, 020068. [Google Scholar] [CrossRef]
- Borsos, D.; Kohanecz, Á.; Kozma, D. LoRa and LoRaWAN in the Aspect of Critical Infrastructures. Tech. Univ. Ostrav. Saf. Eng. Ser. 2022, 17, 1–11. [Google Scholar] [CrossRef]
- Mikhailovich, P.P.; Victorovich, C.A.; Nikolayevich, Y.N.; Yuryevich, Z.M. Implementation of GOST 34.12-2018 Encryption for LoRaWAN End-devices. In Proceedings of the 2021 Ural Symposium on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), Yekaterinburg, Russia, 13–14 May 2021. [Google Scholar]
- Reyneke, M.A.; Mullins, B.E.; Reith, M.G. LoRaWAN & The Helium Blockchain: A Study on Military IoT Deployment. Int. Conf. Cyber Warf. Secur. 2023, 18, 327–337. [Google Scholar]
- Woolley, M. The Bluetooth Low Energy Primer. Bluetooth Blog 2022, 15, 2022. [Google Scholar]
- Gutierrez del Arroyo, J.A.; Air Force Institute of Technology Wright-Patterson AFB OH Wright-Patterson AFB United States. Enhancing Critical Infrastructure Security Using Bluetooth Low Energy Traffic Sniffers; Air Force Air University: Maxwell AFB, AL, USA, 2017. [Google Scholar]
- Zubair, M.; Ghubaish, A.; Unal, D.; Al-Ali, A.; Reimann, T.; Alinier, G.; Hammoudeh, M.; Qadir, J. Secure Bluetooth Communication in Smart Healthcare Systems: A Novel Community Dataset and Intrusion Detection System. Sensors 2022, 22, 8280. [Google Scholar] [CrossRef] [PubMed]
- Joseph, W. A Basic Guide to the HART Protocol; Texas Instruments: Dallas, TX, USA, 2023. [Google Scholar]
- Hall, K.B.; Ngalamou, L. Securing Wireless Scada Systems in Rural American Power Grids. In Proceedings of the IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 10–12 October 2019. [Google Scholar]
- Rondeau, C.; Temple, M. DNA Feature Selection for Discriminating WirelessHART IIoT Devices. In Proceedings of the 53rd Hawaii International Conference on System Sciences, Mānoa, HI, USA, 7–10 January 2020. [Google Scholar] [CrossRef]
- Ambarkar, S.S.; Shekokar, N. An efficient authentication technique to protect iot networks from impact of rpl attacks. Int. J. Eng. Trends Technol. 2021, 69, 137–145. [Google Scholar] [CrossRef]
- Ibrahim, J.; Tonga, D.A.; Danladi; Aderinola, M. Comparative Analysis Between Wired and Wireless Technologies in Communications: A Review. Int. J. Electr. Electron. Data Commun. 2017, 5, 24–27. [Google Scholar]
- Soni, P.; Subhashini, J. Future smart grid communication-deployment of IoT: Opportunities and challenges. Indones. J. Electr. Eng. Comput. Sci. 2021, 23, 14. [Google Scholar] [CrossRef]
- Noel, A.B.; Abdaoui, A.; Elfouly, T.; Ahmed, M.H.; Badawy, A.; Shehata, M.S. Structural Health Monitoring Using Wireless Sensor Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2017, 19, 1403–1423. [Google Scholar] [CrossRef]
- Husnoo, M.A.; Anwar, A.; Chakrabortty, R.K.; Doss, R.; Ryan, M.J. Differential Privacy for IoT-Enabled Critical Infrastructure: A Comprehensive Survey. IEEE Access 2021, 9, 153276–153304. [Google Scholar] [CrossRef]
- Hafsa, B.; Khalil, I.; Abderrahim Benslimane, J.Q. A Deep Reinforcement Learning Based Intrusion Detection System (DRL-IDS) for Securing Wireless Sensor Networks and Internet of Thing. In Proceedings of the Wireless Internet: 12th EAI International Conference, WiCON 2019, TaiChung, Taiwan, 26–27 November 2019. [Google Scholar] [CrossRef]
- Lazrag, H.; Chehri, A.; Saadane, R.; Rahmani, M.D. Efficient and secure routing protocol based on Blockchain approach for wireless sensor networks. Concurr. Comput. Pract. Exp. 2020, 33, e6144. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H. A Comparative Study of AI-Based Intrusion Detection Techniques in Critical Infrastructures. ACM Trans. Internet Technol. 2021, 21, 1–22. [Google Scholar] [CrossRef]
- Basu, K.; Dey, S.; Nandy, S.; Sen, A. Sensor Networks for Structural Health Monitoring of Critical Infrastructures Using Identifying Codes. In Proceedings of the 2019 15th International Conference on the Design of Reliable Communication Networks (DRCN), Coimbra, Portugal, 19–21 March 2019; pp. 43–50. [Google Scholar]
- Subhan, F.; Noreen, M.; Imran, M.; Tariq, M.; Khan, A.; Shoaib, M. Impact of Node Deployment and Routing for Protection of Critical Infrastructures. IEEE Access 2019, 7, 11502–11514. [Google Scholar] [CrossRef]
- Valdivia, L.J.; Del-Valle-Soto, C.; Rosas-Caro, J.C. Wireless communication for railway applications: Reactive and proactive protocols. In Proceedings of the 2019 International Conference on Electronics, Communications and Computers (CONIELECOMP), Cholula, Mexico, 27 February 2018–1 March 2019; pp. 21–26. [Google Scholar]
- Yang, H. A practical method for connectivity and coverage reliability analysis for linear wireless sensor networks. Ad. Hoc. Netw. 2023, 146, 103183. [Google Scholar] [CrossRef]

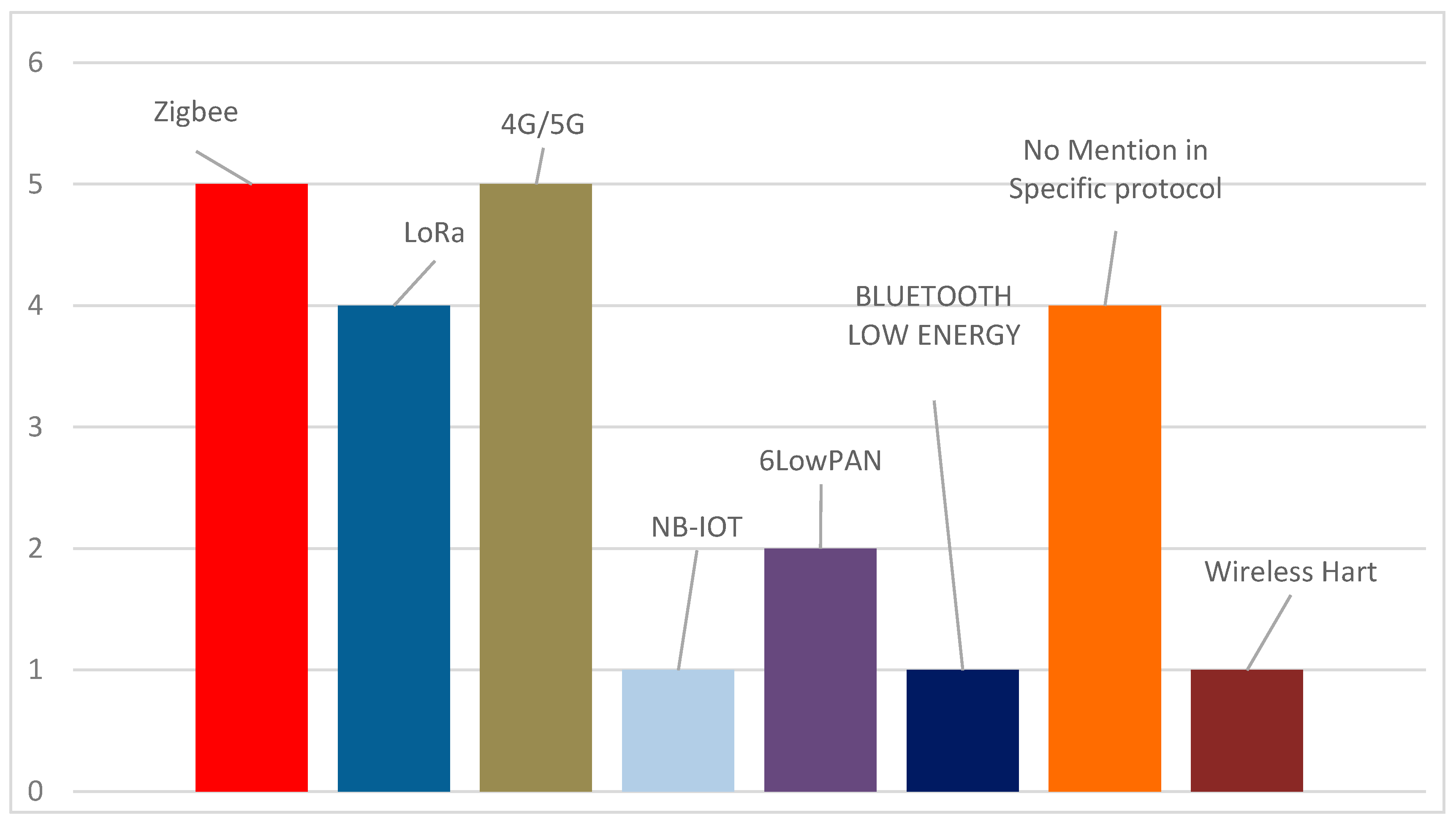
| Sectors | Countries | ||||||
|---|---|---|---|---|---|---|---|
| Germany | United Kingdom | Japan | United States | China | India | Australia | |
| Banking and Finance | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| Central Government/Government Services | ■ | ■ | ■ | ■ | ■ | ||
| Chemical and Nuclear Industry | ■ | ■ | ■ | ||||
| Emergency/Rescue Services | ■ | ■ | |||||
| Energy | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| Food/Agriculture | ■ | ■ | ■ | ■ | |||
| Health Services | ■ | ■ | ■ | ||||
| Information Services/Media | ■ | ■ | |||||
| Military Defense/Army/Defense Facilities | ■ | ■ | ■ | ■ | |||
| Telecommunications /Public Communications | ■ | ■ | ■ | ■ | ■ | ||
| Transportation | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| Water (Supply)/Sewerage | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| Space | ■ | ■ | |||||
| Critical Manufacturing | ■ | ||||||
| Information and Communication Technology | ■ | ■ | ■ | ■ | ■ | ||
| Dams | ■ | ||||||
| e-Government Services | ■ | ||||||
| Strategic and Public Enterprises | ■ | ||||||
| Higher Education and Research | ■ | ||||||
| Citation | Reference Number | CI Sector | Wireless Communication Technologies/Protocols | Standards | Type of Paper | Year |
|---|---|---|---|---|---|---|
| 63 | [41] | Water | ZigBee and 4G wireless | - | Journal Article | 2019 |
| 26 | [42] | Water | ZigBee and 4G | - | Journal Article | 2020 |
| 26 | [43] | Energy | 5G | - | Journal Article | 2021 |
| 1 | [44] | Transportation Sector | 5G | - | Journal Article | 2023 |
| 1 | [46] | Energy | ZigBee | IEEE 802.15.4 | Conference Paper | 2020 |
| 10 | [47] | Energy | ZigBee/LoRaWAN | - | Journal Article | 2021 |
| 22 | [49] | Water | NB-IoT | ISO 37120, ISO 37122 ISO 37120, ISO 37123 ISO/IEC 27001: 2017 n RDL 8/2011, ISO 27002 | Journal Article | 2023 |
| 2 | [50] | Industrial/Manufacturing | NB-IoT | 3GPP standardization | Conference Paper | 2020 |
| [53] | Health Industrial Transportation | LoRaWAN | - | Journal Article | 2022 | |
| - | [54] | Industrial/Manufacturing | LoRaWAN | - | Conference Paper | 2021 |
| - | [55] | Military, Emergency/Rescue Services | LoRaWAN, Helium | AES-128 | Conference Paper | 2023 |
| 6 | [58] | Health | Bluetooth Low Power | - | Journal Article | 2022 |
| - | [60] | Energy | ZigBee PRO, WirelessHART, and ISA 100.11a. | - | Journal Article | |
| 20 | [66] | General Reference to Smart Grids, Intelligent Transport Systems, Healthcare and Medical, Industrial/Manufacturing | General Reference to 5G, LoRaWAN, | - | Journal Article | 2021 |
| 18 | [67] | General Reference to healthcare | - | - | Conference Paper | 2020 |
| 9 | [68] | General Reference to Critical Public Infrastructure Energy Transport Health | General Reference to 6LowPAN | - | Journal Article | 2020 |
| 2 | [62] | General Reference to Critical Infrastructure | 6LowPAN | RPL (Routing Protocol for Low-Power and Lossy Networks) | Journal Article | 2021 |
| [69] | General Reference to Medical | - | - | Journal Article | 2021 | |
| 4 | [70] | Bridges Transportation Sector | - | - | Conference Paper | 2019 |
| 6 | [71] | General Reference to Pipeline (Oil, Gas, And Water) Monitoring Railroad/Subway and Bridge Monitoring | - | - | Journal Article | 2019 |
| - | [72] | Railway Infrastructure Transportation Sector | Multi-Parent Hierarchical (MPH), Ad-Hoc On-Demand Distance Vector (AODV) | - | Conference Paper | 2019 |
| 1 | [73] | General Reference to Military, Manufacturing, Health Care, Railways, Highways, Rivers, Oil or Gas Pipelines, and Energy | Linear Wireless Sensor Networks (LWSNs) | - | Journal Article | 2023 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Daousis, S.; Peladarinos, N.; Cheimaras, V.; Papageorgas, P.; Piromalis, D.D.; Munteanu, R.A. Overview of Protocols and Standards for Wireless Sensor Networks in Critical Infrastructures. Future Internet 2024, 16, 33. https://doi.org/10.3390/fi16010033
Daousis S, Peladarinos N, Cheimaras V, Papageorgas P, Piromalis DD, Munteanu RA. Overview of Protocols and Standards for Wireless Sensor Networks in Critical Infrastructures. Future Internet. 2024; 16(1):33. https://doi.org/10.3390/fi16010033
Chicago/Turabian StyleDaousis, Spyridon, Nikolaos Peladarinos, Vasileios Cheimaras, Panagiotis Papageorgas, Dimitrios D. Piromalis, and Radu Adrian Munteanu. 2024. "Overview of Protocols and Standards for Wireless Sensor Networks in Critical Infrastructures" Future Internet 16, no. 1: 33. https://doi.org/10.3390/fi16010033
APA StyleDaousis, S., Peladarinos, N., Cheimaras, V., Papageorgas, P., Piromalis, D. D., & Munteanu, R. A. (2024). Overview of Protocols and Standards for Wireless Sensor Networks in Critical Infrastructures. Future Internet, 16(1), 33. https://doi.org/10.3390/fi16010033










