1. Introduction
Vehicular ad hoc network (VANET) is an advanced version of the mobile ad hoc network (MANET), which was developed to enhance the safety, efficiency, and convenience of transportation [
1]. VANET is a set of applications designed to offer new services connected to the traffic management system, designed to help various users to be better informed and use the transportation network to be safer, more connected, and significantly more intelligent. VANET can be established for monitoring and controlling traffic using the concept of vehicle-to-everything (V2X) communication, which includes vehicle to infrastructure (V2I), vehicle to sensor (V2S), vehicle to pedestrian (V2P), and Vehicle to Vehicle (V2V) communication [
2,
3]. The general architecture of a VANET is shown in
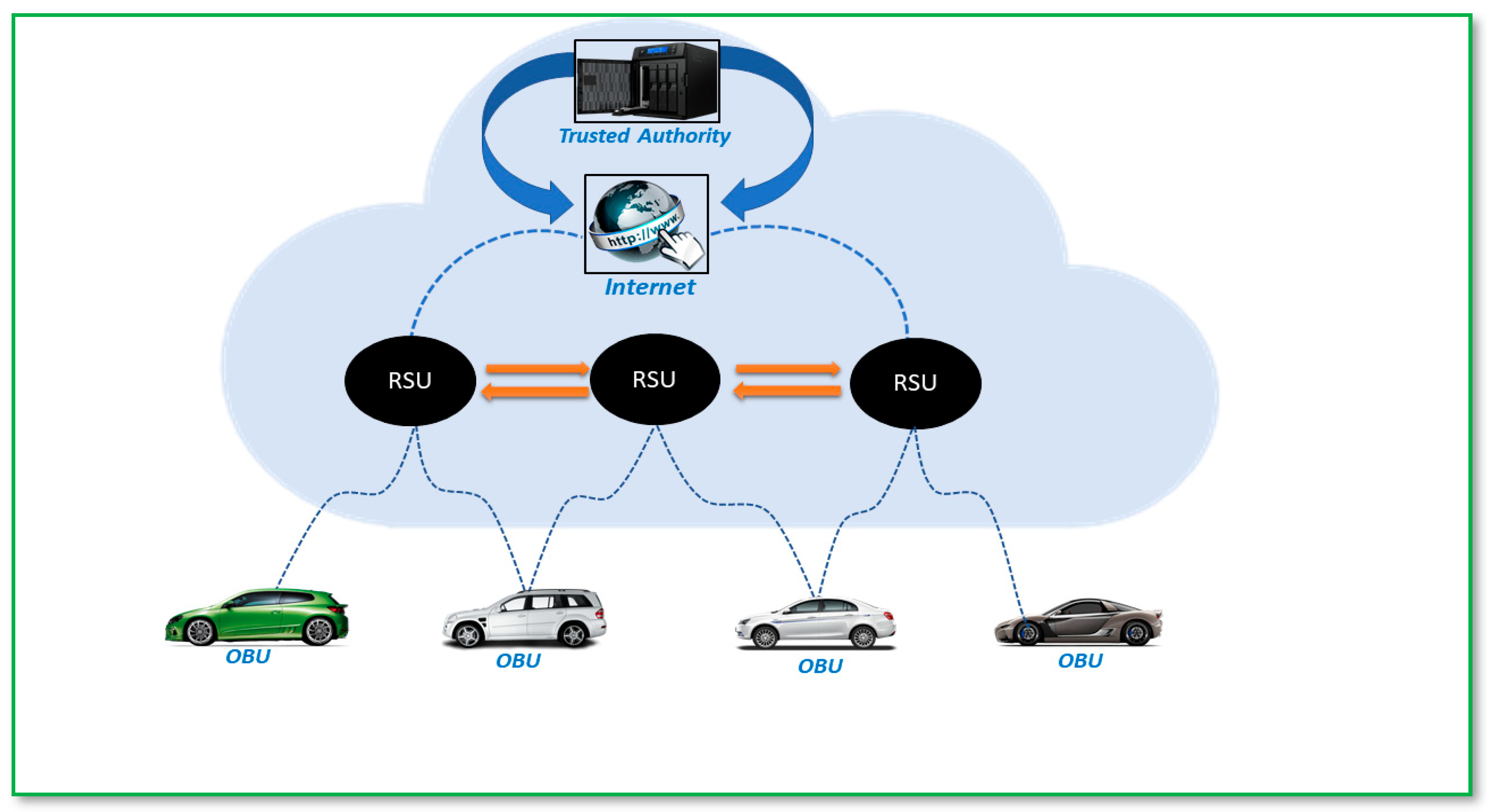
Figure 1, which includes vehicles with built-in 5G-enabled onboard units (OBUs), 5G-enabled roadside units (RSUs), and trusted authorities (TAs). TA is a service provider, ensuring the safety of the VANET network and generating public and private keys for OBUs and RSUs [
4]. In VANETs, each vehicle communicates through an OBU and broadcasts traffic-related information such as positions, speed, current time, traffic and road conditions to a nearby vehicle and an RSU [
5].
Despite all the attractive features offered by a VANET, there are significant challenges regarding its security and privacy when information is shared among vehicles through an open wireless channel. In a VANET system, an attacker can send bogus messages to the RSUs or other OBUs, which might cause disturbance on the roads, so it is necessary to verify the authenticity and integrity of the message [
6]. Digital signature-based authentication techniques for VANETs have been built in various cryptographic frameworks, including public-key infrastructure (PKI), identity-based (ID), and certificateless cryptography.
In the standard implementation of public-key cryptography (PKC), each public key is required to produce a corresponding digital certificate [
7]. Nevertheless, it not only involves certificate management but also contributes to an increase in the verification cost. To address the issues of certificate management, Shamir [
8] came up with a novel technique in 1984 called ID-based public-key cryptography (ID-PKC). The public key consists of the user’s identity, such as phone number, e-mail address, etc., eliminating the need for a certificate. However, the private key is generated by the Key Generation Center (KGC), which might lead to a key escrow problem. To overcome the shortcomings of key management in traditional PKC and the key escrow problem in ID-PKC, Al-Riyami and Paterson [
9] proposed Certificateless Public Key Cryptography (CL-PKC), which also requires the KGC to generate part of the user’s private key.
In contrast, the other part is generated by the user locally. As a result, key escrow is overcome, and CL-PKC does not need to create certificates. Many researchers combine certificateless cryptography with aggregate signature (AS) to create certificateless aggregate signature (CLAS) schemes, which minimize node authentication overhead and address certificate management and key escrow issues in classical cryptosystems. CLAS can prevent the routing information from being forged, altered, or impersonated, as well as ensure its integrity and provide authentication and nonrepudiation for the sender.
Some entities in VANETs, such as RSUs and OBUs, have limited computing and storage capacity; therefore, efficiency must be taken into account while designing a suitable authentication system for efficient communication in VANETs. In 2003, Boneh et al. [
10] proposed the idea of an aggregate signature, which combines the signatures of multiple messages sent by various vehicles into a single, short signature. By using aggregate signatures, we can reduce computational and communicational costs and increase storage capacity to enhance the efficiency of a VANET system.
In this paper, we propose a certificateless aggregate signature scheme based on hyperelliptic curve cryptography (HECC), which is the advanced version of Elliptic Curve Cryptography (ECC), using a key size of 80 bits, providing the same security benefits of ECC, but with less computational cost, communication overhead, and memory requirement. HECs are algebraic curves with the genus ḡ ≥ 1; since the field of an HECC is a quadratic extension of the field of rational functions, we can say that it is the simplest field of algebraic functions, except the field of rational functions [
11]. HECC consists of the divisor ₯, the finite formal sum of points on a hyperelliptic curve. The divisor ₯ also forms an Abelian group known as the Jacobian group [
12]. Based on the above discussion, this research article contributes to the security of VANETs through the following key characteristics:
In this article, we propose an efficient certificateless aggregate signature scheme for the security and privacy protection of VANETs using hyperelliptic curve cryptography;
The proposed scheme enables participating vehicles to share their identities with trusted authorities via an open channel without revealing their identities to unauthorized participants; as a result, sender and recipient anonymity will be ensured;
In addition, this scheme will disclose the partial private key to participating devices via an open channel while keeping it concealed from other third parties;
Finally, the noteworthy feature of the proposed scheme is its utilization of a hyperelliptic curve to generate and verify signatures with less computational and communication costs.
The subsequent sections of this article are organized in the following manner:
Section 2 discusses the literature review. The proposed scheme is described in
Section 4, while
Section 3 discusses the necessary preliminary steps.
Section 5 deals with the security evaluation. An analysis of performance is covered in
Section 6. Concluding remark on the proposed scheme is detailed in
Section 7.
2. Literature Review
A VANET is a communication technology that enables V2V and V2I communications via the Internet, which can be affected by several cyber-attacks. So, to avoid such circumstances, the best solution is authentication, in which the participating nodes in the VANET environment can authenticate each other before transferring data or information. To achieve authentication, the best approach is to use a digital signature, which allows a sender to sign data with his private key and deliver it to the recipient, who can then use the sender’s public key to verify the signature.
In a typical PKC-based signature, each user needs to produce a valid digital certificate that contains information about the identity of the certificate owner and the public key [
7]. However, it not only requires certificate management but also contributes to an increase in the verification cost. To address certificate management issues, Shamir [
8] proposed ID-PKC, in which the user’s identity is his public key, bypassing the need for certificates. However, the private keys are generated via the KGC, which might lead to a key escrow problem.
Al-Riyami and Paterson [
9] proposed the idea of CL-PKC, in which the user’s private key is made up of a secret value and a partial private key. The user chooses his secret key, while the KGC generates the partial private key. Since the KGC cannot access the user’s complete private key without the user’s secret key, the user’s public key can be calculated from the secret value. Thus, the potential security issues associated with key escrow are eliminated. Secondly, the user’s public key can be calculated from the secret value, so a certificate is no longer needed. In other words, the CLS technique has the potential to address issues in both the classic signature method and the ID-based method. CLAS has the benefits of CLS and AS. In 2003, Boneh et al. [
10] proposed the concept of CLAS, which can combine the signatures of n (n > 1) different messages signed by n other users into a single signature. The receiver only needs to check the aggregated signature instead of all the signatures, thereby reducing the computational cost of signature verification and the communication overhead of signature transmission to some extent.
The benefits of CLAS mentioned above have led to a lot of new research. Yum and Lee [
12] proposed a CLAS scheme within the framework of the Random Oracle Model (ROM), but Hu et al. [
13] discovered that Yum and Lee’s [
12] scheme is vulnerable to public key replacement attacks. Deng et al. [
14] designed and proved a secure practical CLAS scheme, although Kumar and Sharma [
15] found that Deng et al. [
14]’s scheme could guarantee unforgeability. A new certificateless signature system was presented by Horng et al. [
16] for the use of V2I in a VANET’s communication. However, Ming and Shen [
17] demonstrated that the scheme proposed by Horng et al. [
16] was vulnerable to various attacks like replay attacks, modification attacks, impersonation attacks, and man-in-the-middle attacks and hence could not provide authentication and message integrity. Li et al. [
18] addressed the limitation of Horng et al. [
16]’s scheme and designed an improved CLAS scheme. However, the scheme has high computational and communicational costs since it uses bilinear pairing and point-to-point hash functions. Keitaro Hashimoto and Wakaha Ogata [
19] came up with an open and small CLAS scheme in which the size of signatures stays the same, and any combination of signatures can be added together. However, the scheme is based on bilinear pairing, which necessitates higher computational and communicational costs. A highly effective AS scheme was developed by Malhi et al. [
20] for privacy and authentication in VANETs. Cui et al. [
21] developed an efficient CLAS scheme using ECC in vehicular sensor networks.
On the other hand, Kamil et al. [
22] claimed that Cui et al.’s [
21] scheme is unsafe against signature forgery attack. Du et al. [
23] proposed an effective CLAS scheme without pairings for healthcare wireless sensor networks. However, the scheme is based on ECC, which results in a significant increase in both computational and communicational costs. To avoid the unpleasant certificate management problem of PKI and the key escrow problem of an ID-based framework, Gowri et al. [
24] developed a CLAS-based authentication scheme for VANETS. However, Yang et al. [
25] proved that Gowri et al.’s [
24] scheme failed to achieve the desired security goals. Ye et al. [
26] designed an improved certificateless authentication and AS scheme that may effectively counter coalition attacks. In the same year, Vallent et al. [
27] developed a safe and efficient certificateless aggregation technique (ECLAS) for VANETs that might be used in a smart grid scenario. However, the [
26,
27] schemes are based on ECC to provide conditional privacy preservation, which leads to heavy computational costs and communication overhead.
A fully aggregated conditional privacy-preserving certificateless aggregate signature system (CPP-CLAS) was designed for VANETs by Yulei and Chen [
28] in 2022. The proposed CPP-CLAS scheme uses ECC and general hash functions, which result in high computational costs and communication overhead. Another efficient pairing-free CLAS for secure VANET communication was introduced in the same year by Yibo et al. [
29]. However, the [
28,
29] scheme was based on ECC, which has more computational costs and communication overhead.
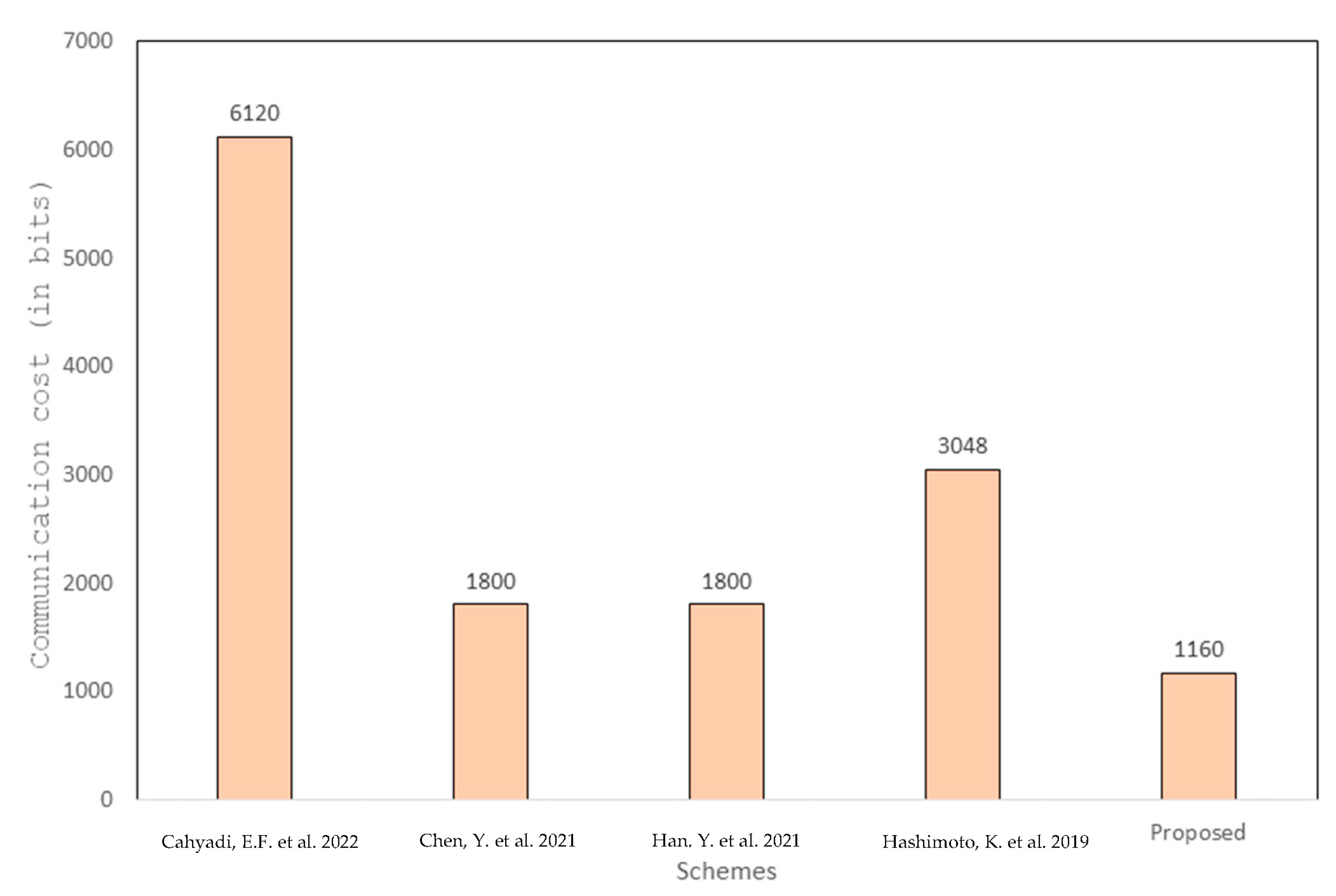
In 2022, Cahyadi et al. [
30] proposed a pairing-based CLAS authentication scheme to improve security, privacy, and efficiency in VANETs. However, it is found that the overall computation cost of the scheme is high due to massive pairing. To improve the security of VANET systems, we propose a CLAS-based authentication scheme based on HECC to reduce the computational cost and communication overhead due to the small parameter size.
3. Preliminaries
Koblitz introduced an algebraic curve called HEC [
31]. It is considered an advanced version of elliptic curves. Points of an HEC cannot be obtained from the group [
32]. In HECC, the additive Abelian group is calculated from the divisor (₯). HECC may be a more suitable option for low-resource environments due to its ability to provide the same level of security as ECC, bilinear pairing, and RSA while utilizing smaller parameters and key sizes [
33]. Let
be the algebraic closure of
, which is the finite field. Suppose the genus of HECC over
is (ḡ >1). Hyperelliptic curve
(H (Up)) is a generalized form of elliptic curves and the state
H (Up) over a finite field is defined using Equation (1):
where (
,
) belongs to [
and polynomial f(ℓ) belongs to (ℓ) with degree ḡ and a monic one as f(ℓ) =
(ℓ) with a degree 2 ḡ +1. If there is no pair (
,
) belonging to [
such a curve is called non-singular.
3.1. Hyperelliptic Curve Discrete Logarithm Problem (HECDLP) Assumptions
Suppose £ ∈ {1,2,3…, n−1} and ₯ is the divisor from HECC.
Let ⍵ = £. ₯, and calculating ₯ from this equation is called the HECC discrete logarithm problem (HECDP).
3.2. Hyperelliptic Curve Computational Defi-Helman Problem (HECCDHP) Assumptions
Suppose, ⦳, Ώ ∈ {1,2,3…, n−1} and ₯ is the divisor from HEC.
Let ⍵ = ⦳. ₯, ¥ = Ώ. ⦳. ₯, and calculating ⦳ and Ώ from △ and ¥ is called the HEC computational Defi–Helman problem (HCDH).
3.3. Network Model
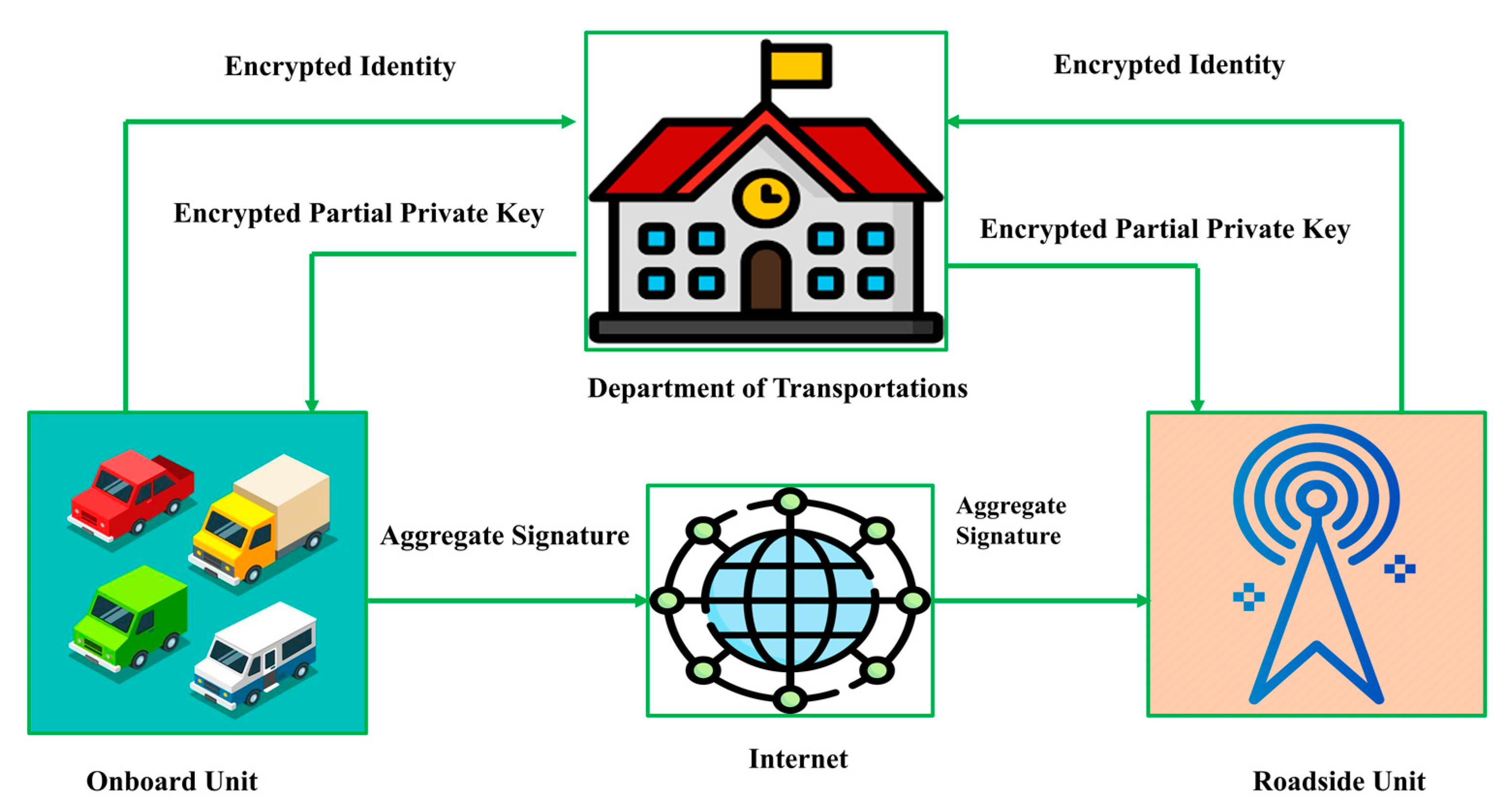
In
Figure 2, the network model of the proposed scheme is shown, which includes three entities: onboard unit (OBU), roadside unit (RSU), and department of transportation (DoT). The following are the explanatory steps:
OBU: It is a 5G-enabled communication device fixed on a vehicle that can communicate with RSU and other OBUs. It is responsible for registering itself with the DoT by sending its identity in an encrypted form. The DoT first decrypts the received encrypted identity, generates a partial private key for this identity, and returns it to the OBU in an encrypted format using an insecure channel. Then, the OBU generates a private key and a public key, generates a signature on data, and sends it to the RSU via an open network.
RSU: It is a 5G-enabled base station responsible for managing and conducting V-I communication. It is responsible for registering itself with the DoT by sending its identity in an encrypted form. The DoT generates a partial private key for this identity and returns it to the RSU in an encrypted format using an insecure channel. Then, the RSU can produce a complete private key and public key. When the RSU receives signed data from the OBU, it verifies the signature and either accepts the message or generates an error message depending on the results. RSU also works as a signature aggregator.
DoT: The DoT is a reliable third party (TA) with significant processing power and storage capability. When the DoT is provided with the identities of OBU and RSU, it produces a partial private key pair and sends it back to the OBU and RSU in two packages in an encrypted form using an insecure channel. Then, both OBU and RSU create their remaining private and public keys for themselves.
3.4. Syntax of the Proposed CLAS Scheme
The syntax of our CLAS contains the following sub-steps:
Setup: The DoT can play the role of a TA, and it will be able to run this phase upon receiving the security parameter, in which it can first choose the hyperelliptic curve. Then, the DoT can set the private and public keys. Further, it generates public param and publishes it to the network.
Partial Private Key Generation (PRPKG): Any participating user who needs a partial private key can first encrypt their real identity using the common secret key between the DoT and that particular user. After doing this, the user sends an encrypted identity to the DoT using an insecure network. Then, the DoT decrypts the encrypted identity and recovers the real identity. Further, the DoT generates the partial private key for that particular identity, encrypts it, and delivers it to the user using an insecure network.
Private Key Generation (PRKG): In this section, the user generates his public and private key pairs.
Signature Generation (SIGG): This section will be run by the OBU to generate and send the signature tuple () to the RSU.
Signature Verifications (SIGV): This section will run by the RSU to verify the signature tuple ().
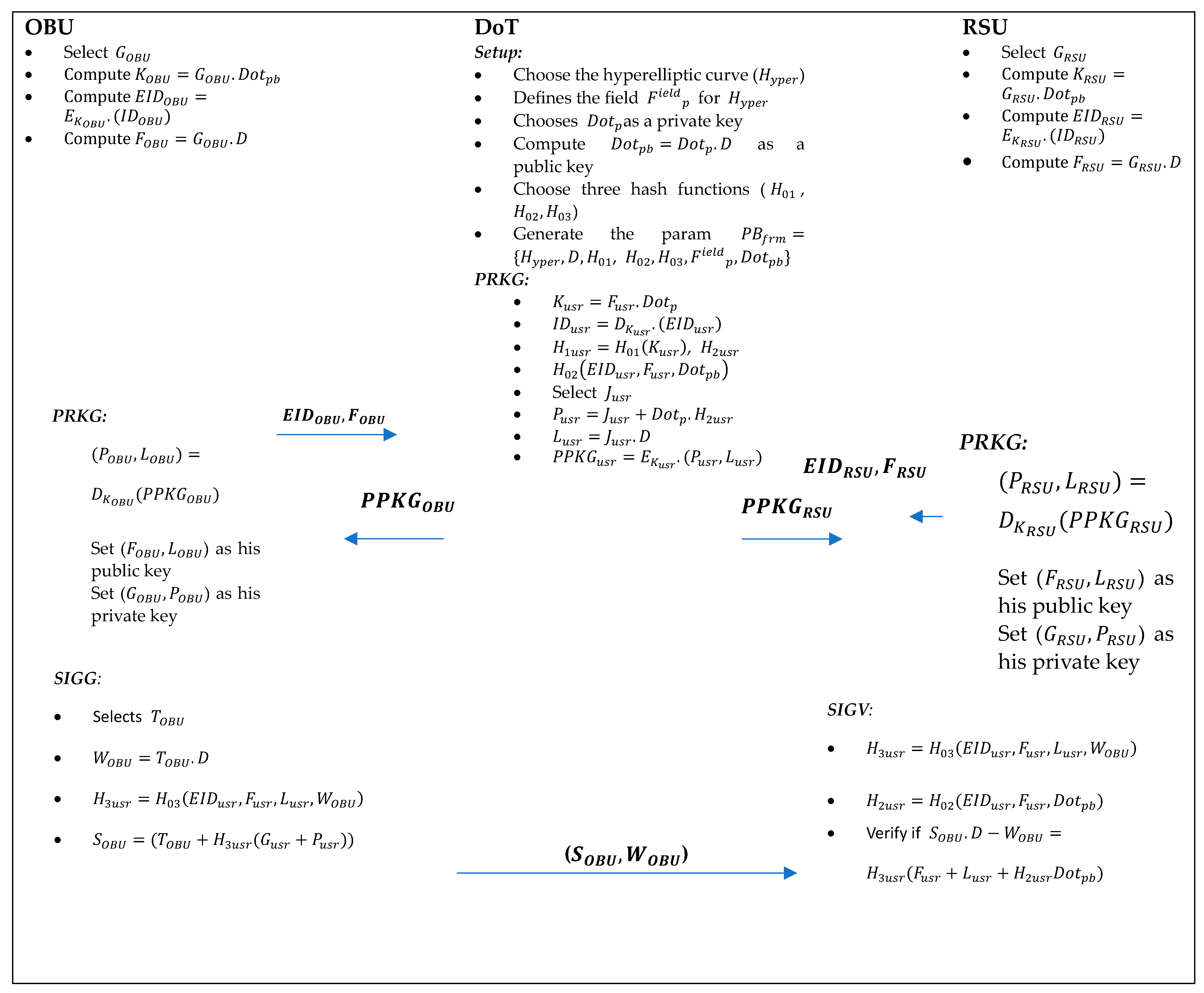
4. Proposed Scheme’s Construction
The proposed scheme consists of the steps listed below, and
Table 1 outlines the fundamental symbols utilized in its construction. The construction of the proposed scheme is also illustrated in
Figure 3.
Setup: The DoT can play the role of a TA, and it will be able to run this phase upon receiving the security parameter , in which it can first choose the hyperelliptic curve () that defines field , a devisor of 80 bis, and then it chooses as a private key from and computes as a public key. Further, it can choose three hash functions, , and the public param , .
Partial Private Key Generation (PRPKG): Any participating user who needs a partial private key can first select from , compute , calculate , compute and send () to DoT through the internet. Upon receiving (), DoT can compute , recover user identity as , compute , , select from , compute , calculate , encrypt , and send to users through an open channel.
Private Key Generation (PRKG): Upon receiving , any participating user can recover as and set () as his public key and () as his private key.
Signature Generation (SIGG): This section will be run by the OBU using the following steps:
Signature Verifications (SIGV): This section will be run by the RSU using the following steps:
Computes and ;
Aggregate Signature Generation and Verifications: This part is the same as performed in [
29].
Adding New Device: If a new device wants to add itself to the network in our proposed scheme, it will first perform the following procedures: it can first select from , compute , calculate , compute and send () to DoT through the internet. Upon receiving (), DoT can compute , recover new device identity as , compute , , select from , compute , calculate , encrypt , and send to new devices through an open channel. A new device then recovers as , sets () as his public key, sets () as his private key, and he can start communications with other devices if he wants.
Correctness
RSU will verify the signature if the following steps are satisfied.
, hence proved.
5. Security Analysis
In this phase, with the help of Theorems 1 and 2, we are going to prove that the proposed aggregate signature scheme is unforgeable against Type 1 () and Type 2 () forgers.
Theorem 1. Utilizing a non-negligible probability , if Type 1 () forger wants to forge the proposed certificateless aggregate signature within a polynomial time successfully, then there will be a challenger () who can serve his services as a facilitator for solving the hyperelliptic curve discrete logarithm problem with the probability , where andrepresent Partial Private Key Generation Query, Signature Generation Query, Signature Verifications Query, Natural Logarithm, Non-negligible Probability, and Hash Queries, respectively.
Proof. A facilitator called will solve the hyperelliptic curve discrete logarithm problem if he receives and his task will be to extract from . □
Setup: calls the Setup algorithm in which it sends the param to and keeps private .
Query Phase: selects the identity and has no access to . Then, selects the identity and performs the following queries with :
H01Query: initializes an empty list (). When generates this query, checks the tuple in . If the value exists, then it sends to ; otherwise, it randomly picks from , sends to and updates with the value .
H02Query: initializes an empty list (). When generates this query, checks the tuple in . If the value exists, then it sends to ; otherwise, it randomly picks from , sends to and updates with the value .
H03Query: initializes an empty list (). When generates this query, checks the tuple in . If the value exists, then it sends to ; otherwise, it randomly picks from , sends to and updates with the value .
Secret Value Generation (SVG) Query: initializes an empty list (). When generates this query, checks the value in . If the value exists, then it sends to otherwise, it randomly picks from , sends to and updates with the value .
PRPKG Query: initializes an empty list (). When generates this query, checks the value in . If the value exists, then it sends to otherwise, it randomly picks from , sends to and updates with the value .
Public Key Generation (PBKG) Query: initializes an empty list (). When generates this query, checks the value in . If the tuple exists, then it sends to otherwise, it performs the following steps:
If , it chooses from , computes , and calculates . Then, it sends to and updates with the value ;
If , it chooses from , computes , and calculates . Then, it sends to and updates with the value .
Public Key Replaced (PKR) Query: chooses the new public key tuple (, ) and sends it to the ; then, includes (, ) into as a replacement of the public key.
SIGG Query: initializes an empty list (). When generates this query, checks the value in . If the value exists, then it selects from
, computes computes
computes and sends () to . Otherwise, it selects from and sends it to the .
Forgery: When the above queries are completed successfully, can return a forged certificateless signature tuple (). By using the concept of the forking lemma, can return another forged certificateless signature tuple (). So these two tuples will be only true if gets the valid value of .
To satisfy this theorem, the results generated via must meet the following conditions:
does not stop the querying process and its probability (.
does not stop the forging process for signature and its probability .
() is a valid tuple, and its probability .
So, the probability of () as (().
Theorem 2. Utilizing a non-negligible probability , if Type 2 () forger wants to forge our certificateless aggregate signature within a polynomial time successfully, then there will be a challenger () who can serve his services as a facilitator for solving the hyperelliptic curve discrete logarithm problem with the probability , whereand represent Signature Generation Query, Signature Verifications Query, Natural Logarithm, Non-negligible Probability, and Hash Queries, respectively.
Proof. A facilitator called will solve the hyperelliptic curve discrete logarithm problem if he receives and his task will be to extract from . □
Setup: calls the Setup algorithm in which he sends the param and to
Query Phase: selects the identity and has no access to . Then, selects the identity and performs the following queries with :
H01Query: sets a list (), which is empty. When generates this query, checks the tuple in . If the value exists, then it sends to otherwise, it randomly picks from , sends to and updates with the value .
H02Query: sets an empty list (). When generates this query, checks the tuple in . If the value exists, then it sends to ; otherwise, it randomly picks from , sends to and updates with the value .
H03Query: FCR sets an empty list (). When generates this query, checks the tuple in . If the value exists, then it sends to otherwise, it randomly picks from , sends to and updates with the value .
Secret Value Generation (SVG) Query: sets an empty list (). When generates this query, checks the value in . If the value exists, then it sends to ; otherwise, it randomly picks from , sends to and updates with the value .
Public key Generation (PBKG)Query: sets an empty list (). When generates this query, checks the value in . If the tuple exists, then it sends to ; otherwise, it performs the following steps:
If , it chooses from , computes , and calculates . Then, it sends to and updates with the value ;
If , it chooses from , computes , and calculates . Then, it sends to and updates with the value .
SIGG Query: sets an empty list (). When generates this query, checks the value in . If the value exists, then it selects from and computes computes computes and sends () to . Otherwise, it selects from and sends it to .
Forgery: When the above queries are completed successfully, can return a forged certificateless signature tuple (). By using the concept of the forking lemma, can return another forged certificateless signature tuple (). So these two tuples will be only true if gets the valid value of .
To satisfy this theorem, the results generated via must meet the following conditions:
does not stop the querying process and its probability (.
does not stop the forging process for signature and its probability .
() is a valid tuple and its probability .
So, the probability of () as (().