A Survey on Pump and Dump Detection in the Cryptocurrency Market Using Machine Learning
Abstract
1. Introduction
2. Background and Related Work
2.1. Background
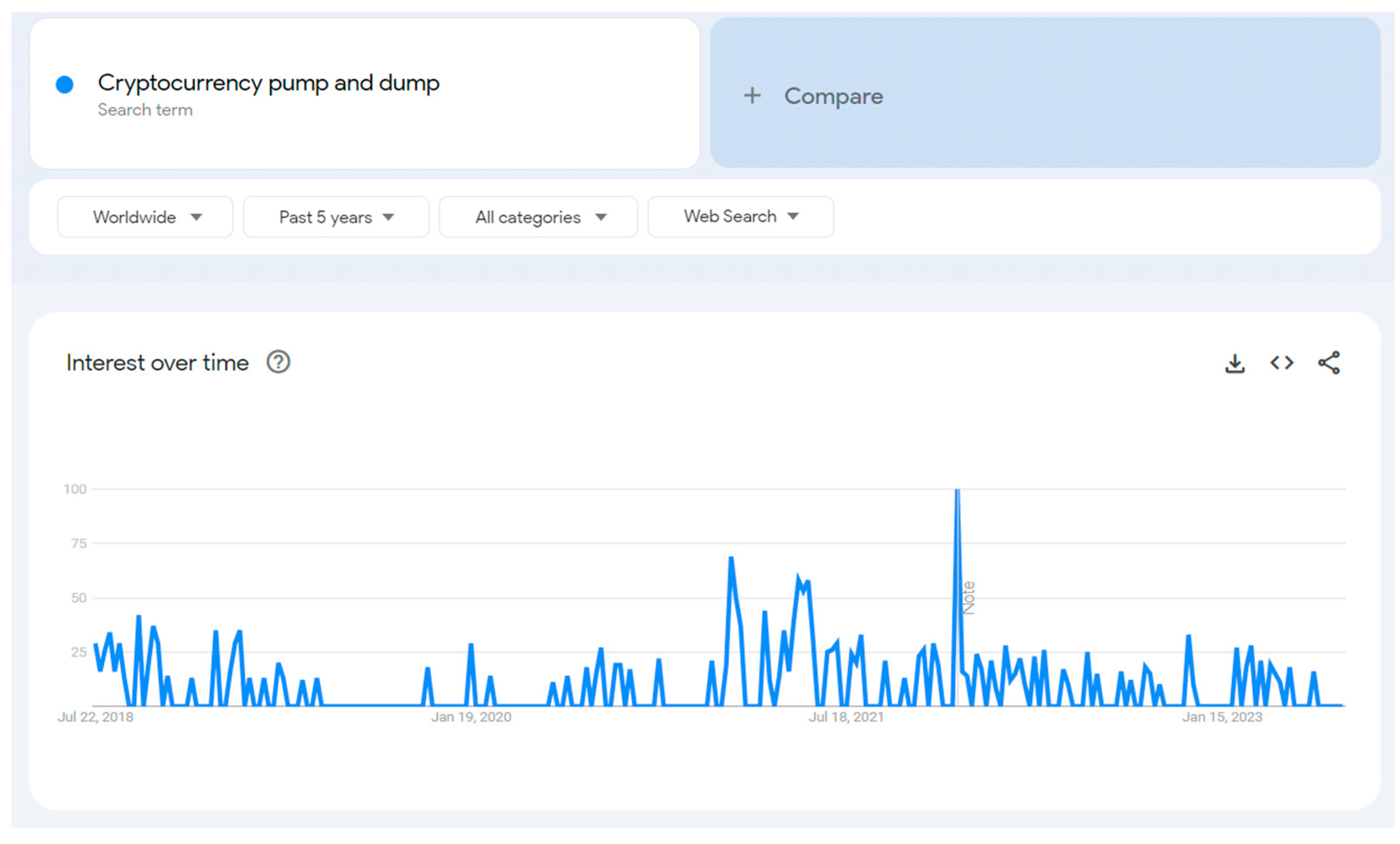
2.1.1. Cryptocurrency Manipulation
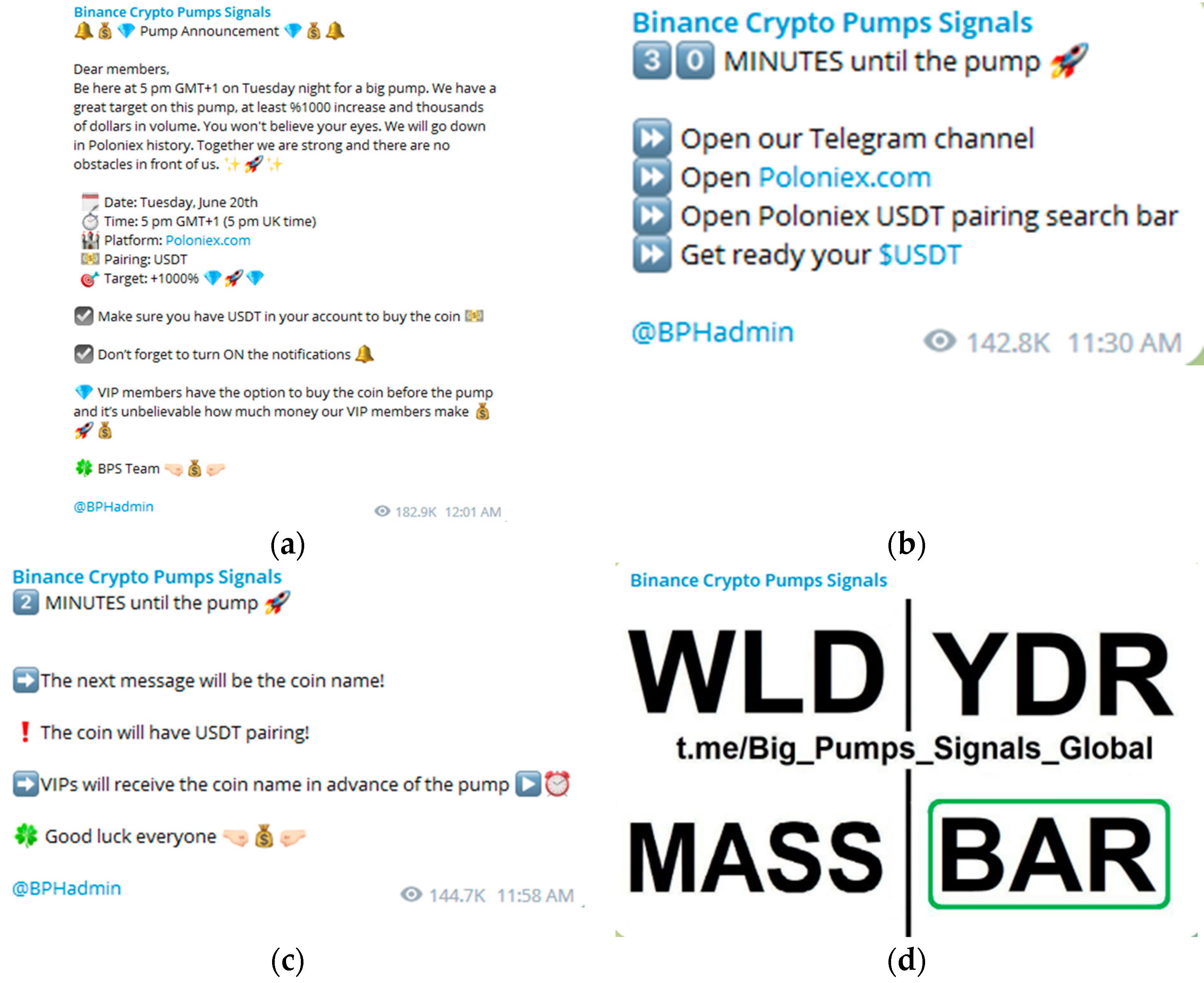
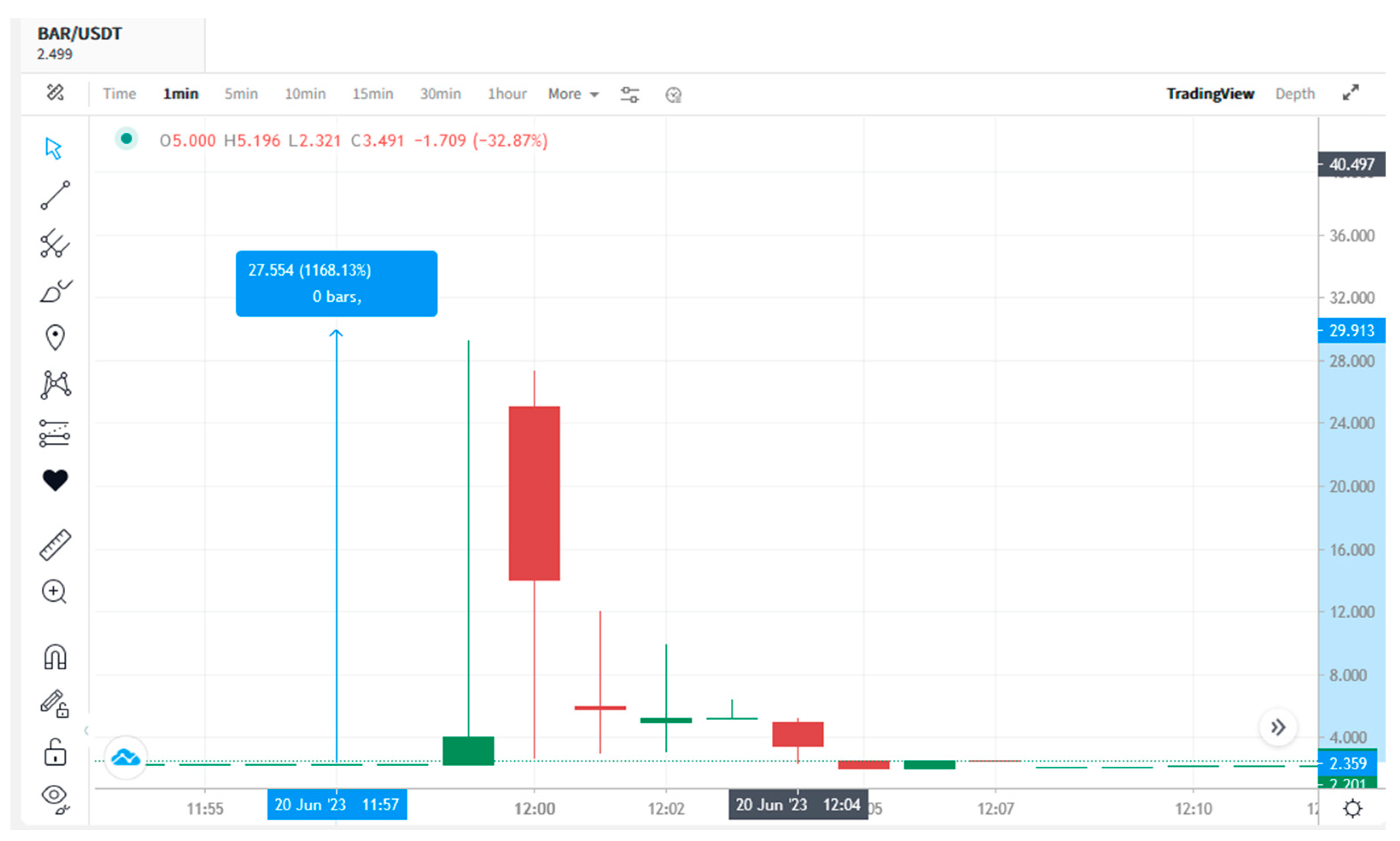
2.1.2. P&D Scheme
2.1.3. P&D Phases
2.2. Related Works
3. Methodology
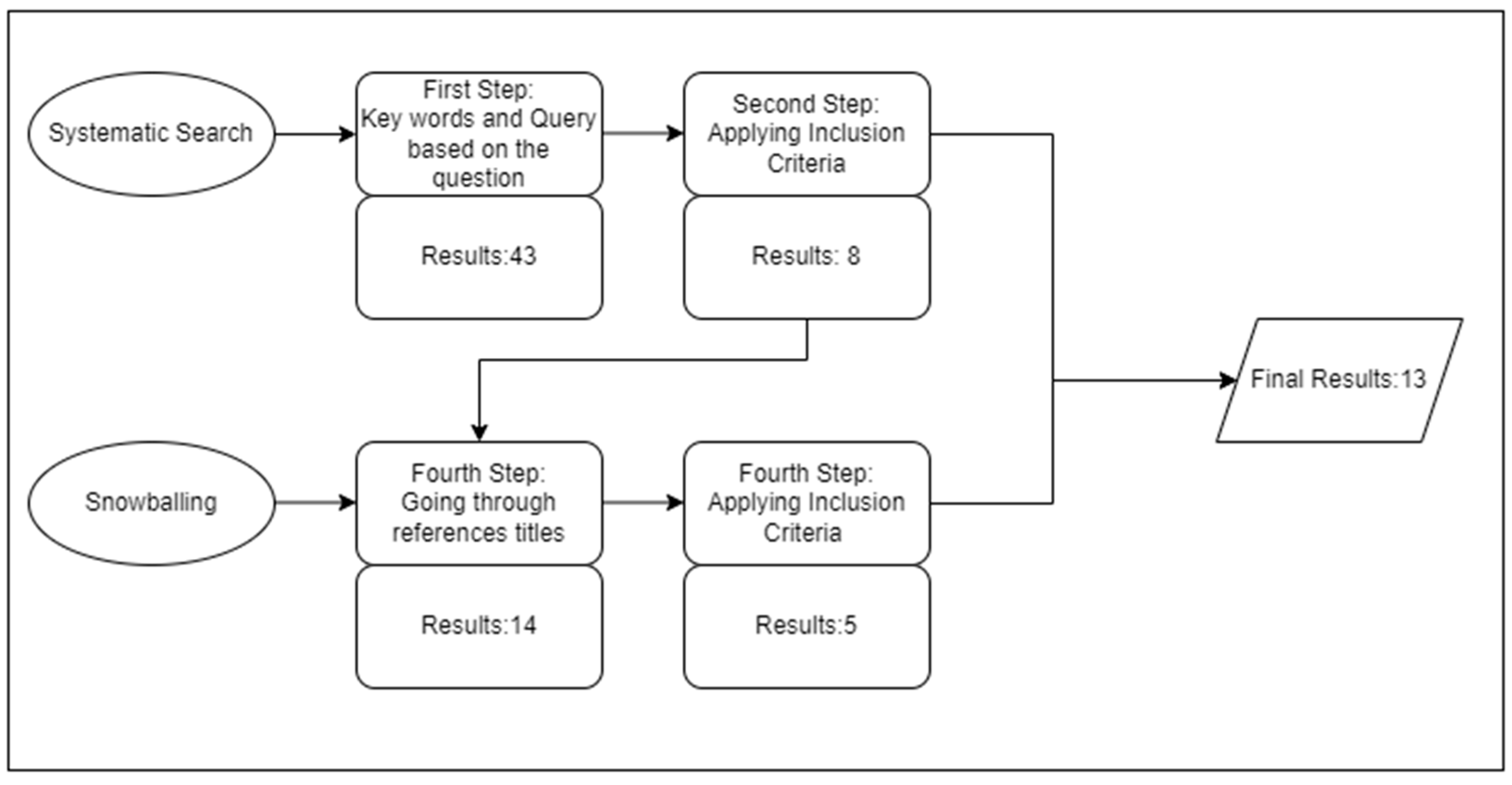
3.1. Search Strategies
- (“Pump and Dump” AND “Twitter”),
- (‘‘Pump and Dump ‘‘ AND ‘‘Machine learning’‘),
- (Real AND time AND cryptocurrency AND market AND manipulations),
- (“Pump and Dump” AND “deep learning”),
- (“Pump and Dump” AND “cryptocurrency”),
- (Cryptocurrency AND manipulation AND prediction).
3.2. Search Sources
3.3. Inclusion and Exclusion Criteria
3.4. Data Collection Procedure
3.5. Data Extraction Strategy
4. Findings
4.1. Supervised Approach
4.2. Semi-Supervised Approach
4.3. Unsupervised Approach
| Paper | Number of Coins | Exchanges | ML Models | Criteria | Best ML |
|---|---|---|---|---|---|
| Kamps and Kleinberg [13] | More than 50 pairs | Binance, Bittrex, Kraken, Kucoin, Lbank | Anomaly detection | Accuracy | Anomaly detection |
| Victor and Hagemann [39] | 172 | Binance | XGBoost | Sensitivity, specificity | XGBoost |
| Xu and Livshits [15] | 296 | Binance, Bittrex, Cryptopia, Yobit | RF, GLM | F1, AUC, precision | RF1 |
| Chen et al. [43] | 1 | Mt. Gox | Apriori | N/M | Improved a priori algorithm |
| Morgia et al. [36] | 194 | Binance | RF and LR | Precision, recall, F1 | RF (10 folds) with chunk size 25 S |
| Mansourifar et al. [45] | 10 | Lbank, Kucoin, Bittrex, Binance | Anomaly detection | Accuracy | Anomaly detection |
| Nghiem et al. [16] | 355 | Binance, Bittrex, Cryptopia, Yobit | LR as baseline model, CNN, BLSTM, and CLSTM | MAPE, precision, recall, F1 | CNN Fin 6 |
| Mirtaheri et al. [40] | 543 | N/M | SVM | Accuracy, precision, recall, F1 | SVM |
| Shao [35] | 1 | Binance | DT + CV, RF + CV, LR + CV, SVM + CV, and an ensemble of LR, RF, and SVM | Accuracy, F1, precision, recall | RF(5-fold) |
| Chadalapaka et al. [38] | 194 | Binance | CLSTM, Anomaly Transformer | Precision, recall, F1 | Anomaly transformer |
| Hu et al. [42] | 1 | Binance | LR, RF, DNN, LSTM, BLSTM, GRU, BGRU, TCN, SNN | AUC, precision, recall, F1, heat ratio | SNN |
| Morgia et al. [37] | 378 | Binance | RF, AdaBoost | F1, recall, precision | AdaBoost |
| Bello et al. [46] | Coins with a pair of BTC and a few USDT and ETH as well | Binance | LSTM-based auto-encoder | Precision, recall, F1 | LSTM-based auto-encoder |
5. Discussion and Research Directions
5.1. Discussion
5.2. Research Directions
- Detecting the end of the pump phase: It would be beneficial to develop methods for detecting the end of the pump phase with a high degree of accuracy. The unavailability of this information on social media platforms makes accurate detection difficult. To address this future work, researchers can explore advanced ML algorithms that can analyze historical price patterns and social media sentiments to detect abrupt changes in market behavior, indicating the end of the pump phase;
- Fake news and coordinated advice impact: One possible future direction is to consider the factor of fake news and coordinated investment advice. Since many individual investors rely on investment websites, news channels, and investment advice channels, if enough of them buy a specific coin because of fake news or coordinated advice, it will cause the price to change quickly. To tackle this research direction, sentiment analysis can be employed to identify false information and advice. Additionally, developing a reliable system that verifies the authenticity and credibility of news sources could help mitigate the influence of false information on the market;
- Feature combinations for enhanced model training: Various combinations of input features in the data can be used to train the models, for example, by using indicators as input features for market data, such as RSI, which considers whether an asset is overbought or oversold; MACD, which tries to forecast market trends by comparing short and long-term tendencies; SMA and EMA, which represent simple and exponential moving averages of the market data, respectively. These indicators are used to improve the efficiency of the prediction process and develop the quality of the data, which could be beneficial to the performance of the trained models. Incorporating and examining the outcomes of different models using such combinations of input data could be the subject of future studies aiming to establish general guidelines for future research in this field. Researchers can address this future work by conducting an extensive feature engineering analysis to identify the most relevant indicators and combine them to enhance model training;
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Liang, J.; Li, L.; Chen, W.; Zeng, D. Towards an understanding of cryptocurrency: A comparative analysis of cryptocurrency, foreign exchange, and stock. In Proceedings of the 2019 IEEE International Conference on Intelligence and Security Informatics (ISI), Shenzhen, China, 1–3 July 2019; pp. 137–139. [Google Scholar]
- Bunjaku, F.; Gjorgieva-Trajkovska, O.; Miteva-Kacarski, E. Cryptocurrencies–advantages and disadvantages. J. Econ. 2017, 2, 31–39. [Google Scholar]
- Eigelshoven, F.; Ullrich, A.; Parry, D.A. Cryptocurrency market manipulation: A systematic literature review. In Proceedings of the 42nd International Conference on Information Systems, Austin, TX, USA, 12–15 December 2021. [Google Scholar]
- Baum, S.C. Cryptocurrency Fraud: A Look into the Frontier of Fraud. Bachelor’s Thesis, Georgia Southern University, Statesboro, GA, USA, 2018. [Google Scholar]
- Alyami, M.; Alhotaylah, R.; Alshehri, S.; Alghamdi, A. Phishing Attacks on Cryptocurrency Investors in the Arab States of the Gulf. J. Risk Financ. Manag. 2023, 16, 271. [Google Scholar] [CrossRef]
- Bonifazi, G.; Corradini, E.; Ursino, D.; Virgili, L. A social network analysis–based approach to investigate user behaviour during a cryptocurrency speculative bubble. J. Inf. Sci. 2021, 49, 1060–1085. [Google Scholar] [CrossRef]
- Hamrick, J.; Rouhi, F.; Mukherjee, A.; Feder, A.; Gandal, N.; Moore, T.; Vasek, M. An examination of the cryptocurrency pump-and-dump ecosystem. Inf. Process. Manag. 2021, 58, 102506. [Google Scholar] [CrossRef]
- Victor, F.; Weintraud, A.M. Detecting and quantifying wash trading on decentralized cryptocurrency exchanges. In Proceedings of the Web Conference 2021, Ljubljana, Slovenia, 19–23 April 2021; International World Wide Web Conference Committee: Ljubljana, Slovenia, 2021; pp. 23–32. [Google Scholar]
- Le Pennec, G.; Fiedler, I.; Ante, L. Wash trading at cryptocurrency exchanges. Financ. Res. Lett. 2021, 43, 101982. [Google Scholar] [CrossRef]
- Cong, L.W.; Li, X.; Tang, K.; Yang, Y. Crypto Wash Trading; National Bureau of Economic Research: Washington, DC, USA, 2022. [Google Scholar]
- Bonifazi, G.; Cauteruccio, F.; Corradini, E.; Marchetti, M.; Montella, D.; Scarponi, S.; Ursino, D.; Virgili, L. Performing Wash Trading on NFTs: Is the Game Worth the Candle? Big Data Cogn. Comput. 2023, 7, 38. [Google Scholar] [CrossRef]
- Cartea, Á.; Jaimungal, S.; Wang, Y. Spoofing and price manipulation in order-driven markets. Appl. Math. Financ. 2020, 27, 67–98. [Google Scholar] [CrossRef]
- Kamps, J.; Kleinberg, B. To the moon: Defining and detecting cryptocurrency pump-and-dumps. Crime Sci. 2018, 7, 18. [Google Scholar] [CrossRef]
- Binance. Public Rest Api for Binance. Available online: https://github.com/binance-exchange/binance-official-api-docs/ (accessed on 20 June 2023).
- Xu, J.; Livshits, B. The Anatomy of a Cryptocurrency Pump-and-Dump Scheme. In Proceedings of the USENIX Security Symposium, Santa Clara, CA, USA, 14–16 August 2019; pp. 1609–1625. [Google Scholar]
- Nghiem, H.; Muric, G.; Morstatter, F.; Ferrara, E. Detecting cryptocurrency pump-and-dump frauds using market and social signals. Expert Syst. Appl. 2021, 182, 115284. [Google Scholar] [CrossRef]
- Big Pumps Signals Global. Available online: https://t.me/Big_Pumps_Signals_Global (accessed on 26 June 2023).
- Poloniex. Available online: https://poloniex.com/ (accessed on 23 June 2023).
- kucoin. Available online: https://www.kucoin.com/ (accessed on 23 June 2023).
- Khodabandehlou, S.; Golpayegani, S.A.H. Market manipulation detection: A systematic literature review. Expert Syst. Appl. 2022, 210, 118330. [Google Scholar] [CrossRef]
- Zulkifley, M.A.; Munir, A.F.; Sukor, A.; Edil, M.; Mohd Shafiai, M.H. A Survey on Stock Market Manipulation Detectors Using Artificial Intelligence. Comput. Mater. Contin. 2023, 75, 4395–4418. [Google Scholar]
- Chullamonthon, P.; Tangamchit, P. Ensemble of supervised and unsupervised deep neural networks for stock price manipulation detection. Expert Syst. Appl. 2023, 220, 119698. [Google Scholar] [CrossRef]
- Leangarun, T.; Tangamchit, P.; Thajchayapong, S. Stock price manipulation detection using deep unsupervised learning: The case of Thailand. IEEE Access 2021, 9, 106824–106838. [Google Scholar] [CrossRef]
- Chullamonthon, P.; Tangamchit, P. A transformer model for stock price manipulation detection in the stock exchange of Thailand. In Proceedings of the 2022 19th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology (ECTI-CON), Prachuap Khiri Khan, Thailand, 24–27 May 2022; pp. 1–4. [Google Scholar]
- Rizvi, B.; Belatreche, A.; Bouridane, A. A dendritic cell immune system inspired approach for stock market manipulation detection. In Proceedings of the 2019 IEEE Congress on Evolutionary Computation (CEC), Wellington, New Zealand, 10–13 June 2019; pp. 3325–3332. [Google Scholar]
- Rizvi, B.; Belatreche, A.; Bouridane, A. Immune inspired dendritic cell algorithm for stock price manipulation detection. In Intelligent Systems and Applications: Proceedings of the 2019 Intelligent Systems Conference (IntelliSys); Springer: Cham, Switzerland, 2020; Volume 1, pp. 352–361. [Google Scholar]
- Cao, Y.; Li, Y.; Coleman, S.; Belatreche, A.; McGinnity, T.M. Adaptive hidden Markov model with anomaly states for price manipulation detection. IEEE Trans. Neural Netw. Learn. Syst. 2014, 26, 318–330. [Google Scholar] [CrossRef]
- Uslu, N.C.; Akal, F. A machine learning approach to detection of trade-based manipulations in Borsa Istanbul. Comput. Econ. 2022, 60, 25–45. [Google Scholar] [CrossRef]
- Yagemann, C.; Chung, S.P.; Uzun, E.; Ragam, S.; Saltaformaggio, B.; Lee, W. On the feasibility of automating stock market manipulation. In Proceedings of the Annual Computer Security Applications Conference, Austin, TX, USA, 7–11 December 2020; pp. 277–290. [Google Scholar]
- Rizvi, B.; Belatreche, A.; Bouridane, A.; Watson, I. Detection of stock price manipulation using kernel based principal component analysis and multivariate density estimation. IEEE Access 2020, 8, 135989–136003. [Google Scholar] [CrossRef]
- Leangarun, T.; Tangamchit, P.; Thajchayapong, S. Stock price manipulation detection using a computational neural network model. In Proceedings of the 2016 Eighth International Conference on Advanced Computational Intelligence (ICACI), Chiang Mai, Thailand, 14–16 February 2016; pp. 337–341. [Google Scholar]
- Abbas, B.; Belatreche, A.; Bouridane, A. Stock price manipulation detection using empirical mode decomposition based kernel density estimation clustering method. In Intelligent Systems and Applications: Proceedings of the 2018 Intelligent Systems Conference (IntelliSys); Springer: Cham, Switzerland, 2019; Volume 2, pp. 851–866. [Google Scholar]
- Kakde, Y.; Chavan, G.; Sah, B.; Sen, A. Solution Approach for Detection of Stock Price Manipulation by Market Operators. In Smart Technologies in Data Science and Communication: Proceedings of SMART-DSC 2022; Springer: Berlin/Heidelberg, Germany, 2023; pp. 281–288. [Google Scholar]
- Zhao, W.; Alwidian, S.; Mahmoud, Q.H. Adversarial Training Methods for Deep Learning: A Systematic Review. Algorithms 2022, 15, 283. [Google Scholar] [CrossRef]
- Shao, S. The effectiveness of supervised learning models in detection of pump and dump activity in Dogecoin. In Proceedings of the Second IYSF Academic Symposium on Artificial Intelligence and Computer Engineering, Xi’an, China, 8–10 October 2021; pp. 356–363. [Google Scholar]
- La Morgia, M.; Mei, A.; Sassi, F.; Stefa, J. Pump and dumps in the bitcoin era: Real time detection of cryptocurrency market manipulations. In Proceedings of the 2020 29th International Conference on Computer Communications and Networks (ICCCN), Honolulu, HI, USA, 3–6 August 2020; pp. 1–9. [Google Scholar]
- La Morgia, M.; Mei, A.; Sassi, F.; Stefa, J. The doge of wall street: Analysis and detection of pump and dump cryptocurrency manipulations. ACM Trans. Internet Technol. 2023, 23, 1–28. [Google Scholar] [CrossRef]
- Chadalapaka, V.; Chang, K.; Mahajan, G.; Vasil, A. Crypto Pump and Dump via Deep Learning Techniques. arXiv 2022, arXiv:2205.04646. [Google Scholar]
- Victor, F.; Hagemann, T. Cryptocurrency pump and dump schemes: Quantification and detection. In Proceedings of the 2019 International Conference on Data Mining Workshops (ICDMW), Beijing, China, 8–11 November 2019; pp. 244–251. [Google Scholar]
- Mirtaheri, M.; Abu-El-Haija, S.; Morstatter, F.; Ver Steeg, G.; Galstyan, A. Identifying and analyzing cryptocurrency manipulations in social media. IEEE Trans. Comput. Soc. Syst. 2021, 8, 607–617. [Google Scholar] [CrossRef]
- Coin Market Cap. Available online: https://coinmarketcap.com/ (accessed on 23 June 2023).
- Hu, S.; Zhang, Z.; Lu, S.; He, B.; Li, Z. Sequence-based target coin prediction for cryptocurrency pump-and-dump. Proc. ACM Manag. Data 2023, 1, 1–19. [Google Scholar] [CrossRef]
- Chen, W.; Xu, Y.; Zheng, Z.; Zhou, Y.; Yang, J.E.; Bian, J. Detecting “Pump & Dump Schemes” on cryptocurrency market using an improved Apriori Algorithm. In Proceedings of the 2019 IEEE International Conference on Service-Oriented System Engineering (SOSE), San Francisco, CA, USA, 4–9 April 2019; pp. 293–295. [Google Scholar]
- Ccxt. Available online: https://github.com/ccxt/ccxt (accessed on 26 June 2023).
- Mansourifar, H.; Chen, L.; Shi, W. Hybrid cryptocurrency pump and dump detection. arXiv 2020, arXiv:2003.06551. [Google Scholar]
- Bello, A.; Schneider, J.; Di Pietro, R. LLD: A Low Latency Detection Solution to Thwart Cryptocurrency Pump & Dumps. In Proceedings of the 2023 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Dubai, United Arab Emirates, 1–5 May 2023. [Google Scholar]

| Paper Title | Market Manipulation | P&D | ML for Detection | Cryptocurrency | Summary |
|---|---|---|---|---|---|
| Cryptocurrency Market Manipulation: A Systematic Literature Review [3] | yes | yes | no | yes | A comprehensive survey on cryptocurrency manipulation papers that provides a complete definition of different manipulations in cryptocurrency and identifies market vulnerabilities. |
| Market manipulation detection: A systematic literature review [20] | yes | yes | yes | no | A survey of the literature on market manipulation detection from 2010 to 2020. It identifies different manipulations and focuses on trade-based manipulation. |
| A Survey on Stock Market Manipulation Detectors Using Artificial Intelligence [21] | yes | yes | yes | no | A survey that aims to discuss state-of-the-art automated methods for detecting manipulations. It also defines a manipulation taxonomy. |
| This Survey | yes | yes | yes | yes | A comprehensive survey that examines the recent progress in using ML to detect and predict P&D in the cryptocurrency market. |
| Inclusion Criteria | Exclusion Criteria |
|---|---|
| English | Languages other than English |
| P&D | Other forms of manipulation |
| Crypto currencies | Other stock markets |
| Utilizing ML for P&D detection | Absence of model for P&D detection |
| Paper | Strengths | Limitations |
|---|---|---|
| Kamps and Kleinberg [13] |
|
|
| Victor and Hagemann [39] |
|
|
| Xu and Livshits [15] |
|
|
| Chen et al. [43] |
|
|
| Morgia et al. [36] |
|
|
| Mansourifar et al. [45] |
|
|
| Nghiem et al. [16] |
|
|
| Mirtaheri et al. [40] |
|
|
| Shao [35] |
|
|
| Chadalapaka et al. [38] |
|
|
| Hu et al. [42] |
|
|
| Morgia et al. [37] |
|
|
| Bello et al. [46] |
|
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rajaei, M.J.; Mahmoud, Q.H. A Survey on Pump and Dump Detection in the Cryptocurrency Market Using Machine Learning. Future Internet 2023, 15, 267. https://doi.org/10.3390/fi15080267
Rajaei MJ, Mahmoud QH. A Survey on Pump and Dump Detection in the Cryptocurrency Market Using Machine Learning. Future Internet. 2023; 15(8):267. https://doi.org/10.3390/fi15080267
Chicago/Turabian StyleRajaei, Mohammad Javad, and Qusay H. Mahmoud. 2023. "A Survey on Pump and Dump Detection in the Cryptocurrency Market Using Machine Learning" Future Internet 15, no. 8: 267. https://doi.org/10.3390/fi15080267
APA StyleRajaei, M. J., & Mahmoud, Q. H. (2023). A Survey on Pump and Dump Detection in the Cryptocurrency Market Using Machine Learning. Future Internet, 15(8), 267. https://doi.org/10.3390/fi15080267






