NDN-BDA: A Blockchain-Based Decentralized Data Authentication Mechanism for Vehicular Named Data Networking
Abstract
1. Introduction
2. Named Data Networking: Nuts and Bolts
2.1. Security Principles in NDN
2.1.1. Digital Signatures
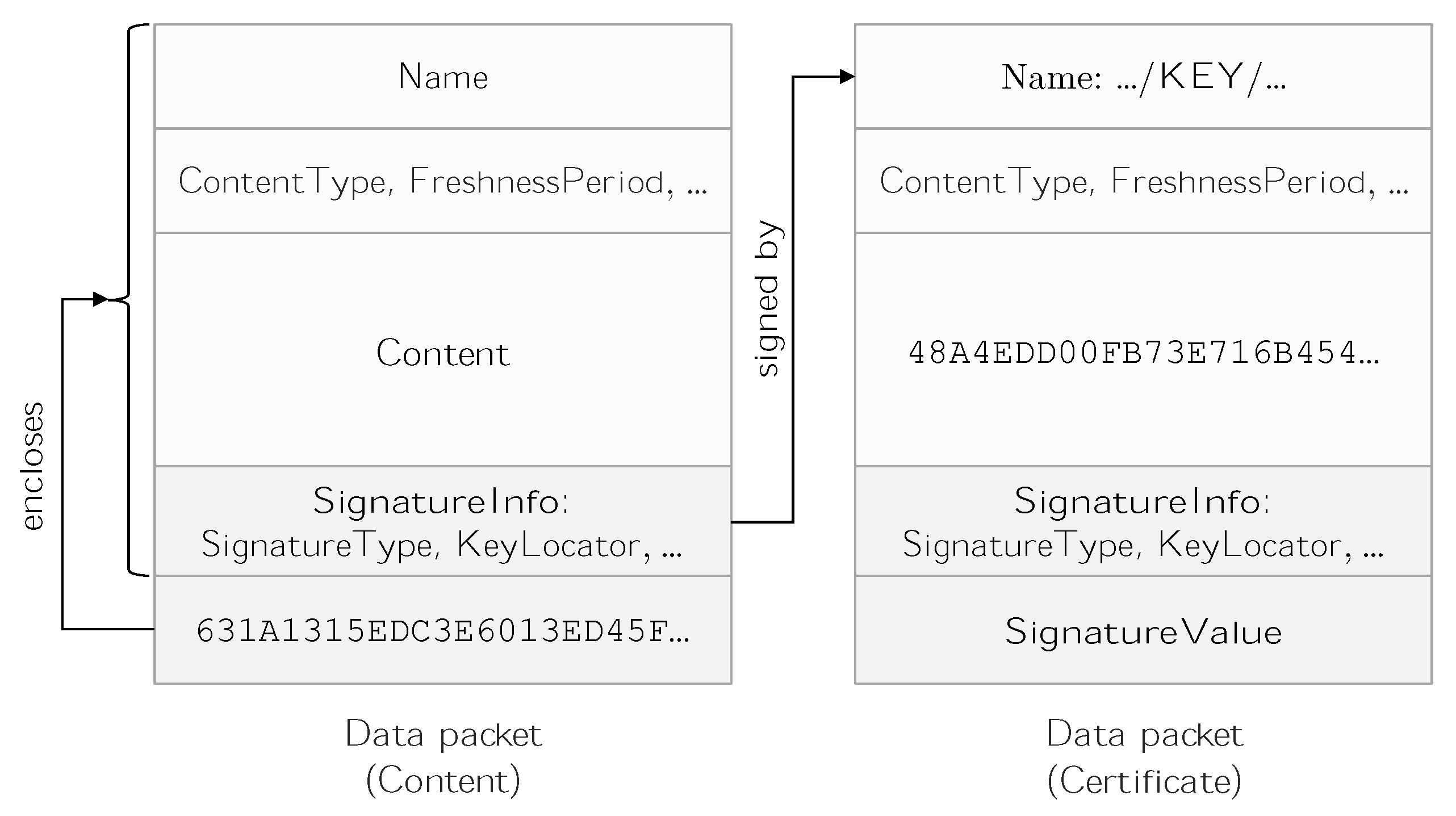
2.1.2. NDN Certificates
2.1.3. Trust Model
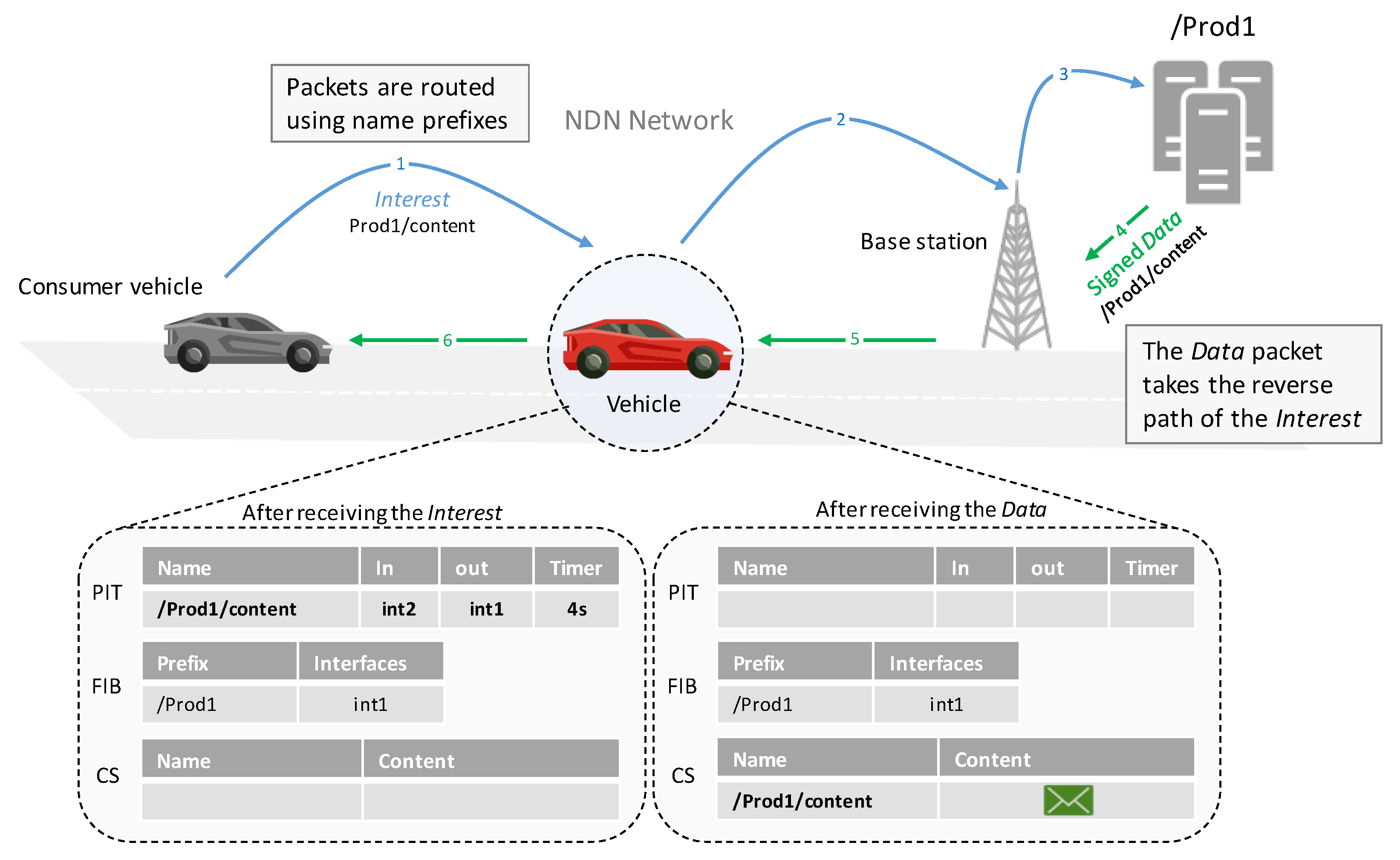
2.2. Packet Forwarding
2.3. Mobility Support in NDN
3. Related Work
4. Threat Model and Assumptions
5. NDN-BDA
5.1. Protocol Overview
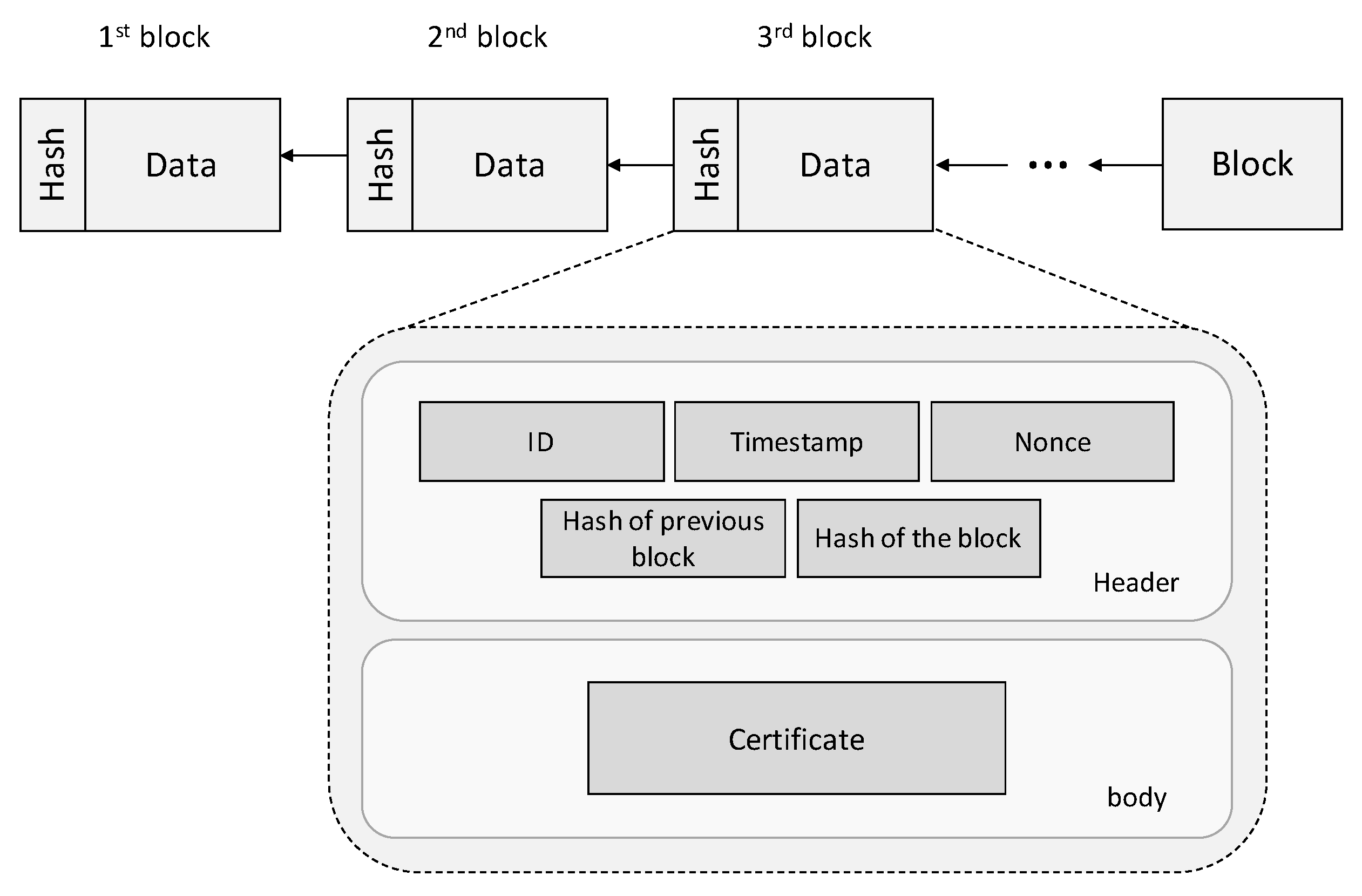
5.2. Blockchain
5.3. Trust Schema
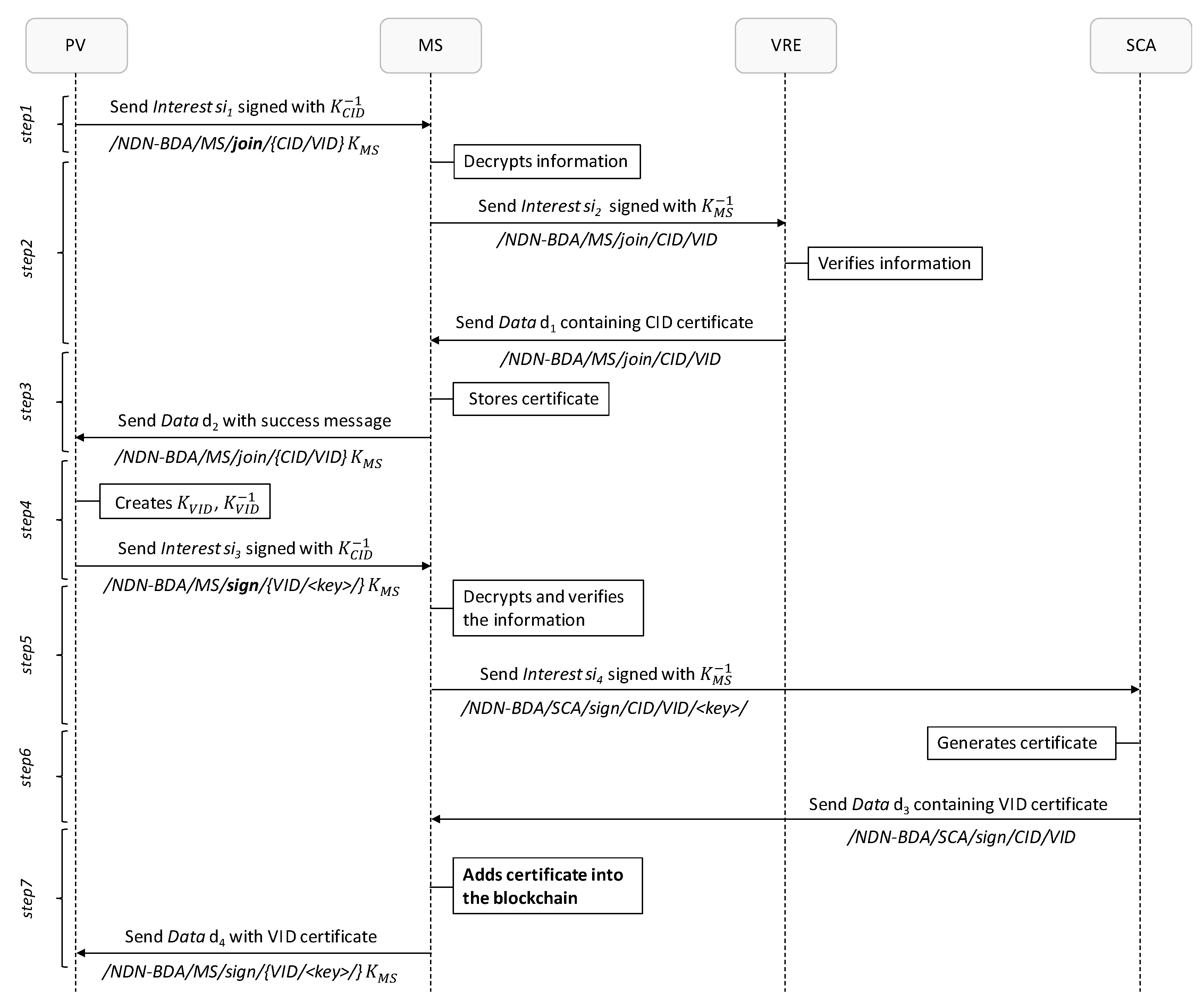
5.4. Producer Registration
5.5. Data Authentication Process
6. Evaluation and Discussion
6.1. Security Analysis
6.1.1. Impersonation Attack
6.1.2. Blockchain Tempering Attack
6.1.3. Man-in-the-Middle Attack
6.1.4. Denial of Service Attack
6.2. Protocol Validation
- (/NDN-BDA/MS/join/{CID/VID}).
- (/NDN-BDA/MS/sign/VID/<key>/).
- (/NDN-BDA/MS/join/{CID/VID}).
- (/NDN-BDA/MS/join/CID/VID).
- (/NDN-BDA/MS/join/CID/VID).
- (/NDN-BDA/MS/join/{CID/VID}).
- (/NDN-BDA/MS/sign/VID/<key>/.
- (/NDN-BDA/SCA/sign/CID/VID/<key>).
- (/NDN-BDA/SCA/sign/CID/VID).
- (/NDN-BDA/MS/sign/VID/<key>/.
7. Conclusions and Future Works
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Cisco Annual Internet Report (2018–2023) White Paper. Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-Internet-report/white-paper-c11-741490.html (accessed on 7 March 2023).
- Xylomenos, G.; Ververidis, C.N.; Siris, V.A.; Fotiou, N.; Tsilopoulos, C.; Vasilakos, X.; Katsaros, K.V.; Polyzos, G.C. A survey of information-centric networking research. IEEE Commun. Surv. Tutor. 2013, 16, 1024–1049. [Google Scholar] [CrossRef]
- Pan, J.; Paul, S.; Jain, R. A survey of the research on future Internet architectures. IEEE Commun. Mag. 2011, 49, 26–36. [Google Scholar] [CrossRef]
- Koponen, T.; Chawla, M.; Chun, B.G.; Ermolinskiy, A.; Kim, K.H.; Shenker, S.; Stoica, I. A data-oriented (and beyond) network architecture. In Proceedings of the 2007 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Kyoto, Japan, 27–31 August 2007; pp. 181–192. [Google Scholar]
- Fotiou, N.; Nikander, P.; Trossen, D.; Polyzos, G.C. Developing information networking further: From PSIRP to PURSUIT. In Proceedings of the Broadband Communications, Networks, and Systems, 7th International ICST Conference, BROADNETS 2010, Athens, Greece, 25–27 October 2010; Revised Selected Papers 7. Springer: Berlin/Heidelberg, Germany, 2012; pp. 1–13. [Google Scholar]
- Zhang, L.; Afanasyev, A.; Burke, J.; Jacobson, V.; Claffy, K.C.; Crowley, P.; Papadopoulos, C.; Wang, L.; Zhang, B. Named data networking. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 66–73. [Google Scholar] [CrossRef]
- Jacobson, V.; Mosko, M.; Smetters, D.; Garcia-Luna-Aceves, J. Content-Centric Networking; Whitepaper; Palo Alto Research Center: Palo Alto, CA, USA, 2007; pp. 2–4. [Google Scholar]
- NDN Packet Format Specification Version 0.3. Available online: https://named-data.net/doc/NDN-packet-spec/current (accessed on 3 March 2023).
- Signed Interest. NDN Packet Format Specification Version 0.3. Available online: https://named-data.net/doc/NDN-packet-spec/current/signed-interest.html (accessed on 3 March 2023).
- Zhang, H.; Li, Y.; Zhang, Z.; Afanasyev, A.; Zhang, L. Ndn host model. ACM SIGCOMM Comput. Commun. Rev. 2018, 48, 35–41. [Google Scholar] [CrossRef]
- Zhang, M.; Luo, H.; Zhang, H. A survey of caching mechanisms in information-centric networking. IEEE Commun. Surv. Tutor. 2015, 17, 1473–1499. [Google Scholar] [CrossRef]
- Zhang, Z.; Yu, Y.; Zhang, H.; Newberry, E.; Mastorakis, S.; Li, Y.; Afanasyev, A.; Zhang, L. An overview of security support in named data networking. IEEE Commun. Mag. 2018, 56, 62–68. [Google Scholar] [CrossRef]
- Tehrani, P.F.; Osterweil, E.; Schmidt, T.C.; Wählisch, M. SoK: Public key and namespace management in NDN. In Proceedings of the 9th ACM Conference on Information-Centric Networking, Osaka, Japan, 19–21 September 2022; pp. 67–79. [Google Scholar]
- Li, Y.; Zhang, Z.; Wang, X.; Lu, E.; Zhang, D.; Zhang, L. A secure sign-on protocol for smart homes over named data networking. IEEE Commun. Mag. 2019, 57, 62–68. [Google Scholar] [CrossRef]
- Zhang, Z.; Yu, Y.; Afanasyev, A.; Zhang, L. NDN Certificate Management Protocol (NDNCERT); Technical Report NDN-0050; NDN: Helensvale, Australia, 2017. [Google Scholar]
- Zhang, Z.; Yu, Y.; Ramani, S.K.; Afanasyev, A.; Zhang, L. Nac: Automating access control via named data. In Proceedings of the MILCOM 2018—2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; pp. 626–633. [Google Scholar]
- Nour, B.; Khelifi, H.; Hussain, R.; Mastorakis, S.; Moungla, H. Access control mechanisms in named data networks: A comprehensive survey. ACM Comput. Surv. 2021, 54, 61. [Google Scholar] [CrossRef]
- Lee, C.A.; Zhang, Z.; Tu, Y.; Afanasyev, A.; Zhang, L. Supporting virtual organizations using attribute-based encryption in named data networking. In Proceedings of the 2018 IEEE 4th International Conference on Collaboration and Internet Computing (CIC), Philadelphia, PA, USA, 18–20 October 2018; pp. 188–196. [Google Scholar]
- Li, Z.; Xu, Y.; Zhang, B.; Yan, L.; Liu, K. Packet forwarding in named data networking requirements and survey of solutions. IEEE Commun. Surv. Tutor. 2018, 21, 1950–1987. [Google Scholar] [CrossRef]
- Voitalov, I.; Aldecoa, R.; Wang, L.; Krioukov, D. Geohyperbolic routing and addressing schemes. ACM SIGCOMM Comput. Commun. Rev. 2017, 47, 11–18. [Google Scholar] [CrossRef]
- Zhang, Y.; Afanasyev, A.; Burke, J.; Zhang, L. A survey of mobility support in named data networking. In Proceedings of the 2016 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), San Francisco, CA, USA, 10–14 April 2016; pp. 83–88. [Google Scholar]
- Khelifi, H.; Luo, S.; Nour, B.; Moungla, H.; Faheem, Y.; Hussain, R.; Ksentini, A. Named data networking in vehicular ad hoc networks: State-of-the-art and challenges. IEEE Commun. Surv. Tutor. 2019, 22, 320–351. [Google Scholar] [CrossRef]
- Zhu, Z.; Afanasyev, A.; Zhang, L. A New Perspective on Mobility Support. NDN, Technical Report NDN-0013. 2013. Available online: https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=a6fc488646c27d13191691f7145745ba828cff9b (accessed on 30 March 2023).
- Afanasyev, A.; Jiang, X.; Yu, Y.; Tan, J.; Xia, Y.; Mankin, A.; Zhang, L. NDNS: A DNS-like name service for NDN. In Proceedings of the 2017 26th International Conference on Computer Communication and Networks (ICCCN), Vancouver, BC, Canada, 31 July–3 August 2017; pp. 1–9. [Google Scholar]
- Zhang, Y.; Xia, Z.; Mastorakis, S.; Zhang, L. Kite: Producer mobility support in named data networking. In Proceedings of the 5th ACM Conference on Information-Centric Networking, Boston, MA, USA, 21–23 September 2018; pp. 125–136. [Google Scholar]
- Chowdhury, M.; Gawande, A.; Wang, L. Anonymous authentication and pseudonym-renewal for VANET in NDN. In Proceedings of the 4th ACM Conference on Information-Centric Networking, Berlin, Germany, 26–28 September 2017; pp. 222–223. [Google Scholar]
- Lu, Y.; Wang, C.; Yue, M.; Wu, Z. Consumer-source authentication with conditional anonymity in information-centric networking. Inf. Sci. 2023, 624, 378–394. [Google Scholar] [CrossRef]
- Yu, Y.; Afanasyev, A.; Seedorf, J.; Zhang, Z.; Zhang, L. NDN DeLorean: An authentication system for data archives in named data networking. In Proceedings of the 4th ACM Conference on Information-Centric Networking, Berlin, Germany, 26–28 September 2017; pp. 11–21. [Google Scholar]
- Zhang, Z.; Liu, S.; King, R.; Zhang, L. Ndn-mps: Supporting multiparty authentication over named data networking. In Proceedings of the 8th ACM Conference on Information-Centric Networking, Paris, France, 22–24 September 2021; pp. 83–94. [Google Scholar]
- Li, T.; Shang, W.; Afanasyev, A.; Wang, L.; Zhang, L. A brief introduction to ndn dataset synchronization (ndn sync). In Proceedings of the MILCOM 2018—2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; pp. 612–618. [Google Scholar]
- Li, R.; Asaeda, H.; Wu, J. DCAuth: Data-centric authentication for secure in-network big-data retrieval. IEEE Trans. Netw. Sci. Eng. 2018, 7, 15–27. [Google Scholar] [CrossRef]
- Barka, E.; Kerrache, C.A.; Hussain, R.; Lagraa, N.; Lakas, A.; Bouk, S.H. A trusted lightweight communication strategy for flying named data networking. Sensors 2018, 18, 2683. [Google Scholar] [CrossRef]
- Zhu, K.; Chen, Z.; Yan, W.; Zhang, L. Security attacks in named data networking of things and a blockchain solution. IEEE Internet Things J. 2018, 6, 4733–4741. [Google Scholar] [CrossRef]
- Goyal, S.; Sharma, N.; Kaushik, I.; Bhushan, B. Blockchain as a solution for security attacks in named data networking of things. In Security and Privacy Issues in IoT Devices and Sensor Networks; Academic Press: Cambridge, MA, USA, 2021; pp. 211–243. [Google Scholar]
- Chen, C.; Wang, C.; Qiu, T.; Lv, N.; Pei, Q. A secure content sharing scheme based on blockchain in vehicular named data networks. IEEE Trans. Ind. Inform. 2019, 16, 3278–3289. [Google Scholar] [CrossRef]
- Rawat, D.B.; Doku, R.; Adebayo, A.; Bajracharya, C.; Kamhoua, C. Blockchain enabled named data networking for secure vehicle-to-everything communications. IEEE Netw. 2020, 34, 185–189. [Google Scholar] [CrossRef]
- Khelifi, H.; Luo, S.; Nour, B.; Moungla, H.; Ahmed, S.H.; Guizani, M. A blockchain-based architecture for secure vehicular Named Data Networks. Comput. Electr. Eng. 2020, 86, 106715. [Google Scholar] [CrossRef]
- Conti, M.; Hassan, M.; Lal, C. BlockAuth: BlockChain based distributed producer authentication in ICN. Comput. Netw. 2019, 164, 106888. [Google Scholar] [CrossRef]
- Zhao, Y.; Qu, Y.; Xiang, Y.; Zhang, Y.; Gao, L. A Lightweight Model-Based Evolutionary Consensus Protocol in Blockchain as a Service for IoT. IEEE Trans. Serv. Comput. 2023; Early Access. [Google Scholar]
- Vigano, L. Automated security protocol analysis with the AVISPA tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61–86. [Google Scholar] [CrossRef]
- Benmoussa, A.; Kerrache, C.A.; Lagraa, N.; Mastorakis, S.; Lakas, A.; Tahari, A.E.K. Interest Flooding Attacks in Named Data Networking: Survey of Existing Solutions, Open Issues, Requirements and Future Directions. ACM Comput. Surv. 2021, 55, 139. [Google Scholar] [CrossRef]
- Benmoussa, A.; El Karim Tahari, A.; Kerrache, C.A.; Lagraa, N.; Lakas, A.; Hussain, R.; Ahmad, F. MSIDN: Mitigation of sophisticated interest flooding-based DDoS attacks in named data networking. Future Gener. Comput. Syst. 2020, 107, 293–306. [Google Scholar] [CrossRef]
- Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Mantovani, J.; Mödersheim, S.; Vigneron, L. A high level protocol specification language for industrial security-sensitive protocols. In Proceedings of the Workshop on Specification and Automated Processing of Security Requirements-SAPS’2004, Linz, Austria, 20–25 September 2004; Austrian Computer Society: Vienna, Austria, 2004; p. 13. [Google Scholar]





| Notation | Meaning |
|---|---|
| Vehicle Registration Entity | |
| Management Server | |
| System Certification Authority | |
| Producer Vehicle | |
| Consumer Vehicle | |
| The signed Interest packet | |
| The Interest packet | |
| The Data packet | |
| K | Cryptographic Key |
| Encrypted message m with K | |
| Public key of | |
| Private key of | |
| Decrypts a message m encrypted with using | |
| Blockchain | |
| Adversary node | |
| impersonates to send a message m to |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Benmoussa, A.; Kerrache, C.A.; Calafate, C.T.; Lagraa, N. NDN-BDA: A Blockchain-Based Decentralized Data Authentication Mechanism for Vehicular Named Data Networking. Future Internet 2023, 15, 167. https://doi.org/10.3390/fi15050167
Benmoussa A, Kerrache CA, Calafate CT, Lagraa N. NDN-BDA: A Blockchain-Based Decentralized Data Authentication Mechanism for Vehicular Named Data Networking. Future Internet. 2023; 15(5):167. https://doi.org/10.3390/fi15050167
Chicago/Turabian StyleBenmoussa, Ahmed, Chaker Abdelaziz Kerrache, Carlos T. Calafate, and Nasreddine Lagraa. 2023. "NDN-BDA: A Blockchain-Based Decentralized Data Authentication Mechanism for Vehicular Named Data Networking" Future Internet 15, no. 5: 167. https://doi.org/10.3390/fi15050167
APA StyleBenmoussa, A., Kerrache, C. A., Calafate, C. T., & Lagraa, N. (2023). NDN-BDA: A Blockchain-Based Decentralized Data Authentication Mechanism for Vehicular Named Data Networking. Future Internet, 15(5), 167. https://doi.org/10.3390/fi15050167








