Utilizing Blockchain for IoT Privacy through Enhanced ECIES with Secure Hash Function
Abstract
:1. Introduction
2. Related Works
2.1. Ethereum Public Blockchain
2.2. Consortium Blockchain
2.3. Hyperledger Fabric Blockchain
2.4. Blockchain Mechanisms for IoT Security
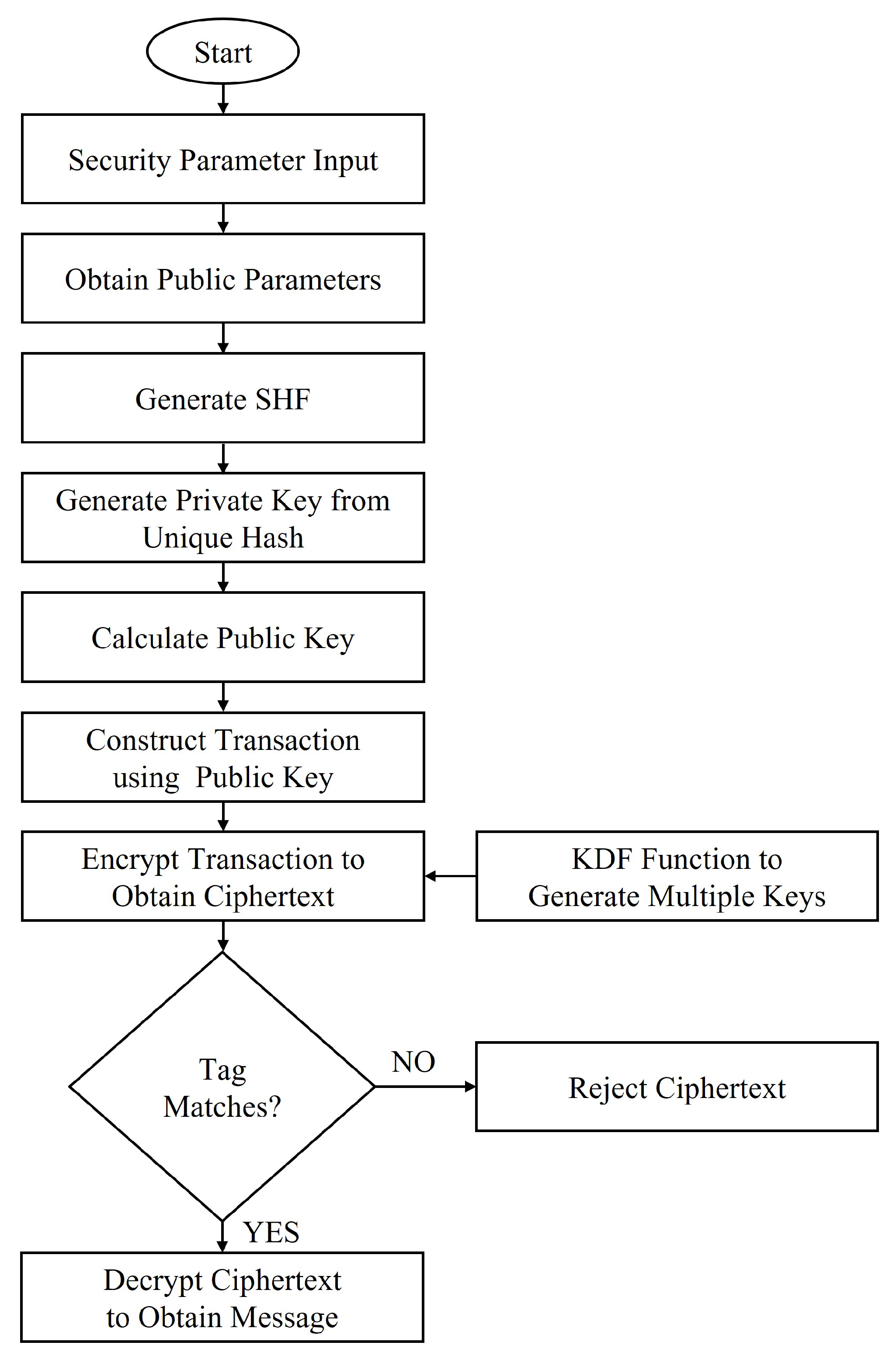
3. Modified ECIES with Secure Hash Function
| Algorithm 1 Proposed ECIES with Secure Hash Utilization. |
| Input: Security parameter and Transactional Request Data Output: Response Data
← else Reject end |
Computation Time for Proposed Scheme
4. Benefits of Modified ECIES with SHF
5. Results and Discussion
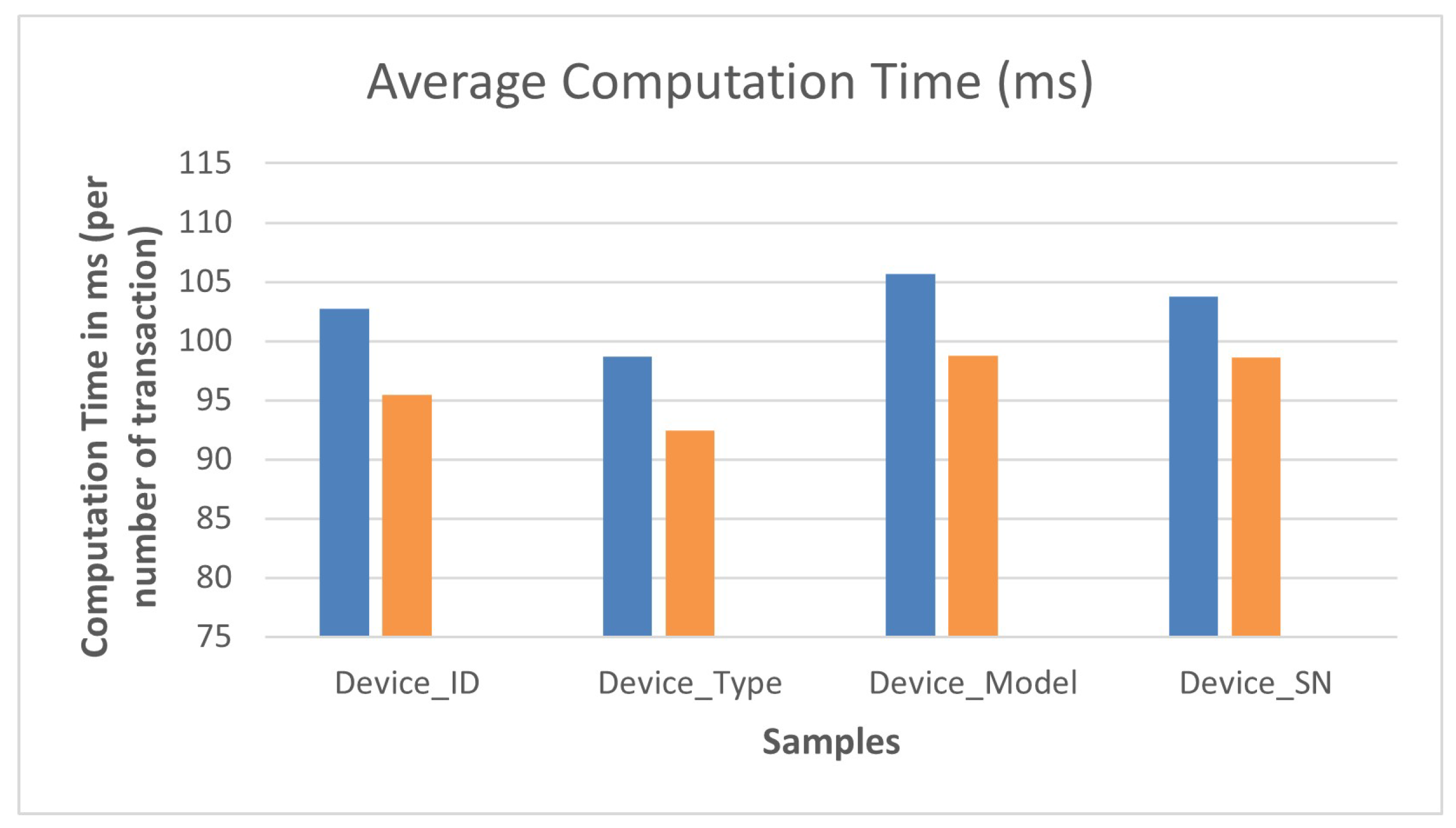
- The average computation time for the proposed scheme of the device_ID samples of the 50-device group dataset is reduced to 95.48 ms, whereas it is 102.733 ms for Lin et al. [14];
- The average computation time for device_Type samples of 150-device group dataset is reduced to 92.447 ms compared to 98.967 ms of Lin et al. [14];
- The average computation time for device_Model samples of 250-device group dataset is 98.745 ms, which is less than the recorded value of 105.68 ms for Lin et al. [14];
- The average computation time for device_SN samples of 500-device group dataset. for the proposed solution is equal to 98.615 ms comparing to 103.766 ms for Lin et al. [14].
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Stoyanova, M.; Nikoloudakis, Y.; Panagiotakis, S.; Pallis, E.; Markakis, E.K. A survey on the internet of things (IoT) forensics: Challenges, approaches, and open issues. IEEE Commun. Surv. Tuts 2020, 22, 1191–1221. [Google Scholar] [CrossRef]
- Sfar, A.R.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the Internet of Things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Rantos, K.; Drosatos, G.; Kritsas, A.; Ilioudis, C.; Papanikolaou, A.; Filippidis, A.P. A blockchain-based platform for consent management of personal data processing in the IoT ecosystem. Secur. Commun. Netw. 2019, 2019, 1431578. [Google Scholar] [CrossRef]
- Fernquist, J.; Fängström, T.; Kaati, L. IoT data profiles: The routines of your life reveals who you are. In Proceedings of the European Intelligence and Security Informatics Conference (EISIC), Athens, Greece, 11–13 September 2017; pp. 61–67. [Google Scholar]
- Lv, P.; Wang, L.; Zhu, H.; Deng, W.; Gu, L. An IoT-oriented privacy-preserving publish/subscribe model over blockchains. IEEE Access 2019, 7, 41309–41314. [Google Scholar] [CrossRef]
- Minoli, D.; Occhiogrosso, B. Blockchain mechanisms for IoT security. Internet Things 2018, 1–2, 1–13. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Alfandi, O.; Khanji, S.; Ahmad, L.; Khattak, A. A survey on boosting IoT security and privacy through blockchain. Clust. Comput. 2020, 24, 37–55. [Google Scholar] [CrossRef]
- Roy, S.; Ashaduzzaman, M.; Hassan, M.; Chowdhury, A.R. Blockchain for IoT security and management: Current prospects, challenges and future directions. In Proceedings of the IEEE International Conference on Networking, Systems and Security (NSysS), Dhaka, Bangladesh, 18–20 December 2018; pp. 1–9. [Google Scholar]
- Bisogni, C.; Iovane, G.; Landi, R.E.; Nappi, M. ECB2: A novel encryption scheme using face biometrics for signing blockchain transactions. J. Inf. Secur. Appl. 2021, 59, 102814. [Google Scholar] [CrossRef]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Zhang, Z.; Qiu, M. Differential privacy-based blockchain for industrial internet-of-things. IEEE Trans. Ind. Inform. 2019, 16, 4156–4165. [Google Scholar] [CrossRef]
- Gnatyuk, S.; Kinzeryavyy, V.; Kyrychenko, K.; Yubuzova, K.; Aleksander, M.; Odarchenko, R. Secure hash function constructing for future communication systems and networks. In Proceedings of the International Conference of Artificial Intelligence, Medical Engineering, Education, Moscow, Russia, 6–8 October 2018; pp. 561–569. [Google Scholar]
- Lin, C.; He, D.; Kumar, N.; Huang, X.; Vijayakumar, P.; Choo, K.-K.R. Homechain: A blockchain-based secure mutual authentication system for smart homes. IEEE Internet Things J. 2019, 7, 818–829. [Google Scholar] [CrossRef]
- Yaga, D.; Mell, P.; Roby, N.; Scarfone, K. Blockchain technology overview. arXiv 2019, arXiv:1906.11078. [Google Scholar]
- Buterin, V. Ethereum White Paper: A Next Generation Smart Contract & Decentralized Application Platform; 1st version. 2014, Volume 53. Available online: https://translatewhitepaper.com/wp-content/uploads/2021/04/EthereumOrijinal-ETH-English.pdf (accessed on 9 January 2022).
- Zou, S.; Xi, J.; Wang, H.; Xu, G. Crowdblps: A blockchain-based location-privacy-preserving mobile crowdsensing system. IEEE Trans. Ind. Inform. 2019, 16, 4206–4218. [Google Scholar] [CrossRef]
- Xu, J.; Xue, K.; Li, S.; Tian, H.; Hong, J.; Hong, P.; Yu, N. Healthchain: A blockchain-based privacy preserving scheme for large-scale health data. IEEE Internet Things J. 2019, 6, 8770–8781. [Google Scholar] [CrossRef]
- Debe, M.; Salah, K.; Rehman, M.H.U.; Svetinovic, D. IoT public fog nodes reputation system: A decentralized solution using Ethereum blockchain. IEEE Access 2019, 7, 178082–178093. [Google Scholar] [CrossRef]
- Xu, X.; Zhang, X.; Gao, H.; Xue, Y.; Qi, L.; Dou, W. BeCome: Blockchain-enabled computation offloading for IoT in mobile edge computing. IEEE Trans. Ind. Inform. 2019, 16, 4187–4195. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Maharjan, S.; Zhang, Y.; Hossain, E. Enabling localized peer-to-peer electricity trading among plug-in hybrid electric vehicles using consortium blockchains. IEEE Trans. Ind. Inform. 2017, 13, 3154–3164. [Google Scholar] [CrossRef]
- Zhang, A.; Lin, X. Towards secure and privacy-preserving data sharing in e-health systems via consortium blockchain. J. Med. Syst. 2018, 42, 1–18. [Google Scholar] [CrossRef]
- Gu, J.; Sun, B.; Du, X.; Wang, J.; Zhuang, Y.; Wang, Z. Consortium blockchain-based malware detection in mobile devices. IEEE Access 2018, 6, 12118–12128. [Google Scholar] [CrossRef]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Workshop on Distributed Cryptocurrencies and Consensus Ledgers; 2016; Volume 310, pp. 1–4. Available online: https://allquantor.at/blockchainbib/pdf/cachin2016architecture.pdf (accessed on 9 January 2022).
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; Caro, A.D.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the 13th EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Biswas, S.; Sharif, K.; Li, F.; Maharjan, S.; Mohanty, S.P.; Wang, Y. PoBT: A lightweight consensus algorithm for scalable IoT business blockchain. IEEE Internet Things J. 2019, 7, 2343–2355. [Google Scholar] [CrossRef]
- Lu, Y.; Huang, X.; Dai, Y.; Maharjan, S.; Zhang, Y. Blockchain and federated learning for privacy-preserved data sharing in industrial IoT. IEEE Trans. Ind. Inform. 2019, 16, 4177–4186. [Google Scholar] [CrossRef]
- He, S.; Tang, Q.; Wu, C.Q.; Shen, X. Decentralizing IoT management systems using blockchain for censorship resistance. IEEE Trans. Ind. Inform. 2019, 16, 715–727. [Google Scholar] [CrossRef]
- Ma, M.; Shi, G.; Li, F. Privacy-oriented blockchain-based distributed key management architecture for hierarchical access control in the IoT scenario. IEEE Access 2019, 7, 34045–34059. [Google Scholar] [CrossRef]
- Islam, A.; Shin, S.Y. BUAV: A blockchain based secure UAV-assisted data acquisition scheme in Internet of Things. J. Commun. Netw. 2019, 21, 491–502. [Google Scholar] [CrossRef]
- Liu, H.; Han, D.; Li, D. Fabric-IoT: A blockchain-based access control system in IoT. IEEE Access 2020, 8, 18207–18218. [Google Scholar] [CrossRef]
- Ding, S.; Cao, J.; Li, C.; Fan, K.; Li, H. A novel attribute-based access control scheme using blockchain for IoT. IEEE Access 2019, 7, 38431–38441. [Google Scholar] [CrossRef]
- Sedlmeir, J.; Buhl, H.U.; Fridgen, G.; Keller, R. The energy consumption of blockchain technology: Beyond myth. Bus. Inf. Syst. Eng. 2020, 62, 599–608. [Google Scholar] [CrossRef]
- Sharma, P.K.; Kumar, N.; Park, J.H. Blockchain technology toward green IoT: Opportunities and challenges. IEEE Netw. 2020, 34, 263–269. [Google Scholar] [CrossRef]
- Sedlmeir, J.; Buhl, H.U.; Fridgen, G.; Keller, R. Recent Developments in Blockchain Technology and their Impact on Energy Consumption. arXiv 2021, arXiv:2102.07886. [Google Scholar]
- Hakeem, S.A.A.; Abd El-Gawad, M.A.; Kim, H. A decentralized lightweight authentication and privacy protocol for vehicular networks. IEEE Access 2019, 7, 119689–119705. [Google Scholar] [CrossRef]
- Krawczyk, H. Cryptographic extraction and key derivation: The HKDF scheme. In Annual Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2010; pp. 631–648. [Google Scholar]
- Sankar, L.S.; Sindhu, M.; Sethumadhavan, M. Survey of consensus protocols on blockchain applications. In Proceedings of the IEEE International Conference on Advanced Computing and Communication Systems, Coimbatore, India, 19–20 March 2017; pp. 1–5. [Google Scholar]
- Brown, D.R. Sec 2: Recommended Elliptic Curve Domain Parameters. Standards for Efficient Cryptography. 2010. Available online: https://ci.nii.ac.jp/naid/10027922258/ (accessed on 9 January 2022).
- Hang, L.; Kim, D.H. Design and implementation of an integrated iot blockchain platform for sensing data integrity. Sensors 2019, 19, 2228. [Google Scholar] [CrossRef] [PubMed] [Green Version]

| Sample | Encrypted Request Transaction Samples from Lin et al. [14] | Encrypted Request Transaction Samples—Proposed Scheme | ||
|---|---|---|---|---|
| Device_ID | Constructed Request Transaction | Encrypted Transaction | Constructed Request Transaction | Encrypted Transaction |
| 5c504f2863 | 01||pk1||5c504f2863||o | nMgxrrzzltep | 01||pk1||5c504f2863||o | #M25*^gh%@sEj_N |
| 7j533g3785 | 01||pk2||7j533g3785||r | VzBsirblemqxj | 01||pk2||7j533g3785||r | &2bgh?+5f*63^”bL+ |
| 2p488d4936 | 01||pk3||2p488d4936||c | blskQohnerJk | 01||pk3||2p488d4936||c | Ox32?@><ghtSE21 |
| S. No. | Device_ID Samples | Constructed Request Transaction | Lin et al. [14] | Proposed Scheme | ||||
|---|---|---|---|---|---|---|---|---|
| Encrypted Transaction | Correlation Coefficient | Computation Time (ms) | Encrypted Transaction | Correlation Coefficient | Computation Time (ms) | |||
| 1 | 5c504f2863 | 01||pk1||5c504f2863||o | nMgxrrzzltep | 0.3451 | 108.45 | #M25*^gh%@sEj_N | 0.3052 | 97.87 |
| 2 | 7j533g3785 | 01||pk2||7j533g3785||r | VzBsirblemqxj | 0.3287 | 102.67 | &2bgh?+5f*63^”bL+ | 0.2881 | 95.35 |
| 3 | 2p488d4936 | 01||pk3||2p488d4936||c | blskQohnerJk | 0.3695 | 110.88 | Ox32?@><ghtSE21 | 0.3197 | 100.01 |
| 4 | 3r622h2678 | 01||pk4||3r622h2678||w | kGniopHcqts | 0.3586 | 105.5 | &&4*^xo78?//@br | 0.3074 | 97.36 |
| 5 | 8x923a0995 | 01||pk5||8x923a0995||r | pxtrJvnerKlsgh | 0.3218 | 100.3 | Xx(+09%#<>P582j# | 0.2821 | 90.8 |
| 6 | 5z307b2305 | 01||pk6||5z307b2305||o | SzhioFnopsltr | 0.3524 | 109.25 | 53>BJIO@+*29_ba | 0.3117 | 99.3 |
| 7 | 1k408m7277 | 01||pk7||1k408m7277||r | zcxvtDlfspqrv | 0.3247 | 98.6 | pM@0873##ghi++ | 0.2851 | 97.2 |
| 8 | 4v978x0355 | 01||pk8||4v978x0355||r | QlnioghTsrvbe | 0.3618 | 96.33 | ST<**3789#(j;st_bt | 0.3125 | 91.78 |
| 9 | 6g388k5669 | 01||pk9||6g388k5669||o | twchjkioAans | 0.3499 | 99.24 | C5!(^78#”gmRb+523 | 0.3071 | 93.68 |
| 10 | 9s028n6082 | 01||pk10||9s028n6082||c | ifniodfXtcrnig | 0.3374 | 96.11 | +93x0”^&pSq*?84((+ | 0.2933 | 91.45 |
| S. No. | Device_Type Samples | Constructed Request Transaction | Lin et al. [14] | Proposed Scheme | ||||
|---|---|---|---|---|---|---|---|---|
| Encrypted Transaction | Correlation Coefficient | Computation Time (ms) | Encrypted Transaction | Correlation Coefficient | Computation Time (ms) | |||
| 1 | Lamp | 01||pk1||lamp||o | hdlOxcjsmkbfaxb | 0.3365 | 100.25 | @2e78(^:xvyio# | 0.2923 | 91.48 |
| 2 | Fan | 01||pk2||fan||c | IDvislzxkrFthjcs | 0.3518 | 96.46 | vM*{14s<”QJixh%j | 0.3091 | 90.01 |
| 3 | Air-conditioner | 01||pk3||ac||r | lpCivzodalfioeLt | 0.3624 | 109.84 | ##hj89!kb(**vm%l | 0.3147 | 101.21 |
| 4 | Television | 01||pk4||tv||r | glaQivtsjiwecbmf | 0.3267 | 104.3 | F4!{9(&&Hjck”b_1 | 0.2865 | 96.45 |
| 5 | Freezer | 01||pk5||freezer||o | iozxJstovhgmcIDf | 0.3378 | 98.8 | Ox5%zkLR++8**d” | 0.2934 | 93.26 |
| 6 | Camera | 01||pk6||camera||c | bchjShBixmveloz | 0.3413 | 97.65 | ++fg^*294(siX3!%K | 0.2984 | 92.68 |
| 7 | Doorbell | 01||pk7||doorbell||c | oxGjzbkdIvsohja | 0.3649 | 95.38 | &&59gX+jq6^^d! | 0.3166 | 89.59 |
| 8 | Door | 01||pk8||door||r | mrXbjiwedjlHaMb | 0.3672 | 94.71 | 3!cAm#]za!_vD8** | 0.3193 | 89.45 |
| 9 | Clock | 01||pk9||clock||r | VbihKzrajioxbfk | 0.3291 | 95.16 | 2!_xjdO(+”8fYios” | 0.2891 | 89.78 |
| 10 | Speaker | 01||pk10||speaker||o | aKleioshBzerjioc | 0.3534 | 97.12 | 56@kWx”67!++^*8) | 0.3112 | 90.56 |
| S. No. | Device_Model Samples | Constructed Request Transaction | Lin et al. [14] | Proposed Scheme | ||||
|---|---|---|---|---|---|---|---|---|
| Encrypted Transaction | Correlation Coefficient | Computation Time (ms) | Encrypted Transaction | Correlation Coefficient | Computation Time (ms) | |||
| 1 | RX350 | 01||pk1||RX350||o | VbxdjklopStpd | 0.3587 | 106.23 | P#5!hbn2e<k” | 0.3138 | 98.45 |
| 2 | HS720A | 01||pk2||HS720A||c | rbpMiosgtkbdji | 0.3393 | 109.04 | ++dfg*7D$%j{ | 0.2954 | 99.34 |
| 3 | ZT8808 | 01||pk3||ZT8808||r | pbfKlacTrxkfdv | 0.3718 | 113.96 | J9_}ndb^&10f | 0.3215 | 103.85 |
| 4 | XY290P | 01||pk4||XY290P||r | Kgankobhmenx | 0.3425 | 105.4 | 28g(7!kvy>?lb | 0.2971 | 98.67 |
| 5 | HDR6E | 01||pk5||HDR6E||o | AchjeoPvmftugy | 0.3274 | 104.55 | “fs9!45@kcql++ | 0.2887 | 96.77 |
| 6 | CBT26Z | 01||pk6||CBT26Z||c | ZxjdriobstJbci | 0.3368 | 110.75 | #46e%Jcmp8!(* | 0.2932 | 101.48 |
| 7 | PB485D | 01||pk7||PB485D||o | oxchksDLnfkwcy | 0.3451 | 100.3 | 0x^{gno**57(% | 0.2995 | 97.26 |
| 8 | AVV56E | 01||pk8||AVV56E||r | GbjiochtgjFcodef | 0.3596 | 104.78 | rDk##99!hsi_4%! | 0.3152 | 97.73 |
| 9 | BM5060 | 01||pk9||BM5060||c | abfdelUbjiotHny | 0.3417 | 99.34 | 3!(gOx<@2dn+*> | 0.2951 | 95.87 |
| 10 | CR2030 | 01||pk10||CR2030||o | rvpmRtzderighj | 0.3624 | 102.45 | +8cY{&269f##k! | 0.3164 | 98.03 |
| S. No. | Device_SN Samples | Constructed Request Transaction | Lin et al. [14] | Proposed Scheme | ||||
|---|---|---|---|---|---|---|---|---|
| Encrypted Transaction | Correlation Coefficient | Computation Time (ms) | Encrypted Transaction | Correlation Coefficient | Computation Time (ms) | |||
| 1 | 72020190805001 | 01||pk1||72020190805001||r | cwkzAldOxvionc | 0.3472 | 103.75 | oxK*3#”4z89!Ws<k# | 0.3072 | 97.33 |
| 2 | 72020190805002 | 01||pk2||72020190805002||c | rcksiKlwgnoxhtVm | 0.3381 | 107.22 | @hs53!jL;(“bKx>++ | 0.2951 | 99.58 |
| 3 | 72020190805003 | 01||pk3||72020190805003||r | MxjkdiyqosdGrdH | 0.3564 | 109.55 | ##gP34{*oX629_jb*D | 0.3115 | 102.67 |
| 4 | 72020190805004 | 01||pk4||72020190805004||o | ldfivrskTaovhxGc | 0.3415 | 105.14 | “lB*{@793!_jf+>VG | 0.2973 | 98.97 |
| 5 | 72020190805005 | 01||pk5||72020190805005||o | bJoxjdlqieczgeorl | 0.3261 | 99.34 | PW(+*51U_”vz#A9<h | 0.2861 | 96.88 |
| 6 | 72020190805006 | 01||pk6||72020190805006||c | xjloFaicehpbhowc | 0.3347 | 109.15 | 9^qxc*{_fk@bi56! | 0.2937 | 101.45 |
| 7 | 72020190805007 | 01||pk7||72020190805007||o | Lpwvnjxzaioerm | 0.3641 | 99.62 | ++7Ox37”#bsT^y>* | 0.3142 | 97.13 |
| 8 | 72020190805008 | 01||pk8||72020190805008||r | mhykdgyerioskzt | 0.3572 | 104.01 | *fV%g_h!{“6do>&r | 0.3116 | 98.35 |
| 9 | 72020190805009 | 01||pk9||72020190805009||c | aQiocdjkguzpljXo | 0.3487 | 98.15 | Ix{&85+^dy@<>g# | 0.3081 | 97.01 |
| 10 | 72020190805010 | 01||pk10||72020190805010||r | PfsklchioxDgerzbj | 0.3293 | 101.73 | &jc*;31k4!+M_”*5%# | 0.2841 | 96.78 |
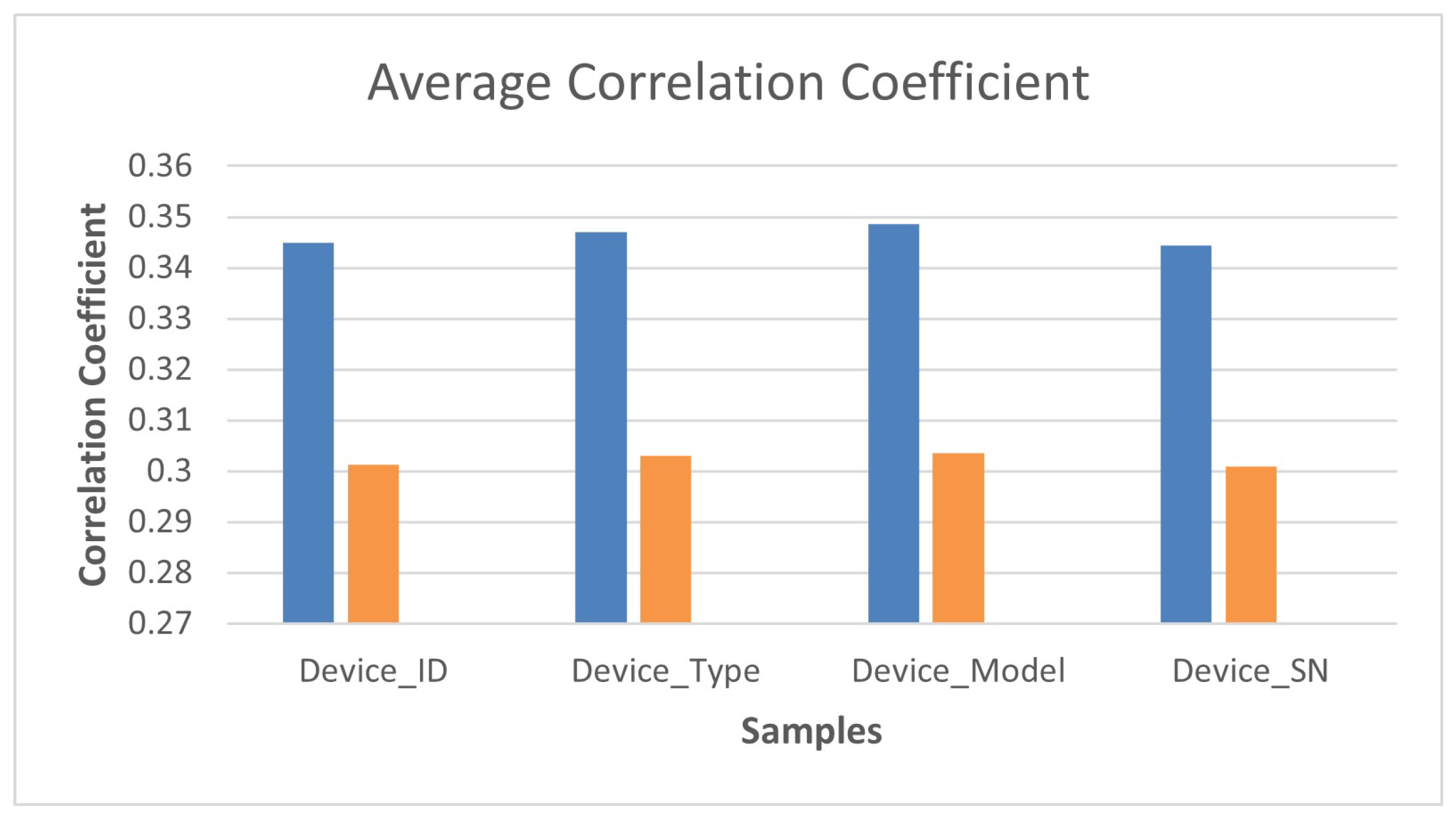
| Dataset | Samples | No. of Tests Taken | Lin et al. [14] | Proposed Scheme | ||
|---|---|---|---|---|---|---|
| Average Correlation Coefficient | Average Computation Time (ms) | Average Correlation Coeffcient | Average Computation Time (ms) | |||
| 50-Device Group Set | Device_ID | 10 | 0.34499 | 102.733 | 0.30122 | 95.48 |
| 150-Device Group Set | Device_Type | 10 | 0.34711 | 98.967 | 0.30306 | 92.447 |
| 250-Device Group Set | Device_Model | 10 | 0.34853 | 105.68 | 0.30359 | 98.745 |
| 500-Device Group Set | Device_SN | 10 | 0.34433 | 103.766 | 0.30089 | 98.615 |
| Approach | Proposed Scheme Modified ECIES with a SHF | Approach of Lin et al. [14] Mutual Authentication with ECIES |
|---|---|---|
| Encryption/Decryption Strength | The strength of the encryption/decryption is measured in terms of the correlation coefficient. The improvement in the correlation coefficient is from 0.34499 to 0.30122 | Provides an average correlation coefficient of 0.34499. |
| Computation time | Computation time is measured in terms of execution time. The computation time decreases from 102.733 ms to 95.48 ms, reducing the encryption/decryption time from 39.925 ms and 41.513 ms to 34.444 ms and 35.859 ms. | Provide an average computation time of 102.733 ms with average encryption decryption time of 39.925 ms and 41.513 ms. |
| Contribution 1 | The generation of an SHF increases the security strength of the key by adding new features for calculating private and public keys from the safer elliptic curve points. With the generation of an SHF, the security strength of the transmitted message is improved, which enhances the user privacy in IoT. | Does not use hash function generation for computing private and public keys for encrypting the transmitted message in IoT, which results in the violation of user privacy. |
| Contribution 2 | The KDF introduces key stretching capability and decreases the number of iterations processes while deriving keys for authentication. This reduces the time for encryption and decryption. | The computation time is affected by the number of users showing the system unreliability. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khanal, Y.P.; Alsadoon, A.; Shahzad, K.; Al-Khalil, A.B.; Prasad, P.W.C.; Rehman, S.U.; Islam, R. Utilizing Blockchain for IoT Privacy through Enhanced ECIES with Secure Hash Function. Future Internet 2022, 14, 77. https://doi.org/10.3390/fi14030077
Khanal YP, Alsadoon A, Shahzad K, Al-Khalil AB, Prasad PWC, Rehman SU, Islam R. Utilizing Blockchain for IoT Privacy through Enhanced ECIES with Secure Hash Function. Future Internet. 2022; 14(3):77. https://doi.org/10.3390/fi14030077
Chicago/Turabian StyleKhanal, Yurika Pant, Abeer Alsadoon, Khurram Shahzad, Ahmad B. Al-Khalil, Penatiyana W. C. Prasad, Sabih Ur Rehman, and Rafiqul Islam. 2022. "Utilizing Blockchain for IoT Privacy through Enhanced ECIES with Secure Hash Function" Future Internet 14, no. 3: 77. https://doi.org/10.3390/fi14030077
APA StyleKhanal, Y. P., Alsadoon, A., Shahzad, K., Al-Khalil, A. B., Prasad, P. W. C., Rehman, S. U., & Islam, R. (2022). Utilizing Blockchain for IoT Privacy through Enhanced ECIES with Secure Hash Function. Future Internet, 14(3), 77. https://doi.org/10.3390/fi14030077









