Abstract
In this paper, we study the flow of signals through linear paths with the nonlinear condition that a node emits a signal when it receives external stimuli or when two incoming signals from other nodes arrive coincidentally with a combined amplitude above a fixed threshold. Sets of such nodes form a polychrony group and can sometimes lead to cascades. In the context of this work, cascades are polychrony groups in which the number of nodes activated as a consequence of other nodes is greater than the number of externally activated nodes. The difference between these two numbers is the so-called profit. Given the initial conditions, we predict the conditions for a vertex to activate at a prescribed time and provide an algorithm to efficiently reconstruct a cascade. We develop a dictionary between polychrony groups and graph theory. We call the graph corresponding to a cascade a chinampa. This link leads to a topological classification of chinampas. We enumerate the chinampas of profits zero and one and the description of a family of chinampas isomorphic to a family of partially ordered sets, which implies that the enumeration problem of this family is equivalent to computing the Stanley-order polynomials of those partially ordered sets.
1. Introduction
Networks directly or indirectly impact many aspects of our lives via numerous modalities, including the internet, telecommunications, social media, the brain, and our bodies. These networks can be modeled through signal flow graphs, or directed graphs in which nodes represent system variables and the edges represent functional connections between pairs of nodes. In this paper, we investigate particular examples of nonlinear signal flow graphs, see Section 2 in which some external stimuli are applied to the vertices of the graph, triggering a chain reaction on these and other vertices.
A cascade refers to those chain reactions in which the number of external stimuli is smaller than the number of reactions generated within the chain. The time duration of these stimuli plays an important role, rendering the study of cascades nonlinear.
A vertex subjected to an external stimulus or triggered indirectly as a consequence of reactions to the stimuli of others is considered activated. In this context, we seek answers to the following questions:
- Is a given vertex activated at a particular time?
- Can we reconstruct all the vertices that will change their states to activated?
Neuronal networks in which the flow of signals form time-locked patterns define the polychrony groups [1]. The word polychrony is derived from the Greek words “poly” (i.e., many) and “chronous” (i.e., time).
Most of the literature focuses on linear signal flow graphs, where the edges represent matrix operations. However, studying polychrony groups requires a language to treat the nonlinear case. As part of our methodology, we adopt the language of graph theory to model signal flow networks. A polychronous group without redundant information is encoded in a graph called a chinampa. The study of chinampas is described in Section 3, Section 4 and Section 5. Section 3 describes the signal flow networks from the point of view of graph theory. In Section 4, we provide a topological characterization of chinampas (see Theorem 1). Section 5 explains the relationship of our work with cellular automata.
We introduce the concept of profit, a measure of how many vertices activate in response to external stimuli. In Section 6, we give formulae for the number of pyramids in a chinampa of profits zero and one. In Section 6.3, we provide the code to answer both of our target questions. The algorithm we implemented is available at https://github.com/mendozacortesgroup/chinampas/ (accessed on 3 March 2023). Note that the algorithm works with an input network of the form and when the input network is a tree. Our code is optimal compared with the state of the art, as explained in the conclusions.
The study of chinampas of a profit greater than one is more difficult. In Section 7, we describe a family of chinampas whose enumeration problem is equivalent to computing the order polynomial of some posets. The order polynomial counts the labeling maps from a poset to chains , and the study of order polynomials is an active area of research in enumerative combinatorics. Our work sets the basis for the study of polychrony groups in combinatorics.
2. Nonlinear Signal Flow Graphs
In this article, we shall study a kind of nonlinear signal flow graph called a directed graph. We think that a signal propagates throughout an edge by following its orientation. When several signals reach a vertex simultaneously, a built-in condition called the threshold determines whether it will react by firing signals. The concept of the signal flow graphs was developed by Samuel Mason and Claude Shannon [2,3]. If the condition is linear in the intensity of the input signals, then the graphs are called linear signal flow graphs.
We study the following nonlinear condition of a signal flow graph:
- Every signal has an intensity of one.
- Every vertex has a threshold intensity of two.
- If a vertex coincidentally receives signals of an intensity higher or equal to the threshold, then the vertex fires a signal through each of its outgoing edges.
Nonlinear signal flow graphs are used to study circulatory regulation [4], to design automatization of nonlinear data converters [5], to compare system-level and spice-level static nonlinear circuits [6], to build models for DC-DC buck-boost converters [7], and to analyze the problem of inverting a system consisting of nonlinear and time-varying components [8]. The nonlinear condition of our signal flow graphs is an abstraction of neural spikes. Neural spikes are used in cognitive computing to develop hardware that emulates the human nervous system [9,10,11,12,13], to implement robust chaotic communication [14], and to power efficient channel coding [15]. The link between neural spikes and pulse position modulation is explained in [16].
In particular, we are interested in polychrony groups defined as a group of primary neurons (vertices) that fire at specific times, leading to secondary neurons firing. As a result, a cascade occurs when the number of primary neurons is below the number of secondary neurons (see [1] for more details).
We study the general phenomena of polychronization of nonlinear signal flow graphs of the form
Our initial objective is to characterize the polychrony groups that lead to cascades. A second goal is to count the families of the cascades. We also explain the algebraic structure of cascades using cellular automata theory. Our final goal is to develop an algorithm that can answer certain types of queries without the need to compute all possible interactions. An example of such a query might be establishing which neuron (vertex) will be activated at some future time.
3. Base and Activation Diagrams
In this section, we introduce the notion of a covering graph to represent the flow of signals in a network. As a part of our methodology, we translate the problem of characterizing our nonlinear signal flow graphs into the problem of color-covering graphs.
3.1. Base Diagram
Consider the set of nonnegative integers . For a directed graph A, we denote the set of vertices and edges of A as and , respectively. We define a base diagram of A as the pair where B is a directed graph with vertices and, given any edge of labeled by , we define an edge in as between the vertices and of . The coordinate i in indicates the row position of the vertex (see Figure 1).
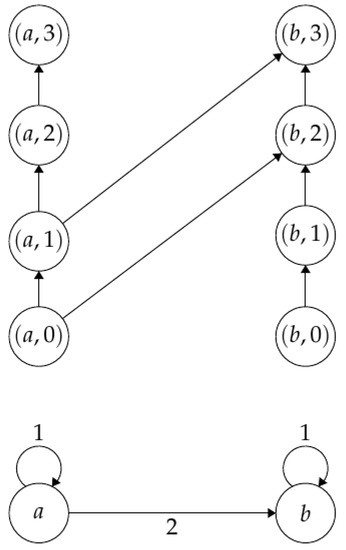
Figure 1.
In the bottom part of the figure, a simple graph A is shown. In the top part, the corresponding base diagram B is shown.
The function is the projection defined by , and the image of every edge under p defines the edge of with a label t.
We are interested in particular types of directed graphs. A singleton u is a graph with one vertex and one self-edge with a label 1. A path of length l, denoted by , is a directed graph with vertices , where each vertex has a self-edge, while each vertex has one outgoing edge to the vertex . Any edge has a label 1. A cycle of length l, denoted by , is a path with vertices in the set , but the vertex l has one outgoing edge to vertex 1 with a label 1. In other words, a cycle is a closed path. The graphs u, , and have their own base diagrams, which we call , , and , respectively. Figure 2 shows examples of a path, a cycle, and their respective base diagrams.
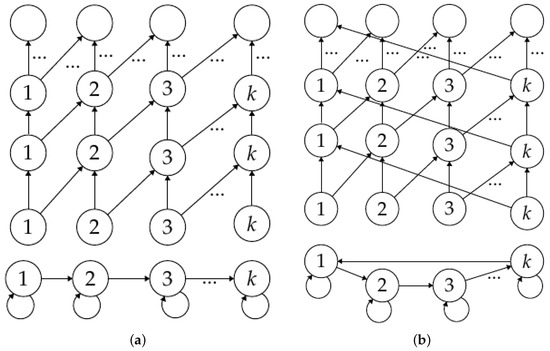
Figure 2.
Directed labeled graphs and their correponding base diagrams. (a) A path(l) and its corresponding base diagram tellis(l). (b) A cyc(l) and its corresponding base diagram cylinder(l).
3.2. Activation Diagram
Given a base diagram, we selected a subset of vertices and called them the primary vertices. The activation diagram is a base diagram B and a subset S of the primary vertices of . A secondary vertex with the coordinates is a vertex in the base diagram in which each one of and is either a primary vertex or a secondary vertex. We associated the activation graph (i.e., the underlying colored graph in which the primary and secondary vertices are black and the remaining vertices are white) to each activation diagram. To simplify the interpretation of theactivation diagrams, we only drew vertices which were either primary or secondary and avoided the others in the base diagram (see Figure 3).
Figure 3.
(left) An example of an activation diagram. The activation diagram turns into an activation graph. (right) A new black vertex appears in a row of the activation graph due to the two corresponding black vertices in the previous row in the activation diagram.
Example 1.
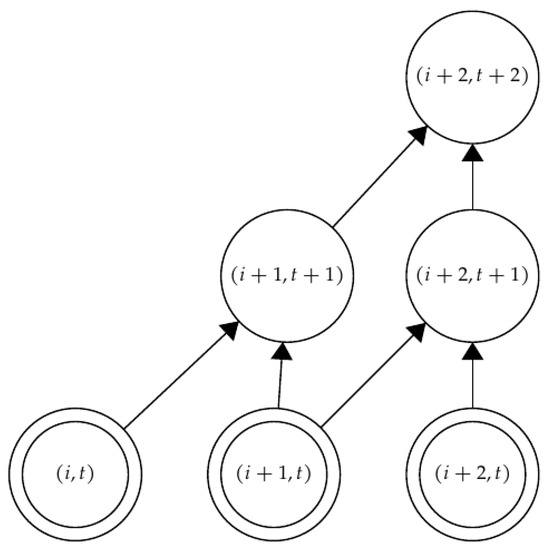
Consider and its corresponding base diagram , as described before. Fix a vertex , and consider with consecutive vertices with the same time. The set S is determined by the initial vertex of the path P, its length l, and a fixed time . We employ apyramid in the activation diagram and denote it as . In Figure 4, the activation diagram of a path with a length of three is illustrated.

Figure 4.
A ring (double circle) indicates the primary vertices. There are three secondary vertices, forming a pyramid.
Remark 1.
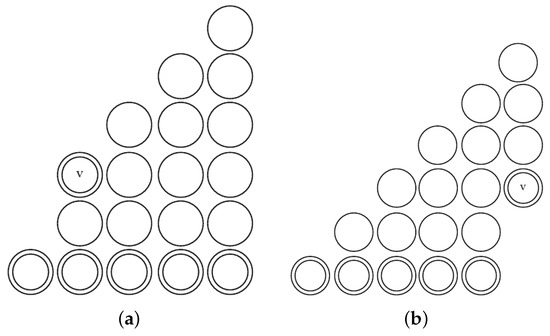
Suppose we have an activation diagram in which there is with an extra primary vertex where . The vertex affects by activating the vertices in the diagonal . On the other hand, if the extra primary vertex is localized in , where , then the vertical line is activated (see Figure 5).

Figure 5.
Effect of adding a primary vertex to a pyramid. (a) If we add an activated vertex v to the left side of a pyramid, then the vertices in the same diagonal with times greater than the time of v are activated until reaching the top of the pyramid. (b) If we add an activated vertex v to the right side of the pyramid, then the vertices in the same column with a time greater than the time of v are activated until reaching the top of the pyramid.
With a path of secondary vertices from to , we define a sequence
with the first point = and final point = such that there is an edge between two consecutive vertices. Here, the edges are considered while ignoring the direction. The edges go from to and from to .
We restricted our study to activation diagrams where every primary vertex contributed to at least one secondary vertex. A redundant activation diagram occurs when a primary vertex is also a secondary vertex (see Figure 6).
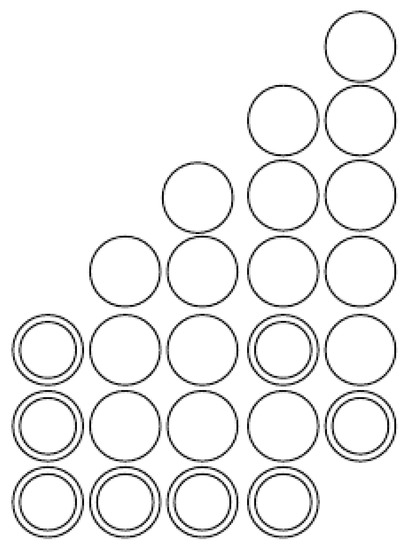
Figure 6.
In this activation graph, there is a primary vertex which is also a secondary vertex.
An activation diagram C is connected if the secondary vertices of the corresponding activation graph form a connected, undirected graph. As an example, Figure 3 and Figure 4 are connected activation diagrams. Figure 7 is not a connected activation diagram.
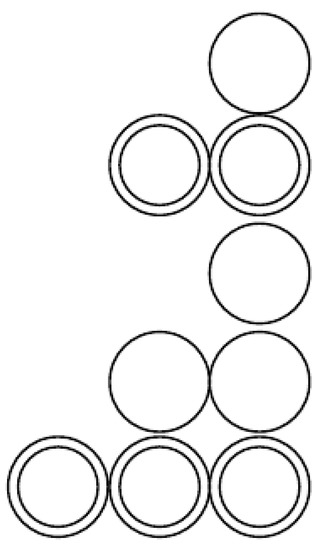
Figure 7.
An example of a non-connected activation diagram. There is no edge between the pyramid below and the pyramid above.
4. Chinampas
Given an activation diagram, the profit is equal to the number of secondary vertices minus the number of primary vertices. The profit measures the maximum number of extra vertices which are activated as a consequence of the topology of the graph. A connected, non-redundant activation diagram is a chinampa if its profit is greater than or equal to zero. An example of a chinampa is illustrated in Figure 8. The simplest chinampa, in the sense that it involves the least number of vertices, is , as shown in Figure 4. The name is due to the similarity of the figures with an ancestral Mexican agricultural technique that uses soil to grow crops on a lake. We imagine that chinampas have crops above the soil, and underneath, there are roots.
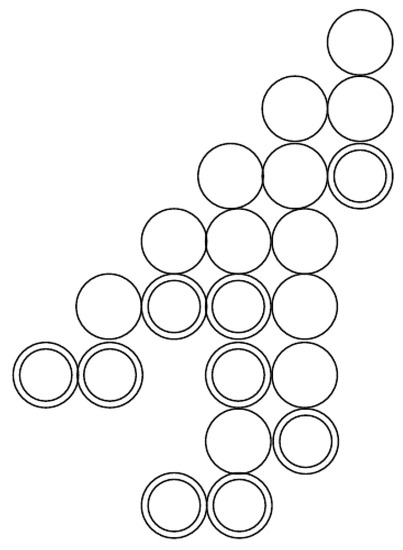
Figure 8.
Example of a chinampa.
The profit defines a function from the set of chinampas to nonnegative integers. We denote with the profit of a chinampa C.
The Topological Description of a Chinampa
We describe chinampas over a . For this goal, we will give the decomposition of a chinampa into pyramids. Remember that we defined as an activation diagram where the primary vertices S are consecutive and have the same time. We extend the definition of a pyramid to the activation diagram , in which S contains the secondary vertices. Thus, in chinampa C of Figure 9, we have two pyramids and , where the vertex is a secondary vertex.
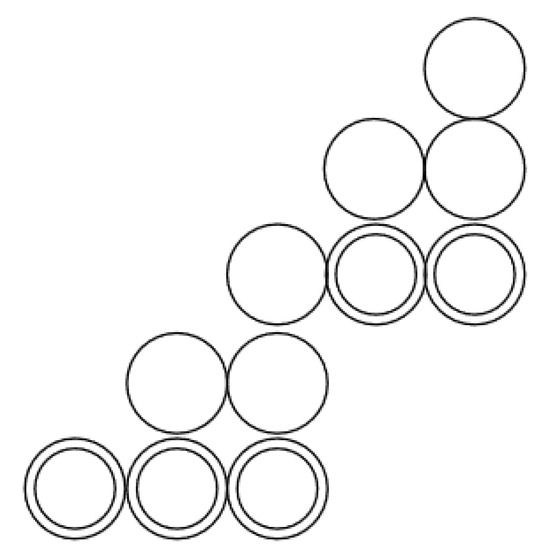
Figure 9.
and with as a secondary vertex, forming a chinampa.
Note that a pyramid has only one secondary vertex at the top, which we call the pyramidion. If and are pyramids in a chinampa, then we say that pyramid is stacking into pyramid if the pyramidion of is a secondary vertex of other than the pyramidion of , and is not contained in .
Remark 1 shows that the activation diagram of a is of the form , together with the primary vertices at the right or left of . We will see that an activation diagram is a sequence of stacked pyramids:
Remark 2.
Consider two pyramids and . The pair of primary vertices and activates , which is not part of any of the two pyramids. Based on Remark 1, the entire diagonal to which the vertex belongs is activated, as well as the vertical line with , and so on. Therefore, we end up with . This argument works for two pyramids: and , separated by activated vertices . Thus, in such cases, instead of considering several small adjacent pyramids, we always consider only the biggest pyramid that includes the small adjacent pyramids.
Proposition 1.
There exists only one pyramidion with the maximum time in a chinampa. We call this a spike.
Proof.
Suppose and with are pyramidia with the maximum time. Through connectedness, there is a path from to with only secondary vertices. Each vertex on the path has a time lower than or equal to t. Starting from the vertices with lower times, we use Remark 2 until we reach those vertices with a time t. At each step, we conclude that all vertices above and between those in the path are secondary vertices. Then, those vertices between and are activated, meaning that and are not pyramidia, which is a contradiction. □
Remark 3.
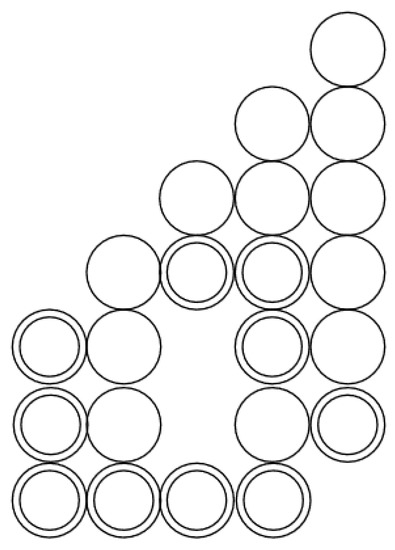
If and are activated vertices connected by a path of activated vertices with a time lower than or equal to t, then the argument in the proof of Proposition 1 shows that both of them are in a pyramid whose pyramidion has a time greater than t. As a consequence, if two pyramids and can be stacked under a given P, then pyramid cannot be adjacent to , since under Remark 2, we would instead stack the biggest pyramid, which includes both and . The activation diagram of Figure 10 is not a chinampa. Assume t is the minimum time of the primary vertices. Then, and are adjacent, and thus they are in , which implies that the middle vertex becomes a secondary vertex, which is contrary to the non-redundancy requirement.

Figure 10.
Here is an example of an activation diagram which is not a chinampa. The copies of at the bottom are next to each other, and as a consequence, all vertices in the hole are internally activated.
Remark 4.
Another consequence of Remark 1 is that a chinampa has no activated vertex located to the right of the spike. If the spike is , then all activated vertices are of the form with and .
Now, we shall give an order to the pyramids in a chinampa:
Proposition 2.
In a chinampa, there exists a unique with of the maximum time. We call it the top pyramid.
Proof.
Start with the spike . If this is the pyramidion of with , then we are done. If not, then we have a sequence of stacked onto each other. However, the chinampa has a profit greater than or equal to zero, so eventually, we will come across with . Let the top pyramid be the first instance found with this strategy. There is no other pyramid with , since through connectedness and Remark 2, we would conclude that there is a bigger pyramid containing both the top pyramid and , which contradicts the assumption that the top pyramid is the first instance found. □
Theorem 1
(Topological classification of chinampas). Any chinampa can be described as a sequence of pyramids stacked onto each other.
Proof.
We showed that in a chinampa, there is a unique top pyramid (Proposition 2). This top pyramid is stacked onto a sequence of unless the spike belongs to the top pyramid (Proposition 1). Any other () must have (Remark 4). Pyramids are connected, which is only possible if they are stacked onto each other. □
The average chinampa is described in Figure 11.
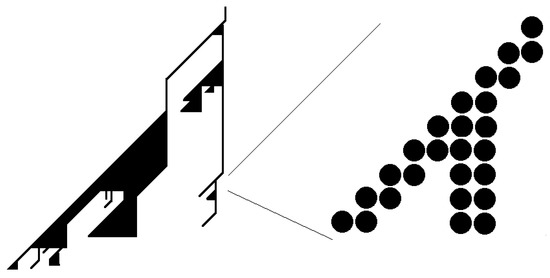
Figure 11.
Standard example of a chinampa. (left) Zoomed-out image of a chinampa, where the chinampa can be represented by stacking pyramids. (right) Zoomed-in image of a chinampa, where we see the details of the activation diagram. The lines in the left figure are groups of activated vertices.
We define an abstract pyramid as an activated diagram without an initial vertex or an initial time. In , we always consider that the vertices at the bottom are primary ones. Then, turns into if placed in a base diagram (i.e., if we choose an initial vertex i and a time t).
Consider a chinampa C. Let be the set of , with one for each stacking of in a chinampa C. We recover the chinampa by stacking abstract pyramids from the set . We associate the corresponding pyramidion with any . If the pyramidion of P belongs to the pyramid Q, then we call Q the parent of the pyramid P. Note that after stacking, some primary vertices of the parent become secondary vertices.
We describe an algorithm to create the list . We can use the breadth-first search (BFS) or depth-first search (DFS) algorithm [17]. Algorithm 1 is the pseudocode of an implementation of BFS. In this algorithm, the pyramidion and the parent of P are attached to P as and , respectively.
| Algorithm 1: Factorization via BFS |
 |
Remark 5.
The vertices in a pyramid are ordered. For example, the dictionary order starts at the top and proceeds from left to right. Provided a fixed order for abstract pyramids, as described above, our algorithm is deterministic. Thus, we consider the returned list as a factorization of the chinampa in terms of pyramids.
5. Cascades and Cellular Atomata
We adopted the convention from [18], stating that “the network, node, link combination often refers to real systems … In contrast, we use the terms graph, vertex, edge when we discuss the mathematical representation of these networks”.
5.1. Base Diagrams as a Model of a Network
Our networks are such that there exist nodes p firing due to external stimuli and nodes s firing when the sum of the input signals from other nodes exceed their thresholds. Our goal is the study of cascades, which are networks whose number of nodes s is greater or equal to the number of nodes p. We translated the networks to a base diagram , where a node p firing due to external stimuli at time t in the network corresponded to a primary vertex of , and a node s firing as a consequence of the signals of other nodes corresponded to a secondary vertex in . In this way, a cascade in a network corresponded to an activation diagram. The activation diagram in Figure 3 is associated to a cascade.
Table 1 resumes the relation between the definitions of networks and the corresponding definitions of the base diagrams. The terms on the left relate to network theory, and the terms on the right are the equivalent concepts in the base diagrams.

Table 1.
Equivalent definitions between networks and base diagrams.
5.2. Cellular Automata
As we will see in this subsection, a cascade can be interpreted as a cellular automaton. We considered cellular automata [19] in which three consecutive colored (black or white) cells determined the color of the middle cell in the next iteration. In particular, we were interested in rule 192. This rule dictates that cell C will be black if C and the one to the left were black in the previous iteration (see Figure 12).
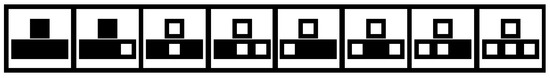
Figure 12.
Rule 192. Only the first and second stages lead to a black cell, similar to our hypothesis on the signal flow graphs.
In Figure 13, the vertical axis is the time, and we thought of the yellow blocks as the stimuli to keep alive the cells of the game of life [20]. The lowest row represents a cell which survived for three units of time under rule 192. The next row shows 3 automata which survived 4 units of time, 6 which survived 5 units of time, and 12 which survived 6 units of time.

Figure 13.
Cellular automata with less than six external stimuli.
Thus, a cascade on networks can be seen as the evolution of cellular automata, where we fixed the external stimuli and applied rule 192 to evolve the cells. More specifically, we employed rule 192 [19] but allowed the initial conditions to occur at different times. Accordingly, we could use the language of graph theory to describe the behavior of the cellular automata (cascade).
6. Combinatorial Description of Chinampas
Since a base diagram is a set of chinampas, we studied the properties of chinampas. As a part of our contributions, we present some combinatorial properties of a chinampa. For example, we will give a formula for the number of chinampas inside a pyramid. This formula is given in terms of a generating function. Another result is the prediction of when a vertex appears as a secondary vertex in a chinampa. This can be accomplished by using algorithms to find the pyramids in a chinampa.
6.1. Profit Properties
In the current context, since there is no confusion between a pyramid and an abstract pyramid, we sometimes refer to both as pyramids. From now on, we will construct chinampas via the stacking process. Remember that we do not allow the stacking of two pyramids when one ends inside the other, neither one is adjacent to the other, or some primary vertices in the abstract pyramid turn into secondary vertices once we stack a pyramid.
Let and be two abstract pyramids, and let C be the chinampa obtained by stacking into . We define the intersection of two abstract pyramids and as the abstract pyramid with activated vertices at the intersection of the activated vertices of and . Given the definition of an abstract pyramid, if a vertex is primary in one vertex and secondary in the other, then the vertex is primary in .
Remember that we defined the profit as the difference between the secondary vertices and the number of primary vertices. If the intersection of two pyramids is only one point, hen we assume a profit of . We have the following result for vertical stacking:
Lemma 1.
Let C be a chinampa obtained by vertical stacking of two abstract pyramids and . The profit function satisfies
Proof.
Suppose pyramid is above . Then, the abstract pyramid is once again a pyramid. Let , , and be the number of primary vertices of , , and , respectively. Then, the primary vertices of turn into secondary vertices in C, and therefore the number of primary vertices of C is given by
What is more, let , , and be the number of secondary vertices of , , and , respectively. Then, the number of secondary vertices of C is
Therefore, the results follow. □
Note that the arguments in the proof of Lemma 1 are standard and can be used to prove the following proposition:
Proposition 3.
Let C be a chinampa with a set of abstract pyramids . The profit function satisfies the inclusion-exclusion principle
There are two approaches to stacking one into another . According to Equation (1), stacking into a chinampa does not change the profit. We describe how the action of stacking affects the profit:
Lemma 2.
Let C be a chinampa with profit n. Stacking a with into C creates a chinampa with profit .
Proof.
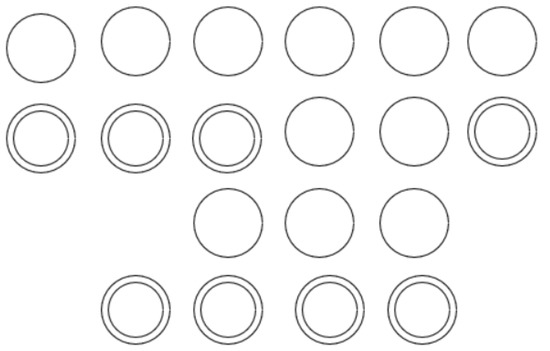
Assume that we stack into C. Locally, is stacked in a pyramid P of C so that the primary vertices of P with time where are replaced by secondary vertices (see Figure 14). The number of primary vertices of C increases by , although the number of secondary vertices increases by because stacking only affects the vertices of P. The result follows since implies . □

Figure 14.
Here, with is stacked into a chinampa C. In this example, the two primary vertices of C at become secondary.
Remark 6.
Stacking one pyramid with a length of three and several pyramids with a length of two returns a chinampa with a profit of zero. Conversely, under Lemma 2, if we have a chinampa with a profit of zero, then it must be the result of stacking one pyramid with a length of three and some pyramids with a length of two. Similarly, a chinampa with a profit of one has two copies of pyramids with a length of three and several copies of pyramids with a length of two. For a profit of two, we can have either one and several instances stacked on or below it or three instances and several instances.
In general, a chinampa with a profit k is made by stacking several so that they satisfy Equation (1). We know that , which is less than or equal to k under Lemma 2. This gives a bound on the largest pyramid contained in a chinampa in terms of the profit of the chinampa
for all
6.2. Combinatorial Description of Chinampas with Profits of Zero and One
We aim to find the number of chinampas inside . A general chinampa can always be considered as part of (see Remark 4). Therefore, consider in . We define
to be the number of all chinampas contained in P and obtained by stacking copies of , where .
Example 2.
It is clear that , for and
To simplify the notation, from now on, we will omit the terms corresponding to , although they remain a part of the calculations. Thus, becomes .
In Figure 15, we show three of the elements identified by . The three chinampas with a profit of zero have at the top.
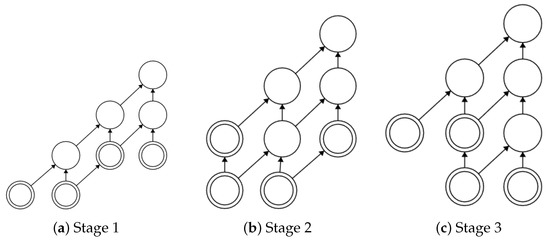
Figure 15.
Three chinampas with a profit of zero having at the top. Note that the stages were obtained from , replacing one of the three primary vertices v at a time of zero by two primary vertices at the time so that v becomes a secondary vertex.
To count the number of zero-profit chinampas within an instance of , we consider the formal series
Following [21], we use the calculus of formal exponential generating functions to determine all coefficients. Note that for .
We will use the fact that
has the solution
Proposition 4.
In , for the nonnegative integer n, there are possible zero-profit chinampas. Furthermore, these numbers are given by the coefficients of the generating function
Proof.
Recall that according to Remark 6, a zero-profit chinampa has only one stacked . First, we can explicitly count the number of chinampas in when is at the top of . For each integer , there are such possible chinampas. This is because for each element in Figure 15, we create new elements by stacking a sequence of below the element. Therefore, the result follows from Equation (3). The remaining chinampas in are those for which is not at the top, namely . This follows because is within one of the two subpyramids : one given by ignoring the main diagonal of or the other by ignoring the right vertical column of .
Therefore, for , we have
Now, we define
so
Using Equation (4) and the condition , we obtain
□
Proposition 5.
Chinampas of a certain unit of profit have the generating function
Proof.
A chinampa unit of profit can only be formed by two copies of and chains of , as shown in Remark 6. We define the formal series
and consider the following cases:
- None of the instances of are at the top. We then have subpyramids as in the previous proposition, so we count
- One instance is at the top. Then, the remaining instances can be placed in ways on the two subpyramids. However, the two subcases have terms in common, as shown in Figure 16. Thus, the correct number of combinations is .
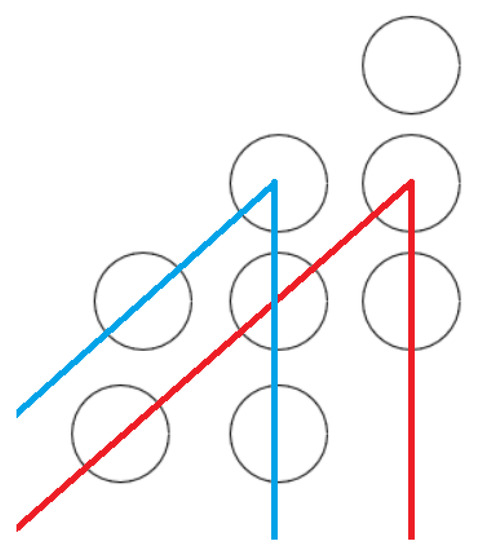 Figure 16. Stacking any pyramid onto pyramid(3) in the vertex, where the red and blue lines collide and continue the process of stacking pyramids iteratively. This process describes a family of pyramids counted twice: once under the blue region and once under the red region.
Figure 16. Stacking any pyramid onto pyramid(3) in the vertex, where the red and blue lines collide and continue the process of stacking pyramids iteratively. This process describes a family of pyramids counted twice: once under the blue region and once under the red region.
We conclude that for each nonnegative integer n, we have
Then, using the generating series found in Lemma 4, we compute
By solving Equation (4), we obtain
We compute to conclude
□
6.3. Algorithms for Activated Vertices
We will describe an algorithm to construct stacked pyramids of chinampas and to predict whether a vertex is activated at a given time within a chinampa.
Building Chinampas
Following ideas from dynamical programming, we compute the pyramids that make up a chinampa. As a reminder, we assume that each comes with a natural time ordering on its vertices.
We first construct a chinampa with a known set of primary vertices sorted by their time of occurrence, followed by a secondary sorting of the vertex labels. For every sequence of n consecutive primary vertices with the same time t, we assign a new structure named an interval. An interval only remembers the coordinates of the first and last primary vertices, while t is the time of the interval’s occurrence. We assign the order inherited from the set of primary vertices to the set of intervals. The left vertex of the interval establishes the order.
Next, we associate with the interval with the lowest parameter t that has l consecutive vertices. An iterative process to build the chinampa is as follows. Given the next interval, defined by consecutive vertices with , we check whether the first or last term is next to a pyramid built previously. If so, then we extend the interval to include the secondary vertices of the pyramid, whose time equals . Once we grow the interval from to , we assign to the interval the (see Algorithm 2). The auxiliary Algorithm 3 removes duplicates.
Let n be the number of primary vertices, and let . To compute the time complexity of Algorithm 2, we analyzed the best-case and worst-case scenarios. The best-case scenario is where all vertices are part of the base of a pyramid. In the best-case scenario, the computational complexity is . The worst-case scenario is where we have copies of concatenated such that two consecutive pyramids with different times share the maximum area possible. In the worst-case scenario, the algorithm complexity is due to the double loop.
To determine whether a vertex is activated, we must determine whether it is contained within a pyramid. Therefore, for each pyramid, one must verify whether the vertex satisfies the constraints necessary to keep them within the region defined by the corners of the pyramid. See Algorithm 4 for the time complexity in the best case and in the worst case (because it calls back to Algorithm 2). The source code of this algorithm can be accessed at https://github.com/mendozacortesgroup/chinampas/ (accessed on 3 March 2023).
| Algorithm 2: Build chinampas |
 |
| Algorithm 3: Remove duplicates |
 |
| Algorithm 4: Will_vertex_be_activated |
 |
7. Triangular Sequences
We study the chinampas obtained by stacking several instances below for . For ease of exposition, we define roots as the sequences of stacked on top of each other. Note that with can have multiple roots. For simplicity, we let have and , and all roots had the same number R of .
Example 3.
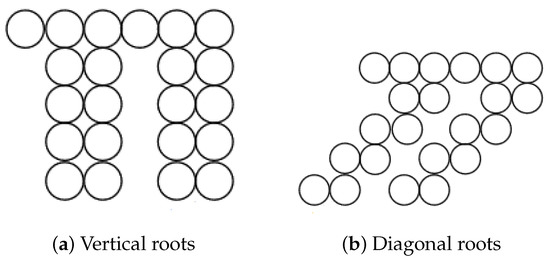
Consider the two extreme cases for , whose roots are depicted in Figure 17. In Figure 17a, the roots are formed by stacking vertically, while in Figure 17b, the instances are stacked along diagonals.

Figure 17.
Roots in . We show all activated vertices except those above the primary vertices of .
Given K and R, we define a -triangular sequence as a sequence with two indexes , where the coefficients are integers and they satisfy the constraints
Remark 7.
The particular relation prevents redundancy of the roots.
Proposition 6.
Consider a chinampa with multiplicity roots , where each root with R copies . The number of -triangular sequences counts the number of possible roots on with the previous conditions.
Proof.
Given the -triangular sequence , consider a rectangular board B of columns and R rows.
Step 1: We place a white mark at the cell of B, given by the intersection of row 1 and column . Step 2: We place a white mark at the cell intersection of row 2 and column and another white mark at the cell intersection of row 2 and column . Step i requires us to place marks at cells with . Now, for each i, we take the row and color all non-white cells in black from columns 1 to .
To recover the roots of , we substitute each black cell with three consecutive cells: one white and two black. The black cells are the activated vertices of the roots of . The fact that each of the sequences is decreasing translates into a movement of the roots to the left. The condition appears because the roots can move only one unit to the left. The map from one black block to a white block with two black blocks prevents redundancy. This assignment can be verified to be an isomorphism. □
Example 4.
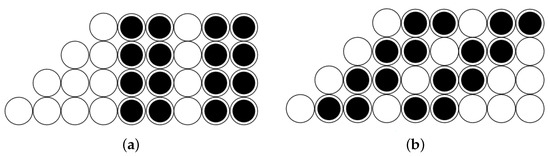
We examine the white spaces as shown in Figure 18. They correspond to the roots of Figure 17. According to Proposition 6, the sequences corresponding to Figure 18a are

Figure 18.
The corresponding triangular sequences come from counting blocks. (a) Vertical roots. (b) Diagonal roots.
For Figure 18b, they are
Ehrhart Series and Order Polynomials
The order polynomial of a partially ordered set (poset) P was introduced by Stanley [22]. The polynomial evaluated on n returns the number of labels on the poset P, which preserves the order.
Similar to the construction of , we can construct a poset containing only the symbol ≥ by subtracting units from the column i from right to left, where . The poset only depends on the variable R and not on the variables k and n:
Lemma 3.
Consider chinampas with roots of multiplicity , where each root with R is a copy of . Then, the number of such chinampas is .
Proof.
The number of triangular sequences is . □
This connection with combinatorics allowed us to determine the properties of the generating functions. For a poset P, one can associate the order polytope [23,24] . Then, the generating function of the order polynomial is the variable x times the Ehrhart series. For example, when , the triangular sequence corresponds to the poset , and we obtain the generating function .
Ehrhart series of order polytopes are known to be of the form or in our case . The term is a polynomial of a degree of at most d, where its coefficients satisfy the Dehn–Sommerville equations and are unimodal.
The previous result relates the enumeration of chinampas with polytopes of the form .
We counted chinampas with the help of Mathematica [25] and a topological version of the calculus of species [26]. These calculations gave us evidence of the validity of Lemma 3 and led to the concept of triangular sequences. For details on the use of Mathematica for counting order polytopes, see [27].
8. Conclusions
In this paper, we introduced activation diagrams, chinampas, and pyramids to study the effect of signals on the vertices of a nonlinear signal flow path. Furthermore, we demonstrated that pyramids are the simplest possible activation diagrams. Finally, we presented a deterministic algorithm to construct chinampas out of pyramids (see Remark 5). Chinampas were conceived to serve as an idealized model for cascades, with sequences of neural spikes forming a polychrony group.
To support our conclusions, we developed an optimal code to answer the following introductory questions: “Will a fixed vertex be activated at a particular time? Can we reconstruct all the vertices that will be activated?” We also achieved the enumeration of chinampas of profits of zero and one. The problem of finding all chinampas of profits bigger than two remains open. Our techniques for counting the chinampas of profits of zero and one cannot be adapted to this case, as the techniques miss a large family of elements (see Remark 6). We established that for a family of chinampas represented by triangular sequences, their enumeration problem is equivalent to computing the Stanley-order polynomial of a family of posets. To the best of our knowledge, finding the order polytope or Erhart series of these posets remains an open problem in enumerative combinatorics.
Modern algorithms aim to emulate the behavior of brain regions by simulating polychrony groups across multiple neurons [28,29]. Our approach differs in that we focus on a particular path of neurons and study the possible polychrony groups on that network.
Our contribution to computational neuroscience is not only theoretical. For example, the algorithm included in [1] and the software of [16,30,31,32,33] each emulate multiple cascades in parallel. When studying individual cascades along a line or in a tree, the software evaluates each cascade with a computational complexity of , where n is the number of neurons. In comparison, our algorithms scale as and in the best and worst cases, respectively. Optimization is important, since brain-like hardware is known to perform poorly [10,34]. We believe that our code can help to better understand the patterns of large polychrony groups efficiently.
Our work is limited to the study of signal flow paths. Possible continuations of this work include modeling triple-spike timing-dependent plasticity [35,36,37,38], for example in this paper we used self edges to model long-term potentiation. Inspired by [39], a machine learning algorithm such as genetic algorithms, combined with our software, should produce an algorithm with input of experimental measurements of spikes and output of the most likely topology of the network. Another possibility is to study redundant polychrony groups, where redundancy is applied to assure that software will work even if some components are damaged. Following [40], we would like to introduce noise in the theory of chinampas. Perhaps polycrhony groups can be used to study sparse neural networks [41,42,43,44,45] when the neuronal network uses a sigmoid activation function which is equivalent to our nonlinearity condition for the signal flow graphs. In relation to the theory of species [21,46], the first and second author are currently developing a topological version of species [26]. Topology is needed because our generating functions are parameterized by posets, as in Lemma 3. Finally, we believe it may be of interest to study signal flow graphs that admit cycles according to Figure 2. The feedback enables the existence of perpetual chinampas, the feedback in [14] is used to encode messages.
Author Contributions
Conceptualization, E.D.-C., J.A.A.-N., J.L.M.-C. and N.C.; methodology, E.D.-C. and J.A.A.-N.; software E.D.-C. and L.V.P.; validation, E.D.-C., J.A.A.-N., A.N. and A.Y.Z.; formal analysis, E.D.-C., J.A.A.-N. and G.E.; investigation, E.D.-C. and J.A.A.-N.; resources, J.L.M.-C.; writing—original draft preparation, E.D.-C., J.A.A.-N. and J.L.M.-C.; writing—review and editing, E.D.-C., J.A.A.-N., N.C., G.E. and J.L.M.-C.; visualization, E.D.-C. and J.A.A.-N.; supervision, J.L.M.-C.; project administration, E.D.-C. and J.L.M.-C.; funding acquisition, G.E. and J.L.M.-C. All authors have read and agreed to the published version of the manuscript.
Funding
The first author received funding from a National Research Foundation of Korea (NRF) grant funded by the Korean government (MSIT) (No. 2020R1C1C1A01008261). We thank FSU open access fund for covering publication costs.
Acknowledgments
We thank Jade Master for clarification of the relationship between Petri nets and chinampas. We thank the reviewers for their comments and suggestions that helped to improve this work. The cellular automata drawings were made using http://madebyevan.com/fsm/ (accessed on 3 March 2023). Figure 13 was made with https://playgameoflife.com/ (accessed on 3 March 2023).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Izhikevich, E.M. Polychronization: Computation with spikes. Neural Comput. 2006, 18, 245–282. [Google Scholar] [CrossRef] [PubMed]
- Mason, S.J. Feedback Theory-Some Properties of Signal Flow Graphs. Proc. IRE 1953, 41, 1144–1156. [Google Scholar] [CrossRef]
- Shannon, C.E. The Theory and Design of Linear Differential Equation Machines Report to National Defense Research Council, January 1942; Wiley-IEEE Press: New York, NY, USA, 1993; Chapter 33; pp. 514–559. [Google Scholar] [CrossRef]
- Guyton, A.C.; Coleman, T.G.; Granger, H.J. Circulation: Overall Regulation. Annu. Rev. Physiol. 1972, 34, 13–44. [Google Scholar] [CrossRef]
- Guilherme, J.; Horta, N.; Franca, J. Symbolic synthesis of non-linear data converters. In Proceedings of the 1998 IEEE International Conference on Electronics, Circuits and Systems. Surfing the Waves of Science and Technology (Cat. No.98EX196), Lisboa, Portugal, 7–10 September 1998; Volume 3, pp. 219–222. [Google Scholar] [CrossRef]
- Coşkun, K.Ç.; Hassan, M.; Drechsler, R. Equivalence Checking of System-Level and SPICE-Level Models of Static Nonlinear Circuits. In Proceedings of the Design, Automation and Test in Europe Conference (DATE), Online, 17–19 April 2023; Volume 16, p. 18. [Google Scholar]
- Ersalı, C.; Hekimoğlu, B. Nonlinear model and simulation of DC-DC Buck-Boost converter using switching flow-graph method. In Proceedings of the International Informatics Congress, Kunming, China, 15–16 December 2022. [Google Scholar]
- Baran, T.A. Inversion of nonlinear and time-varying systems. In Proceedings of the IEEE Digital Signal Processing and Signal Processing Education Meeting (DSP/SPE), Sedona, AZ, USA, 4–7 January 2011; pp. 283–288. [Google Scholar] [CrossRef]
- Thorpe, S.; Delorme, A.; Rullen, R.V. Spike-based strategies for rapid processing. Neural Netw. 2001, 14, 6–7. [Google Scholar] [CrossRef]
- Indiveri, G.; Chicca, E.; Douglas, R.J. Artificial Cognitive Systems: From VLSI Networks of Spiking Neurons to Neuromorphic Cognition. Cogn. Comput. 2009, 1, 119–127. [Google Scholar] [CrossRef]
- Indiveri, G.; Linares-Barranco, B.; Legenstein, R.; Deligeorgis, G.; Prodromakis, T. Integration of nanoscale memristor synapses in neuromorphic computing architectures. Nanotechnology 2013, 24, 384010. [Google Scholar] [CrossRef]
- Mead, C. Neuromorphic electronic systems. Proc. IEEE 1990, 78, 1629–1636. [Google Scholar] [CrossRef]
- Markovic, D.; Mizrahi, A.; Querlioz, D.; Grollier, J. Physics for Neuromorphic Computing. arXiv 2020, arXiv:2003.04711. [Google Scholar] [CrossRef]
- Sushchik, M.; Rulkov, N.; Larson, L.; Tsimring, L.; Abarbanel, H.; Yao, K.; Volkovskii, A. Chaotic pulse position modulation: A robust method of communicating with chaos. IEEE Commun. Lett. 2000, 4, 128–130. [Google Scholar] [CrossRef]
- Shiu, D.S.; Kahn, J. Differential pulse-position modulation for power-efficient optical communication. IEEE Trans. Commun. 1999, 47, 1201–1210. [Google Scholar] [CrossRef]
- Nahmias, M.A.; Shastri, B.J.; Tait, A.N.; Prucnal, P.R. A Leaky Integrate-and-Fire Laser Neuron for Ultrafast Cognitive Computing. IEEE J. Sel. Top. Quantum Electron. 2013, 19, 1–12. [Google Scholar] [CrossRef]
- Cormen, T.H.; Leiserson, C.E.; Rivest, R.L.; Stein, C. Introduction to Algorithms, 3rd ed.; The MIT Press: Cambridge, MA, USA, 2009. [Google Scholar]
- Barabási, A. Network Science; Cambridge University Press: Cambridge, MA, USA, 2016. [Google Scholar] [CrossRef]
- Wolfram, S. A New Kind of Science; Wolfram Media: Champaign, IL, USA, 2002. [Google Scholar]
- Gardner, M. Mathematical Games—The Fantastic Combinations of John Conway’s New Solitaire Game ‘Life’. Sci. Am. 1970, 223, 70–120. [Google Scholar] [CrossRef]
- Wilf, H.S. Generating Functionology, 3rd ed.; A. K. Peters Ltd.: Wellesley, MA, USA, 2006; p. 245. [Google Scholar] [CrossRef]
- Stanley, R.P. A chromatic-like polynomial for ordered sets. In Proceedings of the 2nd Conference on Combinatorics Mathematics Application; University of North Carolina: Chapel Hill, NC, USA, 1970; pp. 421–427. [Google Scholar]
- Beck, M.; Robins, S. Computing the Continuous Discretely. Integer-Point Enumeration in Polyhedra, with Illustrations by David Austin, 2nd ed.; Undergraduate Texts Math; Springer: New York, NY, USA, 2015. [Google Scholar] [CrossRef]
- Beck, M.; Sanyal, R. Combinatorial Reciprocity Theorems. An Invitation to Enumerative Geometric Combinatorics; Grad. Stud. Math.; American Mathematical Society (AMS): Providence, RI, USA, 2018; Volume 195. [Google Scholar] [CrossRef]
- Wolfram Research, I. Mathematica, Version 12.1; Wolfram Research, Inc.: Champaign, IL, USA, 2020. [Google Scholar]
- Arciniega-Nevárez, J.A.; Berghoff, M.; Dolores-Cuenca, E.R. An algebra over the operad of posets and structural binomial identities. Boletín Soc. Mat. Mex. 2022, 29, 478. [Google Scholar] [CrossRef]
- Dolores-Cuenca, E.R. Computing Order Series/Ehrhart Polynomials of Posets with Mathematica. In The Notebook Archive; 2022. Available online: https://notebookarchive.org/2022-02-3pvm73a (accessed on 8 November 2022).
- Pauli, R.; Weidel, P.; Kunkel, S.; Morrison, A. Reproducing Polychronization: A Guide to Maximizing the Reproducibility of Spiking Network Models. Front. Neuroinform. 2018, 12, 46. [Google Scholar] [CrossRef] [PubMed]
- Oberländer, J.; Bouhadjar, Y.; Morrison, A. Learning and replaying spatiotemporal sequences: A replication study. Front. Integr. Neurosci. 2022, 16. [Google Scholar] [CrossRef] [PubMed]
- Pfeil, T.; Grübl, A.; Jeltsch, S.; Müller, E.; Müller, P.; Petrovici, M.A.; Schmuker, M.; Brüderle, D.; Schemmel, J.; Meier, K. Six networks on a universal neuromorphic computing substrate. Front. Neurosci. 2013, 7, 11. [Google Scholar] [CrossRef]
- Merolla, P.; Arthur, J.; Akopyan, F.; Imam, N.; Manohar, R.; Modha, D.S. A digital neurosynaptic core using embedded crossbar memory with 45pJ per spike in 45nm. In Proceedings of the 2011 IEEE Custom Integrated Circuits Conference (CICC), San Jose, CA, USA, 19–21 September 2011; pp. 1–4. [Google Scholar] [CrossRef]
- Seo, J.s.; Brezzo, B.; Liu, Y.; Parker, B.D.; Esser, S.K.; Montoye, R.K.; Rajendran, B.; Tierno, J.A.; Chang, L.; Modha, D.S.; et al. A 45nm CMOS neuromorphic chip with a scalable architecture for learning in networks of spiking neurons. In Proceedings of the 2011 IEEE Custom Integrated Circuits Conference (CICC), San Jose, CA, USA, 19–21 September 2011; pp. 1–4. [Google Scholar] [CrossRef]
- Boahen, K. Neurogrid: Emulating a million neurons in the cortex. In Proceedings of the IEEE Conference on Engineering in Medicine and Biology Society, New York, NY, USA, 30 August 2006–3 September 2006; pp. 1–4. [Google Scholar] [CrossRef]
- Elnagar, S.; Thomas, M.A.; Osei-Bryson, K.M. What is Cognitive Computing? An Architecture and State of The Art. arXiv 2023, arXiv:2301.00882. [Google Scholar] [CrossRef]
- Aghnout, S.; Karimi, G.; Azghadi, M. Modeling triplet spike-timing-dependent plasticity using memristive devices. J. Comput. Electron. 2017, 16, 401–410. [Google Scholar] [CrossRef]
- Froemke, R.; Dan, Y. Spike-timing-dependent synaptic modification induced by natural spike trains. Nature 2002, 416, 433–438. [Google Scholar] [CrossRef]
- Pfister, J.P.; Gerstner, W. Triplets of Spikes in a Model of Spike Timing-Dependent Plasticity. J. Neurosci. 2006, 26, 9673–9682. [Google Scholar] [CrossRef]
- Hartley, M.; Taylor, N.; Taylor, J. Understanding spike-time-dependent plasticity: A biologically motivated computational model. Brain Inspired Cognitive Systems. Neurocomputing 2006, 69, 2005–2016. [Google Scholar] [CrossRef]
- Silva, G. The Need for the Emergence of Mathematical Neuroscience: Beyond Computation and Simulation. Front. Comput. Neurosci. 2011, 5, 51. [Google Scholar] [CrossRef]
- Štukelj, G. Significance of Neural Noise. Ph.D. Thesis, LM University, Munchen, Germany, 2020. [Google Scholar]
- Mozer, M.C.; Smolensky, P. Using Relevance to Reduce Network Size Automatically. Connect. Sci. 1989, 1, 3–16. [Google Scholar] [CrossRef]
- Janowsky, S.A. Pruning versus clipping in neural networks. Phys. Rev. A 1989, 39, 6600–6603. [Google Scholar] [CrossRef] [PubMed]
- LeCun, Y.; Denker, J.; Solla, S. Optimal Brain Damage. In Proceedings of the Advances in Neural Information Processing Systems; Touretzky, D., Ed.; Morgan-Kaufmann: San Francisco, CA, USA, 1989; Volume 2. [Google Scholar]
- Hoefler, T.; Alistarh, D.; Ben-Nun, T.; Dryden, N.; Peste, A. Sparsity in Deep Learning: Pruning and Growth for Efficient Inference and Training in Neural Networks. J. Mach. Learn. Res. 2022, 22, 554. [Google Scholar]
- Liu, S.; Wang, Z. Ten Lessons We Have Learned in the New “Sparseland”: A Short Handbook for Sparse Neural Network Researchers. arXiv 2023, arXiv:2302.02596. [Google Scholar] [CrossRef]
- Bergeron, F.; Labelle, G.; Leroux, P. Combinatorial Species and Tree-like Structures. In Encyclopedia of Mathematics and its Applications; Cambridge University Press: Cambridge, MA, USA, 1997. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).