Blockchain-Based, Dynamic Attribute-Based Access Control for Smart Home Energy Systems
Abstract
1. Introduction
2. Background and Motivation
3. Preliminary
3.1. Attribute-Based Access Control (ABAC)
3.2. Blockchain Technology
4. Related Work
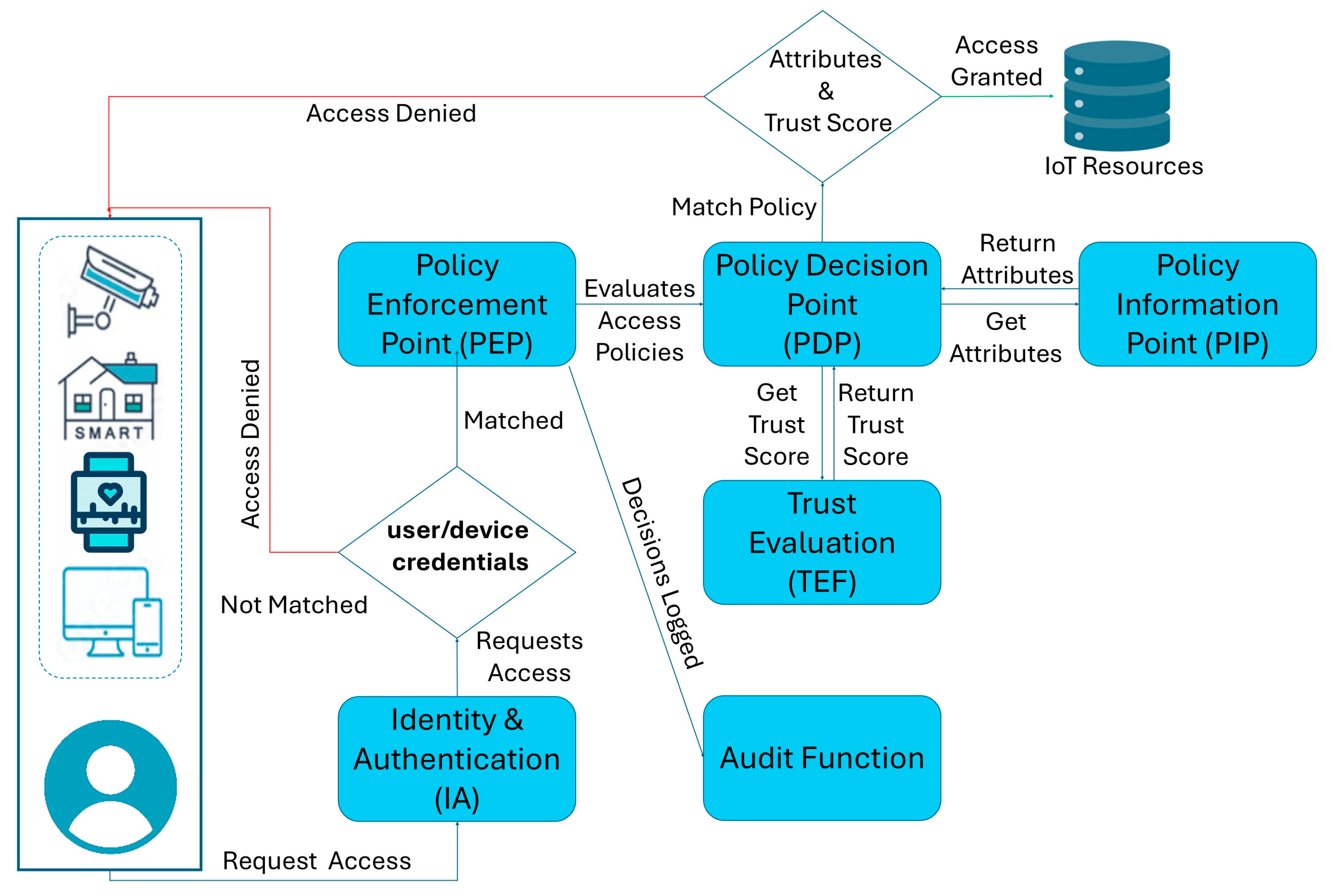
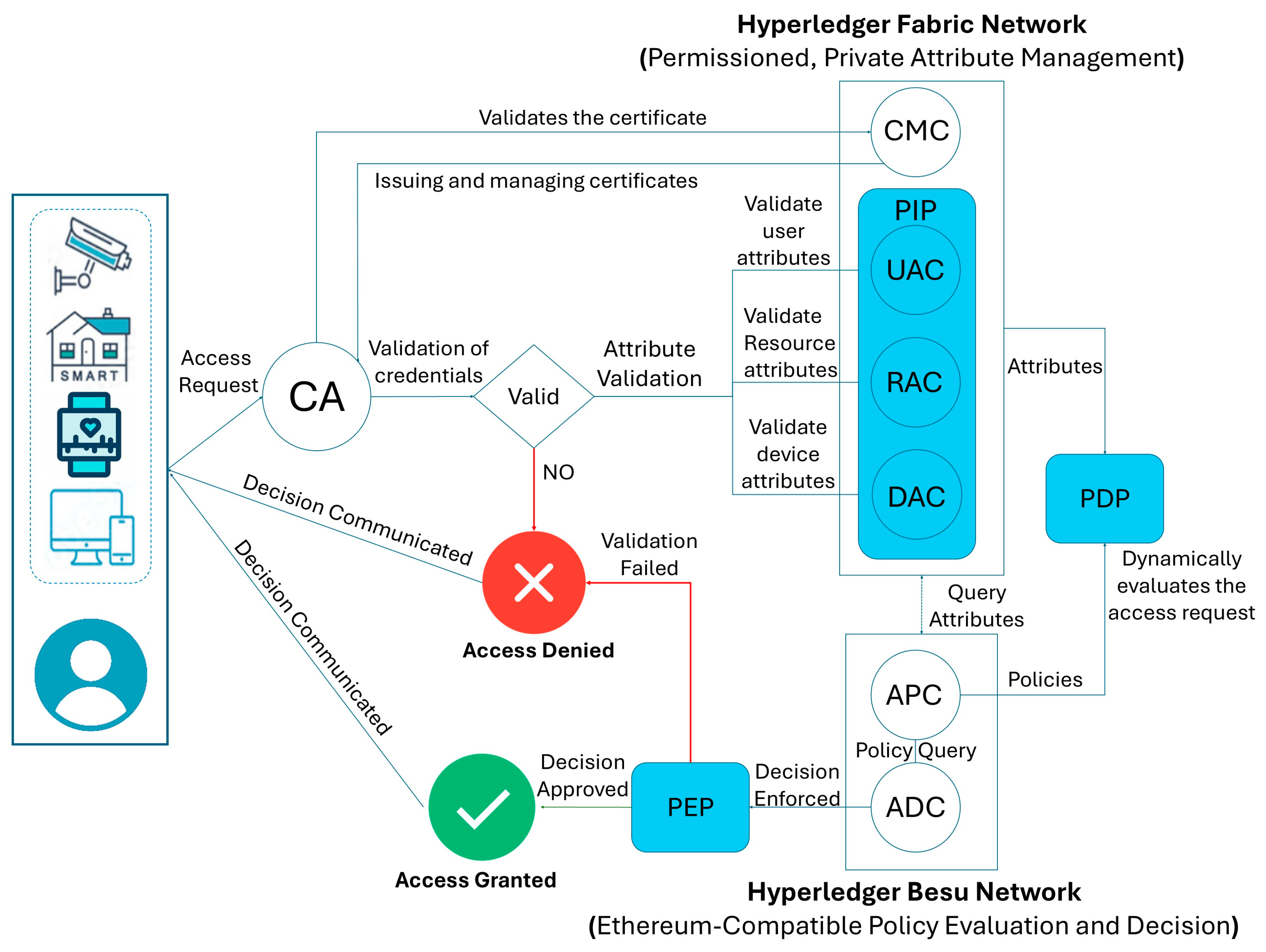
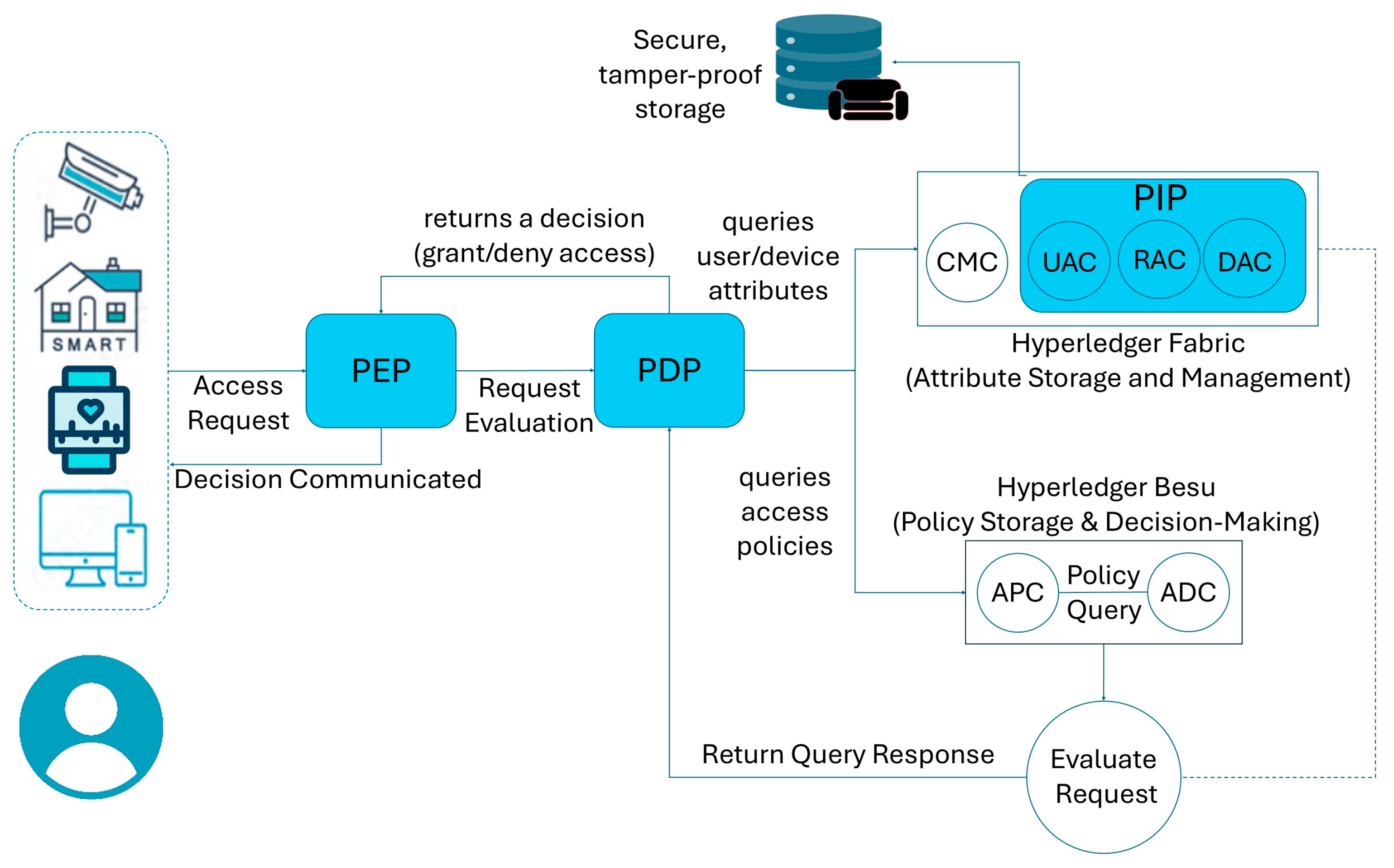
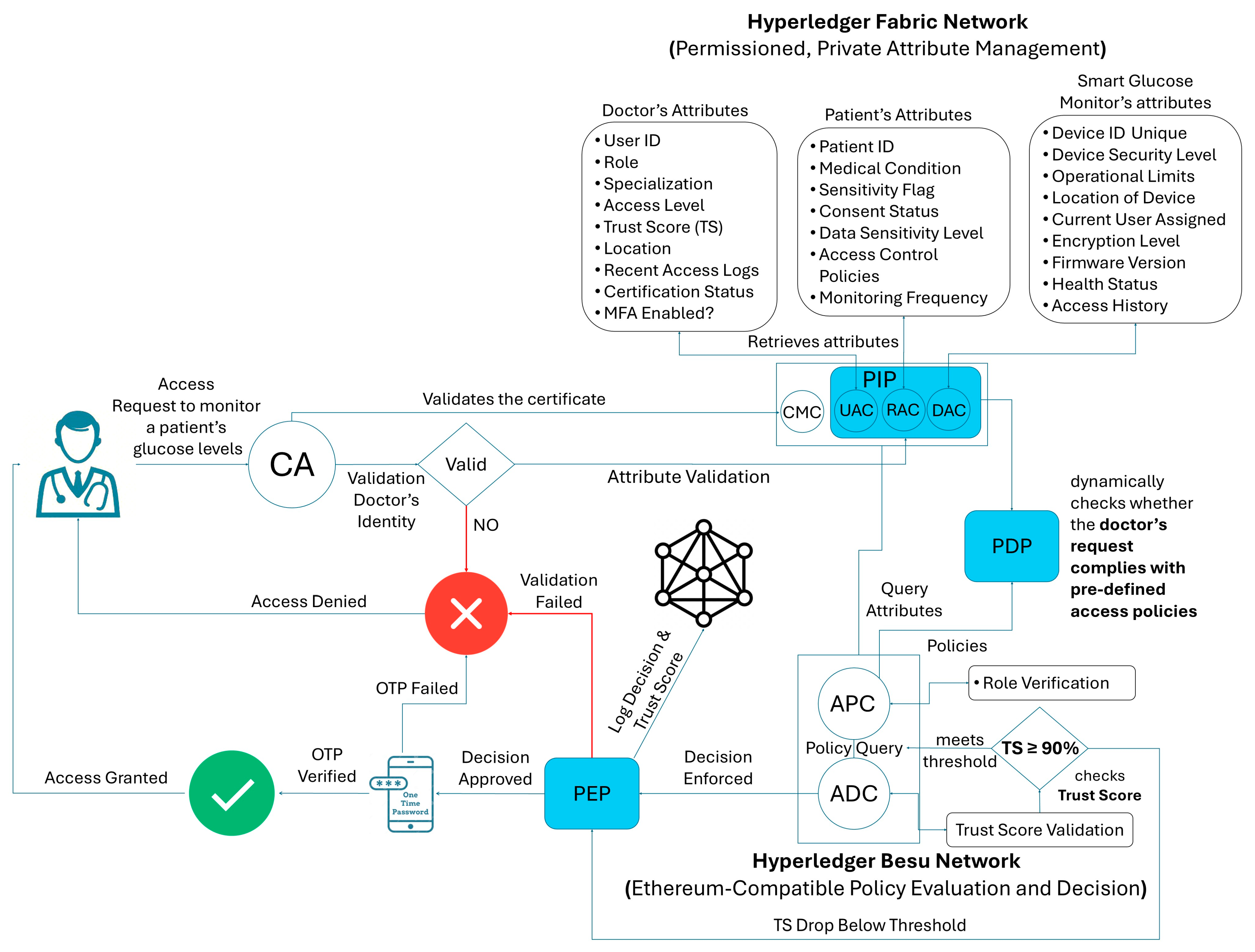
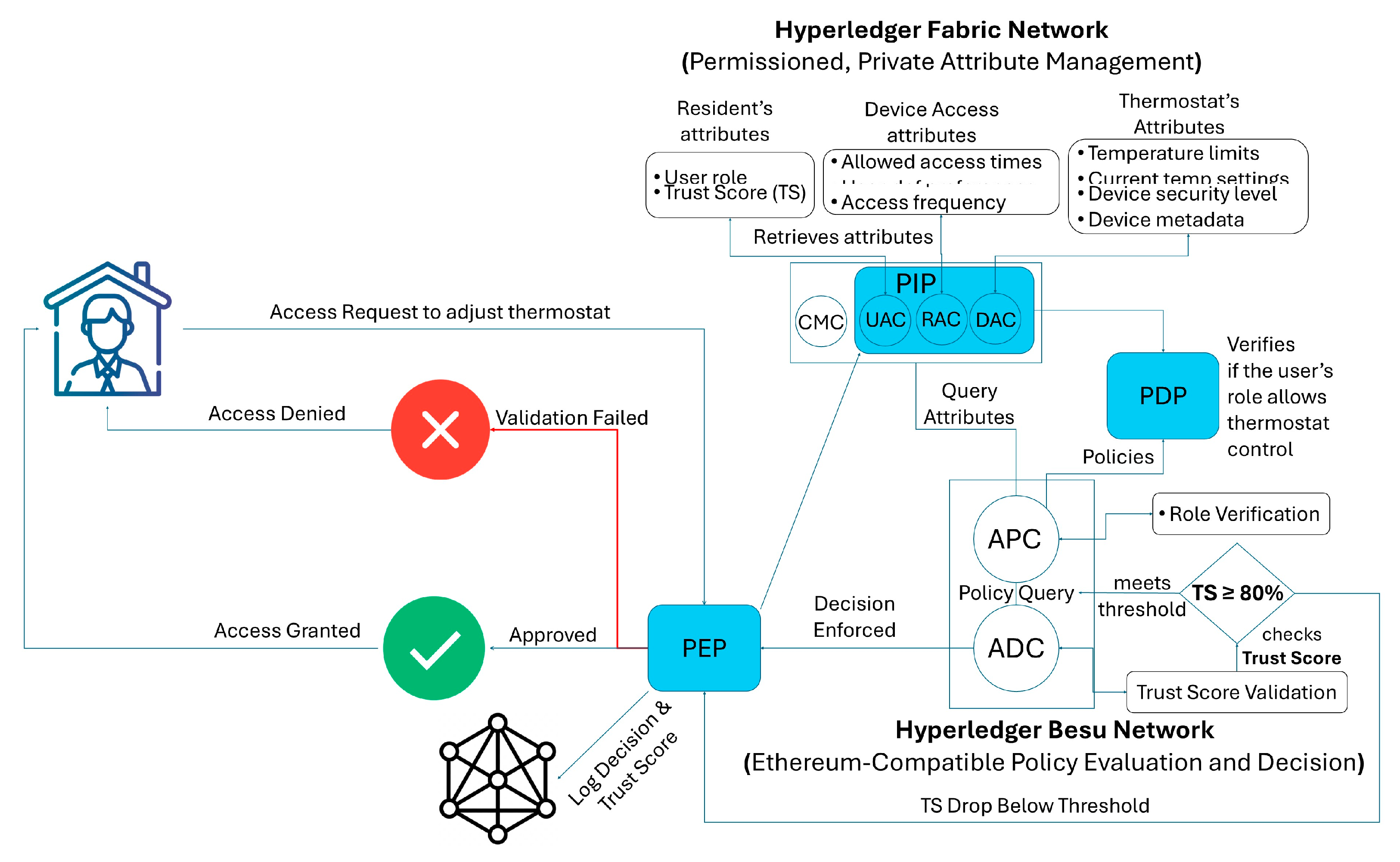
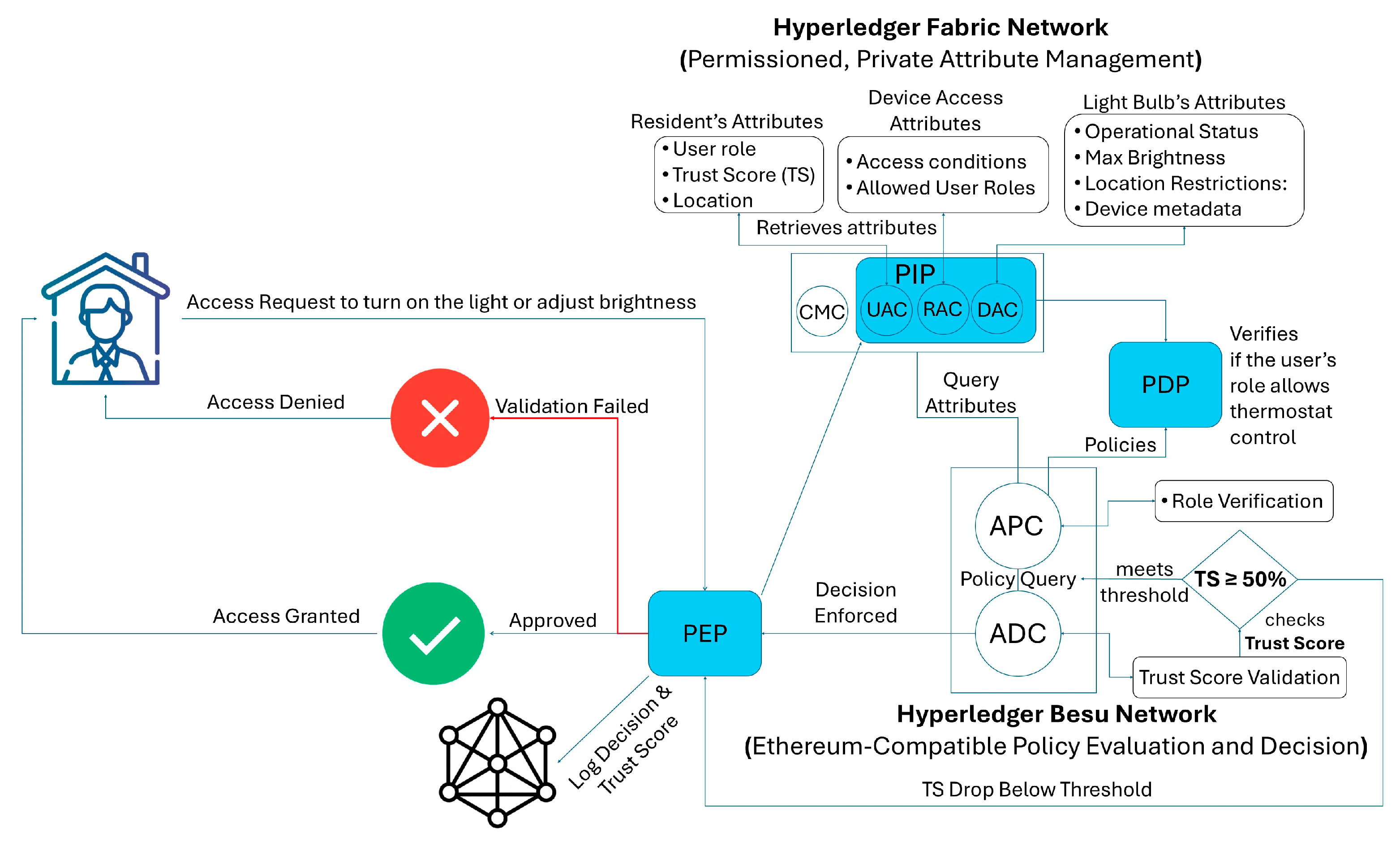
5. Proposed System Architecture for Dynamic ABAC
| Algorithm 1. Dynamic ABAC with Hybrid Blockchain | |
| START | |
| Step 1: | INPUT Collection |
| Collect user/device ID, requested action, trust score (TS), energy sensitivity weight (Te), and System defined attributes. | |
| Step 2: | Device/User Registration |
| |
| Step 3: | Identity Verification and Validation |
| |
| Step 4: | Metadata and Certificate Validation |
| |
| Step 5: | Certificate Issuance and Storage |
| Generate and store digital certificates securely in Hyperledger Fabric. | |
| Step 6: | Access Request Submission |
| |
| Step 7: | Attribute and Policy Retrieval |
| |
| Step 8: | Trust Score Evaluation |
| |
| Step 9: | Policy-Based Access Evaluation |
| |
| Step 10: | Multi-Factor Authentication (MFA) Check |
| |
| Step 11: | Policy Enforcement and Smart Contract Execution |
| |
| Step 12: | Grant or Deny Access |
| |
| Step 13: | Trust Score Recalibration |
| |
| Step 14: | Security Monitoring and Anomaly Detection |
| |
| Step 15: | Quarantine and Revocation Mechanism |
| |
| Step 16: | Blockchain Logging and Record Update |
| |
| END | |
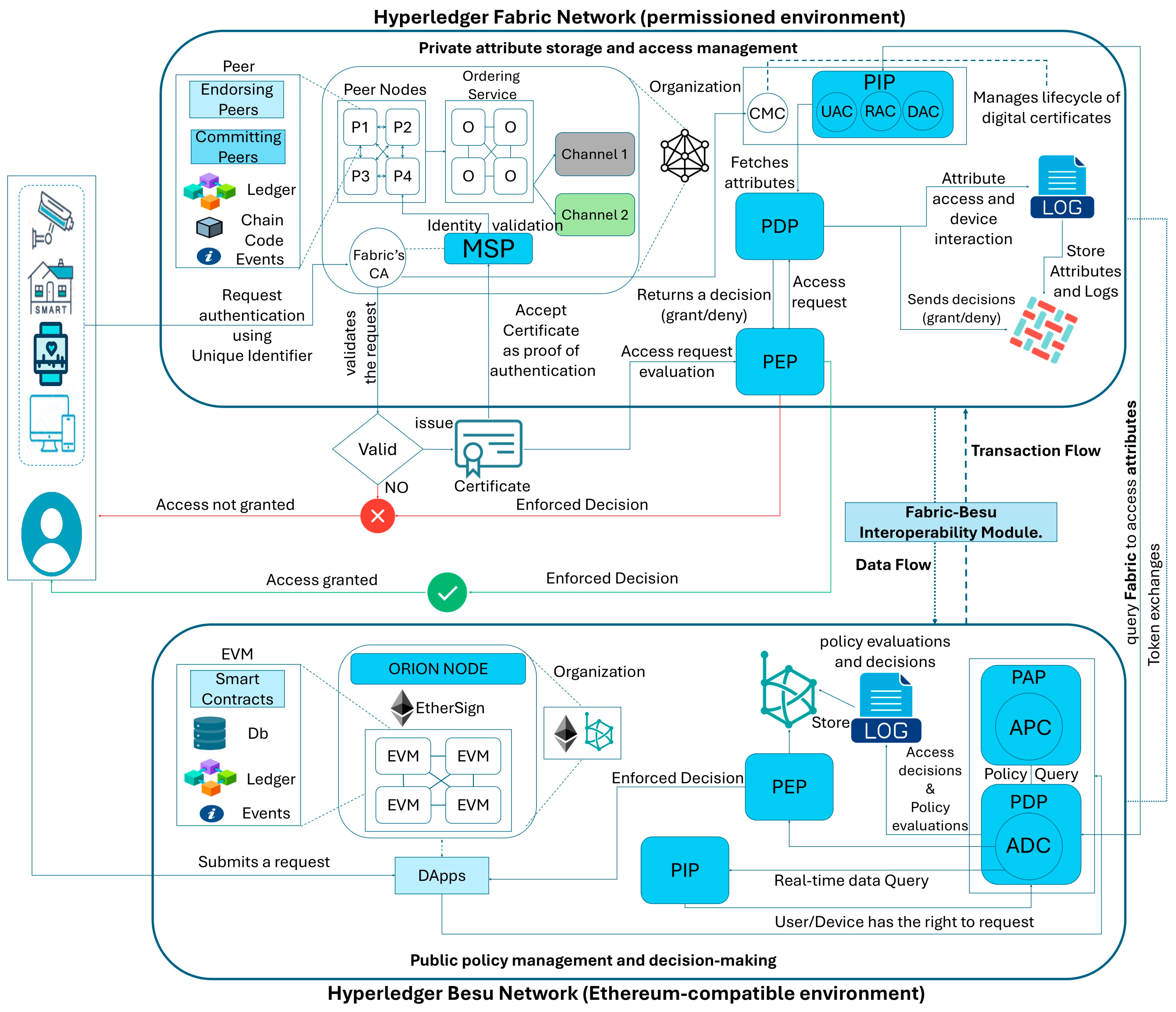
5.1. Hybrid Blockchain Integration for Secure and Controlled Access
5.2. Smart Contracts for Dynamic ABAC
- User Role: Differentiates between homeowners, tenants, energy managers, and utility providers;
- Device Sensitivity: Classifies devices as critical (e.g., smart meters, battery storage, HVAC systems) or non-critical (e.g., smart lights, smart plugs);
- Energy Consumption Context: Real-time power usage, peak demand periods, and available renewable energy sources;
- Environmental Context: Evaluates real-time conditions such as time of day, user location, and household energy demand to adapt policies dynamically.
5.2.1. User Attribute Contract
5.2.2. Resource Attribute Contract
5.2.3. Device Attribute Contract
5.2.4. Certificate Management Contract
5.2.5. Access Policy Contract
5.2.6. Access Decision Contract
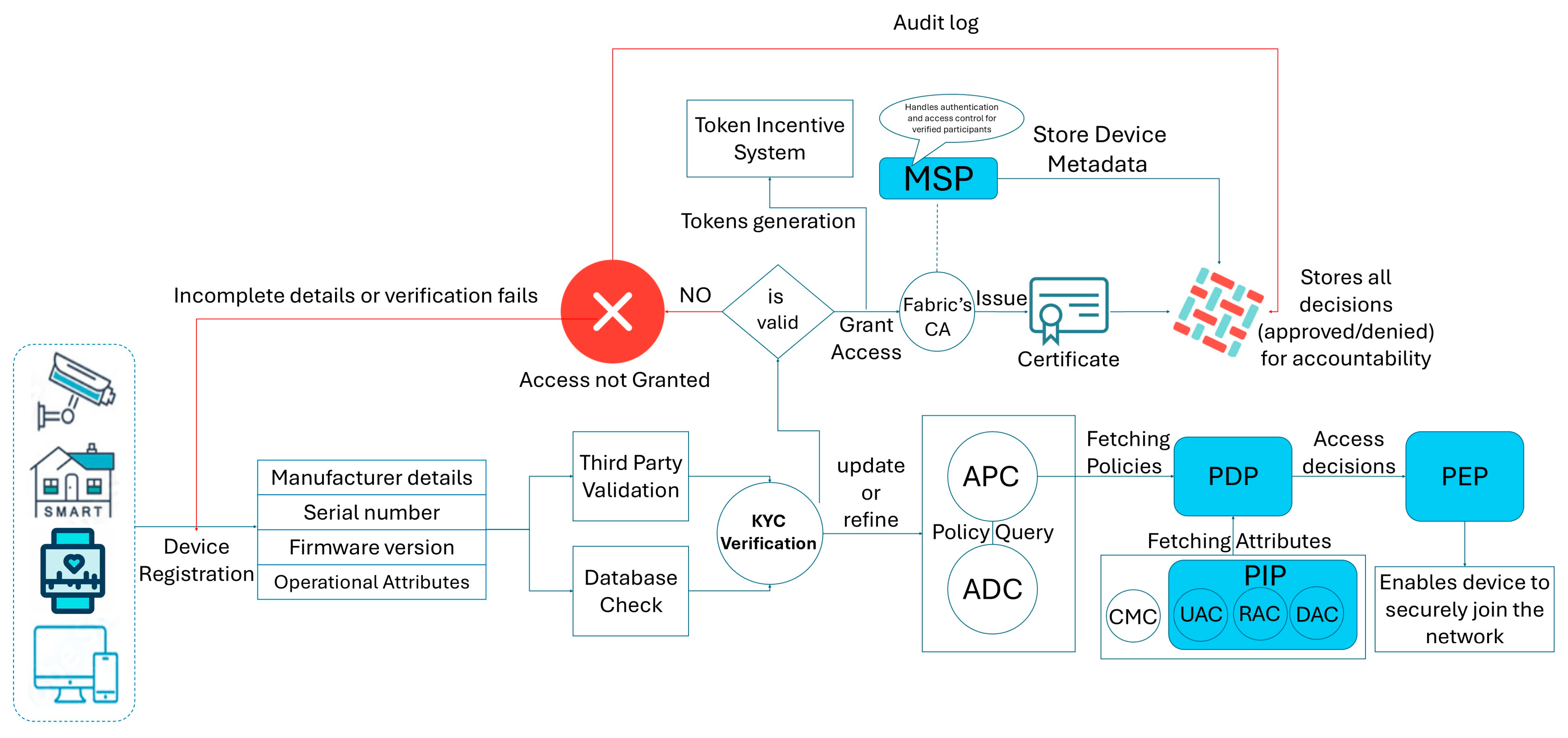
5.3. KYC-Based Identity Verification
5.4. Real-Time Attribute Repository
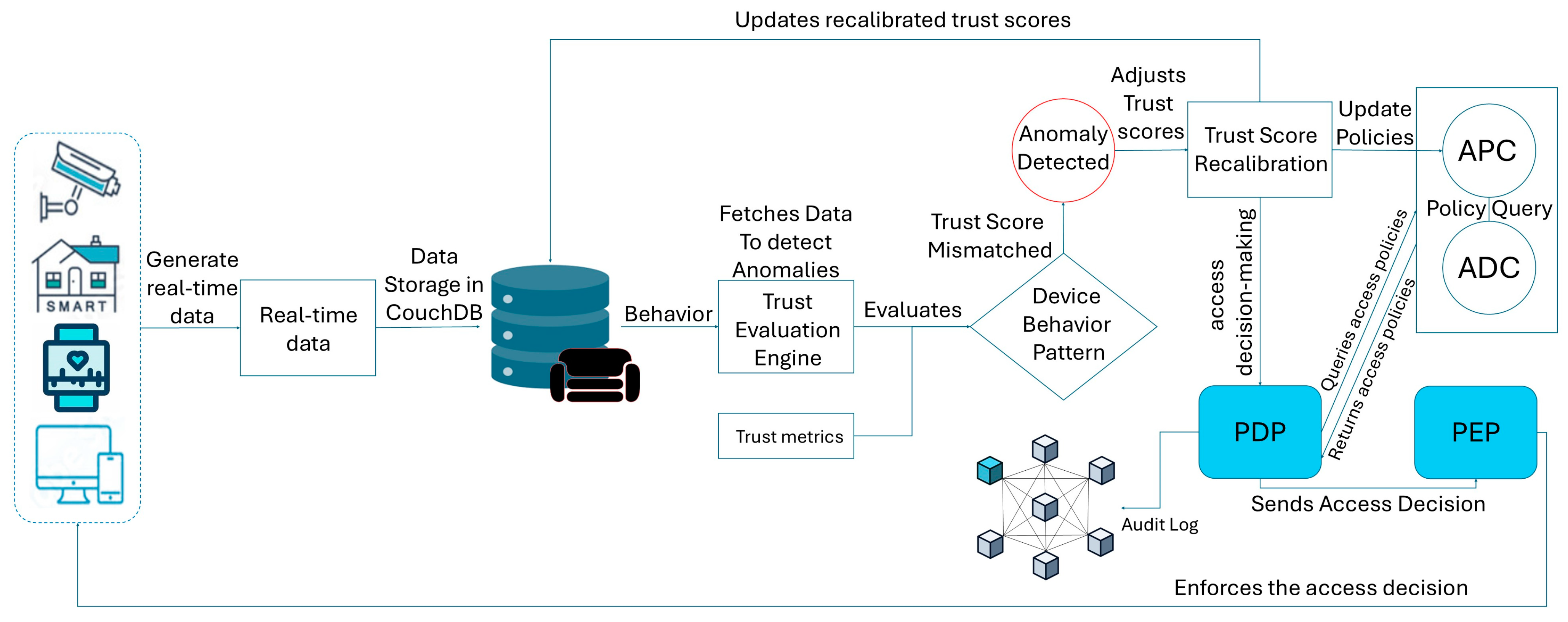
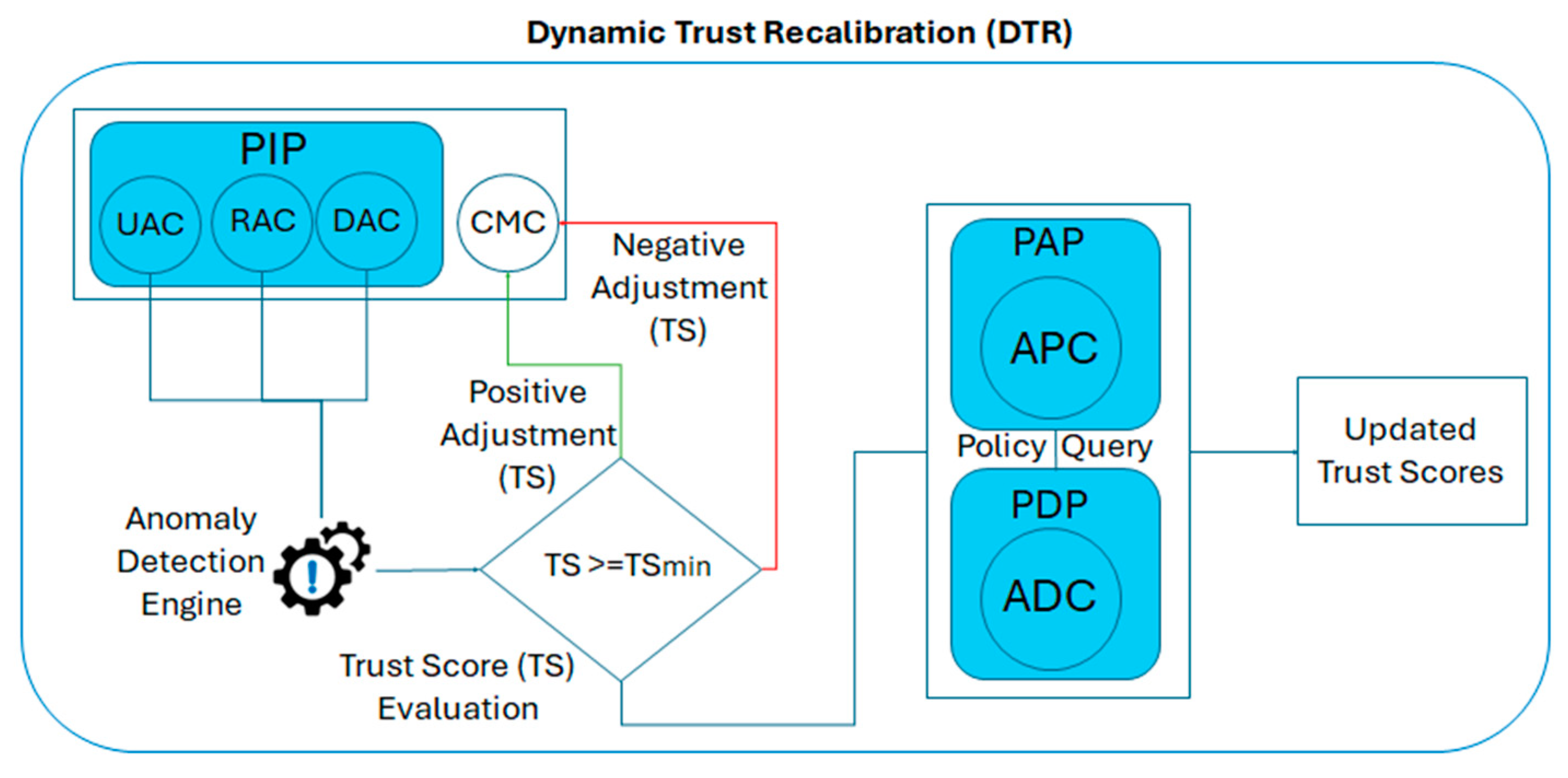
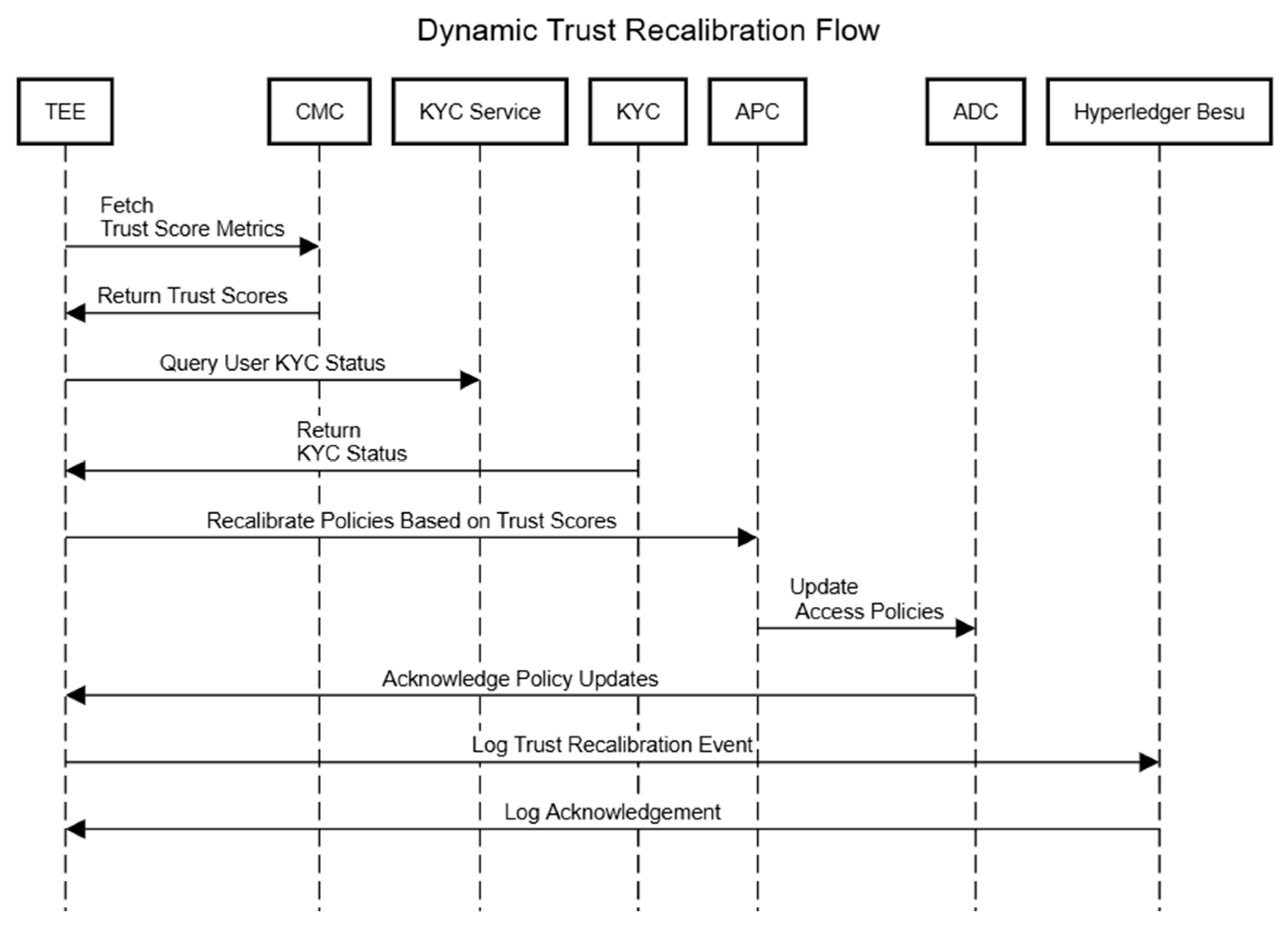
5.5. Dynamic Trust Recalibration
6. Proposed Model Implementation
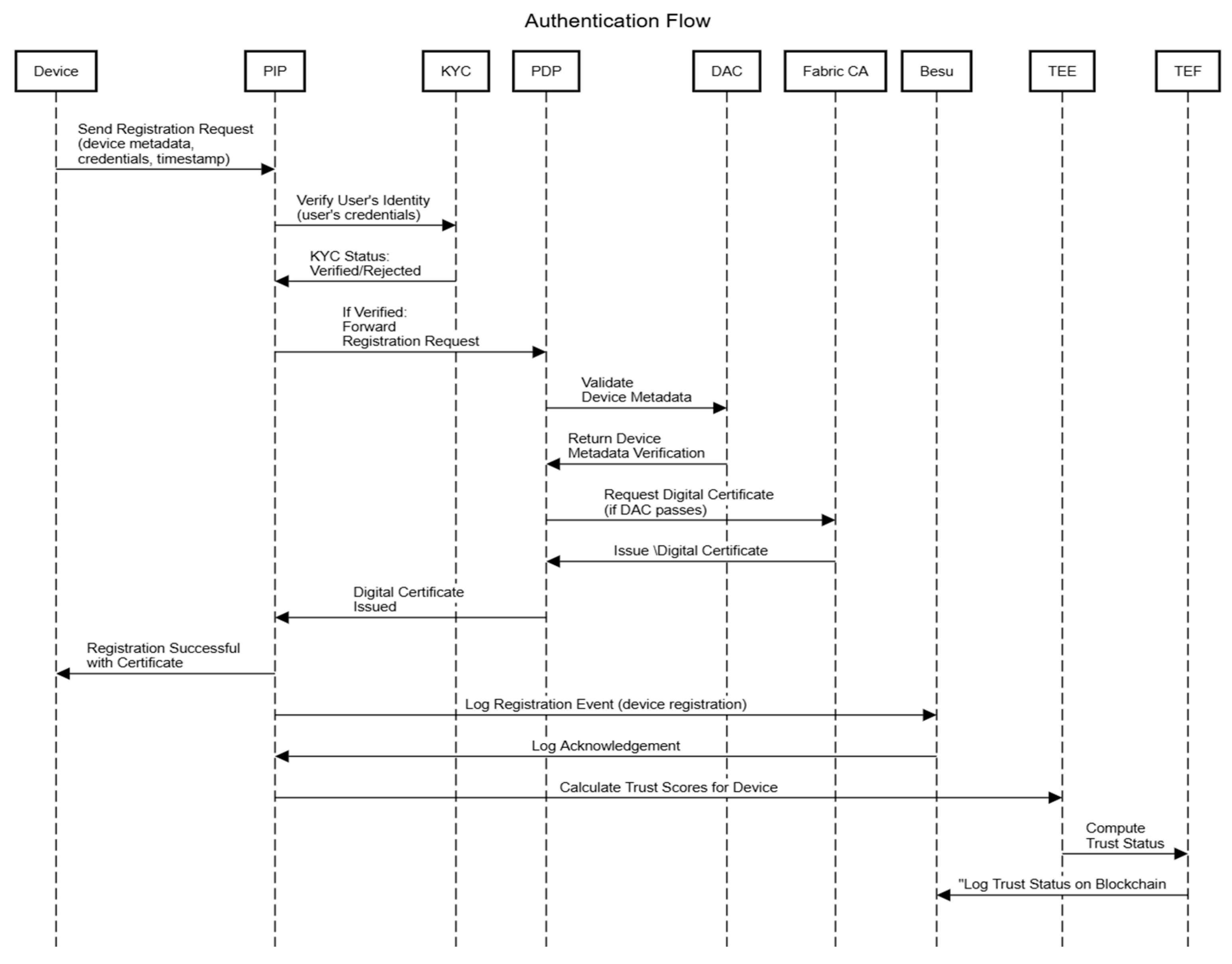
6.1. Device Registration Process on Blockchain
6.2. Data Storage/Collection
6.3. Trust Evaluation Framework (TEF)
6.4. Dynamic Trust Recalibration (DTR)
- Positive Adjustments: Devices and users demonstrating secure and reliable behavior, such as successful authentications and reliable operations, see their scores increase when the TS is above the minimum threshold (TSmin);
- Negative Adjustments: Anomalies or behaviors below the TSmin trigger a recalibration, reducing trust scores.
7. Policy Framework
7.1. Device-Level Policies
7.1.1. Device Acceptance Policy
| Policy A: Initial Restricted Access for New Devices | |
| Rule | New device can only communicate with N devices for the first T hours. |
| Purpose | Stop a rogue device from instantly interacting with all devices. |
| Condition | If (TS < TSmin & Talive < T), communicate with N devices within zone. |
| Action | Restrict access; allow incremental communication as TS increases. |
| Policy B: Progressive Trust-Based Access | |
| Rule | A new device cannot initiate communication with high-security devices until it achieves a TS ≥ 70%. |
| Purpose | Stop unauthorized devices from accessing critical infrastructure. |
| Condition | If the (TS < 70%), inter-zone communication is not allowed. |
| Action | Log attempts, adjust TS accordingly. |
7.1.2. Device Access Policies
| Policy C: Trust-Based Device Communication | |
| Rule | A device can access another device only if its TS and priority is higher than the target device’s threshold. |
| Purpose | Only trusted devices are allowed to initiate communication. |
| Condition | If (TS + Priority) ≥ (TS target + Required Level), access is granted. |
| Action | Log access requests; if TS is insufficient, deny and reduce TS. |
| Policy D: Monitoring Devices Cannot Send Control Commands | |
| Rule | A device with a monitoring role cannot send control signals. |
| Purpose | Only trusted devices are allowed to initiate communication. |
| Condition | If (Device_Role) = “Monitoring”, deny control requests. |
| Action | Generate a security alert on repeated attempts. |
| Policy E: Centralized Device Control Enforcement | |
| Rule | A device can receive control data from only one controlling device at any given time. |
| Purpose | Prevent conflicting control signals. |
| Condition | If (Active (Control Request)), deny control requests. |
| Action | Place additional requests in a pending state. |
7.1.3. Access Limitation Policy
| Policy F: Trust-Based Limited Control Broadcasting | |
| Rule | A monitoring device can send control signals to multiple devices only if its TS is above a defined threshold. |
| Purpose | Prevent large-scale attacks and unauthorized mass control attempts. |
| Condition | If the (TS < 50%), restrict control to a maximum of N devices at a time. |
| Action | Deny excessive control requests, recalculate TS; if the (TS < 40%), quarantine the device. |
| Policy G: Restricted Large-Scale Control Access | |
| Rule | Only authorized supervisory devices with a TS ≥ 80% can initiate mass control operations. |
| Purpose | Ensure only trusted devices can send commands to multiple devices. |
| Condition | If (User_Role! = “Supervisor”) OR (TS < 80%), deny mass control requests. |
| Action | Revoke access and lower the TS if unauthorized attempts persist. |
| Policy H: Network-Wide Broadcast Prohibition | |
| Rule | No device can broadcast messages to all network devices simultaneously. |
| Purpose | Prevent flooding attacks and network congestion. |
| Condition | If a device attempts a network-wide broadcast, reset its TS to zero. |
| Action | Immediately quarantine the device and flag it for security review. |
7.2. User-Level Policies
| Policy I: Trust-Based Multi-Factor Authentication (MFA) | |
| Rule | A user must provide additional authentication factors if their TS is below a defined threshold. |
| Purpose | Stop unauthorized access by requiring stricter authentication for low-trust users. |
| Condition | If the (TS < threshold), enforce MFA |
| Action | Reject access on authentication failure and lower the TS further on repeated failures |
| Policy J: Adaptive RBAC | |
| Rule | A user can only access specific device categories and operations based on their role and TS. |
| Purpose | Restrict users to their assigned permissions while adapting access dynamically based on trust level. |
| Condition | If (User_Role = “Energy Auditor”) → Can access energy monitoring and optimization devices only. If (User_Role = “Homeowner”) → Can control home energy management devices. If the (TS < 50%), restrict access to critical energy functions. |
| Action | Deny unauthorized requests, log violations, and lower the TS for misuse attempts. |
| Policy K: Trust-Driven Time-Based Access | |
| Rule | Users with a lower TS have restricted access windows for security-sensitive devices. |
| Purpose | Prevent unauthorized late-night access and enforce time-sensitive controls. |
| Condition | If the (TS ≥ 80%), full access 24/7. If the (TS < 80%), access is allowed only between 6 a.m.–10 p.m. If the (TS < 40%), restrict access to non-sensitive functions only. |
| Action | If an access request occurs outside the allowed timeframe, deny access and reduce the TS. |
| Policy L: Behavior-Based Access Restrictions | |
| Rule | Users with a lower TS have restricted access windows for security-sensitive devices. |
| Purpose | Detects potential attackers or compromised accounts. |
| Condition | If (Failed Attempts ≥ 3), reduce the TS by 10%. If (Failed Attempts ≥ 5), enforce a mandatory cooldown period before retrying. If the (TS < threshold), flag the user for administrative review. |
| Action | Lock the account if continuous violations occur and alert security admins. |
| Policy M: Device Sensitivity-Based User Authentication | |
| Rule | Users require a higher authentication to access high-security devices. |
| Purpose | Ensure sensitive devices are accessed only by trusted and authorized users. |
| Condition | If (Device_Security_Level = “High”) AND (TS < threshold), enforce biometric + OTP authentication. If (Device_Security_Level = “Moderate”), password + OTP required. If (Device_Security_Level = “Low”), password-only access is allowed. |
| Action | If authentication fails, lock access for T minutes and reduce the TS. |
8. Workflow and Scenario
- A smart home device initiates a registration request by generating an RSA-based public–private key pair.
- The device sends a digitally signed registration packet containing its metadata and timestamp.
- The owner’s credentials undergo KYC verification, and upon successful verification, the DAC validates the device metadata.
- The CMC issues a digital certificate binding the public key, device identifier, and owner details.
- User, device, and environmental attributes are stored securely in Hyperledger Fabric’s CouchDB. Attributes are dynamically updated using the change feed mechanism for real-time evaluations.
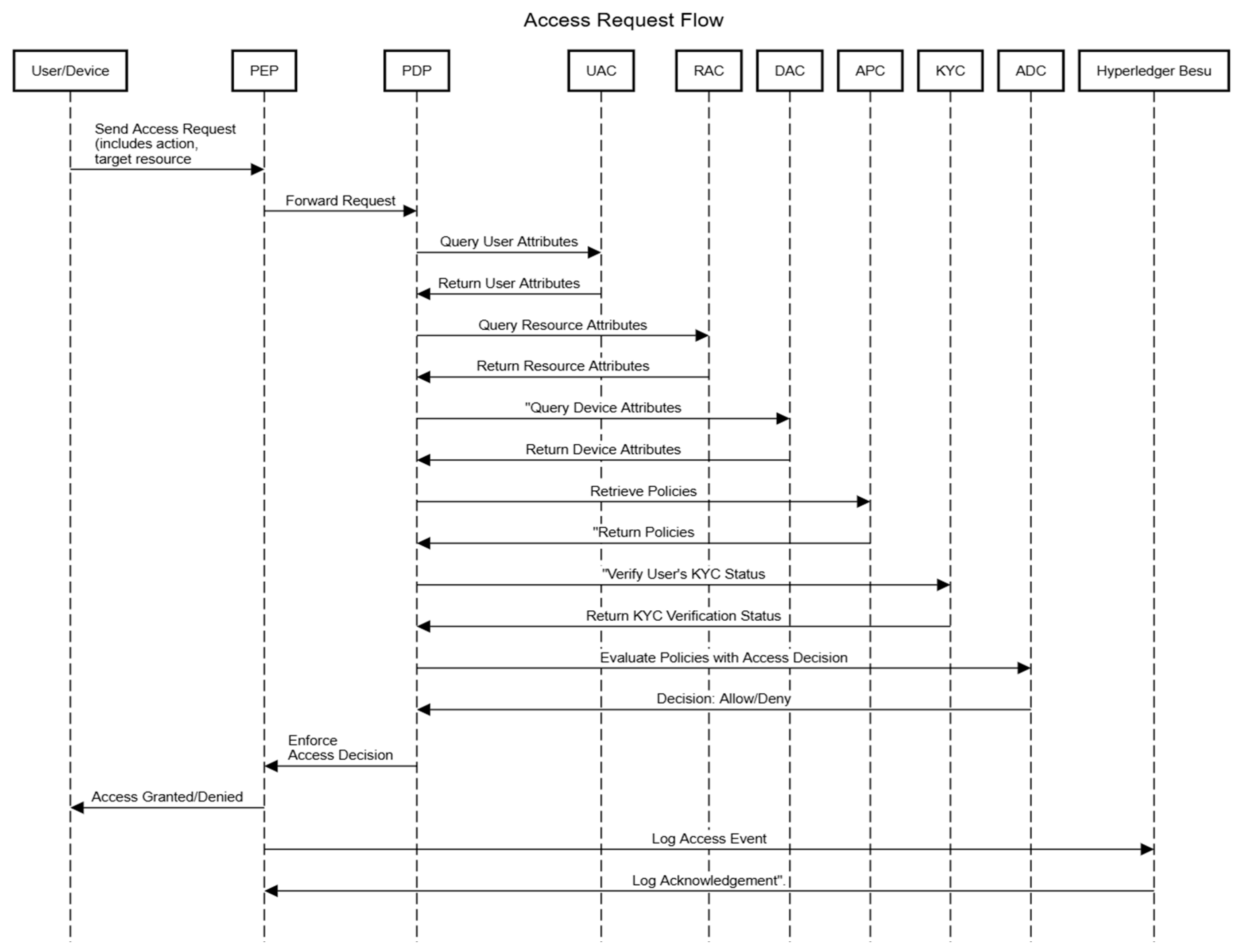
- Access requests from users or devices are routed to the PEPs; the PEP queries attributes and policies.
- a.
- The PDP evaluates the request against predefined policies.
- b.
- Dynamic TSs are integrated into the decision-making process to determine access eligibility.
- The ADC dynamically evaluates the access request using attributes and policies. The decision is logged immutably on the blockchain and communicated back to the PEP for enforcement.
- Real-time behavioral data are analyzed by the trust evaluation framework. Any anomalies trigger a recalibration of the TS and adaptive policy adjustments.
8.1. High-Security Devices
8.2. Moderate-Security Devices
8.3. Low-Security Devices
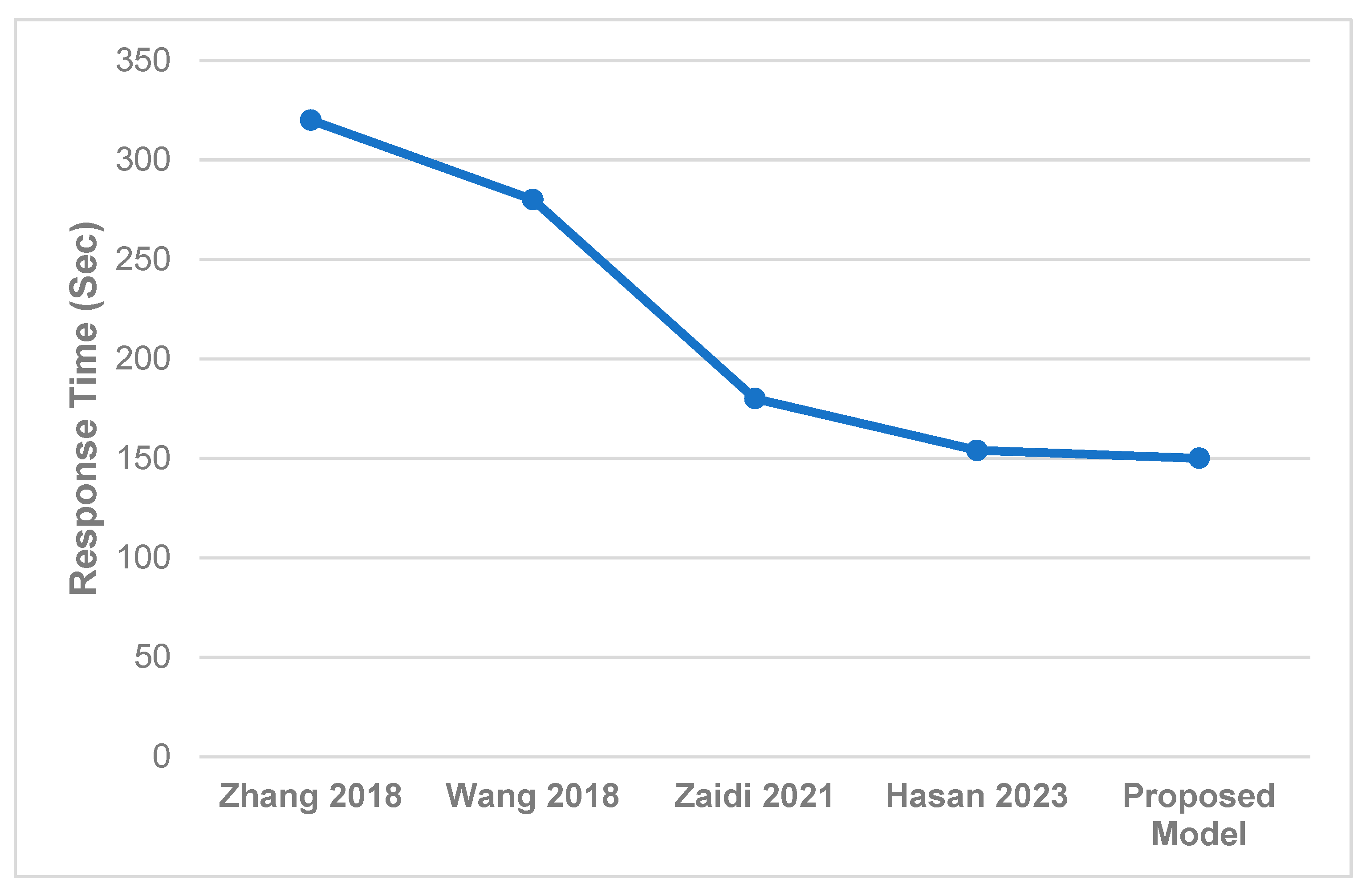
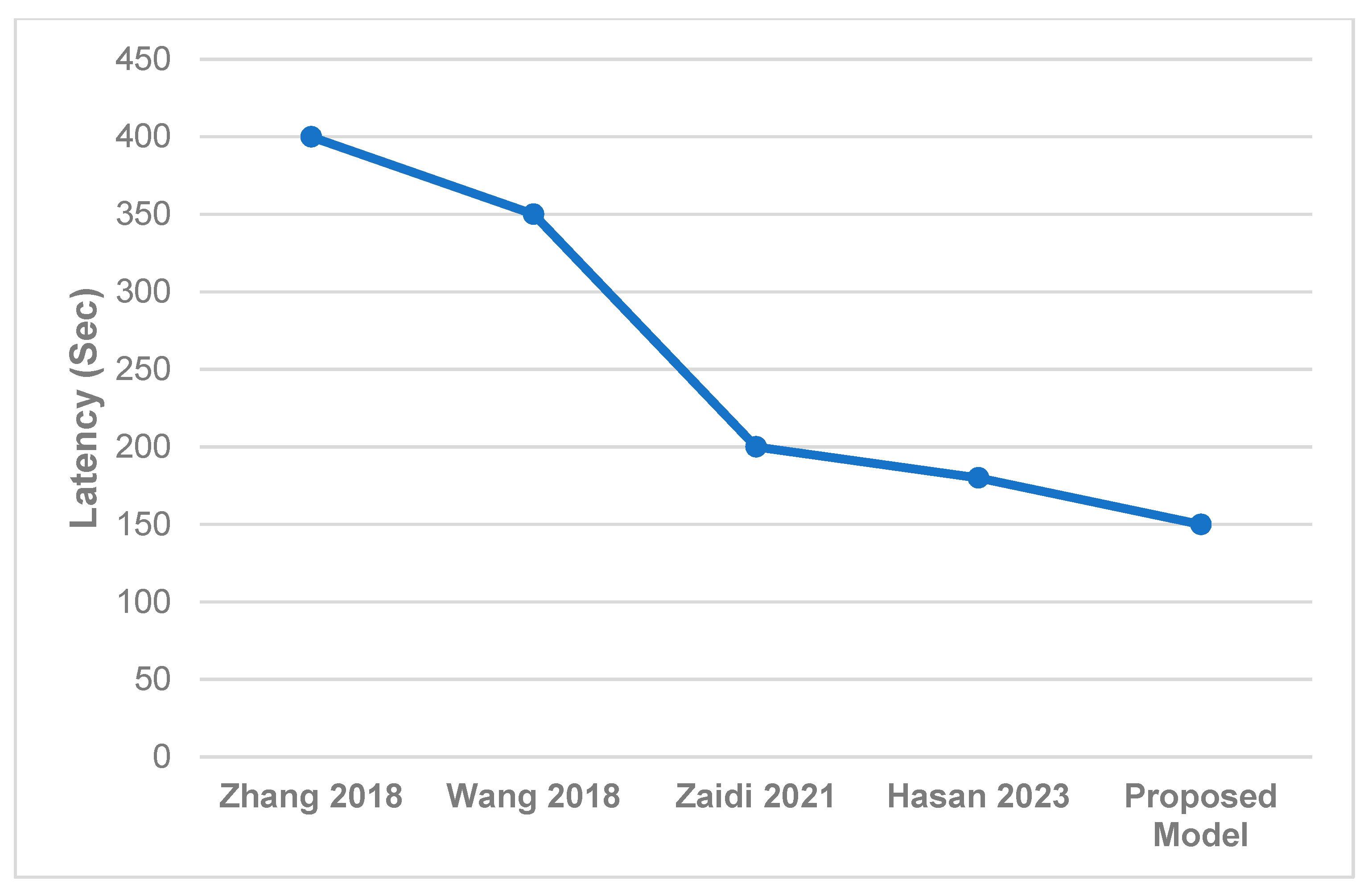
9. Performance Evaluation
10. Discussion
11. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| KYC | Know Your Customer |
| AC | Access Control |
| RSA | Rivest–Shamir–Adleman |
| AI | Artificial Intelligence |
| DAC | Dynamic Access Control |
| RBAC | Role-Based Access Control |
| ABAC | Attribute-Based Access Control |
| ABE | Attribute-Based Encryption |
| TS | Trust Score |
| ZTA | Zero-Trust Architecture |
| PEP | Policy Enforcement Point |
| PDP | Policy Decision Point |
| PAP | Policy Administration Point |
| PIP | Policy Information Point |
| DApps | Decentralized Applications |
| EVM | Ethereum Virtual Machine |
| UAC | User Attribute Contract |
| RAC | Resource Attribute Contract |
| DAC | Device Attribute Contract |
| CMC | Certificate Management Contract |
| APC | Access Policy Contract |
| ADC | Access Decision Contract |
| TEE | Trust Evaluation Engine |
| MFA | Multi-Factor Authentication |
| Kpub | Public Key |
| Kpriv | Private Key |
| Mdevice | Device Metadata |
| Tstamp | Timestamp |
| Sdevice | Sign Devices |
| Vdevice | Device Validation |
| CA | Certificate Authority |
| Cdevice | Device Digital Certificate |
| UDID | User Device Identifier |
| RTD | Real-Time Data |
| Mfinal | Final Metadata |
| TEF | Trust Evaluation Framework |
| Ti | Trust Identity |
| Tb | Trust Behavior |
| Tr | Trust Reliability |
| Ts | Trust Security |
| Th | Trust History |
| Te | Trust Energy Sensitivity Factor |
| TSmin | Static Threshold |
| Tmin | Minimum Threshold |
| Tbase | Base Threshold |
| DTR | Dynamic Trust Recalibration |
| SGC | Smart Grid Controller |
References
- Yarali, A. Intelligent Connectivity: AI, IoT, and 5G; John Wiley & Sons: Hoboken, NJ, USA, 2021. [Google Scholar]
- Vardakis, G.; Hatzivasilis, G.; Koutsaki, E.; Papadakis, N. Review of Smart-Home Security Using the Internet of Things. Electronics 2024, 13, 3343. [Google Scholar] [CrossRef]
- Buil-Gil, D.; Kemp, S.; Kuenzel, S.; Coventry, L.; Zakhary, S.; Tilley, D.; Nicholson, J. The digital harms of smart home devices: A systematic literature review. Comput. Hum. Behav. 2023, 145, 107770. [Google Scholar] [CrossRef]
- Tariq, U.; Ahmed, I.; Bashir, A.K.; Shaukat, K. A Critical Cybersecurity Analysis and Future Research Directions for the Internet of Things: A Comprehensive Review. Sensors 2023, 23, 4117. [Google Scholar] [CrossRef] [PubMed]
- Popoola, O.; Rodrigues, M.; Marchang, J.; Shenfield, A.; Ikpehai, A.; Popoola, J. A critical literature review of security and privacy in smart home healthcare schemes adopting IoT & blockchain: Problems, challenges and solutions. Blockchain Res. Appl. 2023, 5, 100178. [Google Scholar]
- Bharti, P.; Yadav, J.S. Attribute–Based Access Control for AWS Internet of Things—A Review. Int. J. Sci. Res. Sci. Technol. 2023, 10, 690–704. [Google Scholar]
- Ameer, S.; Benson, J.; Sandhu, R. Hybrid Approaches (ABAC and RBAC) Toward Secure Access Control in Smart Home IoT. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4032–4051. [Google Scholar] [CrossRef]
- Zhu, Y.; Wu, X.; Hu, Z. Fine grained access control based on smart contract for edge computing. Electronics 2022, 11, 167. [Google Scholar] [CrossRef]
- Rasori, M.; La Manna, M.; Perazzo, P.; Dini, G. A survey on attribute-based encryption schemes suitable for the internet of things. IEEE Internet Things J. 2022, 9, 8269–8290. [Google Scholar] [CrossRef]
- Punia, A.; Gulia, P.; Gill, N.S.; Ibeke, E.; Iwendi, C.; Shukla, P.K. A systematic review on blockchain-based access control systems in cloud environment. J. Cloud Comput. 2024, 13, 146. [Google Scholar] [CrossRef]
- Maesa DD, F.; Mori, P. Blockchain 3.0 applications survey. J. Parallel Distrib. Comput. 2020, 138, 99–114. [Google Scholar] [CrossRef]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart contract-based access control for the internet of things. IEEE Internet Things J. 2018, 6, 1594–1605. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, Y.; Zhang, Y. A blockchain-based framework for data sharing with fine-grained access control in decentralized storage systems. IEEE Access 2018, 6, 38437–38450. [Google Scholar] [CrossRef]
- Zaidi, S.Y.A.; Shah, M.A.; Khattak, H.A.; Maple, C.; Rauf, H.T.; El-Sherbeeny, A.M.; El-Meligy, M.A. An Attribute-Based Access Control for IoT Using Blockchain and Smart Contracts. Sustainability 2021, 13, 10556. [Google Scholar] [CrossRef]
- Hasan, M.; Diyan, T.; Syed, Y.A.Z.; Munam, A.S. TrustChain: A Decentralized and Lightweight Access Control Architecture Using Blockchain for IoT. Computers 2023, 12, 240. [Google Scholar] [CrossRef]
- Awan, S.M.; Azad, M.A.; Arshad, J.; Waheed, U.; Sharif, T. A Blockchain-Inspired Attribute-Based Zero-Trust Access Control Model for IoT. Information 2023, 14, 129. [Google Scholar] [CrossRef]
- Wang, J.; Zhu, M.; Li, M.; Sun, Y.; Tian, Z. An Access Control Method Against Unauthorized and Noncompliant Behaviors of Real-Time Data in Industrial IoT. IEEE Internet Things J. 2023, 11, 708–727. [Google Scholar] [CrossRef]
- Tan, L.; Shi, N.; Yu, K.; Aloqaily, M.; Jararweh, Y. A blockchain-empowered access control framework for smart devices in green internet of things. Internet Technol. 2021, 21, 1–20. [Google Scholar] [CrossRef]
- Omotunde, H.; Ahmed, M. A comprehensive review of security measures in database systems: Assessing authentication, access control, and beyond. Mesopotamian J. CyberSecurity 2023, 2023, 115–133. [Google Scholar] [CrossRef]
- Mandal, S.; Khan, D.A.; Jain, S. Cloud-based zero trust access control policy: An approach to support work-from-home driven by COVID-19 pandemic. N. Gener. Comput. 2021, 39, 599–622. [Google Scholar] [CrossRef]
- Syed, N.F.; Shah, S.W.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. Zero trust architecture (zta): A comprehensive survey. IEEE Access 2022, 10, 57143–57179. [Google Scholar] [CrossRef]
- Saha, S.; Chattaraj, D.; Bera, B.; Das, A.K. Consortium blockchain-enabled access control mechanism in edge computing based generic Internet of Things environment. Trans. Emerg. Telecommun. Technol. 2020, 32, e3995. [Google Scholar] [CrossRef]
- Khan, J.A. Role-Based access Control (RBAC) and Attribute-Based Access Control (ABAC). In Improving Security, Privacy, and Trust in Cloud Computing; IGI Global: Hershey, PA, USA, 2024; pp. 113–126. [Google Scholar]
- Penelova, M. Access control models. Cybern. Inf. Technol. 2021, 21, 77–104. [Google Scholar] [CrossRef]
- Belhadaoui, H.; Filali, R.; Malassé, O. A Role-Attribute Based Access Control Model for Dynamic Access Control in Hadoop Ecosystem. IAENG Int. J. Comput. Sci. 2023, 50, 13–24. [Google Scholar] [CrossRef]
- Zhang, X.; Jiang, X. IoT architecture based on ABAC smart contract. In Proceedings of the 2020 3rd International Conference on Advanced Electronic Materials, Computers and Software Engineering (AEMCSE), Shenzhen, China, 24–26 April 2020; pp. 122–128. [Google Scholar]
- Huang, Y. A Peer-to-Peer Access Control Infrastructure for IoT Systems with Efficient Blockchain Solutions. Ph.D. Dissertation, The University of Texas at Dallas, Richardson, TX, USA, 2024. [Google Scholar]
- Ragothaman, K.; Wang, Y.; Rimal, B.; Lawrence, M. Access control for IoT: A survey of existing research, dynamic policies and future directions. Sensors 2023, 23, 1805. [Google Scholar] [CrossRef]
- Mishra, R.K.; Yadav, R.K.; Nath, P. Access Control Models and Frameworks for the IoT Environment: Review, Challenges, and Future Direction. Wirel. Pers. Commun. 2024, 138, 1671–1701. [Google Scholar] [CrossRef]
- Cremonezi, B.; Vieira, A.B.; Nacif, J.; Silva, E.F.; Nogueira, M. Identity management for Internet of things: Concepts, challenges and opportunities. Comput. Commun. 2024, 224, 72–94. [Google Scholar] [CrossRef]
- Algarni, S.; Eassa, F.; Almarhabi, K.; Almalaise, A.; Albassam, E.; Alsubhi, K.; Yamin, M. Blockchain-Based Secured Access Control in an IoT System. Appl. Sci. 2021, 11, 1772. [Google Scholar] [CrossRef]
- Habib, G.; Sharma, S.; Ibrahim, S.; Ahmad, I.; Qureshi, S.; Ishfaq, M. Blockchain technology: Benefits, challenges, applications, and integration of blockchain technology with cloud computing. Futur. Internet 2022, 14, 341. [Google Scholar] [CrossRef]
- Sunyaev, A.; Sunyaev, A. Distributed ledger technology. In Internet Computing: Principles of Distributed Systems and Emerging Internet-Based Technologies; Springer: London, UK, 2020; pp. 265–299. [Google Scholar]
- Chen, X.; He, S.; Sun, L.; Zheng, Y.; Wu, C.Q. A survey of consortium blockchain and its applications. Cryptography 2024, 8, 12. [Google Scholar] [CrossRef]
- Oliva, G.A.; Hassan, A.E.; Jiang, Z.M. An exploratory study of smart contracts in the Ethereum blockchain platform. Empir. Softw. Eng. 2020, 25, 1864–1904. [Google Scholar] [CrossRef]
- Wu, K.; Ma, Y.; Huang, G.; Liu, X. A first look at blockchain-based decentralized applications. Softw. Pract. Exp. 2019, 51, 2033–2050. [Google Scholar] [CrossRef]
- Shammar, E.A.; Zahary, A.T.; Al-Shargabi, A.A. An attribute-based access control model for Internet of Things using hyperledger fabric blockchain. Wirel. Commun. Mob. Comput. 2022, 2022, 6926408. [Google Scholar] [CrossRef]
- Kurniawan, E.; Benda, D.; Sun, S.; Tan, S.G.; Chin, A. Blockchain for secure and transparent track-and-trace in manufacturing. In Implementing Industry 4.0: The Model Factory as the Key Enabler for the Future of Manufacturing; CARI Journals: Lewes, DE, USA, 2021; pp. 337–376. [Google Scholar]
- Shafik, W. Blockchain-based internet of things (B-IoT): Challenges, solutions, opportunities, open research questions, and future trends. In Blockchain-Based Internet of Things; Taylor & Francis: Abingdon, UK, 2024; pp. 35–58. [Google Scholar]
- Singh, S.; Hosen, A.S.M.S.; Yoon, B. Blockchain security attacks, challenges, and solutions for the future distributed iot network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- Dong, S.; Abbas, K.; Li, M.; Kamruzzaman, J. Blockchain technology and application: An overview. PeerJ Comput. Sci. 2023, 9, e1705. [Google Scholar] [CrossRef]
- Patil, P.; Sangeetha, M.; Bhaskar, V. Blockchain for IoT access control, security and privacy: A review. Wirel. Pers. Commun. 2020, 117, 1815–1834. [Google Scholar] [CrossRef]
- Asante, M.; Epiphaniou, G.; Maple, C.; Al-Khateeb, H.; Bottarelli, M.; Ghafoor, K.Z. Distributed ledger technologies in supply chain security management: A comprehensive survey. IEEE Trans. Eng. Manag. 2021, 70, 713–739. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E. Decentralized access control for IoT based on blockchain and smart contract. In Modeling and Design of Secure Internet of Things; Wiley: Hoboken, NJ, USA, 2020; pp. 505–528. [Google Scholar]
- Peng, K.; Li, M.; Huang, H.; Wang, C.; Wan, S.; Choo, K.-K.R. Security challenges and opportunities for smart contracts in Internet of Things: A survey. IEEE Internet Things J. 2021, 8, 12004–12020. [Google Scholar] [CrossRef]
- Adam, M.; Hammoudeh, M.; Alrawashdeh, R.; Alsulaimy, B. A survey on security, privacy, trust, and architectural challenges in IoT systems. IEEE Access 2024, 12, 57128–57149. [Google Scholar] [CrossRef]
- Muniswamy, A.; Rathi, R. Trust-Based Consensus and ABAC for Blockchain Using Deep Learning to Secure Internet of Things. Appl. Artif. Intell. 2025, 39, 2459461. [Google Scholar] [CrossRef]
- Hellani, H.; Sliman, L.; Samhat, A.E.; Exposito, E. On blockchain integration with supply chain: Overview on data transparency. Logistics 2021, 5, 46. [Google Scholar] [CrossRef]
- Esposito, C.; Ficco, M.; Gupta, B.B. Blockchain-based authentication and authorization for smart city applications. Inf. Process. Manag. 2021, 58, 102468. [Google Scholar] [CrossRef]
- Tomaz, A.E.B.; Nascimento, J.C.D.; Hafid, A.S.; De Souza, J.N. Preserving privacy in mobile health systems using non-interactive zero-knowledge proof and blockchain. IEEE Access 2020, 8, 204441–204458. [Google Scholar] [CrossRef]
- Shi, N.; Tan, L.; Yang, C.; He, C.; Xu, J.; Lu, Y.; Xu, H. BacS: A blockchain-based access control scheme in distributed internet of things. Peer-to-Peer Netw. Appl. 2020, 14, 2585–2599. [Google Scholar] [CrossRef]
- Sookhak, M.; Jabbarpour, M.R.; Safa, N.S.; Yu, F.R. Blockchain and smart contract for access control in healthcare: A survey, issues and challenges, and open issues. J. Netw. Comput. Appl. 2021, 178, 102950. [Google Scholar] [CrossRef]
- Dhar, S.; Bose, I. Securing IoT devices using zero trust and blockchain. J. Organ. Comput. Electron. Commer. 2021, 31, 18–34. [Google Scholar] [CrossRef]
- Tan, S.F.; Samsudin, A. Recent Technologies, Security Countermeasure and Ongoing Challenges of Industrial Internet of Things (IIoT): A Survey. Sensors 2021, 21, 6647. [Google Scholar] [CrossRef]
- Zhu, Y.; Qin, Y.; Gan, G.; Shuai, Y.; Chu, W.C.-C. TBAC: Transaction-based access control on blockchain for resource sharing with cryptographically decentralized authorization. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan, 23–27 July 2018; Volume 1, pp. 535–544. [Google Scholar]
- Butun, I.; Osterberg, P. A review of distributed access control for blockchain systems towards securing the internet of things. IEEE Access 2020, 9, 5428–5441. [Google Scholar] [CrossRef]
- Dharma Putra, G.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R.; Ignjatovic, A. Trust-based blockchain authorization for iot. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1646–1658. [Google Scholar] [CrossRef]
- Qi, S.; Lu, Y.; Wei, W.; Chen, X. Efficient data access control with fine-grained data protection in cloud-assisted IIoT. IEEE Internet Things J. 2020, 8, 2886–2899. [Google Scholar] [CrossRef]
- Iftekhar, A.; Cui, X.; Tao, Q.; Zheng, C. Hyperledger fabric access control system for internet of things layer in blockchain-based applications. Entropy 2021, 23, 1054. [Google Scholar] [CrossRef]
- Lyu, Q.; Qi, Y.; Zhang, X.; Liu, H.; Wang, Q.; Zheng, N. SBAC: A secure blockchain-based access control framework for information-centric networking. J. Netw. Comput. Appl. 2020, 149, 102444. [Google Scholar] [CrossRef]
- Banerjee, S.; Bera, B.; Das, A.K.; Chattopadhyay, S.; Khan, M.K.; Rodrigues, J.J. Private blockchain-envisioned multi-authority CP-ABE-based user access control scheme in IIoT. Comput. Commun. 2021, 169, 99–113. [Google Scholar] [CrossRef]
- Bera, B.; Saha, S.; Das, A.K.; Vasilakos, A.V. Designing blockchain-based access control protocol in iot-enabled smart-grid system. IEEE Internet Things J. 2020, 8, 5744–5761. [Google Scholar] [CrossRef]
- Ma, M.; Shi, G.; Li, F. Privacy-oriented blockchain-based distributed key management architecture for hierarchical access control in the IoT scenario. IEEE Access 2019, 7, 34045–34059. [Google Scholar] [CrossRef]
- Egala, B.S.; Pradhan, A.K.; Badarla, V.; Mohanty, S.P. Fortified-chain: A blockchain-based framework for security and privacy-assured internet of medical things with effective access control. IEEE Internet Things J. 2021, 8, 11717–11731. [Google Scholar] [CrossRef]
- Sun, S.; Du, R.; Chen, S.; Li, W. Blockchain-based IoT access control system: Towards security, lightweight, and cross-domain. IEEE Access 2021, 9, 36868–36878. [Google Scholar] [CrossRef]







| Model | Description | Security | Flexibility | Energy Efficiency |
|---|---|---|---|---|
| MAC | A centralized security model enforcing access permissions based on security classifications. | High | Low | Limited |
| DAC | A flexible model, where resource owners control access permissions. | Moderate | High | Low |
| RBAC | Access is role-based, simplifying management and enhancing security. | High | Moderate | Moderate |
| ABAC | A dynamic model granting access based on user, device, location, and time for fine-grained control. | High | High | High |
| Component | Description |
|---|---|
| Subject | The initiator of the access request, such as a user or process. |
| Resource | The target of the access request, which could be a file, process, IoT device, etc. |
| Authority | The actions that the subject is permitted to perform on the resources, like opening, reading, or deleting. |
| Environment | Contextual information provided by the subject during the access request, such as the time of the request or the geographical location of the subject and resource. |
| Reference | Approach Used | Blockchain Type | Key Features | Limitations |
|---|---|---|---|---|
| Smart Contract-Based Access Control | ||||
| Zhang et al. [12] | Smart contract-based AC model using blockchain | Public Blockchain (Ethereum) | Ensures transparency by using a public blockchain (Ethereum) with smart contract-based ABAC for decentralized IoT access control | Scalability and cost challenges due to Ethereum’s PoW consensus |
| Zaidi et al. [14] | ABAC model with smart contracts for IoT using multichain blockchain | Private Blockchain (Multichain) | Smart contract-based ABAC, PoA consensus, IPFS for data storage, attribute recording, tamper-resistance, improved scalability | Lacks trust dynamics, no real-time attribute updates, scalability limited by static policies |
| Hasan et al. [15] | Smart contract-based decentralized access control framework | Public Blockchain (Ethereum, Ropsten Testnet) | Three-stage architecture (initialization, ACP, inspection); policy enforcement via smart contracts, misuse detection, two-factor authentication, gas-cost analysis, Slither-based vulnerability testing | No support for dynamic attribute management, limited scalability testing, lacks integration with real-time IoT applications |
| Tomaz et al. [50] | Privacy-preserving healthcare using NIZKP and blockchain | Permissioned Blockchain | Non-interactive zero-knowledge proofs (NIZKPs), patient-controlled ABAC, ABE for secure data sharing, full patient data ownership | High complexity in authentication for constrained devices, less suitable for non-health IoT domains, lacks dynamic trust logic |
| Cryptographic-Based Access Control | ||||
| Wang et al. [13] | Hyperledger Fabric-based access for IoT | Permissioned Blockchain (Hyperledger Fabric) | Supports fine-grained access control for decentralized storage using CP-ABE and smart contracts | Lacks efficient key management for large-scale systems, affecting scalability |
| Shi et al. [51] | BacS: Blockchain-based access control for distributed IoT | Private Blockchain (Ethereum Private Chain) | Uses blockchain wallet address as identity, stores access control policies on-chain, implements symmetric encryption for privacy | High computational and storage overhead for small-scale IoT; lacks efficient retrieval methods |
| Sookhak et al. [52] | Blockchain-based access control for healthcare | Various Blockchain Types | Reviews 28 access control solutions, analyzes blockchain types, consensus mechanisms, and strategies | Scalability concerns, security risks in attribute revocation, privacy issues with outsourced data |
| Dhar et al. [53] | Zero-trust-based IoT security framework with blockchain | Private Blockchain | Risk-based segmentation, zero-trust architecture, device-level authentication, blockchain for access logs and trust extension, security guidelines | Lacks formal policy enforcement mechanism, no real-time trust recalibration, no fine-grained access control model |
| Latency and Scalability of Access Control | ||||
| Soo et al. [54] | Edge-based access control with Hyperledger Sawtooth | Permissioned Blockchain | Uses smart contracts, JSON-based policy storage, distributed trust model | High inconsistency in access time due to edge computing limitations |
| Zhu et al. [55] | TBAC: Transaction-based ABAC integrated with CryptoTBAC | Public Blockchain | Flexible permission management via transaction types, decentralized authorization, script-based policy logic, secure attribute exchange | Script-based logic adds complexity, lacks dynamic policy updates, no trust-based adaptation |
| Butun et al. [56] | Various distributed access control approaches | Permissioned | Threshold signature, reputation, trusted computing, identity, ACL, hybrid access control models | High energy use, processing delays, unsuitable for IoT |
| Putra et al. [57] | Decentralized ABAC with Trust and Reputation System (TRS) | Hybrid (Public + Private Sidechains) | Trust-based dynamic access control, recursive trust and reputation evaluation, TRS-based decision-making, privacy via sidechains | Complex trust evaluation logic, performance limitations on large-scale deployments, reliance on consistent trust feedback |
| Interoperability | ||||
| Qi et al. [58] | Fine-grained access control for cloud-assisted IIoT | Hybrid (Public and Private Cloud) | Uses CP-ABE encryption, hybrid cloud infrastructure, item-level data protection | High computational cost for CP-ABE, privacy risks from key authority compromise |
| Iftekhar et al. [59] | Hyperledger Fabric-based access control for IoT | Permissioned Blockchain (Hyperledger Fabric) | Implements attribute-based access control (ABAC), secure chaincode execution, integrates IoT devices | No runtime policy generation, high latency in policy updates, scalability issues |
| Lyu et al. [60] | SBAC: Blockchain-based access control for ICN | Private Blockchain | Hierarchical access via matching-based model, blockchain-based access tokens, Cuckoo filter for fast query, support for audit and revocation | Focused on ICN use-case, limited generalizability for broader IoT scenarios, complex token verification scheme |
| Smart GRID | ||||
| Banerjee et al. [61] | Multi-authority CP-ABE-based fine-grained access control for IIoT | Private Blockchain | Supports multiple attribute authorities, constant-size key and ciphertext, policy-hidden encryption, and outsourced computation | Lacks automation and keyword search over encrypted data |
| Bera et al. [62] | DBACP-IoTSG: Blockchain-based AC protocol for IoT-enabled smart grid | Private Blockchain | Uses voting-based PBFT consensus, secure smart meter data collection, leader-based block validation | High computation cost for cryptographic operations, scalability concerns |
| Ma et al. [63] | BDKMA: Blockchain-based distributed key management for hierarchical access control | Multi-Blockchain (Fog + Cloud) | Hierarchical key management, fog-assisted latency reduction, decentralized trust model, cross-domain access control, dynamic group authorization | High system complexity, trust challenges in inter-chain operations, limited real-time policy reactivity |
| Hybrid Blockchain Access Control | ||||
| Egala et al. [64] | Fortified Chain: Blockchain-based decentralized EHR with SRAC | Hybrid (Blockchain + IPFS) | Selective Ring-based access control (SRAC), hybrid edge–cloud model, smart contracts, IPFS-based distributed storage, privacy-preserving patient data management | Scalability challenges with large medical datasets, higher latency in hybrid operations, lacks dynamic policy tuning |
| Sun et al. [65] | Cross-domain ABAC system using permissioned blockchain (HLF) | Permissioned Blockchain (Hyperledger Fabric) | Identity-based signatures (IBSs), PDP selection algorithm, local ledgers per IoT domain, cross-domain access via channels, off-chain PDP decisions | Requires multiple domain configurations, higher setup complexity, potential performance bottlenecks in cross-domain coordination |
| Evaluation Criteria | Description | Effect on Trust Score | Smart Home Energy Context |
|---|---|---|---|
| Identity Authentication | Verifies device credentials, manufacturer details, firmware, and KYC compliance. | Trust rating improves upon successful authentication. Devices from verified manufacturers receive a higher initial trust score. | Smart meters, solar inverters, and HVAC systems must have manufacturer-issued energy certifications. |
| Behavior Monitoring | Tracks real-time actions and interactions of the device. | Trust score decreases if suspicious activity is detected (e.g., irregular data patterns, multiple failed access attempts). | Detects excessive energy usage anomalies, signaling potential misuse or unauthorized device access. |
| System Reliability | Measures device stability, including uptime, response speed, and error frequency. | Higher scores are assigned to devices with consistent performance. Trust rating drops if frequent failures or downtime occur. | Ensures HVAC, battery storage, and grid controllers maintain operational stability. |
| Security Adherence | Assesses firmware updates and compliance with security protocols. | Trust score decreases for outdated or unpatched firmware. Devices meeting security standards earn higher trust rating. | Smart home energy devices must comply with energy grid security protocols. |
| Energy Consumption Efficiency | Evaluates whether devices operate within expected energy limits. | Devices exceeding energy limits see a decrease in trust score. | Prevents overconsumption or inefficient energy device behavior. |
| Interaction History | Examines past access attempts, security breaches, and recalibrations. | Devices with frequent anomalies have lower trust; stable history increases trust. | A smart meter repeatedly accessed from multiple unauthorized locations gets flagged. |
| Grid Impact and External Factors | Analyzes manufacturer’s reputation and impact on the smart grid. | Poor reputation or past vulnerabilities reduce trust. | Devices interacting with the power grid require extra validation to prevent unauthorized power flow changes. |
| Evaluation Criteria | Description | Effect on Trust Score (TS) | Smart Home Energy Context |
|---|---|---|---|
| Identity Verification (Ti) | Ensures device and user credentials are validated through KYC and blockchain certificates. |
| Energy devices (e.g., smart meters, battery storage units) require a stricter identity verification. |
| Behavior Monitoring (Tb) | Tracks real-time activity, failed access attempts, and suspicious usage patterns. |
| If a solar inverter is accessed from an unregistered IP, TS drops immediately. |
| Device Reliability (Tr) | Measures uptime, failure frequency, and response times. |
| An HVAC system that fails frequently may be compromised and should be flagged. |
| Security Compliance (Ts) | Checks firmware updates, encryption status, and adherence to security policies. |
| Smart meters must meet energy security compliance to maintain access. |
| Historical Trust Score (Th) | Evaluates previous interactions and recalibrations. |
| Grid controllers with frequent unauthorized access attempts face a stricter TS recalibration. |
| Energy Sensitivity Factor (Te) | Considers device energy consumption and grid impact. |
| If an EV charger exceeds energy limits, the TS decreases dynamically. |
| Operation | Blockchain Platform | Description | Complexity (Big-O Notation) |
|---|---|---|---|
| Policy Retrieval | Hyperledger Fabric | Indexed lookup for attribute verification. | O(1) (constant time) |
| Trust Score Recalibration | Hyperledger Fabric | Iterates through predefined metrics to update scores. | O(n) (linear time) |
| Access Policy Enforcement | Hyperledger Besu | Policy validation via Merkle Patricia Trie lookup. | O(log n) (logarithmic time) |
| Operation | Blockchain Platform | Description | Complexity (Big-O Notation) |
|---|---|---|---|
| RSA-Based Authentication | Hyperledger Fabric/Besu | Constant-time cryptographic key validation. | O (1) |
| Attribute-Based Policy Evaluation | Hyperledger Fabric/Besu | Single attribute check in policy. | O (1) |
| Multiple Attribute Conditions (ABAC) | Hyperledger Fabric/Besu | Evaluates m conditions in an ABAC policy. | O(m) (depends on attributes) |
| Blockchain Logging and Transaction Finalization | Hyperledger Fabric | Uses world state model for transaction recording. | O(log n) (logarithmic time) |
| Attack Type | Impact on Access Control | Proposed Mitigation |
|---|---|---|
| Replay Attacks | Attackers resend intercepted access requests, bypassing authentication. | Timestamp and Nonce Mechanism: Ensures each request is unique. Immutable Logging: Fabric records prevent duplicate execution. |
| Man-in-the-Middle (MitM) Attacks | Unauthorized interception/modification of access requests or policies. | End-to-End Encryption: RSA for key exchange, SHA-256 for hashing. Hyperledger Fabric CA: Secure authentication of devices and users. |
| Collusion Attacks | Malicious users/devices share access to bypass policy enforcement. | Dynamic Trust-Based ABAC: Reduces trust scores of colluding users. Multi-Attribute Policy Enforcement: Fabric validates each access request. |
| Sybil Attacks | Attackers create multiple fake identities to manipulate access control decisions. | Blockchain Identity Verification: Hyperledger Fabric CA ensures unique, verifiable identities. Trust-Based Access Control: Prevents low-trust fake identities from gaining access. |
| Smart Contract Vulnerabilities | Exploiting bugs in smart contracts to bypass security checks. | Gas-Efficient Smart Contract Logic: Ensures strict input validation and execution constraints. Merkle Patricia Trie (MPT) in Besu: Prevents unauthorized state modifications. |
| Data Tampering and Unauthorized Access | Attackers modify stored attributes or policies to gain unauthorized access. | Immutable Blockchain Storage: Access policies and attributes stored in Fabric’s world state prevent tampering. Dynamic Trust Recalibration: Reduces access permissions for suspicious activity. |
| Reference | Comparison with Proposed Approach |
|---|---|
| Zhang et al. [12] | Dynamic ABAC model reduces gas costs, enhances scalability, and improves access control efficiency by offloading attribute management to Hyperledger Fabric, avoiding Ethereum’s PoW overhead |
| Wang et al. [13] | Dynamic ABAC model employs efficient trust recalibration, automated key updates, and cross-chain policy execution, thereby enhancing scalability, flexibility, and computational efficiency |
| Zaidi et al. [14] | Dynamic ABAC model enhances real-time ABAC, introduces dynamic trust recalibration, and supports automated policy updates for better IoT scalability and adaptability |
| Hasan et al. [15] | Dynamic ABAC model ensures enhanced trust recalibration, real-time context-aware access enforcement, and hybrid blockchain scalability for smart home energy systems |
| Tomaz et al. [50] | Dynamic ABAC model offers lightweight authentication and cross-domain ABAC, with real-time policy updates for diverse IoT environments |
| Shi et al. [51] | Dynamic ABAC model optimizes computational efficiency and introduces real-time trust recalibration for adaptive policy enforcement |
| Sookhak et al. [52] | Dynamic ABAC model improves scalability using distributed trust recalibration and dynamic policy updates |
| Dhar et al. [53] | Dynamic ABAC model implements attribute-driven policies with real-time trust adjustment, enabling fine-grained ABAC and reducing reliance on fixed segmentation |
| Soo et al. [54] | Dynamic ABAC model ensures consistent access times using hybrid on-chain/off-chain architecture |
| Zhu et al. [55] | Dynamic ABAC model simplifies policy enforcement via smart contracts, supports real-time dynamic trust, and avoids overhead of cryptographic scripting by using efficient attribute-policy binding |
| Butun et al. [56] | Dynamic ABAC model improves efficiency with hybrid blockchain and dynamic trust recalibration |
| Putra et al. [57] | Dynamic ABAC model simplifies trust computation with lightweight dynamic scoring and integrates adaptive onboarding for improved performance at scale |
| Qi et al. [58] | Dynamic ABAC model reduces computational overhead with efficient hybrid blockchain-based policy enforcement |
| Iftekhar et al. [59] | Dynamic ABAC model enables real-time policy adaptation and dynamic trust recalibration to improve access control efficiency |
| Lyu et al. [60] | Dynamic ABAC model supports general-purpose IoT, enhances policy flexibility, and reduces verification overhead with streamlined access evaluation and trust update logic |
| Banerjee et al. [61] | Dynamic ABAC model introduces automated policy enforcement and real-time attribute updates |
| Bera et al. [62] | Dynamic ABAC model optimizes computation efficiency and enhances scalability with dynamic trust recalibration |
| Ma et al. [63] | Dynamic ABAC model streamlines hierarchical access via trust-based dynamic ABAC, supports faster policy updates, and minimizes multichain complexity with integrated hybrid blockchain design |
| Egala et al. [64] | Dynamic ABAC model enhances scalability using dynamic trust recalibration, supports real-time access policy adaptation, and reduces latency with efficient hybrid deployment |
| Sun et al. [65] | Dynamic ABAC model simplifies cross-domain integration with unified dynamic policy control and enhances scalability using a lightweight trust recalibration mechanism |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Waheed, U.; Khan, S.A.; Masud, M.; Jamshed, H.; Jumani, T.A.; Malik, N.U.R. Blockchain-Based, Dynamic Attribute-Based Access Control for Smart Home Energy Systems. Energies 2025, 18, 1973. https://doi.org/10.3390/en18081973
Waheed U, Khan SA, Masud M, Jamshed H, Jumani TA, Malik NUR. Blockchain-Based, Dynamic Attribute-Based Access Control for Smart Home Energy Systems. Energies. 2025; 18(8):1973. https://doi.org/10.3390/en18081973
Chicago/Turabian StyleWaheed, Urooj, Sadiq Ali Khan, Muhammad Masud, Huma Jamshed, Touqeer Ahmed Jumani, and Najeeb Ur Rehman Malik. 2025. "Blockchain-Based, Dynamic Attribute-Based Access Control for Smart Home Energy Systems" Energies 18, no. 8: 1973. https://doi.org/10.3390/en18081973
APA StyleWaheed, U., Khan, S. A., Masud, M., Jamshed, H., Jumani, T. A., & Malik, N. U. R. (2025). Blockchain-Based, Dynamic Attribute-Based Access Control for Smart Home Energy Systems. Energies, 18(8), 1973. https://doi.org/10.3390/en18081973