1. Introduction
Critical energy infrastructures (CEIs) are essential for economic and social development, ensuring the continuous supply of energy to key sectors such as transportation, healthcare, communications, and industry. Over the past decade, these systems have undergone a significant transformation driven by increasing demand, the depletion of conventional energy sources, and inefficiencies in energy distribution. Innovations such as smart grids and the Internet of Energy (IoE) have emerged, promoting decentralization, distributed storage, and intelligent energy management through information and communication technologies (ICTs) [
1]. However, this modernization has also increased the vulnerability of CEIs to cyber threats by expanding the attack surface and making them prime targets for adversaries seeking to disrupt operations. Ensuring cybersecurity in these infrastructures is critical to maintaining operational continuity and preventing serious economic and societal consequences, especially in a constantly evolving threat landscape that demands proactive and resilient approaches.
Cybersecurity in critical energy infrastructures (CEI) is becoming increasingly essential in an environment characterized by growing interconnectivity and reliance on advanced technologies. The integration of ICT into industrial control systems has improved operational efficiency but has also significantly heightened exposure to cyberattacks with potentially devastating impacts on national and economic security. Notable incidents such as the cyberattacks on Ukraine’s power grid (2015 and 2016) and the Colonial Pipeline (2021) underscore the severe consequences of such threats. Recent reports reveal that 90% of organizations using industrial control systems (ICS) have experienced security breaches, with data theft being the most pressing concern [
2]. Moreover, economic losses from these attacks amount to hundreds of millions of dollars annually [
3]. Emerging technologies such as smart grids and the IoE have broadened the attack surface, making systems more susceptible to sophisticated threats. In this context, the adoption of advanced cybersecurity strategies—such as artificial intelligence (AI), machine learning (ML), and zero-trust architectures—is crucial for real-time anomaly detection, proactive incident response, and ensuring operational resilience. Coordinated efforts among governments, organizations, and industry stakeholders are essential to mitigate risks and protect these critical infrastructures in the face of increasingly complex threats.
The convergence of information technologies (IT) and operational technologies (OT) in CEIs has transformed the cybersecurity landscape by integrating traditionally isolated systems into interconnected networks. IT-OT cybersecurity models aim to ensure operational resilience against cyber threats through innovative approaches. For instance, the hierarchical cyber-physical security model structures protection layers to detect and mitigate vulnerabilities in SCADA networks [
4]. Similarly, blockchain-based models ensure data integrity in critical transactions, reinforcing the protection of substations against denial-of-service attacks [
5]. Another important approach is the Software-Defined Networking (SDN) model, which dynamically segments traffic between IT and OT networks, optimizing real-time threat detection [
6]. Additionally, hybrid models that combine predictive analytics and machine learning enable the simulation of attacks and the evaluation of mitigation strategies in critical environments [
7].
Key dimensions of IT-OT cybersecurity models include services, technical means, facilities, and algorithms. In terms of services, federated learning enhances distributed anomaly detection while preserving data privacy across energy networks [
8]. Centralized monitoring platforms also support efficient incident management through predictive analytics [
9]. Regarding technical means, edge computing technologies have significantly improved local threat detection capabilities by reducing response latency [
6]. Moreover, advanced sensors with secure protocols have increased the resilience of smart grids [
10].
Critical facilities such as substations and smart grids have adopted blockchain technologies to ensure data integrity and operational security [
11]. Hierarchical impact assessment models have also been applied to mitigate risks in SCADA systems [
12]. Finally, advanced algorithms have revolutionized threat detection. Deep neural networks and autoencoders can identify anomalous patterns in imbalanced dataset, while metaheuristic optimization algorithms offer efficient solutions for real-time cyberattack mitigation [
13].
The convergence of IT-OT and artificial intelligence (AI) in CEIs has redefined the cybersecurity landscape, demanding models that comprehensively address vulnerabilities across services, technical infrastructure, facilities, and algorithms. Regarding services, intrusion detection and prevention systems (IDS/IPS) have significantly evolved through deep learning integration, enabling threat prioritization and real-time incident response [
7,
14]. For technical infrastructure, edge and fog computing technologies have enhanced responsiveness by processing data close to the source, reducing latency and enabling efficient monitoring in SCADA systems and smart grids [
6,
15]. As for facilities, substations and electric grids have implemented blockchain to ensure data integrity and defend against targeted cyberattacks, minimizing operational impact [
4,
11]. In terms of algorithms, deep neural networks and autoencoders have improved anomaly detection in complex datasets, bolstering protection against emerging and sophisticated threats [
16]. Within this context, the research question emerges: How have IT-OT cybersecurity models for critical energy infrastructures evolved between 2015 and 2024? Addressing this question is essential to understanding how IT-OT integration has enhanced cybersecurity capabilities, improved attack prevention, and ensured operational continuity throughout this period.
The aim of this study is to analyze the evolution of AI-enhanced IT-OT cybersecurity models in the CEI sector from 2015 to 2024, with the objective of identifying key achievements and remaining challenges. This analysis will provide critical infrastructure security managers and operators with clear guidance on how to optimize their cybersecurity strategies in response to emerging threats, thereby strengthening the protection of vital systems. Furthermore, this study will offer researchers in the cybersecurity field a fresh perspective on the evolution of IT-OT models, serving as a solid foundation for future research and the development of novel defense approaches for critical infrastructures.
The main contributions of this article are: (a) to provide an overview of IT-OT cybersecurity models, detailing their concepts, classifications, and relevance in protecting critical energy infrastructure, along with key dimensions of analysis; (b) to offer an exhaustive inventory of models and technologies implemented in the energy sector to enhance cybersecurity, spanning from traditional solutions to emerging technologies such as AI and blockchain; and (c) to highlight the evolution of OT models from 2015 to 2024, emphasizing the major advances in defense mechanisms against cyber threats and how these strategies have enhanced the resilience of critical infrastructures.
This article is structured into six sections.
Section 2 reviews cybersecurity in critical energy infrastructures.
Section 3 presents a systematic review of OT cybersecurity models in CEIs.
Section 4 analyzes the evolution of OT models from 2015 to 2024, identifying key advances and achievements. Finally,
Section 5 and
Section 6 discuss the findings and present the conclusions of the study, respectively.
3. Systematic Review of IT-OT Cybersecurity Models in CEIs
This section presents a systematic literature review on IT-OT cybersecurity models applied to critical energy infrastructures (CEIs), following a four-phase methodology encompassing planning, execution, results, and analysis.
3.1. Methodology
The methodology for the systematic literature review (SLR) was based on an adaptation of the guidelines proposed by Kitchenham & Charters (2007), structured into four phases. This methodology has been applied in various reviews related to CEI cybersecurity, including those by [
22,
23,
24,
25,
26,
27]. The phases are described as follows:
- A.
Planning: This phase establishes the research questions and the search and selection protocol, which includes journal sources, search period, search strings, and inclusion and exclusion criteria.
- B.
Execution: The search protocol is applied, and articles are selected to answer the research questions.
- C.
Results: Statistical data are compiled and presented regarding the selected studies, including publication trends, quality, and distribution.
- D.
Analysis: The research questions defined in the planning phase are answered based on the selected literature.
3.2. Planning
To investigate how cybersecurity models for CEIs have evolved, the following research questions (RQs) were formulated:
RQ1: What types of CEI cybersecurity models exist?
RQ2: What energy services are addressed by these models?
RQ3: What technical means are considered in these models?
RQ4: What types of facilities are protected by these models?
RQ5: What algorithms are integrated into these models?
To answer these questions, scientific journal articles were retrieved from the following academic databases: Scopus, Web of Science (WoS), IEEE Xplore, and MDPI. The review covered the period from January 2015 to June 2024, beginning with 2015 as it marks the emergence of the first CEI cybersecurity models. The search string used was: [(model OR “operational technology”) AND cybersecurity AND “artificial intelligence”]. This string was applied to the following fields: “Title-Abs-Key” for Scopus, “Topic” for WoS, “ALL” for IEEE Xplore, and “Title/Keyword” for MDPI. The syntax of the string was adapted as necessary for each database’s search engine. Once the articles were retrieved, inclusion and exclusion criteria were applied, as defined in
Table 1.
3.3. Execution
The primary studies identified as potential references during the search process were selected based on the inclusion and exclusion criteria defined earlier. It was essential to review the content of these potential references to assess their relevance to the present study and, specifically, to determine whether they addressed models applicable to CEIs. Most articles were excluded for being outside the scope of this research—for instance, focusing on cybersecurity in generic enterprise networks, assessing vulnerabilities in consumer IoT devices, or addressing unrelated topics such as personal data privacy.
The search protocol defined during the planning phase initially identified 1693 primary studies, distributed as follows: 1195 from Scopus, 382 from Web of Science (WoS), 65 from IEEE Xplore, and 51 from MDPI. During the selection process and following the inclusion and exclusion criteria, an initial filtering by title yielded 299 articles. A second screening based on abstracts reduced the number to 98 articles. Subsequently, a detailed review of introductions and conclusions led to the selection of 71 articles. Finally, after a full-text review, 52 articles were retained. This selection process is illustrated in
Figure 2, and the selected articles are listed in Column 4 of
Table 2.
Table A1 in
Appendix A presents the basic information and identification of the 52 selected articles [
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18,
19,
28,
29,
30,
31,
32,
33,
34,
35,
36,
37,
38,
39,
40,
41,
42,
43,
44,
45,
46,
47,
48,
49,
50,
51,
52,
53,
54,
55,
56,
57,
58,
59,
60,
61,
62], from [R01] to [R52].
3.4. Results
3.4.1. Potential Articles
A total of 1693 potential articles were identified through the search process, from which 52 studies were selected. These represent approximately 3% of the total and are presented in
Table 2.
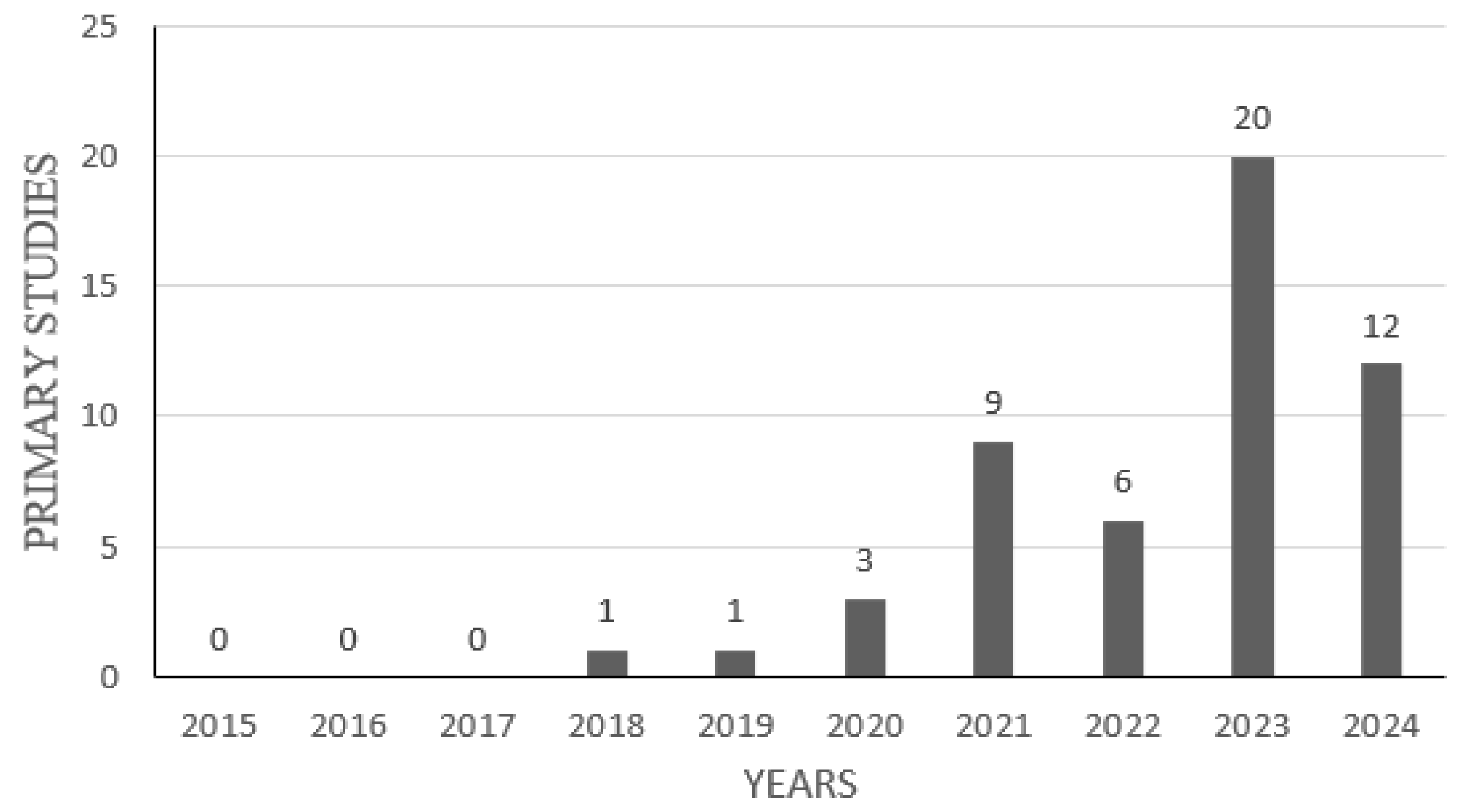
3.4.2. Publication Trends
Figure 3 illustrates a consistent increase in the number of published articles addressing CEI cybersecurity models over the period 2018 to 2024. This upward trend likely reflects the growing recognition among researchers and professionals of the importance of modeling and cybersecurity in critical infrastructures, particularly within the energy sector. Furthermore, as shown in
Figure 2, the first relevant study in this domain appeared in 2018.
3.4.3. Journals and Articles by Quartile
Figure 4 presents the journals in which the selected articles were published, indicating their respective quartile rankings and the number of articles per journal. The most prominent journals are IEEE Access and the Internet of Things Journal, with six and four articles, respectively. Additionally, 25 journals were grouped under the category “Others,” each contributing one selected article. In total, 34 journals were represented: 24 in Q1, 5 in Q2, 4 in Q3, and 1 in Q4.
With respect to the quality ranking of the journals, 71% (37) of the selected articles were published in Q1 journals, and 17% (9) in Q2 journals, meaning that 88% of the studies were published in top-tier journals (Q1 and Q2) (see
Figure 5). This highlights the high quality of the selected studies. Additionally, 2% of the articles fall into a separate category, representing non-indexed publications (brown segment).
3.4.4. Study Classification
Table 3 presents the classification of the 52 selected studies according to the five analytical dimensions, which correspond directly to the research questions. It is important to note that several studies contribute to more than one category. As observed, 25% of the studies focus on algorithms for CEI cybersecurity, while 23% of the studies pertain to each of the following dimensions: services, technical means, and facilities. This indicates a relatively balanced interest across all five-research dimensions.
Appendix A provides a comprehensive overview of the 52 selected articles, as presented in
Table A1. This appendix serves to link each article’s unique identifier (ID) to its corresponding reference number, ensuring traceability between the list of analyzed studies and the reference list [R01] to [R52].
3.5. Analysis
This section addresses the research questions formulated in
Section 3.2, based on the selected studies.
The selected studies did not identify a standardized taxonomy for CEI cybersecurity models. However, the influential book by [
1] provides a foundational framework for understanding CEI cybersecurity, highlighting key elements such as the relevance of international standards (ISO/IEC and NIST), inter-institutional collaboration, and risk management, which may contribute to building a comprehensive taxonomy. Developing a robust classification system is essential to facilitate systematic analysis and conceptual clarity. Accordingly, this study proposes a new taxonomy for CEI cybersecurity models. It consists of seven categories, which incorporate the most relevant and current approaches in the field. This taxonomy provides a structured basis for future research and practical applications and is detailed in
Table 4.
Beyond the descriptive taxonomy, a comparative analysis reveals key differences among the seven categories of models. Detection and prediction models are highly applicable in practice due to their integration with SCADA and smart grid environments, but their scalability depends strongly on computational resources. Risk management and standards-based models demonstrate high maturity, as they are widely adopted in regulatory frameworks, yet their applicability can be limited by regional compliance requirements. Collaborative and information-sharing models remain less mature, facing challenges of interoperability and trust, while architecture-based protection and simulation models offer strong scalability potential but are still underexplored in real deployments. This comparison highlights how applicability, scalability, and maturity vary across categories, providing guidance for selecting models aligned with specific operational needs.
The proposed taxonomy, which organizes cybersecurity models into seven categories, is based on the following rationale. First, it provides comprehensive coverage by addressing technical, organizational, and regulatory aspects—from threat detection to operational resilience. Second, it enables specific and in-depth analysis within each category. Finally, it combines theoretical rigor with clear practical applications, making it valuable to researchers, industry professionals, and policymakers by incorporating standards, compliance frameworks, and collaborative models.
3.5.1. Detection, Prediction, and Explanation Models
A total of 16 models were identified across 49 studies, distributed among three subcategories: 8 detection models, cited in 32 studies, 4 prediction models, appearing in 16 studies, and 4 explanation models, also in 16 studies. Detection models primarily focus on identifying intrusions and anomalies; prediction models aim to anticipate cyber threats; and explanation models seek to justify system decisions, enhancing transparency and trust.
Table 5 details the characteristics of each model. It is worth noting that some studies apply more than one type of model.
3.5.2. Risk Management Models
A total of six risk management models were identified across 18 studies, each applied to a distinct case study. These models are described in
Table 6.
3.5.3. Standards-Based Models
A total of five models categorized under standards and compliance were identified across 15 studies, each corresponding to a distinct use case. These models are detailed in
Table 7.
3.5.4. Collaborative and Information Sharing Models
A total of five models within the category of collaborative or information-sharing frameworks were identified across 15 studies, each corresponding to a distinct case. These models are presented in
Table 8.
3.5.5. Incident Response and Recovery Models
A total of five models were identified within the incident response and recovery category, across 10 studies. The most referenced approach involves digital twins used to simulate and recover OT systems following cyberattacks. These models are detailed in
Table 9.
3.5.6. System Architecture-Based Protection Models
A total of five models in this category were identified across 18 studies. The most frequently referenced are those designed to secure SCADA and IoT environments against cyber threats. These models are detailed in
Table 10.
3.5.7. Simulation and Testing Models
A total of seven models were identified in the simulation and testing category, across 17 studies. This group highlights the development of novel techniques, ranging from cyberattack simulation to self-healing networks. These models are described in
Table 11.
Analyzing CEI cybersecurity models requires identifying the energy services they address, which allows for assessing the scope of their protection strategies and identifying potential security gaps. Based on a systematic review of 52 scientific articles, 10 key services have been identified in 41 models.
Table 12 presents this classification, offering a structured view of how these models contribute to safeguarding the energy sector against cyber threats.
Critical energy infrastructures (CEIs) rely on diverse technical components for monitoring, communication, protection, and resilience against cyber threats. The increasing digitalization and IT-OT convergence have expanded the attack surface, requiring advanced solutions such as SCADA, IoT, blockchain, data analytics, and artificial intelligence. To mitigate these risks, CEI cybersecurity models have incorporated technologies enabling incident detection, response, and recovery in energy systems.
Table 13 presents a classification of six key technical means identified across 29 models.
Critical energy infrastructures (CEIs) rely on a set of strategic facilities that ensure the generation, transmission, distribution, storage, and secure management of energy. The increasing digitalization and IT-OT convergence have enhanced operational efficiency but also expanded the attack surface, exposing these facilities to advanced cyber threats targeting their supervisory and control systems. Ensuring operational continuity and resilience against these risks requires cybersecurity models tailored to the specific characteristics and vulnerabilities of each type of facility. In this context,
Table 14 presents 10 types of facilities addressed across 42 models.
Analyzing CEI cybersecurity models requires identifying the algorithms employed in their implementation—particularly those related to Operational Technology (OT) in cybersecurity contexts. These algorithms play a central role in threat detection, prediction, and response, enabling models to adapt dynamically to emerging threats and optimize defensive capabilities.
Table 15 presents a detailed mapping of the most frequently used algorithms in CEI models, including their application across energy services, technical means, and infrastructure facilities.
5. Discussion
The systematic literature review and the analysis of the evolution of CEIC models from 2015 to 2024 have revealed key trends, technological advances, and areas of opportunity within the field of Critical Energy Infrastructure Cybersecurity (CEIC). The following subsections discuss the most relevant findings, their significance, and their implications for future research and practical applications.
5.1. Evolution of CEIC Models
The temporal analysis of CEIC models in the energy sector reveals a clear trend toward the adoption of advanced technologies—such as Artificial Intelligence (AI), Machine Learning (ML), and blockchain—to counter increasingly sophisticated cyber threats. During the early years of the analyzed period (2015–2017), most models focused primarily on intrusion detection and risk management, relying on standards such as NIST and IEC 62443. However, since 2018, there has been a significant rise in the incorporation of AI and ML techniques for anomaly detection, threat prediction, and explainable decision-making (XAI). This shift reflects the pressing need to adapt to more dynamic and sophisticated threats, such as zero-day exploits and Advanced Persistent Threats (APTs).
The integration of AI- and ML-based models has enabled greater accuracy in intrusion and anomaly detection, as well as enhanced capabilities for real-time risk prediction and mitigation. For instance, Deep Learning Intrusion Detection Systems (DL-IDS) and anomaly detection systems using autoencoders have proven effective in identifying abnormal patterns in OT networks. Furthermore, the incorporation of Explainable AI (XAI) has improved the transparency and trustworthiness of cybersecurity systems, which is essential for their adoption in critical environments.
To further illustrate the practical implications of the reviewed models and their relevance in real-world contexts, this section presents two case studies of energy infrastructures that have faced significant cyber incidents. These cases highlight how different cybersecurity approaches—ranging from AI-enhanced intrusion detection to blockchain-based integrity mechanisms—have been applied or considered to strengthen resilience against advanced threats.
Case Study 1: The cyberattacks on Ukraine’s power grid in 2015 and 2016 represent a milestone in the application of OT cybersecurity models. Intrusion detection systems based on deep learning were tested to analyze abnormal patterns in SCADA communications. These models demonstrated the importance of adaptive anomaly detection for ensuring continuity of electricity supply under conditions of persistent advanced threats.
Case Study 2: The Colonial Pipeline incident in 2021 highlighted the role of blockchain-based integrity models for securing industrial control and billing systems. The attack disrupted fuel distribution across the eastern United States, and subsequent resilience measures emphasized the application of decentralized ledgers to guarantee the immutability and traceability of operational data in critical infrastructures.
5.2. Services, Technical Means, and Facilities
Regarding energy services, CEIC models have evolved to cover a broader range of applications—from energy generation and transmission to demand-side management and operational resilience. Energy generation and transmission services remain the most studied areas, reflecting their critical importance within the energy infrastructure. However, there has also been a notable increase in attention to services such as energy storage and Smart Grids, which are becoming more vulnerable to cyberattacks due to ongoing digitalization.
In terms of technical means, control and supervision systems (SCADA/ICS) and communication networks have been the primary focus of cybersecurity models. These systems form the operational core of critical infrastructures and are prime targets for cyber threats. The incorporation of technologies such as blockchain and microsegmentation has enhanced the security of these systems by reducing the attack surface and increasing resilience against intrusions.
As for facilities, power generation plants and transmission substations have received the most protection in CEIC models. Nonetheless, there is growing interest in securing facilities such as operations control centers and smart metering systems, which are essential for continuous energy delivery and billing services.
In energy-specific scenarios, OT cybersecurity models demonstrate different levels of maturity and applicability. For instance, intrusion detection systems (IDS) based on deep learning have shown high effectiveness in power grids, where the complexity of SCADA traffic requires adaptive anomaly detection. In natural gas pipelines, blockchain-based integrity mechanisms are increasingly applied to protect transaction data and operational flows, while federated learning supports distributed monitoring without exposing sensitive information. Smart meters, on the other hand, remain highly vulnerable to fraud and data manipulation, and require lightweight AI-enhanced models capable of real-time authentication and anomaly detection.
5.3. Algorithms and Their Impact on OT Cybersecurity
Algorithms have played a pivotal role in the evolution of cybersecurity models for Operational Technology (OT). Techniques based on Convolutional Neural Networks (CNNs), Recurrent Neural Networks (RNNs), and Deep Reinforcement Learning (DRL) have proven effective in the detection and prediction of threats. Additionally, the adoption of Federated Learning (FL) approaches has enhanced privacy and security in data exchange between entities—an essential requirement in critical infrastructure environments where inter-organizational collaboration is crucial.
The integration of Explainable Artificial Intelligence (XAI) algorithms, such as SHAP and LIME, has enabled operators of critical infrastructure to better understand the decisions made by cybersecurity systems, thus increasing trust in these technologies. Moreover, the use of blockchain has significantly improved data integrity and traceability within OT environments—an especially important feature in settings where data tampering can have catastrophic consequences.
The adoption of these models varies considerably across regions. In Europe, cybersecurity frameworks such as ENISA and IEC 62443 have facilitated the deployment of standardized models, particularly in smart grid projects. North America, by contrast, shows a strong reliance on NIST-based approaches and sector-specific regulations such as NERC CIP. In Latin America, although progress has been made in implementing AI-based models in pilot projects, the lack of harmonized regulations and limited investment in OT security create significant barriers to large-scale adoption. This regional disparity highlights the importance of developing flexible models that adapt to local regulatory and economic contexts.
5.4. Integral Relationship Between Models, Services, Technical Means, Facilities, and Algorithms in CEIC
Cybersecurity in Critical Energy Infrastructure (CEIC) requires a systemic integration across models, services, technical means, physical facilities, and algorithms. This study demonstrates that cybersecurity models—such as those focused on threat detection, risk management, or attack simulation—are closely tied to essential energy services (generation, storage, distribution). These models are implemented through enabling technologies such as SCADA, Edge/Fog Computing, and threat prediction platforms.
These technologies are deployed within critical facilities (power plants, substations, control centers), which are often the primary targets of cyberattacks. The entire cybersecurity ecosystem is enhanced by advanced algorithms (CNN, RNN, XAI, blockchain) that automate decision-making and strengthen incident response capabilities.
Figure 10 illustrates this interrelational cybersecurity framework. Initially, a client or attacker initiates a transaction. This transaction is analyzed by the CEIC model, which determines whether it constitutes a cyberattack. If an attack is detected, the transaction is blocked and the event is logged for future model updates. If the transaction is deemed legitimate, it proceeds through the corresponding services, technical means, and facilities. This scheme represents a holistic, adaptive, and resilient defense architecture against evolving threats.
Finally,
Table 17 integrates the CEIC models for detection, mitigation, and recovery from cyberattacks, along with their corresponding services, technical means, facilities, and algorithms. This relationship helps to understand how each model adapts to different operational and protection scenarios (categories and subcategories), facilitating the assessment of their effectiveness in safeguarding critical energy infrastructures.
Ultimately, the link between OT cybersecurity models and the future energy transition is crucial. As renewable generation (solar, wind) and emerging hydrogen energy systems expand, the attack surface of CEIs will grow significantly due to the high number of distributed assets and interconnections. The analyzed models provide a foundation for ensuring resilience in these future systems, but they must evolve toward quantum-resilient encryption, lightweight AI algorithms for resource-constrained devices, and cross-sector collaboration to support a secure, decarbonized energy ecosystem.
6. Conclusions
This study presents a systematic and categorized review of 49 cybersecurity models applied to Critical Energy Infrastructures (CEICs), aiming to provide a comprehensive framework for the selection and implementation of protection strategies. Through a rigorous process of review, classification, and analysis, the models were organized into seven core categories: detection, prediction, and explanation (16); risk management (6); standards and regulatory frameworks (5); collaboration and information sharing (5); response and recovery (5); system architecture-based protection (5); and simulation and testing (7). These models are associated with 10 essential services within the energy infrastructure—such as power generation, transmission, and distribution—and encompass critical facilities like generation plants, substations, and control centers. One of the most significant findings is the increasing incorporation of technologies such as artificial intelligence (AI), machine learning (ML), and blockchain, which have substantially enhanced real-time threat detection, prediction, and mitigation capabilities. Unlike previous reviews, this study provides a structured organization around five analytical dimensions—services, technical means, facilities, algorithms, and temporal evolution—offering a more integrated view of the CEIC cybersecurity ecosystem. This structure facilitates adaptation to specific needs and enhances applicability in real operational contexts.
This study provides concrete answers to the five research questions posed regarding CEIC models. First, 49 distinct models were identified, evidencing a significant evolution over the past decade—from isolated and reactive approaches to integrated cybersecurity architectures—organized into seven functional categories. Among these, threat detection models have shown prominent development toward hybrid, intelligent, and adaptive solutions. Second, regarding the protected energy services, the scope of models has evolved from a generation-centric focus to a broader approach that includes transmission, distribution, smart grids, and storage systems—reflecting the sector’s digital transformation. Third, in terms of technical means, the field has shifted from a heavy reliance on legacy SCADA systems toward the progressive incorporation of emerging technologies, such as edge computing, fog computing, and encrypted communication protocols, enabling more robust real-time security and resilience. Fourth, concerning critical facilities, cybersecurity efforts have expanded from traditional protection of power generation plants to a systemic view that includes automated substations and intelligent control centers, addressing the rise in attack vectors across the entire energy value chain. Fifth, in the domain of algorithms, a clear transition was observed—from traditional methods to advanced AI techniques—with a growing emphasis on deep learning and, more recently, federated learning, significantly improving proactive threat detection and automated incident response.
This study was limited to articles indexed in WoS, Scopus, IEEE Xplore, and MDPI repositories, covering the period from January 2015 to June 2024 and restricted to publications in English. Another limitation identified in the reviewed models is the limited consideration of robustness and sensitivity analyses, which constrains the understanding of their performance under varying conditions. Future work could extend this research to include other repositories and non-English sources.
Based on this analysis, five key challenges are identified for strengthening cybersecurity in CEIC:
CEIC models for heterogeneous and legacy OT environments: Many operational systems were not originally designed with cybersecurity in mind, posing a major challenge. Adaptive solutions are required to secure legacy environments without compromising operability [
44].
CEIC models supporting multiple standards: The lack of standardized, interoperable frameworks hinders broader adoption. While the NIST Framework is widely used in the U.S., regions such as Europe follow ENISA guidelines. This underlines the need for multi-standard-supportive models.
Sophisticated cyber threats: Current models still show limitations in addressing advanced persistent threats (APTs) and zero-day attacks.
Emerging risks from quantum computing and IIoT hyperconnectivity: The expansion of the Industrial Internet of Things (IIoT) and the advent of quantum computing enlarge the attack surface and challenge traditional cryptographic mechanisms. Proactive models must incorporate quantum-resilient encryption and lightweight protection schemes.
Limited integration of emerging technologies: Despite their potential, technologies like blockchain and federated learning are still underutilized in CEIC models. The challenge lies in designing architecture that ensures secure, interoperable, and scalable integration.
This review contributes more than a descriptive synthesis by proposing a structured taxonomy of 49 OT cybersecurity models, organized into seven categories and five analytical dimensions. By integrating these perspectives, the study delivers a clear and replicable framework that supports comparative analysis, enhances transparency in systematic reviews, and provides actionable guidance for strengthening the cybersecurity of energy infrastructures in practice.