Privacy-Preserving Machine Learning for IoT-Integrated Smart Grids: Recent Advances, Opportunities, and Challenges
Abstract
1. Introduction
1.1. Background and Importance of Smart Grids (SGs)
1.2. Role of IoT in SGs: Opportunities and Challenges
1.3. Need for Privacy-Preserving Machine Learning (PPML) in SGs
1.4. Objectives and Contributions
1.5. Paper Organization
2. Smart Grid Architecture
2.1. Key Components of Smart Grids
- Power Generation: In the realm of energy generation, IoT aids in analyzing energy production, monitoring distributed energy resources, assessing harmful gas emissions, understanding consumption patterns, predicting energy needs, managing power connections, and coordinating large-scale storage solutions.
- Transmission and Distribution Systems: To ensure the smooth transmission of power from generators to consumers, IoT devices monitor power flow, detect faults, assess the condition of transmission towers, manage substations, and oversee equipment services. At the distribution end, IoT significantly contributes to distributed energy forecasting, load management, demand response, electric vehicle (EV) integration, and enhancing energy efficiency.
- Prosumer End: Energy-storage systems help balance power supply and demand during periods of intermittent renewable energy generation. IoT facilitates user interaction in bidirectional grid operations, allowing smart meters to collect data, encourage demand-side participation, manage EV charging schedules, and integrate distributed energy resources (DERs) such as solar power and battery storage at the consumer level.
2.2. IoT Adaptation in Smart Grids
2.3. Data Flow: From Edge to Cloud
3. Types of Possible Threats in IoT-Based Smart Grids
3.1. Cyber Security Threats
3.1.1. Malware Attacks
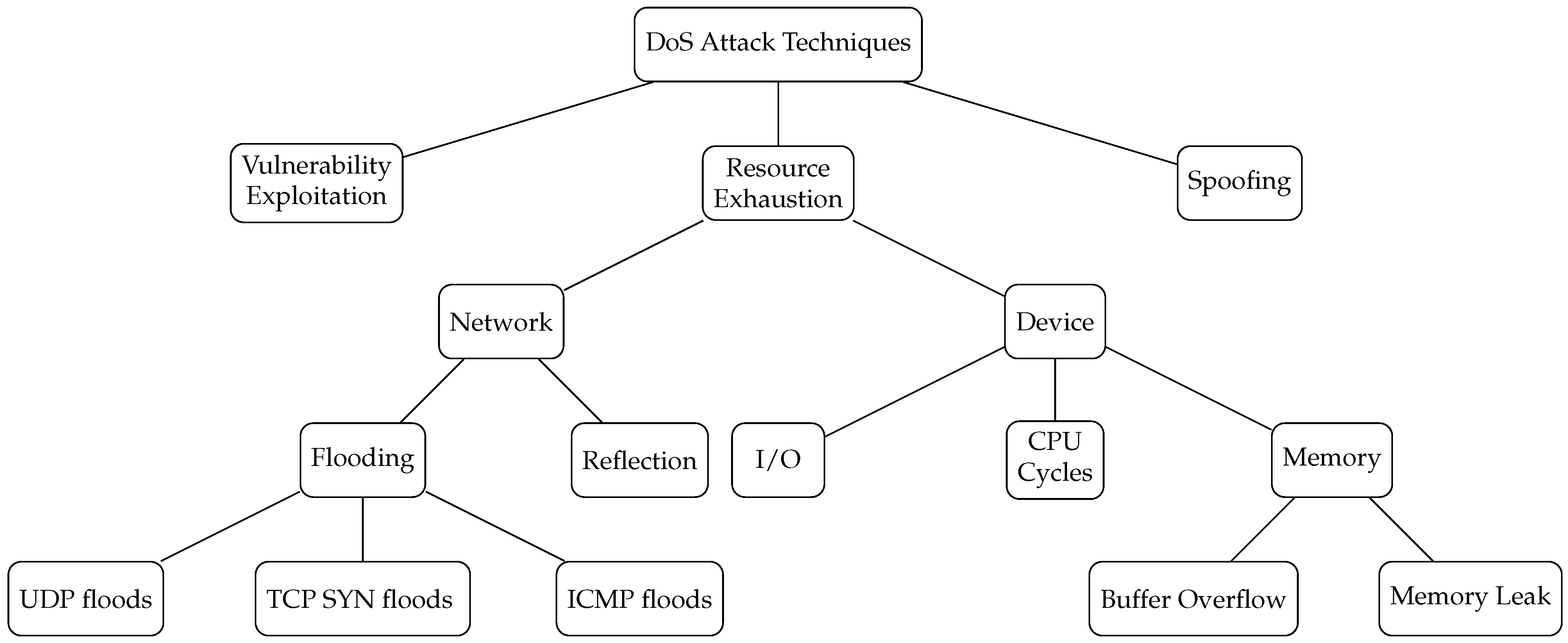
3.1.2. Denial of Services (DoS)
3.1.3. Man-in-the-Middle
3.2. Data-Oriented Threats
3.2.1. Data Breaches and Leakage
3.2.2. Data Poisoning
3.3. Physical Layer Attacks
4. Privacy-Preserving Machine Learning Techniques
- Anonymization
- Differential privacy (DP)
- Synthetic data (SD)
- Secure multiparty computation (SMPC)
- Homomorphic encryption (HE)
- Zero-knowledge proof (ZKP)
- Trusted execution environment (TEE)
- Federated learning (FL)
| Mentioned Attacks | Target Systems | Vulnerability | Countermeasure |
|---|---|---|---|
| CIA Triad Attacks [10,21] | Customer Information Systems (CIS), SCADA, Smart Meters, and Cloud Storage | Privacy breaches, incorrect energy distribution, communication blockage, inaccessible resources, and causes financial loss | Intrusion-Detection and -Prevention Systems, data masking and anonymization, and access control mechanisms |
| Ransom Attacks [31,65] | Communication networks, Automation, and Centralized control systems | Widespread power outages and operational disruptions leading to infrastructure damage and financial loss | Multi-Factor Authentication, ID&PS, and robust access control |
| Data Breach and Leakage [58] | SCADA, Smart meters, Cloud storage systems | Privacy violations and grid operation disruptions leading to financial loss and reputation damage | Strong encryption, access control, regular security audits, and monitoring of data-sharing protocols |
| DoS/DDoS [66,67] | SCADA, Advance Metering Infrastructure (AMI) | Communication overload, flow disruption, and incorrect data transfer | State-of-the-art security protocols to provide secure communication |
| Single Point of Failure [68,69] | Critical Substations and Transformers, Communication Hubs, and Cloud-based Grid Management Platforms | Complete system crash, communication breakdown, de-sync operations, and could impose cyberattacks | Adopting distributed control architecture, blockchain for authentication, and robust anomaly detection |
| Man-in-the-Middle [48,66] | Communication network, SCADA, Energy-management system (EMS) | Misconfigurations, energy blackouts, incorrect billing, and damaged infrastructure | Cryptographic security measures, network-monitoring and -protecting techniques |
| False Data Injection, Meter Spoofing [70,71] | Smart meters, State estimation systems, Distributed Energy Resource (DER) management | Compromised meter unresponsive to critical grid operations and utility requests | Enhanced meter security with data integrity and validation methods to secure physical access |
| Data Manipulation, Identity theft attacks [72] | Customer Information Systems, SCADA, DER Management | Detect identity-based security vulnerabilities in the system, leads to data tampering and privacy breach | Strong data encryption methods, blockchain-based identification, and authentication methods to prevent identity theft and impersonating |
| Malicious Energy Traders [73] | Demand Response Systems, AMI, Billing and Payment Infrastructure | Energy theft and fraud, billing chaos, and exploit demand-response systems to destabilize the power grid | Real-Time Monitoring and Alerts system, blockchain for transactions and AI-Powered Fraud Detections |
4.1. Anonymization
4.2. Differential Privacy
4.3. Synthetic Data
4.4. Secure Multiparty Computation
4.5. Homomorphic Encryption
4.6. Zero-Knowledge Proof
4.7. Trusted Execution Environment
4.8. Federated Learning
5. Applications of PPML in IoT-Integrated Smart Grids
5.1. Non-Intrusive Load Monitoring (NILM)
5.2. Fault Detection, Energy Theft, and Diagnostics
5.3. Demand Forecasting
5.4. Generation Forecasting
5.5. Anomaly Detection
5.6. Energy Trading
5.7. Electric Vehicles
6. Integration of PPML and IoT in Smart Grid Domains
6.1. Challenges in Integrating IoT and PPML in SGs
6.2. Frameworks and Libraries of PPML
6.3. Performance Analysis: Accuracy, Latency, and Resource Constraints
7. Opportunities and Open Challenges
7.1. Emerging Trends in PPML for SGs
7.2. Addressing Scalability and Interoperability Issues
7.3. Future Research Directions: PPML in Decentralized Grids and Blockchain Integration
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| SG | Smart Grid |
| IoT | Internet of Things |
| PPML | Privacy-Preserving Machine Learning |
| CPS | Cyber–Physical System |
| DP | Differential Privacy |
| MPC | Multiparty Computation |
| HE | Homomorphic Encryption |
| FL | Federated Learning |
| TEE | Trusted Execution Environment |
| ZKP | Zero-Knowledge Proof |
| ICT | Information and Communication Technology |
| EV | Electric Vehicle |
| DER | Distributed Energy Resource |
| AMI | Advanced Metering Infrastructure |
| PMU | Phasor Measurement Unit |
| CIA | Confidentiality, Integrity, and Availability |
| DoS | Denial-of-Service |
| DDoS | Distributed Denial-of-Service |
| SCADA | Supervisory Control and Data Acquisition |
| ICS | Industrial Control System |
| VPN | Virtual Private Network |
| MFA | Multi-Factor Authentication |
| IDPS | Intrusion-Detection and -Prevention System |
| IDS | Intrusion-Detection System |
| DPI | Deep Packet Inspection |
| FDI | False Data Injection |
| FCI | False Command Injection |
| MITM | Man-In-The-Middle |
| AES | Advanced Encryption Standard |
| TSL | Transport Layer Security |
| PKI | Public Key Infrastructure |
| ML | Machine Learning |
| IAM | Identity and Access Management |
| RBAC | Role-Based Access Control |
| TPM | Trusted Platform Modules |
| PG&E | Pacific Gas and Electric Company |
| EMS | Energy Management System |
| SD | Synthetic Data |
| SMPC | Secure Multiparty Computation |
| IED | Intelligent Electronic Device |
| EQ | Equivalence Classes |
| PII | Personally Identifiable Information |
| QI | Quasi-Identifier |
| LDP | Local Differential Privacy |
| SpDP | Spectral Differential Privacy |
| TrDP | Trajectory-level DP |
| PDP | Personalized Differential Privacy |
| NILM | Non-Intrusive Load Monitoring |
| DDP | Distributed Differential Privacy |
| RDP | Random Differential Privacy |
| DPML | Differentially Private Machine Learning |
| PPMM-DA | Privacy-Preserving Multi-Dimensional and Multi-Subset Data Aggregation |
| GAN | Generative Adversarial Network |
| RNN | Recurrent Neural Network |
| CNN | Convolutional Neural Network |
| NILM | Non-Intrusive Load Monitoring |
| VAE | Variational Autoencoder |
| GMM | Gaussian Mixture Model |
| DP-SGD | Differentially Private Stochastic Gradient Descent |
| SD3 | Stable Diffusion 3 |
References
- Hu, Y. Research on Industry 4.0 smart grid monitoring and energy management based on data mining and Internet of Things technology. Therm. Sci. Eng. Prog. 2024, 54, 102830. [Google Scholar] [CrossRef]
- Faheem, M.; Shah, S.B.H.; Butt, R.A.; Raza, B.; Anwar, M.; Ashraf, M.W.; Ngadi, M.A.; Gungor, V.C. Smart grid communication and information technologies in the perspective of Industry 4.0: Opportunities and challenges. Comput. Sci. Rev. 2018, 30, 1–30. [Google Scholar] [CrossRef]
- Goudarzi, A.; Ghayoor, F.; Waseem, M.; Fahad, S.; Traore, I. A survey on IoT-enabled smart grids: Emerging, applications, challenges, and outlook. Energies 2022, 15, 6984. [Google Scholar] [CrossRef]
- Ahmad, T.; Madonski, R.; Zhang, D.; Huang, C.; Mujeeb, A. Data-driven probabilistic machine learning in sustainable smart energy/smart energy systems: Key developments, challenges, and future research opportunities in the context of smart grid paradigm. Renew. Sustain. Energy Rev. 2022, 160, 112128. [Google Scholar] [CrossRef]
- Ozay, M.; Esnaola, I.; Vural, F.T.Y.; Kulkarni, S.R.; Poor, H.V. Machine learning methods for attack detection in the smart grid. IEEE Trans. Neural Netw. Learn. Syst. 2015, 27, 1773–1786. [Google Scholar] [CrossRef]
- Kim, Y.; Hakak, S.; Ghorbani, A. Smart grid security: Attacks and defence techniques. IET Smart Grid 2023, 6, 103–123. [Google Scholar] [CrossRef]
- Berghout, T.; Benbouzid, M.; Muyeen, S. Machine learning for cybersecurity in smart grids: A comprehensive review-based study on methods, solutions, and prospects. Int. J. Crit. Infrastruct. Prot. 2022, 38, 100547. [Google Scholar] [CrossRef]
- Mirzaee, P.H.; Shojafar, M.; Cruickshank, H.; Tafazolli, R. Smart grid security and privacy: From conventional to machine learning issues (threats and countermeasures). IEEE Access 2022, 10, 52922–52954. [Google Scholar] [CrossRef]
- Mohammed, S.H.; Al-Jumaily, A.; Singh, M.S.J.; Jiménez, V.P.G.; Jaber, A.S.; Hussein, Y.S.; Al-Najjar, M.M.A.K.; Al-Jumeily, D. A review on the evaluation of feature selection using machine learning for cyber-attack detection in smart grid. IEEE Access 2024, 12, 44023–44042. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094. [Google Scholar] [CrossRef]
- Tomin, N.V.; Kurbatsky, V.G.; Sidorov, D.N.; Zhukov, A.V. Machine learning techniques for power system security assessment. IFAC-PapersOnLine 2016, 49, 445–450. [Google Scholar] [CrossRef]
- Al-Ali, A.; Gupta, R.; Zualkernan, I.; Das, S.K. Role of IoT technologies in big data management systems: A review and Smart Grid case study. Pervasive Mob. Comput. 2024, 100, 101905. [Google Scholar] [CrossRef]
- Zheng, R.; Sumper, A.; Aragüés-Peñalba, M.; Galceran-Arellano, S. Advancing Power System Services with Privacy-preserving Federated Learning Techniques: A Review. IEEE Access 2024, 12, 76753–76780. [Google Scholar] [CrossRef]
- Baksh, R.; Itoo, S.; Ahmad, M. A comprehensive and secure scheme for privacy-preserving smart meter data aggregation in the smart grid. Sustain. Energy Grids Netw. 2024, 39, 101461. [Google Scholar] [CrossRef]
- Cui, L.; Qu, Y.; Gao, L.; Xie, G.; Yu, S. Detecting false data attacks using machine learning techniques in smart grid: A survey. J. Netw. Comput. Appl. 2020, 170, 102808. [Google Scholar] [CrossRef]
- Triantafyllou, A.; Jimenez, J.A.P.; Torres, A.D.R.; Lagkas, T.; Rantos, K.; Sarigiannidis, P. The challenges of privacy and access control as key perspectives for the future electric smart grid. IEEE Open J. Commun. Soc. 2020, 1, 1934–1960. [Google Scholar] [CrossRef]
- Ali, M.; Khan, M.U.; Ali, H.; Haseeb Nawaz, M.; Imran, K.; Wazir, R. Feasibility study for designing a standalone community based energy system to remove energy poverty in rural areas of Pakistan. In Proceedings of the International Conference on Renewable, Applied and New Energy Technologies (ICRANET 2018), Islamabad, Pakistan, 19–22 November 2018; pp. 113–118. [Google Scholar]
- Xie, W.; Jiang, Y.; Tang, Y.; Ding, N.; Gao, Y. Vulnerability detection in iot firmware: A survey. In Proceedings of the 2017 IEEE 23rd International conference on parallel and distributed systems (ICPADS), Shenzhen, China, 15–17 December 2017; pp. 769–772. [Google Scholar]
- Ghiasi, M.; Niknam, T.; Wang, Z.; Mehrandezh, M.; Dehghani, M.; Ghadimi, N. A comprehensive review of cyber-attacks and defense mechanisms for improving security in smart grid energy systems: Past, present and future. Electr. Power Syst. Res. 2023, 215, 108975. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. Analysis of cyber-attacks on smart grid applications. In Proceedings of the 2018 International Conference on Artificial Intelligence and Data Processing (IDAP ), Malatya, Turkey, 28–30 September 2018; pp. 1–5. [Google Scholar]
- Pandey, R.K.; Misra, M. Cyber security threats—Smart grid infrastructure. In Proceedings of the 2016 National Power Systems Conference (NPSC), Bhubaneswar, India, 19–21 December 2016; pp. 1–6. [Google Scholar]
- Ding, J.; Qammar, A.; Zhang, Z.; Karim, A.; Ning, H. Cyber threats to smart grids: Review, taxonomy, potential solutions, and future directions. Energies 2022, 15, 6799. [Google Scholar] [CrossRef]
- El Mrabet, Z.; Kaabouch, N.; El Ghazi, H.; El Ghazi, H. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. [Google Scholar] [CrossRef]
- Gupta, B.B.; Akhtar, T. A survey on smart power grid: Frameworks, tools, security issues, and solutions. Ann. Telecommun. 2017, 72, 517–549. [Google Scholar] [CrossRef]
- Alomari, M.A.; Al-Andoli, M.N.; Ghaleb, M.; Thabit, R.; Alkawsi, G.; Alsayaydeh, J.A.J.; Gaid, A.S. Security of Smart Grid: Cybersecurity Issues, Potential Cyberattacks, Major Incidents, and Future Directions. Energies 2025, 18, 141. [Google Scholar] [CrossRef]
- Kramer, S.; Bradfield, J.C. A general definition of malware. J. Comput. Virol. 2010, 6, 105–114. [Google Scholar] [CrossRef]
- Thomas, S.L.; Francillon, A. Backdoors: Definition, deniability and detection. In Proceedings of the Research in Attacks, Intrusions, and Defenses: 21st International Symposium, RAID 2018, Heraklion, Crete, Greece, 10–12 September 2018; Proceedings 21. Springer: Berlin/Heidelberg, Germany, 2018; pp. 92–113. [Google Scholar]
- Whitehead, D.E.; Owens, K.; Gammel, D.; Smith, J. Ukraine cyber-induced power outage: Analysis and practical mitigation strategies. In Proceedings of the 2017 70th Annual Conference for Protective Relay Engineers (CPRE), College Station, TX, USA, 3–6 April 2017; pp. 1–8. [Google Scholar]
- Baezner, M. Cyber and Information Warfare in the Ukrainian Conflict; Technical report, CSS Cyberdefense Hotspot Analysis, No. 1; Center for Security Studies (CSS), ETH Zürich: Zurich, Switzerland, October 2018; Available online: https://www.research-collection.ethz.ch/handle/20.500.11850/321570 (accessed on 20 February 2025).
- Kozak, P.; Klaban, I.; Šlajs, T. Industroyer cyber-attacks on Ukraine’s critical infrastructure. In Proceedings of the 2023 International Conference on Military Technologies (ICMT), Brno, Czech Republic, 23–26 May 2023; pp. 1–6. [Google Scholar]
- Beerman, J.; Berent, D.; Falter, Z.; Bhunia, S. A review of colonial pipeline ransomware attack. In Proceedings of the 2023 IEEE/ACM 23rd International Symposium on Cluster, Cloud and Internet Computing Workshops (CCGridW), Bangalore, India, 1–4 May 2023; pp. 8–15. [Google Scholar]
- Gasti, P.; Tsudik, G.; Uzun, E.; Zhang, L. DoS and DDoS in named data networking. In Proceedings of the 2013 22nd International Conference on Computer Communication and Networks (ICCCN), Nassau, Bahamas, 30 July–2 August 2013; pp. 1–7. [Google Scholar]
- Alcoy, P.; Bjarnason, S.; Bowen, P.; Chui, C.F.; Kasavchnko, K. Arbor’s 13th Annual Worldwide Infrastructure Security Report. Netscouth: Pune, Maharashtra, 1 January 2018. [Google Scholar]
- Huseinović, A.; Mrdović, S.; Bicakci, K.; Uludag, S. A survey of denial-of-service attacks and solutions in the smart grid. IEEE Access 2020, 8, 177447–177470. [Google Scholar] [CrossRef]
- Yılmaz, E.N.; Sayan, H.H.; Üstünsoy, F.; Gönen, S.; Karacayılmaz, G. Cyber security analysis of DoS and MitM attacks against PLCs used in smart grids. In Proceedings of the 7th International Istanbul Smart Grids and Cities Congress and Fair (ICSG), Istanbul, Turkey, 25–26 April 2019; Volume 36, p. 40. [Google Scholar]
- Recommended Practice: Improving Industrial Control Systems Cybersecurity with Defense-In-Depth Strategies; US-CERT Defense In Depth: Washington, DC, USA, 2009.
- Pillitteri, V.Y.; Brewer, T.L. Guidelines for Smart Grid Cybersecurity: NISTIR 7628 Revision 1; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2014. [Google Scholar]
- Rajesh, L.; Satyanarayana, P. Detection and blocking of replay, false command, and false access injection commands in scada systems with modbus protocol. Secur. Commun. Networks 2021, 8887666, 15. [Google Scholar]
- Cruz, T.; Rosa, L.; Proença, J.; Maglaras, L.; Aubigny, M.; Lev, L.; Jiang, J.; Simões, P. A cybersecurity detection framework for supervisory control and data acquisition systems. IEEE Trans. Ind. Inform. 2016, 12, 2236–2246. [Google Scholar] [CrossRef]
- Yang, Y.; McLaughlin, K.; Sezer, S.; Littler, T.; Im, E.G.; Pranggono, B.; Wang, H. Multiattribute SCADA-specific intrusion detection system for power networks. IEEE Trans. Power Deliv. 2014, 29, 1092–1102. [Google Scholar] [CrossRef]
- Yang, Y.; Xu, H.Q.; Gao, L.; Yuan, Y.B.; McLaughlin, K.; Sezer, S. Multidimensional intrusion detection system for IEC 61850-based SCADA networks. IEEE Trans. Power Deliv. 2016, 32, 1068–1078. [Google Scholar] [CrossRef]
- Almalawi, A.; Fahad, A.; Tari, Z.; Alamri, A.; AlGhamdi, R.; Zomaya, A.Y. An efficient data-driven clustering technique to detect attacks in SCADA systems. IEEE Trans. Inf. Forensics Secur. 2015, 11, 893–906. [Google Scholar] [CrossRef]
- Zhang, F.; Kodituwakku, H.A.D.E.; Hines, J.W.; Coble, J. Multilayer data-driven cyber-attack detection system for industrial control systems based on network, system, and process data. IEEE Trans. Ind. Inform. 2019, 15, 4362–4369. [Google Scholar] [CrossRef]
- Maglaras, L.A.; Jiang, J. A novel intrusion detection method based on OCSVM and K-means recursive clustering. EAI Endorsed Trans. Secur. Saf. 2015, 2, e5. [Google Scholar] [CrossRef]
- Maglaras, L.A.; Jiang, J.; Cruz, T.J. Combining ensemble methods and social network metrics for improving accuracy of OCSVM on intrusion detection in SCADA systems. J. Inf. Secur. Appl. 2016, 30, 15–26. [Google Scholar] [CrossRef]
- Pashaei, A.; Akbari, M.E.; Lighvan, M.Z.; Charmin, A. Early Intrusion Detection System using honeypot for industrial control networks. Results Eng. 2022, 16, 100576. [Google Scholar] [CrossRef]
- Yusheng, W.; Kefeng, F.; Yingxu, L.; Zenghui, L.; Ruikang, Z.; Xiangzhen, Y.; Lin, L. Intrusion detection of industrial control system based on Modbus TCP protocol. In Proceedings of the 2017 IEEE 13th International Symposium on Autonomous Decentralized System (ISADS), Bangkok, Thailand, 22–24 March 2017; pp. 156–162. [Google Scholar]
- Elrawy, M.F.; Hadjidemetriou, L.; Laoudias, C.; Michael, M.K. Detecting and classifying man-in-the-middle attacks in the private area network of smart grids. Sustain. Energy Grids Netw. 2023, 36, 101167. [Google Scholar] [CrossRef]
- Slunjski, M.; Sumina, D.; Groš, S.; Erceg, I. Off-the-shelf solutions as potential cyber threats to industrial environments and simple-to-implement protection methodology. IEEE Access 2022, 10, 114735–114748. [Google Scholar] [CrossRef]
- Nam, S.Y.; Jurayev, S.; Kim, S.S.; Choi, K.; Choi, G.S. Mitigating ARP poisoning-based man-in-the-middle attacks in wired or wireless LAN. Eurasip J. Wirel. Commun. Netw. 2012, 2012, 89. [Google Scholar] [CrossRef]
- Kumar, N.; Mishra, V.M.; Kumar, A. Smart grid security with AES hardware chip. Int. J. Inf. Technol. 2020, 12, 49–55. [Google Scholar] [CrossRef]
- Wu, D.; Zhou, C. Fault-tolerant and scalable key management for smart grid. IEEE Trans. Smart Grid 2011, 2, 375–381. [Google Scholar] [CrossRef]
- Tu, C.; He, X.; Shuai, Z.; Jiang, F. Big data issues in smart grid—A review. Renew. Sustain. Energy Rev. 2017, 79, 1099–1107. [Google Scholar] [CrossRef]
- Gough, M.B.; Santos, S.F.; AlSkaif, T.; Javadi, M.S.; Castro, R.; Catalão, J.P. Preserving privacy of smart meter data in a smart grid environment. IEEE Trans. Ind. Inform. 2021, 18, 707–718. [Google Scholar] [CrossRef]
- Vojković, G.; Milenković, M.; Katulić, T. IoT and smart home data breach risks from the perspective of data protection and information security law. Bus. Syst. Res. Int. J. Soc. Adv. Innov. Res. Econ. 2020, 11, 167–185. [Google Scholar] [CrossRef]
- Peretti, K.K. Data breaches: What the underground world of “carding” reveals. Santa Clara Comput. High Tech. 2008, 25, 375. [Google Scholar]
- Manworren, N.; Letwat, J.; Daily, O. Why you should care about the Target data breach. Bus. Horizons 2016, 59, 257–266. [Google Scholar] [CrossRef]
- Case, D.U. Analysis of the cyber attack on the Ukrainian power grid. Electr. Inf. Shar. Anal. Cent. (E-ISAC) 2016, 388, 3. [Google Scholar]
- Khan, R.; Maynard, P.; McLaughlin, K.; Laverty, D.; Sezer, S. Threat analysis of blackenergy malware for synchrophasor based real-time control and monitoring in smart grid. In Proceedings of the 4th International Symposium for ICS & SCADA Cyber Security Research 2016, Belfast, UK, 23–25 August 2016; pp. 53–63. [Google Scholar]
- Nayak, S.K.; Ojha, A.C. Data Leakage Detection and Prevention: Review and Research Directions. In Machine Learning and Information Processing; Swain, D., Pattnaik, P.K., Gupta, P.K., Eds.; Springer: Singapore, 2020; pp. 203–212. [Google Scholar]
- Blunt, K. California Burning: The Fall of Pacific Gas and Electric–and What It Means for America’s Power Grid; Penguin: London, UK, 2022. [Google Scholar]
- Allen, J. An Examination of US Offensive Cyber Operations in Response to Russian State Sponsored Attacks Against the US Energy Sector. Master’s Thesis, Utica College, Utica, NY, USA, 2020. [Google Scholar]
- Lee, E.K.; Gerla, M.; Oh, S.Y. Physical layer security in wireless smart grid. IEEE Commun. Mag. 2012, 50, 46–52. [Google Scholar] [CrossRef]
- Islam, S.N.; Baig, Z.; Zeadally, S. Physical layer security for the smart grid: Vulnerabilities, threats, and countermeasures. IEEE Trans. Ind. Inform. 2019, 15, 6522–6530. [Google Scholar] [CrossRef]
- Basnet, M.; Poudyal, S.; Ali, M.H.; Dasgupta, D. Ransomware detection using deep learning in the SCADA system of electric vehicle charging station. In Proceedings of the 2021 IEEE PES Innovative Smart Grid Technologies Conference-Latin America (ISGT Latin America), Lima, Peru, 15–17 September 2021; pp. 1–5. [Google Scholar]
- Liu, S.; Liu, X.P.; El Saddik, A. Denial-of-Service (dos) attacks on load frequency control in smart grids. In Proceedings of the 2013 IEEE Pes Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 24–27 February 2013; pp. 1–6. [Google Scholar]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A survey on cyber security for smart grid communications. IEEE Commun. Surv. Tutor. 2012, 14, 998–1010. [Google Scholar] [CrossRef]
- Samuel, O.; Javaid, N. GarliChain: A privacy preserving system for smart grid consumers using blockchain. Int. J. Energy Res. 2022, 46, 21643–21659. [Google Scholar] [CrossRef]
- Dong, X.; Lin, H.; Tan, R.; Iyer, R.K.; Kalbarczyk, Z. Software-defined networking for smart grid resilience: Opportunities and challenges. In Proceedings of the 1st ACM Workshop on Cyber-Physical System Security, New York, NY, USA, 14 April 2015; pp. 61–68. [Google Scholar]
- Wei, L.; Rondon, L.P.; Moghadasi, A.; Sarwat, A.I. Review of cyber–physical attacks and counter defense mechanisms for advanced metering infrastructure in smart grid. In Proceedings of the 2018 IEEE/PES Transmission and Distribution Conference and Exposition (T&D), Denver CO, USA, 16–19 April 2018; pp. 1–9. [Google Scholar]
- Manandhar, K.; Cao, X.; Hu, F.; Liu, Y. Detection of faults and attacks including false data injection attack in smart grid using Kalman filter. IEEE Trans. Control Netw. Syst. 2014, 1, 370–379. [Google Scholar] [CrossRef]
- Dehalwar, V.; Kolhe, M.L.; Deoli, S.; Jhariya, M.K. Blockchain-based trust management and authentication of devices in smart grid. Clean. Eng. Technol. 2022, 8, 100481. [Google Scholar] [CrossRef]
- Li, M.; Hu, D.; Lal, C.; Conti, M.; Zhang, Z. Blockchain-enabled secure energy trading with verifiable fairness in industrial Internet of Things. IEEE Trans. Ind. Inform. 2020, 16, 6564–6574. [Google Scholar] [CrossRef]
- Yang, D.; Mashima, D.; Lin, W.; Zhou, J. DecIED: Scalable k-anonymous deception for iec61850-compliant smart grid systems. In Proceedings of the 6th ACM on Cyber-Physical System Security Workshop, Taipei, Taiwan, 6 October 2020; pp. 54–65. [Google Scholar]
- Alsaid, M.; Bulusu, N.; Adham, M.; Bass, R.B. Distributed energy resource management systems: Preserving customer privacy through k-anonymity. In Proceedings of the 2023 IEEE Power & Energy Society General Meeting (PESGM), Orlando FL, USA, 16–20 July 2023; pp. 1–5. [Google Scholar]
- Brunn, C.; von Voigt, S.N.; Tschorsch, F. Analyzing Continuous K s-Anonymization for Smart Meter Data. In Proceedings of the European Symposium on Research in Computer Security, The Hague, The Netherlands, 25–29 September 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 272–282. [Google Scholar]
- Zhai, F.; Liang, X.; Qin, Y.; Li, B.; Shen, L.; Xie, J. Privacy-preserving method for sensitive partitions of electricity consumption data based on hybrid differential privacy and k-anonymity. J. Phys. Conf. Ser. 2024, 2806, 012010. [Google Scholar] [CrossRef]
- Gai, N.; Xue, K.; Zhu, B.; Yang, J.; Liu, J.; He, D. An efficient data aggregation scheme with local differential privacy in smart grid. Digit. Commun. Netw. 2022, 8, 333–342. [Google Scholar] [CrossRef]
- Parker, K.; Hale, M.; Barooah, P. Spectral differential privacy: Application to smart meter data. IEEE Internet Things J. 2021, 9, 4987–4996. [Google Scholar] [CrossRef]
- Zhao, S.; Xu, S.; Han, S.; Ren, S.; Wang, Y.; Chen, Z.; Chen, X.; Lin, J.; Liu, W. PPMM-DA: Privacy-preserving multi-dimensional and multi-subset data aggregation with differential privacy for fog-based smart grids. IEEE Internet Things J. 2023, 11, 6096–6110. [Google Scholar] [CrossRef]
- Bhattacharjee, A.; Badsha, S.; Sengupta, S. Personalized privacy preservation for smart grid. In Proceedings of the 2021 IEEE International Smart Cities Conference (ISC2), Manchester, UK, 7–10 September 2021; pp. 1–7. [Google Scholar]
- Ravi, N.; Scaglione, A.; Peisert, S.; Pradhan, P. Differentially Private Communication of Measurement Anomalies in the Smart Grid. arXiv 2024, arXiv:2403.02324. [Google Scholar]
- Zheng, Z.; Wang, T.; Bashir, A.K.; Alazab, M.; Mumtaz, S.; Wang, X. A decentralized mechanism based on differential privacy for privacy-preserving computation in smart grid. IEEE Trans. Comput. 2021, 71, 2915–2926. [Google Scholar] [CrossRef]
- Qashlan, A.; Nanda, P.; Mohanty, M. Differential privacy model for blockchain based smart home architecture. Future Gener. Comput. Syst. 2024, 150, 49–63. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Kotagiri, R.; Zhang, J.; Chen, J. Differential privacy for renewable energy resources based smart metering. J. Parallel Distrib. Comput. 2019, 131, 69–80. [Google Scholar] [CrossRef]
- Fekri, M.N.; Ghosh, A.M.; Grolinger, K. Generating energy data for machine learning with recurrent generative adversarial networks. Energies 2019, 13, 130. [Google Scholar] [CrossRef]
- Song, L.; Li, Y.; Lu, N. ProfileSR-GAN: A GAN based super-resolution method for generating high-resolution load profiles. IEEE Trans. Smart Grid 2022, 13, 3278–3289. [Google Scholar] [CrossRef]
- Chai, S.; Chadney, G.; Avery, C.; Grunewald, P.; Van Hentenryck, P.; Donti, P.L. Defining’Good’: Evaluation Framework for Synthetic Smart Meter Data. arXiv 2024, arXiv:2407.11785. [Google Scholar]
- Zhang, C.; Kuppannagari, S.R.; Kannan, R.; Prasanna, V.K. Generative adversarial network for synthetic time series data generation in smart grids. In Proceedings of the 2018 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Aalborg, Denmark, 29–31 October 2018; pp. 1–6. [Google Scholar]
- Mestav, K.R.; Tong, L. State estimation in smart distribution systems with deep generative adversary networks. In Proceedings of the 2019 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Beijing, China, 21–23 October 2019; pp. 1–6. [Google Scholar]
- Zhang, S.; Cheng, Y.; Yu, N. Generating synthetic net load data with physics-informed diffusion model. arXiv 2024, arXiv:2406.01913. [Google Scholar]
- Aldegheishem, A.; Anwar, M.; Javaid, N.; Alrajeh, N.; Shafiq, M.; Ahmed, H. Towards sustainable energy efficiency with intelligent electricity theft detection in smart grids emphasising enhanced neural networks. IEEE Access 2021, 9, 25036–25061. [Google Scholar] [CrossRef]
- Croce, D.; Giuliano, F.; Tinnirello, I.; Giarré, L. Privacy-preserving overgrid: Secure data collection for the smart grid. Sensors 2020, 20, 2249. [Google Scholar] [CrossRef]
- Ababneh, M.; Kolachala, K.; Vishwanathan, R. Private and Secure Smart Meter Billing. In Proceedings of the 8th ACM on Cyber-Physical System Security Workshop, Nagasaki, Japan, 30 May 2022; pp. 15–25. [Google Scholar]
- Rahman, M.A.; Manshaei, M.H.; Al-Shaer, E.; Shehab, M. Secure and private data aggregation for energy consumption scheduling in smart grids. IEEE Trans. Dependable Secur. Comput. 2015, 14, 221–234. [Google Scholar] [CrossRef]
- Guan, Z.; Zhou, X.; Liu, P.; Wu, L.; Yang, W. A blockchain-based dual-side privacy-preserving multiparty computation scheme for edge-enabled smart grid. IEEE Internet Things J. 2021, 9, 14287–14299. [Google Scholar] [CrossRef]
- von der Heyden, J.; Schlüter, N.; Binfet, P.; Asman, M.; Zdrallek, M.; Jager, T.; Darup, M.S. Privacy-Preserving Power Flow Analysis via Secure Multi-Party Computation. IEEE Trans. Smart Grid 2024, 16, 344–355. [Google Scholar] [CrossRef]
- Franke, M.; Stanojev, O.; Mitridati, L.; Hug, G. Privacy-preserving distributed market mechanism for active distribution networks. Electr. Power Syst. Res. 2024, 234, 110616. [Google Scholar] [CrossRef]
- Wang, N.; Chau, S.C.K.; Zhou, Y. Privacy-preserving energy storage sharing with blockchain and secure multi-party computation. Acm Sigenergy Energy Inform. Rev. 2021, 1, 32–50. [Google Scholar] [CrossRef]
- Mustafa, M.A.; Cleemput, S.; Aly, A.; Abidin, A. A secure and privacy-preserving protocol for smart metering operational data collection. IEEE Trans. Smart Grid 2019, 10, 6481–6490. [Google Scholar] [CrossRef]
- Xie, S.; Wang, H.; Hong, Y.; Thai, M. Privacy preserving distributed energy trading. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, 29 November–1 December 2020; pp. 322–332. [Google Scholar]
- Fan, H.; Fan, X.; Wei, W.; Hao, T.; Chen, K.; Wang, G.; Xu, W. Privacy preserving ultra-short-term prediction in clustered wind farms with encrypted data sharing: A secure multi-party computation approach. Expert Syst. Appl. 2025, 278, 127218. [Google Scholar] [CrossRef]
- Saputro, N.; Akkaya, K. Performance evaluation of smart grid data aggregation via homomorphic encryption. In Proceedings of the 2012 IEEE Wireless Communications and Networking Conference (WCNC), Paris, France, 1–4 April 2012; pp. 2945–2950. [Google Scholar]
- Foti, M. Privacy-preserving market-driven transactive energy system using homomorphic encryption. In Proceedings of the 2023 19th International Conference on the European Energy Market (EEM), Lappeenranta, Finland, 6–8 June 2023; pp. 1–8. [Google Scholar]
- Xu, W.; Sun, J.; Cardell-Oliver, R.; Mian, A.; Hong, J.B. A privacy-preserving framework using homomorphic encryption for smart metering systems. Sensors 2023, 23, 4746. [Google Scholar] [CrossRef] [PubMed]
- Guo, C.; Jiang, X.; Choo, K.K.R.; Tang, X.; Zhang, J. Lightweight privacy preserving data aggregation with batch verification for smart grid. Future Gener. Comput. Syst. 2020, 112, 512–523. [Google Scholar] [CrossRef]
- Alabdulatif, A.; Kumarage, H.; Khalil, I.; Atiquzzaman, M.; Yi, X. Privacy-preserving cloud-based billing with lightweight homomorphic encryption for sensor-enabled smart grid infrastructure. IET Wirel. Sens. Syst. 2017, 7, 182–190. [Google Scholar] [CrossRef]
- Braeken, A.; Kumar, P.; Martin, A. Efficient and privacy-preserving data aggregation and dynamic billing in smart grid metering networks. Energies 2018, 11, 2085. [Google Scholar] [CrossRef]
- Bos, J.W.; Castryck, W.; Iliashenko, I.; Vercauteren, F. Privacy-friendly forecasting for the smart grid using homomorphic encryption and the group method of data handling. In Proceedings of the International Conference on Cryptology in Africa, Dakar, Senegal, 24–26 May 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 184–201. [Google Scholar]
- Mai, V.; Khalil, I. Design and implementation of a secure cloud-based billing model for smart meters as an Internet of Things using homomorphic cryptography. Future Gener. Comput. Syst. 2017, 72, 327–338. [Google Scholar] [CrossRef]
- Parameswarath, R.P.; Gope, P.; Sikdar, B. User-empowered privacy-preserving authentication protocol for electric vehicle charging based on decentralized identity and verifiable credential. ACM Trans. Manag. Inf. Syst. (TMIS) 2022, 13, 1–21. [Google Scholar] [CrossRef]
- Li, Z.; Xu, H.; Zhai, F.; Zhao, B.; Xu, M.; Guo, Z. A privacy-preserving, two-party, secure computation mechanism for consensus-based peer-to-peer energy trading in the smart grid. Sensors 2022, 22, 9020. [Google Scholar] [CrossRef]
- Ma, Y.; Qiu, J.; Sun, X.; Tao, Y. A Novel Cryptography-based Architecture to Achieve Secure Energy Trading in Microgrid. IEEE Trans. Smart Grid 2023, 15, 2056–2072. [Google Scholar] [CrossRef]
- Sebastian, D.; Agrawal, U.; Tamimi, A.; Hahn, A. DER-TEE: Secure distributed energy resource operations through trusted execution environments. IEEE Internet Things J. 2019, 6, 6476–6486. [Google Scholar] [CrossRef]
- Li, Z.; Mashima, D.; Ong, W.S.; Esiner, E.; Kalbarczyk, Z.; Chang, E.C. On Practicality of Using ARM TrustZone Trusted Execution Environment for Securing Programmable Logic Controllers. In Proceedings of the 19th ACM Asia Conference on Computer and Communications Security, Singapore, 1–5 July 2024; pp. 947–961. [Google Scholar]
- Will, N.C.; Valadares, D.C.G.; Santos, D.F.D.S.; Perkusich, A. Intel software guard extensions in Internet of Things scenarios: A systematic mapping study. In Proceedings of the 2021 8th International Conference on Future Internet of Things and Cloud (FiCloud), Rome, Italy, 23–25 August 2021; pp. 342–349. [Google Scholar]
- Li, S.; Xue, K.; Wei, D.S.; Yue, H.; Yu, N.; Hong, P. SecGrid: A secure and efficient SGX-enabled smart grid system with rich functionalities. IEEE Trans. Inf. Forensics Secur. 2019, 15, 1318–1330. [Google Scholar] [CrossRef]
- Ali, M.; Singh, A.K.; Kumar, A.; Ali, S.S.; Choi, B.J. Comparative analysis of data-driven algorithms for building energy planning via federated learning. Energies 2023, 16, 6517. [Google Scholar] [CrossRef]
- Husnoo, M.A.; Anwar, A.; Reda, H.T.; Hosseinzadeh, N.; Islam, S.N.; Mahmood, A.N.; Doss, R. FedDiSC: A computation-efficient federated learning framework for power systems disturbance and cyber attack discrimination. Energy AI 2023, 14, 100271. [Google Scholar] [CrossRef]
- Singh, V.K.; Tucker, E.; Rath, S. Federated Machine Learning-Based Anomaly Detection System for Synchrophasor Network Using Heterogeneous Data Sets; Technical Report; National Renewable Energy Laboratory (NREL): Golden, CO, USA, 2024. [Google Scholar]
- Su, Z.; Wang, Y.; Luan, T.H.; Zhang, N.; Li, F.; Chen, T.; Cao, H. Secure and efficient federated learning for smart grid with edge-cloud collaboration. IEEE Trans. Ind. Inform. 2021, 18, 1333–1344. [Google Scholar] [CrossRef]
- Jithish, J.; Alangot, B.; Mahalingam, N.; Yeo, K.S. Distributed anomaly detection in smart grids: A federated learning-based approach. IEEE Access 2023, 11, 7157–7179. [Google Scholar] [CrossRef]
- Lin, W.T.; Chen, G.; Huang, Y. Incentive edge-based federated learning for false data injection attack detection on power grid state estimation: A novel mechanism design approach. Appl. Energy 2022, 314, 118828. [Google Scholar] [CrossRef]
- Husnoo, M.A.; Anwar, A.; Reda, H.T.; Hosseinzadeh, N.; Islam, S.N.; Mahmood, A.N.; Doss, R. Fedisa: A semi-asynchronous federated learning framework for power system fault and cyberattack discrimination. In Proceedings of the IEEE INFOCOM 2023-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Hoboken NJ, USA, 20 May 2023; pp. 1–6. [Google Scholar]
- Taheri, S.I.; Davoodi, M.; Ali, M.H. A modified modeling approach of virtual power plant via improved federated learning. Int. J. Electr. Power Energy Syst. 2024, 158, 109905. [Google Scholar] [CrossRef]
- Yang, Y.; Wang, Z.; Zhao, S.; Wu, J. An integrated federated learning algorithm for short-term load forecasting. Electr. Power Syst. Res. 2023, 214, 108830. [Google Scholar] [CrossRef]
- Li, Y.; Li, Y. Semi-supervised federated learning for collaborative security threat detection in control system for distributed power generation. Eng. Appl. Artif. Intell. 2025, 148, 110374. [Google Scholar] [CrossRef]
- Gupta, H.; Agarwal, P.; Gupta, K.; Baliarsingh, S.; Vyas, O.; Puliafito, A. Fedgrid: A secure framework with federated learning for energy optimization in the smart grid. Energies 2023, 16, 8097. [Google Scholar] [CrossRef]
- Li, Y.; Wang, R.; Li, Y.; Zhang, M.; Long, C. Wind power forecasting considering data privacy protection: A federated deep reinforcement learning approach. Appl. Energy 2023, 329, 120291. [Google Scholar] [CrossRef]
- Ali, S.S.; Ali, M.; Bhatti, D.M.S.; Choi, B.J. dy-TACFL: Dynamic Temporal Adaptive Clustered Federated Learning for Heterogeneous Clients. Electronics 2025, 14, 152. [Google Scholar] [CrossRef]
- Barros, R.M.R.; da Costa, E.G.; Araujo, J.F. Maximizing the financial return of non-technical loss management in power distribution systems. IEEE Trans. Power Syst. 2021, 37, 1634–1641. [Google Scholar] [CrossRef]
- Adewole, K.S.; Torra, V. Privacy Protection of Synthetic Smart Grid Data Simulated via Generative Adversarial Networks. In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT), Rome, Italy, 10–12 July 2023; SciTePress: Setúbal, Portugal, 2023; pp. 279–286. [Google Scholar]
- Syed, D.; Refaat, S.S.; Bouhali, O. Privacy preservation of data-driven models in smart grids using homomorphic encryption. Information 2020, 11, 357. [Google Scholar] [CrossRef]
- Abdallah, A.; Shen, X.S. A lightweight lattice-based homomorphic privacy-preserving data aggregation scheme for smart grid. IEEE Trans. Smart Grid 2016, 9, 396–405. [Google Scholar] [CrossRef]
- Zhou, X.; Wang, B.; Guo, Q.; Sun, H.; Pan, Z.; Tian, N. Bidirectional privacy-preserving network-constrained peer-to-peer energy trading based on secure multiparty computation and blockchain. IEEE Trans. Power Syst. 2023, 39, 602–613. [Google Scholar] [CrossRef]
- Ali, S.S.; Kumar, A.; Ali, M.; Singh, A.K.; Choi, B.J. Temporal adaptive clustering for heterogeneous clients in federated learning. In Proceedings of the 2024 International Conference on Information Networking (ICOIN), Ho Chi Minh City, Vietnam, 17–19 January 2024; pp. 11–16. [Google Scholar]
- Long, Y.; Chen, Y.; Ren, W.; Dou, H.; Xiong, N.N. Depet: A decentralized privacy-preserving energy trading scheme for vehicular energy network via blockchain and k-anonymity. IEEE Access 2020, 8, 192587–192596. [Google Scholar] [CrossRef]
- El-Afifi, M.I.; Sedhom, B.E.; Padmanaban, S.; Eladl, A.A. A review of IoT-enabled smart energy hub systems: Rising, applications, challenges, and future prospects. Renew. Energy Focus 2024, 51, 100634. [Google Scholar] [CrossRef]
- Tran, H.Y.; Hu, J.; Pota, H.R. Smart meter data obfuscation with a hybrid privacy-preserving data publishing scheme without a trusted third party. IEEE Internet Things J. 2022, 9, 16080–16095. [Google Scholar] [CrossRef]
- Ramana K., V.; Yadav G., H. K.; Basha P., H.; Sambasivarao, L.; Rao, Y.B.K. Secure and efficient energy trading using homomorphic encryption on the green trade platform. Int. J. Intell. Syst. Appl. Eng. 2023, 12, 345–360. [Google Scholar]
- Vu, D.H.; Luong, T.D.; Ho, T.B. An efficient approach for secure multi-party computation without authenticated channel. Inf. Sci. 2020, 527, 356–368. [Google Scholar] [CrossRef]
- Ali, M.; Kumar, A.; Choi, B.J. Privacy Preserving Federated Learning for Energy Disaggregation of Smart Homes. IET Cyber-Phys. Syst. Theory Appl. 2025, 10, e70013. [Google Scholar] [CrossRef]
- Chen, Z.; Jiang, Y.; Song, X.; Chen, L. A survey on zero-knowledge authentication for Internet of Things. Electronics 2023, 12, 1145. [Google Scholar] [CrossRef]
- Ziller, A.; Trask, A.; Lopardo, A.; Szymkow, B.; Wagner, B.; Bluemke, E.; Nounahon, J.M.; Passerat-Palmbach, J.; Prakash, K.; Rose, N.; et al. Pysyft: A library for easy federated learning. Fed. Learn. Syst. Towards-Next-Gener. AI 2021, 965, 111–139. [Google Scholar]
- Ma, J.; Zheng, Y.; Feng, J.; Zhao, D.; Wu, H.; Fang, W.; Tan, J.; Yu, C.; Zhang, B.; Wang, L. {SecretFlow-SPU}: A performant and {User-Friendly} framework for {Privacy-Preserving} machine learning. In Proceedings of the 2023 USENIX Annual Technical Conference (USENIX ATC 23), Boston MA, USA, 10–12 July 2023; pp. 17–33. [Google Scholar]
- Bhadani, R. A Survey on Differential Privacy for SpatioTemporal Data in Transportation Research. arXiv 2024, arXiv:2407.15868. [Google Scholar]
- Zeng, Z.; Fang, Z.; Chen, L.; Gao, Y.; Zheng, K.; Chen, G. FedCTQ: A Federated-Based Framework for Accurate and Efficient Contact Tracing Query. In Proceedings of the 2024 IEEE 40th International Conference on Data Engineering (ICDE), Utrecht, The Netherlands, 13–16 May 2024; pp. 4628–4642. [Google Scholar]
- Benaissa, A.; Retiat, B.; Cebere, B.; Belfedhal, A.E. Tenseal: A library for encrypted tensor operations using homomorphic encryption. arXiv 2021, arXiv:2104.03152. [Google Scholar]
- Ali, M.; Kumar, A.; Choi, B.J. Power Quality Forecasting of Microgrids Using Adaptive Privacy-Preserving Machine Learning. In Proceedings of the International Conference on Applied Cryptography and Network Security, Abu Dhabi, United Arab Emirates, 5–8 March 2024; Springer: Berlin/Heidelberg, Germany, 2024; pp. 235–245. [Google Scholar]
- Keller, M. MP-SPDZ: A versatile framework for multi-party computation. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 9–13 November 2020; pp. 1575–1590. [Google Scholar]
- Foley, P.; Sheller, M.J.; Edwards, B.; Pati, S.; Riviera, W.; Sharma, M.; Moorthy, P.N.; Wang, S.h.; Martin, J.; Mirhaji, P.; et al. OpenFL: The open federated learning library. Phys. Med. Biol. 2022, 67, 214001. [Google Scholar] [CrossRef]
- Acar, A.; Aksu, H.; Uluagac, A.S.; Conti, M. A survey on homomorphic encryption schemes: Theory and implementation. ACM Comput. Surv. (CSUR) 2018, 51, 1–35. [Google Scholar] [CrossRef]
- Husnoo, M.A.; Anwar, A.; Chakrabortty, R.K.; Doss, R.; Ryan, M.J. Differential privacy for IoT-enabled critical infrastructure: A comprehensive survey. IEEE Access 2021, 9, 153276–153304. [Google Scholar] [CrossRef]
- Almanifi, O.R.A.; Chow, C.O.; Tham, M.L.; Chuah, J.H.; Kanesan, J. Communication and computation efficiency in federated learning: A survey. Internet Things 2023, 22, 100742. [Google Scholar] [CrossRef]
- Senol, N.S.; Baza, M.; Rasheed, A.; Alsabaan, M. Privacy-Preserving Detection of Tampered Radio-Frequency Transmissions Utilizing Federated Learning in LoRa Networks. Sensors 2024, 24, 7336. [Google Scholar] [CrossRef] [PubMed]
- Zeng, Z.; Li, Y.; Cao, Y.; Zhao, Y.; Zhong, J.; Sidorov, D.; Zeng, X. Blockchain technology for information security of the energy Internet: Fundamentals, features, strategy and application. Energies 2020, 13, 881. [Google Scholar] [CrossRef]
| Features and Capabilities of IDSs | Intrusion-Detection Schemes | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| [38] | [39] | [40,41] | [42] | [43] | [44,45] | [46] | [47] | [48] | [49] | [50] | |
| Identify Two-way/One-way MITM attacks | – | – | ◯ | – | – | – | ◯ | ◯ | ◯ | ◯ | ◯ |
| Identify ARP poisoning-based MITM attacks | ◯ | – | – | – | – | – | – | – | ◯ | ◯ | – |
| Identify eavesdropped packets | – | – | – | – | – | – | – | – | ◯ | ◯ | – |
| Identify MITM while intercepting | – | ◯ | ◯ | ◯ | ◯ | ◯ | ◯ | ◯ | ◯ | ◯ | ◯ |
| Identify attack victims | – | – | – | – | – | – | – | – | – | ◯ | – |
| Consider customer privacy | – | – | ◯ | – | – | – | ◯ | ◯ | – | ◯ | – |
| DP Approach | DP Mechanism | Algorithm | Tasks | Adversaries or Attacks Types | Privacy Parameters | Task Metrics | Dataset |
|---|---|---|---|---|---|---|---|
| DDP (2021) [83] | Laplace noise | Energy aggregation | NILM | Dishonest but non-intrusive | Accumulative error/Aggregation error | Precision, Recall, F1-score | 6 households real-world, Switzerland |
| RDP (2024) [84] | Gaussian noise | Neural Network | Classification (attack/normal) | Inference attacks | Privacy budget () against accuracy | Categorical cross-entropy loss, accuracy, F1-score | UNSW-NB15, NSL-KDD, and ToN-IoT |
| DPML (2019) [85] | Laplace noise with peak-factor | Energy aggregation | Demand Response | Eavesdropping, curious-but-honest utility/aggregator | Privacy budget () | Percentage error of kWh(%) | NREL |
| PPMM-DA (2023) [80] | Geometric and Laplace noise | Multidimensional energy aggregation | Load monitoring | Differential attack, collision attack, eavesdropping, active attack | Privacy budget () | Relative error | Mathematical model |
| DP Chi-square (2024) [82] | Gaussian noise | System state estimation | Anomaly detection | Stealth attack, FDI attack, untrusted third party | Privacy budget () | Area under the ROC (AUROC) | Values from mathematical model |
| PDP (2021) [81] | Local DP on trusted distance | Graph Theory | Energy Prediction | Correlation, collusion attacks | Privacy budget () | Root mean squared error (RMSE) | EPFL-Campus real-world |
| Synthetic Data Approach | ML Algorithms | Energy Tasks | Evaluation Metrices | Dataset |
|---|---|---|---|---|
| DP-SGD (2024) [88] | Faraday algorithm | Generate smart meter energy | Quantile values, accuracy, precision | Low Carbon London (LCL) |
| K-Mean (2018) [89] | Generative adversarial network (GAN) | Short-term prediction | MAPE | Pecan Street |
| R-GAN(2019) [86] | Recurrent generative adversarial network (R-GAN) | Load generation | MAPE, MAE | UCI-Energy, Building Genome |
| Bayesian NN (2019) [90] | Generative adversarial network (GAN) | System state estimation | MSE | IEEE-118, Pecan Street |
| ProfileSR-GAN (2022) [87] | GAN-based on maximum-a-posteriori | NILM | MSE, Peak load error (PLE) | Pecan Street |
| PDM (2024) [91] | Physics-informed diffusion model | Load and solar generation | t-SNE, QS, MAE, RMSE | Pecan Street |
| SMOTEENN (2021) [92] | AlexNet and light gradient boosting (LGB) | Electricity theft detection | AUC, recall, precision, F1-score | State grid corporation of China (SGCC) |
| Ref. | SG Domain | Privacy Concerns/Parameters | Contribution |
|---|---|---|---|
| (2022) [94] | Consumer billings | Routine, Appliance types and preferences | Shamir secret sharing-based SMPC with five key algorithms including setup, blinded reading generation, interpolation, and final reading calculation ensures secure energy consumption billing. The system assumes an honest-but-curious utility provider, while smart meters may be malicious, facing passive (peer or leader compromise) and active (malicious peer or leader behavior) attacks. |
| (2024) [97] | State estimation, optimal power flow | Measurement matrix | Efficient SMPC approach for Newton-Raphson method power flow analysis (PFA) leverages secret sharing, Cartesian formulation, and sparsity optimization. The system operates in semi-honest and malicious adversarial settings without relying on a Trusted Third Party. |
| (2024) [98] | Day-ahead energy forecasting | Global iteration, relative accuracy | Privacy-preserving distributed market mechanism using SMPC and the Shamir secret-sharing scheme employs the Consensus ADMM algorithm and a chance-constrained LinDistFlow model for an uncertainty-aware joint market of energy and reserves. A recovery scheme handles missing network measurements, supporting day-ahead energy balancing under a static, honest-but-curious setting. |
| (2021) [99] | Day-ahead energy-storage scheduling | Energy data breaches, computation and communication costs | SMPC framework for energy-storage sharing enables confidential cost-sharing and verifiable virtual net metering settlement without trusted third parties. It address risks from dishonest users, data misuse, and privacy breaches while balancing privacy protection and performance. |
| (2019) [100] | Transmission, Distribution fees balancing | Computation and communication costs | MPC-based protocol for secure smart metering data collection incorporates three aggregation algorithms: Naïve Aggregation (NAA), No Comparison Aggregation (NCAA), and Non-Interactive Aggregation (NIAA). It enables distribution, transmission, and balancing fee calculations using real smart metering data while considering malicious behavior from both internal and external entities, including grid operators and suppliers. |
| (2020) [101] | Energy market pricing | Individual profiles and incentives | Private Energy Market (PEM) ensures optimal pricing through a Nash Equilibrium-based Stackelberg game under a semi-honest adversarial model without a trusted third party. The approach maintains privacy, individual rationality, and incentive compatibility, addressing risks where local generation and demand data may reveal user consumption patterns. |
| (2024) [102] | Wind energy forecasts | Computation time, Spatial, and temporal patterns | Privacy-preserving ultra-short-term wind power-forecasting method using secure multiparty computation (MPC) and pwXGBoost, an encrypted variant of XGBoost operates under a semi-honest model and leverages real-world data from 27 wind farms in China, capturing nonlinear spatial and temporal correlations for improved prediction accuracy. |
| HE Approach | SG Domain | ML Approach | Security Concerns | Evaluation | Dataset |
|---|---|---|---|---|---|
| Pailler-based asymmetric (2022) [94] | Distributed Grid fault localization and energy forecasting | DNN | Inference, reverse engineering, eavesdropping | Computational complexity of DNN activation function, execution time | IEEE-68 bus system |
| Domingo-Ferrer (2017) [107] | Cloud-based billing | Load aggregation | Data integrity, availability | Long execution time | 15 min based Melbourne smart meters |
| CKKS-based (2023) [105] | Consumer smart meters | Load aggregation | Consumer behavior and absence event | Summation, variance, memory and time consumption | DAIAD project real-world |
| Elliptic curve (2018) [108] | Dynamic billing | Load aggregation | Confidentiality, integrity, authentication | Computation and communication overhead | Mathematical model |
| Fan-Vercauteren somewhat (2017) [109] | Energy forecasting | ANN with GMDH data imputation | Consumer behavior | performance cost in MSE, time in ms | Irish smart meter |
| Asymmetric (2017) [110] | Energy pricing | Fixed-point arithmetic aggregation | Consumer privacy and confidentiality | Computation time | Real-world Smart project |
| FL Approach | SG Task | Contribution |
|---|---|---|
| FedDiSa (2023) [124] | Fault and attack classification | Federated learning with secure and lightweight communication for power system state estimation and classification of disturbance and cybersecurity events in the SCADA sub-system nodes connected to IED nodes for data collection and Central control center for model aggregation. |
| Multi-task FL (2024) [125] | VPP energy prediction | Multi-task FL shows comparable optimization results as that of mathematical algorithms such as HBMO and TLBO in term of generation cost, while FL showed faster convergence than other mathematical ML approaches. |
| VMD-FK-SecureBoost (2023) [126] | Short-term load forecasting | VMD-FK-SecureBoost provides secure aggregation under distributed setup to address the data heterogeneity of highly variable energy client data. VMD extract the features of individual clients which is support by K-means clustering mechanism to aggregate the same weights of the cohort using secureboost ML forecasting algorithm. |
| FedUPS (2025) [127] | Anomaly detection | Centralized processing of security threat detections associated with the interconnected distribution network have the shortcoming of communication burdens, data leakage and performance degradation for real-time operations. FedUPS proposed a semi-supervised FL to dynamically aggregate the parameter with a thresold to filter the clients with poor data for a distributed power control system. |
| FedGrid (2023) [128] | Generation and load forecasting | Integration of both highly variable load and renewable energies make energy management a difficult task in a cyber-physical SG. FedGrid optimized the demand and supply management by predicting the corresponding load and generation of every component in the secure federated setup. |
| FedDRL (2023) [129] | Wind energy forecasting | FedDRL combines the deep learning with reinforcement approach to predict the ultra-short term prediction of wind farms which reluctant to share island data due to commercial liabilities. |
| dy-TACFL (2025) [130] | EV station energy prediction | dy-TACFL employs affinity propagation to adaptive clusters and predicts the energy of EV charging stations according to client behavior in a heterogeneous, time-varying environment. |
| PPML Technique | Computational Complexity | Communication Overhead | Suitability for IoT Devices |
|---|---|---|---|
| HE (2022/23) [139,140] | for circuit depth d; bootstrapping | Low (encrypted inference only) | Low (due to high computation and memory requirements) |
| SMPC (2020) [141] | rounds and cryptographic operations | High (multiple k rounds between m parties) | Moderate to Low |
| FL (2025) [142] | where E: epochs, C: clients, R: rounds | High (transmitting model weights per round) | Moderate (affected by communication and heterogeneity) |
| DP (2019) [85] | per SGD iteration (noise affects convergence speed) | Low | High (efficient but may impact model accuracy) |
| ZKP (2023) [143] | Depends on protocol; typically polynomial | Moderate (interactive protocols) | Moderate |
| Framework/Libraries | Description | DP | MPC | HE | FL | TEE |
|---|---|---|---|---|---|---|
| PySyft [144] | Open source python library supporting deep learning | ✓ | ✓ | ✓ | ✓ | - |
| SecretFlow [145,146,147] | Python (3.8–3.11) and C++ (14/17/20)-based libraries for privacy-preserving data intelligence and machine learning | ✓ | ✓ | ✓ | ✓ | ✓ |
| CrypTen [126] | Open source cryptographic protocol by Meta | - | ✓ | - | - | - |
| TenSEAL [148] | OpenMined privacy framework for deep learning models | - | - | ✓ | - | - |
| TensorFlow Federated [149] | Open source framework by Google Inc., for federated deep learning networks | ✓ | - | - | ✓ | - |
| MP-SPDZ [150] | Open source library based on SPDZ-2 with 34 MPC protocols | - | ✓ | - | - | - |
| PaddleFL [150] | Open source federated framework integrated with PaddlePaddle DL platform and other PPML techniques | ✓ | ✓ | ✓ | ✓ | - |
| OpenFL [151] | Open source framework to run distributed learning under Intel SGX environment | - | - | - | ✓ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, M.; Suchismita, M.; Ali, S.S.; Choi, B.J. Privacy-Preserving Machine Learning for IoT-Integrated Smart Grids: Recent Advances, Opportunities, and Challenges. Energies 2025, 18, 2515. https://doi.org/10.3390/en18102515
Ali M, Suchismita M, Ali SS, Choi BJ. Privacy-Preserving Machine Learning for IoT-Integrated Smart Grids: Recent Advances, Opportunities, and Challenges. Energies. 2025; 18(10):2515. https://doi.org/10.3390/en18102515
Chicago/Turabian StyleAli, Mazhar, Moharana Suchismita, Syed Saqib Ali, and Bong Jun Choi. 2025. "Privacy-Preserving Machine Learning for IoT-Integrated Smart Grids: Recent Advances, Opportunities, and Challenges" Energies 18, no. 10: 2515. https://doi.org/10.3390/en18102515
APA StyleAli, M., Suchismita, M., Ali, S. S., & Choi, B. J. (2025). Privacy-Preserving Machine Learning for IoT-Integrated Smart Grids: Recent Advances, Opportunities, and Challenges. Energies, 18(10), 2515. https://doi.org/10.3390/en18102515








