1. Introduction
Virtual power plants (VPPs) represent complex cyber-physical systems comprising various distributed energy resource (DER) units, microgrids, energy storage systems (ESSs), loads, conventional power plants, and electric vehicles, interconnected through a communication network. To control VPPs, both centralized and distributed mechanisms have been implemented. Centralized control faces a significant challenge related to high data analysis and calculation costs [
1]. Among distributed control approaches, federated learning (FL) has shown promise, offering enhanced reliability and scalability compared to centralized control [
2]. However, the distributed nature of FL renders VPPs more susceptible to physical and cyber anomalies, including poisoning attacks and information compromise in the network [
3,
4]. These anomalies pose serious threats, leading to system instability and synchronization issues during operation [
5]. Therefore, to ensure the smooth and secure functioning of VPPs under such adverse conditions, an effective anomaly mitigation strategy is imperative.
FL is a decentralized learning approach where various clients, including Internet of Things (IoT) devices, electrical generators, and more, interact with a central service provider like Google or an energy management system (EMS) of a VPP [
2]. Operating on separate datasets, these clients collaboratively train a global model while maintaining data privacy. This safeguarding of private data aligns well with evolving privacy regulations like the General Data Protection Regulation (GDPR), leading to its widespread adoption. A recent innovation in this field is FL-trust [
6], a Byzantine-robust FL technique that introduces trust at the server level. Here, a curated “root dataset” forms the basis for server-side training, alongside updates from individual clients. Despite its strengths, FL-trust’s effectiveness is limited when dealing with non-independent and identically distributed (non-IID) datasets, as encountered in scenarios such as VPPs [
7].
The conventional approach to VPP modeling using FL has showcased significant advancements in decentralizing the modeling process, thereby leading to improved accuracy, computational efficiency, and the facilitation of optimal power generator dispatch. Additionally, both traditional FL and FL-trust are susceptible to cyber-attacks [
8,
9], primarily stemming from inherent vulnerabilities within their communication networks [
10].
Existing mitigation systems employed in VPPs, such as the proportional-integral (PI)-based mitigation system [
11], exhibit sluggish response times, necessitate a heightened accuracy, and cause voltage deviation. PI controllers are known for their straightforward structure, incorporating proportional and integral components that facilitate efficient system regulation. In attack mitigation scenarios, a PI controller can be employed to regulate the system response to deviations caused by cyber-attacks or disturbances. The integral component helps eliminate steady-state errors, and the proportional component contributes to a quick response to sudden changes. However, it is important to note that traditional PI controllers might have limitations when dealing with complex and dynamic systems, especially in the presence of rapidly evolving cyber threats. Consequently, an urgent imperative emerges to address these security concerns comprehensively and to formulate robust strategies that preserve the integrity and privacy of the VPP modeling process within the overarching framework of FL and FL-trust methodologies [
12].
In VPPs and FL-based systems, prevailing anomaly mitigation often relies on model-based approaches, requiring accurate system models and architectural knowledge [
3]. However, large-scale VPPs [
13] face challenges in deriving precise mathematical models, making learning-based tools like artificial neural networks (ANNs) a viable alternative for cyber anomaly mitigation. Also, ANNs can make FL-trust compatible with non-IID datasets, as suggested for future study in [
8]. The nature of non-IID datasets is characterized by disparities in class representation, data volumes, and distributions across localized client datasets. This unaddressed gap in the existing body of literature underscores the need for dedicated inquiries aimed at devising resilient and efficient mechanisms that harness ANN-based strategies within FL-trust.
Based on the above background, this paper proposes innovative mechanisms that seamlessly integrate FL-trust with ANNs to mitigate cyber anomalies in a VPP system. The aim is to effectively manage non-IID datasets prevalent in VPP scenarios, thereby enhancing the accuracy of global models in the face of data heterogeneity, class imbalances, and distribution variations across localized client datasets.
This paper presents some noteworthy contributions. Firstly, it introduces an innovative ANN-based FL-trust technique that effectively addresses cyber anomalies, enhancing the security and reliability of the system. The proposed control method is demonstrated to maintain the desired system operation despite poisoning attacks in voltage communication links.
Secondly, this research achieves the robustness of the voltage in an ANN-based FL-trust process by generating diverse training data that represent varying load scenarios, enabling accurate performance evaluations under time-varying cyber anomalies.
Thirdly, this paper presents an interpretable framework for ANN models employed in the FL-trust process, allowing for a comprehensive assessment of input impacts on model performance.
This study validates the effectiveness of the proposed ANN-based secondary control for a VPP through real-time simulations on the real-time HOMER simulator, providing valuable insights into its performance. By conducting various case studies and employing essential metrics such as accuracy measurements and voltage regulation, this research determined the proficiency of the trained ANNs in achieving the desired control outcomes. Overall, the contributions of this work advance the understanding and application of ANN-based FL-trust methods for mitigating cyber anomalies and enhancing the operational reliability of VPP systems. The suggested method showcases its exceptional capability to maintain regular VPP functioning in the presence of cyber anomalies, surpassing a PI-based mitigation system in terms of accuracy (i.e., difference of 0.0001 per unit) and speed of detection. Specifically, the detection rate is improved by 64.3%, with the proposed method achieving less than 1 s and the PI-based approach achieving 2.8 s.
The paper is structured with a systematic organization that unfolds the complexities of cyber anomaly mitigation in VPPs. In
Section 2, the fundamental aspects of the VPP system are elucidated, laying the groundwork for a comprehensive understanding of the ensuing mitigation strategies.
Section 3 delves into the novel approach utilizing ANNs for cyber anomaly mitigation. This section provides a detailed exposition of the proposed methodology, emphasizing the integration of the FL-trust adaptation to enhance the efficacy of the ANN-based approach. In contrast,
Section 4 explores the conventional PI controller as a comparative mitigation method. This section discusses the limitations and drawbacks of this traditional approach in contrast to the proposed ANN-based method. Finally,
Section 5 presents the outcomes of the simulations conducted to evaluate the performance of both methods.
2. System Modeling and Formulation
The VPP devised for this research is structured as a composite system, comprising both a physical layer and a cyber layer [
4]. The physical layer, analogous to conventional VPP configurations, encompasses a variety of components, namely DER units, microgrids, ESSs, loads, conventional power plants, and electric vehicles, all interconnected through a communication network [
14,
15]. On the other hand, the cyber layer encompasses the communication protocols that facilitate the exchange of voltage and frequency information within a distributed cooperative control architecture [
16], as depicted in
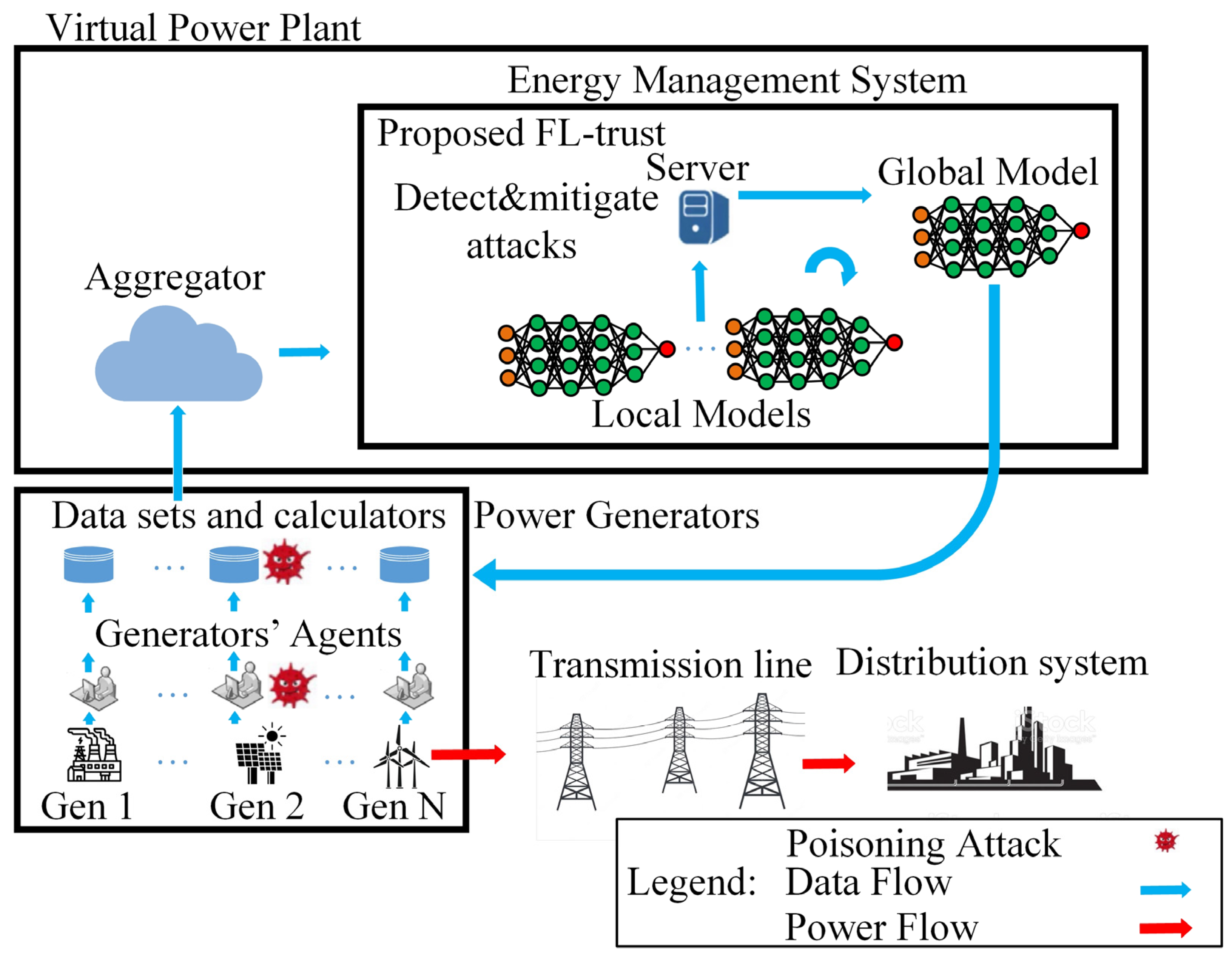
Figure 1. This figure depicts the comprehensive functional block diagram of a VPP employing FL in the presence of potential poisoning attacks. The diagram not only outlines the standard operational components of the VPP but also incorporates elements specifically designed to detect, mitigate, and adapt to poisoning attacks within the FL framework. This figure provides a holistic view of the VPP’s architecture, showcasing its resilience and adaptability to cybersecurity challenges posed by poisoning attacks.
The FL process is intricately integrated into the energy management system (EMS) of a VPP, overseen by the VPP’s decision-maker. The FL protocol extends its influence across various components within the VPP, utilizing the comprehensive access granted by the energy management system. This expansive reach ensures that the FL framework can effectively tap into and optimize various facets of the VPP, allowing for collaborative and distributed learning across the interconnected energy infrastructure.
The local implementation of the primary controller at each electrical generator is achieved through a conventional droop control technique, establishing the correlations between the frequency (
), reactive power (
), active power (
), and voltage (
). In this paper, we have tackled the potential ambiguity related to the acronym “
F”, conventionally denoting both frequency and functions, particularly objective functions. To mitigate any confusion, we have assigned “
W” to represent frequency and retained “
F” for functions. The voltage and frequency droop characteristics can be described mathematically as:
where
and
represent the desired primary frequency and voltages, respectively. The parameters
and
signify the reactive and active droop coefficients, respectively. In order to mitigate voltage and frequency deviations from their nominal values induced by the primary control, a distributed cooperative control strategy [
4] is employed.
The control protocols pertinent to this study are implemented through a distributed communication network. Secondary control establishes reference values (
and
) for the primary control, aiming to synchronize the voltage (
) and frequency (
) of each power generator unit within the power grid with their respective reference values. Mathematically, this synchronization is expressed as follows:
Depending on the communication protocol [
17], it may be necessary for the nth generator in the VPP to share its voltage information over the communication network. In scenarios where only one generator has access to the reference
v*, a weight factor known as pinning gain (
) is employed to achieve the cooperative control objective, which is defined in terms of the local neighborhood tracking error (
). The expression for
is given as:
where
represents the set of neighboring power generators of the nth generator,
denotes the elements of the adjacency matrix, and only one generator has a nonzero
value. Similarly, for distributed secondary frequency control, the auxiliary control input (
) is defined as:
where
represents the coupling gain. For a more comprehensive understanding of the distributed cooperative control architecture, further details can be found in [
18].
Subsequently, this paper investigates the FL and FL-trust process in the VPP and related necessary modifications, also the cyber anomalies and a description of these anomalies are provided in the subsequent sections.
2.1. Federated Learning Process in a VPP
The FL process can be succinctly described as a sequential execution of three key steps [
19,
20], as illustrated in
Figure 1:
Step I: Synchronization of the global model with clients: In this initial step, the server disseminates the current global model (the first global model is generated based on the previous year’s recordings of electrical generators) to the clients (electrical generators of the VPP) (either to all clients or a designated subset of them).
Consider n clients, each with their local dataset
, i = 1, 2, …,
n. Combined as
, these datasets contain training examples drawn from an unknown distribution
. The clients collaborate, aided by a service provider, to develop a shared global model. The optimal global model
is determined by solving
, where
represents the expected empirical loss of
over joint dataset
D. Typically, due to the complexity of evaluating expectations, the global model is trained by minimizing empirical loss; i.e.,
gives the learned global model [
21].
Step II: Training of local models: Each client engages in the training of a local model by fine-tuning the received global model using its local training dataset (
). Specifically, the
i-th client formulates an optimization problem as
, where
represents the client’s local model [
2]. To initialize the process, the client adopts the global model as its local model and utilizes stochastic gradient descent to iteratively update the local model for one or more iterations. Consequently, each client communicates its local model update (
) to the server, signifying the disparity between its local model and the current global model [
22].
Step III: Updating the global model via aggregation: In the final step, the server aggregates the received local model updates to calculate a global model update (
g) according to a predefined aggregation rule. Subsequently, the server updates the global model (
) by incorporating the global model update with a global learning rate (
α), i.e.,
, where the
is the global learning rate [
23].
2.2. Poisoning Attack in the Federated Learning Process of a VPP
Poisoning attacks represent a distinct category within the realm of adversarial attacks, with a unique focus on the training phase of machine learning systems. These attacks, often referred to as data poisoning attacks, are strategically crafted to contaminate the training data, posing a significant threat to the integrity of the learned model [
24]. In essence, these malicious strategies involve the injection of tainted or falsified data points into the training dataset, with the explicit intention of distorting the learning process. By infiltrating the foundational data used for model training, adversaries seek to skew the model’s understanding of patterns and relationships within the dataset. This insidious manipulation can lead to severe consequences, including erroneous predictions and compromised decision-making capabilities.
Data poisoning attacks, while sophisticated, are a tangible manifestation of the vulnerabilities inherent in machine learning systems. As the technology landscape continues to evolve, defending against such attacks is becoming paramount. Comprehensive research and innovative defenses are crucial to fortifying machine learning algorithms against these insidious strategies, ensuring the reliability and trustworthiness of artificial intelligence systems in various applications [
24].
2.2.1. Attack Model
In this study, the attack model adheres to the approach followed in previous research [
3,
25,
26]. The attacker assumes control over specific malicious clients, which may comprise either spurious clients introduced by the attacker or authentic clients that the attacker has compromised. Importantly, the server itself remains uncompromised. These malicious clients possess the capability to submit arbitrary local model updates to the server during each iteration of the FL training process. Typically, the attacker possesses partial knowledge about the FL system, including information about local training data and local model updates on the malicious clients, the loss function utilized, and the learning rate.
In the context of this study, the cyber anomalies target the communication layer of the VPP by introducing false data or by compromising the information exchange within the network [
27]. The implementation of a poisoning attack involves injecting false data into the voltage and frequency information transmitted between neighboring electrical generators, specifically meant for the distributed secondary controller. Consequently, the feedback signal of the controller can be characterized as follows:
where
represents the feedback signal after the attacker injects false data
(t) into the controller’s nth normal feedback signal [
2]. We consider
as the RMS voltage at the slack bus equal to
in Equation (3), but it can be the frequency of the system equal to
in Equation (4).
The attack proposed in this study is characterized by a nonperiodic nature, whereby it is initiated by injecting a constant multiple of the desired signal
into
at a specific moment during the system’s operation, as depicted below:
2.2.2. Detection System
The FL-trust method functions as a highly efficient means to detect poisoning attacks within the EMS of a VPP, as depicted in
Figure 1. This detection mechanism shares a resemblance with residual detection methods, where FL-trust systematically assigns a trust score (TS) to each local model update based on its directional alignment with the corresponding server model update. Formally calculated as the residual error function, representing the similarity between the local and server model updates, the TS plays a pivotal role. We specifically employ the widely used rectified linear unit (ReLU) operation for thresholding. Formally, our trust score (
) is articulated as follows:
where
represents the trust score for the
i-th local model update
and
denotes the cosine similarity between
and server model update
, expressed as
. The ReLU function is mathematically defined as:
The system promptly recognizes discrepancies in the local models of identical generators, signaling a potential poisoning attack. For a comprehensive understanding of this detection system, the algorithm and detailed flowchart can be found in [
8].
3. Proposed ANN-Based Attack Mitigation Method
In this study, we employ a single-layer ANN to produce reference voltages for the primary controllers.
1. Input layer: The input layer is the initial stage of the ANN, comprising 13 nodes. These nodes represent crucial information related to voltage and frequency within the network.
2. Hidden layer: A hidden layer, consisting of 10 nodes, follows the input layer. This layer processes the information from the input layer through its nodes.
3. Output layer: The final stage is the output layer, which contains eight nodes. Each node in this layer corresponds to the reference outputs for the individual electrical generator units.
The architecture and configuration of the ANN, as described in these layers, are essential for understanding how the network processes and produces outcomes based on the given inputs as it is illustrated in
Figure 2 for this specific system. The configuration of ANN layers is designed based on the specific structural characteristics of the VPP. The initial layer serves as the input layer, representing the generators’ powers. The eight nodes encompass generator agents responsible for formulating the generators’ local model. The 13 nodes are shaped by a number of buses in the power grid. In essence, our study delved into 8 DERs and 13 bus network buses. Nevertheless, more complex VPPs can leverage a similar methodology tailored to their specific structure and objective functions. The mathematical model of the ANN is defined as follows:
where
represents the model output,
denotes the model input at a discrete time interval
,
denotes the input memory order, and
represents the output memory order. Assuming a delay term of
, the model takes the following form:
which can be expressed in vector form as:
where boldface letters
and
represent vectors for output and input, respectively. The nonlinear mapping function
is approximated using a standard multilayer perceptron network. The EMS uses the aggregated
to update the global model:
where
represents local model changes considering the local model in the previous iteration. Also,
represents local changes in generators
. After updating the global model
T times, the algorithm will stop. The data on generator i can be denoted as:
where
and
are the j-th input sample and its corresponding label showing the pattern type, respectively. In different datasets, the labels may take various forms. In this paper, the labels show the active power level in generators and on/off states. All generators have five levels. Level zero means the generator is off, and level four indicates the generator’s operation is at full load. Also,
is the total number of local training samples in generator
i.
The proposed ANN was introduced to overcome the non-IID nature of generators’ datasets. The neural network model
was implemented to create the reference voltage as the generator’s local model
from
j samples
. Also,
is the error function of data on generator
i, which shows the prediction error of the model for
. The error function is defined as follows:
The training phase of the generators’ agents performs the minimization of the error function via the gradient descent (GD) optimization algorithm as follows:
where
represents the learning rate as the gradient descent step size and
is the epoch of local training. After some local training, the generator obtains a model for
.
The proposed ANN-based mitigation method is demonstrated in Algorithm 1. In refining the algorithm, a meticulous tuning and optimization procedure was executed to enhance its efficacy. The initial step involved a thorough analysis of the algorithm’s performance metrics and its response to various inputs. This analysis helped identify key algorithmic parameters that significantly influenced its behavior. Subsequently, a combination of manual adjustment and automated optimization techniques were employed. Manual tuning involves fine-tuning parameters iteratively based on the algorithm’s output and observed behavior. Simultaneously, an automated optimization method, gradient descent, was implemented to systematically explore the parameter space and identify optimal configurations. The objective was to minimize the error function. The tuned parameters were rigorously validated using benchmark datasets and performance metrics to ensure the algorithm’s improved effectiveness in handling non-IID datasets and its generalization across various contexts.
| Algorithm 1 The proposed ANN-based mitigation method for VPPs |
|
5. Simulation Results and Discussion
This paper implicates the proposed FL approach to solve the scheduling dispatch problem of generators located in the VPP. All the generators were used for the training and testing process. The datasets for generators are from the National Aeronautics and Space Administration (NASA) and are available online:
https://power.larc.nasa.gov (accessed date: 1 January 2024). This paper used HOMER Pro (available online:
https://www.homerenergy.com/products/pro/index.html (accessed date: 1 January 2024)) for simulations, which is compatible with the mentioned datasets.
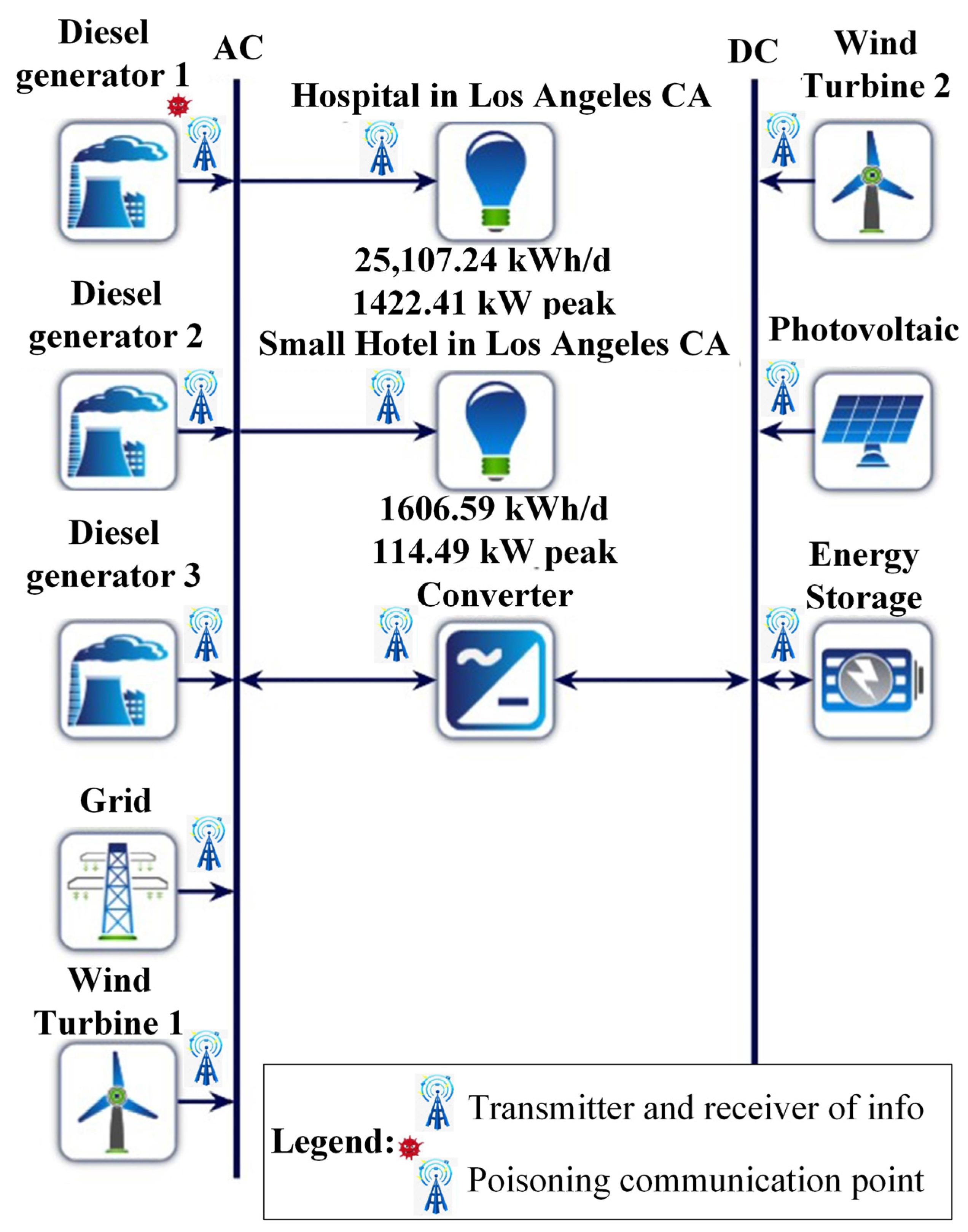
In this paper, we delve into a comprehensive case study, illustrated in
Figure 2, that centers around a VPP. This intricate VPP configuration comprises two diesel generators, a wind turbine, an energy storage system (ESS), a photovoltaic (PV) unit, and a microgrid housing both a diesel generator and a wind turbine. The technical specifications of these generators are meticulously outlined in
Table 1, offering a detailed overview of their capabilities and capacities. The production column illustrates the optimal proportion for electricity generation by generators. The remaining approximately 31.9166% represents grid purchases. For a deeper understanding of the VPP setup, including its intricate components and functionalities, readers are encouraged to refer to the comprehensive details provided in reference [
3]. This case study not only serves as an essential focal point for our research but also offers valuable insights into the integration and optimization of diverse renewable energy sources within the framework of a VPP.
5.1. Impact of Poisoning Attacks on the FL-Trust Approach in VPPs
In our study, we have conducted a thorough analysis of FL-trust within a VPP context, with the primary objective of minimizing the cost function associated with this system. The outcomes of this analysis are meticulously presented in our research findings.
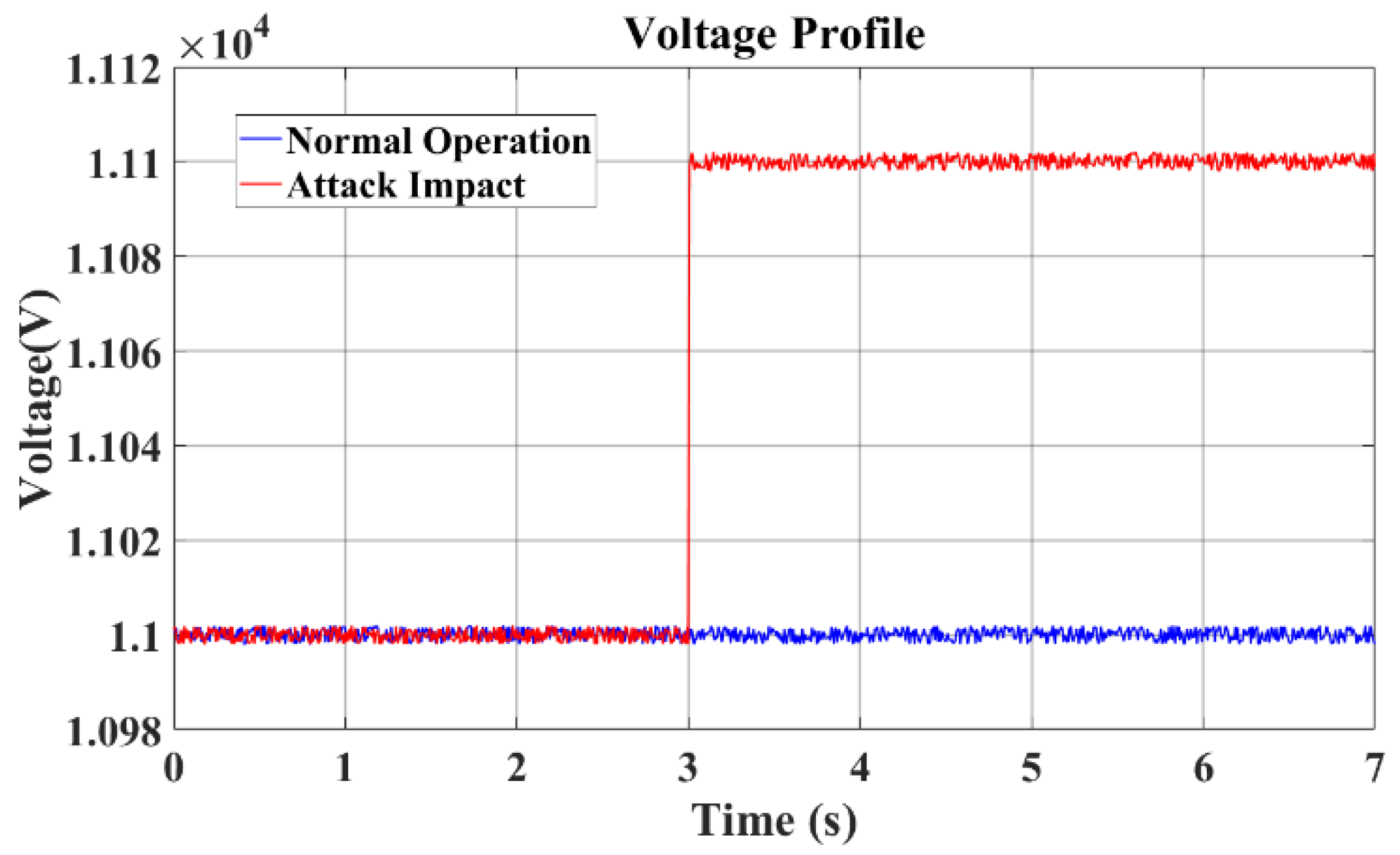
Figure 3, a visual representation of our results, showcases the root mean square (RMS) voltage profile. This profile provides a detailed insight into the RMS voltage levels within the system, offering a comparative perspective between normal operational states and those impacted by external attacks. By studying this visual representation, we gain a comprehensive understanding of how the system’s voltage levels fluctuate under different conditions, shedding light on the effectiveness of FL-trust in maintaining a stable and secure operation within the VPP framework. These findings not only contribute significantly to our understanding of VPP dynamics but also pave the way for enhanced strategies in managing voltage stability during various operational scenarios.
In our simulation, we systematically applied Equation (6) to inject fabricated data into the voltage communication links of generators, specifically focusing on the communication link associated with diesel generator 1. This experiment was designed to simulate a poisoning attack scenario. At t = 3 s, a poisoning attack was initiated with the parameter γ set to 1.5. The attack continues after t = 3 s. Prior to this attack (t < 3 s), the VPP functioned under normal operational conditions. Following the initiation of the attack, the VPP’s performance was monitored and compared with its pre-attack state to gauge the impact of the poisoning attack.
The simulation results, visually represented in
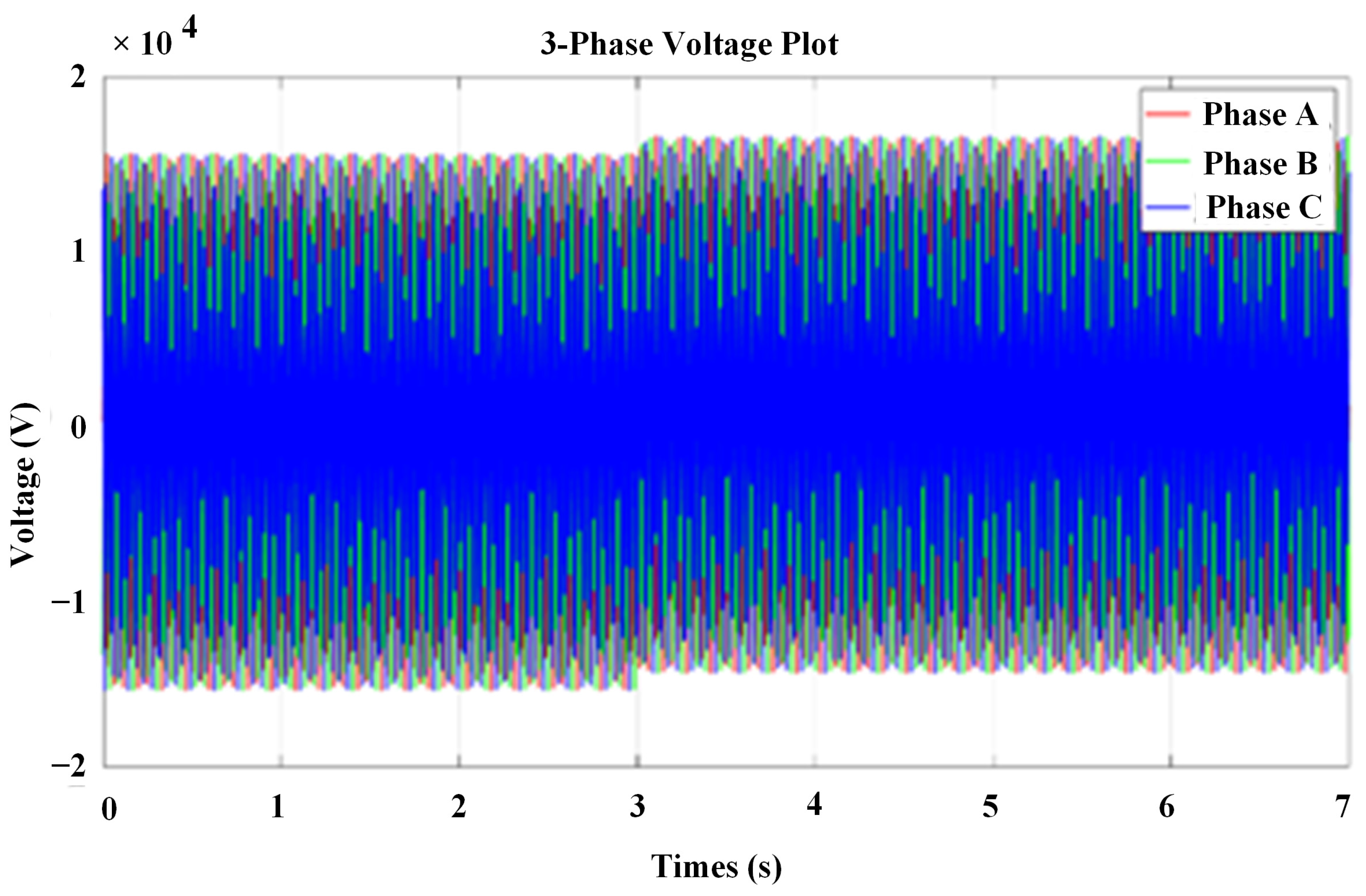
Figure 3, provide a clear depiction of the alterations in voltage levels induced by the proposed poisoning attack. This graphical representation highlights the significant changes in the VPP’s voltage characteristics post-attack, illustrating the attack’s disruptive influence on the system. Furthermore, similar observations were made for the three-phase voltage, as evidenced in
Figure 4. In this figure, the attack is initiated at t = 3 s, leading to a voltage deviation. The attack persists continuously after the third second. These findings serve as crucial evidence of the attack’s implications on the VPP’s overall performance and underscore the importance of understanding and mitigating such cybersecurity threats in power systems. Through these simulations, we gain valuable insights into the vulnerabilities of the VPP framework and emphasize the need for robust security measures to ensure the resilience and stability of power systems in the face of potential attacks.
5.2. Effectiveness of the Proposed ANN-Based FL-Trust Mitigation Approach
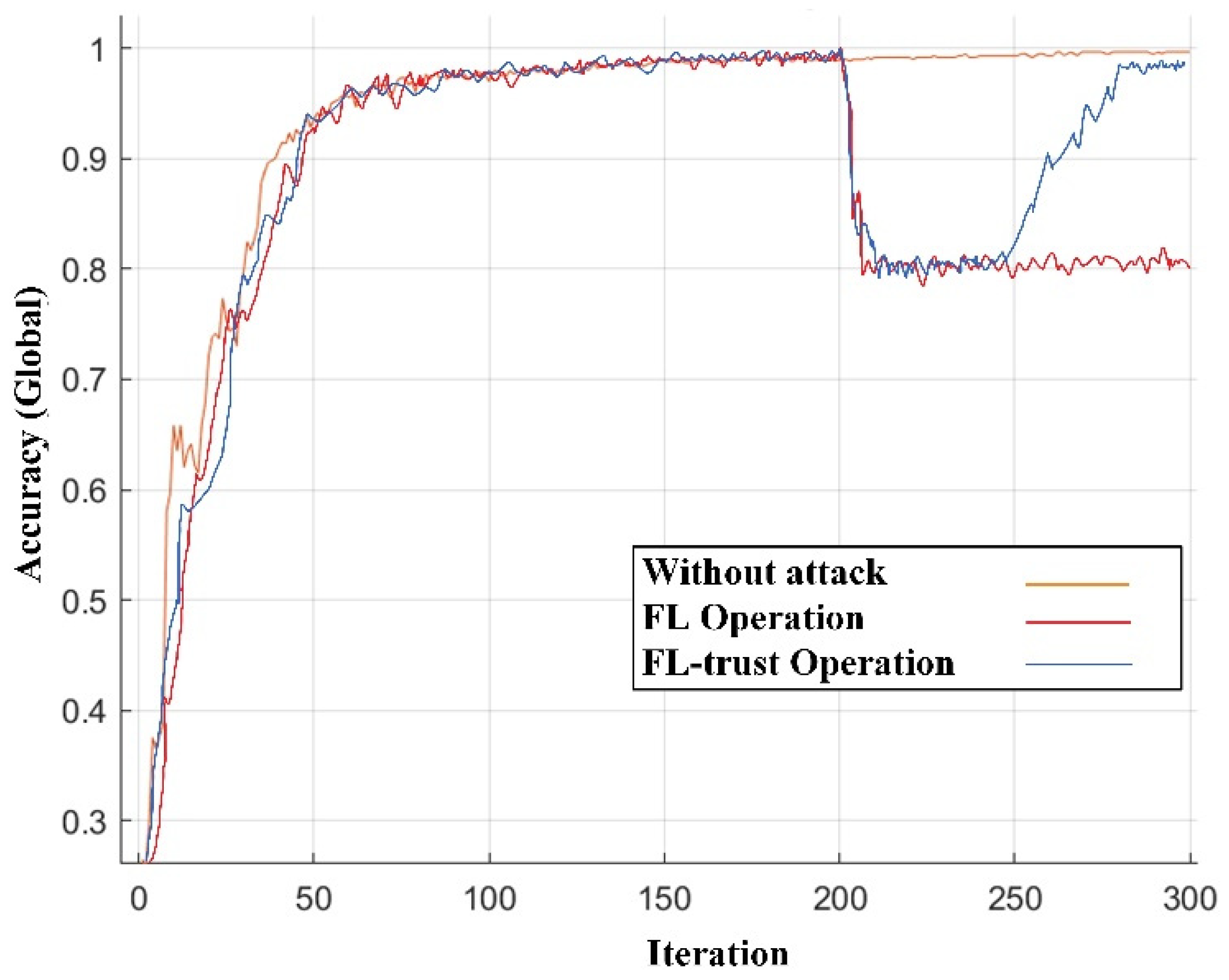
In this work, we conducted a comprehensive evaluation of the novel ANN-based FL-trust mitigation system. This innovative approach was meticulously compared to the conventional FL control method currently in use. The research findings, summarized in
Figure 5, provide a compelling visual representation of the comparative performance. The figure exhibits four zones. Initially, iterations 0 to 150 illustrate the system’s startup operation. Subsequently, from iteration 150 to 200, the normal operation of the system is represented. Following that, from iteration 200 to 250, the detection of the continuous poisoning attack occurring after iteration 200 by FL-trust is demonstrated. Lastly, iterations 250 to 270 denote the operations of FL-trust to mitigate the attack.
Under normal operational conditions, the proposed ANN-based FL-trust system exhibited a remarkable accuracy, achieving an impressive 0.98 per unit accuracy level. This showcases the system’s robustness and reliability in maintaining accuracy during regular operations. More notably, during our analysis of a poisoning attack scenario initiated at iteration 200, the proposed system effectively mitigated the attack within a mere 70 iterations. This rapid response time underscores the agility and efficiency of the ANN-based FL-trust approach in counteracting malicious attacks, thereby safeguarding the virtual power plant’s performance and voltage characteristics.
These results illuminate the substantial superiority of our proposed ANN-based FL-trust approach over the existing FL-based control method. By offering a high level of accuracy and swift mitigation capabilities, the ANN-based system is proven to be a significant advancement in fortifying a VPP against cyber threats. This research not only highlights the innovative strides made in power system security but also provides invaluable insights into the future of cybersecurity measures within the realm of energy management.
5.3. Performance Comparison of the Proposed ANN-Based Mitigation Approach with a PI-Based Approach
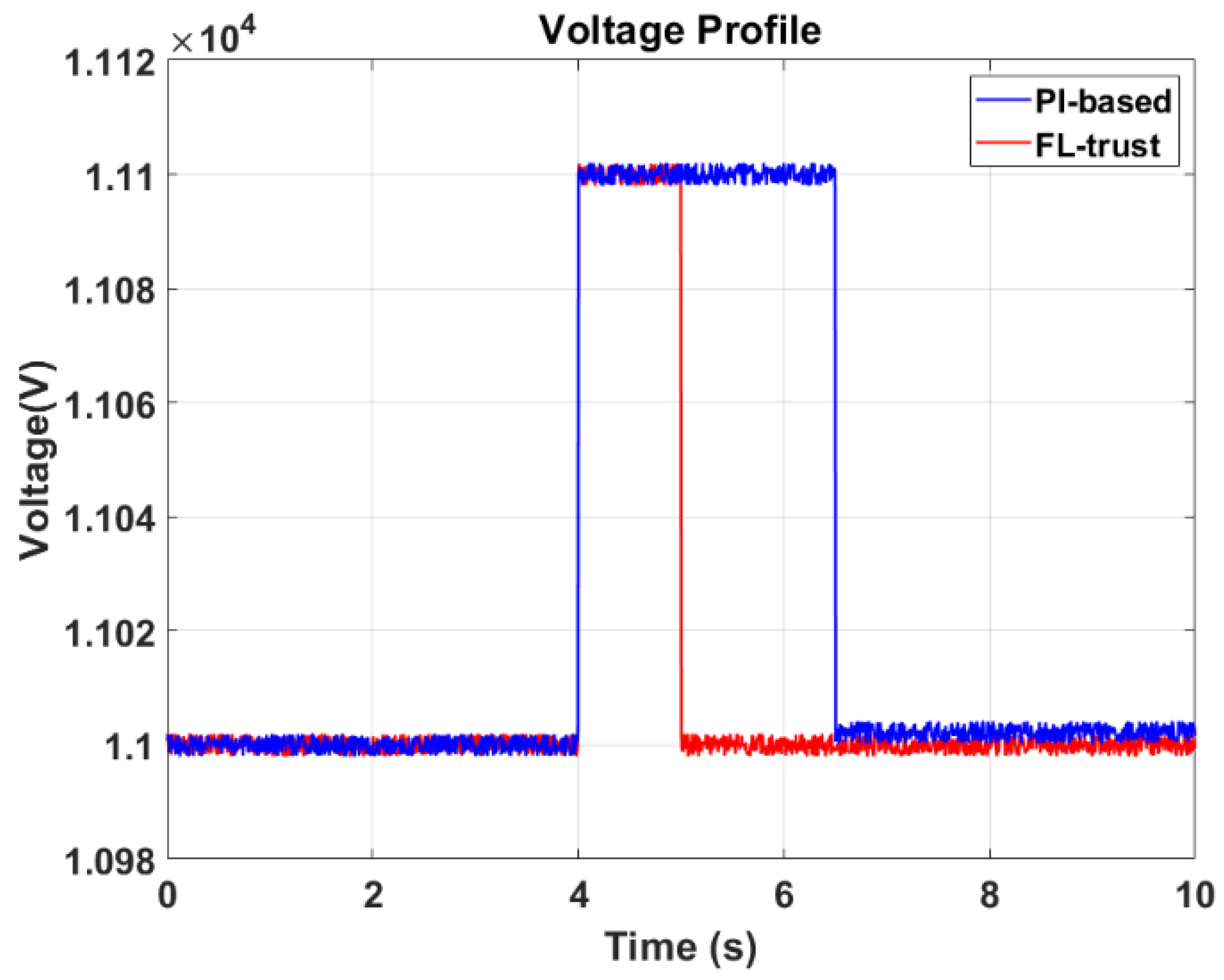
To comprehensively assess the performance of our proposed FL-trust approach, we conducted a direct comparison with the conventional proportional-integral (PI)-based mitigation system, a widely utilized method in similar contexts. This comparison is crucial in understanding the nuanced differences in mitigation capabilities under attack conditions. The results, as visually presented in
Figure 6, illuminate a significant contrast in response dynamics between the two systems. FL-trust detects and mitigates the attack in approximately 70 iterations, while the PI-based method requires about 200 iterations, highlighting the superior calculation speed of FL-trust.
At the critical 4 s mark, an attack was initiated, setting the stage for a real-time evaluation of the mitigation mechanisms. The FL-trust approach swiftly demonstrated its agility, promptly detecting and effectively countering the attack. In stark contrast, the PI-based system exhibited a comparatively delayed and less precise response, indicating its limitations in swiftly mitigating cyber threats in high-stress scenarios.
It is noteworthy that Fl-trust, like other learning processes, relies heavily on the quality and sufficiency of the training data. If the training data are insufficient or lack representativeness of the underlying patterns, the FL-trust process may face challenges in accurately learning and adapting to the system dynamics. However, having some trusted patterns causes it to operate better than conventional FL in these cases.
The FL-trust method is a robust approach to enhancing the security of VPPs by effectively mitigating various types of cyber-attacks. One of its primary advantages lies in its ability to detect and counteract poisoning attacks within the EMS of the VPP. By assigning trust scores to local model updates and normalizing them based on their alignment with the server model update, FL-trust excels in handling non-IID datasets, a common challenge in VPP contexts. However, it is essential to note that FL-trust, like any method, has its limitations. The approach might face challenges in scenarios where training data are insufficient. Moreover, while FL-trust demonstrates efficacy against poisoning attacks, its performance in countering other types of cyber threats needs further exploration.
In comparison to traditional FL and other defense methods, FL-trust stands out for its resilience in the face of non-IID datasets, providing a superior performance. The method showcases an adept mechanism for managing data heterogeneity, leading to an enhanced accuracy in global models. Contrastingly, conventional FL may struggle with the intricacies of non-IID datasets. Additionally, FL outperforms a traditional PI-based mitigation system, offering a better accuracy and detection rate. As the field of cybersecurity in VPPs evolves, ongoing research and exploration are vital to further refine and optimize defense mechanisms against a broader spectrum of cyber threats.
Crucially, post-mitigation, the FL-trust system seamlessly restored the system to its original state, showcasing its accuracy and effectiveness in neutralizing the threat while ensuring the system’s stability. This outcome underscores the robustness and reliability of the FL-trust approach in real-world situations, emphasizing its superiority over traditional methods like PI control.
These results not only validate the efficacy of our FL-trust approach but also pave the way for future advancements in cyber-resilient energy systems. By highlighting its precision, agility, and ability to restore normalcy swiftly, this research contributes significantly to the evolving landscape of power system security, offering a promising path toward enhanced cybersecurity protocols within the realm of energy management.