Artificial Neural Network Controller in Two-Area and Five-Area System with Security Attack and Game-Theory Based Defender Action
Abstract
1. Introduction
2. Materials and Methods
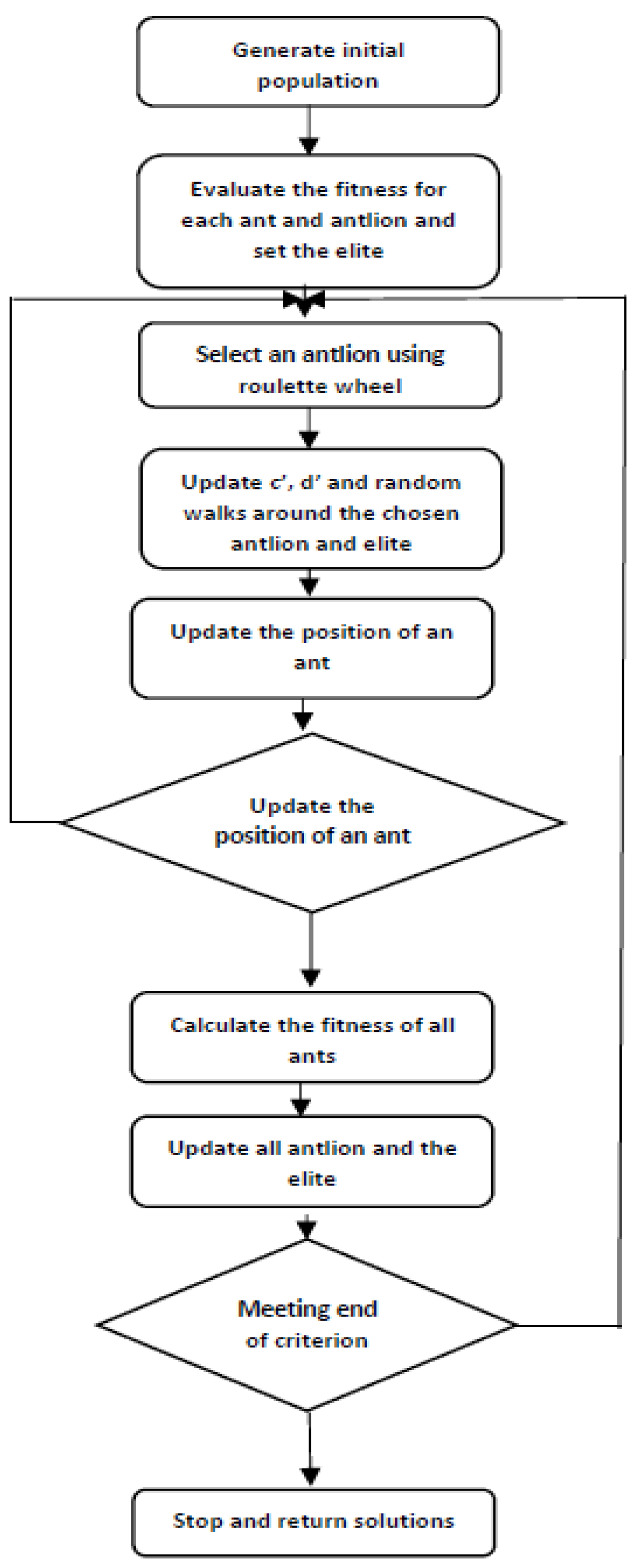
| Algorithm 1. ALO algorithm | |
| 1: | Random initialization of ant(X(t)) is performed ( and values are the vectors of X(t)). |
| 2: | Calculate the fitness (after running the LFC the setting time is taken) of ants and antlions. |
| 3: | The elite identification is performed from the best antlion (determined optimum Kp and Ki). |
| 4: | Check for the satisfaction of termination criteria for ants of each type. Choice of an antlion using a Roulette wheel. c and d are updated using The randomized walk and normalization are performed using the equation below. walk of the i-th variable, is the minimum of the i-th variable at the t-th iteration, and indicates the maximum of the i-th variable at t-th iteration. Additionally, is the random walk around the antlion selected by the roulette wheel at t-th iteration, is the random walk around the elite at t-th iteration, and indicates the position of i-th ant at t-th iteration End for loop. For all the ants, calculate the fitness. If the ant is fitter than other ants, stack that ant as the elite one. End while. |
| 5: | Return elite |
2.1. Applying an Artificial Neural Network (ANN) Controller in the Place of an ALO-PI Controller
2.2. Attacks Applied in LFC
2.2.1. Constant Injection
2.2.2. Injecting the Bias
2.2.3. Overcompensation
2.2.4. Negative Compensation
2.3. Preliminary Defenses
2.3.1. Saturation Filter
2.3.2. Redundancy
2.3.3. Detection
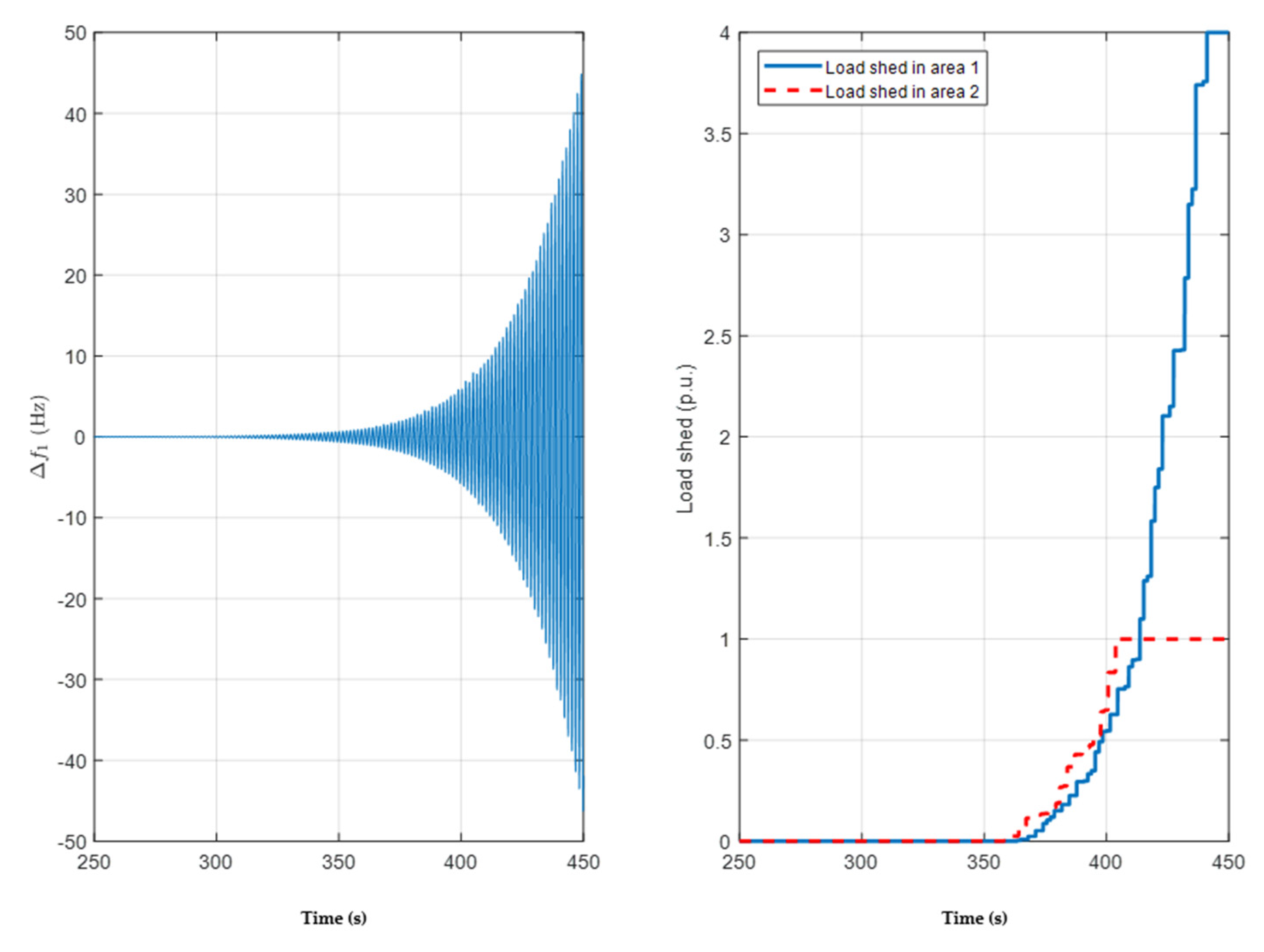
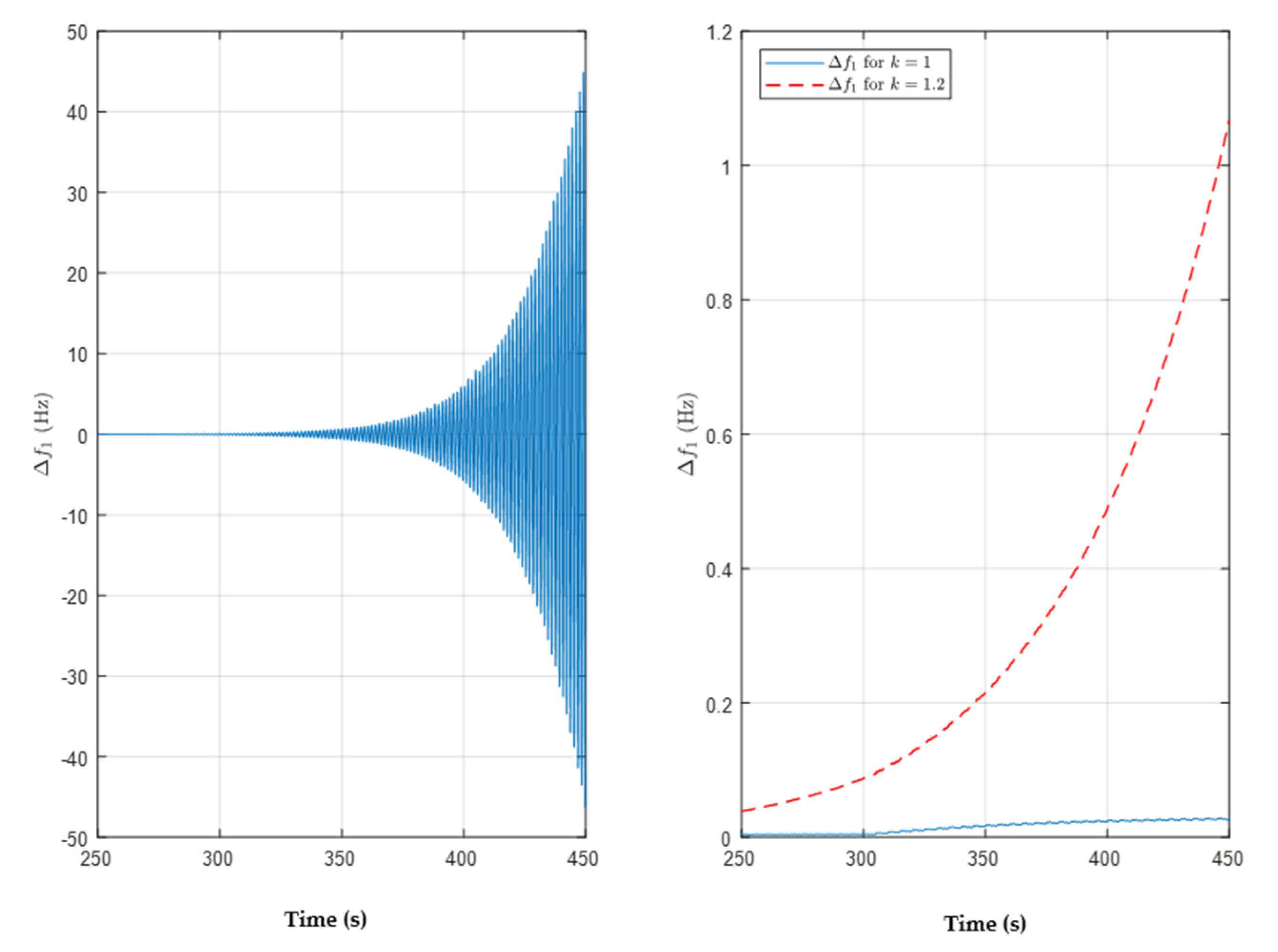
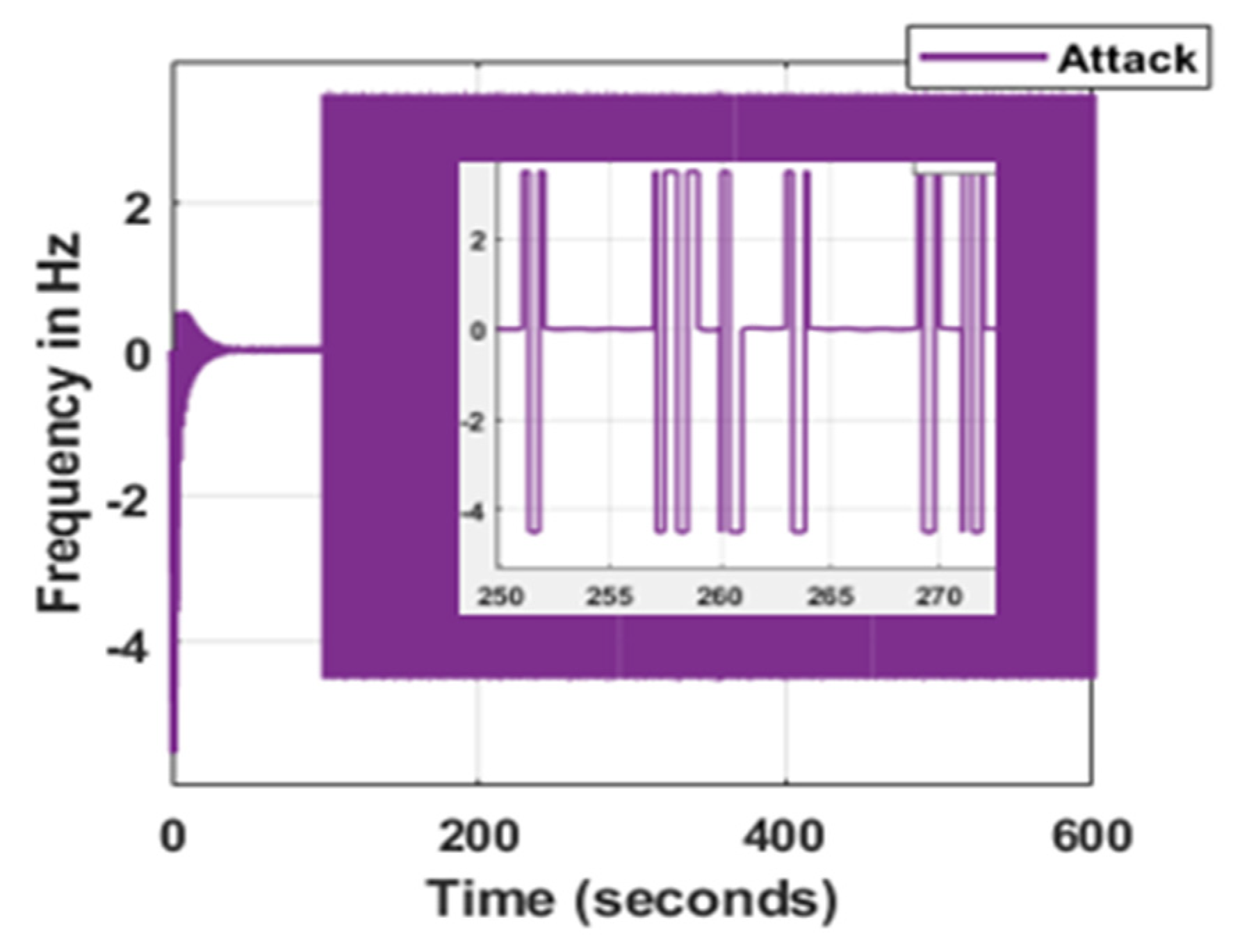
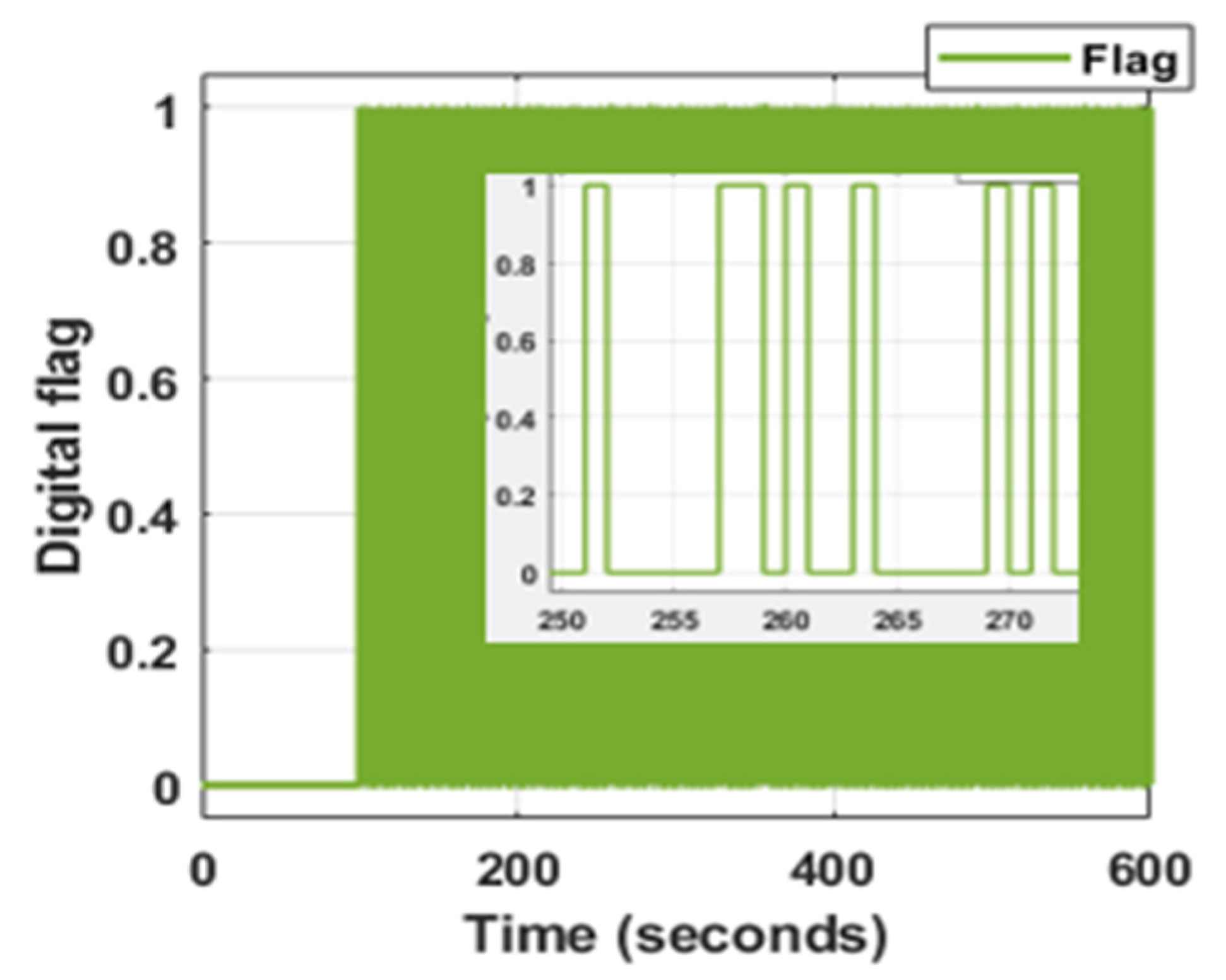
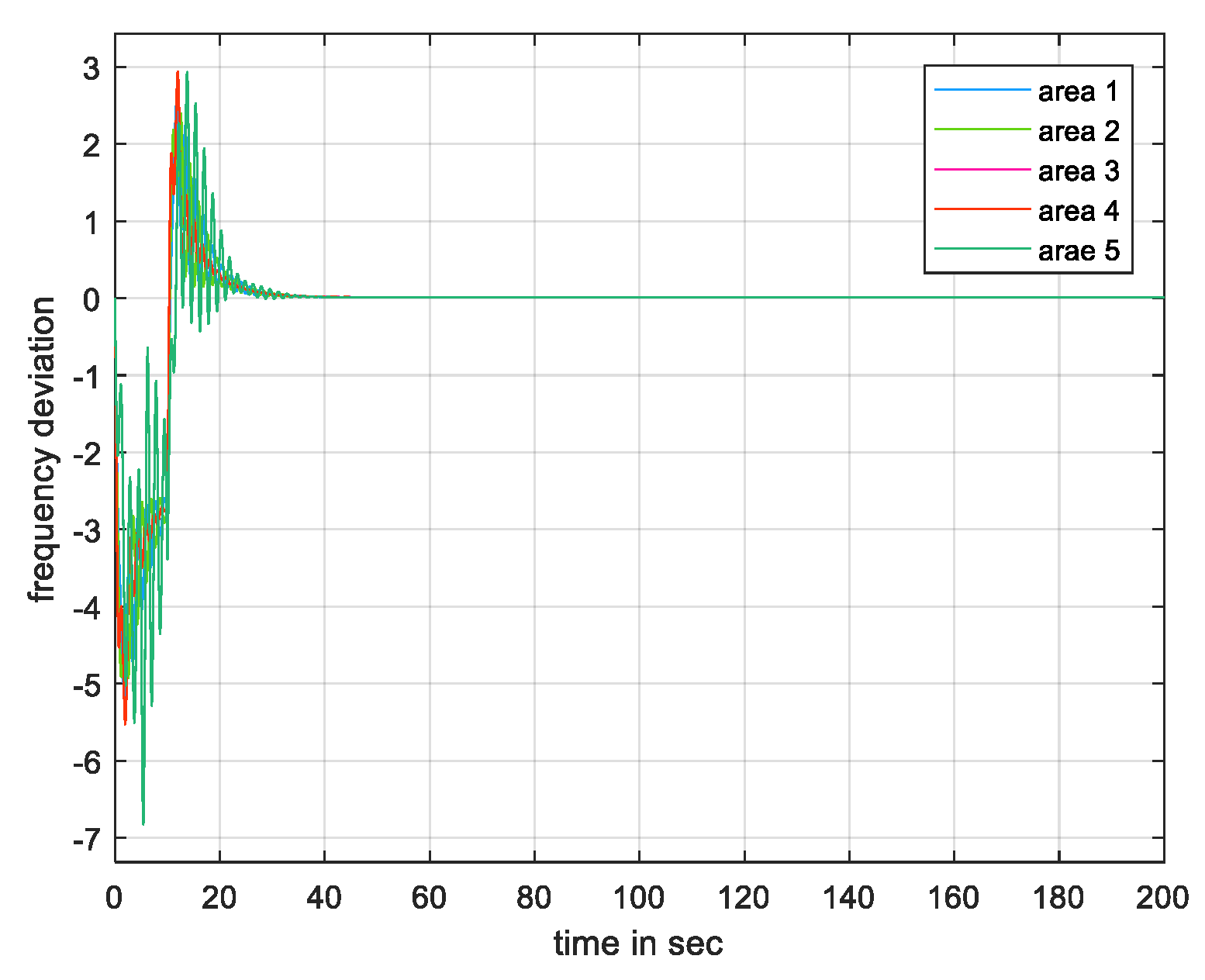
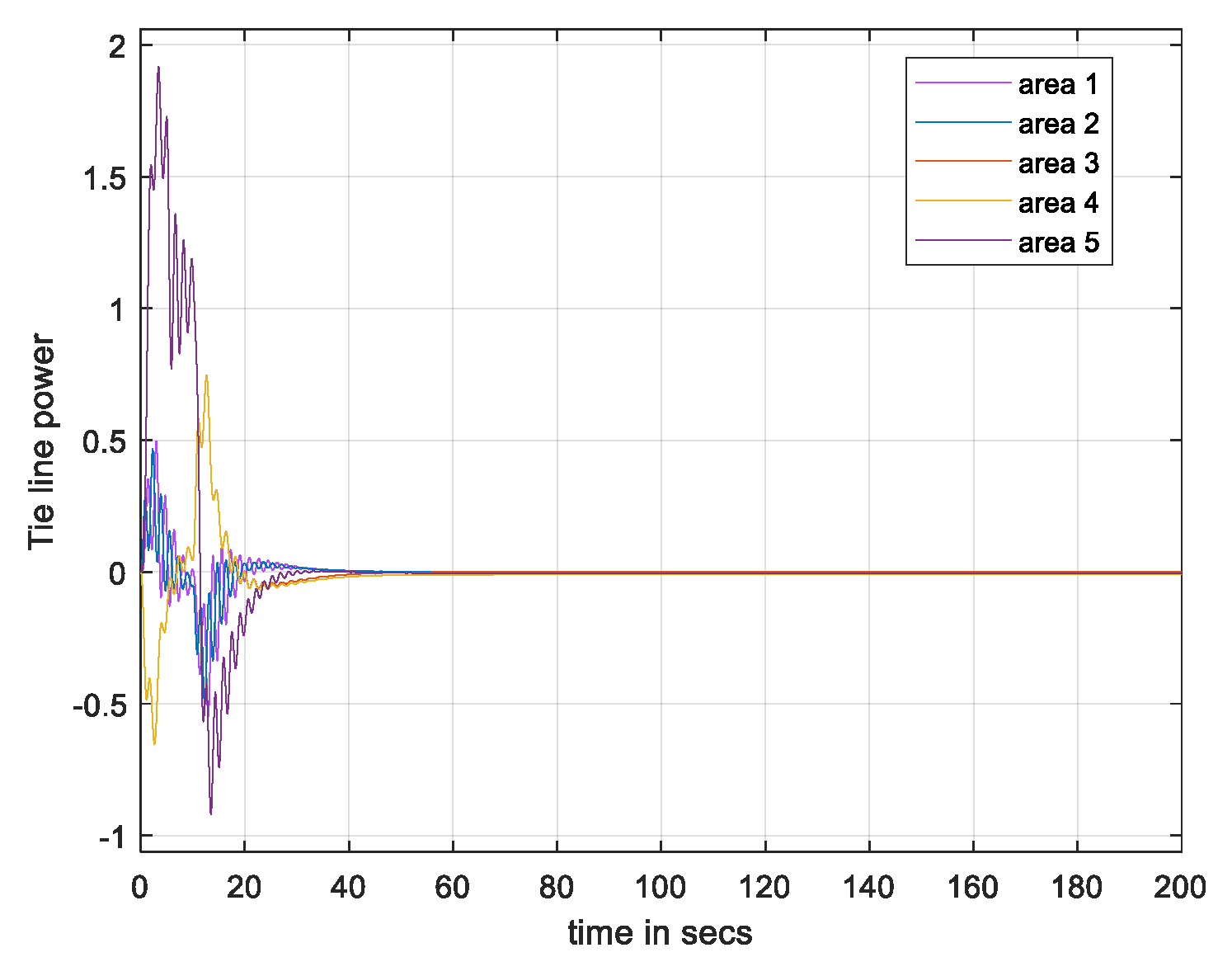
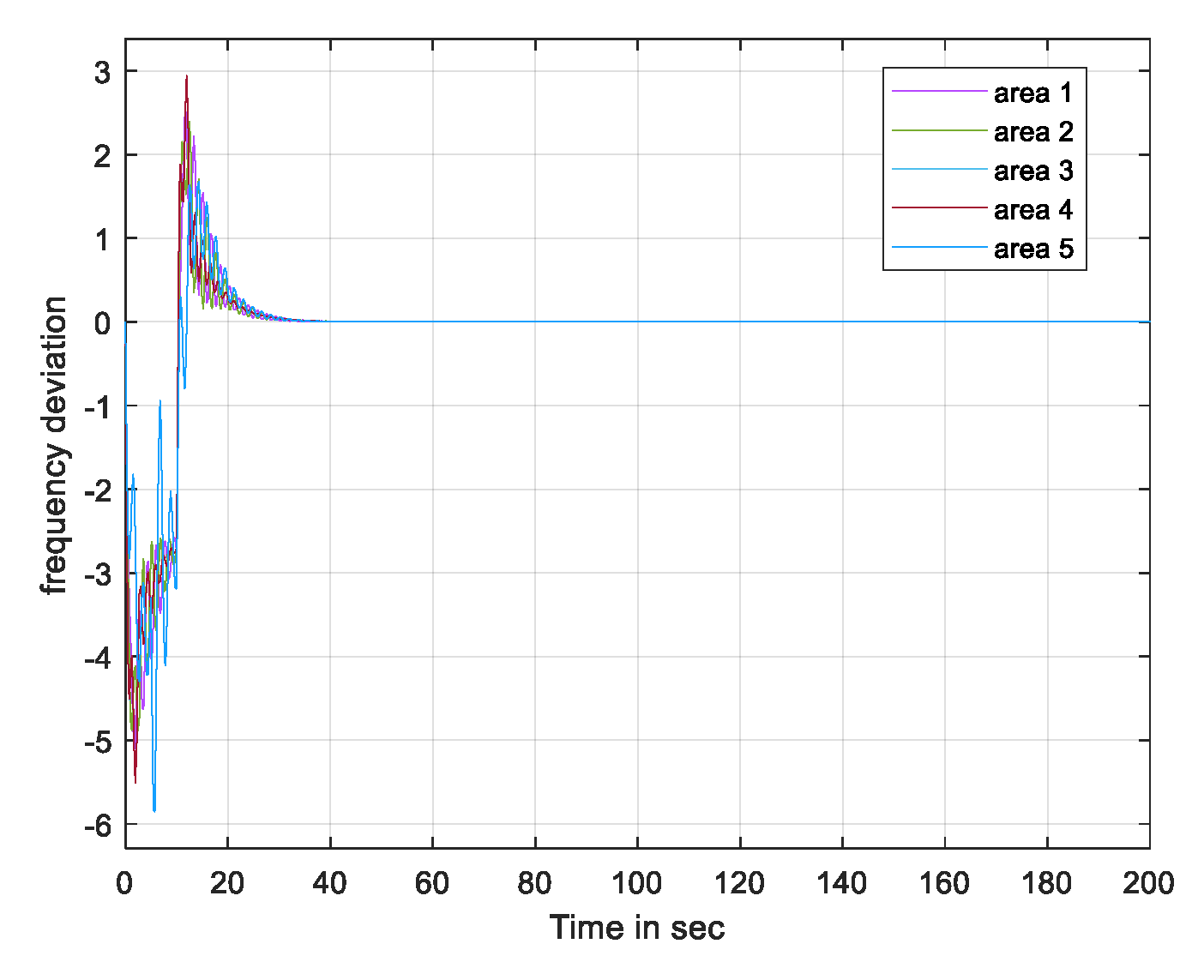
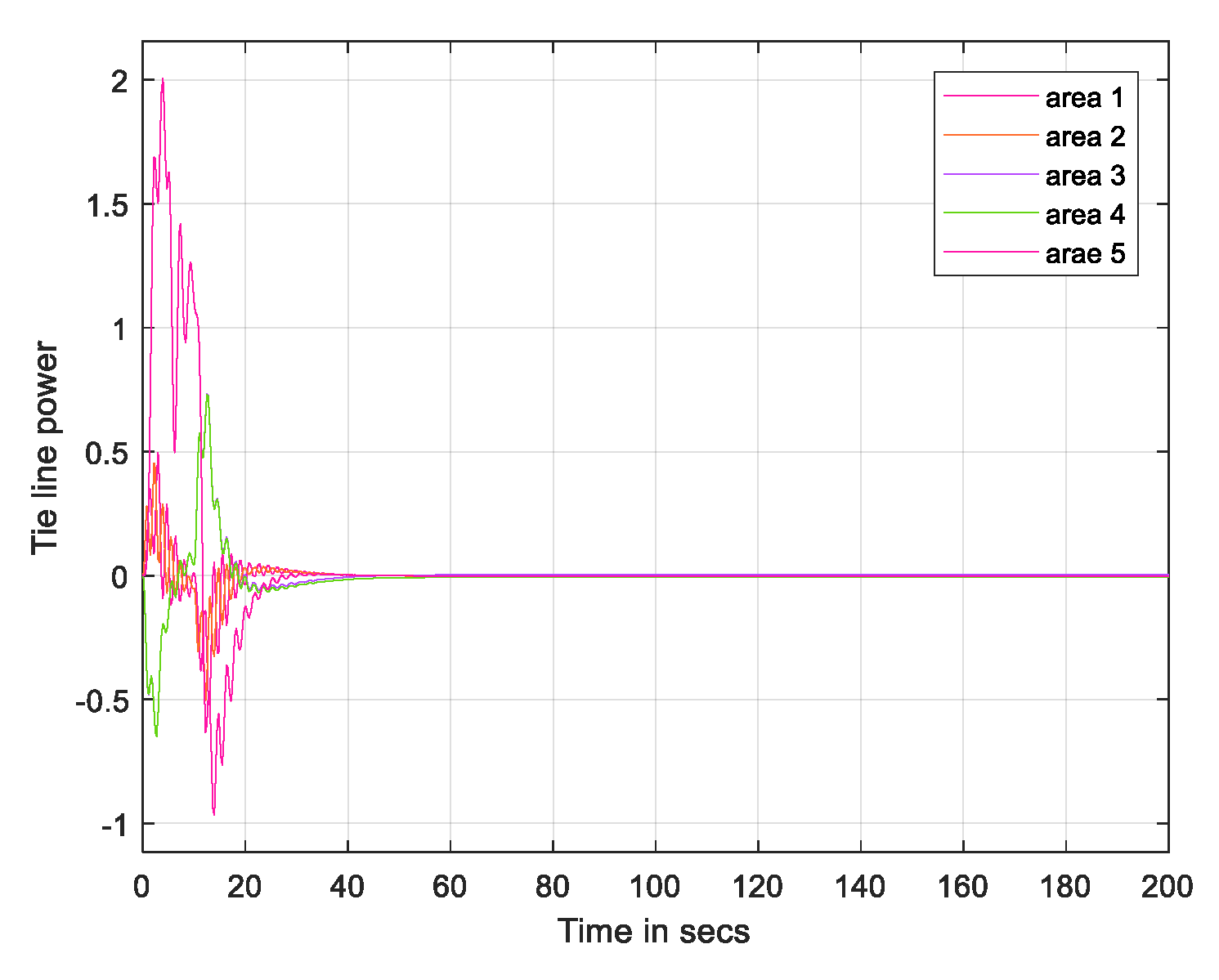
3. Results
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kundur, P. Power System Stability and Control; McGraw-Hill: New York, NY, USA, 1994. [Google Scholar]
- Wu, F.; Moslehi, K.; Bose, A. Power system control centers: Past, present, and future. Proc. IEEE 2005, 93, 1890–1908. [Google Scholar] [CrossRef]
- Ten, C.-W.; Liu, C.-C.; Manimaran, G. Vulnerability assessment of cybersecurity for SCADA systems. IEEE Trans. Power Syst. 2008, 23, 1836–1846. [Google Scholar] [CrossRef]
- Bevrani, H. Robust Power System Frequency Control; Power Electronics and Power Systems; Springer: New York, NY, USA, 2009. [Google Scholar]
- Shoham, Y.; Leyton-Brown, K. Multiagent Systems: Algorithmic, Game-Theoretic, and Logical Foundations; Cambridge Univ. Press: Cambridge, UK, 2009. [Google Scholar]
- Sommestad, T.; Ekstedt, M.; Nordstrom, L. Modeling security of power communication systems using defense graphs and influence diagrams. IEEE Trans. Power Deliv. 2009, 24, 1801–1808. [Google Scholar] [CrossRef]
- Esfahani, P.M.; Vrakopoulou, M.; Margellos, K.; Lygeros, J.; Andersson, G. A robust policy for automatic generation control cyber attack in two area power network. In Proceedings of the 49th IEEE Conference on Decision and Control (CDC), Atlanta, GA, USA, 15–17 December 2010. [Google Scholar]
- Esfahani, P.M.; Vrakopoulou, M.; Margellos, K.; Lygeros, J.; Andersson, G. Cyber attack in a two-area power system: Impact identification using reachability. In Proceedings of the 2010 American Control Conference, Baltimore, MD, USA, 30 June–2 July 2010. [Google Scholar]
- Mounzer, J.; Alpcan, T.; Bambos, N. Dynamic control and mitigation of interdependent IT security risks. In Proceedings of the 2010 IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010; pp. 1–6. [Google Scholar]
- Conejo, A.J.; Carrión, M.; Morales, J.M. Decision Making Under Uncertainty in Electricity Markets; Springer Science + Business Media: New York, NY, USA, 2010. [Google Scholar]
- Ten, C.-W.; Manimaran, G.; Liu, C.-C. Cybersecurity for critical infrastructures: Attack and defense modeling. IEEE Trans. Syst. Man Cybern. Part A Syst. Hum. 2010, 40, 853–865. [Google Scholar] [CrossRef]
- Liu, N.; Zhang, J.; Zhang, H.; Liu, W. Security assessment for communication networks of power control systems using attack graph and MCDM. IEEE Trans. Power Deliv. 2010, 25, 1492–1500. [Google Scholar] [CrossRef]
- Alpcan, T.; Başar, T. Network Security: A Decision and Game Theoretic Approach; Cambridge Univ. Press: Cambridge, UK, 2011. [Google Scholar]
- Kim, T.T.; Poor, H.V. Strategic protection against data injection attacks on power grids. IEEE Trans. Smart Grid 2011, 2, 326–333. [Google Scholar] [CrossRef]
- Hahn, A.; Govindarasu, M. Cyber attack exposure evaluation framework for the smart grid. IEEE Trans. Smart Grid 2011, 2, 835–843. [Google Scholar] [CrossRef]
- Sridhar, S.; Manimaran, G. Data integrity attack and its impacts on voltage control loop in power grid. In Proceedings of the IEEE PES General Meeting, Detroit, MI, USA, 24–28 July 2011; pp. 1–6. [Google Scholar]
- Mohsenian-Rad, A.; Leon-Garcia, A. Distributed internet-based load altering attacks against smart power grids. IEEE Trans. Smart Grid 2011, 2, 667–674. [Google Scholar] [CrossRef]
- Bommannavar, P.; Alpcan, T.; Bambos, N. Security risk management via dynamic games with learning. In Proceedings of the 2011 IEEE International Conference on Communications (ICC), Kyoto, Japan, 5–9 June 2011; pp. 1–6. [Google Scholar]
- Kundur, D.; Feng, X.; Mashayekh, S.; Liu, S.; Zourntos, T.; Butler-Purry, K.L. Towards modelling the impact of cyber-attacks on a smart grid. Int. J. Secur. Netw. 2011, 6, 2–13. [Google Scholar] [CrossRef]
- Chen, P.-Y.; Cheng, S.-M.; Chen, K.-C. Smart attacks in smart grid communication networks. IEEE Commun. Mag. 2012, 50, 24–29. [Google Scholar] [CrossRef]
- Law, Y.W.; Alpcan, T.; Palaniswami, M.; Dey, S. Security games and risk minimization for automatic generation control in smart grid. In Proceedings of the 3rd Conference Decision and Game Theory for Security (GameSec 2012), Budapest, Hungary, 5–6 November 2012; LNCS. Springer: Berlin/Heidelberg, Germany, 2012; Volume 7638, pp. 281–295. [Google Scholar]
- Law, Y.W.; Alpcan, T.; Palaniswami, M. Security games for voltage control in smart grid. In Proceedings of the 012 50th Annual Allerton Conference on Communication, Control, and Computing, Monticello, IL, USA, 1–5 October 2012. [Google Scholar]
- Sridhar, S.; Govindarasu, M.; Liu, C.-C. Risk Analysis of Coordinated Cyber-Attacks on Power Grid. In Control and Optimization Methods for Electric Smart Grids; Springer: New York, NY, USA, 2012; pp. 275–294. [Google Scholar]
- Liu, S.; Liu, X.; Saddik, A.E. Denial-of-Service (DoS) attacks on load frequency control in smart grids. In Proceedings of the 2013 IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 24–27 February 2013; pp. 1–6. [Google Scholar]
- Law, Y.W.; Alpcan, T.; Palaniswami, M. Security Games for Risk Minimization in Automatic Generation Control. IEEE Trans. Power Syst. 2015, 30, 223–232. [Google Scholar] [CrossRef]
- Mirjalili, S. The Ant Lion Optimizer. Adv. Eng. Softw. 2015, in press. [Google Scholar] [CrossRef]
- Khadarvali, S.; Madhusudhan, V.; Kiranmayi, R. Robust Cooperative Control in Multi Area Power System Using Differential Game theory Under Weak Grid Condition. ARPN J. Eng. Appl. Sci. 2019, 1400–1406. [Google Scholar]
- Khadarvali, S.; Madhusudhan, V.; Kiranmayi, R.; Al Farawn, A.; Rjeib, H.D.; Al-Sadawi, B. Differential Game Theory with FPA Optimization in Multi-Area Power System. Int. J. Power Electron. Drive Syst. 2020, 11, 302–308. [Google Scholar] [CrossRef][Green Version]
- Khadarvali, S.; Madhusudhan, V.; Kiranmayi, R. Differential Game Theory with ALO Control in Multi-Area Power System. Int. J. Adv. Sci. Technol. 2020, 29, 608–614. [Google Scholar]
- Khadarvali, S.; Madhusudhan, V.; Kiranmayi, R. Load Frequency Control of Two Area System with Security Attack and Game Theory Based Defender Action Using ALO Tuned Integral Controller. In Proceedings of the 2021 International Conference on Computational Intelligence and Computing Applications (ICCICA), Nagpur, India, 26–27 November 2021; pp. 1–5. [Google Scholar] [CrossRef]
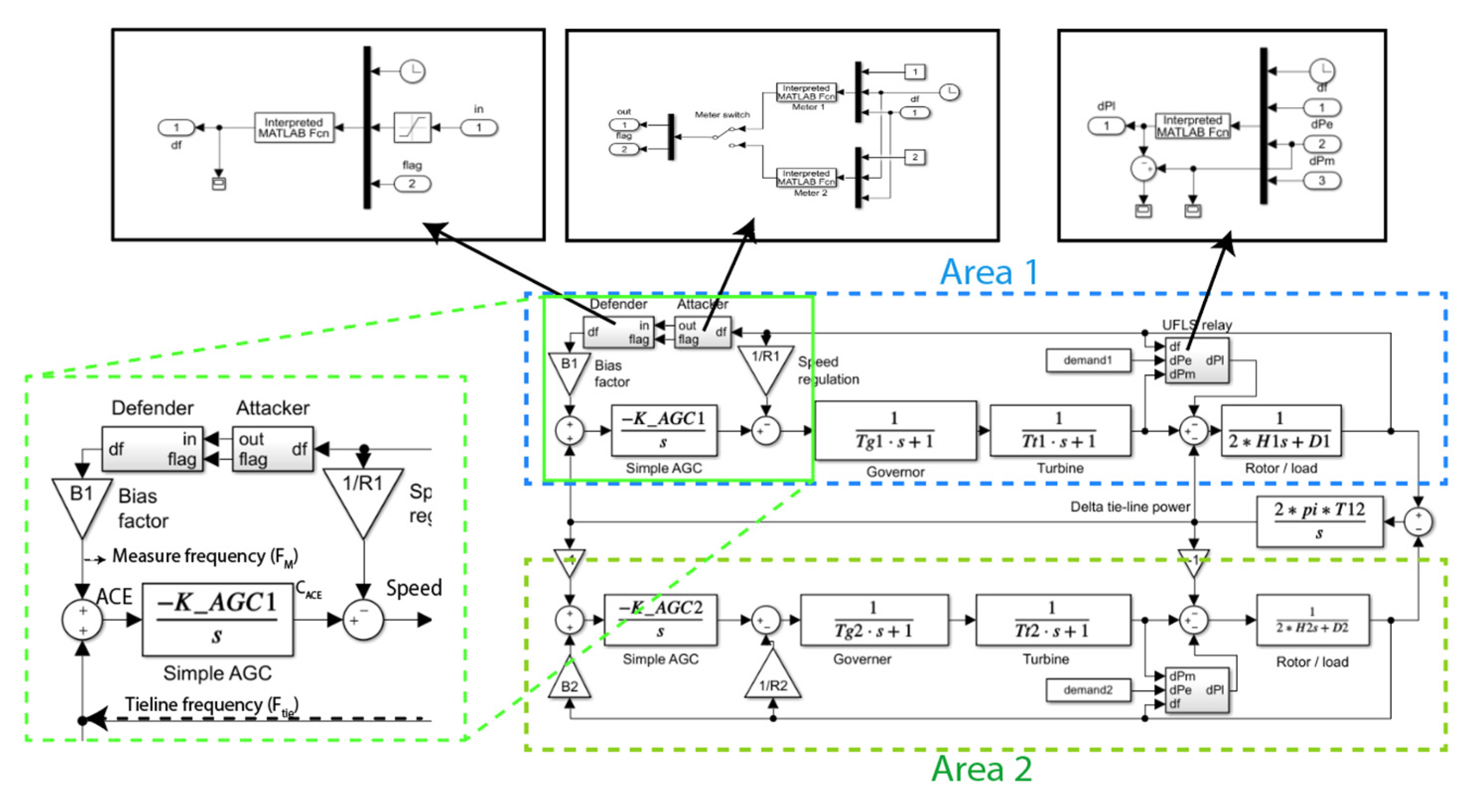
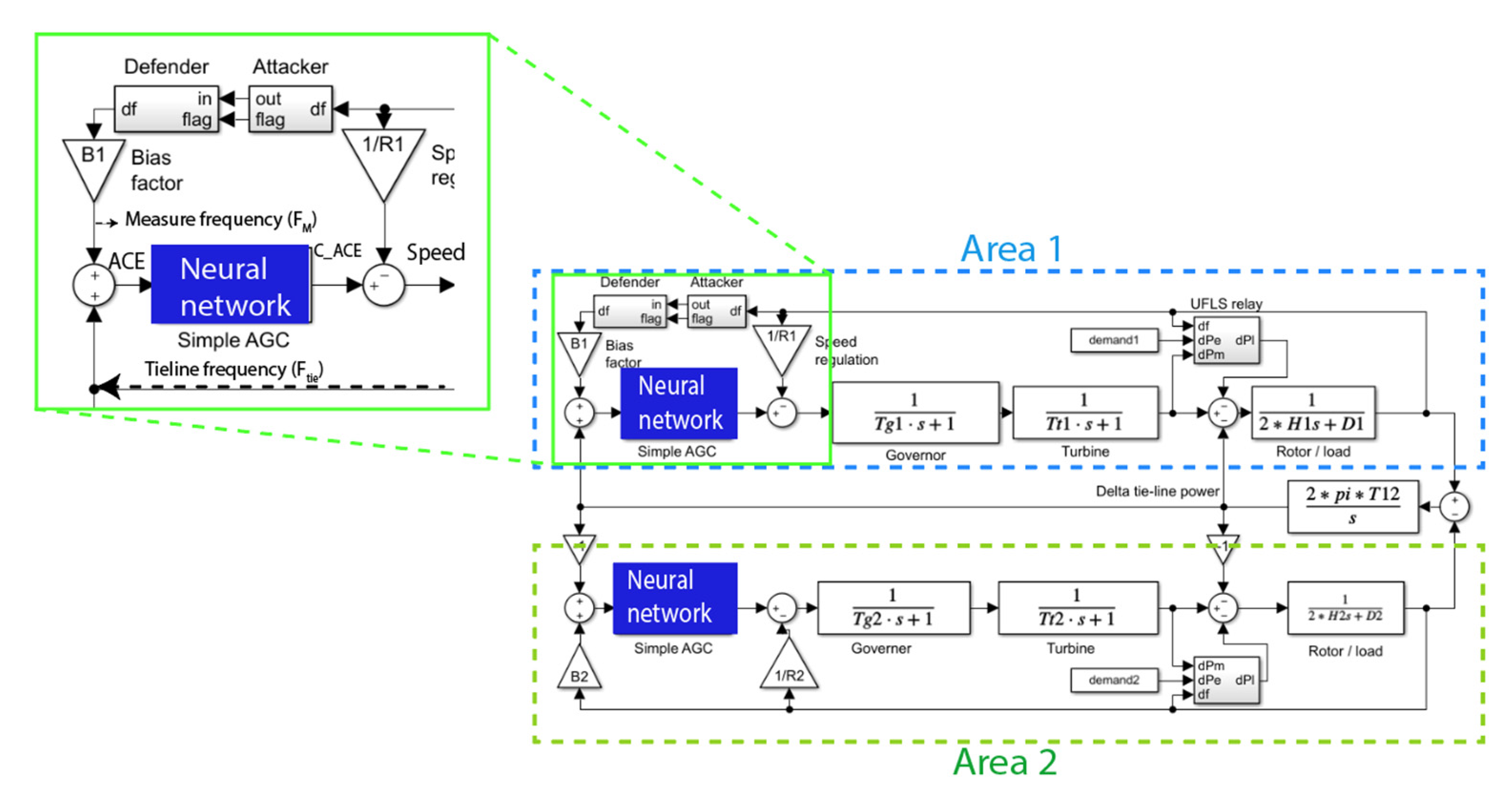
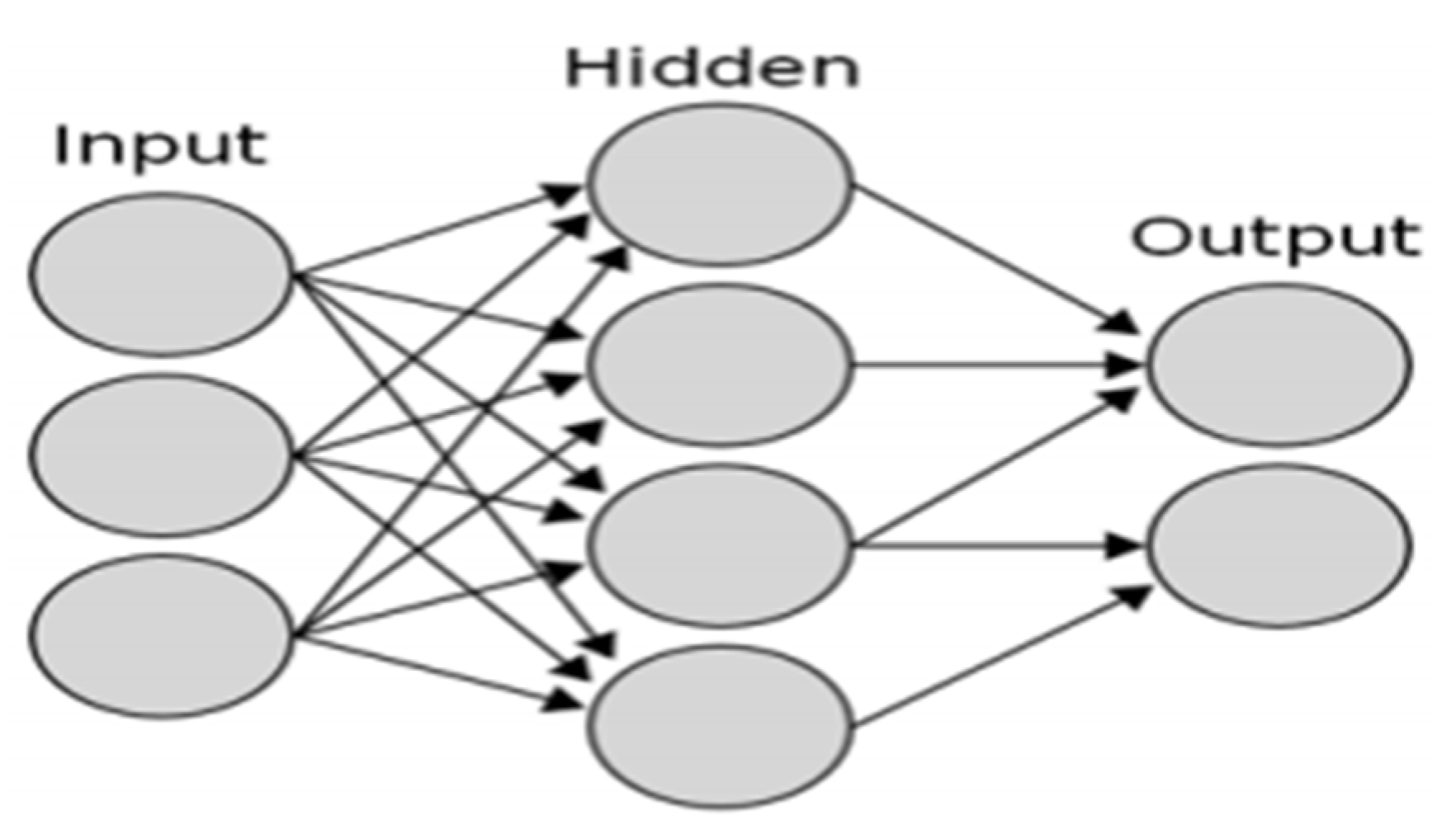
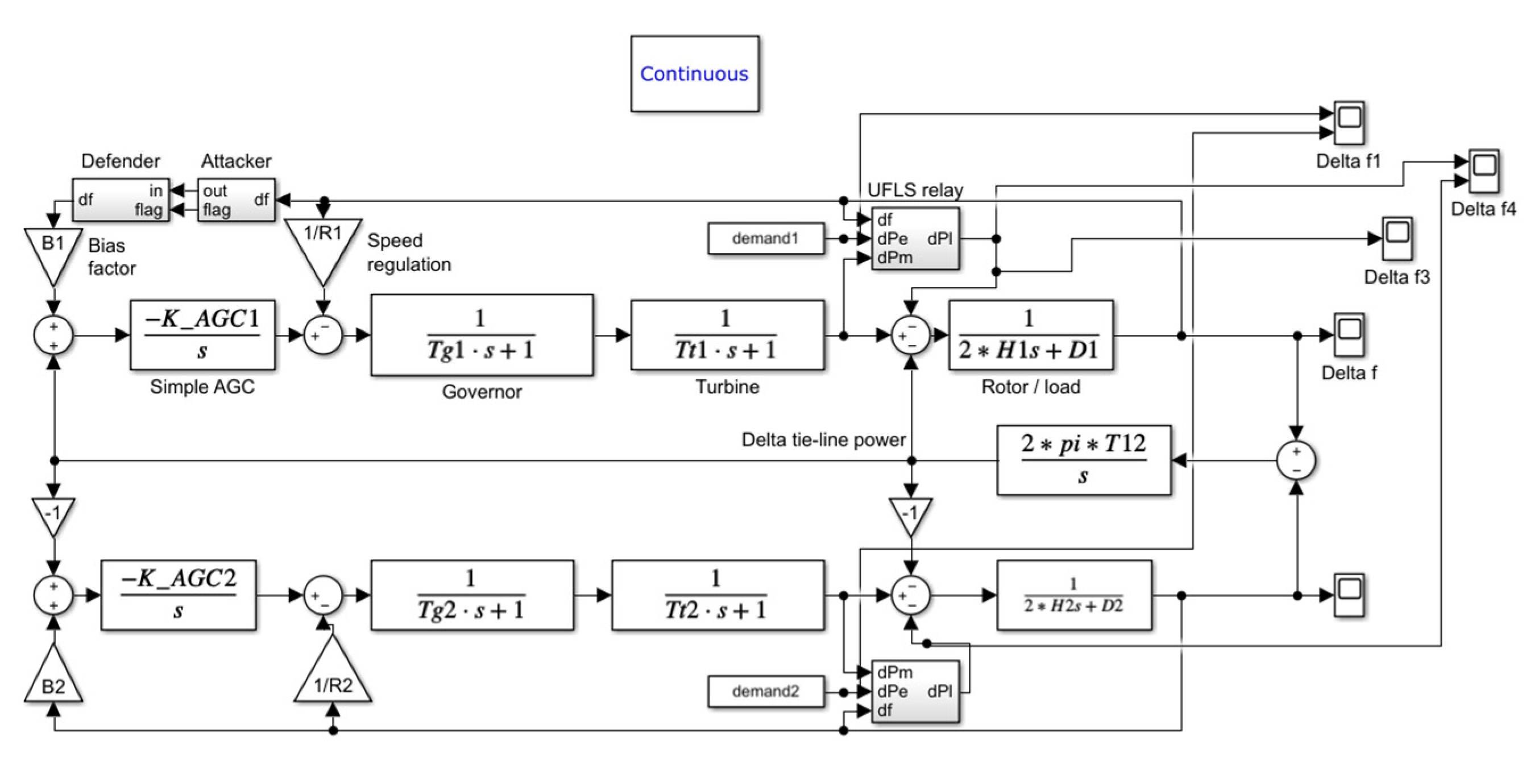
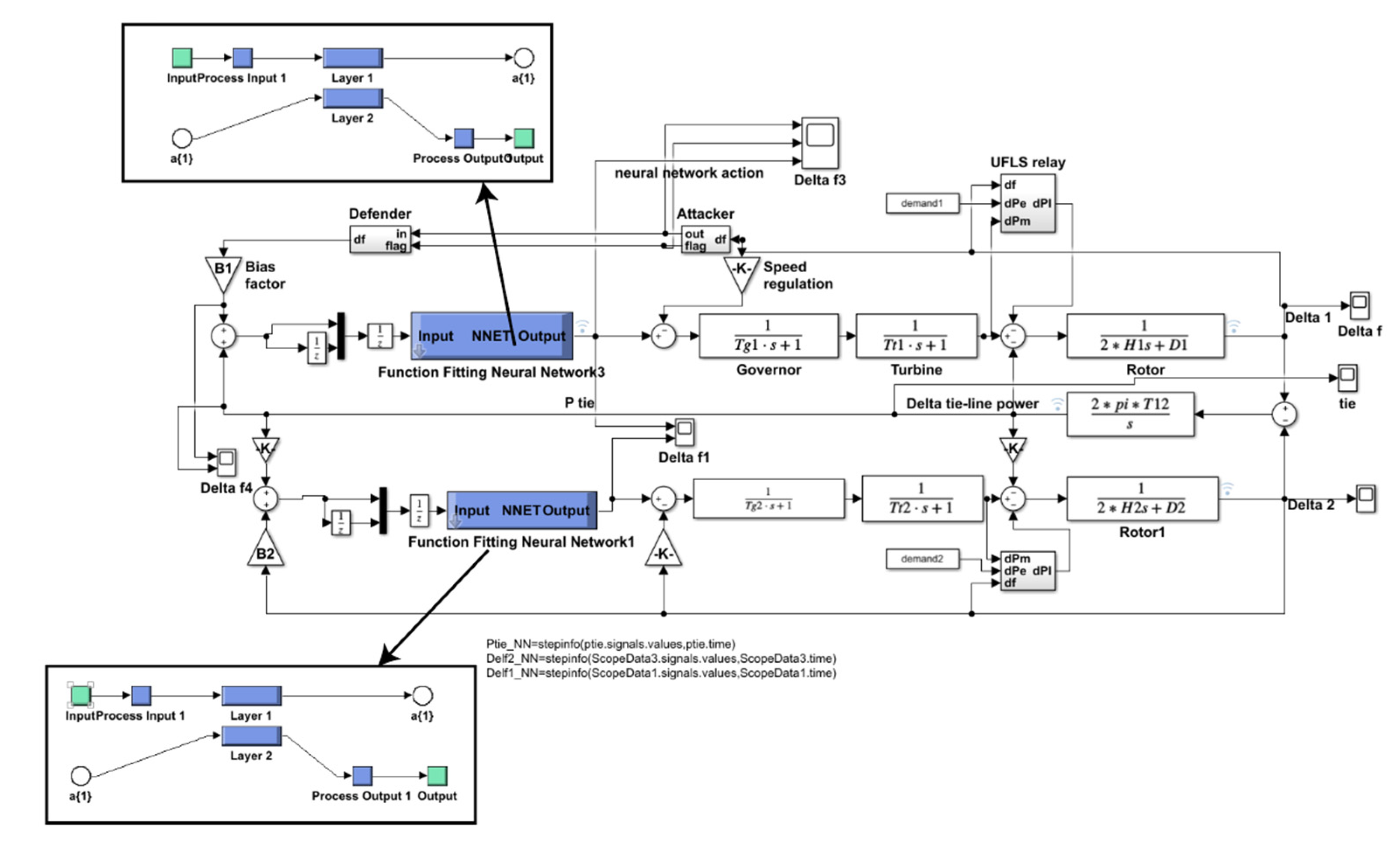
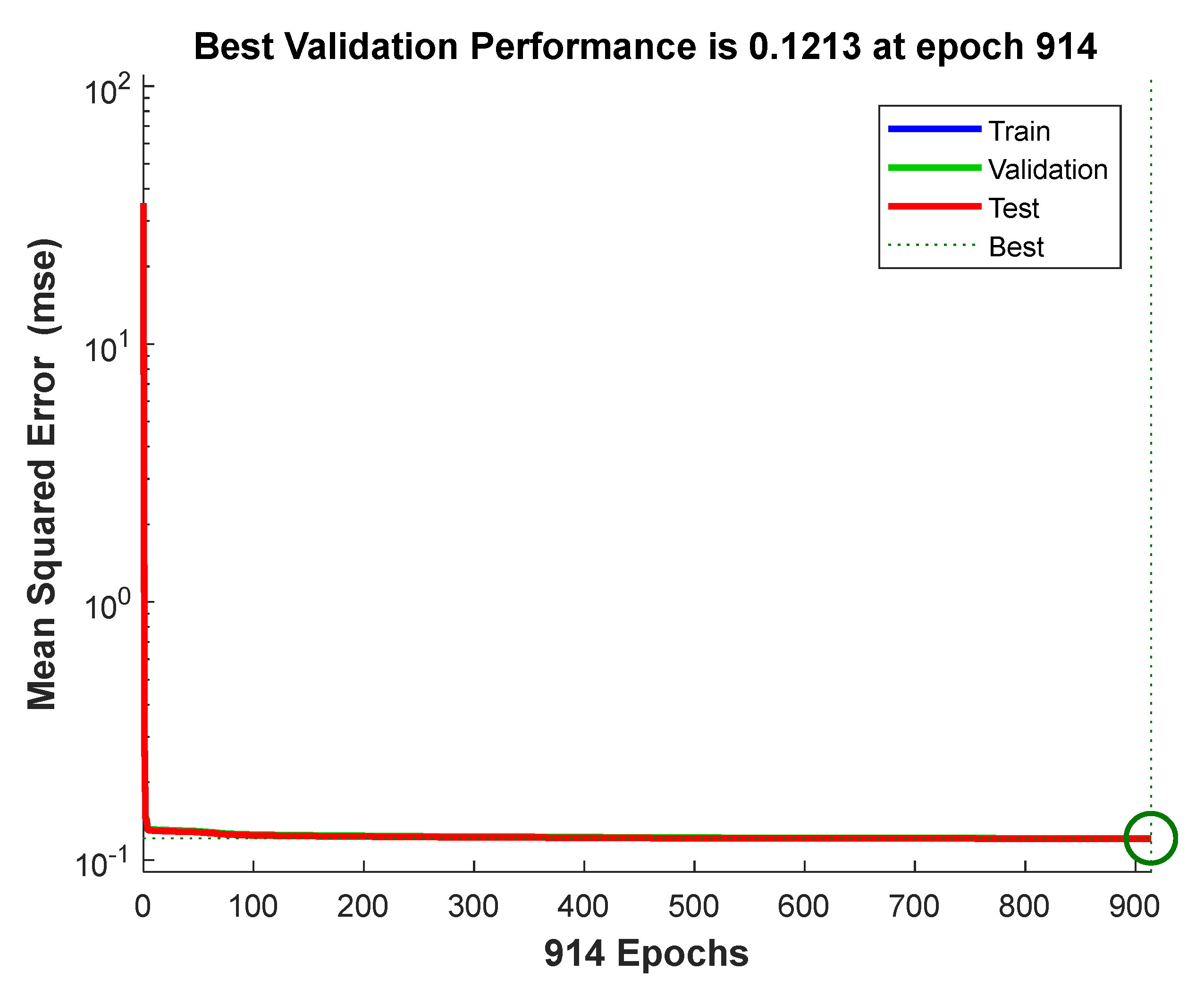
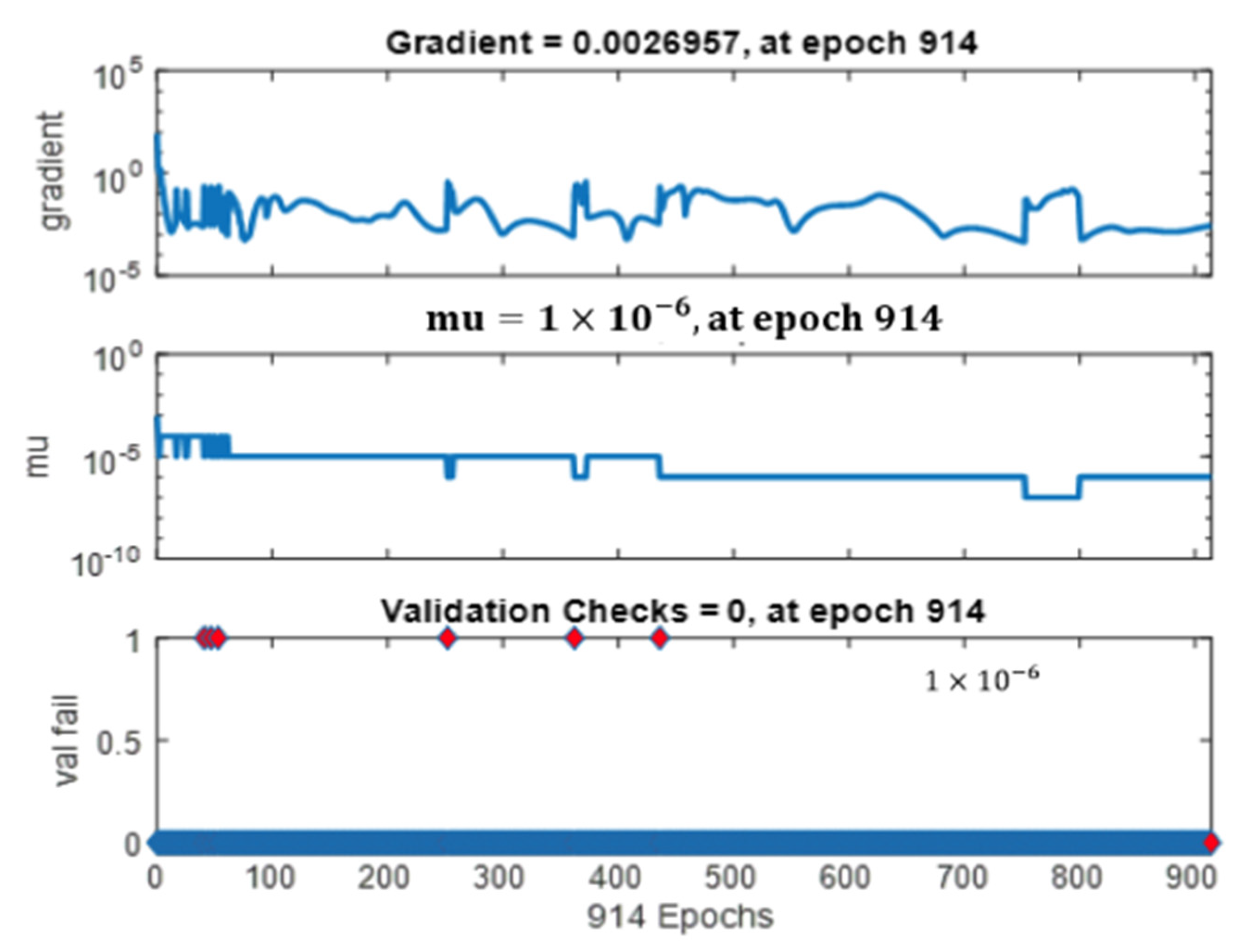


| ANN Unit | Availability Status of Training Data |
|---|---|
| Controller | Available to train the controller |
| Plant | LFC model |
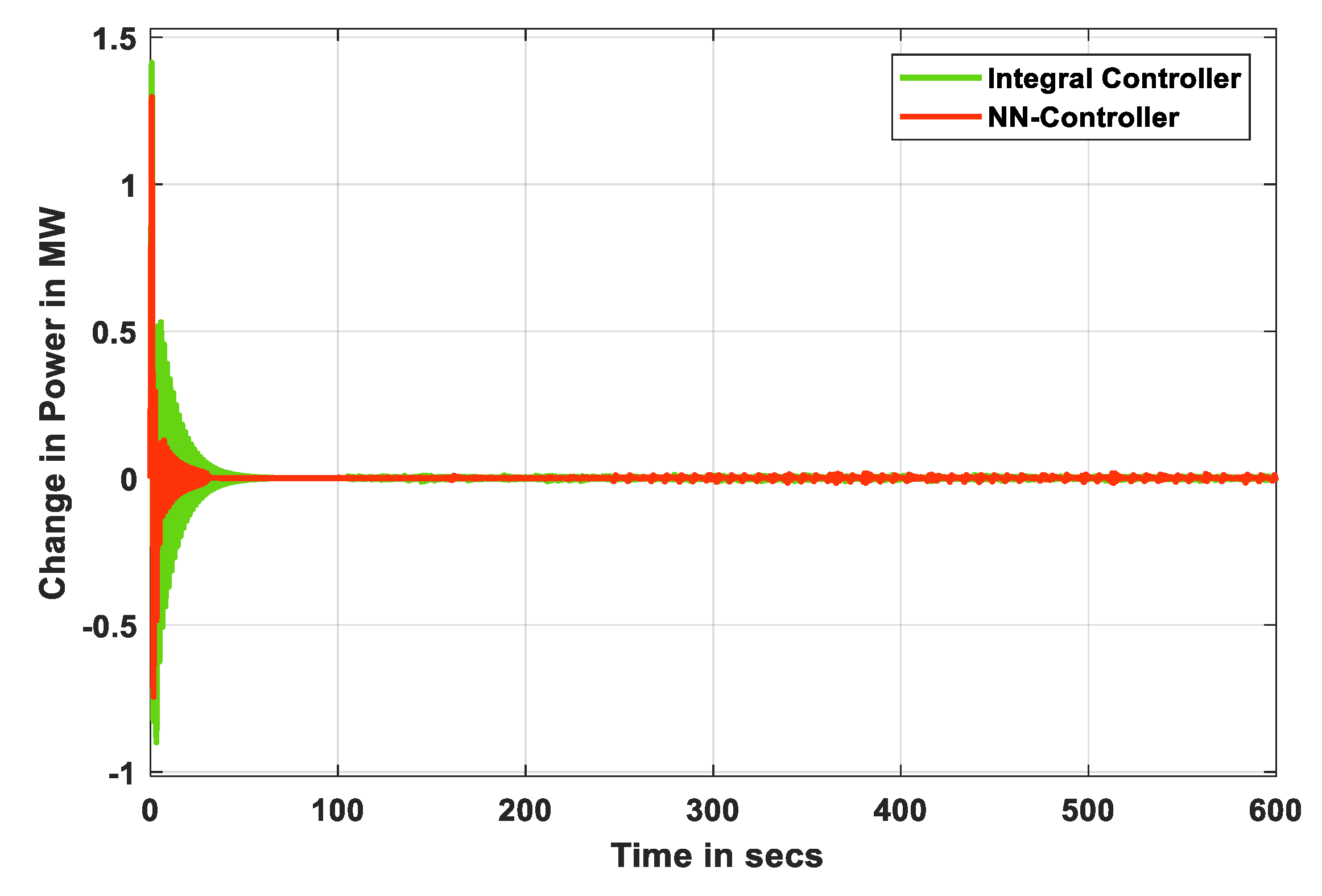
| Integral Controller [25] | NN Controller | |||||
|---|---|---|---|---|---|---|
| Δf1 (Hz) | Δf2 (Hz) | ΔPtie (p.u) | Δf2 (Hz) | Δf2 (Hz) | ΔPtie (p.u) | |
| Rise Time(s) | 0.000816 | 0.000149 | 0.02057 | 6.6132 | 0.00714 | 0.01136 |
| Settling Time (s) | 27 | 27.851 | 38.771 | 17.376 | 18.285 | 25.846 |
| Settling Min(s) | −1.0612 | 4.8252 | −0.89933 | −0.2872 | −0.2957 | −0.7447 |
| Settling Max(s) | 0.53052 | 0.55137 | 1.4133 | 0.10266 | 0.10431 | 1.297 |
| Overshoot (ratio) | 16,209 | 2.70 × 105 | 19,560 | 394 | 1323.1 | 66,981 |
| Undershoot (ratio) | 1.70 × 105 | 30,907 | 12,510 | 24,241 | 54,439 | 38,515 |
| Peak Value | 5.5215 | 4.8252 | 1.4133 | 5.0377 | 3.9904 | 1.297 |
| Peak Time (s) | 1.25 | 1.95 | 0.75 | 1.23 | 1.893 | 0.741 |
| PI Controller | NN Controller | |
|---|---|---|
| Rise Time (s) | 2.0968 | 0.30207 |
| Settling Time (s) | 34.451 | 24.842 |
| Settling Min (s) | 0.063062 | 0.78426 |
| Settling Max (s) | 25.779 | 27.734 |
| Overshoot (ratio) | 40,315 | 3435 |
| Undershoot (ratio) | 0 | 0 |
| Peak value | 25.779 | 27.734 |
| Peak Time (s) | 9.5024 | 2.301 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khadarvali, S.; Madhusudhan, V.; Kiranmayi, R. Artificial Neural Network Controller in Two-Area and Five-Area System with Security Attack and Game-Theory Based Defender Action. Energies 2022, 15, 5715. https://doi.org/10.3390/en15155715
Khadarvali S, Madhusudhan V, Kiranmayi R. Artificial Neural Network Controller in Two-Area and Five-Area System with Security Attack and Game-Theory Based Defender Action. Energies. 2022; 15(15):5715. https://doi.org/10.3390/en15155715
Chicago/Turabian StyleKhadarvali, S., V. Madhusudhan, and R. Kiranmayi. 2022. "Artificial Neural Network Controller in Two-Area and Five-Area System with Security Attack and Game-Theory Based Defender Action" Energies 15, no. 15: 5715. https://doi.org/10.3390/en15155715
APA StyleKhadarvali, S., Madhusudhan, V., & Kiranmayi, R. (2022). Artificial Neural Network Controller in Two-Area and Five-Area System with Security Attack and Game-Theory Based Defender Action. Energies, 15(15), 5715. https://doi.org/10.3390/en15155715






