1. Introduction
In today’s world, the use of blockchain technology is popular in various fields such as healthcare, big data, finance, law, cyber security, and supply chain management, for example, Blochie, a blockchain-based platform for healthcare information exchange and TSAR, a fully-distributed trustless data sharing platform. Blockchain is popular because of several characteristics such as its decentralized network style, auditability, security, immutability, and inconspicuousness [
1]. In this paper, the word “activities” refers to “transactions”. Shared digital notes of activities are managed by the blockchain, which is distributed among all the working nodes in the environment. Most of the auditability process can be done through the activities stored in the digital notes. The process is decentralized in the blockchain, where all transactions are evaluated and checked by all other processing nodes in the environment. A group of distinctive nodes, called miners, are used to append activities to the collection of activities waiting for transmission, in which the appended activities are produced as new ones. The appended activities are merged with the waiting activities in the block through the miner, whereby the size of the merged activities touches the limit of the size of the block. When the new block is included in the blockchain environment, an agreement algorithm is used in the blockchain environment to ensure that it is secure against malevolent miners and inappropriate transactions.
Traditionally, deployment of the blockchain uses proof-of-work or proof-of-stake protocols [
2]. In order to extract the next block, the proof-of-work strategy requires maximum computing resources to defeat the agreement algorithm. Similarly, the proof-of-stake strategy requires the miners to latch their stake or property into the blockchain network to extract the next block. A public key is used as an identification card for every user when they generate activities, which results in the maximum level of inconspicuousness in the blockchain network [
3].
Blockchain, owing to its characteristics, has been integrated into the IoT to enhance security, auditability, reliability, and inconspicuousness. Traditional IoT architectures have several disadvantages or restrictions, such as the utilization of resources and its centralized structure [
4,
5,
6,
7,
8,
9,
10,
11,
12,
13]. The merits of the blockchain technology solve some of these issues. IBM developed a new blockchain strategy called Hyperledger fabric, whereby only legitimate nodes can access the blockchain network [
14]. Even though the blockchain has many merits, it also has some disadvantages and challenges such as extensibility and irregular transmission of data, complicated agreement algorithms, delay, and throughput. The primary objective of this research work is to provide solutions to the above-mentioned issues.
In this regard, the proposed approach introduces the simple size extensible (SSE) blockchain for the IoT. In order to maintain the blockchain and to provide extensibility, the chiefs of the clusters (CC) will take charge. The cluster contains components of the IoT, storage from the cloud, and service providers. The cluster is formed to represent these things as an overlay network. The administration of the blockchain contains valuation and checking and storage of every single activity or block of activities. An activity is said to be the fundamental interaction for networking the authority data among the nodes. A block is developed through the collection of activities where these blocks are added to the blockchain to generate the shared digital notes. In SSE blockchain, the information regarding the IoT components is stored in the cloud storage and not in the chain. This is done to minimize the amount of memory and irregularity of the packet in the blockchain. The exchange of information among the IoT components is not included in the activity flow.
After the information about the packets is updated at the receiver’s ends, the activities based on these packets are transmitted through the overlay nodes to the receiving block of the blockchain environment. The process of individuality in the exchange of information among the IoT components results in the best one-to-one scheduling of information packets. Finally, the latency and irregularity of packets are minimized while the information is exchanged. The shared time depending agreement algorithm (STD) has been proposed to minimize any irregularity in the extraction operation in the blockchain. Here, every CC has to wait for a non-interval time before extracting the new block. The STD restricts the CC’s ability to produce new blocks within a stipulated time in order to provide security against malevolent CCs. The SSE blockchain appoints a shared faith algorithm to minimize the processing irregularity along with evaluating and checking new blocks that are to be included in the blockchain. Each CC collects proof about the other CCs, depending on the lifetime of the produced new blocks. No verification process has not been done for the activities that have gained the trust of the chiefs of clusters.
Lastly, the shared throughput administration (STA) algorithm was proposed to improve the throughput of the blockchain. The STA ensures maximization of the throughput by adopting extensibility in the blockchain by adding new blocks in the network.
The objectives of this paper are as follows:
To reduce the gap between the IoT and the blockchain
To generate a flexible extensible for obtaining more activities in the blockchain
To perform secure activities and disseminate the blockchain technology in the outside world through the IoT.
The rest of the paper is organized in five sections.
Section 2 examines and analyses the literature. The proposed model is outlined in
Section 3 and the results are given and discussed in
Section 4.
Section 5 concludes the paper and considers the implications for the future.
2. Literature Review
A detailed literature review based on the security and inconspicuousness of the IoT and blockchain systems was carried out to examine previous research with the clear objective of finding the optimal solution.
According to Saberi et al. [
15], there are still several barriers that prevent the development of a definitive blockchain technology (e.g., inter-organizational barriers, external barriers, and intra-organizational barriers). They refer to supply chain management, but many of the barriers they identify can also be applied in other contexts. Blockchain is not the solution to everything because many limitations and challenges still exist. Astarita et al. [
16] states that blockchain technology is promising, but much effort is still necessary for it to reach the maturation stage. The main reason for this is that many models have been theorized in recent years, but only a few have been practically implemented in the area of supply chain and logistics, road traffic management, and smart cities. It is essential to note that the regulatory framework linked to the blockchain is complex, and many questions remain unanswered in this area.
Yeoh [
3] analyzed how key regulatory challenges are impacting blockchains in the European Union and the USA. Khan et al. [
1] and Panarello et al. [
17] highlighted the research problems and challenges regarding blockchains, security, and IoT. Cachin [
18] proposed a novel Hyperledger blockchain fabric architecture in which the network overhead was minimized by removing unwanted header fields. This resulted in minimizing the size of the header of the 6LowPAN and host identity protocol to 25 bytes [
18]. To protect the network against illegal users and processes, a novel access control and authentication mechanism was proposed to ensure the security and extensibility of the IoT environment by Liu et al. [
19]. In SSE blockchain, one blockchain infrastructure has been proposed and it is maintained through the network of overlay nodes. The components evaluate and authenticate various overlay nodes in the network by refreshing the list of keys in the overlay block administrator. The proposed system performs well by providing better extensibility and optimal security against a more extensive boundary of attacks.
The concept of bitcoin introduced the methodology of blockchain [
20]. The objective of the bitcoin was to eliminate the concept of centralization and to promote the decentralization of money transfers by providing maximum security to the users. Ethereum, a novel blockchain methodology was proposed whereby users can develop and utilize intelligent working agreements with a minimum amount of network performance but with maximum security [
4]. It had been used in many blockchain applications such as agriculture, to provide grant information, and mini blogging [
21,
22]. A new technique for energy trading was proposed in which energy developers could negotiate the market price with their consumers by generating an intelligent work agreement to perform the vending. A shared process manager was included in the system to provide security in the energy trading on both sides for the customer and the energy developers [
23]. A three-tier mechanism for blockchain was proposed to distribute information among the components of the IoT, companies, and users. The mechanism develops a separate blockchain to store the information in a secure manner [
24]. The proposed system does not depend on separate blockchains for storing the information. Here, the information is stored in the form of the hash in the cloud storage in the blockchain.
Internet of Things Application (IOTA) is a digital note, which depends on cryptocurrency that removes the concept of blocks. It also extracts the details to the environment, which helps to minimize the time required to verify the activities [
25]. IOTA is a distributed ledger designed to record and execute transactions between machines and devices in the IoT ecosystem. The ledger uses a cryptocurrency called mIOTA to account for transactions in its network. IOTA’s key innovation is Tangle, a system of nodes used to confirm transactions. There is some similarity between the SSE blockchain and the IOTA. Both techniques do not charge for the activities, and both adopt an extensible network. Due to this, the proposed SSE blockchain has the advantage of proper auditability through the immutability of digital notes.
A standard blockchain technique was proposed to provide faith in the vehicular networks [
8]. An efficient resource clustering model was proposed to develop an efficient wireless cloud that will help future blockchain environments [
26]. The system utilizes the shared faith of all the processing nodes in the environment. The proposed SSE blockchain utilizes the same type of shared faith but minimizes the operational irregularity for checking the new blocks in the blockchain. The GraphCoin technique [
27] was proposed to provide the solution for the extensibility in the digital money transactions. The technique aims to validate the security and individuality of the users. Further, a technique called catena was proposed to minimize the irregularity in blockchain auditability and to maximize the throughput of the network. It also enables the establishment of the interactions among the various authors out of the blockchain to minimize the audit and storage of the network [
28].
The Memory Optimized and Flexible Blockchain (MOF-BC) method was proposed to facilitate the elimination of activities in the blockchain database, optimize the memory and provide reliable blockchain. Blockchain does not allow for the elimination of activities. The MOF-BC method manages the stability in the blockchain [
29]. An agreement algorithm based on proof-of-authority can be related to the proof-of-stake, in which the extracting strength of every extractor depends on its address in the environment instead of the number of latches it owns [
30]. Intel developed an agreement algorithm known as the proof-of-elapsed-time to work in the blockchain, in which it is merged with the Hyperledger. The proof-of-elapsed-time algorithm is a chief voting algorithm that was designed to run in a faith deployment network [
31]. Another agreement algorithm named AlgoRand is proposed, which depends on Byzantine understanding in which the extractors shall have an understanding in a single meeting of execution [
7]. The shared version of Byzantine understanding called federated Byzantine understanding was proposed to facilitate the nodes in the environment to select the evaluators [
14]. Restricted or minimum throughput are the major disadvantages of the traditional agreement algorithms. When it comes to the security of the blockchain, the traditional systems restrict the number of blocks that can be included in the blockchain, thus, the throughput of the blockchain is minimized. The proposed STD manages the required blocks through the feedback of the proposed STA to maintain an optimal or to maximize the throughput of the blockchain network. This results in the extensibility of blockchain for the IoT through the proposed STA algorithm and also reduces the gap between the IoT and blockchain.
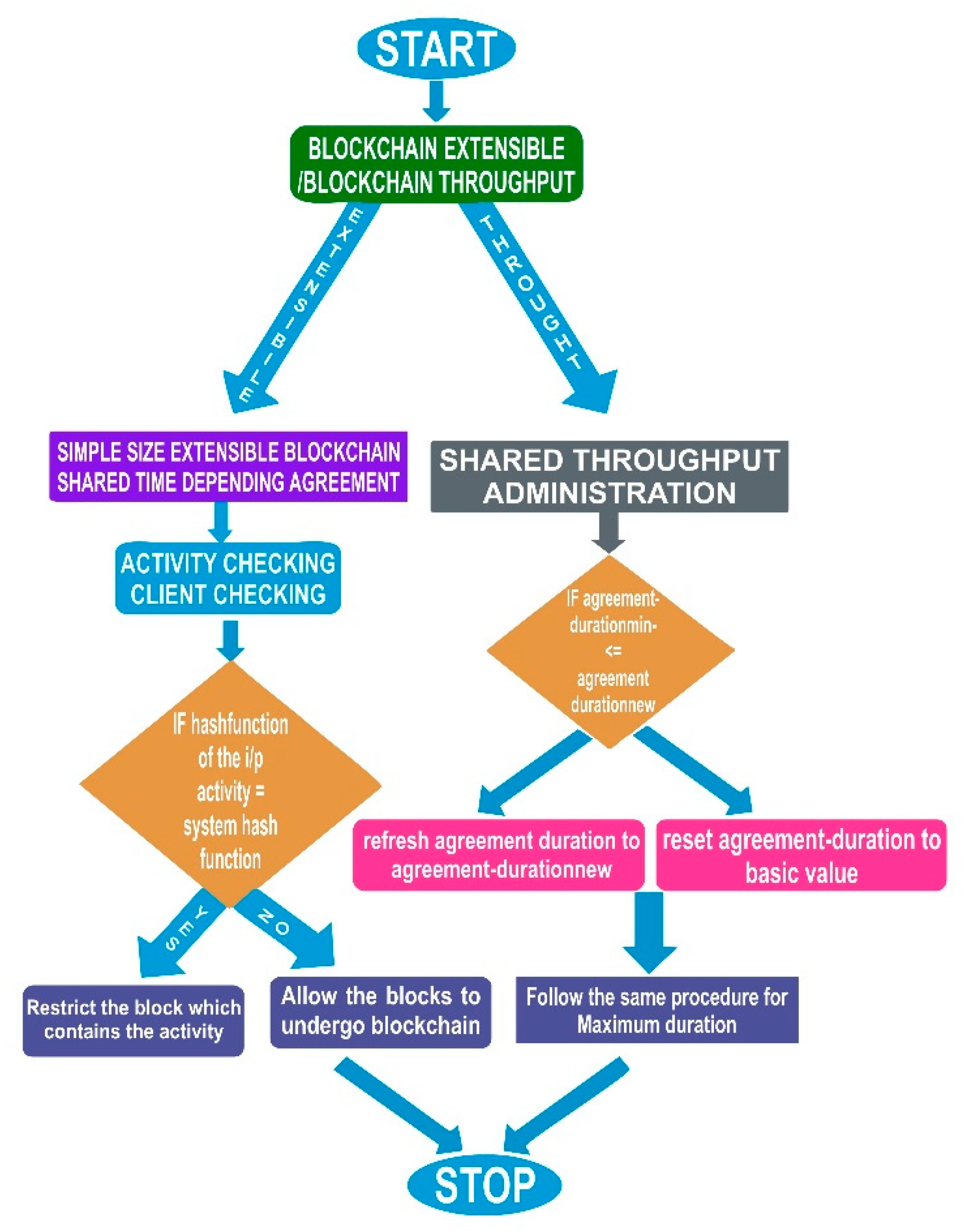
3. Proposed Simple Size Extensible (SSE) Blockchain
An overlay network is developed by the processing and operating components in the blockchain, such as components of the IoT, users of the IoT, and service providers. The overlay network is depicted in
Figure 1. The public key is assigned to every node in the overlay network. In order to ensure inconspicuousness, the new public key is used by the nodes to develop every new activity. Due to some of the restrictions on the IoT, such as limited resources, it is very difficult for it to check every activity of every new block. In order to improve the extensibility and to minimize the operation and irregularity in the packet on the IoT components, one of the inner parts of the overlay nodes maintains the blockchain. Clustering algorithms will be used to form the clusters among the nodes [
32,
33].
A cluster head is then selected based on the protocol stated by the clustering algorithm [
16]. The overlay block administrators (OBA), acting as the chiefs of the clusters, take charge of maintaining the blockchain. The maintenance of the blockchain includes production, checking, and storage of every activity and block. The participants of the clusters verify the work of the OBA. If any doubt or irregularity regarding the OBA is identified by the participants of the cluster, it will not be transferred to the other OBAs. Instead, a new OBA will be created and selected for transferring the activity.
In the current scenario, Tablet requires interaction with the service provider server. The activities of Tablet are stored in the blockchain. Tablet exchanges the needed information with the server of the service provider, which is required to be done in the blockchain. It is already stated that the information exchange of the SSE is different from the activities. One-to-one communication has been maintained for all of the widely spread activities in the environment. The optimal routing has been performed for these activities by the overlay network. The proposed algorithm supports any scheduling algorithm because it is designed in a flexible manner.
The overlay network uses some scheduling algorithms to perform this scheduling. Here, a scheduling algorithm based on ant colony optimization is used. In order to transmit the information packets, the receiver’s overlay block administrator identification should be shared informally in the activities that facilitate the overlay block manager to schedule the packet. As a result, this minimizes the irregularity in the packet during transmission or information interaction. The activity producer authorizes the activity interaction among the overlay nodes through the hash of the information to produce the data integrity. In SSE, all the activities are loaded in the blockchain. The information regarding the IoT components is loaded outside of the blockchain to minimize the irregularity of the packet and utilization of memory in the blockchain. Together, a faith Table record, the faith rate of the other overlay block administrators, and the timeclock specify the creation time of the blocks produced by various overlay block administrators of the blockchain environment. At least “y” verifications (y is checked) should be done out of “x” verifications (x is checked) where x and y are some constant variables. This process is performed to check whether the activity generated by the user is valid or not.
Cryptographic techniques such as digital signatures, hash functions, and asymmetric encryption are used to secure the activities produced by the overlay node. Activities in the blockchain are divided into one-sign activities, and multi-sign activities. One-sign activities constitute only the sign of the activity producer. Multi-sign activities constitute the need for many signs for the actual activities. A multi-sign activity needs
y out of
x signs, in which
y and
x are the number of signs and
. For instance, the structure of the activity is given as
A_RC represents the activity identifier that constitutes the hash of the activity subject. P_A_RC represents the pointer of the predecessor activity of the overlay node. The overlay node develops one or more sign activity and one-sign activity, which is to merge within the same blockchain and audit in the future. These things can be done through the OS outside security and the verification sign of the activity producer. The verified A_RC will be utilized for the verification of the activity. In the situation of one or more sign activity, the outside security OS, and the verification sign of the various processing, the node will operate the result section. In order to perform a valid activity, y signs are needed out of the x signs. As a cumulative x will be the overall activity, in that the y activity which is appended by the user should be verified to ensure that the activity is valid. The result section includes the outside security OS hash function, which the activity producer will utilize for its successor activity. It is mandatory to check the following activity developed by the node of the same overlay network where the OS outside security is changed by the overlay nodes in which it is used to produce each new activity.
The data about the data section generates the added data about the processing nodes in the activity, which could be present in the future. For instance, the activity is produced to obtain the required information from the components of the IoT at a particular time. The time is mentioned in the data about the data section. The above sections are needed for an activity that is stated as valid. Meanwhile, the other sections can be specified according to the application. The original activity is developed as the initial operation of the overlay node that acts as the source end for the digital notes in the blockchain by utilizing any of the given techniques mentioned below. One of these techniques is guarantee authorization [
34]. Here the node depends on the broadly implemented outside security infrastructure of the global web. The nodes in the overlay network communicate a faith guarantee authorization that approves the node in outside security by connecting a verified guarantee. The node adds the guarantee in the initial activity. An overlay block administrator checks the guarantee to check the activity. The overlay block administrator has the right to process the collection of faith-oriented guarantee authorization to do the checking.
Another technique is removing the coin in bitcoin. Some of the nodes will not depend on the outside security infrastructure; in such cases, the node internally develops an initial activity by removing bitcoins [
35]. The node develops a non-temporary activity in the bitcoin blockchain by eliminating a needed quantity of coins, known as burning coins. The location of the removed activity is taken as the information for the initial activity. Each cluster has some number of overlay networks in the blockchain-embedded IoT network. The nodes in the overlay network develop an initial activity with outside security as the removed activity and transfer it to the overlay block administrator and depend on its cluster. In some cases, the overlay block administrator acts as an initial activity producer at that time and communicates the activity to other overlay block administrators. In order to check the arrived initial activity, the overlay block administrator compares the outside security of the initial activity with the outside security of the removed activity in the bitcoin blockchain. After that, the overlay block administrators check the sign in the initial activity.
After checking, the abovementioned techniques utilize overlay block administrators to transfer the initial activity to various overlay block administrators, so as to be loaded in the blockchain. In the SSE blockchain, the flow of information is maintained ideally from the flow of activity. Like the bitcoin, more than one activity is combined and then operated as a single block. The maximum number of activities stored at a single block is represented as A_high activities. The capacity of the A_high creates changes in the throughput of the blockchain, so that many activities can be loaded in the one block with a maximum A_high. Every block includes two major components, such as activities and a block chief. The block chief is represented as given below,
The hash function reveals information about the block, and it is represented as B_RC. The hash function of the last block is represented by L_B_RC and ensures immutability in the blockchain environment. Consider a scenario: an intruder tries to alter the last loaded activity, then the hash function of that particular block loaded in the consecutive block will not work and it will announce the involvement of the intruder. To obtain extensibility, activities and blocks are shared with the overlay block administrators. In the situation of multi-sign activity, the activities will not be considered as actual until y out of x processing nodes in the activities have included their sign.
The resolution of this issue lies in managing a security collection by the overlay block administrator. Security collection includes the collection of outside securities that can process and communicate with the cluster members. The flowchart of the SSE blockchain is shown in
Figure 2. The activities are shared in the cluster to secure the characteristics of the members in the cluster against malevolent overlay block administrators. There is a possibility that the malevolent overlay block administrators will follow the activities accepted by the corresponding member of the cluster to connect various activities, and it will misguide the node. Therefore, from the receiving activities, one of the outside security
B is compared with the arrival in the security collection. Then, the overlay block manager transfers the activities to the members of the cluster in which it has stored the security during the security collection. In either case, the activity will be shared with all other overlay block administrators. All unresolved activities are loaded into the activity pool at each overlay block manager. If
A_high equals the capacity of the execution collection, the overlay block administrator develops the new block using a shared time depending agreement algorithm (STD).
3.1. Shared-Time Depending Agreement Algorithm (STD)
The proposed simple size extensible blockchain introduced an agreement algorithm based on the time duration called the shared-time depending agreement algorithm. The primary objective of any agreement algorithm is to make sure that a block produced is based on random picking, and the fact that there will be limitations in the number of blocks produced. As a result, it secures the blocks against the malevolent blocks. Each and every overlay block administrator will have some latency time before producing a new block. This is done to ensure randomness is achieved in producing the block by the block producers. Some of the overlay block administrators request more short latency time than their quota. At that time, other overlay block administrators check the duration of the new block production from the particular overlay block administrator. By doing this, it limits the overlay block administrators from requesting the short latency time. In such situations, if any overlay block administrator exceeds its count on block production, the extra blocks, as well as their activities will be eliminated. Thus, the standard latency time will minimize fake block production, which is a continuous process if there is no standard latency time. More importance is given to the new block production because these new blocks are shared further in the overlay network and included in the blockchain.
The proposed system limits the number of new blocks generated by the OBAs. A malevolent overlay block administrator may occur, which acts as described above. In order to restrict the malevolent overlay block administrator, a technique called durability utilization is proposed. The objective is to ensure that the overlay block administrator can produce the new block only during that particular duration.
The shared throughput administrator (STA) algorithm is used to maintain durability. The verification process for the activity is described through an algorithm called activity checking, as shown in Algorithm 1.
| Algorithm 1: Activity Checking |
| 1. Input: Overlay Activity (O) |
| 2. Output: True or False |
| 3. Client Checking: |
| 4. if (hash function (O.OS) ≠ O_1.result) then |
| 5. return False; |
| 6. else |
| 7. if (O.OS rescue O.verification Sign) then |
| 8. return True; |
| 9. end if |
| 10. end if |
3.2. Shared Throughput Administrator (STA)
The existing blockchain algorithms that are -based on agreement minimize the throughput of the environment. The amount of activity processed in the blockchain per second is minimized. However, when some agreement algorithms are used for the components of IoT, these types of restrictions will not be accepted because the nodes in the IoT environment communicate with all other nodes in various ways. These issues can be resolved by, the proposed simple size extensibility blockchain, which introduces an algorithm called the shared throughput administrator strategy, to ensure the proper usage of the blockchain and also to provide valuable duration. In this algorithm, the overlay block administrator calculates the usage
β as the ratio of the sum of new activities produced to the sum of activities included in the blockchain. The objective of the shared throughput administrator is to make sure the value range is set by the
β as (
βmin,
βmax). The mathematical formula for processing the
β is as follows
Here,
E represents the endpoint devices of the environment,
P represents the overlay block administrators, and
V represents the mean value of the new activity the node produces per second. When performing calculations, the counts, or values should be specified. The usage of the duration can be altered based on this specification in two ways: first, by altering the duration time, which represents the repetitions of the blocks included in the blockchain; second, by altering the
P-value in which every overlay block administrator can produce one block within the duration time. These two ways are represented in the algorithm shared throughput administrator, as depicted in Algorithm 2.
| Algorithm 2: Shared Throughput Administration |
| 1. Input: β |
| 2. while True do |
| 3. if (β > βmax) then |
| 4. Calculate agreement-durationnew with the formula |
| 5. if (agreement-durationmin <= agreement-durationnew) then |
| 6. refresh agreement-duration to agreement-durationnew |
| 7. else |
| 8. reset agreement-duration to basic value |
| 9. Calculate Z from the formula |
| 10. Cluster again overlay |
| 11. end if |
| 12. end if |
| 13. if (β < βmin) then |
| 14. Calculate agreement-durationnew with the formula |
| 15. if (agreement-durationnew <= agreement-durationmax) then |
| 16. refresh agreement-duration to agreement-durationnew |
| 17. else |
| 18. reset agreement-duration to basic value |
| 19. Calculate Z from the formula |
| 20. Cluster again overlay |
| 21. end if |
| 22. end if |
| 23. end while |
A maximum level field of vision for all algorithms running through the overlay block administrator to maintain the proposed simple size extensible blockchain, is described through the algorithm given below. An overlay block administrator may either obtain an activity A or a Block C through the various overlay block administrators. As in the previous case, the overlay block administrator initially checks the activity, and if it is acceptable, it is included in the collection of waiting activities. In a situation such as A_Collection ≥ block capacity A_max, these activities are combined to develop a block. Non acceptable transactions are eliminated. In some situations, the overlay block administrator checks the block initially by checking the related activities. The overlay block administrator uninterruptedly runs the shared throughput administrator through the same collection of threads to maintain the throughput of the simple size extensible blockchain in relation to the job of the environment as shown in Algorithm 3.
| Algorithm 3: A maximum level field of vision of algorithms implemented by an overlay block administrator |
| 1. Input: A, C |
| 2. while True do |
| 3. Obtaining from Blockchain |
| 4. if attain an A then |
| 5. if (A is acceptable) then |
| 6. A_collection +=A |
| 7. if (capacity.A_collection ≥ A_max) then |
| 8. Execute Shared Throughput Administrator Algorithm |
| 9. end if |
| 10. else |
| 11. Discard A |
| 12. end if |
| 13. end if |
| 14. if Attained a C then |
| 15. Check block |
| 16. end if |
| 17. Execute Shared Throughput Administrator Algorithm |
| 18. end while |
4. Results and Discussion
This section details the results and discusses the research work. The results have been obtained and verified using the following parameters: irregularity of packets (in kilobytes), the number of overlay block administrators used, operating time (in milliseconds), and the percentage of activities checked for the blockchain environment.
Table 1,
Table 2 and
Table 3, and
Figure 3,
Figure 4 and
Figure 5 show the comparative results for the existing systems such as the lightweight, scalable blockchain and baseline overhead, and the proposed system, i.e., the simple size extensible blockchain based on the packet irregularity and operating time.
Table 4,
Table 5 and
Table 6 and
Figure 5,
Figure 6,
Figure 7 and
Figure 8 show the comparative results for the existing systems such as lightweight, scalable blockchain and baseline overhead, and the proposed simple size extensible blockchain based on the percentage of activity checked and operating time.
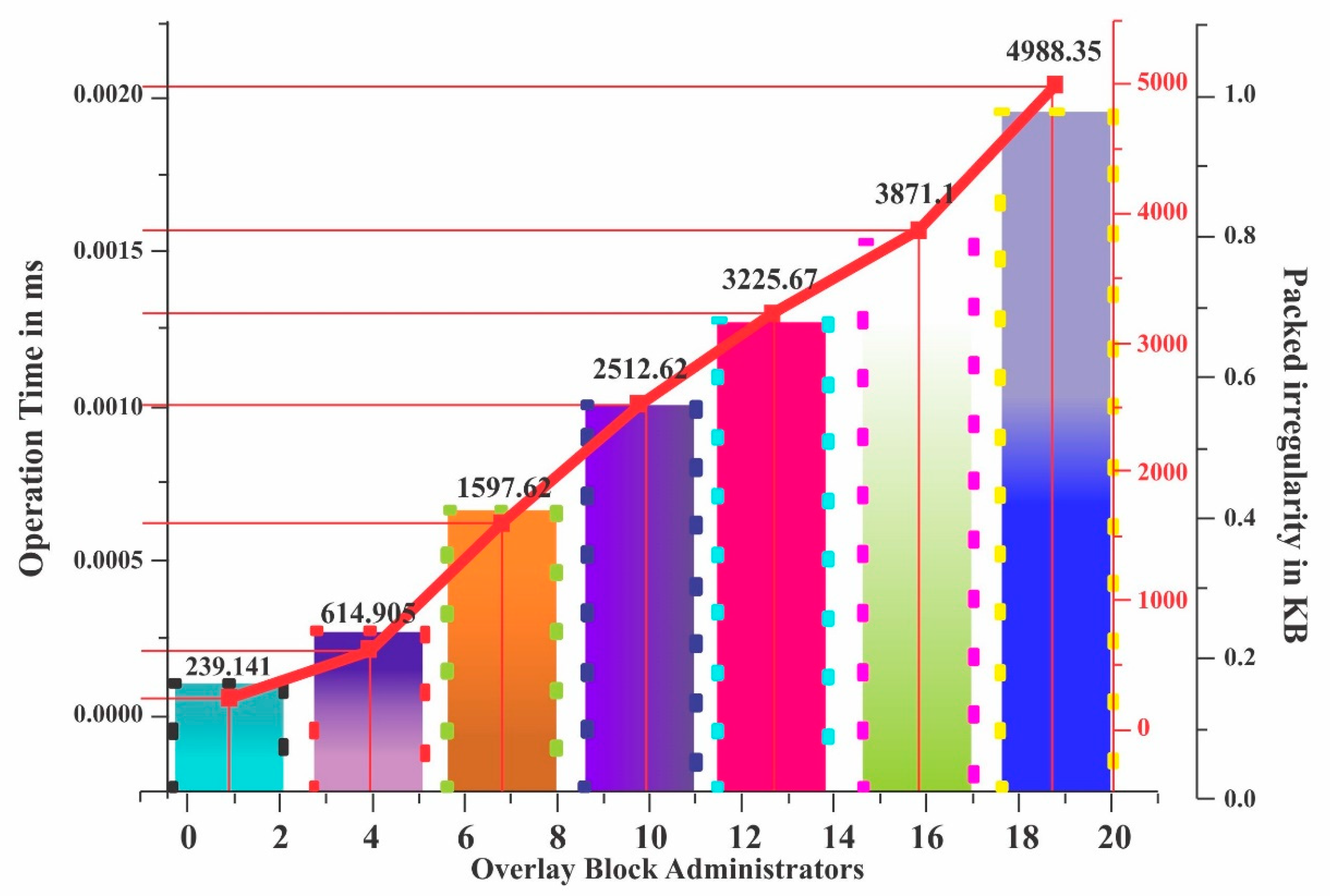
Table 1 and
Figure 3 depict the performance of an existing system, the baseline packet overhead. Here, the operating time and packet irregularity is highlighted. The operating time is measured in milliseconds, and packet irregularity is measured in kilobytes.
Table 1 gives the actual number of overlay block (OB) administrators whereas the graph depicts this as a whole. The OB administrators from 1 to 2 have an operating time of 1.0 ×
ms and the packet irregularity is 239.141 KB. Moreover, the procedure followed is the same for the remaining OB administrators.
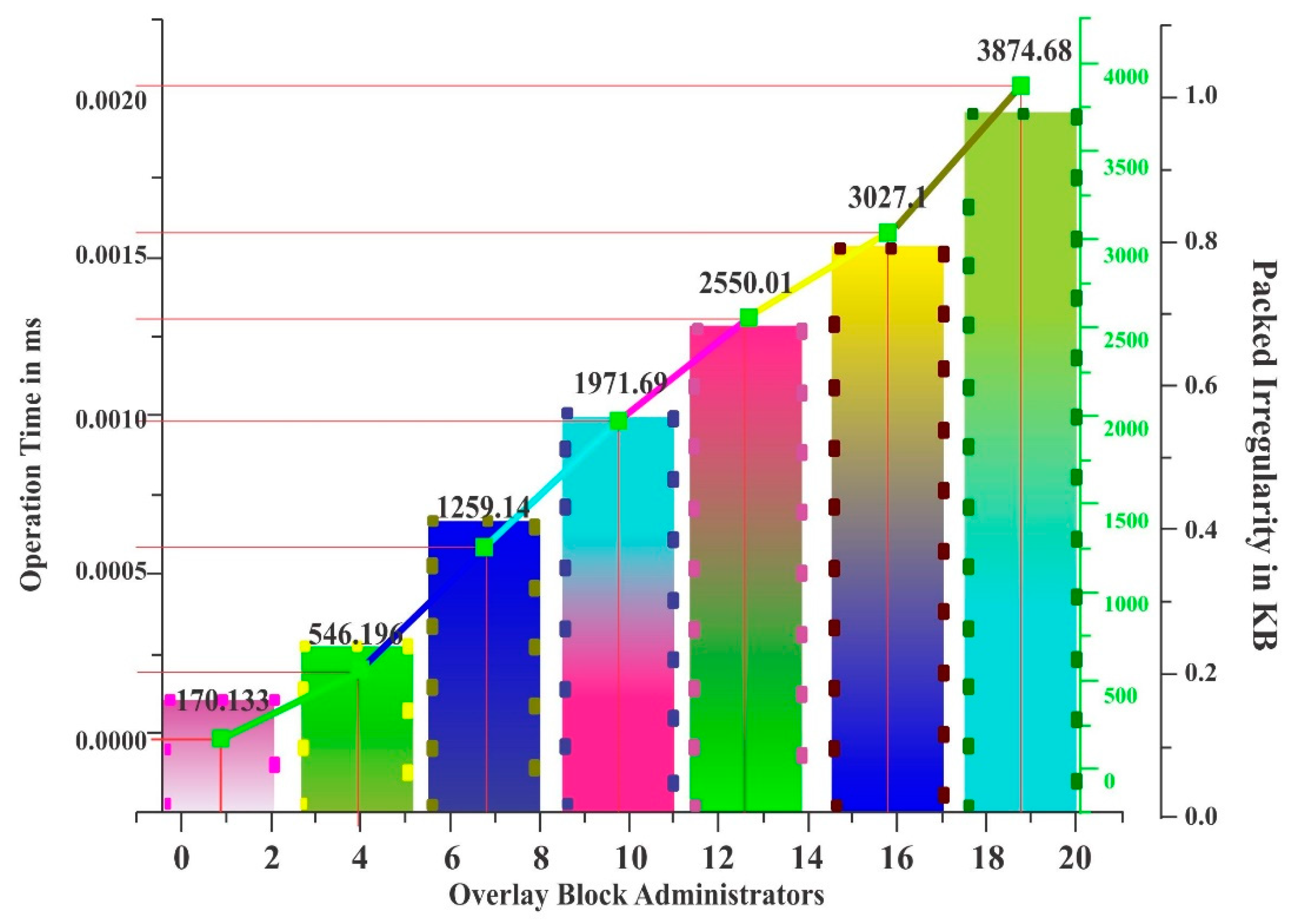
Table 2 and
Figure 4 depict the performance of another existing system called the light weight scalable blockchain. Here, the operating time and packet irregularity is examined. The operating time is measured in milliseconds, and packet irregularity is measured in kilobytes.
Table 2 gives the actual number of overlay block administrators, whereas the graph depicts this as a whole. The OB administrators from 1 to 2, have an operating time of 1.0 ×
ms and the packet irregularity is 170.133 KB. Moreover, the procedure followed is the same for the remaining OB administrators.
From the above results, it can be seen that the proposed system, the simple size extensible blockchain performs well when compared to existing systems such as the baseline overhead and lightweight scalable blockchain in terms of packet irregularity and operating time. The proposed system minimizes the packet overhead as well as the operating time of the blockchain environment. It produces packet irregularity in the range of 101.124 kilobytes to 3337.08 kilobytes, which is shown in
Table 3 and
Figure 5. Meanwhile, the existing baseline overhead system produces packet irregularity in the range of 239.141 kilobytes to 4988.35 kilobytes, which is shown in
Table 1. The existing system, the lightweight, scalable blockchain, produces packet irregularity in the range of 170.133 kilobytes to 3874.68 kilobytes, which is shown in
Table 2.
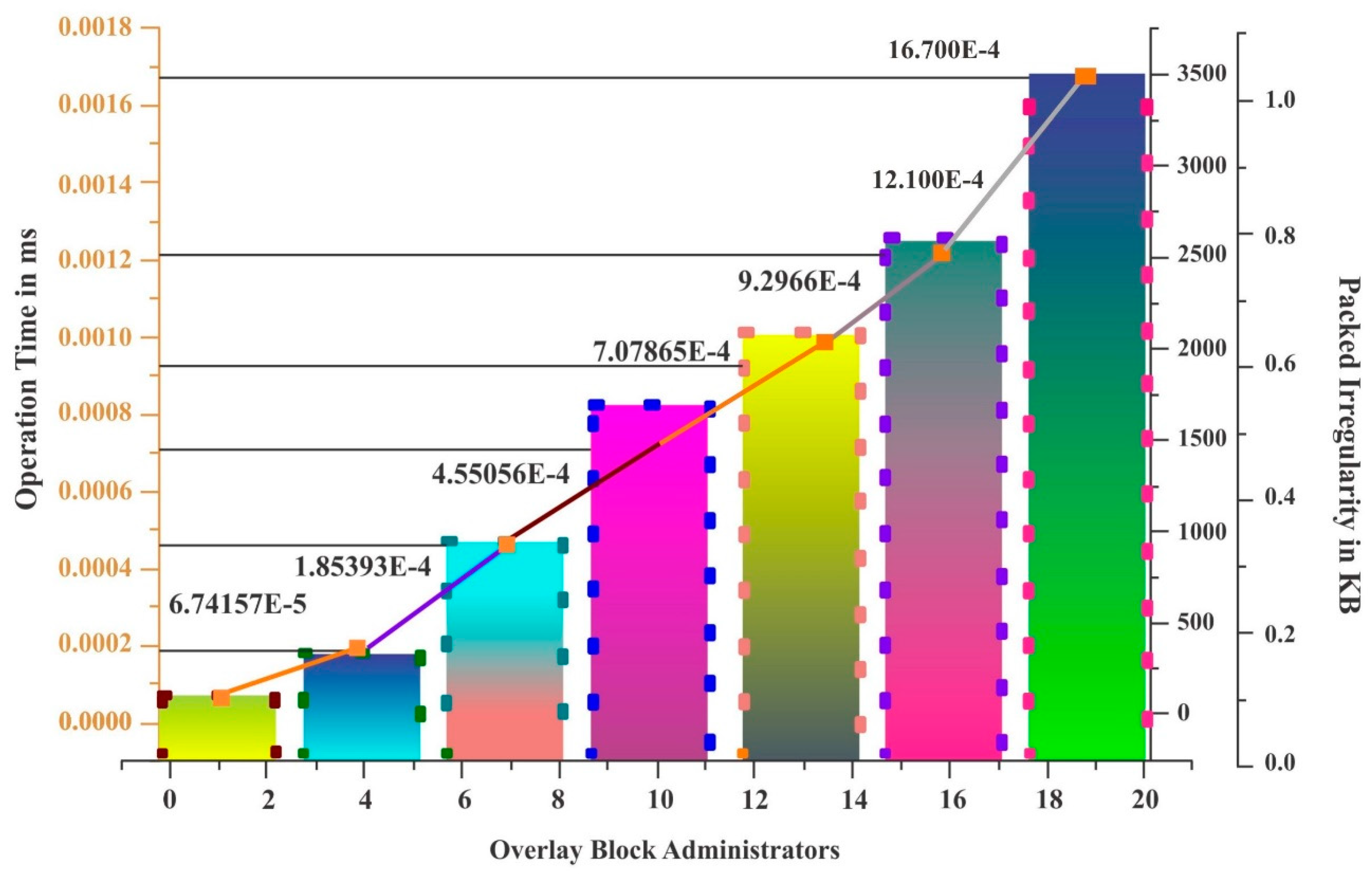
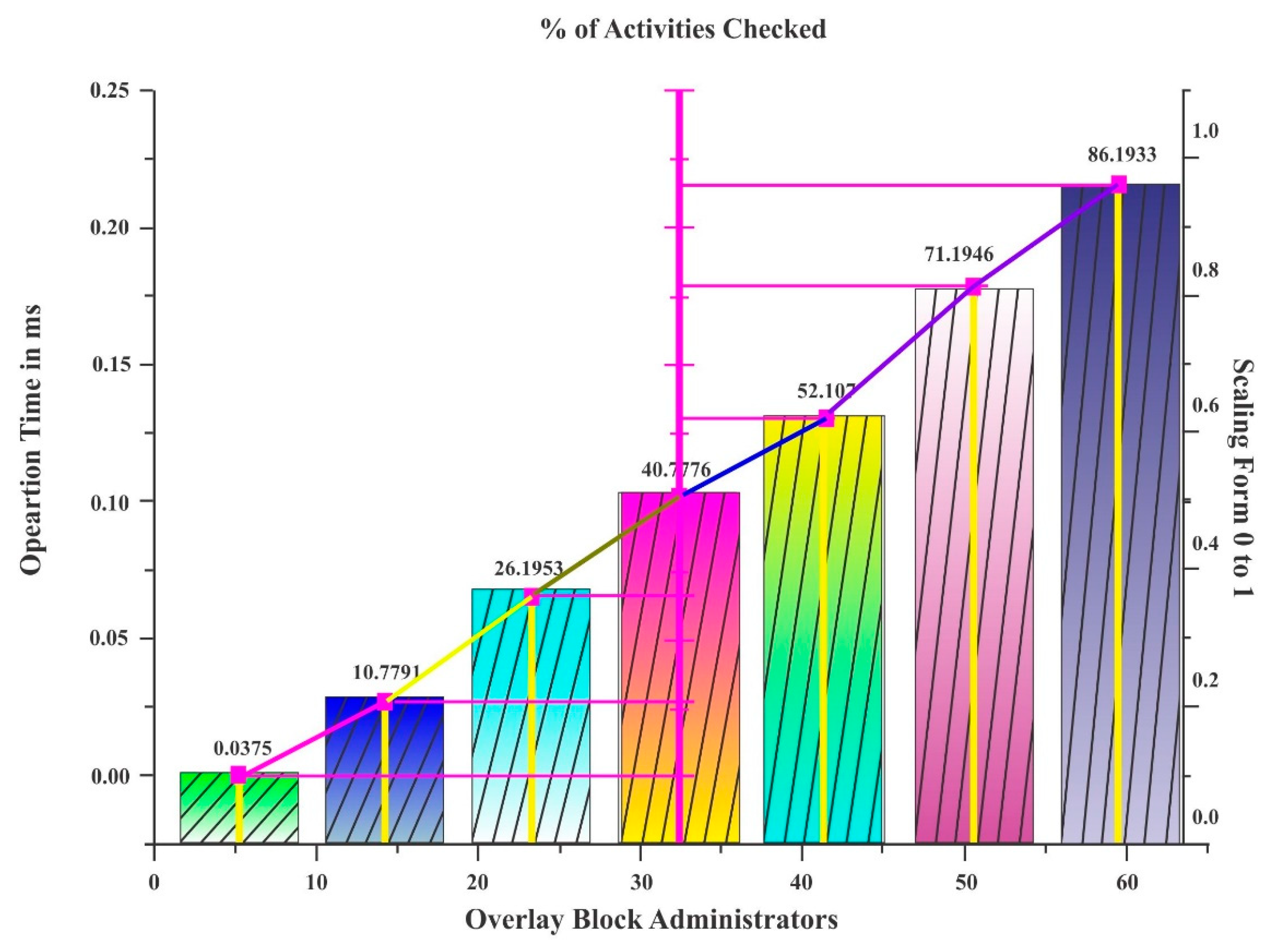
Table 4 and
Figure 6 depict the performance of one of the existing systems called baseline packet overhead. Here, the operating time and % of activities checked are given. The operating time is measured in milliseconds, and the activities checked are given as a percentage.
Table 4 gives the actual number of overlay block administrators, whereas the graph depicts this as a whole. The OB administrators from 1 to 5, have an operating time of 9.5 ×
ms, and the % of activities checked is −0.0375%. Moreover, the procedure followed is the same for the remaining OB administrators.
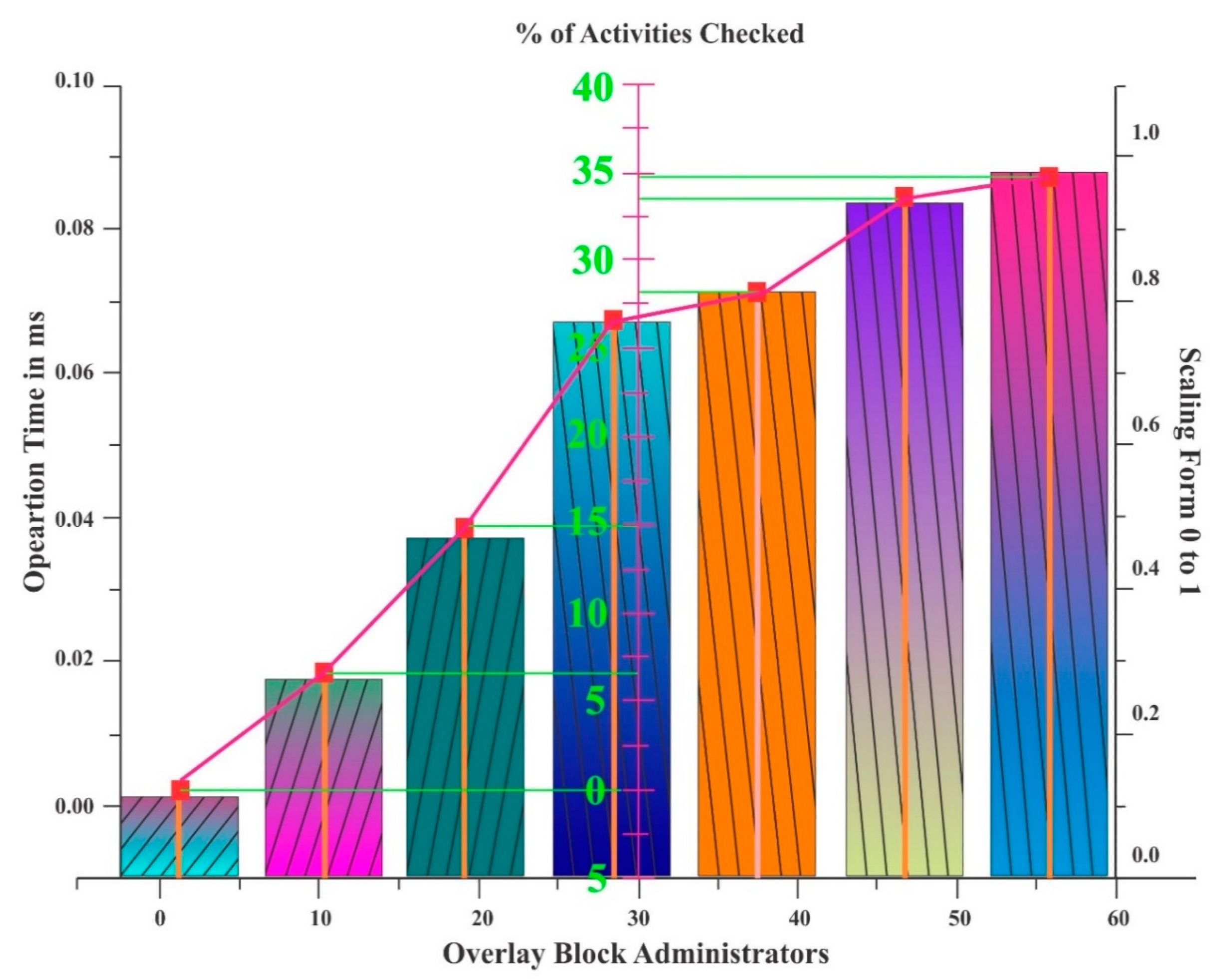
Table 5 and
Figure 7 depict the performance of the existing light weight scalable blockchain system. Here, the operating time and % of activities checked are given. The operating time is measured in milliseconds, and the activities checked are given as a percentage.
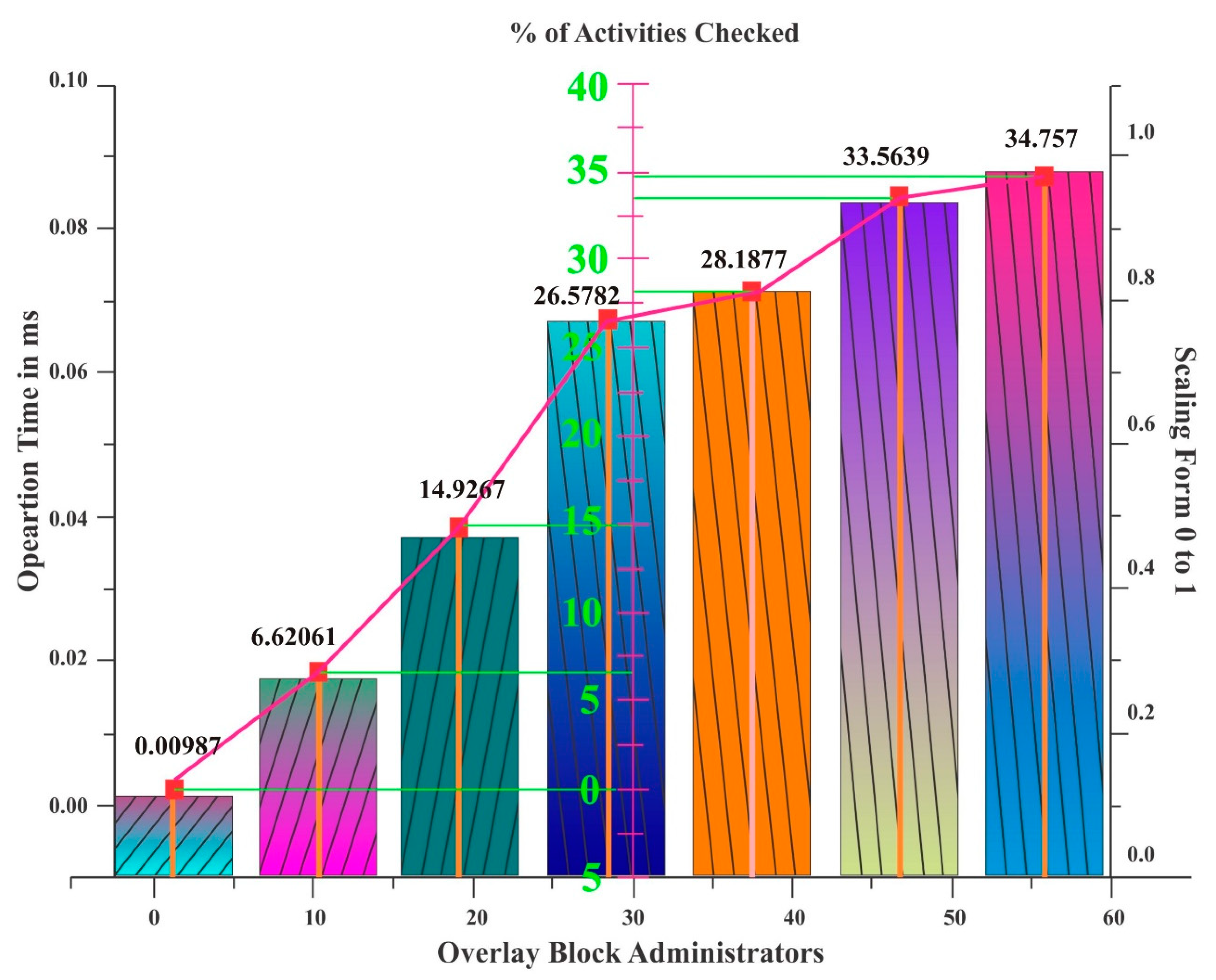
Table 5 gives the actual number of overlay block administrators, whereas the graph depicts this as a whole. The OB administrators from 1 to 5, have an operating time of 90.00102 ms, and the % of activities checked is −0.00987%. Moreover, the procedure followed is the same for the remaining OB administrators.
The results shown in
Table 4,
Table 5 and
Table 6, highlight that the proposed system simple size extensible blockchain performs well when compared to the existing systems such as baseline overhead and lightweight, scalable blockchain with respect to the percentage of activity checked and operating time. It also minimizes the percentage of activity checked as well as the operating time of the blockchain environment. The percentage of activity checked ranges from 0.40855 to 22.2046, which is shown in
Table 6 and
Figure 8. Meanwhile, the existing baseline overhead system utilizes a percentage of activity checked ranging from −0.0375 to 86.1933, which is shown in
Table 4. The existing lightweight scalable blockchain system utilizes a percentage of activity checked that ranges from −0.00987 to 34.757, as shown in
Table 5.