A Smart Grid AMI Intrusion Detection Strategy Based on Extreme Learning Machine
Abstract
1. Introduction
2. Related Works
3. Research Foundation
- (1)
- Randomly initialize the input weights ωi and the offset of the hidden layer bi,
- (2)
- Calculate the output weight of the hidden layer H and
- (3)
- Calculate the output weight from the hidden layer to the output layer .
- (1)
- Population initialization
- (2)
- Individual fitness calculation
- (3)
- Individual evolution
- Selection operation: Selection operation is based on the fitness of individuals in the population and randomly selects L parent pairs from the t generation population of Y(t), where .
- Crossover operation: Crossover operation is the key algorithm in GA, which determines the global convergence. Among them, the key criterion is that the offspring chromosome should inherit the excellent characteristics of the parent chromosome and, at the same time, ensure the feasibility of the offspring itsel and,. further, randomly select L/2 chromosomes of the parents. When the probability of the chromosomes is less than the crossover probability Px, the crossover is made by randomly formulating one or more points, so as to obtain two progeny chromosomes and, finally, obtain L intermediate individuals by crossover.
- Mutation operation: L intermediary individuals are obtained through crossover operations. Then, the mutation operation is performed according to the mutation probability Pm, which is achieved by changing alleles and, finally, determined to form L candidate individuals.
- (4)
- Child selection
- Calculate the fitness value of each candidate individually,
- Calculate the sum of the fitness values of all candidates in the population and record the intermediate cumulative value S-mid,
- randomly generate a number between 0 < n < sum,
- Select the corresponding first chromosome of S-mid to enter a new population,
- Repeat steps (c) and (d) until a population of chromosomes is formed and
- Stop evolution.
4. Data Selection and Technical Evaluation Indicators
4.1. Data Selection
- (1)
- DoS attack: Denial of Service attack. Classification identification: back, and, Neptune, pod, smur and, teardrop.
- (2)
- R2L attack: Unauthorized access from a remote host. Classification identification: ftp_write, guess_passwd, imap, multihop, phf, spy, warezclient and warezmaster.
- (3)
- U2R attack: Local supergroup users have unauthorized access to remote computers. Classification identification: buffer_overflow, loadmodule, perl and rootkit.
- (4)
- Probing attack: Attack by scanning ports. Classification identification: ipsweep, nmap, portsweep and satan.
4.2. Technical Evaluation Indicators
5. ELM Intrusion Detection Algorithm Based on Optimization
- (1)
- Population initialization
- (2)
- Fitness setting and calculation
- (3)
- Parameter optimization
6. Experiment
6.1. Intrusion Detection Technology Based on the GA-ELM
6.2. Intrusion Detection Technology Based on the OS-ELM
6.3. Comparison of Detection Indexes
6.3.1. Influence of the Number of Hidden Layer Neurons on the Test Error
6.3.2. Evaluation of Other Indicators
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- FBI-Smart Meter Hacks Likely to Spread. Available online: http://krebsonsecurity.com/2012/04/fbi-smart-meter-hacks-likely-to-spread/ (accessed on 22 May 2020).
- Knapp, D.E.; Langill, J.T. Industrial Cyber Security History and Trends. In Industrial Network Security, 2nd ed.; Elsevier Inc.: Amsterdam, The Netherlands, 2015; Chapter 3; pp. 41–53. [Google Scholar]
- Tang, Y.; Chen, Q.; Li, M.Y. Overview of network attack research in the environment of power information physical fusion system. Power Syst. Autom. 2016, 40, 59–69, (In Chinese with English Abstract). [Google Scholar]
- Vega Vega, R.A.; Chamoso-Santos, P.; González Briones, A.; Casteleiro-Roca, J.-L.; Jove, E.; Herrero, A.; Corchado, E.; Calvo-Rolle, J.L.; Matsui, K.; Meizoso-Lopez, M.d.C.; et al. Intrusion Detection with unsupervised techniques for Network Management Protocols over Smart Grids. Appl. Sci. 2020, 10, 2276. [Google Scholar] [CrossRef]
- Ipakchi, A.; Albuyeh, F. Grid of the Future. IEEE Power Energy Mag. 2013, 11, 20. [Google Scholar] [CrossRef]
- Zhang, J.C.; Chen, Z.Y. The impact of AMI on the future power system. Autom. Electr. Power Syst. 2010, 34, 20–23. [Google Scholar]
- Modaghegh, H.; Abasgholi, B.; Gilani, N.; Arian, M.; Soleimani, V. Advanced Metering Infrastructure System Architecture. In Proceedings of the Asia-Pacific Power and Energy Engineering Conference, Wuhan, China, 25–28 March 2011; pp. 1–6. [Google Scholar]
- Zhou, L.; Chen, S. A Survey of Research on Smart Grid Security. In Network Computing and Information Security 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 345, pp. 395–405. [Google Scholar]
- Shein, R. Security Measures for Advanced Metering Infrastructure Components. In Proceedings of the IEEE Power & Energy Engineering Conference, Chengdu, China, 28–31 March 2010; pp. 1–3. [Google Scholar]
- Zhang, X.D.; Tong, W.M. Research on Fusion Algorithm of Elliptic Curve Cryptography in Advanced Metering Infrastructure Communication. In Proceedings of the International Symposium on Computational Intelligence and Design, Hangzhou, China, 13–14 December 2014; pp. 395–398. [Google Scholar]
- Soykan, E.U.; Ersoz, S.D.; Soykan, G. Identity based signcryption for advanced metering infrastructure. In Proceedings of the IEEE Smart Grid Congress & Fair, Istanbul, Turkey, 29–30 April 2015; pp. 1–5. [Google Scholar]
- Kamto, J.; Qian, L.; Fuller, J. Key Distribution and Management for Power Aggregation and Accountability in Advance Metering Infrastructure. In Proceedings of the IEEE Smart Grid Communications, Tainan, China, 5–8 November 2012; pp. 360–365. [Google Scholar]
- Wan, Z.; Wang, G.; Yang, Y. SKM: Scalable Key Management for Advanced Metering Infrastructure in Smart Grids. IEEE Trans. Ind. Electron. 2014, 61, 7055–7066. [Google Scholar] [CrossRef]
- Woong, G.; Jin, K. Two-Dimensional Key Table-Based Group Key Distribution in Advanced Metering Infrastructure. J. Appl. Math. 2014, 2014, 149649. [Google Scholar]
- Jeon, J.W.; Lim, S.H.; Yi, O.Y. A Wireless Network Structure and AKA (Authentication and Key Agreement) Protocol of Advanced Metering Infrastructure on the Smart Grid based on Binary CDMA. J. Korea Inst. Inf. Sec. Cryptol. 2010, 20, 111–124. [Google Scholar]
- Yan, Y.; Qian, Y.; Sharif, H. A Secure and Reliable In-Network Collaborative Communication Scheme for Advanced Metering Infrastructure in Smart Grid. In Proceedings of the IEEE Wireless Communications & Networking Conference, Cancun, Quintana Roo, Mexico, 28–31 March 2011; pp. 909–914. [Google Scholar]
- Deng, P.; Yang, L. A Secure and Privacy-Preserving Communication Scheme for Advanced Metering Infrastructure. In Proceedings of the IEEE PES Innovative Smart Grid Technologies Conference, Washington, DC, USA, 24–27 February 2012; pp. 1–5. [Google Scholar]
- Chen, S.; Xu, K.; Li, Z. A Privacy-Aware Communication Scheme in Advanced Metering Infrastructure (AMI) Systems. In Proceedings of the IEEE Wireless Communications & Networking Conference, Shanghai, China, 7–10 April 2013; pp. 1860–1863. [Google Scholar]
- Saputro, N.; Akkaya, K. On preserving user privacy in Smart Grid advanced metering infrastructure applications. SEC Commun. Netw. 2014, 7, 206–220. [Google Scholar] [CrossRef]
- Yan, Y.; Hu, R.Q.; Das, S.K. An efficient security protocol for advanced metering infrastructure in smart grid. IEEE Netw. 2013, 27, 64–71. [Google Scholar] [CrossRef]
- Yan, Y.; Hu, R.Q.; Das, S.K. A Security Protocol for Advanced Metering Infrastructure in Smart Grid. In Proceedings of the IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 649–654. [Google Scholar]
- Berthier, R.; Sanders, W.H.; Khurana, H. Intrusion Detection for Advanced Metering Infrastructures: Requirements and Architectural Directions. In Proceedings of the First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 350–355. [Google Scholar]
- Zhang, Y.; Wang, L.; Sum, W. Distributed IDS in a multi-layer network architecture of smart grids. IEEE Trans. Smart Grid 2011, 2, 796–808. [Google Scholar] [CrossRef]
- Krishna, V.B.; Weaver, G.A.; Sanders, W.H. PCA-Based Method for Detecting Integrity Attacks on Advanced Metering Infrastructure. In Quantitative Evaluation of Systems; Springer International Publishing: Cham, Switzerland, 2015. [Google Scholar]
- Mohammadi, B.; Nasim, M.; Jelena, M.; Vojislav, B. A framework for intrusion detection system in advanced metering infrastructure. SEC Commun. Netw. 2014, 7, 205. [Google Scholar] [CrossRef]
- Faisal, M.A.; Aung, Z.; Williams, J.R. Securing Advanced Metering Infrastructure Using Intrusion Detection System with Data Stream Mining. In Proceedings of the Pacific Asia conference on Intelligence and Security Informatics, Kuala Lumpur, Malaysia, 29–30 May 2012; pp. 96–111. [Google Scholar]
- Faisal, M.A.; Aung, Z.; Williams, J.R. Data-Stream-Based Intrusion Detection System for Advanced Metering Infrastructure in Smart Grid: A Feasibility Study. Syst. J. IEEE 2015, 9, 31–44. [Google Scholar] [CrossRef]
- Alseiari, F.A.A.; Aung, Z. Real-Time Anomaly-Based Distributed Intrusion Detection Systems for Advanced Metering Infrastructure Utilizing Stream Data Mining. In Proceedings of the International Conference on Smart Grid & Clean Energy Technologies, Offenburg, Germany, 20–23 October 2015; pp. 148–153. [Google Scholar]
- Berthier, R.; Sanders, W.H. Specification-Based Intrusion Detection for Advanced Metering Infrastructures. In Proceedings of the IEEE Pacific Rim International Symposium on Dependable Computing, Pasadena, CA, USA, 12–14 December 2011; pp. 184–193. [Google Scholar]
- Jokar, P.; Nicanfar, H.; Leung, V.C.M. Specification-Based Intrusion Detection for Home Area Networks in Smart Grids. In Proceedings of the IEEE International Conference on Smart Grid Communications, Brussels, Belgium, 17–20 October 2011; pp. 208–213. [Google Scholar]
- Ali, M.Q.; Alshaer, E. Probabilistic Model Checking for AMI Intrusion Detection. In Proceedings of the IEEE International Conference on Smart Grid Communications, Vancouver, BC, Canada, 21–24 October 2013; pp. 468–473. [Google Scholar]
- Ali, M.Q.; Alshaer, E. Configuration-Based IDS for Advanced Metering Infrastructure. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 451–462. [Google Scholar]
- Ali, M.Q.; Alshaer, E. Randomization-Based Intrusion Detection System for Advanced Metering Infrastructure. ACM Trans. Inf. Syst. Sec. 2015, 18, 7. [Google Scholar] [CrossRef]
- Ruan, H.M.; Yeap, G.W.; Lei, C.L. Hybrid intrusion detection framework for advanced metering infrastructure. Front. Artif. Intell. Appl. 2015, 2015, 894–903. [Google Scholar]
- Gao, J.L.; Chai, S.C.; Zhang, B.H.; Xia, Y.Q. Research on Network Intrusion Detection Based on Incremental Extreme Learning Machine and Adaptive Principal Component Analysis. Energies 2019, 12, 1223. [Google Scholar] [CrossRef]
- Hakim, L.; Fatma, R.; Novriandi. Influence Analysis of Feature Selection to Network Intrusion Detection System Performance Using NSL-KDD Dataset. In Proceedings of the International Conference on Computer Science, Information Technology, and Electrical Engineering, Jember, Indonesia, 16–17 October 2019; pp. 217–220. [Google Scholar]
- Tabrizi, F.M.; Pattabiraman, K. A Model-Based Intrusion Detection System for Smart Meters. In Proceedings of the IEEE International Symposium on High-assurance Systems Engineering, Miami Beach, FL, USA, 9–11 January 2014; pp. 17–24. [Google Scholar]
- Liu, X.; Zhu, P.; Zhang, Y. A Collaborative Intrusion Detection Mechanism Against False Data Injection Attack in Advanced Metering Infrastructure. IEEE Trans. Smart Grid 2015, 6, 2435–2443. [Google Scholar] [CrossRef]
- Dong, Y.; Wang, R.; He, J. Real-Time Network Intrusion Detection System Based on Deep Learning. In Proceedings of the IEEE 10th International Conference on Software Engineering and Service Science, Beijing, China, 18–20 October 2019; pp. 1–4. [Google Scholar]
- Yu, S.E.; Cha, J.M.; Lee, T.Y.; Kim, J.; Mun, D.W. Features Recognition from Piping and Instrumentation Diagrams in Image Format Using a Deep Learning Network. Energies 2019, 12, 4425. [Google Scholar] [CrossRef]
- Ishaque, M.; Hudec, L. Feature Extraction using Deep Learning for Intrusion Detection System. In Proceedings of the International Conference on Computer Applications & Information Security, Riyadh, Saudi Arabia, 19–21 March 2019; pp. 1–5. [Google Scholar]
- Huang, G.B.; Zhu, Q.Y.; Siew, C.K. Extreme learning machine: Theory and applications. Neurocomputing 2006, 70, 489–501. [Google Scholar] [CrossRef]
- Zhang, K.; Duan, C.; Jia, H.T. Genetic simulated annealing-based coverage-enhancing algorithm for multimedia directional sensor networks. Int. J. Comm. Syst. 2015, 28, 1598–1609. [Google Scholar] [CrossRef]
- Sapre, S.; Ahmadi, P.; Islam, K. A Robust Comparison of the KDDCup99 and NSL-KDD IoT Network Intrusion Detection Datasets Through Various Machine Learning Algorithms. arXiv 2019, arXiv:1912.13204. [Google Scholar]
- Huang, S.H.; Chen, W.Z.; Li, J. Network intrusion detection technology based on PCA and elm. J. Jilin Univ. 2017, 5, 576–583, (In Chinese with English Abstract). [Google Scholar]
- Zhan, X.; Yuan, H.B.; Wang, X.D. Research on Block Chain Network Intrusion Detection System. In Proceedings of the International Conference on Computer Network, Electronic and Automation, Xi’an, China, 27–29 September 2019; pp. 191–196. [Google Scholar]
- Liang, N.Y.; Huang, G.B.; Saratchandra, P. A Fast and Accurate Online Sequential Learning Algorithm for Feedforward Networks. IEEE Trans. Neural Netw. 2006, 17, 1411–1423. [Google Scholar] [CrossRef] [PubMed]


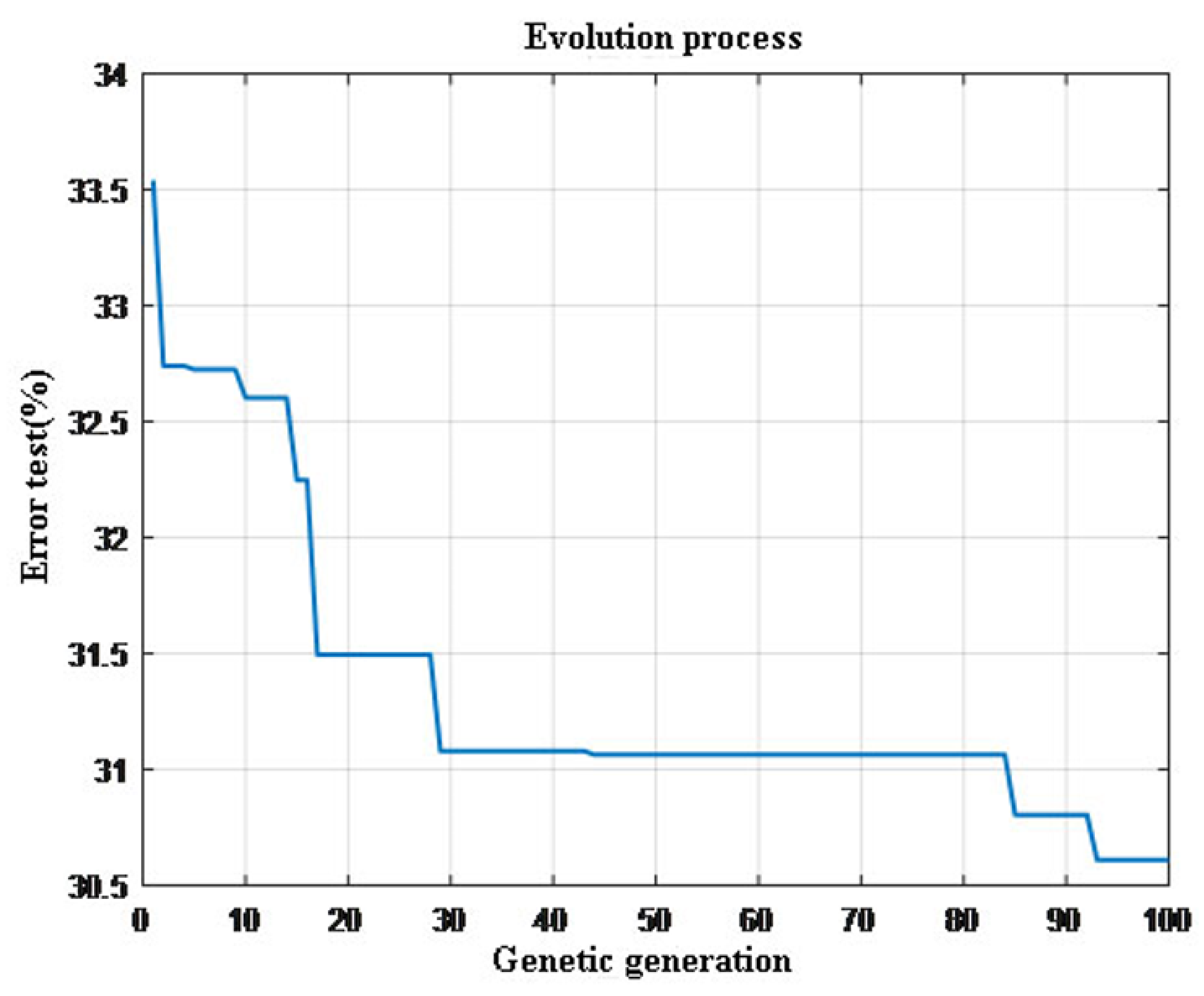
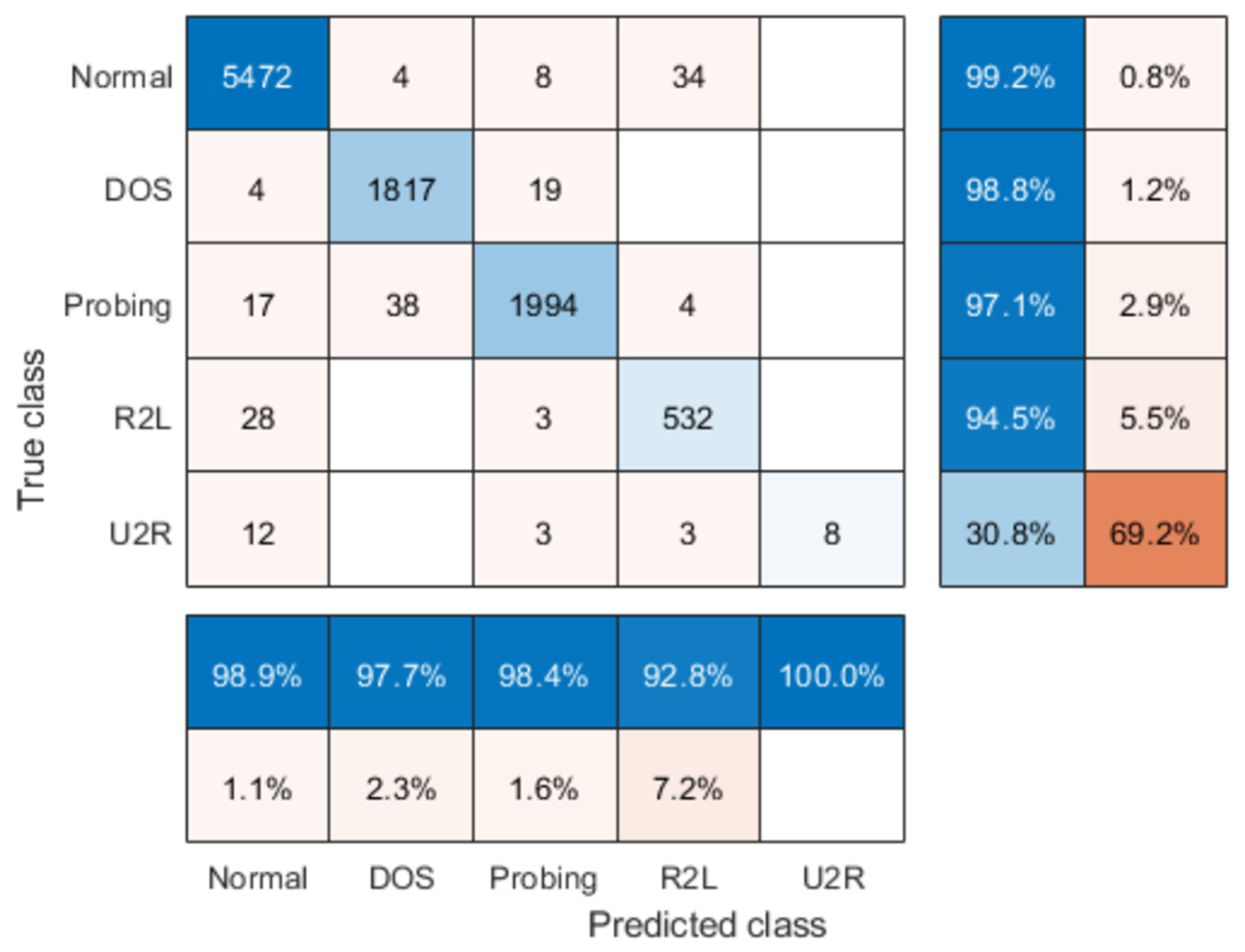
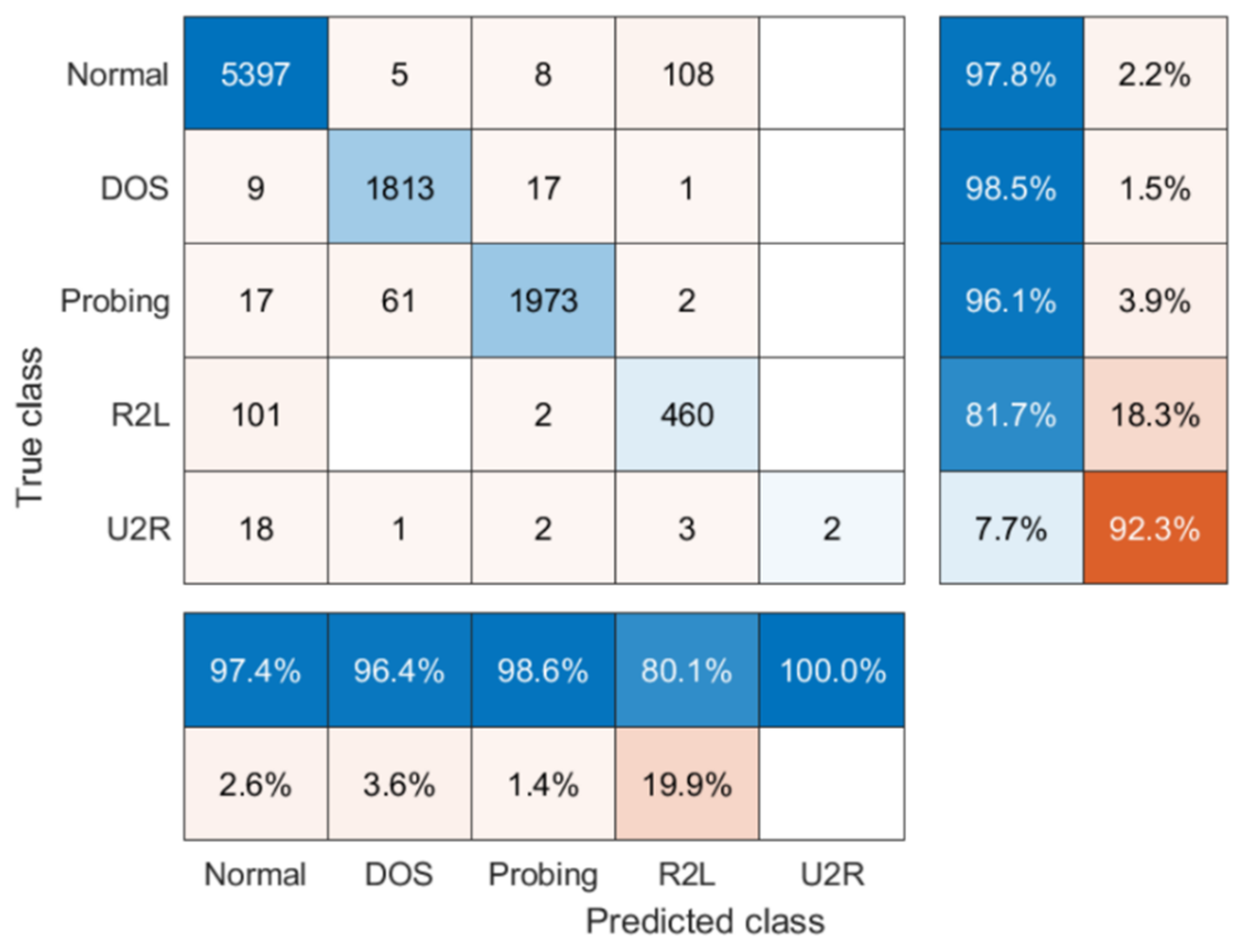

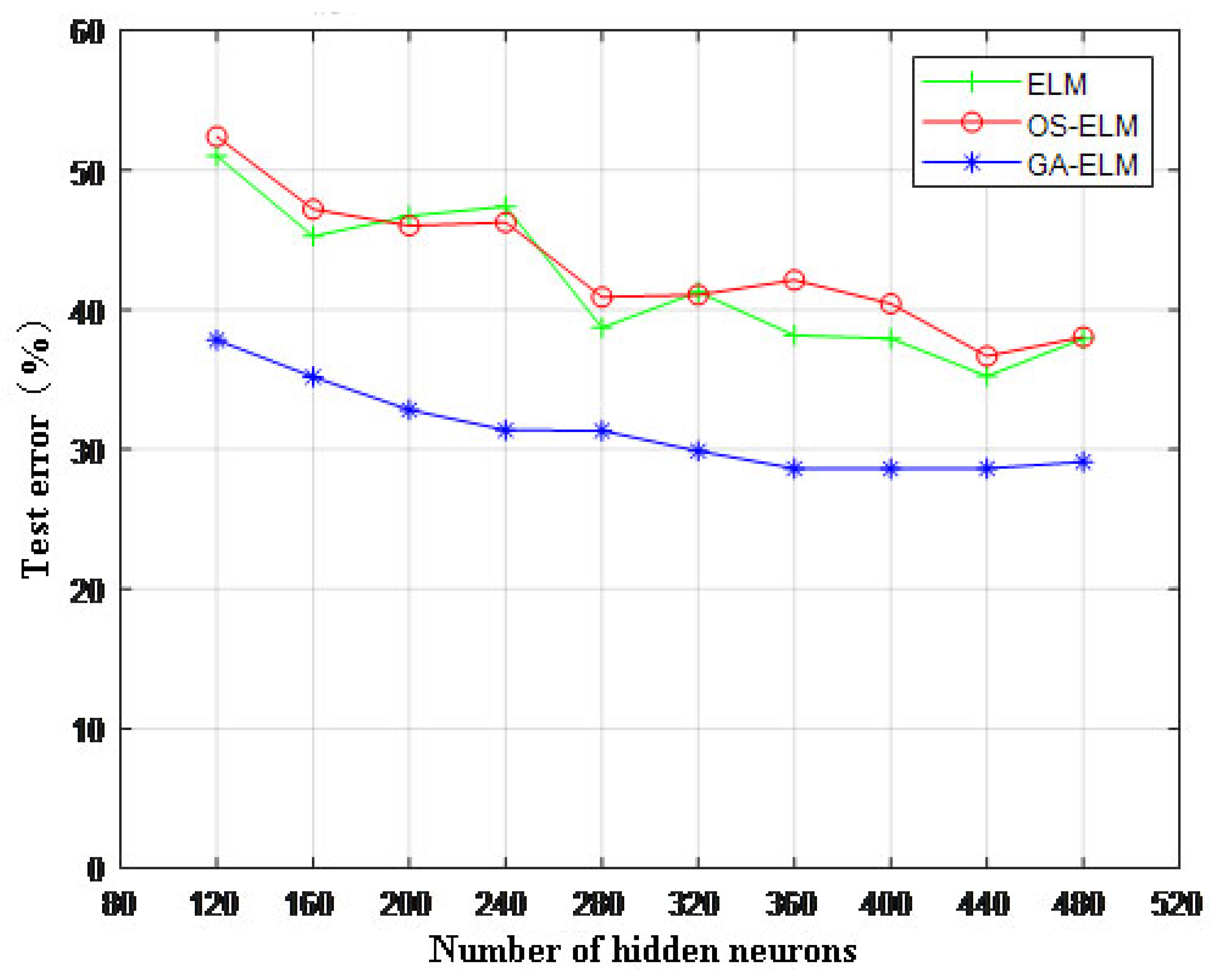
| Type of Invasion | 10% Data Set | Training Set | Test Set | |||
|---|---|---|---|---|---|---|
| Quantity | Proportion/% | Quantity | Proportion/% | Quantity | Proportion/% | |
| Normal | 97,278 | 19.69 | 5518 | 55.18 | 5518 | 55.18 |
| DoS | 391,458 | 79.24 | 1840 | 18.4 | 1840 | 18.4 |
| Probing | 4107 | 0.83 | 2053 | 20.53 | 2053 | 20.53 |
| R2L | 1126 | 0.23 | 563 | 5.63 | 563 | 5.63 |
| U2R | 52 | 0.01 | 26 | 0.26 | 26 | 0.26 |
| Total | 494,021 | 100.00 | 10,000 | 100.00 | 10,000 | 100.00 |
| Identification Type | Error Detection Number/Total Number of Samples | ||
|---|---|---|---|
| GA-ELM | OS-ELM | ELM | |
| Normal | 46/5518 | 72/5518 | 121/5518 |
| DoS | 23/1840 | 28/1840 | 27/1840 |
| Probing | 59/2053 | 71/2053 | 80/2053 |
| R2L | 31/563 | 75/563 | 103/563 |
| U2R | 18/26 | 21/26 | 24/26 |
| Identification Type | Detection Rate/% | ||
|---|---|---|---|
| GA-ELM | OS-ELM | ELM | |
| Normal | 99.17 | 98.70 | 97.81 |
| DoS | 98.75 | 98.48 | 98.53 |
| Probing | 97.13 | 96.54 | 96.10 |
| R2L | 94.49 | 86.68 | 81.71 |
| U2R | 30.77 | 19.23 | 7.69 |
| Identification Type | Three Methods | ||
|---|---|---|---|
| GA-ELM | OS-ELM | ELM | |
| Correct rate/% | 98.23 | 97.33 | 96.45 |
| False alarm rate/% | 0.83 | 1.30 | 2.19 |
| False-negative rate/% | 1.36 | 2.59 | 3.24 |
| Accuracy/% | 98.90 | 97.91 | 97.38 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, K.; Hu, Z.; Zhan, Y.; Wang, X.; Guo, K. A Smart Grid AMI Intrusion Detection Strategy Based on Extreme Learning Machine. Energies 2020, 13, 4907. https://doi.org/10.3390/en13184907
Zhang K, Hu Z, Zhan Y, Wang X, Guo K. A Smart Grid AMI Intrusion Detection Strategy Based on Extreme Learning Machine. Energies. 2020; 13(18):4907. https://doi.org/10.3390/en13184907
Chicago/Turabian StyleZhang, Ke, Zhi Hu, Yufei Zhan, Xiaofen Wang, and Keyi Guo. 2020. "A Smart Grid AMI Intrusion Detection Strategy Based on Extreme Learning Machine" Energies 13, no. 18: 4907. https://doi.org/10.3390/en13184907
APA StyleZhang, K., Hu, Z., Zhan, Y., Wang, X., & Guo, K. (2020). A Smart Grid AMI Intrusion Detection Strategy Based on Extreme Learning Machine. Energies, 13(18), 4907. https://doi.org/10.3390/en13184907






