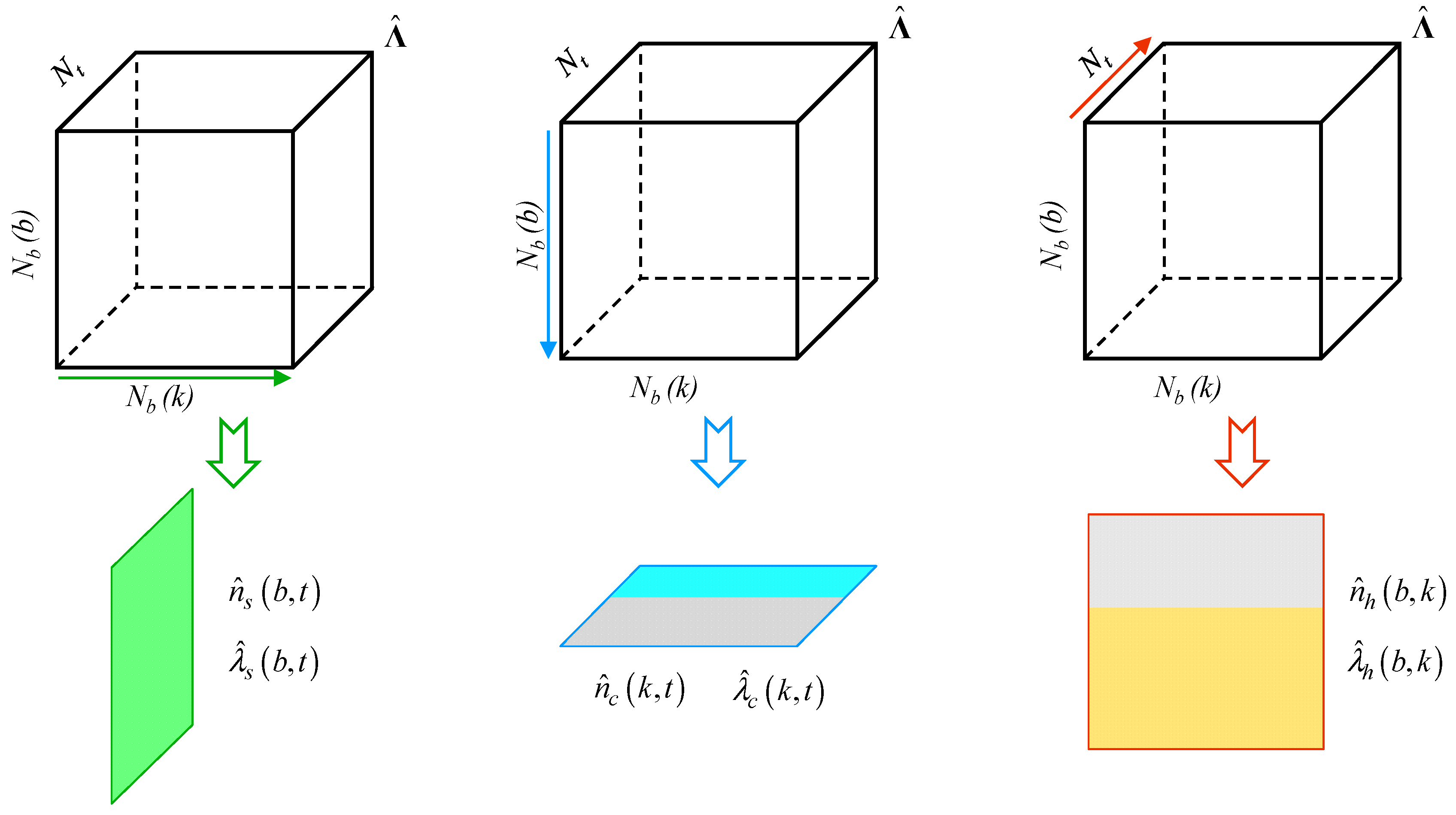
The method is implemented in a MSExcel
®-MatLab
® environment, exploiting Matpower [
46] for network analysis. The operating condition of the test system is determined according to a nodal shifting of electricity market results, in order to obtain power production levels for each generator according to technology and zone, and to obtain load level at each node, finally determining nodal power injections [
47]. In particular, HVDC links are represented by coupled active power injection-withdrawal at extreme nodes, whereas phase shift transformers (PSTs) are modelled by equivalent power injections at extreme nodes, depending on shift angle [
48].
The whole procedure, running on a 64-bit workstation with 3.50 GHz processor and 16 GB RAM, and exploiting virtual parallel calculus, takes roughly 50 h from yearly market input data to outputs of N and N−1 network analysis. To carry out the preliminary security analysis, more than 1.5 × 1012 cases are analyzed (13,123 × 13,123 × 8760). In the following, results refer to line loading, neglecting the representation of transformer loading levels for sake of readability; therefore, 681 × 109 cases (8817 × 8817 × 8760) are handled.
3.1. Yearly Operation—N Conditions
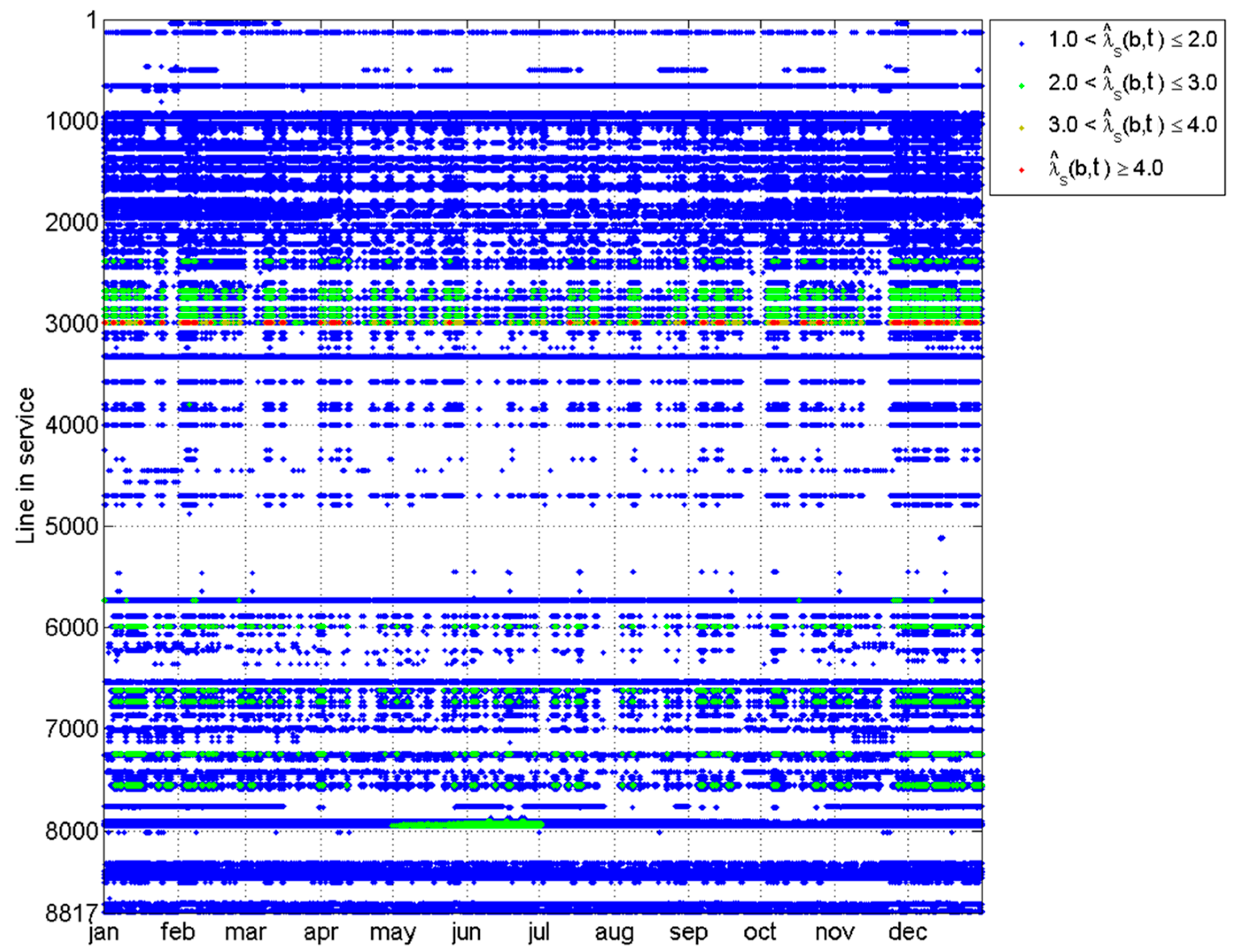
The graphical representation of the
matrix
of yearly loading conditions in the absence of contingencies, obtained by means of PDTFs, and with 77.2 × 10
6 cases (8817 lines × 8760 h), is reported in
Figure 3, where overload cases are represented by markers whose different colors represent overload intensity levels. It can be deduced that the network is interested by slight N overloads affecting a limited set of lines, although no overload is detected in 68 h only.
A synthesis of performance indices is reported in
Table 2. It can be seen that the total number of overloads corresponds to the 0.25% of the total combinations line-hour, affecting only 1.5% of lines. A particular focus should be given to extreme conditions, registered at hours 849–852 for maximum
and for lines 2992–2993, pertaining to Voltage Range C, for maximum
. Maximum
is observed at hour 5773 for 23 lines.
Values of the indices by voltage range are reported in
Table 3, where the number of branches in overload for less than 15% of the year
and the number of branches with average overload higher than 1.2 p.u.
are reported as well. It can be observed that overloaded lines in Range A are 2.2% of the total number, but they show sporadic overloads, since only 5 of them are in overload for more than 15% of the year. Lines in Range A have low overloads as well; considering a 1.2 p.u. overload as acceptable in planning standards [
49,
50], only 4 lines are troubling. On the other hand, the 9 focused lines in Range C are subject to overloads for more than 40% of hours on average, and with a mean loading value higher than 2. Lines in Range B show an intermediate behavior in each aspect.
For global network analysis, given that the sum of the ratings of all lines
is equal to 26.2 GW, trends of indices are reported in
Figure 4. It can be noted that
ranges between 3.1% and 9.6% (maximum at hour 849), with an average of 5.4%, resulting in a weakly charged network. This conforms to the assumptions of the method, based on DC power flow equations. On the other hand,
reaches a maximum of 0.097% at hour 848, although the mean value is 0.0190%, the median value is 0.0133% and the 90-percentile is 0.0491%, highlighting good performances.
3.2. Yearly Operation–N−1 Conditions
The N−1 analysis is therefore carried out by means of the LODF matrix, and the loading matrix is obtained. It is worthwhile to mention that 1583 cases of N−1 islanding are detected, i.e., 18% of total outages, and they are efficiently dealt with through the developed procedure.
According to the definition of indices in
Section 2.3, for the sake of representation, the values of
and
are depicted in
Figure 5 and
Figure 6, respectively, representing the values assumed by the indices in 77.2 × 10
6 cases. It can be derived that at least one N−1 overload in each hour is registered for 9 lines (rows full of markers in
Figure 5 and
Figure 6).
The summary of indices is reported in
Table 4. It can be noted that N−1 overloads are seen in 0.8% of branch-hour combinations (the total number of markers reported in
Figure 5 and
Figure 6), and affect 3.8% of branches. Moreover, the cases with overload for the maximum number of outages—i.e., when
reaches the maximum value of 8817 (red markers in
Figure 5)—are detected in 5.9% of total overload cases, affecting 12 lines, mostly in Voltage Range B. The maximum level of
is registered at hour 851, and the maximum level of
is observed for lines 2992–2993. Regarding overload intensity,
is registered for 7.3% of total overloads, affecting 31 lines, whereas the maximum levels of
have analogous features of maximum
.
Regarding time distribution, from
Figure 6 it stems that, for lines with identifier 2500–3000 and 6500–7000, in Ranges B and C, higher overloads are registered in December, January and February, whereas the critical period for lines with identifier 7500–7800, in Range B, is between May and June.
In
Table 5, the analysis of the 340 lines in N−1 overload by voltage range is reported. Further to indices analogous to the ones proposed in the N condition (see
Table 3), the average number of N−1 events causing and overload
is estimated, whereas
represents the number of lines of the
th voltage range with average
lower than 10% of total N−1 events.
It can be seen that the increase of overloaded lines is most evident in Range A, where more than 6% of lines are affected. However, it is confirmed that higher voltage levels experience less frequent and less intense overloads, seldom reaching remarkable peaks, as compared to Range C.
For N−1 global network indices, no remarkable difference is seen between
and
. Moreover,
has an average of 0.106%, and a maximum of 0.338% at hour 849, its median is 0.0849%, and its 90-percentile is 0.2165%. These values can be acceptable in N−1 planning, considering the probability of events [
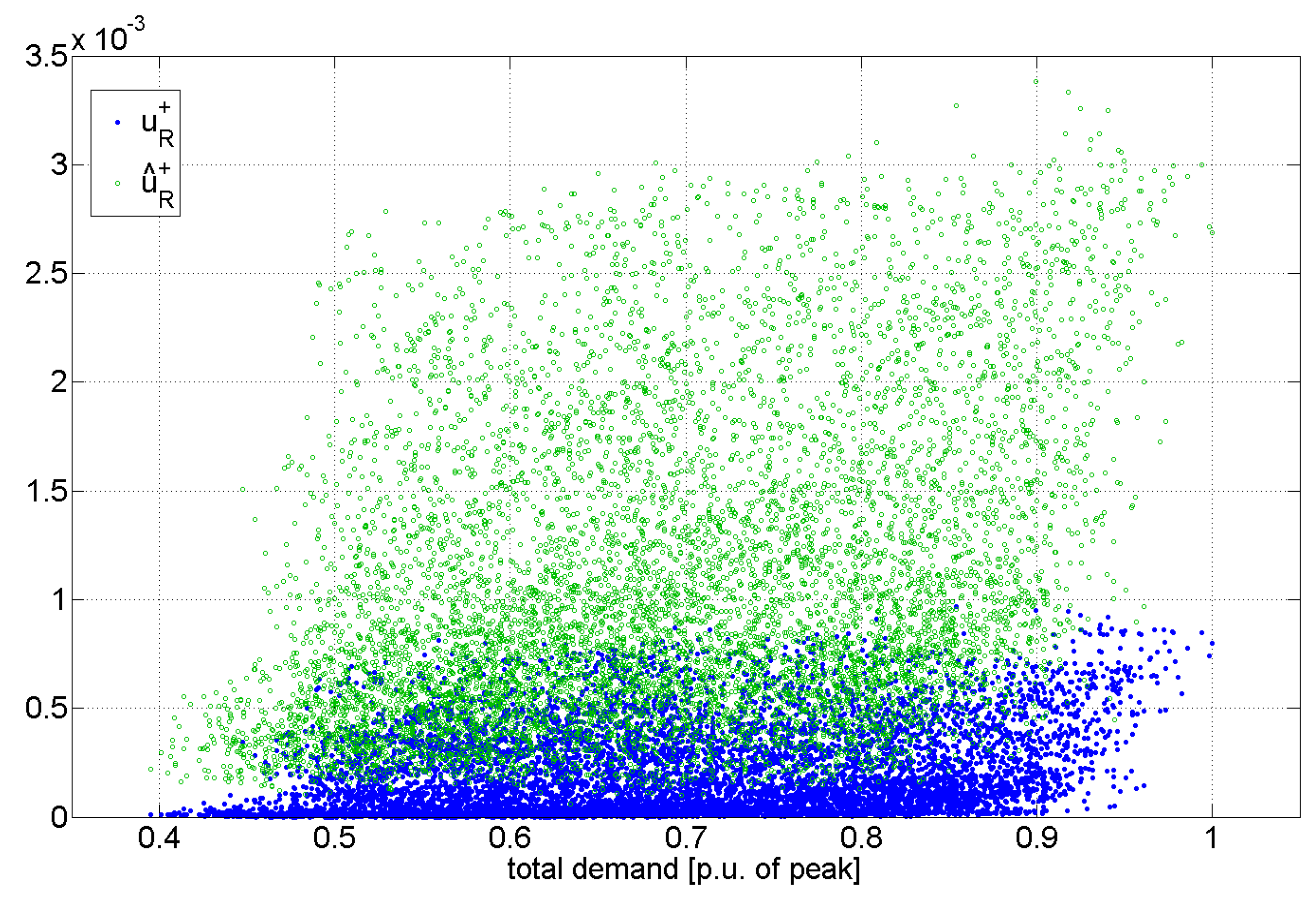
51]. Distributions of
and
with respect to total network demand (between 107.7 MW at hour 8107 and 272.4 MW at hour 3846), are shown in
Figure 7. As expected, it can be seen that N−1 events make overloads increase, although severe conditions are not linked to maximum demand (values higher than the 90-percentile are also seen for half of the peak load). This can be ascribed to the load distribution among zones.
In
Table 6, the analysis of indices by outage-hour,
and
, is synthesized. Overloads are seen in the majority of outage cases. The maximum number of N−1 overloads
is 84, observed at hour 849 for the outage of line 1036, in Voltage Range A, whereas the maximum
of 2.43 is seen for the outage of line 2924 at hour 2842, and values of
are reached in 2.9% of total overloads.
Hourly analysis by means of indices
and
is carried out on 77.7 × 10
6 cases (8817 lines × 8817 lines), and reported in
Table 7. It can be deduced that N−1 overloads are observed in 1.5% of total cases. The 132 lines in overload in the N condition experience N−1 overload for more than 8600 outages. Moreover, N−1 overload is present in 191 lines for less than 10 outages, in 11 lines for a range of 10 to 100 events and in 6 lines for 100 to 600 outages. As regards the values of indices, 31 lines in service have
for almost all outages, whereas other 68 lines are interested by
in less than 20 N−1 events. Only in 13 cases, each affecting a single line in service, is
is observed. Values of
are present in 3% of overloads, affecting 4 branches in any N−1 event, and another 16 branches in less than 5 outages, but only in 7 cases is a
observed.
In order to individuate the most troubling conditions, for each couple line in service–line in outage (i.e.,
), the hour with the maximum
, defined as critical overload, is found. The occurrences of critical overloads in each hour
are reported in
Figure 8, where the bullet color represents the number of lines affected by critical overloads in that hour
. Critical overloads are detected in 144 h (total number of markers in
Figure 8), mostly in winter. The highest number is 124.4 × 10
3 for hour 848 (10.7% of the total), whereas the maximum number of 48 lines with critical overload is registered in hour 849. This last hour is the most critical condition for different aspects, deserving a detailed analysis in the next subsection.
3.3. Analysis of Specific Loading Condition
The line loading levels in the N condition at hour 849 show that 74 lines are in overload in the N condition, and 22 of them, in Ranges B and C, have . The global network performance is described by = 9.63% and = 0.095%.
As regards N−1 analysis, involving 77.7 × 10
6 cases, synthetic indices are reported in
Table 8. Overloads are observed in 0.8% of combinations, affecting 193 lines. Peak overloads, with
, are detected only in 6 lines due to outages close to lines already overloaded in the N condition. In 28.6% of the overloads, the amount of N−1 overload is higher than the overload in the N condition, affecting in particular lines 8432 and 8433, in Voltage Range B. Moreover, global N−1 performances are described through the index
= 0.338%.
In
Table 9, average N−1 overloads
are divided into classes. More than half of overloaded lines have
, considered acceptable in N−1 network planning as described in the above, whereas 23 lines, mostly in overload in the N condition, show values higher than 2.
The number of lines in overload due to the outage of line
,
, is detailed in
Table 10. In 91.7% of outages, the number of overloaded lines is the same as in the N condition. The maximum of 84 overloads is observed for the outage of lines 1035 and 1036, in Voltage Range A, arising as the most critical lines for N−1 analysis in this hour. Moreover, 9 lines are in overload for any outage, whereas for 44 lines, only 1 outage induces an overload.
The performed investigation allows an early detection of critical lines, which could represent the target of a specific security analysis during operational planning, along with risk measures depending on device failure rates and further technical details.