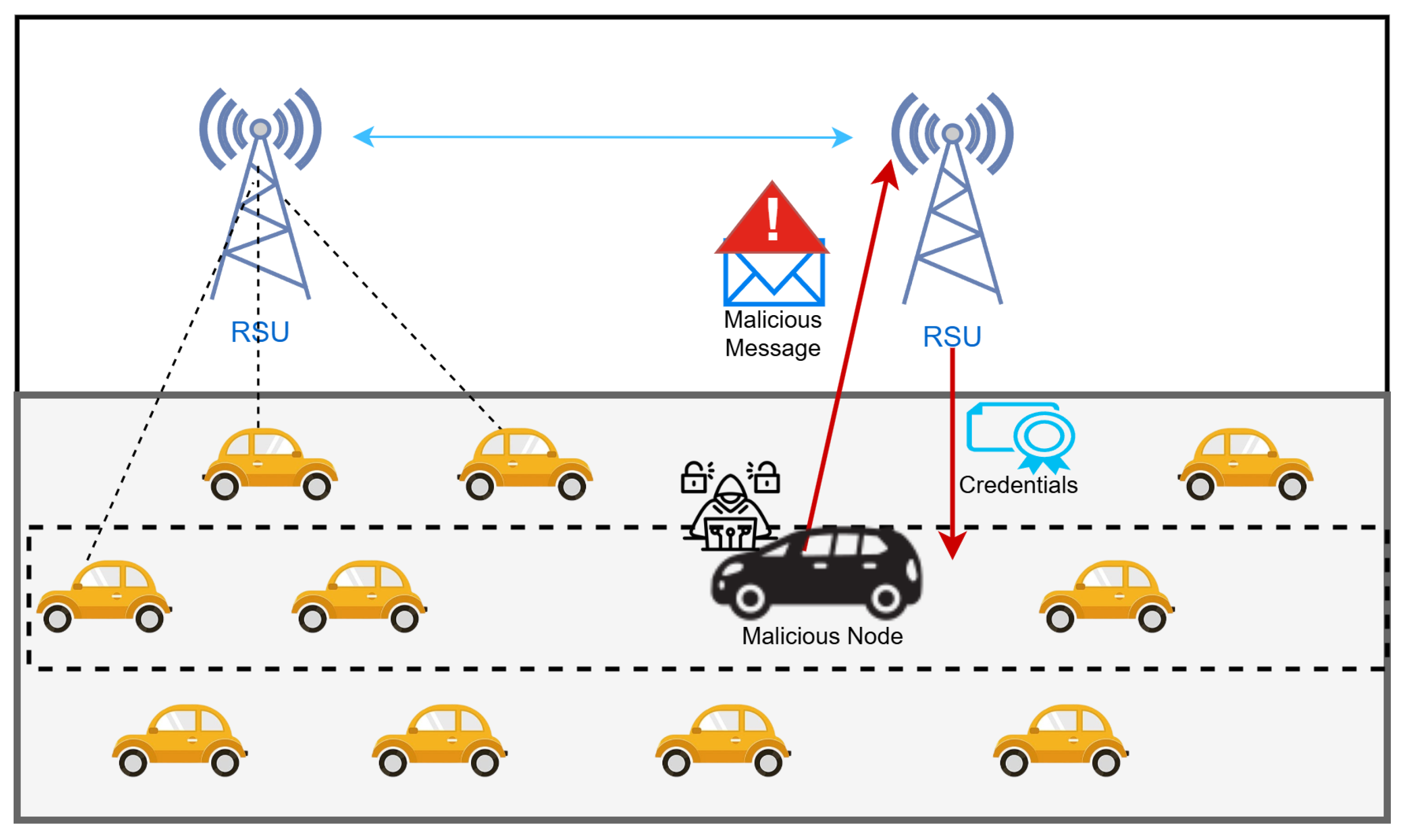
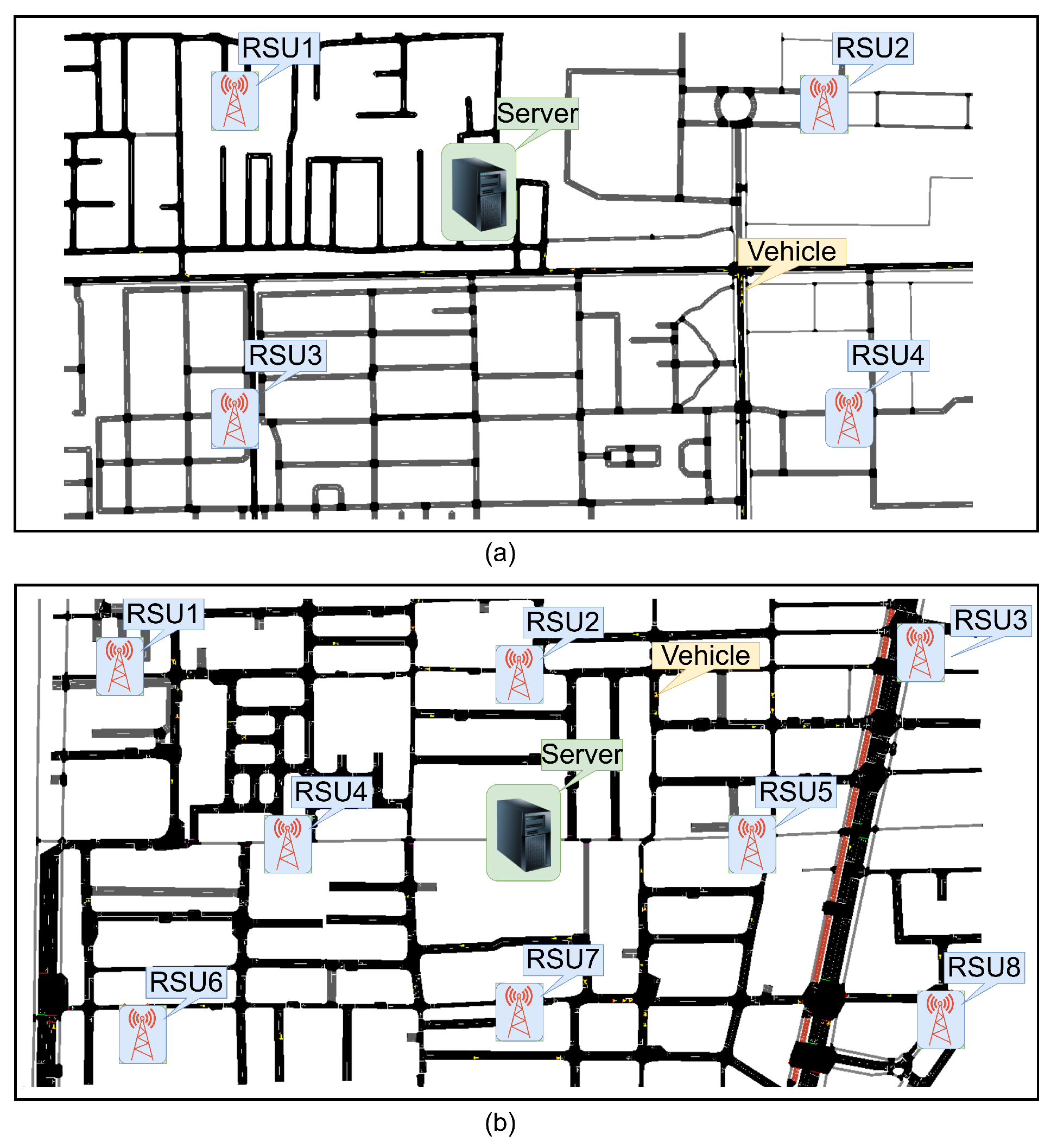
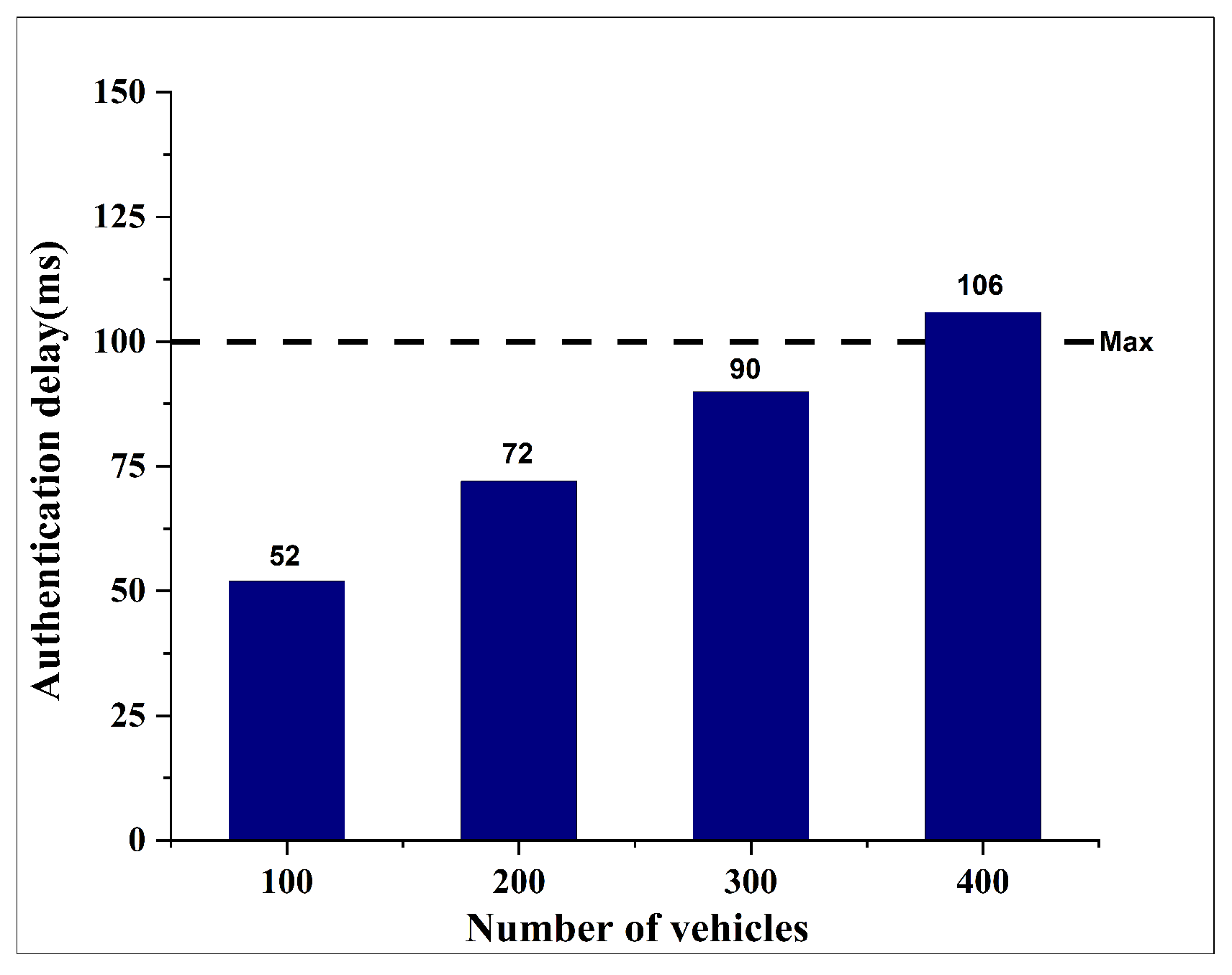This section discuss the authentication method and authentication stages proposed in this research and the entities that influenced these stages. These stages include the initial authentication stage, the stage where authentication messages are stored in blockchain, and the handover stage.
5.1. Overview of the System
We utilized the blockchain to record the authentication messages generated by Kerberos authentication to reduce the handover delay while also maintaining the security. The proposed system integrates Kerberos authentication within a blockchain framework by recording authentication messages generated by the Kerberos server onto the blockchain. By leveraging the decentralized nature of blockchain technology, the system aims to reduce authentication delays, particularly during the handover process in vehicular networks.
The system is structured into three main stages: the initial authentication stage, where authentication messages are generated; the blockchain uploading stage, where these messages are recorded onto the blockchain; and the re-authentication stage, conducted during handovers. After the initial authentication is completed, the vehicle no longer requires a direct connection to the Kerberos server, as subsequent re-authentication processes only involve verifying authentication messages stored on the blockchain. This study focuses on optimizing the Kerberos authentication process by combining the Authentication Server (AS) and the Ticket Granting Server (TGS) to achieve lower authentication times compared to existing approaches.
The system utilized the Advanced Encryption Standard (AES) with a 128-bit key and is applied to secure the Kerberos authentication process. For the blockchain framework, the system employs the Ethereum blockchain. This proposed system figure is depicted in
Figure 3.
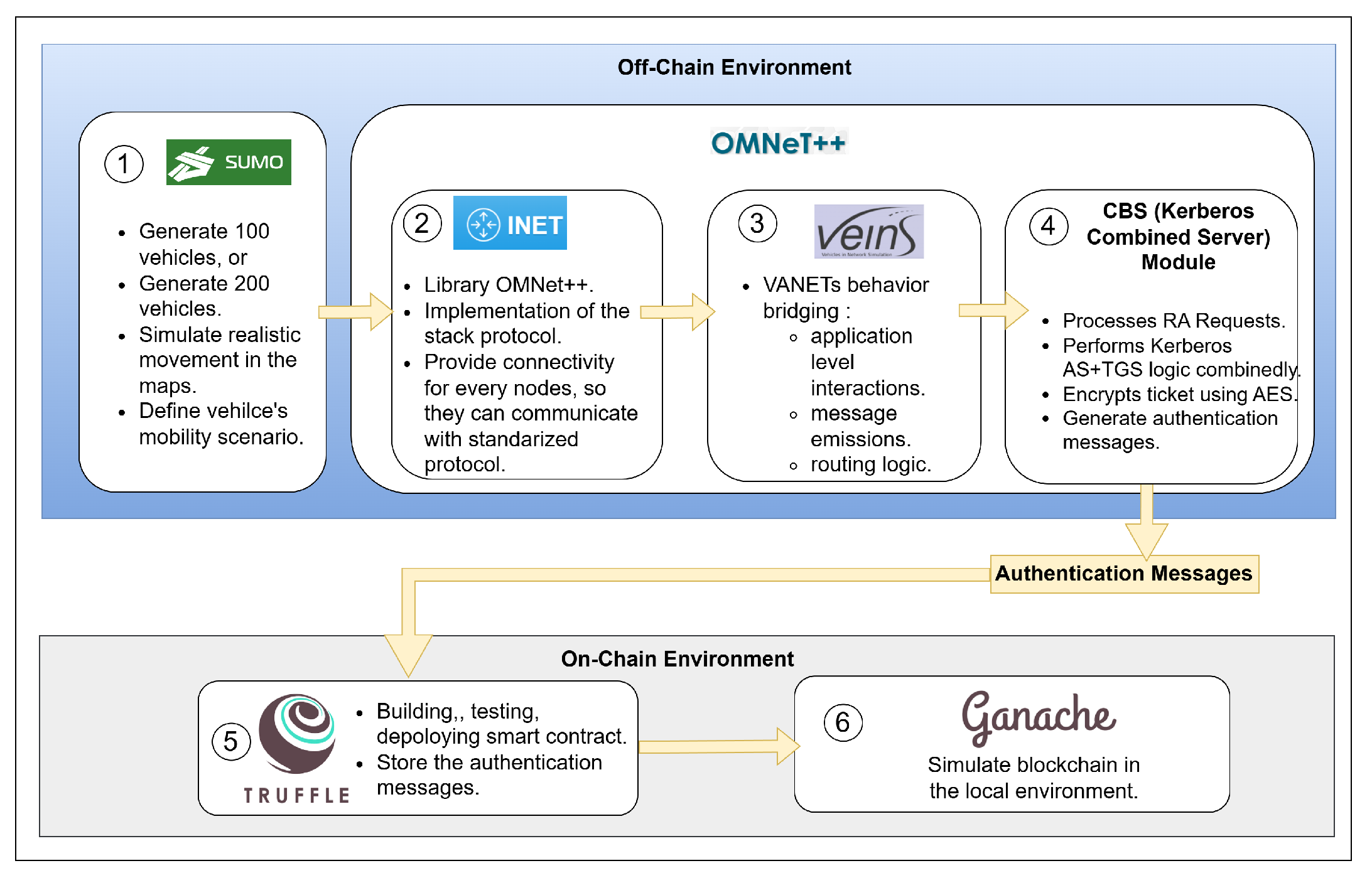
In this study, we reuse the suburban and urban mobility scenarios introduced in our previous work [
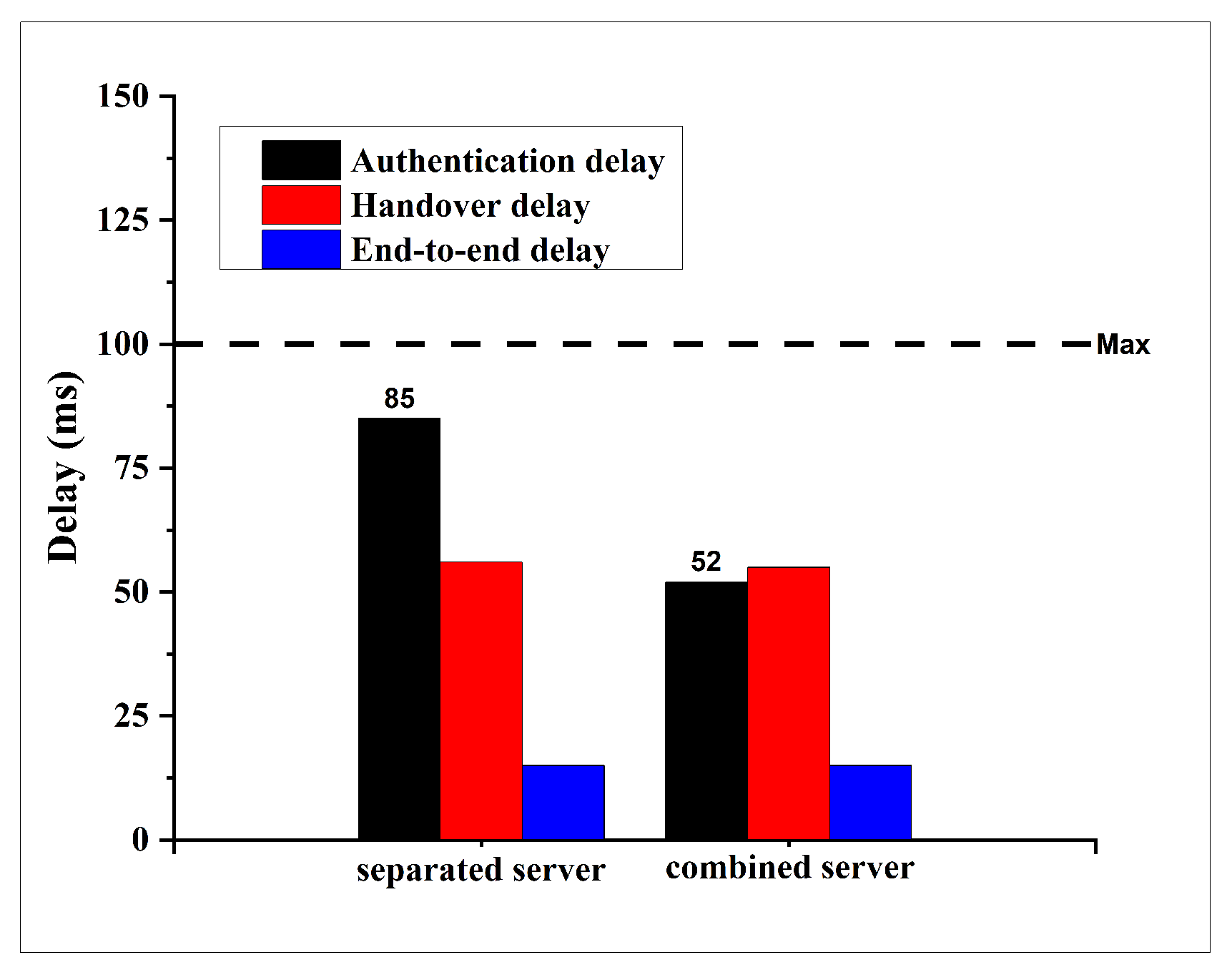
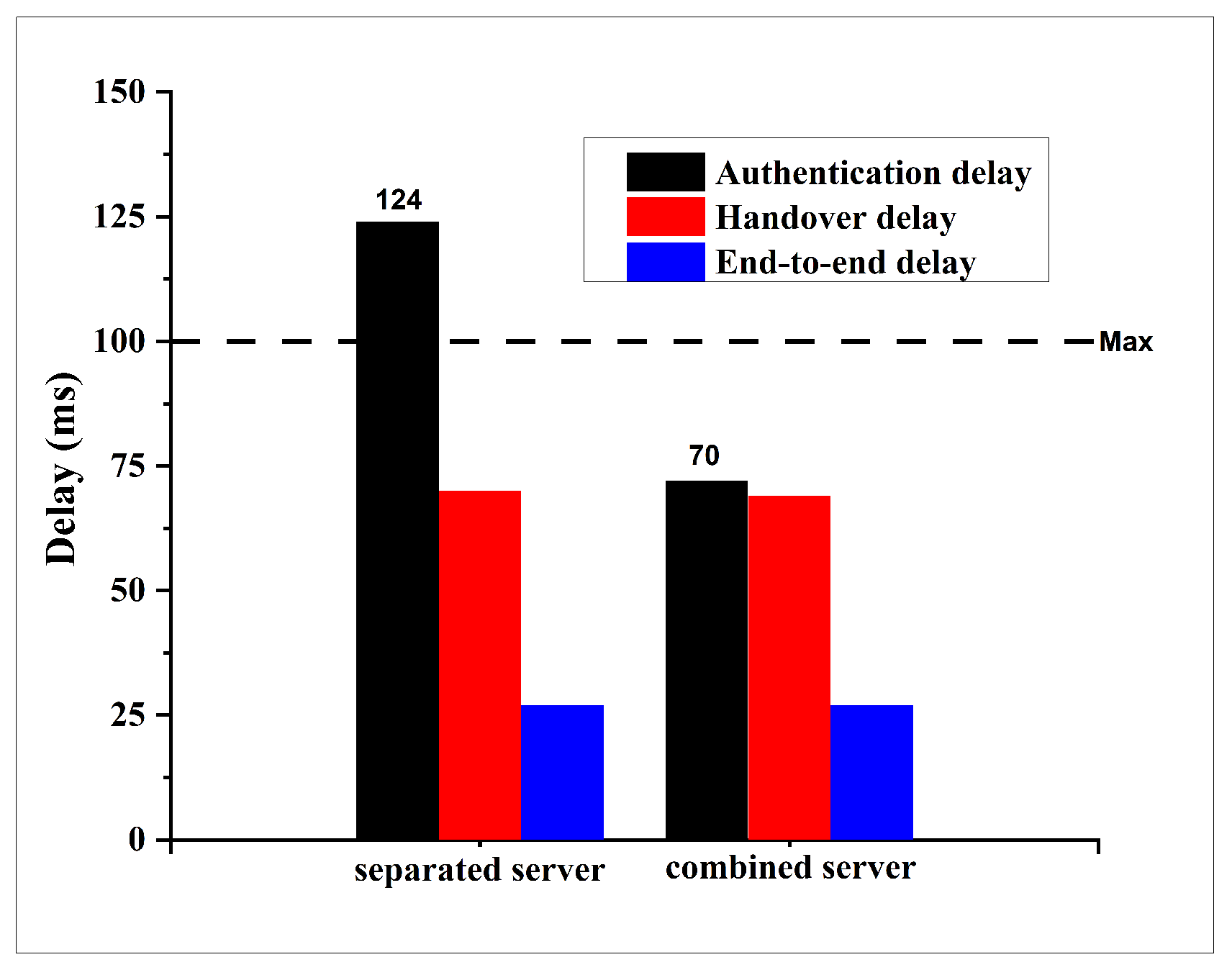
8], generated using SUMO–OMNeT++ with the Duarouter mobility model. However, we extend the evaluation in two key directions. First, we analyze the proposed CBS architecture under the same scenarios, but across multiple delay metrics: authentication delay, ticket validation delay, and blockchain transaction delay. Second, to assess the scalability of CBS under higher vehicle densities, we introduce additional simulation configurations with 300 and 400 vehicle nodes in the suburban scenario. These new simulation runs provide insights into CBS performance in more congested environments and allow for a more thorough comparison against the baseline architecture.
Figure 3.
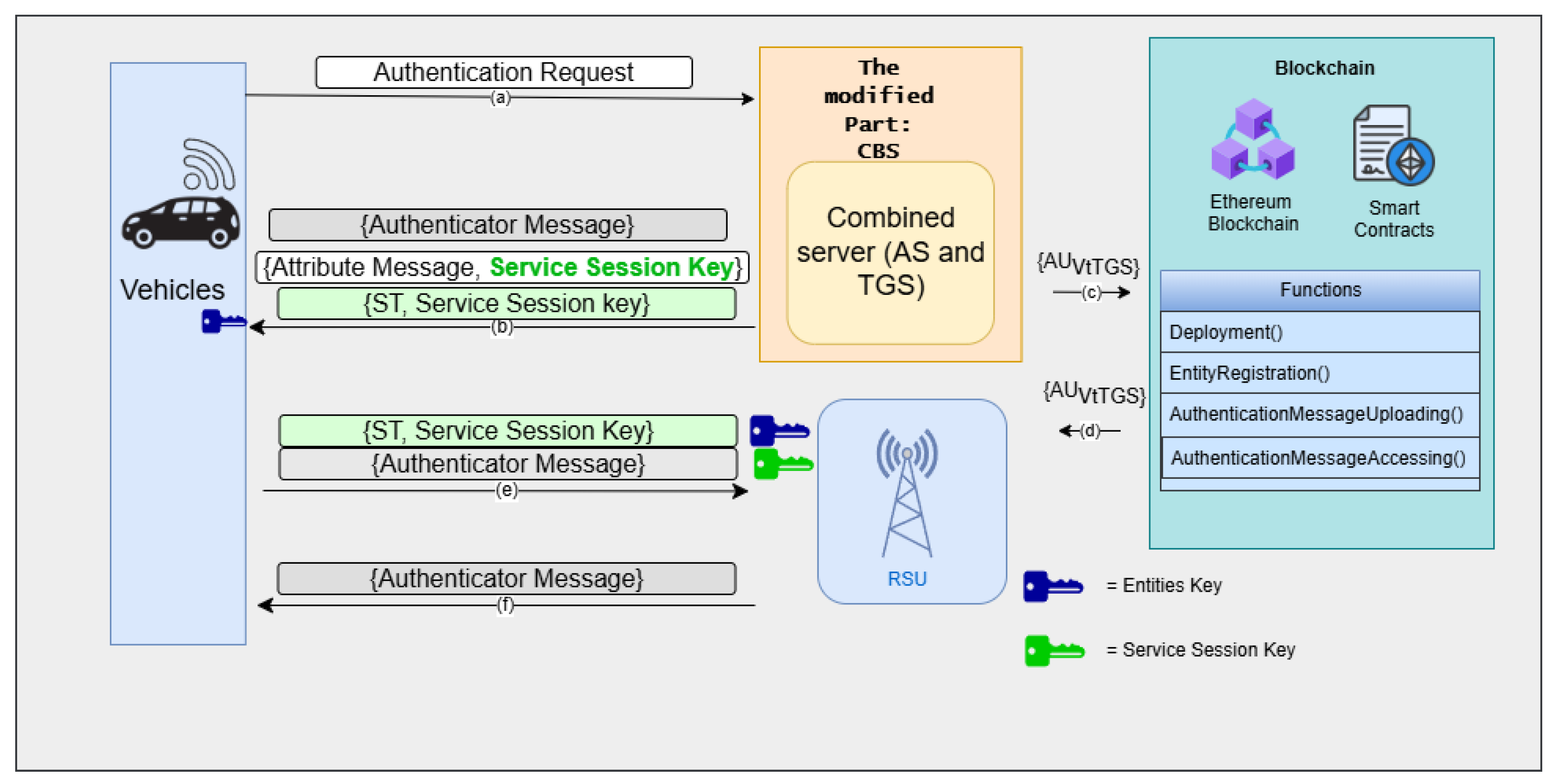
Proposed system architecture integrating AS and TGS into the combined blockchain server (CBS). (a) Vehicle sends authentication request to KBC; (b) AS verifies the vehicle and generates Service Ticket and Service Session Key to the vehicle; (c) TGS store the authentication message to the blockchain ledger; (d) Blockchain ledger send the authentication message to RSU; (e) Vehicle presents ST to the RSU for service access; (f) RSU validates the ticket and grants service.
Figure 3.
Proposed system architecture integrating AS and TGS into the combined blockchain server (CBS). (a) Vehicle sends authentication request to KBC; (b) AS verifies the vehicle and generates Service Ticket and Service Session Key to the vehicle; (c) TGS store the authentication message to the blockchain ledger; (d) Blockchain ledger send the authentication message to RSU; (e) Vehicle presents ST to the RSU for service access; (f) RSU validates the ticket and grants service.
5.1.1. Entities and Functions
Our system comprises three fundamental entities: the Combined Server (CBS) that has function as the Trusted Authentication Server, the Road Side Unit (RSU), and the vehicle. The CBS functions as a server responsible for registering all entities, authenticating vehicles, and disseminating authentication messages to the blockchain. RSUs serve as intermediaries between the vehicles and the CBS. They facilitate the integration of vehicles into the network, assist in the transfer of data among network entities, and disseminate information pertinent to traffic conditions. The vehicles assume the role of network nodes and data sources. Each vehicle is equipped with an On-board unit (OBU), enabling it to communicate road-related data to nearby RSUs and neighboring vehicles within its communication range.
5.1.2. Overview of the Phases
The proposed system architecture is structured into three primary phases: system initialization and entity registration, initial authentication, and the handover procedure.
The registration stage serves the purpose of documenting all entities, which include the RSUs, CBS, and vehicles.
The initial authentication process is initiated when a vehicle enters the network and submits an authentication request to the CBS. Upon successful authentication, it issues a service ticket to the vehicle, granting it access to connect to the network via RSU1.
The CBS generates authentication messages, which are subsequently uploaded to the blockchain. These messages are utilized by vehicles during the handover process to facilitate seamless re-authentication.
When a vehicle moves beyond the coverage area of RSU1, it initiates a handover procedure by sending its previously issued authentication message to RSU2. RSU2 then interacts with the blockchain to retrieve and verify the corresponding credential stored during the initial authentication phase. If the provided credential matches the one recorded on the blockchain, the vehicle is successfully re-authenticated. This blockchain-assisted handover mechanism eliminates the need to repeat the initial authentication process, thereby significantly minimizing the overall authentication delay.
5.2. The Combination of the Server
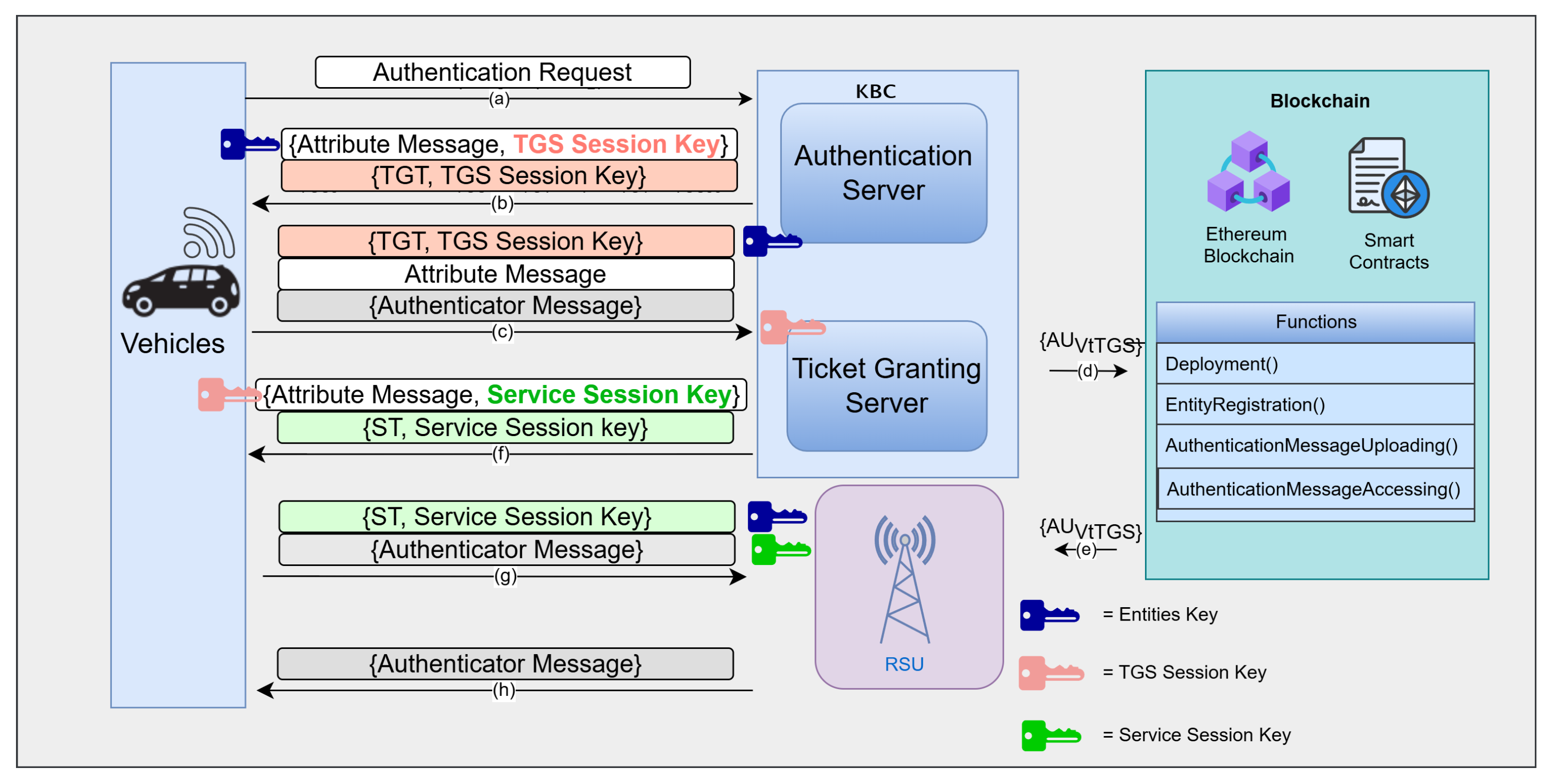
In this research, we focuss on the combination of the Authentication Server (AS) and (TGS) from the conventional Kerberos–Blockchain system (KBS) to becomes the combined server (CBS) to reach higher performance without any additional infrastructure.
In the original modular architecture, the AS was responsible for handling vehicle registration, secret key issuance, and generating Authentication Messages, whereas the TGS handled ticket validation and Secure Ticket (ST) generation for service access. In contrast, the proposed CBS architecture consolidates these responsibilities into a single logical entity, allowing for more efficient and centralized handling of authentication processes.
A critical advantage of this unified design is the removal of inter-module communication. In the previous KBC model, packets such as authentication messages and session keys, needed to be transmitted between separate servers, introducing delays and processing overhead, especially under high vehicle density. By contrast, the CBS model eliminates these transmissions by directly processing all authentication steps within one server. For example, the socketDataArrived function in KBC now handles both ticket validation and secure ticket generation, which minimizes the need for inter-module signaling and improves overall efficiency.
Furthermore, the integration into a single server significantly improves end-to-end delay performance. In the KBC model, communication latency between the modules often led to processing bottlenecks, especially during handovers or in scenarios with rapid vehicle mobility. The CBS design, through centralized processing in functions such as handleRegistrationOfVehiclePacket and handleVehicleToTGSPacket, reduces these delays by enabling direct and immediate handling of all authentication-related packets.
The unified architecture also leads to a more efficient cryptographic key management scheme. In the previous model, AS and TGS each maintained their own sets of secret and session keys, increasing complexity and coordination requirements. In the CBS system, key generation and management—such as the generateSecretKey routine—are performed within a single scope. This centralization allows for simplified encryption workflows and secure ticket issuance, reducing the risk of synchronization issues between multiple servers.
Lastly, the CBS model offers considerable simplification of the overall codebase. The KBC architecture required distinct initialization, runtime operations, and teardown procedures, which increased software maintenance effort and redundancy. The CBS implementation reduces this complexity by utilizing unified methods such as initialize and a single event-handling function, socketDataArrived, to perform the complete authentication lifecycle. This makes the codebase more maintainable and extensible for future enhancements or deployment scenarios.
In contrast to prior Kerberos–Blockchain frameworks where the Authentication Server (AS) and Ticket Granting Server (TGS) were implemented as separate modules, our proposed architecture integrates these roles into a single Combined Server (CBS). This integration is a purposeful optimization to streamline the authentication process [
6,
8].
This integration is shown in the
Figure 4. In the baseline Kerberos architecture, authentication messages must pass through two servers (AS and TGS) before reaching the RSU, resulting in four protocol steps. In contrast, the CBS architecture eliminates one server layer, reducing the flow to two major hops, CBS and RSU, thus minimizing communication latency.
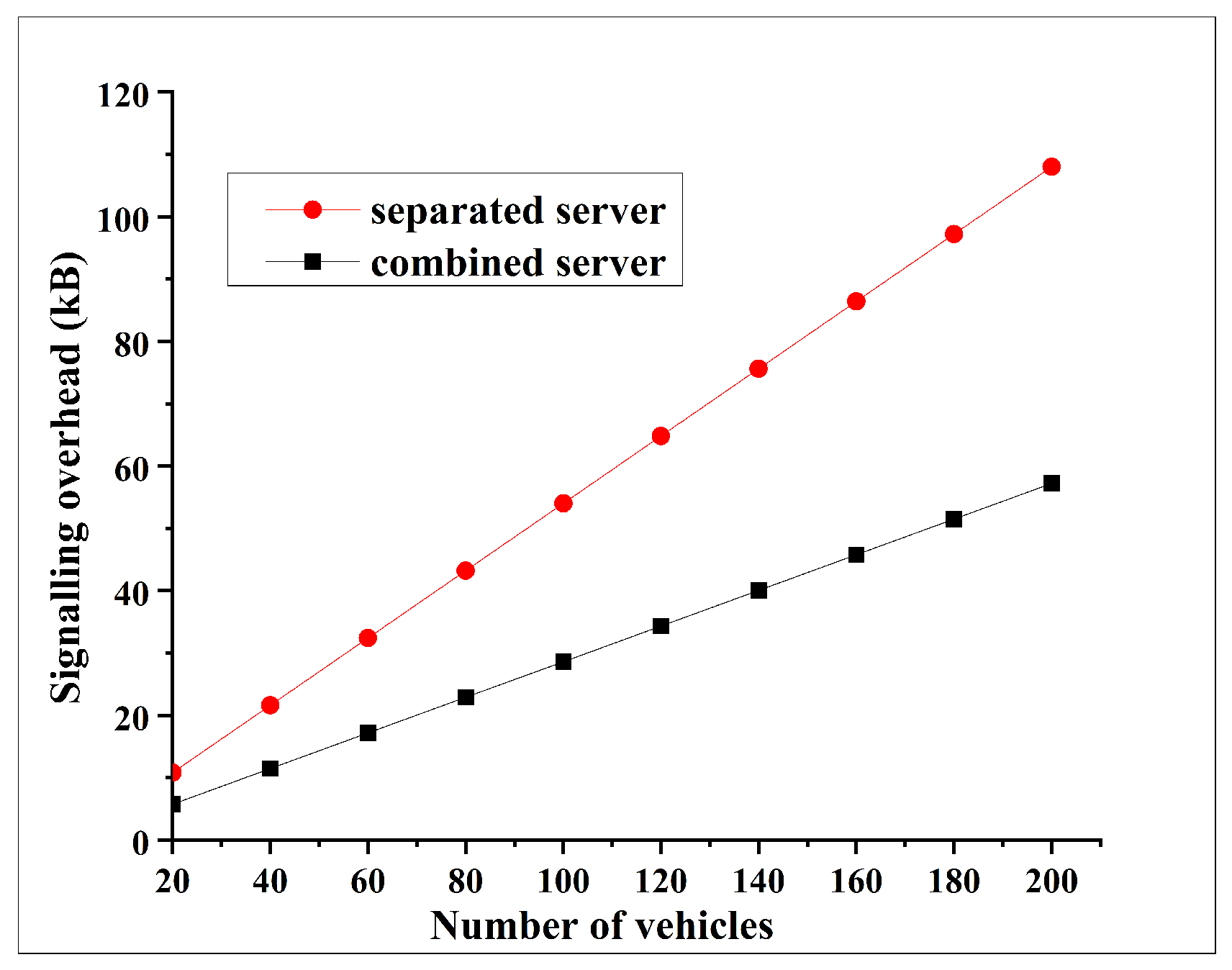
First, merging AS and TGS eliminates the inter-server communication steps inherent in traditional Kerberos. In the separated design, each vehicle’s authentication requires two sequential exchanges (AS followed by TGS), incurring an extra network round-trip and processing delay. The unified CBS handles the entire ticket issuance in one place, reducing the number of message exchanges and thus lowering the overall authentication latency.
Second, the unified server architecture improves resource utilization and scalability through load consolidation. Instead of two servers that might individually run at partial load or become unevenly bottlenecked, the CBS serves a single aggregated request queue, ensuring full utilization of server capacity. This means that the system can handle higher vehicle volumes without deploying additional servers—a limitation of the earlier two-server approach (KBC), which required extra infrastructure in high-density scenarios.
Third, our evaluation shows that this architectural redesign yields measurable performance gains without any new cryptographic algorithms. As reported in the revised manuscript, the integrated CBS consistently maintains authentication delays below the critical 100 ms VANET requirement, even in heavy traffic scenarios. By shortening the signal path and reducing duplicate work (e.g., cryptographic operations and database lookups performed separately by AS and TGS), the CBS can serve substantially more vehicle authentications per second.
Fourth, the CBS design continues to leverage blockchain for storing authenticators and does not alter the Kerberos trust model, thereby maintaining the same security guarantees as the baseline scheme (e.g., no secret keys exposed, tamper-proof audit trail).
In summary, the CBS integration streamlines the signaling path and reduces system complexity while maintaining the rigorous security of the Kerberos–Blockchain protocol. This innovative redesign provides a clear improvement over the state-of-the-art [
6,
8].
The Combined Server (CBS) proposed in this work introduces clear protocol-level innovations beyond the physical consolidation of the Authentication Server (AS) and Ticket Granting Server (TGS). In traditional Kerberos, authentication involves two distinct rounds: one with the AS to obtain a Ticket-Granting Ticket (TGT), followed by another with the TGS to request a Service Ticket (ST). In contrast, the CBS unifies these steps into a single exchange, wherein the combined entity performs both identity verification and service ticket issuance. This redesign reduces protocol rounds, minimizes communication overhead, and streamlines the client-side authentication flow.
In addition, the CBS enables inline ticket derivation, eliminating the need for intermediate credentials and redundant cryptographic operations. It also integrates a blockchain-based session validation mechanism, allowing for seamless handovers between Roadside Units (RSUs) without requiring full re-authentication. This protocol-level optimization enhances performance under VANET mobility constraints while preserving Kerberos security semantics.
In summary, the CBS constitutes a purposeful architectural and protocol-level redesign, not merely a colocation of servers, yielding measurable improvements in latency, signaling complexity, and mobility support.
The proposed CBS framework addresses the key limitations of the traditional KBS architecture by offering reduced delay, centralized key management, elimination of inter-module communication, and improved code maintainability, thereby providing a more robust and scalable solution for secure VANET authentication. The key difference in both scenario are shown in
Table 3.
5.2.1. Comparison of Vehicle Registration of AS in KBC vs. CBS
In the original Kerberos-based VANET design, vehicle registration and initial authentication are handled by the Authentication Server (AS) via a dedicated function, commonly referred to as
handleVehicleRA. This routine processes a vehicle’s registration request by verifying the vehicle’s identity (e.g., via a pre-shared secret or digital certificate) and then issuing the necessary Kerberos credentials, namely a Ticket-Granting Ticket (TGT) and a session key [
8]. Internally, the AS generates a random session key for vehicle–TGS communication. It then constructs the TGT containing this session key and vehicle identity, encrypting it with the TGS’s secret key. Simultaneously, the session key and accompanying metadata are encrypted with the vehicle’s secret key. The response sent to the vehicle therefore includes two encrypted segments: one encrypted for the vehicle, and the other (the TGT) encrypted for the TGS. This follows the standard Kerberos key exchange flow.
The encryption used in
handleVehicleRA is based on AES-128, and both the TGT and the session key are handled through symmetric encryption. Each vehicle possesses a long-term secret key shared only with the AS, which is used to decrypt the session key and associated data. The TGT includes the session key and is readable only by the TGS, ensuring the integrity of the authentication process. This
handleVehicleRA function is explained in Algorithm 1.
| Algorithm 1: handleVehicleRA—AS Registration Process |
| Input: Authentication request |
| Output: Encrypted session key and Ticket Granting Ticket |
| 1 if not VerifyID() then; |
| 2 return error response; |
| 3 end if |
| 4 GetVehicleKey; |
| 5 GenerateAES128Key(); |
| 6 AES_Envrypt; |
| 7 AES_Envrypt; |
| 8 return; |
In the proposed unified architecture, the CBS consolidates both AS and TGS functions into a single module. The core function responsible for this operation is handleRegistration OfVehiclePacket. Upon receiving a registration packet, the CBS verifies the vehicle’s identity and proceeds to generate a fresh session key. It then creates a ticket embedding the session key and relevant metadata (e.g., vehicle ID, timestamp, validity duration). This ticket is encrypted with the CBS’s own master key. The session key and related metadata are simultaneously encrypted using the vehicle’s long-term secret key. This handleRegistrationOfVehiclePacket function is explained in Algorithm 2.
Due to the merged roles, CBS can issue a final service ticket or authenticator directly to the vehicle, reducing the number of steps required in the authentication exchange. Additionally, the CBS logs a record of the authentication result onto a blockchain ledger, enabling subsequent verification by RSUs or other entities.
| Algorithm 2: handleRegistrationOfVehiclePacket—CBS Registration Process |
| Input: Registration packet |
| Output: Encrypted session key and Ticket Granting Ticket |
| 1 if not VerifyCreds() then; |
| 2 return error response; |
| 3 end if |
| 4 GetVehicleKey; |
| 5 GenerateAES128Key(); |
| 6 AES_Encrypt; |
| 7 AES_Encrypt; |
| 8 return; |
For encryption and key handling, both functions apply AES-128 encryption to ensure secure session establishment, but they differ in mechanism and performance. In both implementations, a secure session key is generated by the server and distributed securely, encrypted for the vehicle using its own key, and stored in a ticket encrypted for the relevant server (TGS or CBS). The CBS implementation also benefits from blockchain integration, enabling verifiable and tamper-proof authentication logging. Overall, the unified CBS function achieves reduced latency, simpler protocol flow, and stronger encryption with AES, while preserving the secure key handling principles of Kerberos.
5.2.2. Comparison of Authentication Ticket
In the Authentication Server (AS) implementation, the function aesEncrypt is utilized to secure the initial authentication ticket, referred to as the Ticket Granting Ticket (), generated for the vehicle. After verifying the vehicle’s identity, the AS generates a fresh 128-bit Ticket Granting Server session key (), which is shared between the vehicle and the Ticket Granting Server (TGS). This session key, along with the vehicle’s identifier (), timestamp (), and requested ticket lifetime (), is encrypted using AES-128 with the TGS’s long-term secret key () to produce the . Additionally, the AS encrypts the same session key and its associated metadata using the Vehicle’s secret key () to securely deliver it to the On-Board Unit (OBU). This dual encryption ensures confidentiality and isolation of trust between the communicating entities. This aesEncrypt function is explained in Algorithm 3.
In contrast, the Combined Server (CBS) integrates the roles of both the AS and TGS. When a vehicle submits a request containing a and the authenticator message (), the handleVehicleToTGSPacket function first decrypts the using to retrieve the embedded session key and validate the ticket’s timestamp. The authenticator is then decrypted using to verify the freshness and authenticity of the request. Upon successful validation, the CBS generates a new 128-bit service session key () to enable secure communication with the target service. The generateTicket function then encrypts this session key along with the required metadata using the service’s secret key () to produce the Service Ticket (), which is returned to the vehicle along with the encrypted attribute ticket (), both protected under AES-128 encryption with . This handleVehicleToTGSPacket function is explained in Algorithm 4.
Therefore, the CBS architecture enhances the authentication process by eliminating inter-server communication and combining validation and issuance operations within a single module. This design significantly reduces latency and signaling overhead, rendering it particularly well suited for dynamic and resource-constrained VANET environments.
| Algorithm 3: Service Ticket Issuance-KBC |
| Input: Received , , requested |
| Output: Encrypted session key and Service Ticket |
| 1 AES_Decrypt; |
| 2 ; |
| 3 AES_Decrypt; |
| 4 if ( is valid and timestamp is fresh) then; |
| 5 GenerateAES128Key(); |
| 6 AES_Encrypt; |
| 7 AES_Encrypt; |
| 8 return ; |
| 9 end if |
| Algorithm 4: Service Ticket Issuance—CBS |
| Input: Received , , requested service |
| Output: Encrypted session key and Service Ticket |
| 1 AES_Decrypt; |
| 2 ; |
| 3 AES_Decrypt; |
| 4 if ( is valid and is fresh) then; |
| 5 GenerateAES128Key(); |
| 6 AES_Encrypt; |
| 7 AES_Encrypt; |
| 8 return ; |
| 9 else; |
| 10 return error response; |
| 11 end if |
5.2.3. Authentication Logic and Encryption Handling in KBC and TGS Functions
The handleVehicleToTGSPacket function in the CBS and the handlePacketFrom Vehicle function in the Ticket Granting Server (TGS) module perform distinct but complementary roles within the proposed authentication protocol. In the CBS stage, the handleVehicleTo TGSPacket function is responsible for verifying the vehicle’s identity using the Vehicle’s secret key (). Upon successful validation, the CBS generates a fresh Ticket Granting Server session key () for secure communication between the vehicle and the TGS. This session key is encapsulated in two outputs: (i) the Ticket Granting Ticket (), encrypted with the TGS’s long-term secret key (), and (ii) the authentication ticket from KBC to vehicle (), encrypted with the vehicle’s secret key (). The is designed to be opaque to the vehicle and validated solely by the TGS, while the enables the vehicle to retrieve the session key . The handleVehicleToTGSPacket function is explained in Algorithm 5.
In contrast, the
handlePacketFromVehicle function explained in Algorithm 5 in the TGS processes authentication requests from vehicles by validating the previously issued
and the Authenticator from vehicle to TGS (
). The
is decrypted using
to extract
, which is then used to decrypt and validate
. This dual-stage verification ensures both the integrity of the ticket and the freshness of the authentication request, thereby mitigating replay attacks. Upon successful validation, the TGS generates a Service session key (
) to be shared between the vehicle and the target service. This key is encapsulated in two forms: the Service Ticket (
), encrypted with the service’s secret key (
), and the attribute ticket from TGS to vehicle (
), encrypted with
for decryption by the vehicle. Both the CBS and TGS modules thereby implement a layered encryption strategy to safeguard key confidentiality and mutual authentication using timestamped authenticators and rigorous key validation procedures tailored for secure operation in Vehicular Ad Hoc Networks (VANETs).
| Algorithm 5: handlePacketFromVehicle—Service Ticket Issuance and TGT Verification (TGS) |
| Input: Request |
| Output: Service Ticket and Access Ticket |
| 1 AES_Decrypt; |
| 2 Extract from ; |
| 3 if (Expired or malformed format) then; |
| 4 return error (invalid or expired ); |
| 5 end if |
| 6 AES_Decrypt; |
| 7 Extract from ; |
| 8 if ( or AU replayed or IP mismatch) then; |
| 9 return error (invalid ); |
| 10 end if |
| 11 Mark as used; |
| 12 GenerateAES128Key(); |
| 13 ; |
| 14 AES_Encrypt; |
| 15 ; |
| 16 AES_Encrypt; |
| 17 return; |
5.3. The System Phases
The phases of the proposed system are divided into five stages, including a system initialization and registration phase, vehicles and CBS communication stage, CBS and RSU interaction, an authentication message upon uploading to the blockchain, and a handover phase, which are shown in
Figure 3.
5.3.1. System Initialization and Registration Phase
During the offline registration phase, vehicles submit their credentials, including the vehicle ID, password, origin, destination, service type, and access rights (such as read, write, and modify permissions). Similarly, Roadside Units (RSUs) are registered with details like their physical location, MAC address, IP address, and RSU ID. Before the verification phase begins, the CBS generates and securely distributes secret keys to each entity involved.
5.3.2. Vehicles and CBS Communication Stage
This phase includes communications that are relayed from the vehicle to CBS, and, conversely, reflecting the processes outlined in steps (a) and (b) illustrated in
Figure 3. In the initial stage, the vehicle conveys a Request Authentication (RA) to the CBS, which comprises the
, the particular service designation that the vehicle aims to access (in this scenario, the service designation is related to RSU service),
, and the lifetime (
). The
limits the temporal span, thereby bolstering system security through a bounded time constraint. This information will be transmitted to the CBS.
The messages dispatched by the vehicles to the CBS are delineated in Equation (
3). The corresponding response messages are represented in Equations (
4), (
5), and (
7). The parenthesis symbol signifies a collection of unencrypted messages, whereas the bracket symbol represents the encrypted messages.
The initial function of CBS involves maintaining a database of authenticated users along with their associated secret keys. When a verification request is received, the CBS checks whether the identifier and corresponding message exist within this registry. If validation is successful, the secret key is retrieved. The CBS then generates an attribute token , which includes the service identifier , the requested lifetime (), and a specified validity period. This information is encrypted using a randomly generated symmetric session key , which is used by the user to decrypt subsequent communications from the CBS and RSU during the current session. Additionally, the attribute message is encrypted with the vehicle’s secret key . These encrypted messages are then transmitted from the CBS to the vehicle.
Following this, the CBS creates the authentication message
, composed of the vehicle ID
and a timestamp
. This message is encrypted using the session key
, employing AES encryption with a 128-bit key. Once the
is generated, it is uploaded to the blockchain network in step (c) for secure storage. Afterward, the same message is forwarded to the RSU in step (d). Further explanation of the blockchain storage mechanism for
is provided in
Section 5.3.5.
5.3.3. Vehicles and RSU Interaction
Once the vehicle receives the attribute message and the service ticket, the authentication process advances to steps (e) and (f), as illustrated in
Figure 3. Using the session key
, the vehicle decrypts the received
to retrieve the service session key
. With this key, the vehicle constructs a new authentication message
, which contains its identifier
and a timestamp
. This message is then encrypted using
. Subsequently, the vehicle sends both the service ticket and the encrypted authentication message to the intended service provider, which, in this context, is the RSU. The structure and content of the messages transmitted by the vehicle to the RSU are outlined below:
The RSU follows a process analogous to that previously executed by the TGS. It begins by decrypting the service ticket (
) using its private key
, through which it obtains the session key
for further communication. This session key is then used to decrypt the vehicle’s authentication message
. After successful decryption and validation, the RSU generates a new authentication response message, denoted as
, which contains its own identifier
and a timestamp
, as formulated in Equation (
9).
The generated is transmitted back to the vehicle and decrypted using the session key . Upon receipt, the vehicle performs two critical checks: it verifies that the service name included in the response matches the expected service, and it validates the freshness of the message by examining the timestamp , thereby preventing replay attacks. Additionally, the vehicle updates its local cache mechanism. Upon the successful completion of mutual authentication between the vehicle and the RSU, the service ticket is securely stored in the vehicle’s cache for subsequent use in future sessions.
5.3.4. CBS and RSU Interaction
The CBS and the RSU exhibit a non-direct engagement during the preliminary authentication stage as well as throughout the handover procedure. In the preliminary authentication stage, as depicted in
Figure 3, it is evident that the CBS and the RSU do not engage in direct communication; nevertheless, their operational roles are interconnected. The CBS has first task to oversee the initial authentication of vehicles that seek services from the RSU within the confines of a secure network. The second responsibility of the CBS is to encompass the verification of vehicle identities, the issuance of Ticket Granting Tickets (TGTs), and the encryption of user credentials to ensure security. Subsequently, it is also responsible for issuing service tickets, which are utilized by vehicles to gain access to RSU services. The service server then validates these tickets to authenticate the client and facilitate authorized access to services.
During the handover phase, the CBS generates the , which serves as the essential credential for enabling seamless authentication continuity. This credential is securely uploaded to the blockchain, where access control and upload operations are governed by a predefined smart contract. The underlying smart contract, implemented in Solidity, defines parameters such as the entity’s name, unique identifier, and associated network designation. Only the CBS, designated as the trusted authority, is authorized to upload the credential to the blockchain.
When a vehicle initiates a handover to a new RSU, the RSU retrieves the corresponding by submitting its own entity name to the blockchain interface. Access is granted through a consensus-based validation mechanism that ensures the authenticity and integrity of the request. Upon successful verification, the transaction is committed to the blockchain as a new block, thereby allowing for the RSU to access the stored and complete the handover process securely.
5.3.5. Authentication Message Uploading in the Blockchain Phase
Once the is generated by the CBS, it is subsequently stored on the blockchain. This credential serves as proof of the vehicle’s authenticity during future authentication attempts. The upload and retrieval of the are facilitated through smart contract functions written in Solidity. Specifically, the off-chain simulation environment (OMNeT++) produces the , which must be transmitted through the smart contract interface before it can be visualized or interacted with on the Ganache platform. To store the authentication credential, the smart contract function AuthenticationMessageUploading() is invoked. This function accepts the as an input argument, and a transaction request is initiated by the CBS to upload this data to the blockchain. Upon successful validation and mining of the transaction, the message is stored as part of a blockchain block. The function also emits events, which allow for observers to extract and verify the stored data via the Ganache user interface.
In this scenario, the CBS is modeled as the sender, while the RSU acts as the intended recipient. For identification purposes, the entity ID for the CBS is assigned as “1,” and the RSU is designated as “2.” Both entities operate within a shared blockchain network labeled “TsushimaVanet.” To retrieve the , the RSU sends a transaction request by calling the AuthenticationMessageAccessing() function within the smart contract. Once the transaction is confirmed, the RSU successfully obtains the from the blockchain, enabling it to complete the authentication or handover operation securely.
5.3.6. Handover Phase
When a vehicle exits an RSU’s coverage, a handover process begins with the source RSU verifying the target RSU. The vehicle sends a request, prompting the target RSU to upload an authentication message to the blockchain. After validation via smart contracts, the blockchain returns an authentication unit. The RSU confirms the vehicle’s data, completes the handover, and the vehicle updates and shares the new state.