BcDKM: Blockchain-Based Dynamic Key Management Scheme for Crowd Sensing in Vehicular Sensor Networks
Abstract
1. Introduction
1.1. Related Work
1.2. Our Contribution
- We propose the CGKAwAM scheme, which extends CGKA scheme with a lightweight administrator-driven group member management mechanism. Unlike the standard CGKA scheme, CGKAwAM supports multiple administrators within a single VC. Each administrator is capable of independently processing user-initiated proposals (such as Join, Remove, and Update) in a single communication round.
- Based on CGKAwAM and blockchain technology, we design the BcDKM scheme, which provides several key advantages. First, it enables distributed VC discovery and management (see Section 2.2). RSUs act as blockchain nodes and use smart contracts to publish VC information, facilitating efficient matching and information sharing between vehicles and VCs. Additionally, multiple cloud administrators collaboratively manage each VC in a decentralized manner, reducing the risk of a single point of failure. Second, the scheme achieves round optimality and large-scale VC scalability (see Section 2.2). VC initialization and member join/leave operations can be completed asynchronously in a single communication round, without requiring all members to be online. Furthermore, the computational complexity grows logarithmically with the number of members, making the scheme suitable for large-scale deployment.
- We provide a rigorous formal security analysis for both the CGKAwAM and BcDKM schemes. Specifically, under a non-adaptive security model, we construct a game-based proof using the game-hopping technique, reducing the security of CGKAwAM to the CPA security of the underlying public key encryption scheme and the security of the pseudorandom generator. Our analysis shows that the proposed scheme satisfies multiple critical security properties, including key independence, forward secrecy, and post-compromise security. In addition, we analyze the security of the BcDKM scheme and show that it not only satisfies basic security requirements but also provides protection for vehicle privacy.
- We conduct a comprehensive evaluation of the proposed scheme through both theoretical analysis and simulation experiments. We also compare our scheme with several existing representative solutions. The results demonstrate that BcDKM achieves a balance between security and efficiency, confirming its practical feasibility.
2. Background
2.1. System Model
- Certificate Authority (CA): The CA is a trusted third party responsible for generating public system parameters and issuing digital certificates to vehicles and RSUs.
- Vehicles: Each vehicle is equipped with an onboard unit (OBU) that provides computing and communication capabilities and stores certificates and related secrets. A VC is formed by a group of vehicles and supports dynamic membership, allowing vehicles to join or leave the VC as needed. The vehicle that initiates the VC formation may act as the cloud administrator or delegate this responsibility to another vehicle, while the remaining participants serve as cloud members.
- Roadside Unit (RSU): The RSU is located along the roadside; it communicates with vehicles within its coverage area, authenticates their identities, and publishes the VC information. Additionally, RSUs are assumed to function as part of the blockchain infrastructure, acting as blockchain nodes.
- Blockchain (BC): The BC provides reliable data storage and supports automated execution via smart contracts. In our system, it is used to record VC-related information and assist VC administrators in managing the cloud.
- Cloud Users (CUs): A CU refers to any authorized entity that accesses and utilizes the services provided by a VC. CUs can submit tasks to their selected VC for execution.
2.2. Threat Model and Design Goals
- Vehicle privacy: This property ensures that no one, except the CA, can learn the true identity of a cloud member (a vehicle) within a VC.
- Known-key security: This property ensures that even if an attacker obtains a session key of a cloud member within a particular VC, the security of other independent session keys remains uncompromised.
- Forward secrecy: This property ensures that if a vehicle is compromised by an attacker at a certain point in time, all session keys generated prior to the compromise remain confidential.
- Post-compromise security: This property ensures that if a vehicle is compromised at a certain point in time and the compromised vehicle subsequently performs a session key update that is not influenced by the attacker, then the updated session key remains confidential.
- Distributed VC discovery: This property enables a vehicle to efficiently discover existing VCs and their metadata via nearby RSUs, avoiding reliance on centralized platforms and mitigating single points of failure.
- Distributed management: This property ensures that each VC is managed by multiple cloud administrators. If one administrator becomes unavailable, others can still handle requests from vehicles inside or outside the VC (e.g., join and leave). This design mitigates insider threats and avoids single points of failure.
- Round optimality: This property ensures that group session key establishment and updates within a VC can be completed in a single round of communication, achieving optimal round complexity.
- Large-scale VC scalability: This property ensures efficient operation in VCs with many cloud members, as key management complexity grows logarithmically with group size.
2.3. Building Blocks
- : This algorithm accepts and outputs the system parameters ().
- : This algorithm accepts and generates a private–public key pair .
- : This algorithm accepts a plaintext (m) and a public key () and outputs a ciphertext ().
- : This algorithm accepts a ciphertext () and a secret key () and outputs a plaintext (m).
- : This algorithm takes as input and outputs a private–public key pair .
- : This algorithm takes and a message (m) as input and outputs a signature (σ).
- : This algorithm takes , a message (m), and a signature (σ) as input and outputs 1 if the signature is valid or 0 otherwise.
- : This algorithm takes as input and outputs a secret key (k).
- : This algorithm takes a secret key (k) and a message (m) as input and outputs a ciphertext (c).
- : This algorithm takes k and a ciphertext (c) as input and outputs a message (m).
- The algorithm expressed as , where , is used to retrieve the sequence of nodes along the path from the I-th leaf node to the root of the given PBT . It is typically executed by the cloud administrator or a cloud member. Given a PBT () and position (I) selected by the cloud administrator or a cloud member, the algorithm returns a path () that consists of direct references to the original PBT nodes so that any modification of a node in the path immediately affects the original PBT nodes.
- The algorithm expressed as , where , is used to generate a modified copy of a given PBT (), with all sensitive information (i.e., private key and secret value) outside the specified path () masked. It is typically executed by the cloud administrator. Given a PBT () and a path () within the PBT selected by the cloud administrator, the algorithm returns a duplicate PBT (), in which the private keys and secret values of all nodes not included in the path () are set to null.
- The algorithm expressed as is used to obtain the set of common ancestor nodes shared by and in the tree expressed as , ranging from their lowest common ancestor () up to the root node ().
3. Building Blocks
3.1. CGKA with Administrator Mechanism (CGKAwAM)
- SetUp: This algorithm is executed by a trusted authority (e.g., certification authority) to generate system parameters. Upon input of a security parameter (), it outputs a common system parameter (). The trusted authority proceeds as follows:
- 1.
- Select a public key encryption scheme (. Invoke to obtain (see Definition 1).
- 2.
- Choose a secure PRG (; see Definition A2).
- 3.
- Publish the common system parameter (, , )).
- KeyGen: This algorithm is executed by a user with identifier to generate their own key pair. Upon input of and , it outputs a public–private key pair (). Internally, it invokes to generate the key pair ().
- Create (, CM): This algorithm is executed by user , acting as the group administrator, to initiate a new group. Upon input of , an identifier set ( with ), and an identifier (), it outputs the administrator’s local state (, where is the newly assigned group identifier), and a set of control messages () is used to invite the remaining members in G to join the group. The state encapsulates the user’s status in the group, including the session key, the list of group administrators, the list of group members, public parameters, and so on. Furthermore, suppose that each user holds a key pair . initializes a group as follows:
- 1.
- Set the group identifier (, where is a timestamp).
- 2.
- Select s users from G to serve as administrators, forming the set expressed as . The remaining users form the set expressed as .
- 3.
- Assign each user () a unique random number (). This yields the set expressed as .
- 4.
- Invoke to construct a PBT , where and .
- 5.
- Compute the session key as , where is the serialized string of the tuple stored at the root node ; see Definition 5.
- 6.
- Initialize a mapping array () of length to associate each PBT leaf node with a user from G. Set for and for .
- 7.
- For each user with identifier in , generate a control message as follows:
- –
- If , do the following:
- (a)
- Invoke to obtain the ciphertext (), where denotes the position assigned to user in the PBT (i.e., the -th leaf node such that ).
- (b)
- Add the control message () to set .
- –
- Otherwise, do the following:
- (a)
- Invoke to obtain a path (, where , .
- (b)
- Invoke to obtain a PBT ().
- (c)
- Invoke , to obtain .
- (d)
- Add the control message () to set .
- 8.
- Set the state as , where indicates that is designated as the administrator and indicates that is mapped to the first leaf node of the PBT, i.e., .
- 9.
- Send each control message in set to the corresponding user.
- Proposal: This algorithm is executed by user to generate a proposal message () intended for the group administrator () within the group, with the purpose of requesting a group membership change (e.g., join or leave) or a session key update. Upon input of and a proposal type (), it outputs the proposal message (). The parameter specifies the purpose of the proposal: adding a member, removing a member, or updating the session key. The field represents the payload associated with the proposal. We present three example proposal messages used in our scheme as follows.
- –
- : A join request from an external user (), asking administrator to add it to group , where .
- –
- : A removal request by current group member , requesting to leave or be removed from the group, where .
- –
- : A key update request by current group member , asking to update the group session key, with , where is the public key of and is randomly selected by .
User sends the proposal message () to the administrator (). - Commit: This algorithm is executed by user , who serves as the administrator of the group. It is used to process a proposal message () submitted by another user. Upon input of , it outputs the updated state () and a set of control messages (), which are used by the other group members to update their local states. Suppose in a group () has a local state of = (, ). Suppose . then processes the as follows:
- –
- If , do the following:
- 1.
- Search the Map array for an index () such that . If no such index exists (i.e., all current leaf nodes are occupied), invoke the helper function () to extend the PBT, and search again for an empty index (). Once an empty index is found, set , , and add to the the set.
- 2.
- Select a random value () for user .
- 3.
- Generate the corresponding control messages for user as follows:
- (a)
- Invoke to update the path in the PBT ().
- (b)
- Invoke to obtain the updated path ().
- (c)
- Invoke to obtain .
- (d)
- Invoke , to obtain .
- (e)
- Add the message expressed as to set .
- 4.
- Generate the corresponding control messages for administrators () as follows:
- (a)
- Invoke to obtain the ciphertext ().
- (b)
- Add the message expressed as to set .
- 5.
- Generate the corresponding control messages for the other group members (i.e., ) as follows:
- (a)
- Invoke to obtain the path expressed as.
- (b)
- For each node on the path expressed as , do the following:
- i.
- If node has a non-empty sibling node () in the PBT (, i.e., and share the same direct parent node, where or ), then retrieve the tuple expressed as from node and invoke to obtain the node set expressed as , which represents the sequence of common ancestor nodes of and , up to the root node . The total number of nodes in this set is . Otherwise, continue the loop.
- ii.
- Invoke to obtain the ciphertext , where is a list of public keys corresponding to those stored in the node along the path expressed as .
- iii.
- For each non-administrator user () whose identifier is stored in the array (, where q satisfies ), set the control message as . Note that the control messages for these users are identical, except for the recipient identifier (). Add each message () to the control message set ().
- –
- If , do the following:
- 1.
- Search the array (Map) for an index () such that . Then, set , and remove from the set.
- 2.
- Select a random value ().
- 3.
- Invoke to update the path in the PBT ().
- 4.
- Generate the corresponding control messages for the other administrators (i.e., ) in the same way as Step 4 under the condition of in this algorithm.
- 5.
- Generate the corresponding control messages for the other group members (i.e., ) in the same way as Step 5 under the condition of in this algorithm.
- –
- If , do the following:
- 1.
- Search the array (Map) for an index () such that .
- 2.
- Obtain the tuple expressed as from the node leaf ().
- 3.
- Compute , where is the private key stored in the node expressed as .
- 4.
- Invoke to update the path in the PBT ().
- 5.
- Generate the corresponding control message for , and proceed as follows:
- (a)
- Invoke to obtain a path ().
- (b)
- Set the cipher to .
- (c)
- Add the control message () to set .
- 6.
- Generate the corresponding control messages for the other administrators (i.e., ) in the same way as Step 4 under the condition of in this algorithm.
- 7.
- Generate the corresponding control messages for the other group members (i.e., ) in the same way as Step 5 under the condition of in this algorithm.
- –
- Compute the updated session key as . Note that denotes the PRG computation with the concatenation of the session key () and the tuple stored in node .
- –
- Update the state ( = , , n, , , ).
- : This algorithm is executed by user , who is a member of the group. It is used to process a control message () sent by the group administrator within the group for the purpose of updating the user’s local session state. Upon input of , , , and , it outputs the updated state (). If user receives the control message () for the first time, then inputs and are set as ⌀. Suppose that receives the control message () from administrator within the group and is associated with a key pair . then processes as follows:
- –
- A format of indicates that is joining group for the first time, then proceeds as follows:
- 1.
- Invoke to obtain , where .
- 2.
- Compute the session key as = .
- 3.
- If , then set ; otherwise, set .
- 4.
- Set state = .
- –
- Otherwise, a format of indicates that is a cloud administrator within the group. Suppose possesses a local state of = . Then, proceeds as follows:
- 1.
- Invoke to obtain ().
- 2.
- Compute the session key as = .
- 3.
- Set state = ().
- –
- Otherwise, the control message () originates from the group, which has already joined. Suppose has a format of and user possesses a local state of = , , , . does the following:
- *
- If and , another member has either joined the group, updated the group session key, or exited. proceeds as follows:
- 1.
- If , then set , and add to the set.
- 2.
- If , then set , and remove from the set.
- 3.
- Invoke to obtain the node set expressed as , which represents the sequence of common ancestor nodes of and , up to the root node (). is the lowest common ancestor.
- 4.
- Obtain the tuple expressed as from the child node of , which is also an ancestor of .
- 5.
- Invoke , to obtain .
- 6.
- Replace the nodes in the set expressed as , which belong to the PBT , with the corresponding nodes in the set expressed as .
- 7.
- Replace the public keys in the tuples stored in the nodes along the path from the leaf node () to the root node () with the corresponding public keys in list .
- 8.
- Compute the updated session key as = .
- 9.
- Set state = .
- *
- Otherwise, the received control message () is the administrator’s response to the proposal message submitted by , where , with and being a random value chosen by . The message is processed as follows:
- 1.
- Invoke to update the corresponding path.
- 2.
- Compute the updated session key as = .
- 3.
- Set state = .
3.2. Design of Smart Contract
3.2.1. Vehicle Identity Smart Contract (VIDSC)
3.2.2. Vehicular Cloud Smart Contract (VCSC)
- Update: Invoked by cloud administrators to initialize VC-related variables;
- Upload: Invoked by vehicles or administrators to append new proposal messages;
- Return: Invoked by administrators to retrieve unprocessed proposal messages.
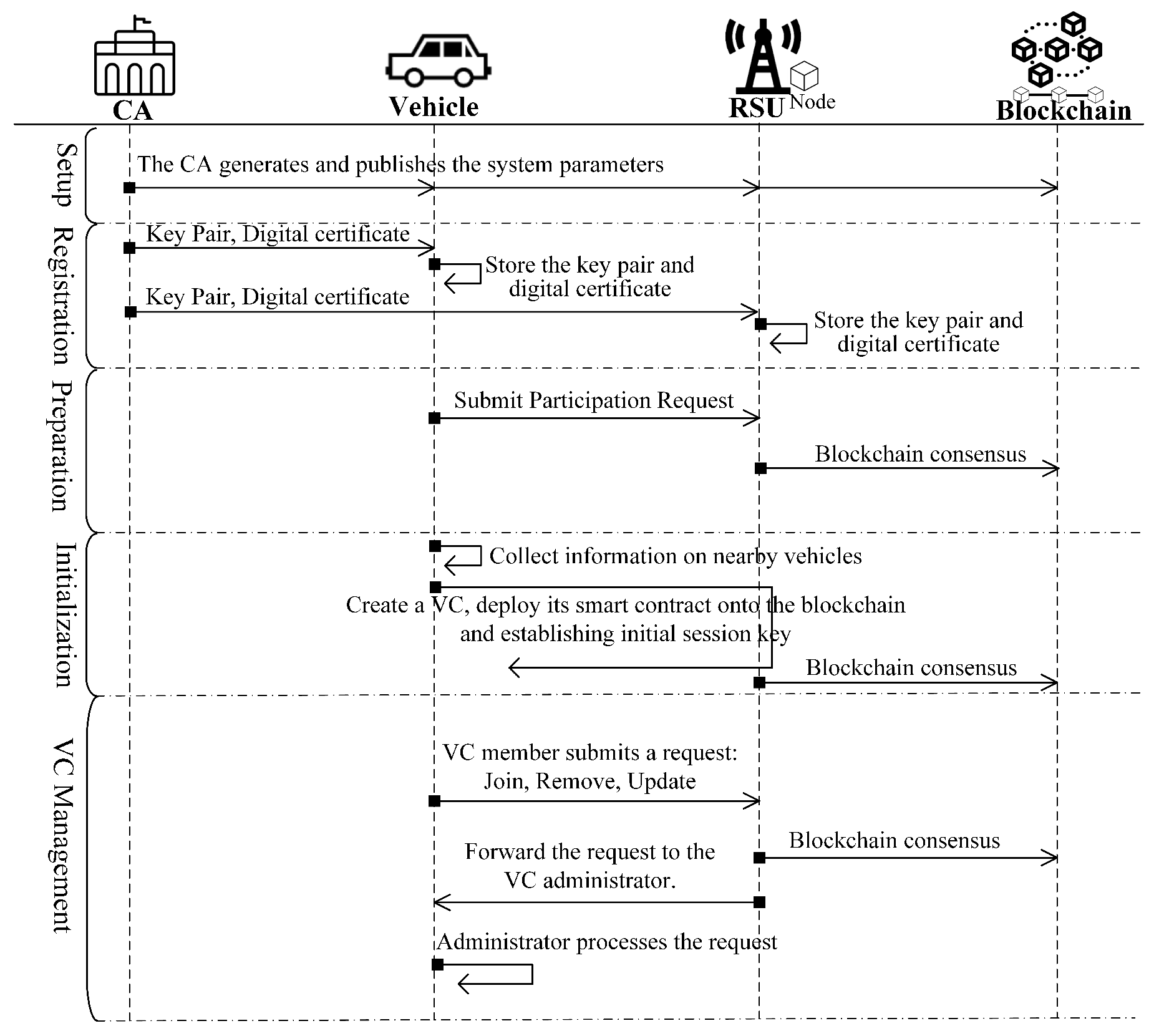
4. Blockchain-Based Dynamic Key Management (BcDKM) Scheme
4.1. High-Level Description
4.2. Setup
- 1.
- Invoke the SetUp algorithm of the CGKAwAM (see Definition 3) to obtain the common system parameters ().
- 2.
- Select a digital signature scheme (). Invoke to obtain the parameters, and invoke to generate a key pair (See Definition 2).
- 3.
- Select a symmetric encryption scheme (. Invoke ) to generate a secret key (k).
- 4.
- Initialize a blockchain system, denoted as , which supports the VCSC for the management of VC-related information and the VIDSC for the recording of information of vehicles willing to join a VC. Those smart contracts are defined in Section 3.2.
- 5.
- Publish the system parameter as = , , ,, . We assume is pre-stored in vehicles and RSUs.
4.3. Registration
- 1.
- invokes to generate a private–public key pair, i.e., , and sends to the CA via a secure channel. For simplicity, we assume that the key pair is used for both CGKAwAM and digital signature schemes.
- 2.
- Upon receiving , the CA does the following:
- (a)
- Issue an anonymous certificate ( = , , , , where is a pseudonym generated by the CA by running , is a serial number, denotes the validity period, and is a signature generated by running ).
- (b)
- Send to over a secure channel.
- 3.
- can then easily verify the signature () using the algorithm and store locally.
4.4. Preparation
- 1.
- When enters the area managed by , it generates a signature () on the message expressed as using , where is a timestamp and is the description of ’s resource information. Then, sends to .
- 2.
- Upon receiving , does the following:
- (a)
- Verify the validity of the signature by invoking . If the signature is invalid, abort; otherwise, invoke the Upload method (see Section 3.2) within to store the vehicle information.
- (b)
- Generate a signature () on the message () using , , where is the address of .
- (c)
- Send to .
- 3.
- can easily verify the validity of the received signature by invoking , , . Moreover, since the blockchain is public, it is straightforward to check the correctness of the contract address.
4.5. Initialization
- 1.
- Invoke the Create algorithm of CGKAwAM (see Section 3) to obtain the initialization local state () and a set of control messages ().
- 2.
- Deploy a VCSC smart contract (see Section 3.2.2) for the VC identified by via the RSU on the blockchain as follows:
- (a)
- Deploy the on the blockchain. If the deployment is successful, the RSU returns the contract address (); otherwise, the process is aborted.
- (b)
- Invoke the Update method within the contract to initialize the VC-related data (see Section 3.2.2).
- 3.
- Send each control message () to its corresponding vehicle in , attaching the same to all messages.
4.6. VC Management
- 1.
- A vehicle () invokes the Proposal algorithm of CGKAwAM (see Section 3) to generate a proposal message (). Here, cmd correspond to Join, Remove, and Update, respectively. For Join and Remove, , while for Update, , where is a random number selected by .
- 2.
- uploads message to the smart contract () through the RSU by invoking the Upload method, where .
- 3.
- Once message has been successfully stored, the RSU notifies the administrator () to handle the message.
- 4.
- invokes the Return(cmd) method within to retrieve .
- 5.
- runs the Commit algorithm of CGKAwAM to update its local state (), yielding a new state () and a set of control messages ().
- 6.
- invokes the Update method in to update the VC-related data using .
- In the case of Join, is added to the membership set.
- In the case of Remove, is excluded from the membership set.
- 7.
- sends each control message () to the corresponding vehicles. The recipient set differs slightly depending on the operation:
- Join: all members in ;
- Remove: all members in ;
- Update: all members in .
Each recipient vehicle () executes the Process algorithm of CGKAwAM to update its local state accordingly.
5. Security Analysis
5.1. Security Analysis of CGKAwAM
5.1.1. Security Definition and Model
- represents the identifier of the group session ().
- represents the role of in the group session (). If , the user is the administrator; otherwise, the user is the group member.
- represents the number of stages that have occurred in the group session () since its creation. This variable is used solely within the security model.
- represents a set containing the identifiers of the users in the group session () at stage t with whom intends to establish a session key, including himself.
- represents the group session key associated with the group session () at stage t.
- represents the status associated with group session at stage t. If the status is accepted, the session key () has been computed; otherwise, the status is unaccepted.
- represents the local state associated with group session at stage t. It corresponds to the γ state in our scheme (see Section 3).
- represents the messages sent and received in group session at stage t.
- : This query models the Setup algorithm of CGKAwAM. Upon receiving the security parameter (κ), simulates the CA to generate the common system parameter ().
- : This query models the KeyGen algorithm of CGKAwAM. Upon receiving the and a user identifier () chosen by , returns to the key pair () associated with the user identified by .
- : This query models the Create algorithm of CGKAwAM. In this query, is allowed to select an initial administrator () to cr(eate a VC with a group of users , where ). Then, initializes the oracle () and outputs a set of control messages.
- : This query models the Proposal algorithm of CGKAwAM. In this query, is allowed to submit a proposal message (), which suggests that the administrator () execute a command (). then uploads the proposal message to the smart contract.
- : This query models the Commit algorithm of CGKAwAM. In this query, is allowed to request the administrator () to execute the proposal message () within the session (). updates the variables associated with the oracle () and outputs a set of control messages.
- : This query models the Process algorithm of CGKAwAM. In this query, is allowed to request the user () to execute the control message (). updates the variables associated with the oracle ().
- : This query models the adversary’s ability to reveal a group session key in session at stage t. returns the group session key ().
- : This query models the adversary’s ability to compromise the user () in session at stage t. returns all the values stored in session at stage t, except the group session key.
- : It requires that and the output of be fresh (see Definition 10). If either of these two conditions is not satisfied, the query outputs ⊥. Otherwise, the output of this query is determined as follows: If (where the bit (b) is defined in Definition 9), it outputs ; otherwise (i.e., ), it outputs a random session key.
- 1.
- Before begins simulating the security game, it chooses a random bit ().
- 2.
- outputs a fixed query set of to , specifying the exact sequence of queries it intends to issue. Each query () corresponds to a specific query type defined in Definition 8. Note that the and queries are each restricted to be issued once, at most.
- 3.
- Once the game begins, allows to issue only the predefined queries in set and returns the corresponding responses.
- 4.
- After completing all queries, outputs a bit (). If , we say that wins the game. The advantage of is defined as .
- 1.
- : If , then set . Otherwise, set .
- 2.
- : If the adversary has not issued query and has not issued for any stage that is a partner of (see Definition 11), then set ; otherwise, set . ensures that the group session key is not trivially accessible by the adversary and is used to capture the notion of known-key security.
- 3.
- : If the adversary has not issued query and has not issued for any stage that is a partner of (see Definition 11), prior to , and the same condition holds for all related stages with , then set ; otherwise, set . is used to capture forward secrecy.
- 4.
- : For any , if has been queried by at any time prior to , then there must exist a stage () such that
- , indicating that both stages belong to the same group and that occurred earlier than .
- The stage corresponds to a group key update for initiated via a proposal with a UPD command and successfully executed, without being influenced by the adversary.
If this condition is satisfied for all such values, set ; otherwise, set . is used to capture post-compromise security.
- 1.
- They have the same status, i.e., .
- 2.
- They are associated with the same group identifier, i.e., .
- 3.
- They share the same participant list, i.e., .
- 4.
- They correspond to the same update stage of the group, i.e., .
5.1.2. Security Proof
5.2. Security Analysis of the Blockchain-Based Dynamic Key Management (BcDKM) Scheme
6. Performance Analysis
6.1. Functional Comparison
6.2. Computation and Communication Overhead
6.2.1. Computation Overhead
6.2.2. Communication Overhead
6.3. Simulation
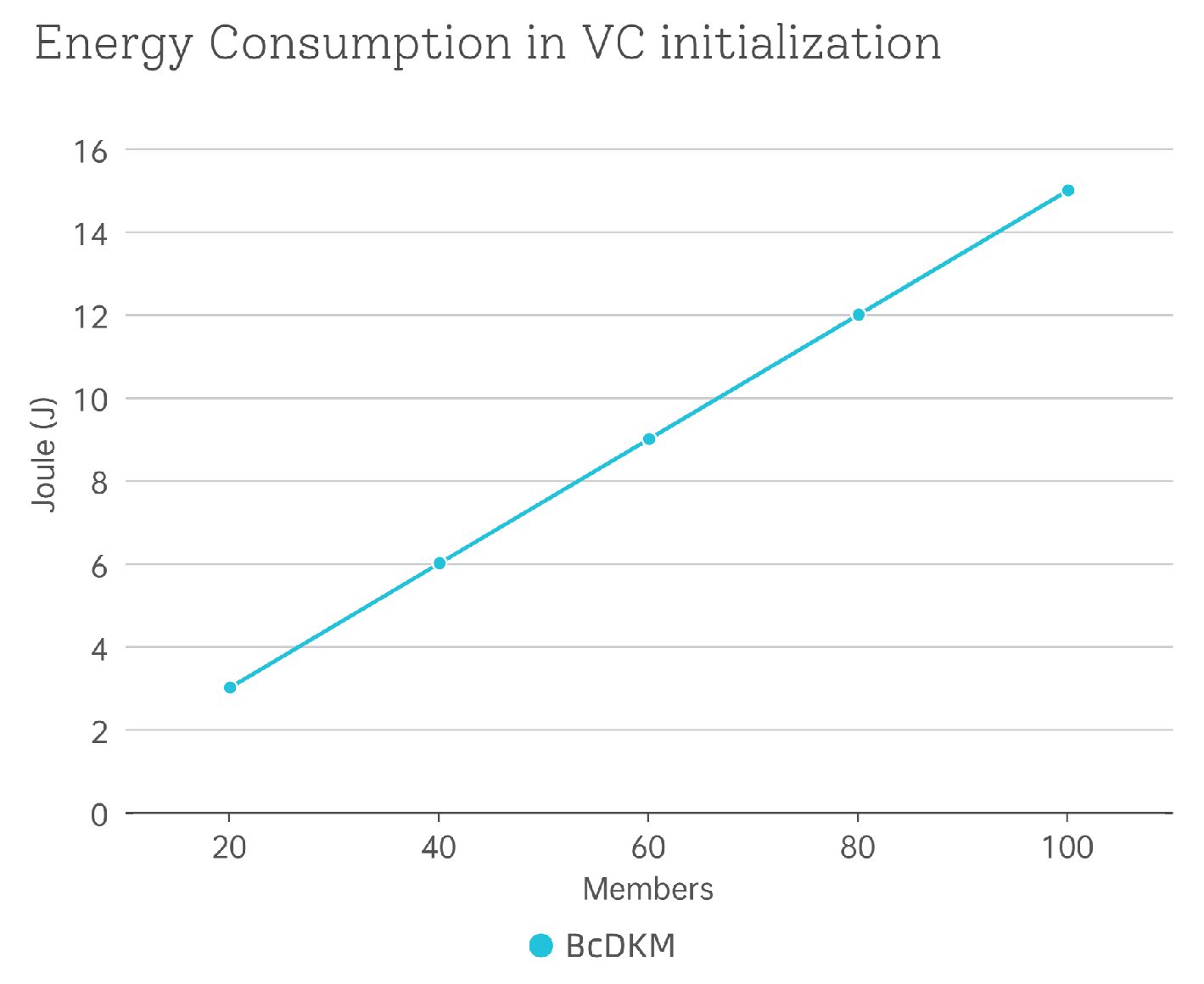
6.3.1. Computational Efficiency Evaluation
6.3.2. Smart Contract Overhead Evaluation
6.3.3. Network Simulation
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
- 1.
- runs and and sends the and public key () to .
- 2.
- outputs two equal-length messages .
- 3.
- chooses a random bit (), computes the challenge ciphertext (), and sends to .
- 4.
- outputs a guess bit ().
- 1.
- chooses a random bit ().
- 2.
- If , returns to for a uniformly random ; otherwise, it returns a uniformly random value () to .
- 3.
- outputs a guess bit ().
Appendix B
| Algorithm A1 |
|
| Algorithm A2 |
|
| Algorithm A3 |
|
Appendix C
| Algorithm A4 Vehicle Identity Smart Contract (VIDSC) |
|
| Algorithm A5 Vehicular Cloud Smart Contract (VCSC) |
|
Appendix D
- 1.
- Before begins simulating the security game, it chooses a random bit ().
- 2.
- Let be the sequence of queries issued by the (non-adaptive) adversary ().
- 3.
- Once the security game begins, allows to issue only the predefined queries in the query set () and returns the corresponding responses (see Definition 8). Since we assume is a non-adaptive adversary, the target group chosen by is fixed in advance. Considering the targeted group associated with the query set (), we describe the execution of the query set issued by by as follows:
- Initialization: The first query () must be the query, which initializes the system parameters and may be issued, at most, once. Subsequently, a subset of queries in , including , is executed to initialize the users. After the system parameters are generated and the users are initialized, the query is executed to initialize the target group for , and this query may also be issued, at most, once.
- Execution: The following queries in are then executed, allowing to interact with the targeted group. These queries include , , , , and .
- Challenge: Finally, the last query () must be the query. This query can be issued, at most, once and must not output ⊥.
- 4.
- After completing all queries, outputs a bit ().
- The algorithm simulates Game j through the following procedure:
- 1.
- Query the challenger in the PRG security game defined in Definition A1 to obtain a sequence of random values .
- 2.
- Let denote the -th level of the PBT (). In this game, any query that uses the PRG to compute on the secret value () in the tuple stored in node will have its PRG output replaced with the corresponding random value ().
- 3.
- For the remainder of the execution, the simulation proceeds identically to Game and outputs the bit returned by .
We now formally analyze the simulation described above and show that it is perfect. Specifically, we prove that the views of in hybrid Game and Game j are computationally indistinguishable. Observe that the only way for to distinguish between the two hybrid games is by distinguishing a sequence of random values () from those generated by the PRG . Since the queries issued by must satisfy the freshness (see Definition 10), it follows from conditions and with respect to freshness that is not allowed to obtain any secret values held by users of the group associated with the target session () at stage t. In particular, this implies that the secret values stored in node of the PBT at level j remain unknown to . We conclude that the above simulation is correct, without accessing the seed of the PRG security game.Hence, if can successfully distinguish between Game and Game j, then can leverage the advantage of to break the security of the PRG across multiple instances of the PRG security game, reaching a contradiction. We therefore derive the following advantage bound: - The algorithm simulates Game j through the following procedure:
- 1.
- Query the challenger in the CPA security game defined in Definition A1 to obtain a sequence of public keys .
- 2.
- Let denote the -th level of the PBT (). In this game, if a query (e.g., ) involves encrypting a secret value () using the public key stored in node , the original public key in the tuple is replaced with the corresponding public key ().
- 3.
- Set and .
- 4.
- Send to the challenger in the CPA security game and receives the ciphertext ().
- 5.
- For the remainder of the execution, the simulation proceeds identically to Game and outputs the bit returned by .
The only difference between Game and Game j is that in Game j, for queries (e.g., ), the resulting ciphertexts are replaced with fake ciphertexts, whereas in Game , they are generated using the public key encryption scheme.We now formally analyze the simulation described above and show that it is perfect. Specifically, we prove that the views of in hybrid Game and Game j are computationally indistinguishable. First, the queries issued by must satisfy the freshness (see Definition 10), and it follows from conditions and with respect to freshness that is not allowed to obtain any secret values held by users of the group associated with the target session () at stage t. Since the adversary does not possess the corresponding secret keys, cannot distinguish between the public keys used in Game and those replaced in Game j with the challenge public key provided by the CPA security game. Observe that the only way for to distinguish between the two hybrid games is by distinguishing a sequence of ciphertext from those generated by the PKE scheme.We conclude that the above simulation is correct.Hence, if can successfully distinguish between Game and Game j, then can leverage the advantage of to break the security of the CPA across multiple instances of the CPA security game, reaching a contradiction. Consequently, we derive the following advantage bound:
References
- Cao, D.; Wang, X.; Li, C.; Lv, C.; Na, X.; Xing, Y. Future Directions of Intelligent Vehicles: Potentials, Possibilities, and Perspectives. IEEE Trans. Intell. Veh. 2022, 7, 7–10. [Google Scholar] [CrossRef]
- Whaiduzzaman, M.; Sookhak, M.; Gani, A.; Buyya, R. A survey on vehicular cloud computing. J. Netw. Comput. Appl. 2014, 40, 325–344. [Google Scholar] [CrossRef]
- Boukerche, A.; Robson, E. Vehicular cloud computing: Architectures, applications, and mobility. Comput. Netw. 2018, 135, 171–189. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, L.; Yang, Y.; Choo, K.K.R. Certificateless signature scheme with batch verification for secure and privacy-preserving V2V communications in VANETs. IEEE Trans. Dependable Secure Comput. 2025, 22, 1448–1459. [Google Scholar] [CrossRef]
- Olariu, S. A survey of vehicular cloud research: Trends, applications and challenges. IEEE Trans. Intell. Transp. Syst. 2019, 21, 2648–2663. [Google Scholar] [CrossRef]
- Mekki, T.; Jabri, I.; Rachedi, A.; Ben Jemaa, M. Vehicular cloud networks: Challenges, architectures, and future directions. Veh. Commun. 2017, 9, 268–280. [Google Scholar] [CrossRef]
- Awais, S.M.; Yucheng, W.; Mahmood, K.; Akram, M.W.; Hussain, S.; Das, A.K.; Park, Y. PUF-based privacy-preserving simultaneous authentication among multiple vehicles in VANET. IEEE Trans. Veh. Technol. 2023, 73, 6727–6739. [Google Scholar] [CrossRef]
- Danquah, W.M.; Altilar, D.T. Vehicular cloud resource management, issues and challenges: A survey. IEEE Access 2020, 2020 8, 180587–180607. [Google Scholar] [CrossRef]
- Zheng, Y.; Chen, Y.; Tan, C.; Yang, Y.; Shu, C.; Chen, L. Optimization model for vehicular network data queries in edge environments. J. Cloud Comput. 2024, 13, 145. [Google Scholar] [CrossRef]
- Maurer, U.M.; Wolf, S. The diffie-hellman protocol. Des. Codes Cryptogr. 2000, 19, 147–171. [Google Scholar] [CrossRef]
- Li, J.; Wen, M.; Zhang, T. Group-based authentication and key agreement with dynamic policy updating for MTC in LTE-A networks. IEEE Internet Things J. 2015, 3, 408–417. [Google Scholar] [CrossRef]
- Kim, Y.; Perrig, A.; Tsudik, G. Group key agreement efficient in communication. IEEE Trans. Comput. 2004, 53, 905–921. [Google Scholar] [CrossRef]
- Jiang, Q.; Ni, J.; Ma, J.; Yang, L.; Shen, X. Integrated authentication and key agreement framework for vehicular cloud computing. IEEE Netw. 2018, 32, 28–35. [Google Scholar] [CrossRef]
- Joux, A. A one round protocol for tripartite Diffie-Hellman. In Proceedings of the International Algorithmic Number Theory Symposium, Leiden, The Netherlands, 2–7 July 2000; pp. 385–393. [Google Scholar]
- Khurana, D.; Rao, V.; Sahai, A. Multi-party key exchange for unbounded parties from indistinguishability obfuscation. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Auckland, New Zealand, 29 November–3 December 2015; pp. 52–75. [Google Scholar]
- Wu, Q.; Mu, Y.; Susilo, W.; Qin, B.; Domingo-Ferrer, J. Asymmetric group key agreement. In Proceedings of the 28th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cologne, Germany, 26–30 April 2009; pp. 153–170. [Google Scholar]
- Zhang, R.; Zhang, L.; Wu, Q.; Zhou, J. Secure channel establishment scheme for task delivery in vehicular cloud computing. IEEE Trans. Inf. Forensics Secur. 2024, 19, 2865–2880. [Google Scholar] [CrossRef]
- Zhang, L.; Meng, X.; Choo, K.K.R.; Zhang, Y.; Dai, F. Privacy-preserving cloud establishment and data dissemination scheme for vehicular cloud. IEEE Trans. Dependable Secur. Comput. 2018, 17, 634–647. [Google Scholar] [CrossRef]
- Zhang, R.; Han, W.; Zhang, L.; Wang, L.; Meng, X. Provably secure receiver-unrestricted group key management scheme for mobile ad hoc networks. Sensors 2023, 9, 4198. [Google Scholar] [CrossRef] [PubMed]
- Zhang, L. Key management scheme for secure channel establishment in fog computing. IEEE Trans. Cloud Comput. 2019, 9, 1117–1128. [Google Scholar] [CrossRef]
- Alwen, J.; Coretti, S.; Dodis, Y.; Tselekounis, Y. Security Analysis and Improvements for the IETF MLS Standard for Group Messaging. In Proceedings of the Annual International Cryptology Conference, Santa Barabara, CA, USA, 17–21 August 2020; pp. 248–277. [Google Scholar]
- Xu, G.; Yin, X.; Li, X. ER-CGKA: Efficient and robust continuous group key agreement scheme with post-compromise security forward security for IoV. PLoS ONE 2024, 19, e0307867. [Google Scholar] [CrossRef]
- Balbás, D.; Collins, D.; Vaudenay, S. Cryptographic administration for secure group messaging. In Proceedings of the 32nd USENIX Security Symposium, Anaheim, CA, USA, 9–11 August 2023; pp. 1253–1270. [Google Scholar]
- Cheng, Y.; Agrawal, D.P. An improved key distribution mechanism for large-scale hierarchical wireless sensor networks. Ad Hoc Netw. 2007, 5, 35–48. [Google Scholar] [CrossRef]
- Xu, G.; Li, X.; Jiao, L.; Wang, W.; Liu, A.; Su, C. BAGKD: A batch authentication and group key distribution protocol for VANETs. IEEE Commun. Mag. 2020, 58, 35–41. [Google Scholar] [CrossRef]
- Li, C.; Ji, S.; Zhang, X.; Wang, H.; Li, D.; Liu, H. An Effective and Secure Key Management Protocol for Message Delivery in Autonomous Vehicular Clouds. Sensors 2018, 18, 2896. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and privacy on blockchain. ACM Comput. Surv. 2019, 52, 25. [Google Scholar] [CrossRef]
- Li, X.; Yin, X. Blockchain-based group key agreement protocol for vehicular ad hoc networks. Comput. Commun. 2022, 183, 107–120. [Google Scholar] [CrossRef]
- Royo, S.; Ballesta-Garcia, M. An overview of lidar imaging systems for autonomous vehicles. Appl. Sci. 2019, 9, 4093. [Google Scholar] [CrossRef]
- Fan, L.; Wang, J.; Chang, Y.; Li, Y.; Wang, Y.; Cao, D. 4D mmWave radar for autonomous driving perception: A comprehensive survey. IEEE Trans. Intell. Veh. 2024, 9, 4606–4620. [Google Scholar] [CrossRef]
- NVIDIA. DRIVE AGX Orin Developer Kit Overview. 2025. Available online: https://developer.nvidia.com/drive/agx (accessed on 5 September 2025).
- Nguyen, H.; Guan, Y.L. DSRC Performance Under the Adjacent Channel Interference of Cellular-Based V2X at 5.9 GHz Band. In Proceedings of the IEEE 99th Vehicular Technology Conference, Singapore, 24–27 June 2024; pp. 1–5. [Google Scholar]
- Tsiounis, Y.; Yung, M. On the security of ElGamal based encryption. Public Key Cryptogr. 1998, 1431, 117–134. [Google Scholar]
- MIRACL Ltd. MIRACL Cryptographic SDK: Multiprecision Integer and Rational Arithmetic Cryptographic Library. 2025. Available online: https://github.com/miracl/MIRACL (accessed on 5 September 2025).
- Gillmor, D. Negotiated Finite Field Diffie-Hellman Ephemeral Parameters for Transport Layer Security (TLS). Available online: https://www.rfc-editor.org/rfc/rfc7919 (accessed on 5 September 2025).
- Remix. 2025. Available online: https://remix.ethereum.org (accessed on 5 September 2025).
- NS-3 Network Simulator. 2025. Available online: https://www.nsnam.org (accessed on 5 September 2025).



| Property | TGKA [12] | NIGKA [15] | GKD [26] | AGKA [17] | ER-CGKA [22] | BcGKA [28] | Ours |
|---|---|---|---|---|---|---|---|
| Vehicle privacy | × | × | ✓ | ✓ | ✓ | ✓ | ✓ |
| Known-key security | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Forward secrecy | × | × | × | × | ✓ | × | ✓ |
| Post-compromise security | × | × | × | × | ✓ | × | ✓ |
| Distributed VC Discovery | × | × | × | × | × | ✓ | ✓ |
| Distributed Management | × | × | × | × | × | × | ✓ |
| Round optimality | ✓ | ✓ | × | ✓ | ✓ | × | ✓ |
| Large-scale VC scalability | × | × | × | × | ✓ | × | ✓ |
| Scheme | VC Initialization | Join |
|---|---|---|
| GKD [26] | + | |
| AGKA [17] | + + | |
| BcGKA [28] | ||
| Ours | + |
| Scheme | VC Initialization | Join | Remove | Update | ||||
|---|---|---|---|---|---|---|---|---|
| Overhead | Rounds | Messages | Rounds | Messages | Rounds | Messages | Rounds | Messages |
| GKD [26] | 4 | 1 | 1 | 1 | ||||
| AGKA [17] | 1 | 1 | 1 | 1 | ||||
| BcGKA [28] | 2 | 1 | 1 | 1 | ||||
| Ours | 1 | 1 | 1 | 1 | ||||
| Method | Deploy | Upload | Update | Return |
|---|---|---|---|---|
| VIDSC | 504,155 | 91,498 | - | - |
| VCSC | 1,246,805 | 185,560 | 29,618 | 25,193 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, M.; Meng, R.; Zhang, L. BcDKM: Blockchain-Based Dynamic Key Management Scheme for Crowd Sensing in Vehicular Sensor Networks. Sensors 2025, 25, 5699. https://doi.org/10.3390/s25185699
Zhang M, Meng R, Zhang L. BcDKM: Blockchain-Based Dynamic Key Management Scheme for Crowd Sensing in Vehicular Sensor Networks. Sensors. 2025; 25(18):5699. https://doi.org/10.3390/s25185699
Chicago/Turabian StyleZhang, Mingrui, Ru Meng, and Lei Zhang. 2025. "BcDKM: Blockchain-Based Dynamic Key Management Scheme for Crowd Sensing in Vehicular Sensor Networks" Sensors 25, no. 18: 5699. https://doi.org/10.3390/s25185699
APA StyleZhang, M., Meng, R., & Zhang, L. (2025). BcDKM: Blockchain-Based Dynamic Key Management Scheme for Crowd Sensing in Vehicular Sensor Networks. Sensors, 25(18), 5699. https://doi.org/10.3390/s25185699





